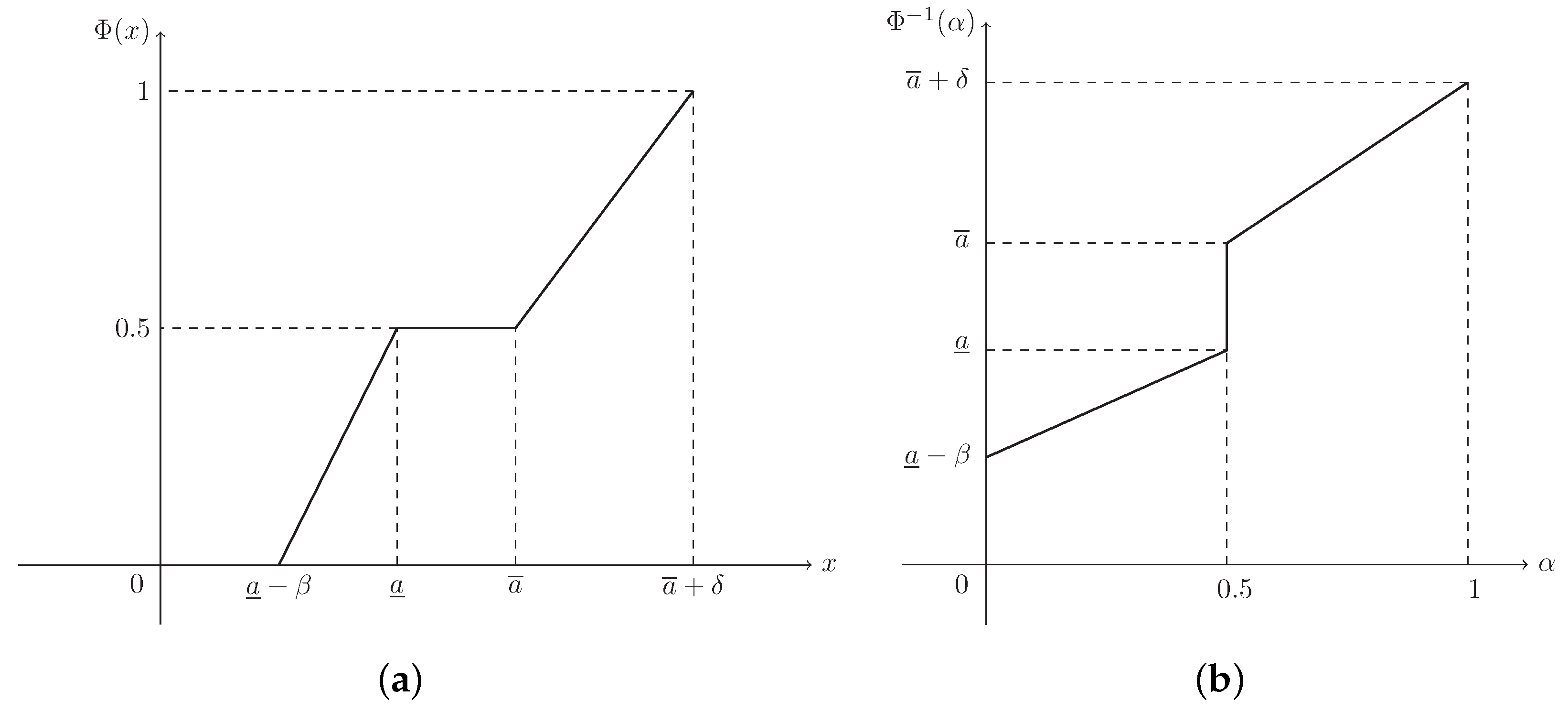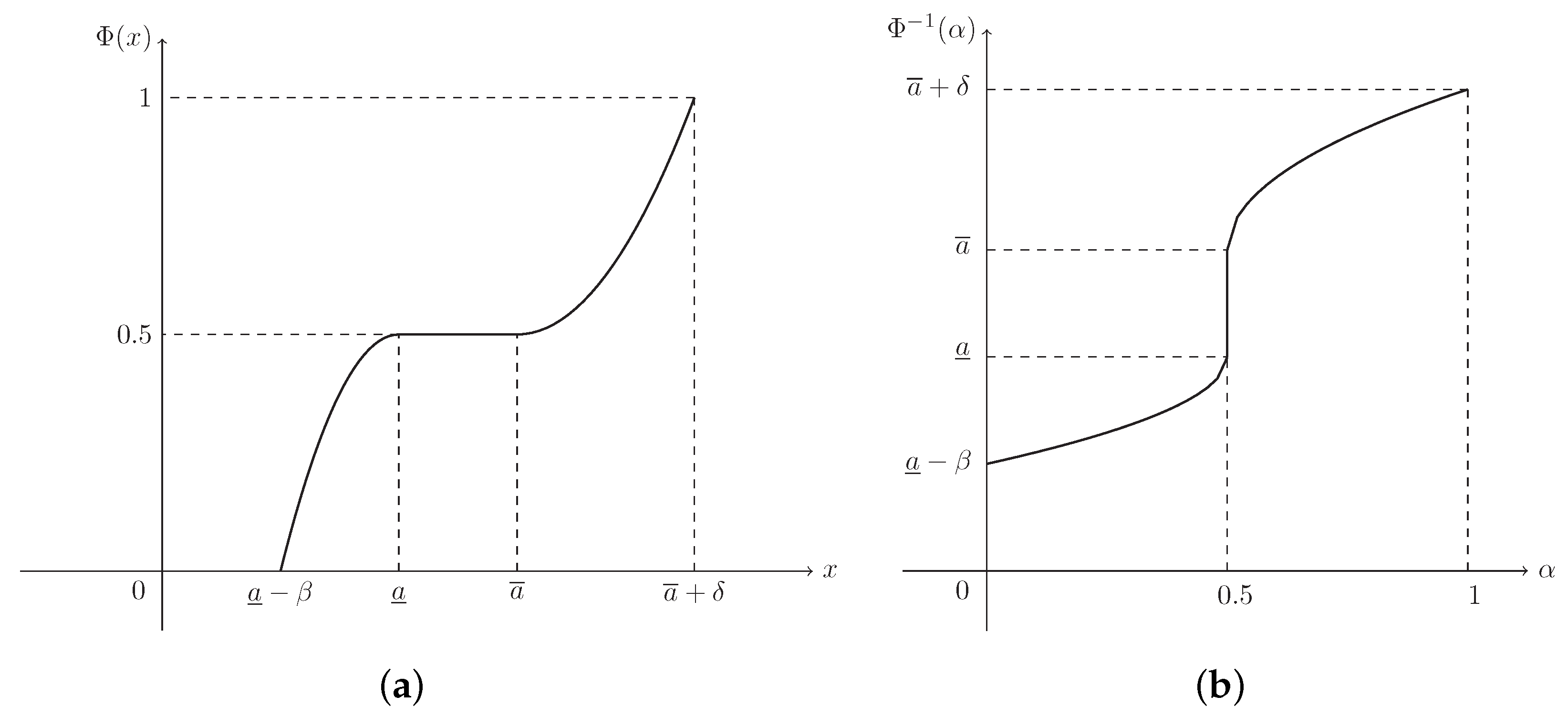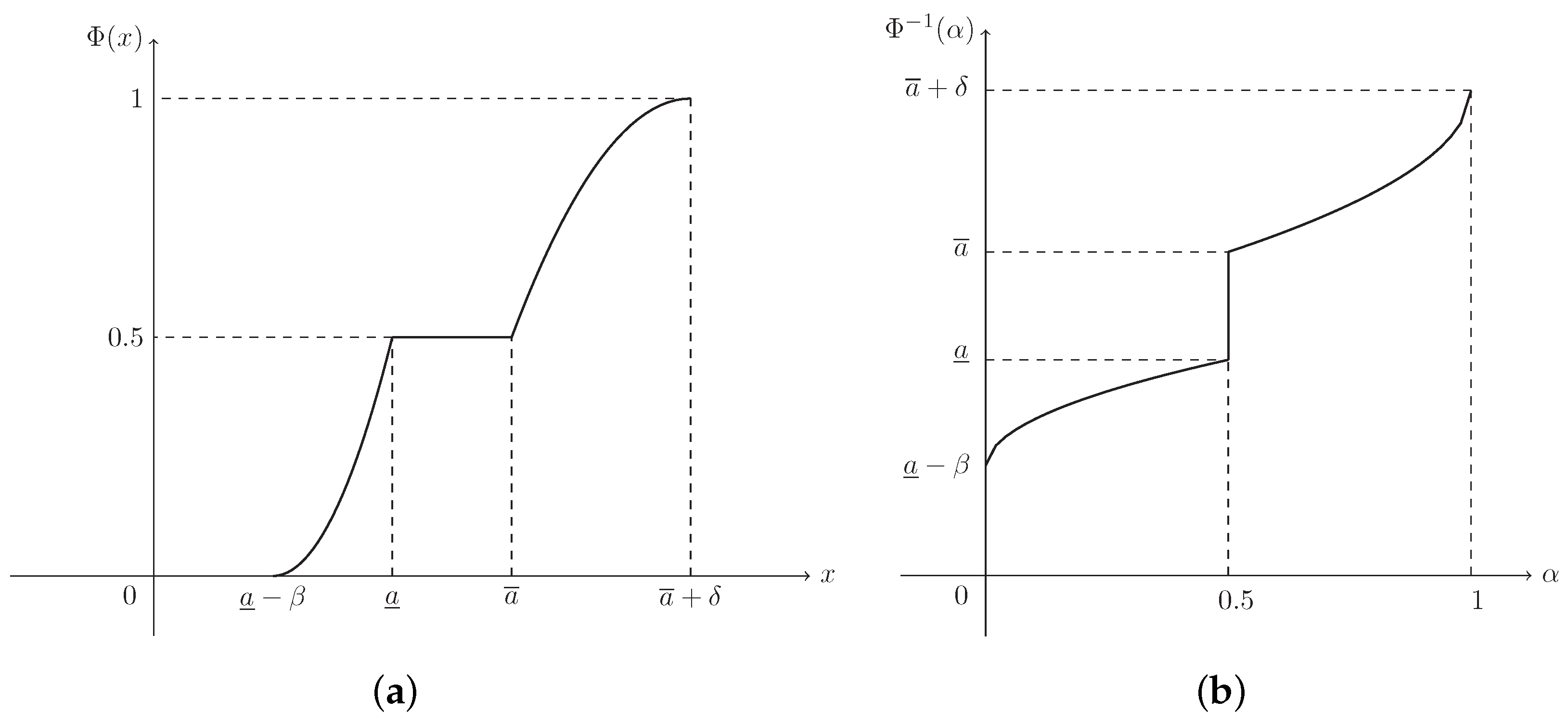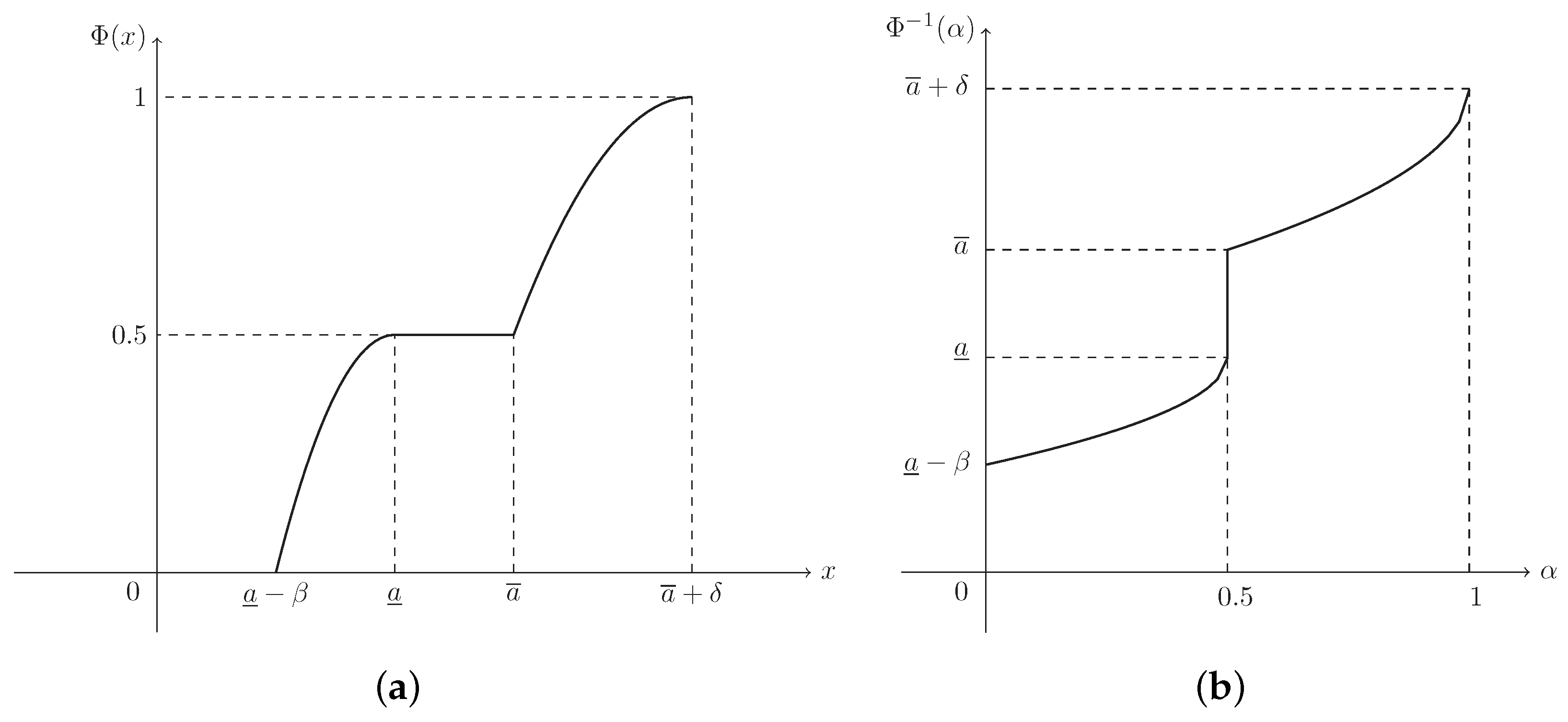Abstract
Entropy has continuously arisen as one of the pivotal issues in optimization, mainly in portfolios, as an indicator of risk measurement. Aiming to simplify operations and extending applications of entropy in the field of LR fuzzy interval theory, this paper first proposes calculation formulas for the entropy of function via the inverse credibility distribution to directly calculate the entropy of linear function or simple nonlinear function of LR fuzzy intervals. Subsequently, to deal with the entropy of complicated nonlinear function, two novel simulation algorithms are separately designed by combining the uniform discretization process and the numerical integration process with the proposed calculation formulas. Compared to the existing simulation algorithms, the numerical results show that the advantage of the algorithms is well displayed in terms of stability, accuracy, and speed. On the whole, the simplified calculation formulas and the effective simulation algorithms proposed in this paper provide a powerful tool for the LR fuzzy interval theory, especially in entropy optimization.
1. Introduction
Entropy, which made its debut in 1948, was designed by Shannon [1] to measure the randomness or uncertainty of a random phenomenon. Since then, entropy has been extensively applied to various fields such as physics, finance, medicine, artificial intelligence, and so on. Philippatos and Wilson [2] scored a first by using entropy in portfolio selection problems and illustrated the construction of mean-entropy efficient portfolios. Simonelli [3] considered the entropy as an increased portfolio risk and verified the effectiveness of entropy. In addition, Xiao and Qin [4] employed a weighted combination method based on the belief entropy function [5] to solve the evidence conflict problem in multi-sensor data fusion. Guan et al. [6] presented a maximum entropy solution for implementing active queue management. In addition, Gustafsson et al. [7] used maximum entropy to improve the Bayesian credibility interval for classifier error rates. In the field of optimization, Zhang et al. [8] summarized entropy used in crowd analysis and concluded that it can effectively deal with the issues related to crowd abnormal behavior detection, crowd counting and density estimation, and crowd motion segmentation. Khan et al. [9] emphasized the optimal estimations of auxiliary variables including the entropy generation modeled via second thermodynamics law to solve flow problems. Besides, Wang et al. [10] presented a Renyi mean-entropy-skewness information criterion so that the scheduling optimization problems in flexible manufacturing systems can be handled.
It should be noted that studies above are all conducted under the probabilistic framework, which needs to collect large amounts of sample data to figure out probability distributions. However, there are many non-random factors in reality such as vagueness and ambiguity, associated in a natural way with different types of linguistic expressions, which makes the research of entropy under the probabilistic framework not yet suitable. As another study on entropy under uncertain environments, Zadeh [11] proposed new operations for the calculus of logic and initially mentioned entropy in his theory of fuzzy sets in 1965. Zadeh [12] further defined the entropy as a weighted Shannon entropy to quantify the fuzziness of an event. Moreover, Criadoa and Gachechiladzeb [13] considered the uncertainty of possibility to describe Zadeh’s general formula for the entropy. Meanwhile, there exist many applications of entropy under the possibility theory. For instance, when distributions were multimodal or discontinuous, Smaldino [14] adopted entropy to characterize the uncertainty regarding the state of the environment, which was faced by moving organisms. Liu and Zhang [15] proposed a general multi-period fuzzy portfolio optimization model with return demand which involved the entropy based on possibility measure to maximize both terminal and cumulative diversification. Additionally, Yin et al. [16] provided a possibility-based robust design optimization framework in which the entropy of the fuzzy system response was regarded as the variability index for the uncertain structural-acoustic system.
The possibility measure has properties including normality, nonnegativity and maximality [17], bar self-duality. Since self-duality is of utmost importance in both theory and practice, adhering to human’s intuition to a large extent, Liu and Liu [18] creatively defined the credibility measure, which equals the average value of the possibility measure and the necessity measure. In accordance with the credibility measure, Li and Liu [19] introduced the entropy to depict the uncertainty associated with fuzzy variables. Since then, a handful of theoretical research on entropy under the credibility theory is carried out (see, e.g., [20,21]). Recently, Rahimi et al. [22] provided novel definitions of entropy of intuitionistic fuzzy variables based on the notion of credibility under intuitionistic fuzzy environment. According to credibility measure, Zhou et al. [23] studied the entropy of LR fuzzy numbers, and the calculation formulas together with related concepts were proposed in great detail.
Meanwhile, the entropy derived from credibility measure was also employed in decision-making process. Table 1 displays the application literature about credibility theory, summarizing the objects processed by the entropy of function , including the types of fuzzy variables and function f, and further considers whether the entropy of function can be clearly and analytically expressed excluding the measure operator. Most of the current literature tackled the entropy of linear function of fuzzy variables with the same type in portfolios, and thus the explicit expression of entropy of function could be obtained with no difficulty from the arithmetic operation linearity of fuzzy variables. Differently, Li [21] studied the entropy of linear function containing different types of fuzzy variables. Since it was difficult to obtain the explicit expression of entropy in this case, fuzzy simulation was used by Li [21] to solve this problem.

Table 1.
A summary of literature on calculation of fuzzy entropy of function, . Our paper improves the existing work and reduces the computation complexity via an explicit expression for both linear and nonlinear functions involving different types of fuzzy variables.
Fuzzy simulation is a widely accepted technique for simulating approximations, which has been studied by plenty of scholars since it was introduced by Bruckley and Hayashi [30] to solve fuzzy optimization problems in 1994. Liu and Iwamura [31] designed the fuzzy simulation whose basic idea was to convert continuous fuzzy numbers into discrete fuzzy ones by stochastically generating sample points to deal with the fuzzy chance constrained programming. After that, Liu [32] introduced this technique to solve different fuzzy programming problems based on the concept of credibility, relying on randomly generating discrete membership degrees. Huang [33] then took the lead in fuzzy simulation for entropy (FSE) based on Liu [32]’s idea, and innovatively performed stochastic discretization simulation on the entropy-integrated function, that is, the credibility function. Later, Li [21] also simulated the entropy of function to handle the entropy optimization models involving entropy of general function through stochastic discretization process in [32], which assumed that the joint credibility function was known (the simulation algorithm is denoted as FSE* in this paper). Table 2 shows the function studied in [21] and [33], as well as the principles and accuracy of the algorithms. Since the stochastic discretization simulation in Liu [32] would inevitably lead to inaccurate and lower membership degrees especially when the number of fuzzy variables involved in the function increases as pointed out in Miao et al. [34], the two existing simulation algorithms FSE and FSE* are both with low accuracy.

Table 2.
A summary of current simulation algorithms for entropy of function . Our paper improves the existing work with extremely high accuracy and short computing time by presenting the uniformly discretization algorithm and the numerical integration algorithm for monotone functions.
According to the literature mentioned above, there is a paucity of theoretical research of entropy based on credibility measure. Also, the application research is basically aimed at linear functions, merely involving simple triangular or trapezoidal fuzzy numbers of the same category, thus it is mainly applied in portfolios. Moreover, there is no research on entropy of nonlinear function. Attracted by this limited status, and considering that LR fuzzy intervals summarize triangle, trapezium, Gauss, and other nonlinear curves in fuzzy set theory, this paper is aimed at improving the calculation of fuzzy entropy of functions with respect to LR fuzzy intervals by simplifying the operation formulas and designing novel simulation algorithms from an entirely different perspective so as to extend the application situations of fuzzy entropy in decision-making problems. There are two main contributions in this paper. In terms of the definition for entropy pioneered by Li and Liu [19], some calculation formulas with analytical expressions for the entropy of fuzzy variable and function are derived separately by using the inverse credibility distribution (ICD), which can be used to figure out the entropy without difficulty when f is a linear function or a simple nonlinear function. With regard to the situation when f is a complicated nonlinear function, two simulation algorithms are designed to approximate the entropy of function on the basis of the presented calculation formulas, including the uniform discretization algorithm (UDA) referring to the method of generating the exact membership degree of each function value proposed by Miao et al. [34] and the numerical integration algorithm (NIA) based on the operational law of ICD proposed by Zhou et al. [35].
After the brief introduction as Section 1, this paper reviews fundamental knowledge of LR fuzzy intervals and credibility theory in Section 2. Section 3 proposes the calculation formulas for entropy of variable and function separately, and derives the linearity property of entropy operator. Section 4 describes the existing simulation algorithms in [21,33], and further provides two new algorithms to simulate the entropy of function. In Section 5, some numerical experiments are conducted to depict the performance of these algorithms from different perspectives, followed by Section 6, which summarizes conclusions.
2. Preliminaries
In this section, we present some preliminary concepts, theorems, and examples related to LR fuzzy intervals and monotone functions in the credibility theory, which will be employed throughout the whole paper.
Definition 1.
(Dubois and Prade [36]) L (or R) is a decreasing function from , known as a shape function such that
- (1)
- (2)
- (3)
- (4)
Definition 2.
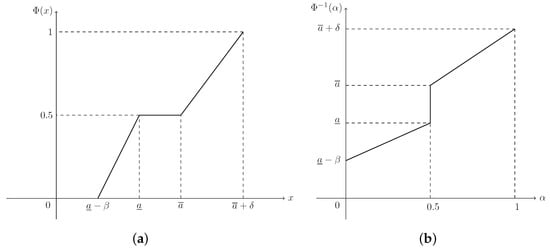
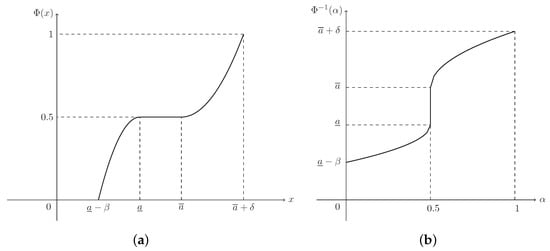
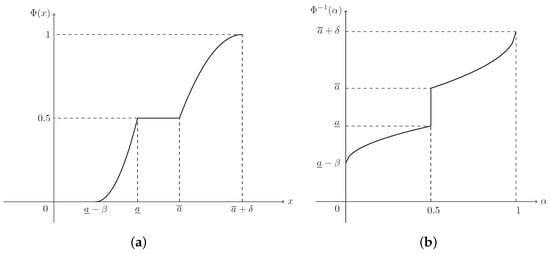
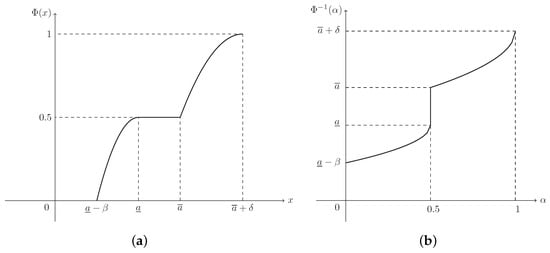
(Dubois and Prade [36]) A fuzzy interval ξ is of LR-type if there exist shape functions L (for left) and R (for right), and scalers with membership function (MF)
which is denoted as , where is the core of ξ, and are respectively called the lower and upper modal values, β and δ are respectively called the left-hand and right-hand spreads.
Remark 1.
When , the LR fuzzy interval degenerate to an LR fuzzy number, e.g., a triangular fuzzy number or a Gaussian fuzzy number [37]. In other words, the LR fuzzy number is a special case of LR fuzzy interval discussed in this paper.
For an LR fuzzy interval defined in Definition 2, the shape functions L and R determine its type, while the parameters determine its position and spreads. Examples 1–4 provide some commonly used LR fuzzy intervals with the same parameter setting and the different shape functions, including trapezoidal fuzzy numbers, parabolic fuzzy intervals, normal fuzzy intervals, and mixture fuzzy intervals. These fuzzy intervals will be used to illustrate our work in the following sections.
Example 1.
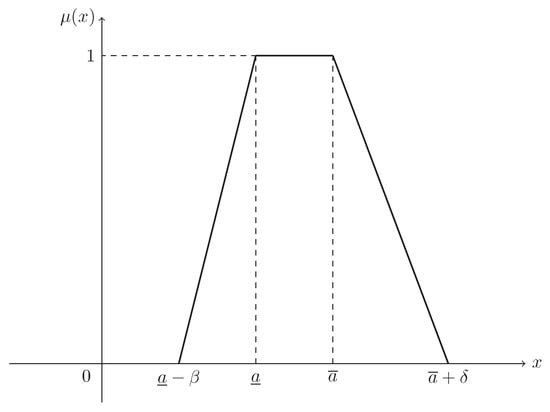
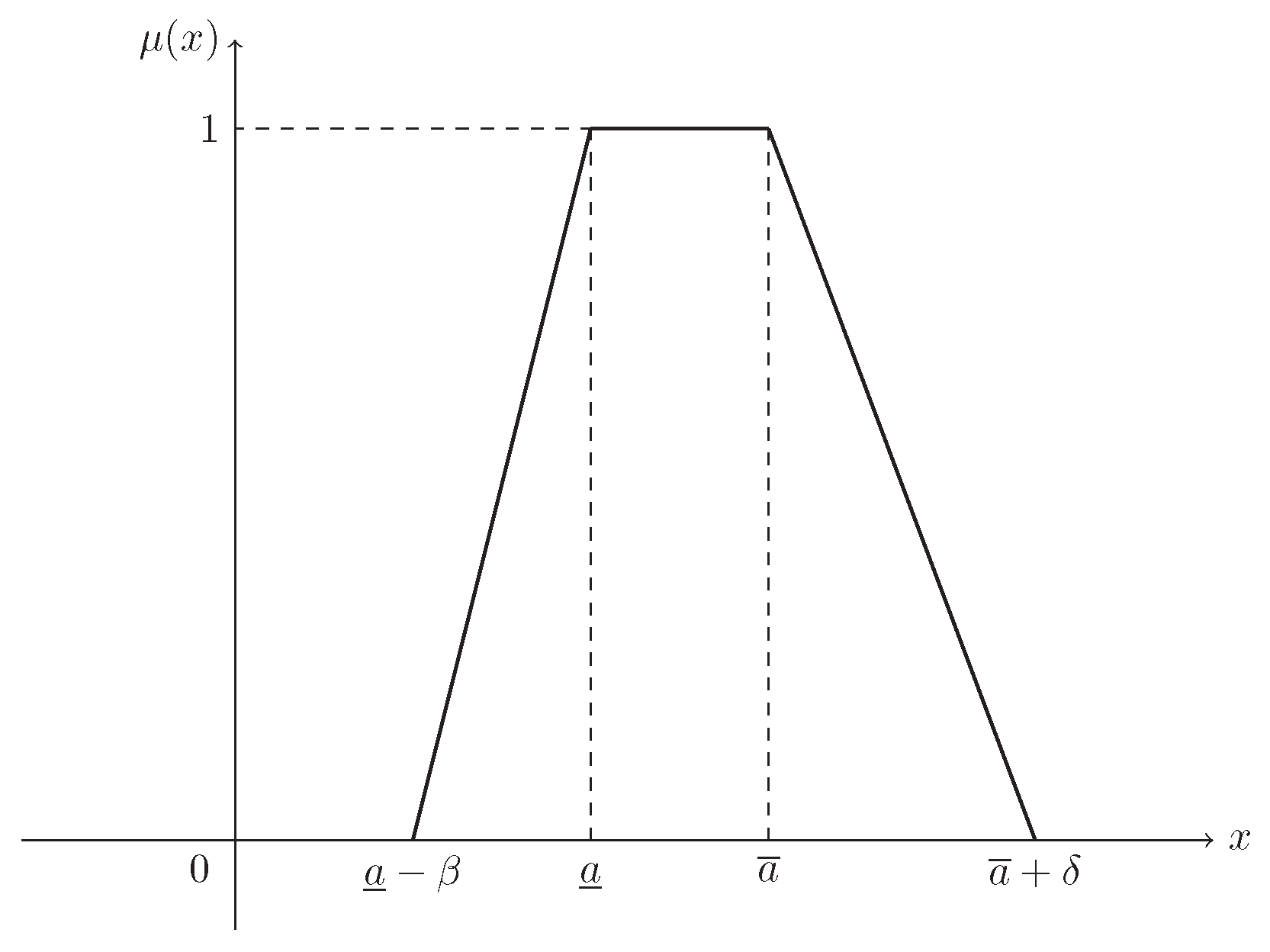
Supposing that , then ξ is known as a trapezoidal fuzzy number, denoted by , and its MF is (see Figure 1)

Figure 1.
The MF in Example 1. is the MF in Equation (2) of trapezoidal fuzzy number .
Example 2.
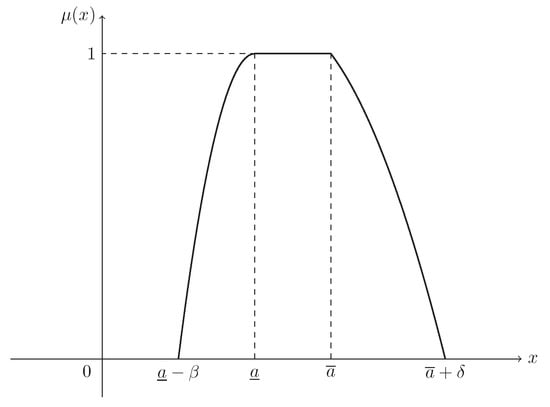
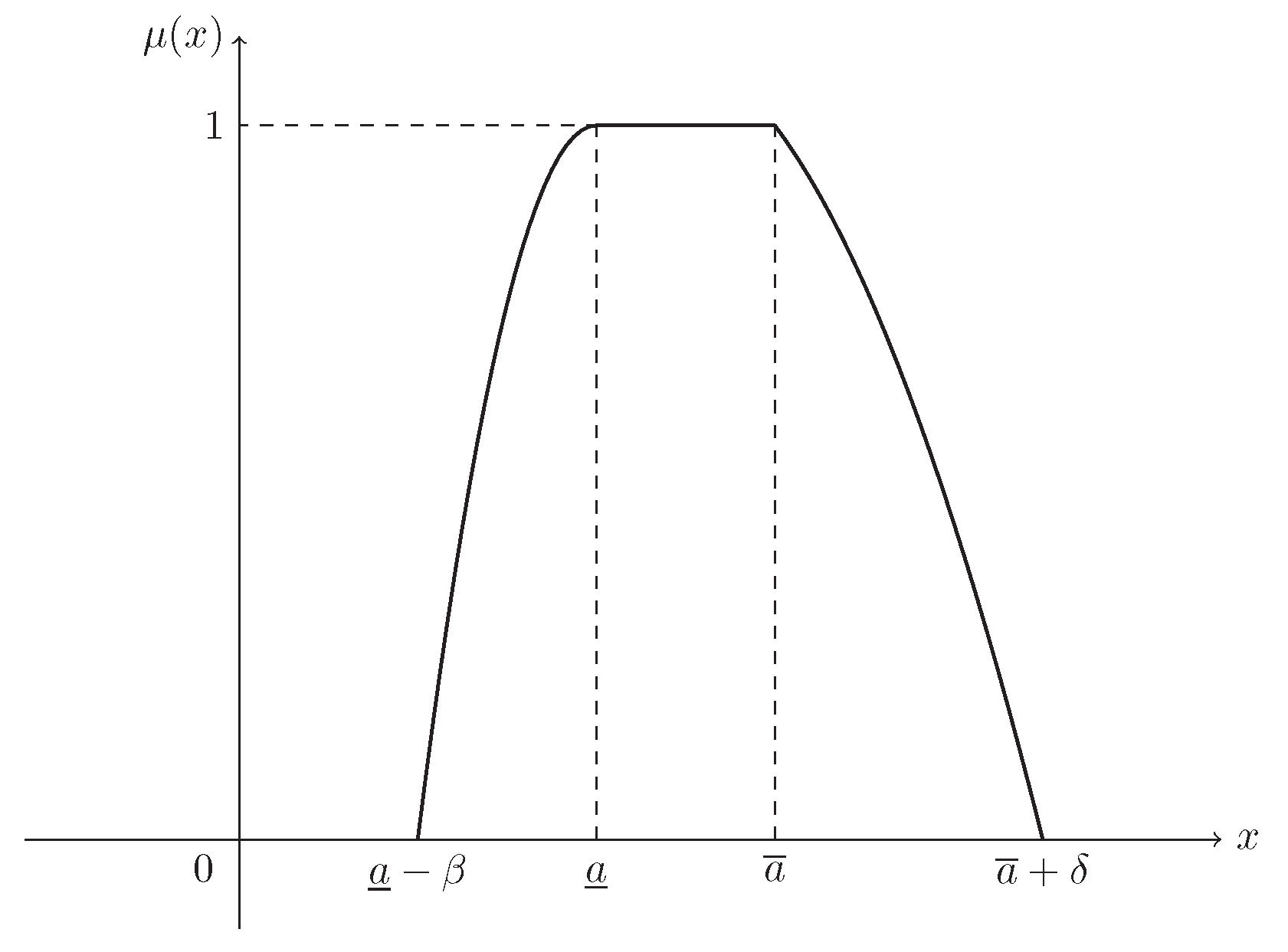
If , then ξ is known as a parabolic fuzzy interval, denoted by , and its MF is (see Figure 2)

Figure 2.
The MF in Example 2. is the MF in Equation (3) of parabolic fuzzy interval .
Example 3.
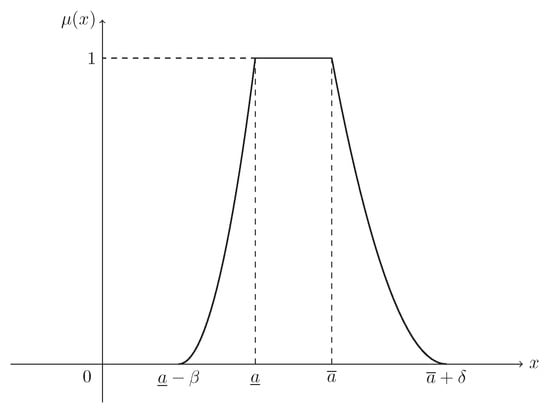
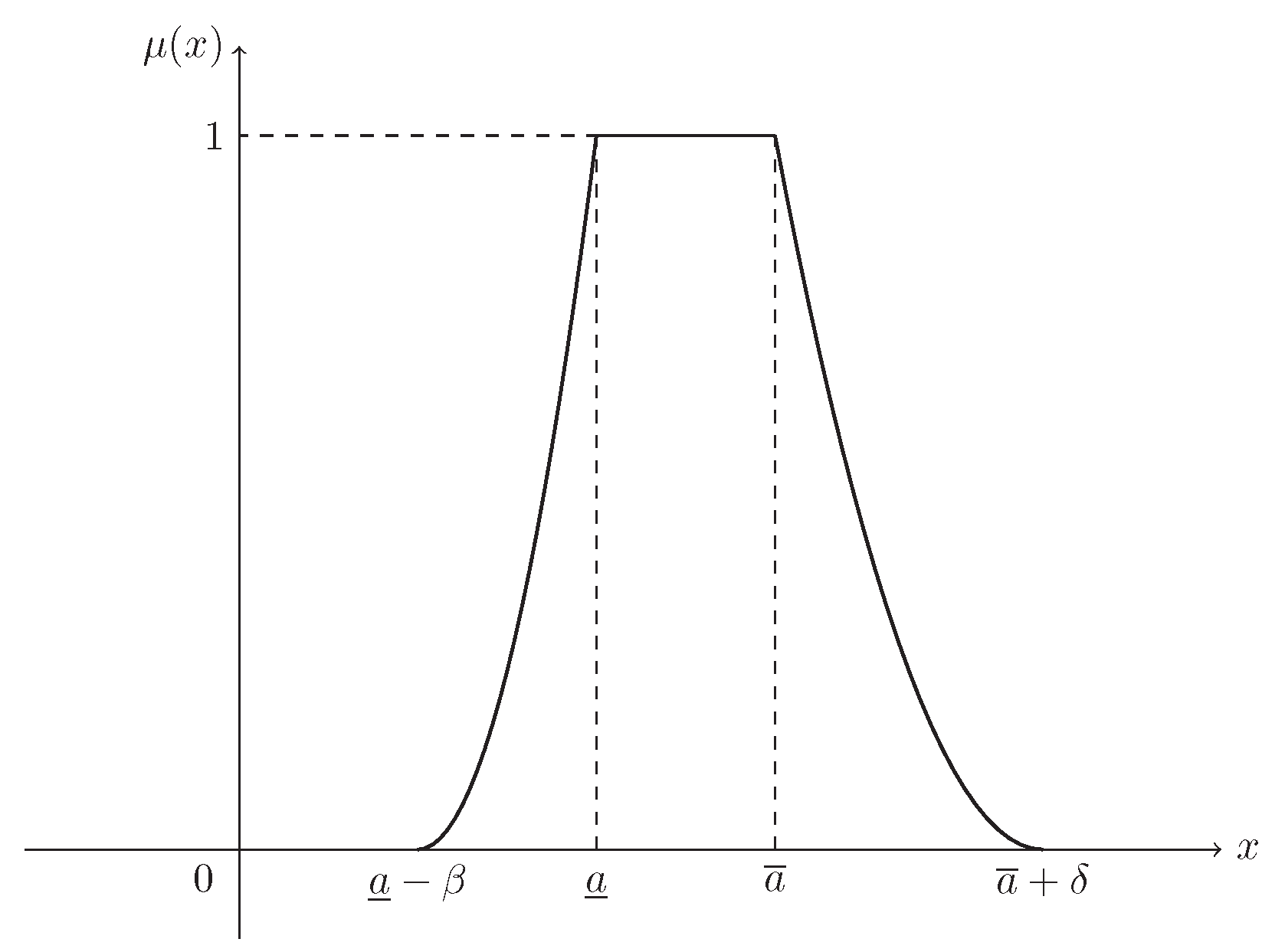
Suppose that . Then ξ is known as a normal fuzzy interval, denoted by , with (see Figure 3)

Figure 3.
The MF in Example 3. is the MF in Equation (4) of normal fuzzy interval .
Example 4.
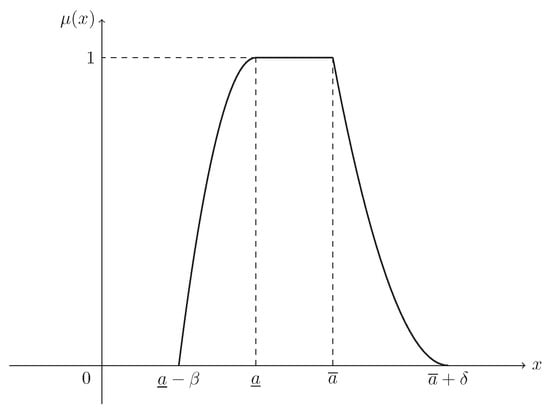
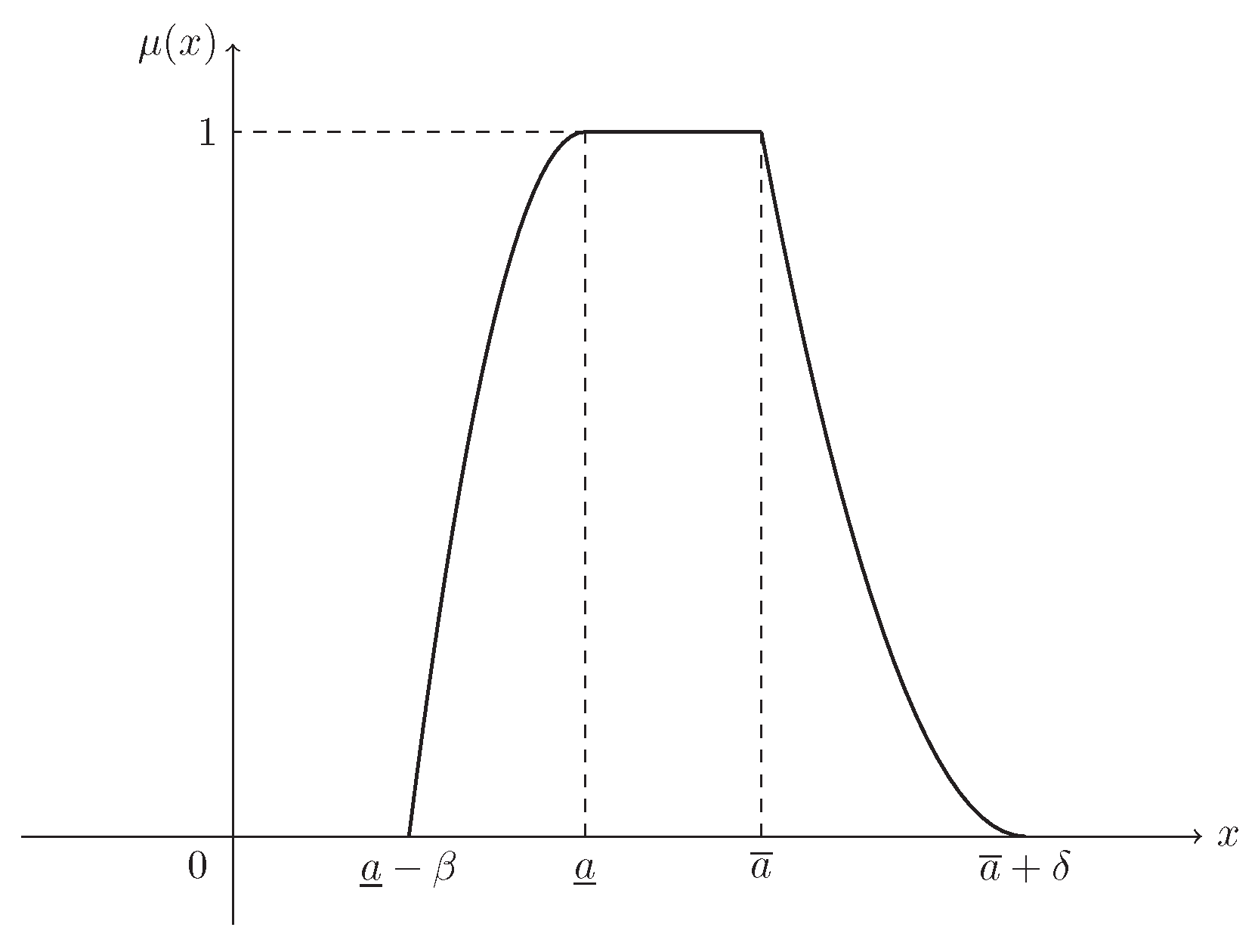
Suppose that and . Then ξ is known as a mixture fuzzy interval, denoted by , and its MF is (see Figure 4)

Figure 4.
The MF in Example 4. is the MF in Equation (5) of mixture fuzzy interval .
Definition 3.
(Liu and Liu [18]) Assuming that ξ is a fuzzy variable with MF, μ, and B is a set, the credibility of fuzzy event is defined by
Definition 4.
(Liu [38]) The credibility distribution (CD) of a fuzzy variable ξ is defined as
As for an LR fuzzy interval with MF, , in Equation (1), on account of Equations (6) and (7), its CD can be derived as
In view of the continuity and monotonicity of CDs of LR fuzzy intervals, Zhou et al. [35] defined a special type of LR fuzzy interval, which is called the regular LR fuzzy interval.
Definition 5.
(Zhou et al. [35]) An LR fuzzy interval ξ is said to be regular if its CD, , is continuous on and strictly increasing on .
Definition 6.
(Zhou et al. [35]) Suppose that is a regular LR fuzzy interval. Then its inverse credibility distribution (ICD) is defined as
Please note that the ICD, , is well defined on the domain . If required, the open interval can be extended by
Based on Definition 5, it is clear that the four kinds of LR fuzzy intervals given in Examples 1–4 are all regular LR fuzzy intervals. Thus, in the light of Equations (8) and (9), Examples 5–8 derive their CDs and ICDs, respectively, for our purpose.
Example 5.
Example 6.
Example 7.
Example 8.
Definition 7.
(Liu [38]) A strictly monotone function is established when it is strictly increasing in regard to and strictly decreasing in regard to , that is,
whenever for and for , and
whenever for and for .
Theorem 1.
(Zhou et al. [35]) Let be independent regular LR fuzzy intervals with CDs, , respectively. If the continuous function is strictly increasing in regard to and strictly decreasing in regard to , then is a regular LR fuzzy interval with ICD,
3. Calculation Formulas for Entropy of Monotone Function
This section first presents the definition of entropy of continuous fuzzy variable proposed by Li and Liu [19]. Then, an equivalent formula for entropy of LR fuzzy interval is derived in terms of the ICD. Ultimately, the calculation formula for entropy of monotone function of LR fuzzy intervals is presented, and the linearity of entropy operator is also verified.
3.1. Definition and Calculation Formula for
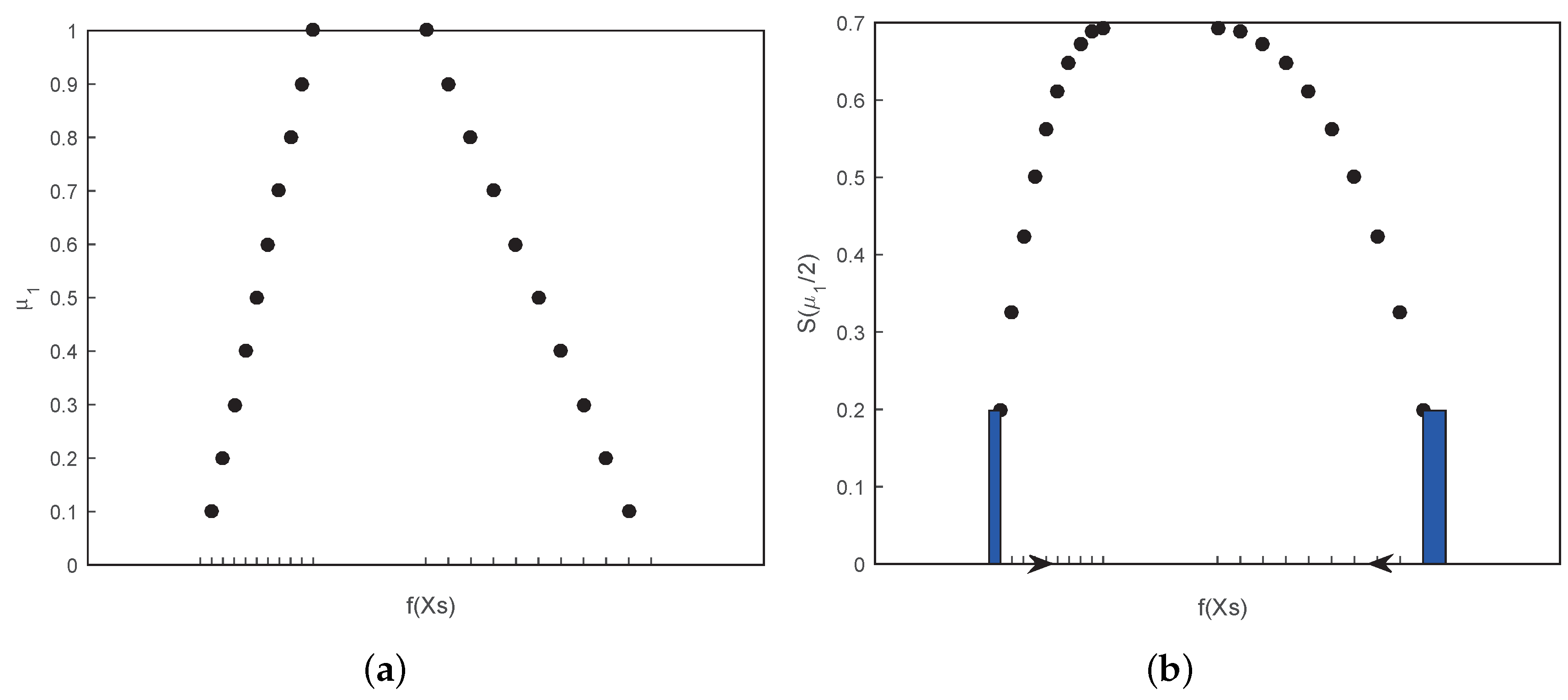
Definition 8.
(Li and Liu [19]) Suppose that ξ is a continuous fuzzy variable. Then the entropy of ξ is defined as
where .
Hence, the entropy of is
By using the calculation formula in Equation (22), the entropy of the four kinds of LR fuzzy intervals mentioned above is derived and presented in Examples 9–12.
Example 9.
Suppose that ξ is a trapezoidal fuzzy number in Example 1. Then its entropy can be calculated as
Assuming that , which signifies that ξ is a triangular fuzzy number, its entropy is .
Example 10.
Suppose that ξ is a parabolic fuzzy interval in Example 2. Then its entropy can be calculated as
Assuming that , which signifies that ξ is a parabolic fuzzy number, its entropy is .
Example 11.
Suppose that ξ is a normal fuzzy interval in Example 3. Then its entropy can be calculated as
Assuming that , which signifies that ξ is a normal fuzzy number, its entropy is .
Example 12.
Suppose that ξ is a mixture fuzzy interval in Example 4. Then its entropy can be calculated as
Assuming that , which signifies that ξ is a mixture fuzzy number, its entropy is .
Theorem 2.
Provided that ξ is a regular LR fuzzy interval, if its entropy exists, then
where is the ICD of ξ. □
Proof of Theorem 2.
Suppose that is an LR fuzzy interval represented by with the CD, . According to Equations (8) and (21), we can obtain
In light of Definition 8 and the equation , the entropy can be easily calculated as
Thus, we have
where is the derivative of with By the Fubini theorem, it immediately follows that
Remark 2.
It should be noted that Zhou et al. [23] have verified that the calculation formulas in Equation (27) is also effective for LR fuzzy numbers. That is, the formulas derived in Theorem 2 with respect to LR fuzzy intervals is a generalized one involving Zhou et al. [23]’s result as a special case.
3.2. Calculation Formula for
According to Definition 8, it is clear that the calculation of entropy in credibility theory is complicated due to the definition itself. Hence, it is more difficult to deal with the entropy of function, that is,
which results in the limitations of the current research.
Referring to the existing literature about the entropy of function , in terms of continuous fuzzy variable , Li and Liu [19] has proved that , where is a linear function of the single fuzzy variable . Regarding the function of fuzzy variables, , where f is an n-dimensional function, almost all the current work focuses on portfolio selection problems to process the linear function of fuzzy variables. In addition, the fuzzy variables involved are either triangular fuzzy numbers or trapezoidal fuzzy numbers (see, e.g., [24,27]).
Take the trapezoidal fuzzy numbers as an example to illustrate their work. Assume that , and , . According to the arithmetic operation linearity of trapezoidal fuzzy numbers, it is easy to derive that
Then in accordance with Equation (23), the entropy of function in portfolio can be obtained as
To break the deadlock and apply fuzzy entropy to more range of areas besides portfolios, according to Theorems 1 and 2, we put forward a new calculation formula for entropy of function that can be universally applied.
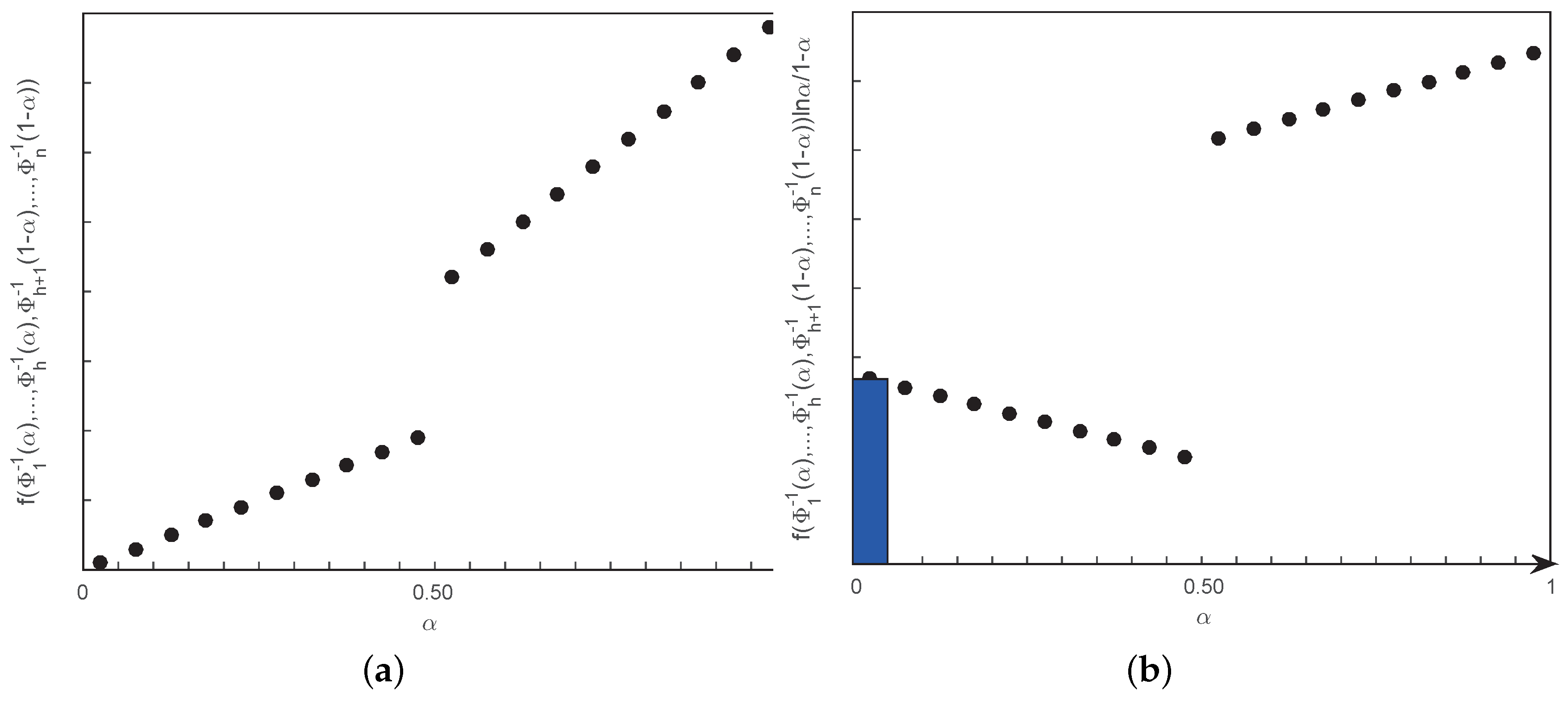
Theorem 3.
Let be independent regular LR fuzzy intervals with CDs, , respectively. If the continuous function is strictly increasing in regard to and strictly decreasing in regard to , then the entropy of is
Proof of Theorem 3.
It follows immediately from Theorems 1 and 2. □
Through this calculation formula for entropy of function, the crisp integration can be obtained by substituting the ICDs of LR fuzzy intervals (i.e., , see Equation (9) in Definition 6) into Equation (34), which avoids the difficulty of calculating the entropy of function via the credibility measure and the function S in Equation (33). In consequence, in addition to the entropy of linear function, Equation (34) can be also used to directly figure out some slightly more complex conditions, such as entropy of some simple nonlinear functions of different types of fuzzy variables.
3.3. Linearity Property of Entropy Operator
In the following, we further verify the linearity of entropy operator with respect to regular fuzzy intervals based on Theorem 3.
Theorem 4.
Let be independent regular LR fuzzy intervals. If their entropies exist, then for any real numbers , we have
Proof of Theorem 4.
Without loss of generality, we only demonstrate the case . Suppose that and are two real numbers, and and are two independent regular LR fuzzy intervals with ICDs, and , respectively. If and , it follows from Theorem 3 that
Similarly, if and , we have
It is easy to derive that the equality also holds for the other two cases (i.e., 0 and 0; 0 and 0). □
Example 14.
Let and . In view of Theorem 4 and Examples 9 and 10, the entropy of can be derived as
which is consistent with the result of Example 13.
4. Simulation Algorithms for Entropy of Monotone Function
The calculation formula proposed in the above section can be used to directly calculate the entropy of linear function or simple nonlinear function. However, when the function becomes comparatively complicated or the quantity of fuzzy variables contained in the function increases, it becomes difficult to directly derive the entropy of function via the formula. In this case, designing effective simulation algorithms is a general and better choice instead of computing straightforwardly. This section first introduces two existing simulation algorithms by the stochastic discretization process, and then separately proposes two new simulation algorithms through the methods of uniform discretization and numerical integration, respectively.
4.1. FSE
By using the stochastic discretization simulation method introduced in [32], Huang [33] proposed the FSE through randomly generating the MF and CF in the light of the extension principle of Zadeh.
FSE in [33] is employed to approximate the fuzzy entropy , where f is a real-valued function, and are independent fuzzy variables. Let be respectively generated from the -level sets of , where K is a sufficiently large integer, and is a sufficiently small positive number. Denote and for . Thus, the credibility function can be approximately formulated as
which can be simplified as
Subsequently, by approximating the integration based on the sample points generated above, the detailed fuzzy simulation procedure of FSE is designed and described in Algorithm 1 below. Please note that in this simulation algorithm, there are two approximation processes which may produce errors, including randomly generating the discrete MF and randomly simulating the integration.
| Algorithm 1 Fuzzy Simulation for Entropy, FSE, Huang [33] | |
| Step 1. | Initialize the numbers of sample points K and integration points N, and a sufficiently small positive number . Set and . |
| Step 2. | Randomly generate real numbers such that , respectively. |
| Step 3. | Set , and . |
| Step 4. | Randomly generate r from . |
| Step 5. | Calculate , where is estimated via Equation (42). |
| Step 6. | Set . If , let and go to Step 4. |
| Step 7. | Return as the estimated value of . |
Li [21] also developed an algorithm FSE* to simulate the entropy of function, , in which the process of randomly generating sample points of continuous fuzzy numbers was the same as FSE. The essential difference between the two algorithms was the calculation of the joint credibility function . In FSE, the credibility function is estimated via Equation (42), whereas in FSE*, it is assumed to be predetermined by the decision-maker, which is impractical and difficult to perform.
4.2. UDA
Since FSE and FSE* both stemmed from the stochastic discretization process in [32], which has been verified by Miao et al. [34] to bring potential significant errors in most cases. To provide a superior approximate value of , this section innovatively proposes a novel simulation method by performing the sampling experiments uniformly and then acquiring the fairly accurate membership degrees on account of the following theorem.
Theorem 5.
(Miao et al. [34]) Let be independent regular LR fuzzy intervals. If the continuous function is strictly increasing in regard to and strictly decreasing in regard to , then the MF of the fuzzy interval is
where is the MF of ,
and is the α-level of , .
Theorem 5 tells us that the exact membership degree of any point in the two sets or can be achieved by means of that of the first fuzzy variable, , which motivates us to discretize the continuous fuzzy interval by generate sample points uniformly from or , instead of the stochastic discretization process used in FSE and FSE*.
Suppose that is a continuous function which is strictly increasing in regard to and strictly decreasing in regard to , and are regular LR fuzzy intervals, . Then separately divide the two close intervals and into k equal pieces, and denote the s-th point of as and the (k-s)-th point of as , that is,
For convenience, denote
Thus, based on Theorem 5, for any , the credibility function of , , can be well approximated by the following formula
Subsequently, according to Equations (33) and (47), through the discretization method mentioned above, the UDA is designed in Algorithm 2 as follows. Figure 9a,b explain the simulation process of UDA with the trapezoidal fuzzy numbers when k is set to 10.
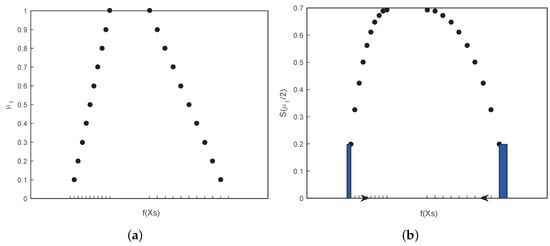
Figure 9.
(a) Discretization process of UDA. The horizontal axis represents the function of fuzzy variables, and the left and right sides of this set variable are respectively cut into uniform parts. The vertical axis represents the membership of the first fuzzy variable. (b) Calculation process of UDA. The small area with color is the simulation value, the bottom is the spacing of the adjacent set function and the height is the integrand function, adding from the two sides to the middle.
| Algorithm 2 Uniform Discretization Algorithm, UDA | |
| Step 1. | Initialize the number of sample points K. Set , , and . |
| Step 2. | Set and calculate , where , . |
| Step 3. | If , go to Step 2. Otherwise, set and go to Step 4. |
| Step 4. | Set and calculate , where , . |
| Step 5. | If , go to Step 4. Otherwise, go to Step 6. |
| Step 6. | Calculate , where . |
| Step 7. | Return H as the estimated value of . |
Although both FSE and UDA estimate the entropy of function by using the discretization process and the calculation formula in Equation (33), there are two underlying differences between them. One is the sampling method for discretization of continuous fuzzy intervals. FSE generates sample points randomly with a less accurate MF, while UDA generates sample points uniformly, outputting a pretty accurate MF. The other is the integration simulation process, the performance of which will be demonstrated in the next section.
4.3. NIA
As proved above, the entropy of function of regular LR fuzzy intervals can be calculated via an integration involving its ICD in integrand (see Theorem 3). Based on this calculation formula (i.e., Equation (27)), a NIA is suggested to simulate the entropy of monotone function efficiently.
Suppose that is strictly increasing in regard to and strictly decreasing in regard to , and are regular LR fuzzy intervals with ICDs, , respectively. Then in view of Theorem 3, the entropy can be simulated as the numerical integration of function . To further reduce the deviation, the median values of two sample points are used to simulate the above integrand. More concretely, divide the close interval into K equal pieces, and integrate the above function for , . Taking the trapezoidal fuzzy numbers as an example, Figure 10a,b explain the simulation process of NIA when K is set to 20. The detailed procedure is described in Algorithm 3 as follows.
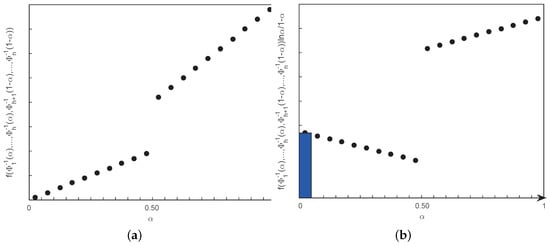
Figure 10.
(a) Discretization process of NIA. The abscissa of the discrete points is the midpoint of the adjacent sample points, and the ordinate is the value of corresponding to the midpoint. (b) Calculation process of NIA. The small area with color is the simulation value, the bottom is the spacing of the adjacent sample points and the height is the integrand function, adding from 0 to 1.
| Algorithm 3 Numerical Integration Algorithm, NIA | |
| Step 1. | Initialize the number of sample points K. Set and . |
| Step 2. | Set . For each , let , and for each , let . |
| Step 3. | Reset and . |
| Step 4. | If , go to Step 2. Otherwise, return H as the estimated value of . |
NIA provides a new method to simulate the entropy of monotone function, which is slightly different from FSE and UDA as it substantially simulates the entropy through the ICD rather than the credibility function. As seen from the process of the algorithms, compared to UDA, the accuracy of the results of NIA is apparently improved since the simulation errors only come from the process of the integral simulation. When K tends to be infinite, the simulation results of NIA will definitely approach the real value of the entropy .
5. Numerical Experiments
In this section, a series of experiments on different types of fuzzy intervals with same parameters shown in Table 3 are conducted in C language and run in the same environment, a windows 10 platform PC with processor speed of 2.50 GHz.

Table 3.
Parameter settings of LR fuzzy intervals used in Examples 15–18. Please note that in each example represents different types of LR fuzzy intervals, but with the same parameters, , for the sake of simplicity on the symbols.
Next, we will give four examples to compare the efficiency of FSE, UDA, and NIA from three perspectives, separately studying the influence of the changes in the number of fuzzy intervals, the types of fuzzy intervals and functions on the algorithm results, and further explore the applicable conditions of the three algorithms. Besides, the parameters involved in the algorithms are fixed, in which the numbers of sample points and integration points are both set to be 10,000. To reasonably compare the results simulated by FSE, UDA, and NIA, the simulation error is measured by , where the exact results in all examples are calculated according to Theorem 3.
Example 15.
This example is used to verify the stability and precision of algorithms when calculating the entropy of a single fuzzy variable, .
Assume that is an LR fuzzy interval with listed in Table 3. Firstly, we run FSE, UDA, and NIA 20 times on the trapezoidal fuzzy number to figure out the estimated entropy , and record their simulation results in Table 4, respectively.

Table 4.
Results and their descriptive statistics by running FSE, UDA, and NIA 20 times in Example 15. The results of UDA and NIA keep unchanged, while those of FSE fluctuate with a small coefficient of variation.
The mean, variance, and coefficient of variation are obtained by descriptive statistics. Here, the coefficient of variation is the ratio of standard deviation to mean, reflecting the dispersion degree of observations. From Table 4, we can get the conclusion that the algorithms of UDA and NIA are extremely stable and constant, since the two algorithms will output a unique result according to their respective principles, and the stability of FSE is acceptable as well with a quite small coefficient of variation 0.002387.
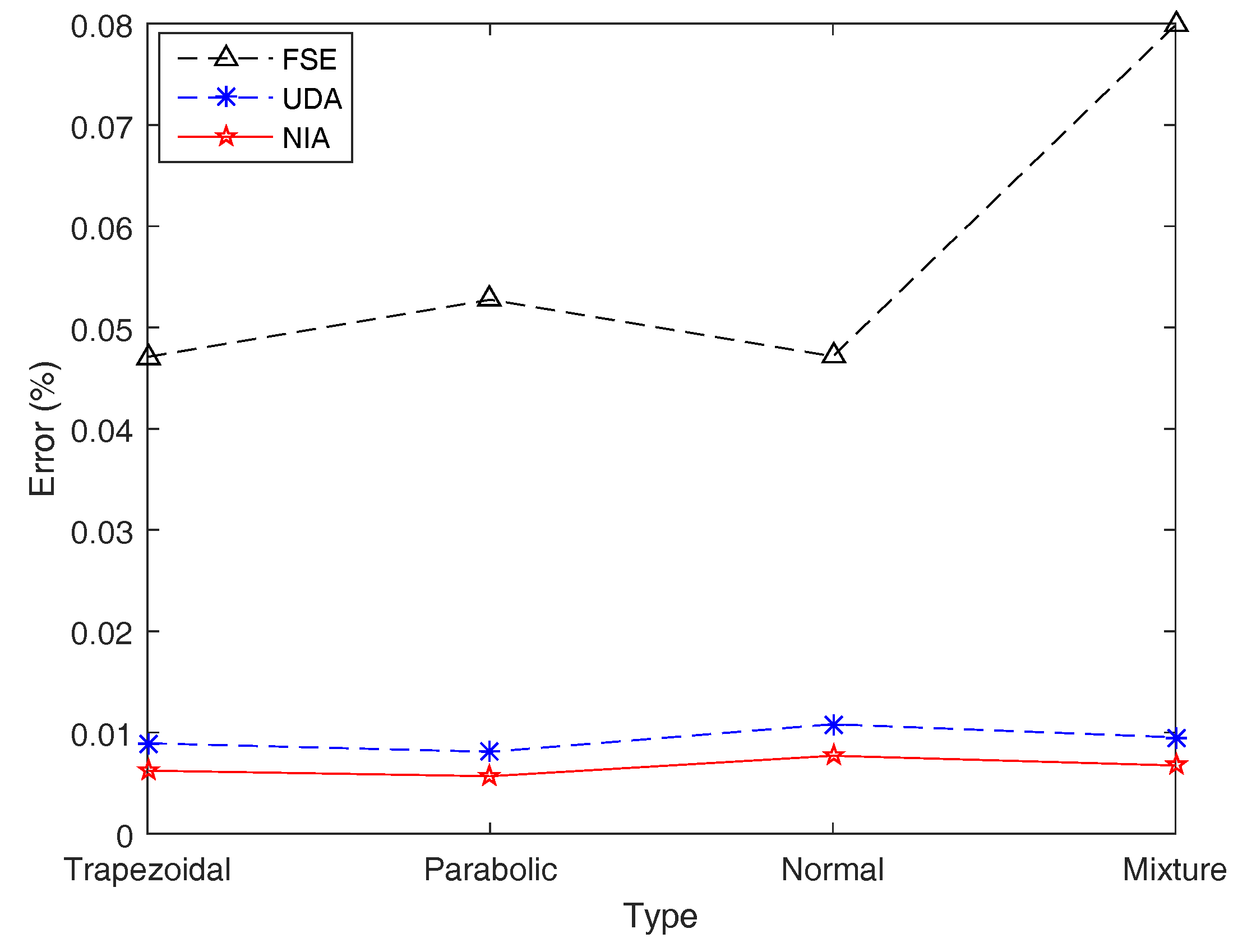
Subsequently, by employing the three simulation algorithms, the simulation and exact results for entropy of on four types of LR fuzzy intervals are obtained and shown in Table 5 and Figure 11, where each simulation result is reported as the average of 20 simulated trials.

Table 5.
Comparative results in Example 15. FSE, UDA, and NIA are respectively run to simulate the entropy of a single fuzzy interval, , and their simulation results, running time and simulation errors are reported.
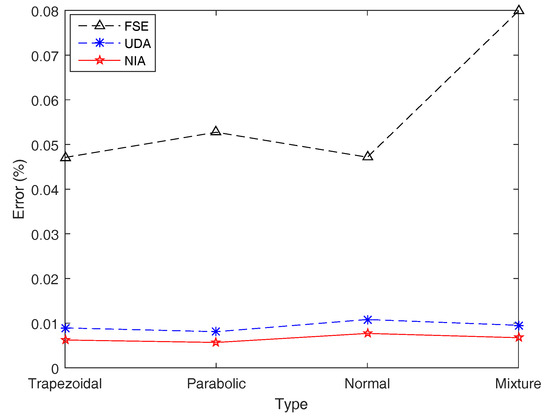
Figure 11.
Simulation errors of FSE, UDA, and NIA in Example 15. Simulation errors of UDA and NIA are close, and those of FSE are acceptable.
Table 5 and Figure 11 show that NIA performs best on simulation results compared with the other two algorithms, while UDA runs fastest for its algorithm principle using the first membership value to represent all, which can be verified by the following examples. For an individual fuzzy interval, although the simulation errors of FSE are several times more than those of the other two algorithms, the precision of FSE is still acceptable with a maximum error 0.079867%. In terms of the speed of operation, the maximum computing time of FSE is 0.6928s, which is far worse than UDA and NIA.
Example 16.
This example is used to verify the stability and precision of algorithms when calculating the entropy of function, , where are LR fuzzy intervals belonging to the same type, .
Let , and be regular LR fuzzy intervals with listed in Table 3. Firstly, analogously, we run FSE, UDA, and NIA 20 times on the trapezoidal fuzzy numbers to estimate the entropy , and then record their simulation results in Table 6, together with some descriptive statistics.

Table 6.
Results and their descriptive statistics by running FSE, UDA, and NIA 20 times in Example 16. The results of UDA and NIA keep unchanged, while those of FSE fluctuate with a small coefficient of variation.
From Table 6, the stability of UDA and NIA keeps perfect, exporting only one result for all trials, but that of FSE becomes weaker obviously when compared to Example 15. To avoid contingency and enhance persuasiveness, in the following experiments, we always run FSE 20 times and then report their average as the final result.
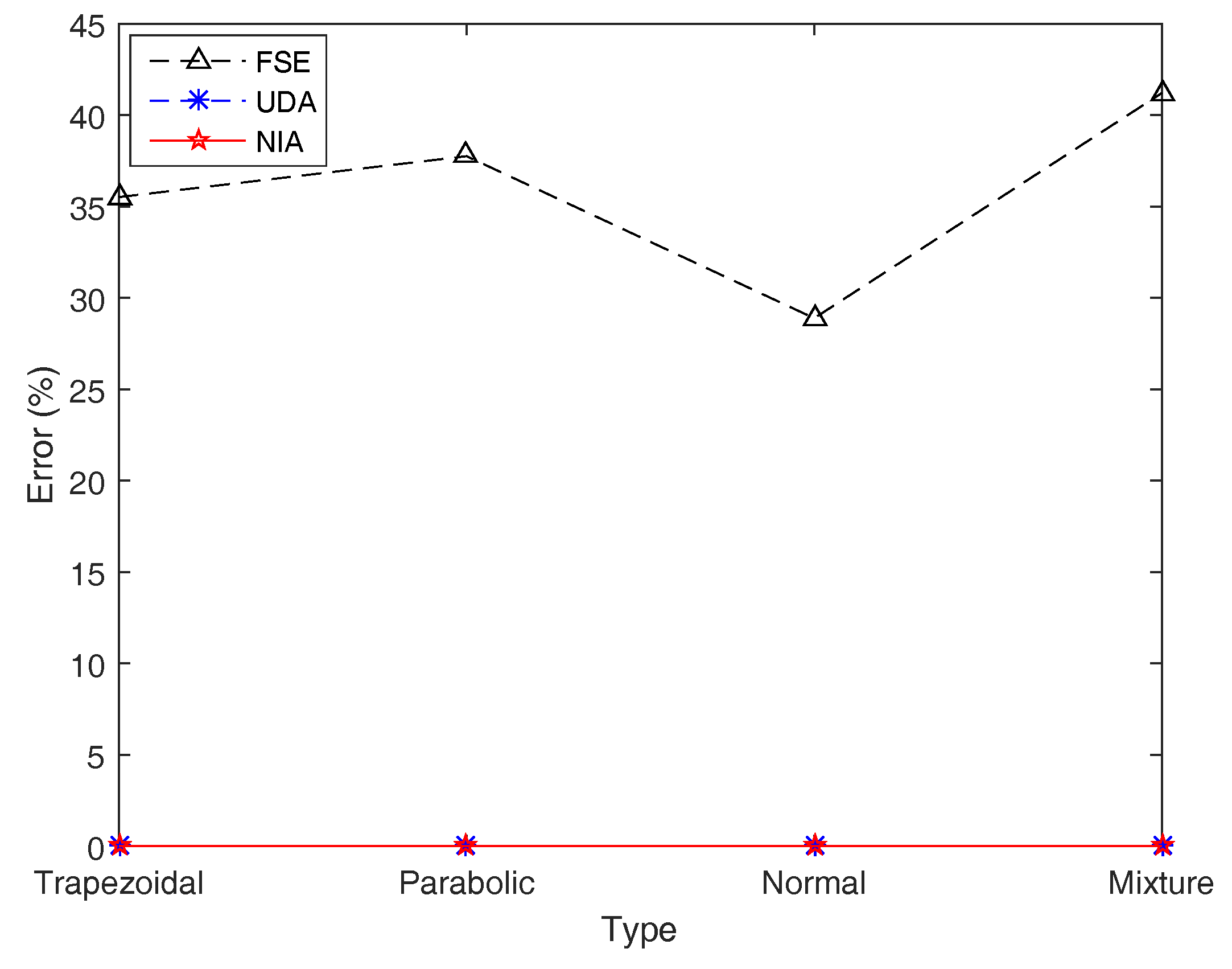
Furthermore, for exploring the accuracy of the three simulation algorithms, the (average) simulation results of the entropy on four types of LR fuzzy intervals by running FSE, UDA, and NIA are presented in Table 7 and Figure 12.

Table 7.
Comparative results in Example 16. FSE, UDA, and NIA are respectively run to simulate the entropy of function, , where are with the same type, and their simulation results, running time and simulation errors are reported.
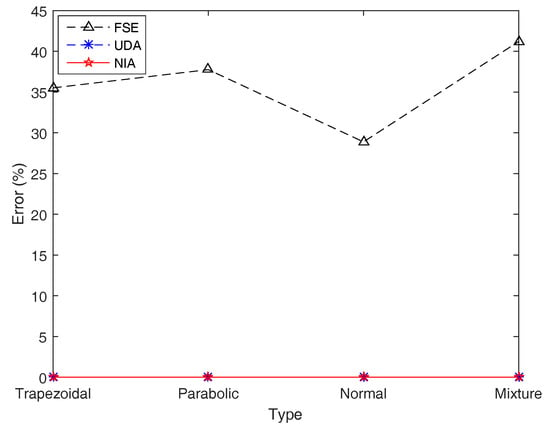
Figure 12.
Simulation errors of FSE, UDA, and NIA in Example 16. Simulation errors of UDA and NIA are close, and those of FSE are poor.
By observing Table 7 and Figure 12, with regard to the addition function f with respect to the same type of LR fuzzy intervals, NIA still performs best at simulation results, followed by UDA, and FSE has the worst performance, with a maximum error of 41.208792%, while the highest errors of UDA and NIA are just 0.009314% and 0.007314%, respectively. In addition, the comparative analysis of the running time demonstrates that UDA is still the most advantageous, followed by NIA, while FSE is far behind, hundreds of times slower.
Example 17.
This example is used to verify the precision of algorithms when calculating the entropy of function, , where are LR fuzzy intervals belonging to different types, .
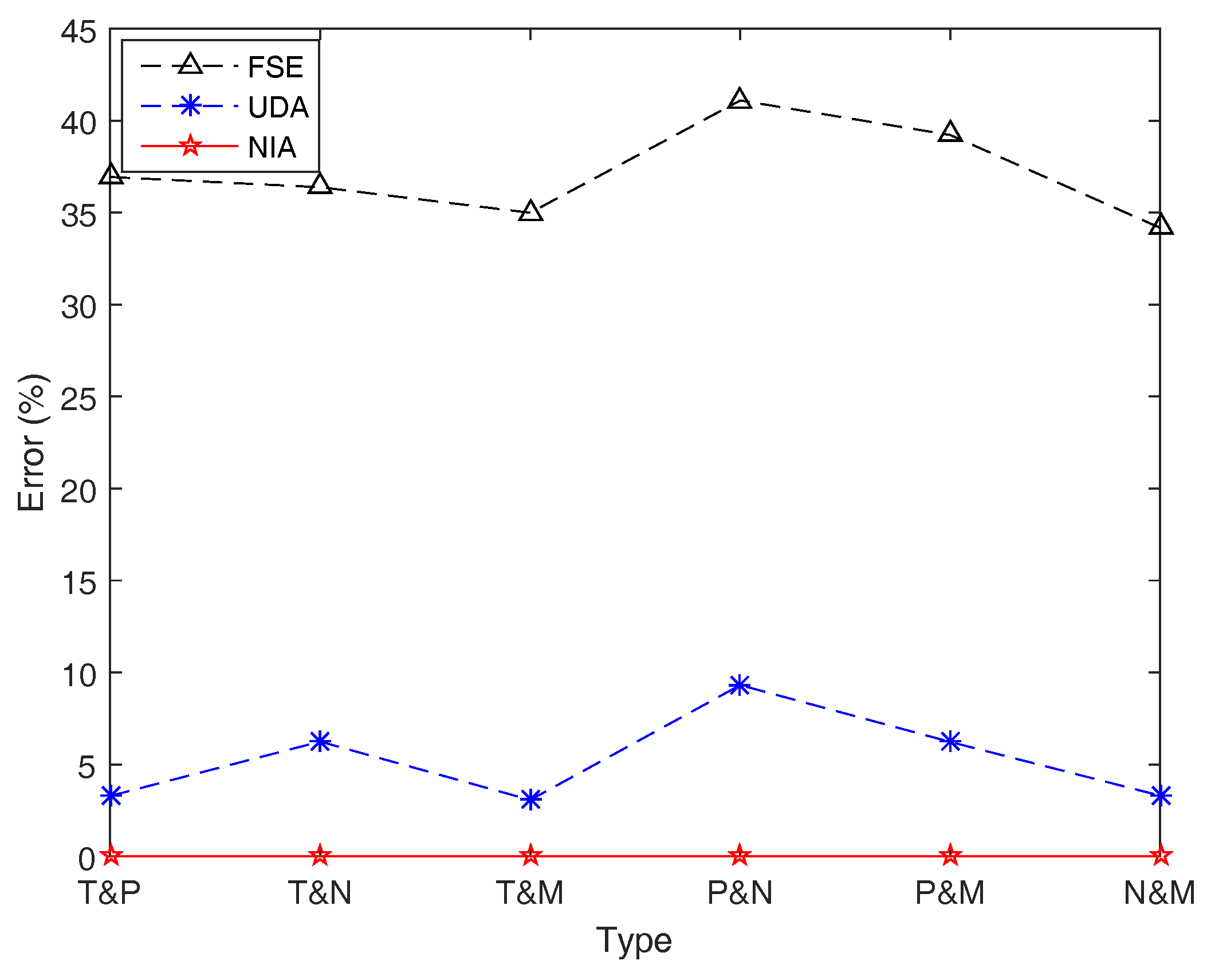
Let , and be regular LR fuzzy intervals with listed in Table 3. To investigate the performance of the three algorithms for calculating the entropy of function involving different types of fuzzy intervals, in this example, we assume that the first five fuzzy intervals, , belong to the same type, and the last five, , are another kind of the same type. For instance, , are all trapezoidal fuzzy numbers, and , are all parabolic fuzzy intervals, which is denoted as “T& P” for simplicity. As for different combinations of different types of LR fuzzy intervals, FSE, UDA, and NIA are run to export the (average) simulation results of the entropy , and the results are shown in Table 8 and Figure 13.

Table 8.
Comparative results in Example 17. FSE, UDA, and NIA are respectively run to simulate the entropy of function, , where are with different types, and their simulation results, running time, and simulation errors are reported.
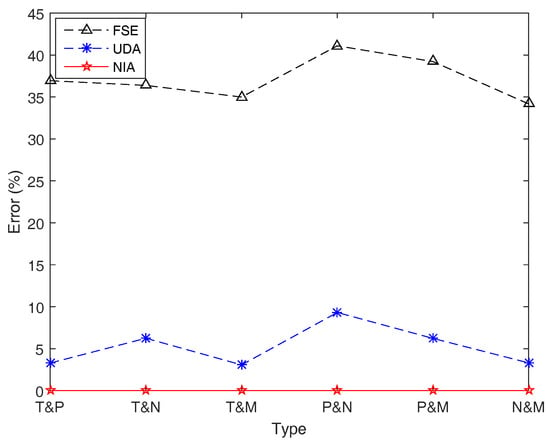
Figure 13.
Simulation errors of FSE, UDA, and NIA in Example 17. Simulation errors of UDA are worse than those of NIA, and those of FSE are quite large up to 41%.
From and Table 8 and Figure 13, we can find that NIA has an overwhelming superiority on accuracy compared with the other two algorithms in this case, while FSE still performs worst with the maximal error 41.098743%. It is worth noting that the accuracy of UDA is reduced when the function f includes different types of fuzzy intervals. In this situation, the method which helps UDA take an absolute advantage in speed, that is, to use the membership of the first fuzzy interval to represent all, may lead to a big error up to 9.312994%. In other words, UDA cannot effectively estimate the entropy of function involving different combinations of different types of fuzzy intervals.
Example 18.
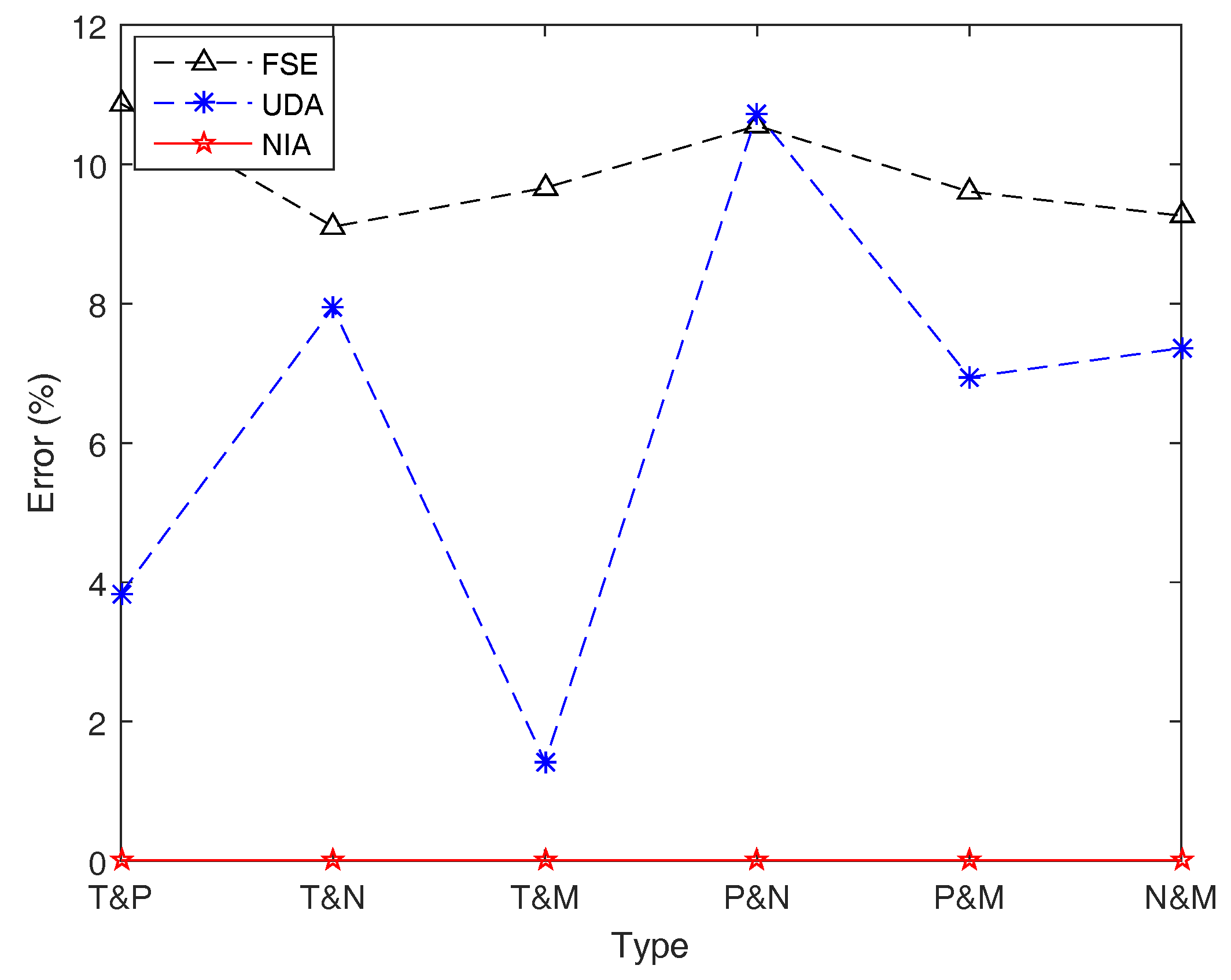
This example is used to further verify the precision of algorithms when calculating the entropy of function, , where belong to different types, , and f is a more complex function compared with Example 17.
Let , and the other conditions are the same as Example 17. The (average) simulation results for entropy with respect to different combinations of different types of LR fuzzy intervals are shown in Table 9 and Figure 14.

Table 9.
Comparative results in Example 18. FSE, UDA, and NIA are respectively run to simulate the entropy of function, , where are with different types, and their simulation results, running time, and simulation errors are reported.
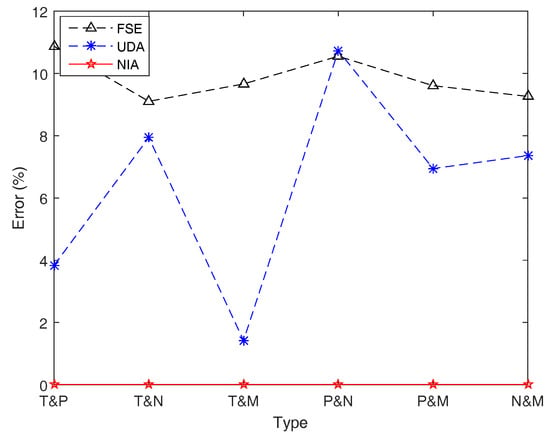
Figure 14.
Simulation errors of FSE, UDA, and NIA in Example 18. Simulation errors of FSE and UDA are obviously greater than those of NIA.
From Table 9 and Figure 14, we can get similar conclusions as the previous example. In terms of accuracy, NIA performs best, while FSE and UDA perform not very well. For NIA, both accuracy and the operation speed are extremely excellent. However, for UDA, although it has an outstanding running speed, it cannot figure out an acceptable estimation result with good precision when different types of fuzzy variables are involved in the function. As for FSE, there is no reason to choose it either in terms of accuracy or speed.
From Examples 15–18, it can be concluded that NIA is the best algorithm when considering the precision and stability, whether it is simulating the entropy of individual fuzzy interval or monotone function. All the estimation errors of the results by running NIA are less than 0.008%, and the maximal running time is less than 0.007s. The speed of UDA is most advantageous, nearly ten times faster than NIA, but its simulation results are rather poor when the estimated function involves different types of fuzzy intervals, and it is only applicable to the simulation of functions regarding the same type of fuzzy intervals. Compared with the proposed two new algorithms for entropy simulation, the existing algorithm FSE is bad in any case, which will report the estimation result with the maximal error of greater than 40%.
6. Conclusions
Motivated by the limitation of the current literature, this paper aims to improve the calculation of entropy of function, , to extend the application scope of fuzzy entropy in the decision-making optimization problems. In our paper, all the fuzzy variables are assumed to be regular LR fuzzy intervals, a type of commonly used fuzzy variables, involving triangular fuzzy numbers and trapezoidal fuzzy numbers as special cases. In addition, the function f is considered to be a strictly monotone function with respect to all the fuzzy variables, and most of the functions involved in real application problems meet this condition. Thus, the simplified calculation formulas as well as the simulation algorithms based on the formulas can provide a valuable reference to entropy optimization from a new perspective, supplementing the existing measures such as mean and variance to extend the applications of LR fuzzy intervals.
Table 10 summarizes most work referred to in this paper, in which the colored methods (i.e., the calculation formula Equation (34), the simulation algorithms UDA and NIA) are contributions of our paper, while Equation (33) and FSE come from literature [19,33], respectively. The relevant research can be mostly divided into two parts from the perspective of processing objects. On the one hand, as for the entropy of linear or simple nonlinear function f, the calculation formulas Equations (33) and (34) can be directly used to obtain the entropy . Compared with Equation (33), our calculation formula Equation (34) replaced the credibility function by the ICD, which greatly simplifies the integrand by removing the function S contained in the original definition (see Definition 8). Correspondingly, Equation (34) can solve all the linear functions and some simple nonlinear functions effortlessly, but Equation (33) can only deal with linear functions , with the constraint that belong to the same type of fuzzy variables, e.g., they are all triangular or trapezoidal fuzzy numbers.

Table 10.
A summary of the methods for calculating the entropy referred to in this paper, including the calculation formulas and the simulation algorithms. The colored methods are contributions of the current paper.
On the other hand, regarding complicated nonlinear function f, using Equation (34) becomes incredibly difficult even with the help of software packages such as MATLAB. Therefore, fuzzy simulation, a widely used technique for obtaining an approximation, is introduced to deal with this issue based on the above calculation formulas and some discretization sampling procedures. The representative simulation algorithm in the current literature, FSE, was proposed by Huang [33], which is based on Equation (33) and the stochastic discretization process presented by Liu [32]. Due to the complexity of Equation (33) and the inaccuracy of Liu [32]’s method, FSE can return satisfactory results stably only when calculating the entropy of an individual fuzzy variable, , with an estimation error of less than 0.08% (see Table 9 in Example 15), whereas for other situations, the performance of FSE is rather poor, possibly reporting results with errors of greater than 40% (see Table 7, Table 8 and Table 9 in Examples 16–18), and simultaneously the running time is hundreds of times more than our algorithms.
The proposed two algorithms in this paper have different mechanisms. Inspired by Theorem 5 presented by Miao et al. [34], the first proposed simulation algorithm, UDA, generates sample points from the possible range of each fuzzy variable uniformly, and then estimates the entropy of function via Equation (33) by using the membership of the first fuzzy variable, , to approximate that of . For this reason, UDA has the absolute advantage in computing speed. The running time of UDA in all the examples is less than 0.0004 s, ten times faster than NIA and hundreds of times than FSE. However, this simplification may also cause potential errors of greater than 10% when the MFs of differ greatly from each other (see Table 8 and Table 9 in Examples 17–18).
The second simulation algorithm designed in this paper, NIA, is based on Equation (34) represented by the ICD. After dividing the close interval into sufficiently small equal pieces, NIA computes the numerical integration of each area via the median values of two sample points. Since the error of NIA just comes from the integration simulation, the performance of NIA is extremely excellent both in accuracy and speed. Even though its operation speed is worse than UDA, the running time is also acceptable. Thus, as concerning the universality of applications, NIA will be recommended preferentially because of its highest accuracy (all errors are less than 0.008%), best stability (always output only one result), and acceptable speed (all computing times are less than 0.007s).
Author Contributions
Formal analysis, J.S.; methodology, J.S.; supervision, J.Z.; validation, J.S.; visualization, J.S.; writing–original draft, J.S.; writing–review & editing, J.Z.; funding acquisition, J.Z.
Funding
This research was funded by the National Natural Science Foundation of China under grant number 71872110.
Acknowledgments
The authors’ sincere appreciation goes to Mingxuan Zhao, who has helped to sort out the theory and check the contents. We also thank the anonymous reviewers for their helpful suggestions, which led to substantial improvements of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| FSE | Fuzzy simulation for entropy |
| UDA | Uniform discretization algorithm |
| NIA | Numerical integration algorithm |
| MF | membership function |
| CD | credibility distribution |
| ICD | inverse credibility distribution |
References
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Philippatos, G.C.; Wilson, C.J. Entropy, market risk, and the selection of efficient portfolios. Appl. Econ. 1972, 4, 209–220. [Google Scholar] [CrossRef]
- Simonelli, M.R. Indeterminacy in portfolio selection. Eur J. Oper. Res. 2005, 163, 170–176. [Google Scholar] [CrossRef]
- Xiao, F.; Qin, B. A weighted combination method for conflicting evidence in multi-sensor data fusion. Sensors 2018, 18, 1487. [Google Scholar] [CrossRef] [PubMed]
- Deng, Y. Deng entropy. Chaos Solitons Fractals 2016, 91, 549–553. [Google Scholar] [CrossRef]
- Guan, L.; Awan, I.U.; Phillips, I.; Grigg, A.; Dargie, W. Performance analysis of a threshold-based discrete-time queue using maximum entropy. Simul. Model. Pract. Theory 2009, 17, 558–568. [Google Scholar] [CrossRef]
- Gustafsson, M.G.; Waman, M.; Bolin, U.W.; Goransson, H.; Fryknas, M.; Andersson, C.R.; Isaksson, A. Improving Bayesian credibility intervals for classifier error rates using maximum entropy empirical priors. Artif. Intell. Med. 2010, 49, 93–104. [Google Scholar] [CrossRef]
- Zhang, X.; Yu, Q.; Yu, H. Physics inspired methods for crowd video surveillance and analysis: A survey. IEEE Access 2018, 6, 66816–66830. [Google Scholar] [CrossRef]
- Khan, M.I.; Qayyum, S.; Hayat, T.; Khan, M.I.; Alsaedi, A. Entropy optimization in flow of Williamson nanofluid in the presence of chemical reaction and Joule heating. Int. J. Heat Mass Transf. 2019, 133, 959–967. [Google Scholar] [CrossRef]
- Wang, Z.; Pang, C.; Ng, T. Data-driven scheduling optimization under uncertainty using Renyi entropy and skewness criterion. Comput. Ind. Eng. 2018, 126, 410–420. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Zadeh, L.A. Probability measures of fuzzy events. J. Math. Anal. Appl. 1968, 23, 421–427. [Google Scholar] [CrossRef]
- Criadoa, F.; Gachechiladzeb, T. Entropy of fuzzy events. Fuzzy Sets Syst. 1997, 88, 99–106. [Google Scholar] [CrossRef]
- Smaldino, P.E. Measures of individual uncertainty for ecological models: Variance and entropy. Ecol. Model. 2013, 254, 50–53. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, W. Multiperiod fuzzy portfolio selection optimization model based on possibility theory. Int. J. Inf. Technol. Decis. Mak. 2018, 17, 941–968. [Google Scholar] [CrossRef]
- Yin, H.; Yu, D.; Yin, S.; Xia, B. Possibility-based robust design optimization for the structural-acoustic system with fuzzy parameters. Mech. Syst. Signal Process. 2018, 102, 329–345. [Google Scholar] [CrossRef]
- Nahmias, S. Fuzzy variables. Fuzzy Sets Syst. 1978, 1, 97–110. [Google Scholar] [CrossRef]
- Liu, B.; Liu, Y. Expected value of fuzzy variable and fuzzy expected value models. IEEE Trans. Fuzzy Syst. 2002, 10, 445–450. [Google Scholar]
- Li, P.; Liu, B. Entropy of credibility distributions for fuzzy variables. IEEE Trans. Fuzzy Syst. 2008, 16, 123–129. [Google Scholar]
- Gao, X.; You, C. Maximum entropy membership functions for discrete fuzzy variables. Inf. Sci. 2009, 179, 2353–2361. [Google Scholar] [CrossRef]
- Li, X. Credibilistic Programming; Springer: Heidelberg, Germany, 2013. [Google Scholar]
- Rahimi, M.; Kumar, P.; Yari, G. Credibility measure for intuitionistic fuzzy variables. Mathematics 2018, 6, 50. [Google Scholar] [CrossRef]
- Zhou, J.; Huang, C.; Zhao, M.; Li, H. Entropy Optimization of Fuzzy Linear Programming, Technical Report. 2019; unpublished work.
- Huang, X. Mean-entropy models for fuzzy portfolio selection. IEEE Trans. Fuzzy Syst. 2008, 16, 1096–1101. [Google Scholar] [CrossRef]
- Li, X.; Zhang, Y.; Wong, H.S.; Qin, Z. A hybrid intelligent algorithm for portfolio selection problem with fuzzy returns. J. Comput. Appl. Math. 2009, 233, 264–278. [Google Scholar] [CrossRef]
- Jalota, H.; Thakur, M.; Mittal, G. Modelling and constructing membership function for uncertain portfolio parameters: A credibilistic framework. Expert Syst. Appl. 2017, 71, 40–56. [Google Scholar] [CrossRef]
- Zhou, J.; Li, X.; Kar, S.; Zhang, G.; Yu, H. Time consistent fuzzy multi-period rolling portfolio optimization with adaptive risk aversion factor. J. Ambient Intell. Humaniz. Comput. 2017, 8, 651–666. [Google Scholar] [CrossRef]
- Deng, X.; Zhao, J.; Li, Z. Sensitivity analysis of the fuzzy mean-entropy portfolio model with transaction costs based on credibility theory. Int. J. Fuzzy Syst. 2018, 20, 209–218. [Google Scholar] [CrossRef]
- Yari, G.; Sajedi, A.; Rahimi, M. Portfolio selection in the credibilistic framework using Renyi entropy and Renyi cross entropy. Int. J. Fuzzy Log. Intell. Syst. 2018, 18, 78–83. [Google Scholar] [CrossRef]
- Bruckley, J.J.; Hayashi, Y. Fuzzy genetic algorithm and applications. Fuzzy Sets Syst. 1994, 61, 129–136. [Google Scholar] [CrossRef]
- Liu, B.; Iwamura, K. Chance constrained programming with fuzzy parameters. Fuzzy Sets Syst. 1998, 94, 227–237. [Google Scholar] [CrossRef]
- Liu, B. Theory and Practice of Uncertain Programming; Physica-Verlag: Heidelberg, Germany, 2002. [Google Scholar]
- Huang, X. A review of credibilistic portfolio selection. Fuzzy Optim. Decis. Mak. 2009, 8, 263–281. [Google Scholar] [CrossRef]
- Miao, Y.; Zhou, J.; De Baets, B. A Novel Fuzzy Simulation Technique on Possibilistic Constraints, Technical Report. 2019; unpublished work.
- Zhou, J.; Han, Y.; Zhao, M. An Extensive Operational Law for Monotone Functions of LR Fuzzy Intervals with Applications to Fuzzy Optimization, Technical Report. 2019; unpublished work.
- Dubois, D.; Prade, H. Operations on fuzzy numbers. Int. J. Syst. Sci. 1978, 9, 613–626. [Google Scholar] [CrossRef]
- Zhou, J.; Yang, F.; Wang, K. Fuzzy arithmetic on LR fuzzy numbers with applications to fuzzy programming. J. Intell. Fuzzy Syst. 2016, 30, 71–87. [Google Scholar] [CrossRef]
- Liu, B. Uncertainty Theory; Springer: Berlin, Germany, 2010. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).