Implementing a Chaotic Cryptosystem by Performing Parallel Computing on Embedded Systems with Multiprocessors
Abstract
1. Introduction
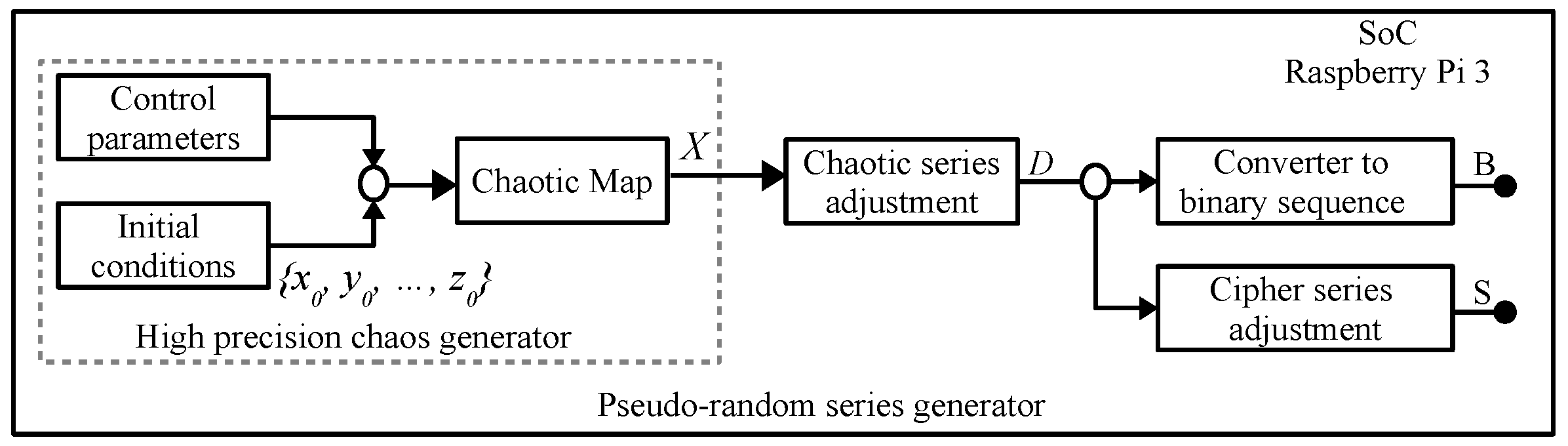
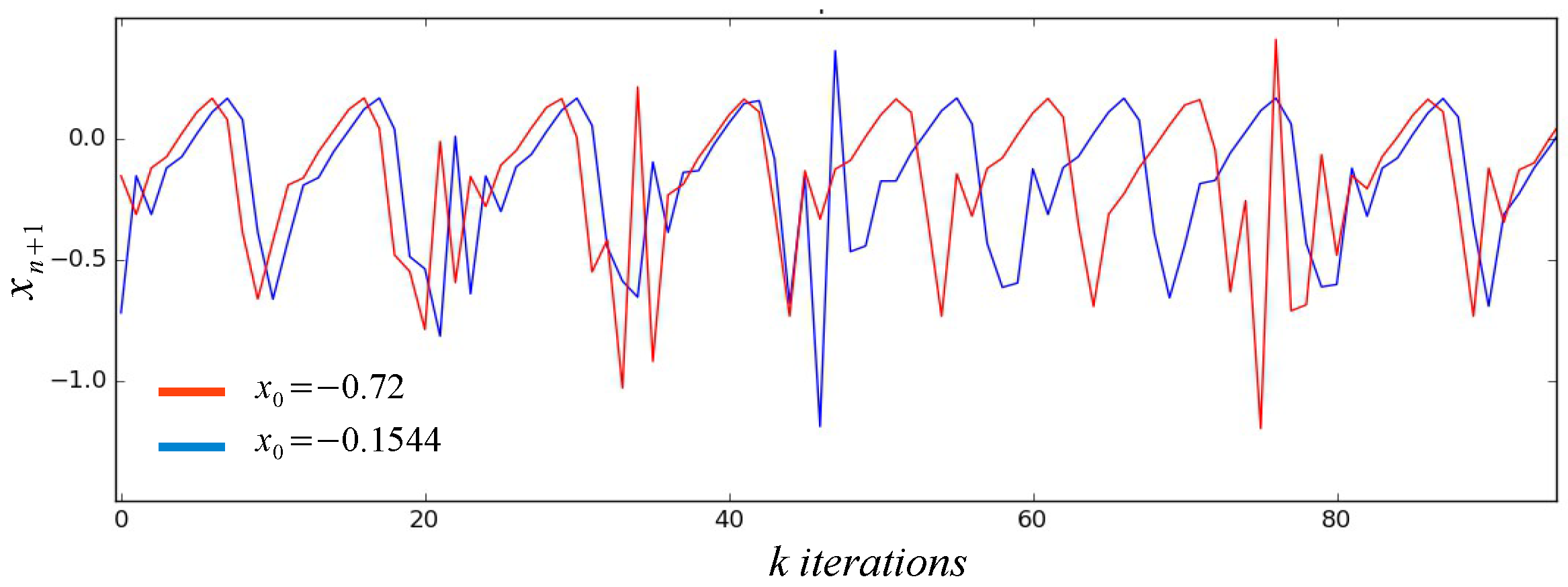
2. Proposed PRNG and Dynamic Keys Generator
- = −0.5044175778616422926572575875229294547046448096553074629030668113991951…
- = −0.3460286548462436652145266889485621403916728515023067284157645131661259…
- = −0.50441757786164229265725758752292945470464480965530
- = −0.34602865484624366521452668894856214039167285150230.
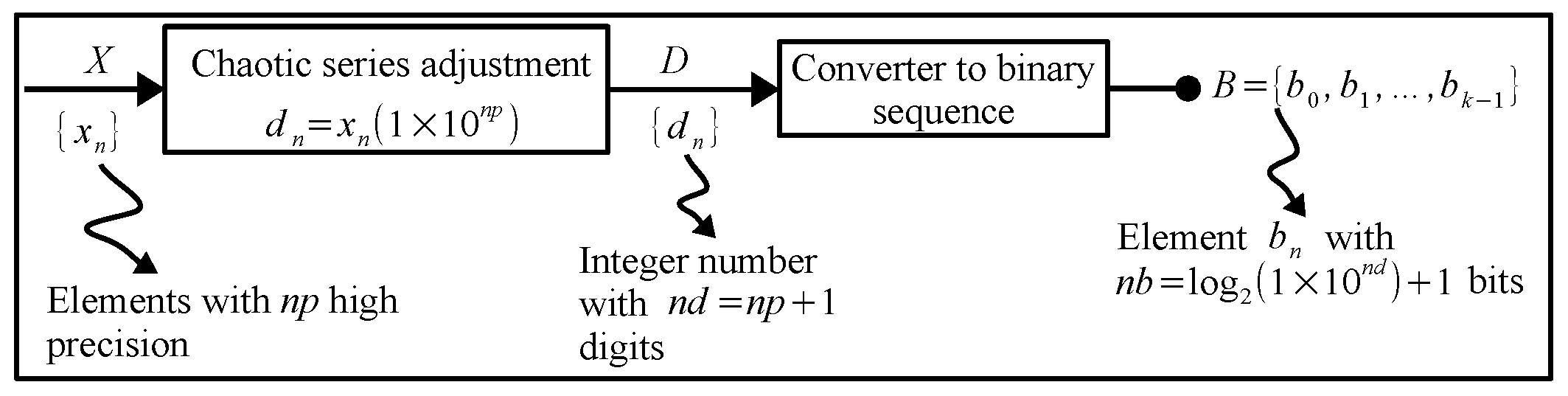
Proposed Pseudo-Random Bit Generator (PRBG)
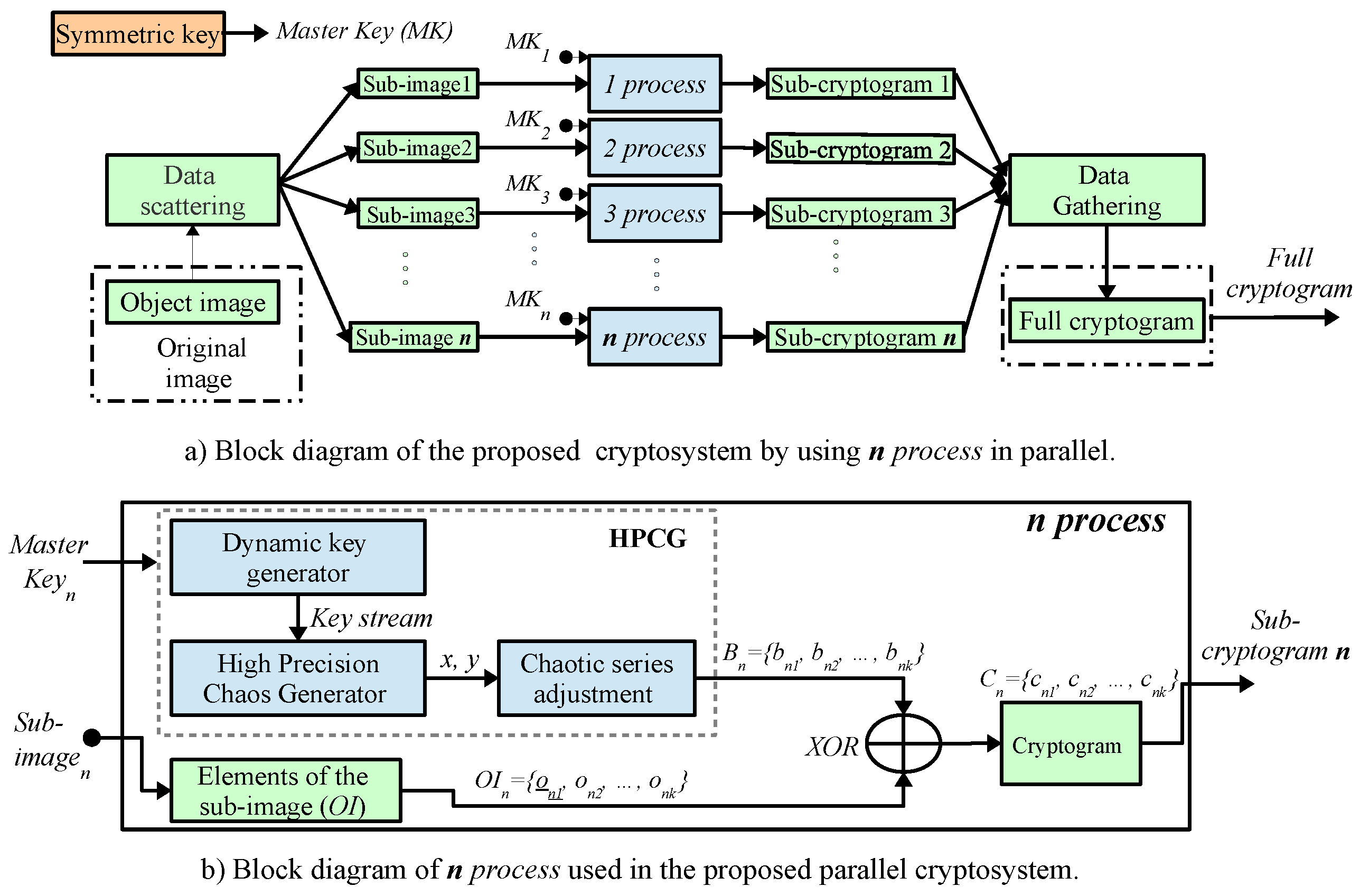
3. Proposed Parallel Encryption Method
3.1. Profiling Algorithms Using Python
Wrote profile results to Encrypter.py.lprof
Timer unit: 3.79968e-07 s
Total time: 862.992 s
File: Encrypter.py
Function: encrypt at line 5
Line # Hits Time Per Hit % Time Line Contents
==============================================================
4 @profile
5 def encrypt():
6 1 146078 146078.0 0.0 foto = Image.open(’land…
7 1 761832 761832.0 0.0 foto = np.array(foto)
8 1 63 63.0 0.0 ren = foto.shape[0]
9 1 7 7.0 0.0 col = foto.shape[1]
10 1 6 6.0 0.0 cap = foto.shape[2]
11 1 8 8.0 0.0 vector=ren*col*cap
12 1 97 97.0 0.0 foto=np.reshape(foto,(v…
13 1 98 98.0 0.0 a= Decimal(’0.9’)
14 1 11 11.0 0.0 b= Decimal(’-0.6013’)
15 1 9 9.0 0.0 c= Decimal(’2.0’)
16 1 9 9.0 0.0 d= Decimal(’0.5’)
17 1 8 8.0 0.0 x0= Decimal(’-0.72’)
18 1 8 8.0 0.0 y0= Decimal(’-0.64’)
19 1 5 5.0 0.0 ret=0
20 1 4 4.0 0.0 npx0=8
21 1 4 4.0 0.0 np_prec=99
22 1 15 15.0 0.0 getcontext().prec=npx0
23 2 12 6.0 0.0 while (ret<1):
24 1 69 69.0 0.0 x1 = Decimal((x0*x0)…
25 1 14 14.0 0.0 y1 = Decimal((2*x0*y…
26 1 5 5.0 0.0 x0=x1
27 1 6 6.0 0.0 y0=y1
28 1 6 6.0 0.0 ret=ret+1
29 1 6 6.0 0.0 getcontext().prec=np_prec
30 1 6 6.0 0.0 j=0
31 16384001 78137141 4.8 3.4 while(j<vector):
32 16384000 439917303 26.9 19.4 x1 = Decimal((x0*…
33 16384000 351247125 21.4 15.5 y1 = Decimal((2*x…
34 16384000 87992069 5.4 3.9 x0=x1
35 16384000 79512478 4.9 3.5 y0=y1
36 16384000 300653689 18.4 13.2 x1=x1*Decimal(10**…
37 16384000 136258513 8.3 6.0 x1=Decimal.to_inte…
38 16384000 91137986 5.6 4.0 if x1<0:
39 10906047 83757897 7.7 3.7 x1=x1*(-1)
40 16384000 185584508 11.3 8.2 s1=int(x1%255)
41 16384000 337097363 20.6 14.8 foto[j]= foto[j]^s1
42 16384000 93981721 5.7 4.1 j=j+1
43 1 77 77.0 0.0 foto=np.reshape(foto,(ren,c…
44 1 456 456.0 0.0 foto=Image.fromarray(foto)
45 1 5036187 5036187.0 0.2 foto.save(’output.png’)
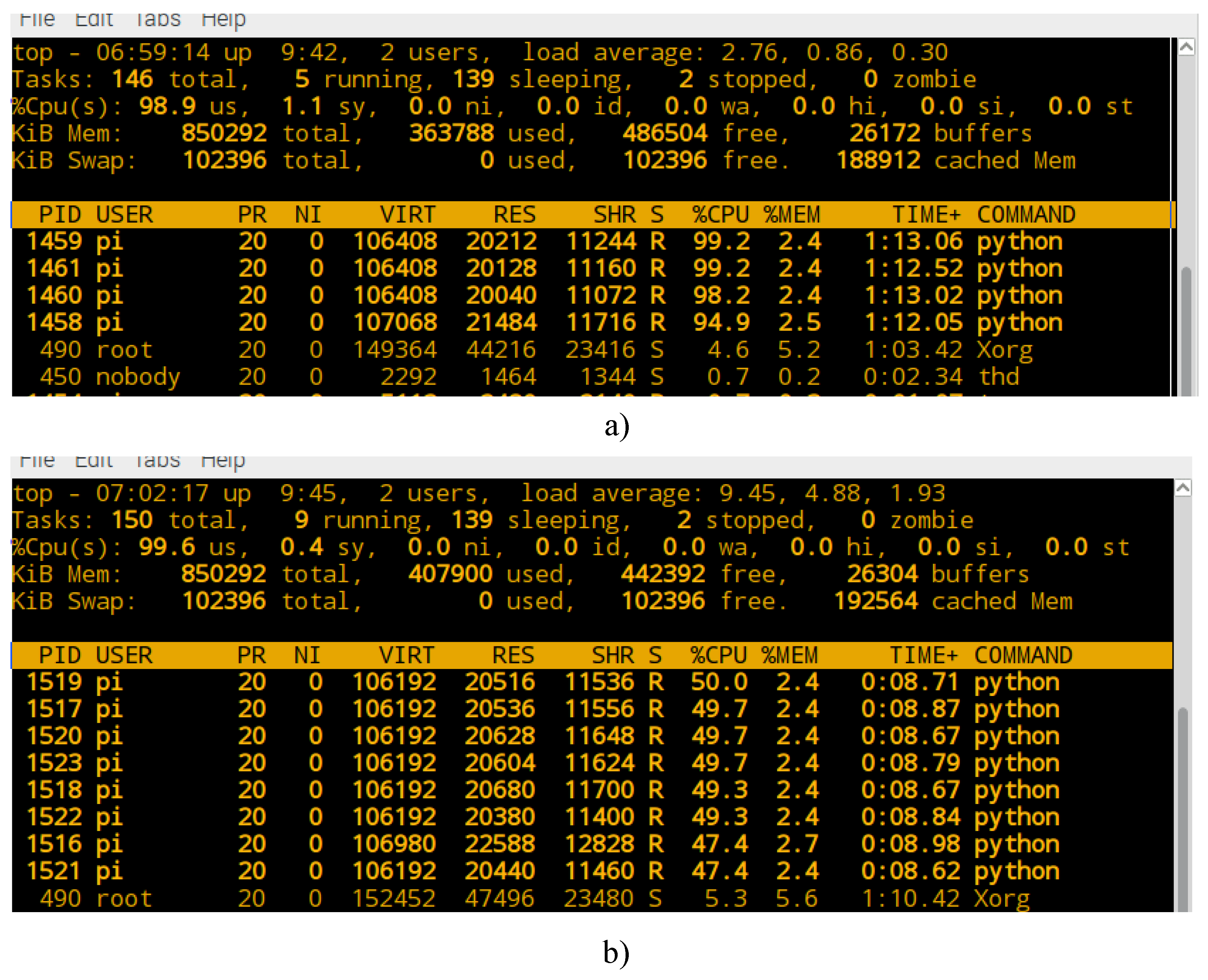
3.2. Parameters of Parallel Processing
3.3. Implementing the MPI Library Using Collective Communication in the Algorithm
| Algorithm 1 First sequential time () |
| 1: from mpi4py import MPI 2: import numpy as np 3: from PIL import Image 4: from decimal import * 5: comm=MPI.COMM_WORLD 6: size=comm.Get_size() # Number of processors 7: rank=comm.Get_rank() # Processor ID 8: if rank == 0: 9: imagen=Image.open(’image.png’) # Read original image 10: imagen=np.array(imagen) # Convert the object image into an array 11: ren=imagen.shape[0] # Size of the array (rows) 12: col=imagen.shape[1] # Size of the array (cols) 13: cap=imagen.shape[2] 14: n_ren=np.int(ren/size) # Resize the array 15: foto=np.reshape(imagen,(size,n_ren,col,cap)) # for scattering data |
| Algorithm 2 Second sequential time () |
| 1: if rank == 0: 2: foto=np.array(newData) 3: foto=np.reshape(foto,(ren,col,cap)) 4: foto=Image.fromarray(foto) 5: foto.save(’output.png’) 6: fin=datetime.now() 7: print(“Done!”) 8: print(end-brgin) 9: if __name__ == ’__main__’: 10: encrypt() |
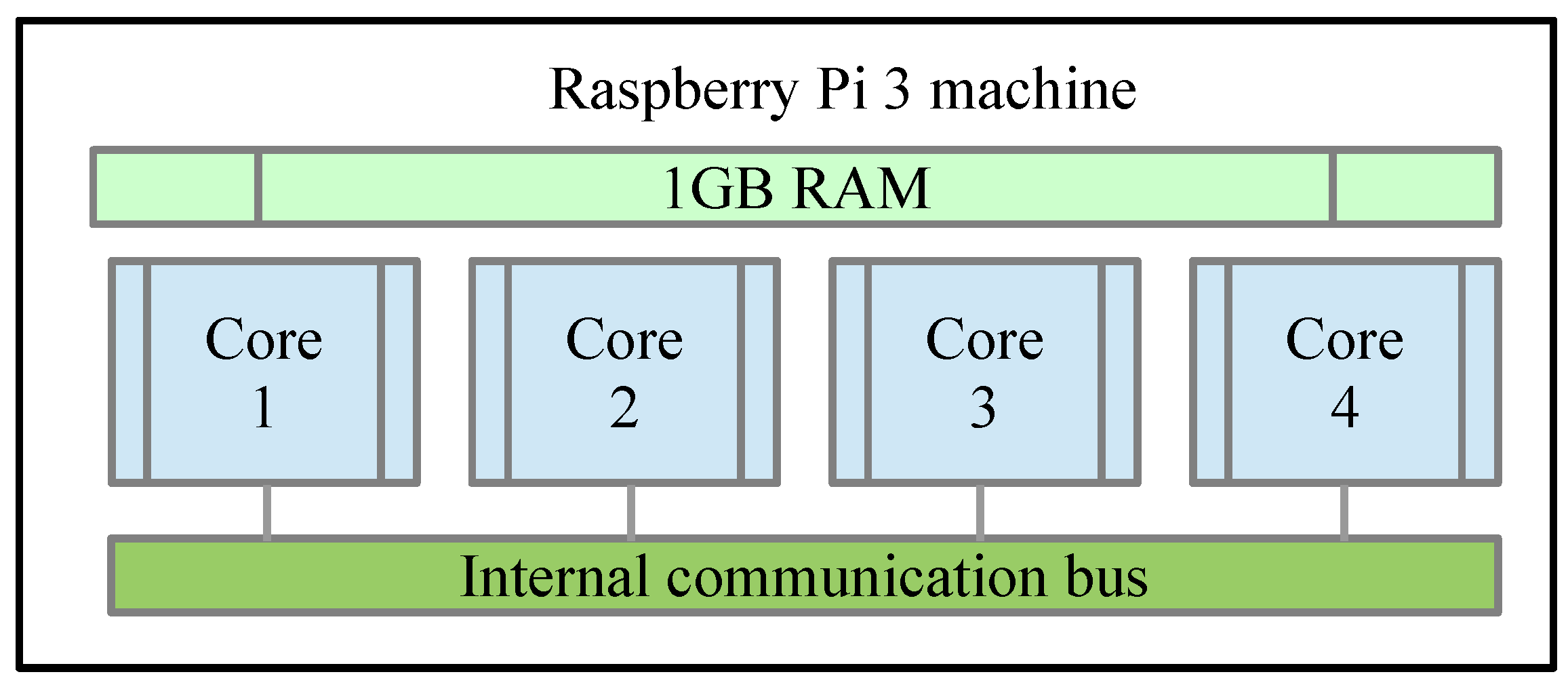
3.4. Implementing a Machine Based on Raspberry Pi 3
3.5. Implementing a Machine Based on a Cluster of Six Embedded Systems (FIAD Cluster)
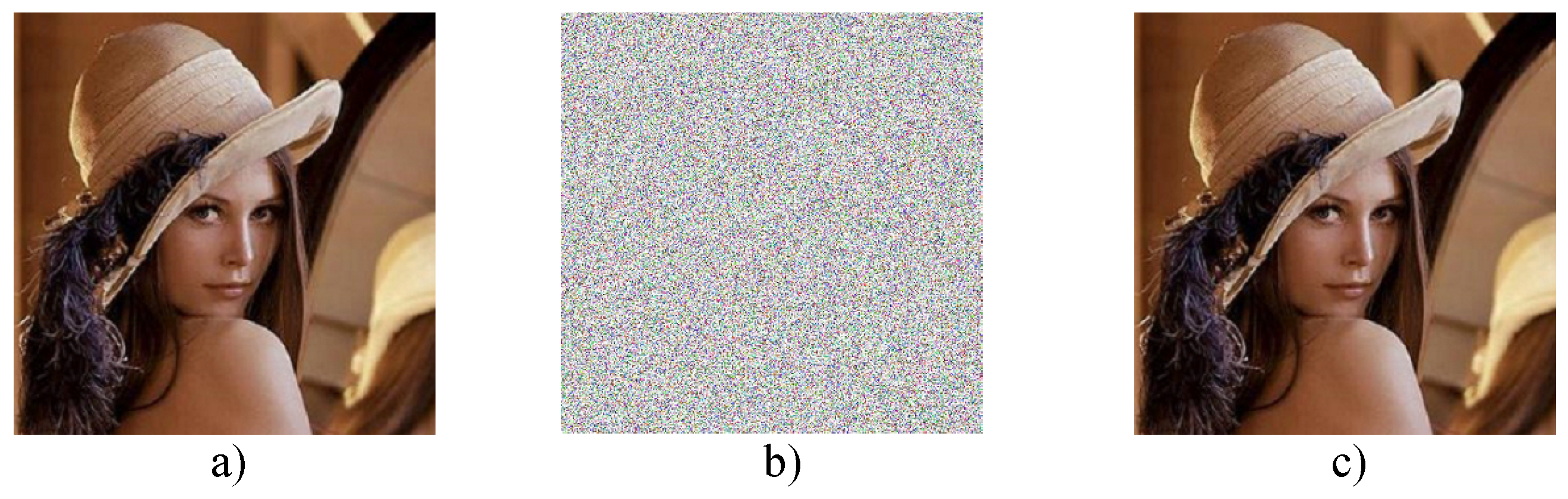
4. Experimental Results
4.1. Security Analysis
4.1.1. The NIST Statistical Test
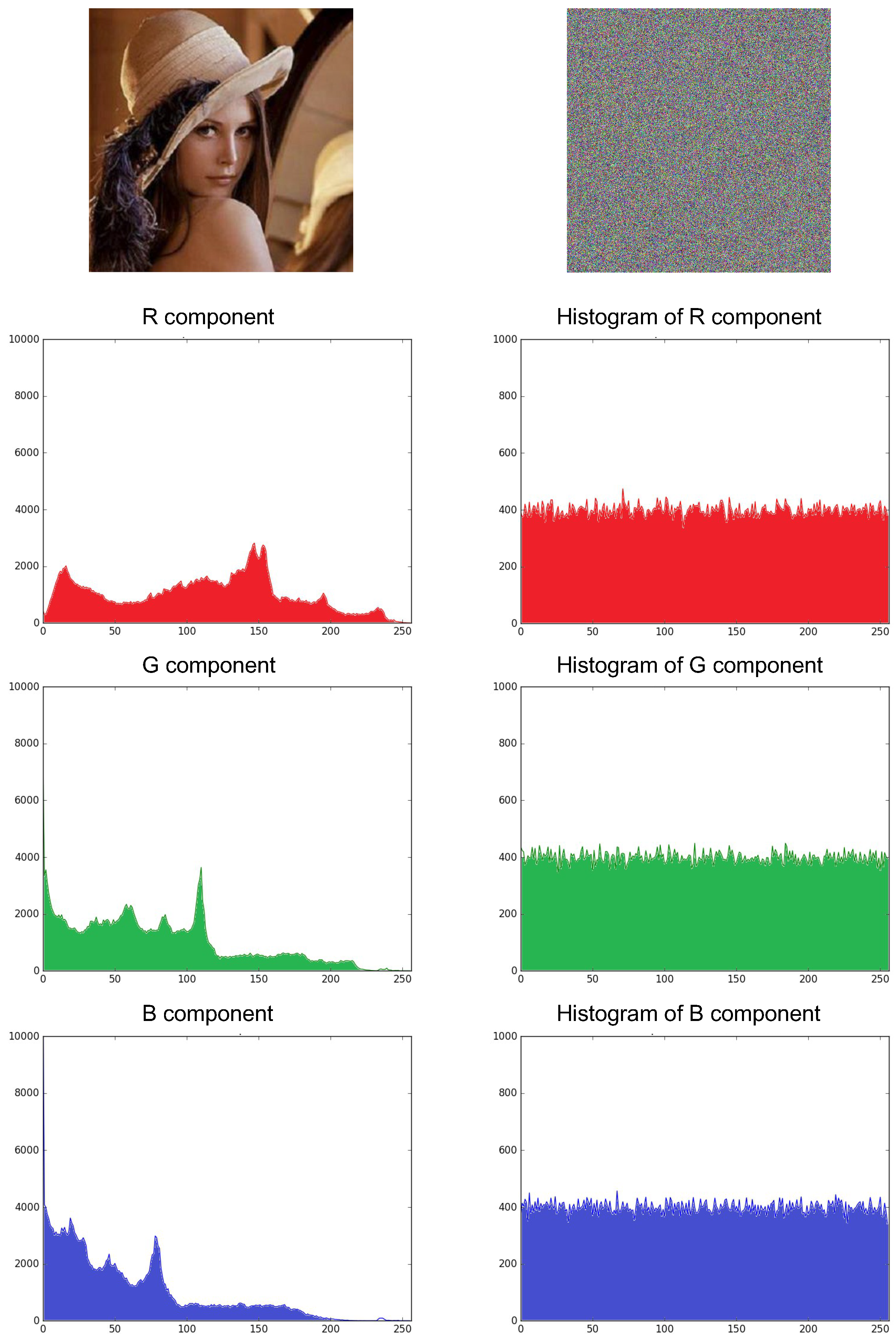
4.1.2. Histogram Analysis
4.1.3. Entropy
4.1.4. NPCR and UACI Differential Attacks
4.2. Key Space
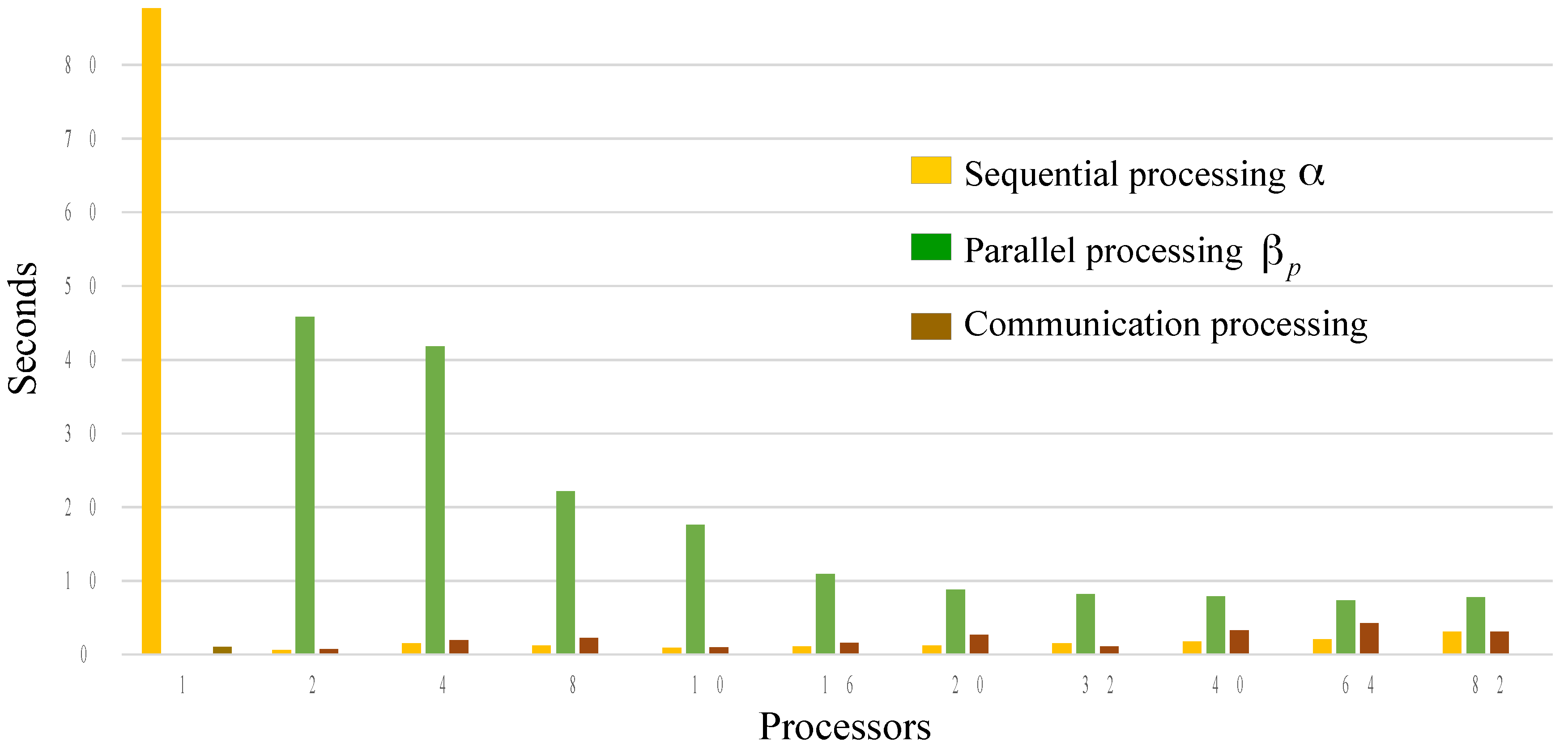
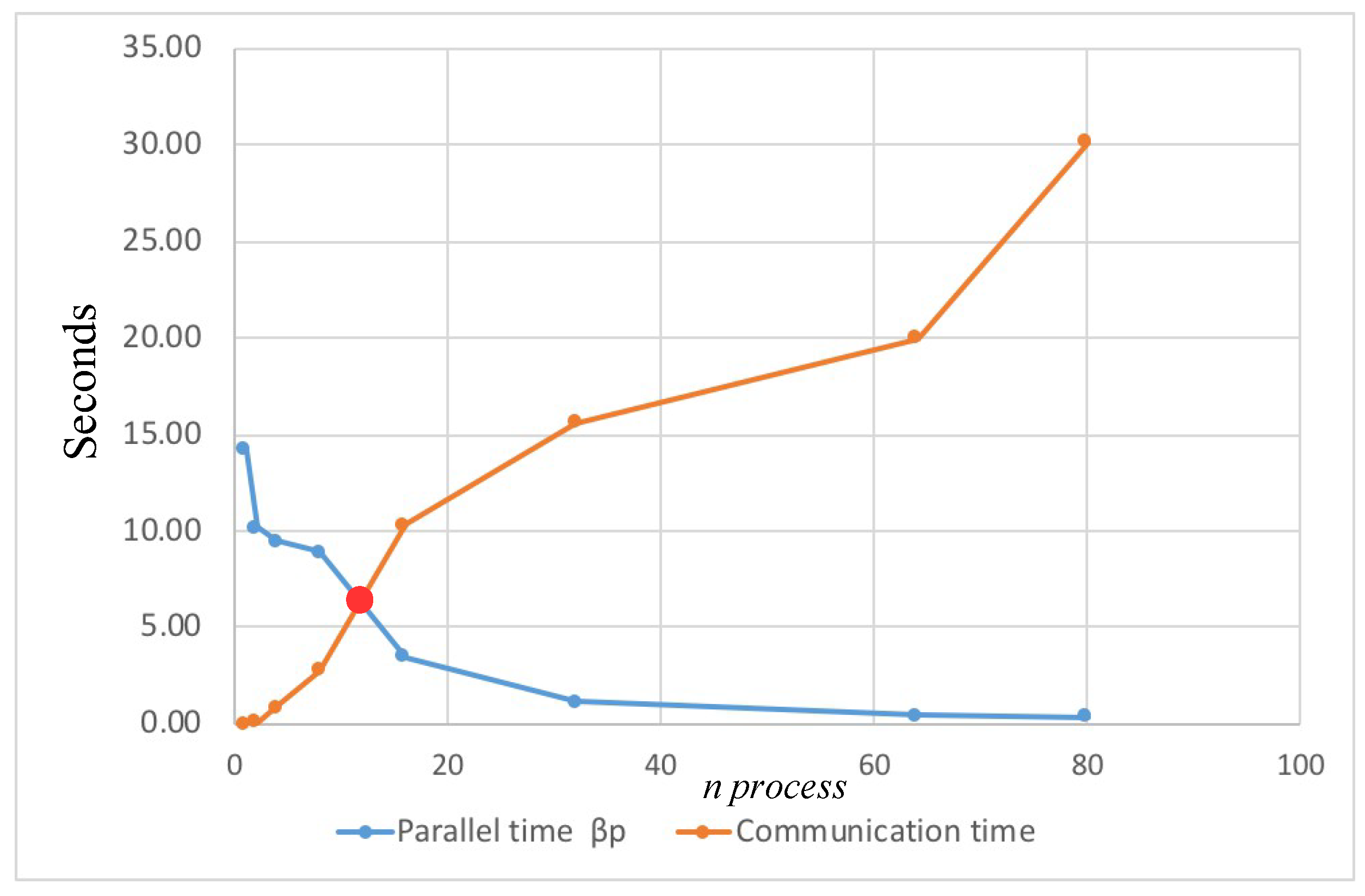
4.3. Performance Results Using Parallel Computing
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Tsai, C.J.; Wang, H.C.; Wu, J.L. Three Techniques for Enhancing Chaos-Based Joint Compression and Encryption Schemes. Entropy 2019, 21, 40. [Google Scholar] [CrossRef]
- Natiq, H.; Said, M.; Al-Saidi, N.; Kilicman, A. Dynamics and Complexity of a New 4D Chaotic Laser System. Entropy 2019, 21, 34. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiao, M.; Xiong, X. A Simple Chaotic Map-Based Image Encryption System Using Both Plaintext Related Permutation and Diffusion. Entropy 2018, 20, 535. [Google Scholar] [CrossRef]
- Sahari, M.L.; Boukemara, I. A Pseudo-Random Numbers Generator Based on A Novel 3D Chaotic Map with An Application to Color Image Encryption. Nonlinear Dyn. 2018, 94, 723–744. [Google Scholar] [CrossRef]
- Kocarev, L.; Lian, S. Chaos-Based Cryptography. Theory, Algorithms and Aplications; Springer-Verlag: Berlin, Germany, 2011; Volume 354. [Google Scholar]
- Lü, J.; Chen, G. New Chaotic Attractor Coined. Int. J. Bifurc. Chaos 2002, 12, 659–661. [Google Scholar] [CrossRef]
- Eckmann, J.P.; Ruelle, D. Ergodic Theory of Chaos and Atrange Attractors. Rev. Mod. Phys. 1985, 57, 617–656. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C.; Wang, W. A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy 2018, 20, 716. [Google Scholar] [CrossRef]
- Mondal, B.; Kumar, P.; Singh, S. A chaotic permutation and diffusion based image encryption algorithm for secure communications. Multimed. Tools Appl. 2018, 77, 31177–31198. [Google Scholar] [CrossRef]
- Fu, C.; Huang, J.B.; Wang, N.N.; Hou, Q.B.; Lei, W.M. A Symmetric Chaos-Based Image Cipher with an Improved Bit-Level Permutation Strategy. Entropy 2014, 16, 770–788. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S. A Fast Color Image Encryption Algorithm based on Hyper-chaotic Systems. Nonlinear Dyn. 2014, 78, 995–1015. [Google Scholar] [CrossRef]
- Hermassi, H.; Rhouma, R.; Belghith, S. Improvement of an Image Encryption Algorithm based on Hyper-chaos. Telecommun. Syst. 2013, 52, 539–549. [Google Scholar] [CrossRef]
- Inzunza-González, E.; Cruz-Hernández, C. Double Hyperchaotic Encryption for Security in Biometric Systems. Nonlinear Dyn. Syst. Theory 2013, 13, 55–68. [Google Scholar]
- Fu, C.; Chen, J.J.; Zou, H.; Meng, W.H.; Zhan, Y.F.; Yu, Y.W. A Chaos-Based Digital Image Encryption Scheme with an Improved Diffusion Strategy. Opt. Express 2012. [Google Scholar] [CrossRef] [PubMed]
- Seyedzadeh, S.; Mirzakuchaki, S. A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process. 2012, 92, 1202–1215. [Google Scholar] [CrossRef]
- Gao, T.; Chen, Z. A New Image Encryption Algorithm Based on Hyper-chaos. Phys. Lett. A 2008, 372, 394–400. [Google Scholar] [CrossRef]
- Mao, Y.; Chen, G.; Lian, S. A Novel Fast Image Encryption Scheme Based on 3D Chaotic Baker Maps. Int. J. Bifurc. Chaos 2004, 14, 3613–3624. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric Ciphers Based on Two-Dimensional Chaotic Maps. Int. J. Bifurc. Chaos 1998. [Google Scholar] [CrossRef]
- Matthews, R. On the derivation of a chaotic encryption algorithm. Cryptologia 1989, 13, 29–42. [Google Scholar] [CrossRef]
- Ping, P.; Wu, J.; Mao, Y.; Xu, F.; Fan, J. Design of Image Cipher Using Life-Like Cellular Automata and Chaotic Map. Signal Process. 2018, 150, 233–247. [Google Scholar] [CrossRef]
- Özkaynak, F. Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dyn. 2018, 92, 305–313. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
- Cao, C.; Sun, K.; Liu, W. A novel bit-level image encryption algorithm based on 2D-LICM hyperchaotic map. Signal Process. 2018, 143, 122–133. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Murillo-Escobar, M.A.; Cruz-Hernández, C.; Abundiz-Pérez, F.; López-Gutiérrez, R.M.; del Campo, O.R. A RGB Image Encryption Algorithm Based on Total Plain Image. Signal Process. 2015, 109, 119–131. [Google Scholar] [CrossRef]
- Kwok, H.; Tang, W.K. A Fast Image Encryption System Based on Chaotic Maps with Finite Precision Representation. Chaos Solitons Fractals 2007, 32, 1518–1529. [Google Scholar] [CrossRef]
- Muhammad, N.; Bibi, N.; Qasim, I.; Jahangir, A.; Mahmood, Z. Digital watermarking using Hall property image decomposition method. Pattern Anal. Appl. 2018, 21, 997–1012. [Google Scholar] [CrossRef]
- Farwa, S.; Muhammad, N.; Shah, T.; Ahmad, S. A Novel Image Encryption Based on Algebraic S-box and Arnold Transform. 3D Res. 2017, 8, 1–14. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Perez-Resa, A.; Sanchez-Azqueta, C.; Aldea, C.; Celma, S. Chaos-Based Bitwise Dynamical Pseudorandom Number Generator on FPGA. IEEE Trans. Instrum. Meas. 2019, 68, 291–293. [Google Scholar] [CrossRef]
- Rezk, A.; Madian, A.; Radwan, A.; Soliman, A. Reconfigurable Chaotic Pseudo Random Number Generator Based on FPGA. AEU - Int. J. Electron. Commun. 2019, 98, 174–180. [Google Scholar] [CrossRef]
- Elmanfaloty, R.; Abou-Bakr, E. Random Property Enhancement of a 1D chaotic PRNG with Finite Precision Implementation. Chaos Solitons Fractals 2019, 118, 134–144. [Google Scholar] [CrossRef]
- Palacios-Luengas, L.; Pichardo-Méndez, J.L.; Díaz-Méndez, J.A.; Rodríguez-Santos, F.; Vázquez-Medina, R. PRNG Based on Skew Tent Map. Arabian J. Sci. Eng. 2018, 1–14. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, Z.; Ma, J.; He, H. A Pseudorandom Number Generator Based on Piecewise Logistic Map. Nonlinear Dyn. 2016, 83, 2373–2391. [Google Scholar] [CrossRef]
- García-Martínez, M.; Campos-Cantón, E. Pseudo-Random Bit Generator Based on Multi-Modal Maps. Nonlinear Dyn. 2015, 82, 2119–2131. [Google Scholar] [CrossRef]
- Dragan, L.; Mladen, N. Pseudo-Random Number Generator Based on Discrete-Space Chaotic Map. Nonlinear Dyn. 2017, 90, 223–232. [Google Scholar]
- Murillo-Escobar, M.A.; Cruz-Hernández, C.; Cardoza-Avendaño, L.; Méndez-Ramírez, R. A novel pseudorandom number generator based on pseudorandomly enhanced logistic map. Nonlinear Dyn. 2017, 87, 407–425. [Google Scholar] [CrossRef]
- François, M.; Grosges, T.; Barchiesi, D.; Erra, R. Pseudo-random number generator based on mixing of three chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 887–895. [Google Scholar] [CrossRef]
- François, M.; Grosges, T.; Barchiesi, D.; Erra, R. A New Pseudo-Random Number Generator Based on Two Chaotic Maps. Informatica 2013, 24, 181–197. [Google Scholar]
- Stoyanov, B.; Kordov, K. Novel secure pseudo-random number generation scheme based on two tinkerbell maps. Adv. Stud. Theor. Phys. 2015, 9, 411–421. [Google Scholar] [CrossRef]
- Liu, Y.; Tong, X.J. A new pseudorandom number generator based on complex number chaotic equation. Chin. Phys. B 2012, 21, 090506. [Google Scholar]
- Yeoh, W.; Teh, J.; Chern, H. A Parallelizable Chaos-Based True Random Number Generator Based on Mobile Device Cameras for the Android Platform. Multimed. Tools Appl. 2018, 1–21. [Google Scholar] [CrossRef]
- Zhang, Y.; Aviad, Y.; Grahn, H.T. Chaotic Current Self-oscillations in Doped, Weakly Coupled Semiconductor Superlattices for True Random Number Generation. In Coupled Mathematical Models for Physical and Biological Nanoscale Systems and Their Applications; Springer Proceedings in Mathematics & Statistics; Bonilla, L., Kaxiras, E., Melnik, R., Eds.; Springer: Cham, Switzerland, 2018; Volume 232, pp. 35–50. [Google Scholar]
- Avaroğlu, E.; Tuncer, T.; Özer, A. A novel chaos-based post-processing for TRNG. Nonlinear Dyn. 2015, 81, 189–199. [Google Scholar] [CrossRef]
- Teh, J.; Samsudin, A.; Al-Mazrooie, M. GPUs and Chaos: A New True Random Number Generator. Nonlinear Dyn. 2015, 82, 1913–1922. [Google Scholar] [CrossRef]
- Cicek, I.; Pusane, A.; Dundar, G. A new dual entropy core true random number generator. Analog Integr. Circuits Signal Process. 2014, 81, 61–70. [Google Scholar] [CrossRef]
- Pano-Azucena, A.D.; Ovilla-Martinez, B.; Tlelo-Cuautle, E.; Muñoz-Pacheco, J.M.; de la Fraga, L.G. FPGA-based implementation of different families of fractional-order chaotic oscillators applying Grünwald–Letnikov method. Commun. Nonlinear Sci. Numer. Simul. 2019, 72, 516–527. [Google Scholar] [CrossRef]
- Rodríguez-Orozco, E.; García-Guerrero, E.E.; Inzunza-Gonzalez, E.; López-Bonilla, O.R.; Flores-Vergara, A.; Cárdenas-Valdez, J.R.; Tlelo-Cuautle, E. FPGA-based Chaotic Cryptosystem by Using Voice Recognition as Access Key. Electronics 2018, 7, 414. [Google Scholar] [CrossRef]
- Wang, Q.; Yu, S.; Li, C.; Lü, J.; Fang, X.; Guyeux, C.; Bahi, J.M. Theoretical design and FPGA-based implementation of higher-dimensional digital chaotic systems. IEEE Trans. Circuits Syst. I Regul. Pap. 2016, 63, 401–412. [Google Scholar] [CrossRef]
- Sadoudi, S.; Tanougast, C.; Azzaz, M.S.; Dandache, A. Design and FPGA implementation of a wireless hyperchaotic communication system for secure real-time image transmission. EURASIP J. Image Video Process. 2013, 2013, 43. [Google Scholar] [CrossRef]
- Azzaz, M.S.; Tanougast, C.; Sadoudi, S.; Fellah, R.; Dandache, A. A new auto-switched chaotic system and its FPGA implementation. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 1792–1804. [Google Scholar] [CrossRef]
- Guillen-Fernandez, O.; Melendez-Cano, A.; Tlelo-Cuautle, E.; Nuñez-Perez, J.C.; Rangel-Magdaleno, J.J. On the synchronization techniques of chaotic oscillators and their FPGA-based implementation for secure image transmission. PLoS ONE 2019, 14, 1–34. [Google Scholar] [CrossRef]
- Carbajal-Gomez, V.; Tlelo-Cuautle, E.; Sanchez-Lopez, C.; Fernandez-Fernandez, F. PVT-Robust CMOS Programmable Chaotic Oscillator: Synchronization of Two 7-Scroll Attractors. Electronics 2018, 7, 252. [Google Scholar] [CrossRef]
- De la Fraga, L.; Torres Pérez, E.; Tlelo-Cuautle, E.; Mancillas-López, C. Hardware implementation of pseudo-random number generators based on chaotic maps. Nonlinear Dyn. 2017, 90, 1661–1670. [Google Scholar] [CrossRef]
- Zuras, D.; Cowlishaw, M.; Aiken, A.; Applegate, M.; Bailey, D.; Bass, S.; Bhandarkar, D.; Bhat, M.; Bindel, D.; Boldo, S.; et al. IEEE Standard for Floating-Point Arithmetic; IEEE Std 754-2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–70. [Google Scholar]
- Li, S.; Mou, X.; Cai, Y.; Ji, Z.; Zhang, J. On the Security of a Chaotic Encryption Scheme: Problems with Computerized Chaos in Finite Computing Precision. Comput. Phys. Commun. 2003, 153, 52–58. [Google Scholar] [CrossRef]
- Li, S.; Chen, G.; Mou, X. On the Dynamical Degradation of Digital Piecewise Linear Chaotic Maps. Int. J. Bifurc. Chaos 2005, 15, 3119–3151. [Google Scholar] [CrossRef]
- Hu, H.; Deng, Y.; Liu, L. Counteracting the Dynamical Degradation of Digital Chaos via Hybrid Control. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 1970–1984. [Google Scholar] [CrossRef]
- Liu, L.; Liu, B.; Hu, H.; Miao, S. Reducing the Dynamical Degradation by Bi-Coupling Digital Chaotic Maps. Int. J. Bifurc. Chaos 2018, 28, 1850059-1–1850059-14. [Google Scholar] [CrossRef]
- Lee, W.-K.; Phan, R.C.-W.; Yap, W.-S.; Goi, B.-M. SPRING: A novel parallel chaos-based image encryption scheme. Nonlinear Dyn. 2018, 92, 575–593. [Google Scholar]
- ITU. Global Cybersecurity Index (GCI) 2017; Technical Report; ITU: Geneva, Switzerland, 2017. [Google Scholar]
- Liang, W.; Huang, W.; Chen, W.; Li, K.C.; Li, K. Hausdorff Distance Model-Based Identity Authentication for IP Circuits in Service-Centric Internet-of-Things Environment. Sensors 2019, 19, 487. [Google Scholar] [CrossRef] [PubMed]
- Zhu, C.; Wang, G.; Sun, K. Improved Cryptanalysis and Enhancements of an Image Encryption Scheme Using Combined 1D Chaotic Maps. Entropy 2018, 20, 843. [Google Scholar] [CrossRef]
- Zhu, C.; Wang, G.; Sun, K. Cryptanalysis and Improvement on an Image Encryption Algorithm Design Using a Novel Chaos Based S-Box. Symmetry 2018, 10, 399. [Google Scholar] [CrossRef]
- Farajallah, M.; Assad, S.; Deforges, O. Cryptanalyzing an image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Multimed. Tools Appl. 2018, 77, 28225–28248. [Google Scholar] [CrossRef]
- Yoo, T.; Kang, J.S.; Yeom, Y. Recoverable Random Numbers in an Internet of Things Operating System. Entropy 2017, 19, 113. [Google Scholar] [CrossRef]
- Ge, X.; Lu, B.; Liu, F. Cryptanalyzing an image encryption algorithm with compound chaotic stream cipher based on perturbation. Nonlinear Dyn. 2017, 90, 1141–1150. [Google Scholar] [CrossRef]
- Ng, I.C.; Wakenshaw, S.Y. The Internet-of-Things: Review and research directions. Int. J. Res. Mark. 2017, 34, 3–21. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Ashton, K. That “Internet of Things| Thing. RFiD J. 2009, 22, 97–114. [Google Scholar]
- Hussain, M.; Beg, M. Fog Computing for Internet of Things (IoT)-Aided Smart Grid Architectures. Big Data Cogn. Comput. 2019, 3, 8. [Google Scholar] [CrossRef]
- Sanou, B. ICT Facts and Figure 2017; ITU: Geneva, Switzerland, 2017. [Google Scholar]
- Ferreira, H.G.C.; de Sousa Junior, R.T. Security Analysis of a Proposed Internet of Things Middleware. Clust. Comput. 2017, 20, 651–660. [Google Scholar] [CrossRef]
- Flores-Vergara, A.; Garcia-Guerrero, E.E.; Inzunza-Gonzalez, E.; Bonilla, O.R.L.; Rodriguez-Orozco, E.; Cardenas-Valdez, J.R.; Tlelo-Cuautle, E. Implementing a chaotic cryptosystem in a 64-bit embedded system by using multiple-precision arithmetic. Nonlinear Dyn. 2019, 1–20. [Google Scholar] [CrossRef]
- Almasi, G.S.; Gottlieb, A. Highly Parallel Computing; ACM Digital Library: New York, NY, USA, 1989. [Google Scholar]
- Adve, S.V.; Adve, V.S.; Agha, G.; Frank, M.I.; Garzarán, M.J.; Hart, J.C.; Hwu, W.m.W.; Johnson, R.E.; Kale, L.; Kumar, R.; et al. Parallel Computing Research at Illinois: The UPCRC Agenda; University of Illinois: Urbana-Champaign, IL, USA, 2008. [Google Scholar]
- Asanovic, K.; Bodik, R.; Catanzaro, B. The Landscape of Parallel Computing Research: A View from Berkeley; Technical Report; EECS: Berkeley, CA, USA, 2006. [Google Scholar]
- Yuan, H.M.; Liu, Y.; Lin, T.; Hu, T.; Gong, L.H. A New Parallel Image Cryptosystem Based on 5D Hyperchaotic System. Signal Process. Image Commun. 2017, 52, 87–96. [Google Scholar] [CrossRef]
- Luo, Y.; Zhou, R.; Liu, J.; Cao, Y.; Ding, X. A Parallel Image Encryption Algorithm Based on the Piecewise Linear Chaotic Map and Hyper-Chaotic Map. Nonlinear Dyn. 2018, 93, 1165–1181. [Google Scholar] [CrossRef]
- Burak, D. Parallelization of an Encryption Algorithm Based on a Spatiotemporal Chaotic System and a Chaotic Neural Network. Procedia Comput. Sci. 2015, 51, 2888–2892. [Google Scholar] [CrossRef]
- Kim, J.; Kim, S.G.; Nam, B. Parallel multi-dimensional range query processing with R-trees on GPU. J. Parallel Distrib. Comput. 2013, 73, 1195–1207. [Google Scholar] [CrossRef]
- Omid, M.; Mahdi, Y.; Hassan, I. A New Image Encryption Method: Parallel Sub-Image Encryption with Hyper Chaos. Nonlinear Dyn. 2012, 67, 557–566. [Google Scholar]
- Zhou, Q.; Wong, K.; Liao, X.F.; Xiang, T.; Hu, Y. Parallel Image Encryption Algorithm Based on Discretized Chaotic Map. Chaos Solitons Fractals 2008, 38, 1081–1092. [Google Scholar] [CrossRef]
- Smith, D.M. Using multiple-precision arithmetic. Comput. Sci. Eng. 2003, 5, 88–93. [Google Scholar] [CrossRef]
- Larsen, A.H.; Mortensen, J.J.; Blomqvist, J.; Castelli, I.E.; Christensen, R.; Dułak, M.; Friis, J.; Groves, M.N.; Hammer, B.; Hargus, C.; et al. The atomic simulation environment—A Python library for working with atoms. J. Phys. Condens. Matter 2017, 29, 273002. [Google Scholar] [CrossRef] [PubMed]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; National Institute of Standards and Technology Special Publication 800-22 Rev.1a; National Institute of Standards and Technology Special: Gaithersburg, MD, USA, 2010; pp. 1–131.
- NIST. Security Requirements for Cryptographic Modules; Federal Information Processing Standard (FIPS PUB 140-2); NIST: Gaithersburg, MD, USA, 2001; pp. 1–56.
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. Cyber J. 2011, 1, 31–38. [Google Scholar]
- Behnia, S.; Akhshani, A.; Ahadpour, S.; Mahmodi, H.; Akhavand, A. A Fast Chaotic Encryption Scheme Based on Piecewise Nonlinear Chaotic Maps. Phys. Lett. A 2007, 366, 391–396. [Google Scholar] [CrossRef]
- Behnia, S.; Akhshani, A.; Mahmodi, H.; Akhavand, A. A Novel Algorithm for Image Encryption Based on Mixture of Chaotic Maps. Chaos Solitons Fractals 2008, 35, 408–419. [Google Scholar] [CrossRef]
- Akhshani, A.; Behnia, A.A.S.; Hassan, H.A.; Hassan, Z. A Novel Scheme for Image Encryption based on 2D Piecewise Chaotic Maps. Opt. Commun. 2010, 283, 3259–3266. [Google Scholar] [CrossRef]
- Fu, C.; Lin, B.b.; Miao, Y.s.; Liu, X.; Chen, J.J. A Novel Chaos-Based Bit-Level Permutation Scheme for Digital Image Encryption. Opt. Commun. 2011, 284, 5415–5423. [Google Scholar] [CrossRef]
- Patidar, V.; Pareek, N.K.; Purohit, G.; Sud, K.K. A Robust and Secure Chaotic Standard Map Based Pseudorandom Permutation-Substitution Scheme for Image Encryption. Opt. Commun. 2011, 284, 4331–4339. [Google Scholar] [CrossRef]
- Gene, A. Validity of the Single Processor Approach to Achieving Large-Scale Computing Capabilities. IEEE Solid-State Circuits Soc. Newsl. 2007, 12, 19–20. [Google Scholar]
- Yuan, S.; Jiang, T.; Jing, Z. Bifurcation and Chaos in the Tinkerbell map. Int. J. Bifurc. Chaos 2011, 11, 3137–3156. [Google Scholar] [CrossRef]
- Goldszztejn, A.; Hayes, W.; Collins, P. Tinkerbell is Chaotic. Siam J. Appl. Dyn. Syst. 2011, 10, 1480–1501. [Google Scholar] [CrossRef]
- Menezes, A.J.; Oorschot, P.C.V.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 1996. [Google Scholar]
- Dalcin, L.; Kler, P.; Paz, R.; Cosimo, A. Parallel Distributed Computing using Python. Adv. Water Resour. 2011, 34, 1124–1139. [Google Scholar] [CrossRef]
- Dalcin, L.; Paz, R.; Storti, M. MPI for Python. J. Parallel Distrib. Comput. 2005, 65, 1108–1115. [Google Scholar] [CrossRef]
- Hwang, K.; Jotwani, N. Advanced Computer Arquitecture: Parallelism, Scalability, Programmability; McGraw Hill: New York, NY, USA, 2011. [Google Scholar]
- Pareschi, F.; Rovatti, R.; Setti, G. On statistical tests for randomness included in the NIST SP800-22 test suite and based on the binomial distribution. IEEE Trans. Inf. Forensics Secur. 2012, 7, 491–505. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication Theory of Security Systems. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication Theory of Secrecy System. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Mao, Y.Y.; Deng, Z.C. A New Image Encryption Algorithm of Input-Output Feedback Based on Multi-chaotic System. Appl. Mech. Mater. 2011, 40–41, 924–929. [Google Scholar] [CrossRef]
- Kerckhoffs, A. La cryptographie militaire. J. Sci. Mil. 1883, IX, 161–191. [Google Scholar]
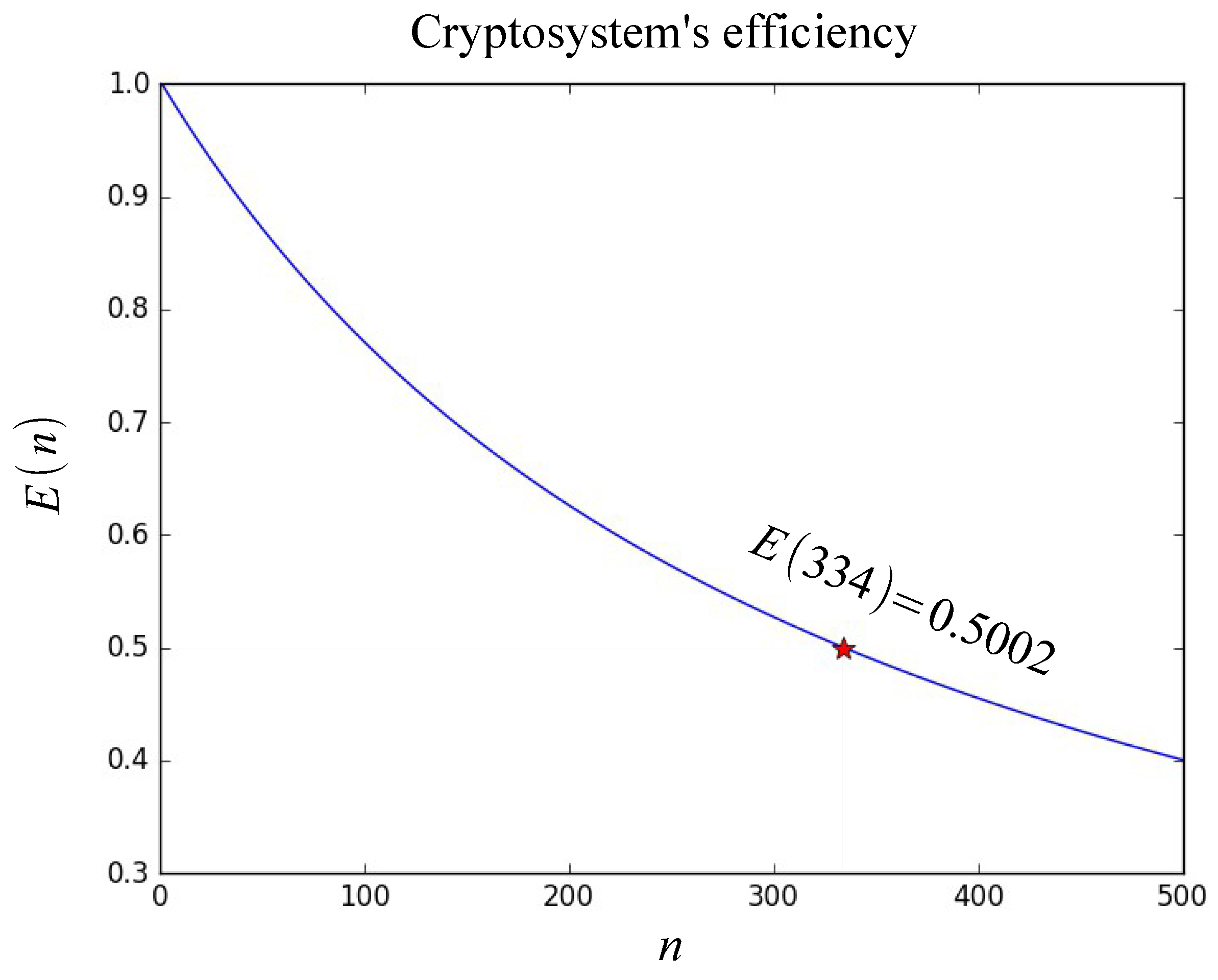
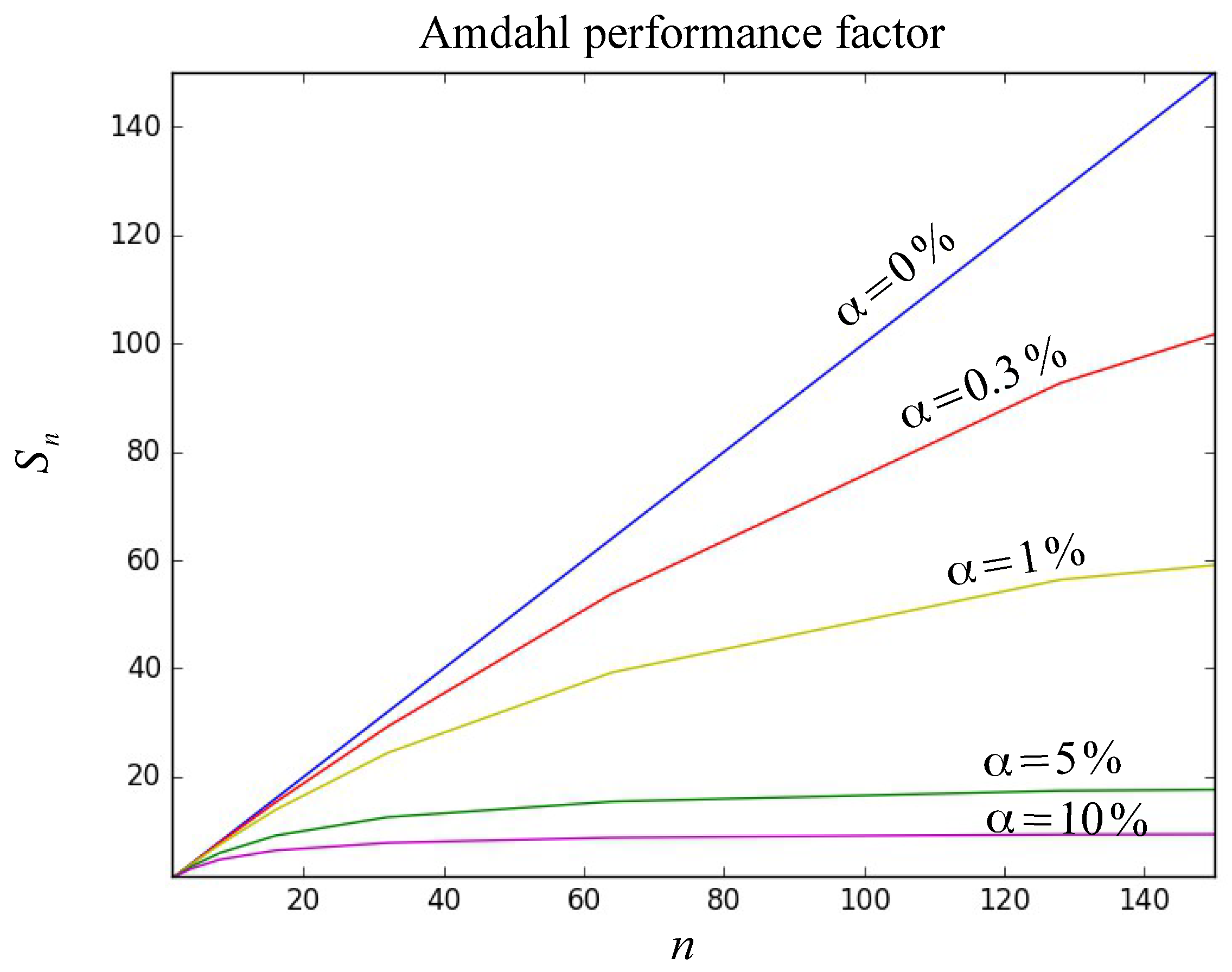



| Test Name | p-Value | p-Value | ||||
|---|---|---|---|---|---|---|
| x | Proportion | Results | y | Proportion | Results | |
| Frequency | Success | Failed | ||||
| Block Frequency | Success | Success | ||||
| Cumulative Sums-Forward | Success | Failed | ||||
| Cumulative Sums-Reverse | Success | Failed | ||||
| Runs | Failed | Failed | ||||
| Longest Run | Success | Success | ||||
| Rank | Success | Success | ||||
| FFT | Success | Success | ||||
| Non-Overlapping Templates | Success | Success | ||||
| Overlapping Templates | Success | Success | ||||
| Universal | Failed | Success | ||||
| Approximate Entropy | Success | Failed | ||||
| Random Excursions | Success | Success | ||||
| Random Excursions Variant | Success | Success | ||||
| Linear Complexity | Success | Success | ||||
| Serial (2m) | Failed | Success | ||||
| Average | - | - | ||||
| Cryptogram Size | Components RGB of 8 bit Entropy (bit/symbol) | |||
|---|---|---|---|---|
| Chaotic Map | Average Entropy | R | G | B |
| Proposed Tinkerbell [73] | 7.99925 | 7.99925 | 7.99924 | 7.99926 |
| Related work | ||||
| Logistic 1D [25] | 7.997200 | 7.99740 | 7.99750 | 7.99690 |
| PELM [36] | 7.994500 | N/A | N/A | N/A |
| Tent [32] | 7.998000 | N/A | N/A | N/A |
| Novel 3D [4] | 7.998200 | 7.99830 | 7.99820 | 7.99820 |
| Chen [11] | 7.997200 | 7.99720 | 7.99730 | 7.99710 |
| Lorenz & Chen [81] | 7.999300 | N/A | N/A | N/A |
| 5D Hyperchaotic [77] | 7.997300 | N/A | N/A | N/A |
| Logistic 1D [41] | 7.999999 | N/A | N/A | N/A |
| Logistic 1D [59] | 7.999100 | N/A | N/A | N/A |
| Cryptogram Size | Components RGB of 8 bit Entropy (bit/symbol) | |||
|---|---|---|---|---|
| n Process | Average Entropy (%) | R | G | B |
| FIAD cluster, CPU 1.2 GHz | ||||
| 1 | 7.9992743 | 7.9992716 | 7.9992623 | 7.9992888 |
| 2 | 7.9992962 | 7.9992525 | 7.9993085 | 7.9993277 |
| 4 | 7.9992476 | 7.9992258 | 7.9992211 | 7.9992959 |
| 8 | 7.9992692 | 7.9991658 | 7.9993238 | 7.9993182 |
| 16 | 7.9992042 | 7.9991641 | 7.9992064 | 7.9992421 |
| 32 | 7.9992992 | 7.9991472 | 7.9993798 | 7.9993705 |
| 64 | 7.9992831 | 7.9992403 | 7.9993189 | 7.9992901 |
| 128 | 7.9993141 | 7.9992695 | 7.9992722 | 7.9994006 |
| CPU 2.7 GHz | ||||
| 1 | 7.9992742 | 7.9992716 | 7.9992623 | 7.9992888 |
| 2 | 7.9992962 | 7.9992525 | 7.9993085 | 7.9993276 |
| 4 | 7.9992476 | 7.9992258 | 7.9992210 | 7.9992959 |
| 8 | 7.9992692 | 7.9991657 | 7.9993237 | 7.9993181 |
| 16 | 7.9992041 | 7.9991640 | 7.9992063 | 7.9992421 |
| 32 | 7.9992991 | 7.9991472 | 7.9993798 | 7.9993704 |
| 64 | 7.9992831 | 7.9992403 | 7.9993188 | 7.9992901 |
| 128 | 7.9993140 | 7.9992695 | 7.9992721 | 7.9994006 |
| Cryptogram Size | Critical NPCR Values [88] | |||
|---|---|---|---|---|
| = 99.5893%, | = 99.5810%, | = 99.5717%, | ||
| Chaotic Map | Average NPCR (%) | NPCR Test Result | ||
| Proposed Tinkerbell [73] | 99.6029 | Passed | Passed | Passed |
| Related work | ||||
| Logistic 1D [25] | 99.6100 | Passed | Passed | Passed |
| PELM [36] | 99.5774 | Failed | Failed | Passed |
| Multi-modal [34] | 99.0000 | Failed | Failed | Failed |
| Tent map [32] | 99.6300 | Passed | Passed | Passed |
| Novel 3D [4] | 99.6100 | Passed | Passed | Passed |
| Chen [11] | 99.8031 | Passed | Passed | Passed |
| 5D Hyperchaotic [77] | 99.6122 | Passed | Passed | Passed |
| Logistic 1D [59] | 99.6100 | Passed | Passed | Passed |
| Cryptogram Size | Critical NPCR Values [88] | |||
|---|---|---|---|---|
| = 99.5893%, | = 99.5810%, | = 99.5717%, | ||
| n Process | Average NPCR(%) | NPCR Test Result | ||
| FIAD cluster (1.2 GHz) | ||||
| 1 | Passed | Passed | Passed | |
| 2 | Passed | Passed | Passed | |
| 4 | Passed | Passed | Passed | |
| 8 | Passed | Passed | Passed | |
| 16 | Failed | Passed | Passed | |
| 32 | Passed | Passed | Passed | |
| 64 | Passed | Passed | Passed | |
| 128 | Failed | Failed | Passed | |
| CPU (2.7) GHz | ||||
| 1 | Passed | Passed | Passed | |
| 2 | Passed | Passed | Passed | |
| 4 | Passed | Passed | Passed | |
| 8 | Passed | Passed | Passed | |
| 16 | Failed | Passed | Passed | |
| 32 | Passed | Passed | Passed | |
| 64 | Passed | Passed | Passed | |
| 128 | Failed | Failed | Passed | |
| Cryptogram Size | Critical UACI Values [88] | |||
|---|---|---|---|---|
| = 33.3730%, = 33.5541%, | = 33.3445%, = 33.5826%, | = 33.3115%, = 33.6156%, | ||
| n Process | Average UACI (%) | UACI Test Result | ||
| FIAD cluster, CPU 1.2 GHz | ||||
| 1 | Passed | Passed | Passed | |
| 2 | Passed | Passed | Passed | |
| 4 | Passed | Passed | Passed | |
| 8 | Passed | Passed | Passed | |
| 16 | Passed | Passed | Passed | |
| 32 | Passed | Passed | Passed | |
| 64 | Passed | Passed | Passed | |
| 128 | Passed | Passed | Passed | |
| CPU (2.7) GHz | ||||
| 1 | Passed | Passed | Passed | |
| 2 | Passed | Passed | Passed | |
| 4 | Passed | Passed | Passed | |
| 8 | Passed | Passed | Passed | |
| 16 | Passed | Passed | Passed | |
| 32 | Passed | Passed | Passed | |
| 64 | Passed | Passed | Passed | |
| 128 | Passed | Passed | Passed | |
| Related work | ||||
| Logistic 1D [25] | 33.3600% | Failed | Passed | Passed |
| PELM [36] | 33.3014% | Failed | Failed | Failed |
| Multi-modal [34] | 34.8353% | Failed | Failed | Failed |
| Tent map [32] | 33.2800% | Failed | Failed | Failed |
| Novel 3D [4] | 33.4500% | Passed | Passed | Passed |
| Chen [11] | 33.6236% | Failed | Failed | Failed |
| 5D Hyperchaotic [77] | 33.4573% | Passed | Passed | Passed |
| Logistic 1D [59] | 33.4500% | Passed | Passed | Passed |
| Key Space | ||||
|---|---|---|---|---|
| Chaotic Map | Simple Precision | Double Precision | Multiple Precision (Proposed PRNG) | |
| Proposed Tinkerbell () [73] | ||||
| Tinkerbell () [73] | ||||
| Related work | ||||
| Rössler hyperchaotic [13] | N/A | N/A | N/A | |
| Discrete [35] | N/A | N/A | N/A | |
| Three chaotic maps [37] | N/A | N/A | N/A | |
| 5D Hyperchaotic [77] | N/A | N/A | N/A | |
| Chen [11] | N/A | N/A | N/A | |
| Tent map [32] | N/A | N/A | N/A | |
| Two chaotic maps [38] | N/A | N/A | N/A | |
| Logistic 1D [59] | N/A | N/A | N/A | |
| Novel 3D [4] | N/A | N/A | N/A | |
| Tinkerbell [39] | N/A | N/A | N/A | |
| Multi-modal [34] | N/A | N/A | N/A | |
| PLM [33] | N/A | N/A | N/A | |
| Logistic 1D [36] | N/A | N/A | N/A | |
| Logistic 1D [25] | N/A | N/A | N/A | |
| Quantity (n Process) | Cryptosystem Times and PRNG Speed | ||||
|---|---|---|---|---|---|
| Total Time (s) | (s) | Communication Time (s) | PRNG Speed (Mbit/s) | ||
| FIAD cluster, CPU 1.2 GHz | |||||
| 1 | N/A | N/A | 0.011799 | ||
| 2 | 0.045848 | ||||
| 4 | 0.100242 | ||||
| 8 | 0.381060 | ||||
| 10 | 0.682574 | ||||
| 16 | 2.998515 | ||||
| 20 | 4.673369 | ||||
| 32 | 6.169972 | ||||
| 40 | 6.338776 | ||||
| 64 | 20.131226 | ||||
| 80 | 12.362623 | ||||
| Dual core CPU 2.7 GHz | |||||
| 1 | N/A | ||||
| 2 | |||||
| 4 | |||||
| 8 | |||||
| 16 | |||||
| 32 | |||||
| 64 | |||||
| 80 | |||||
| Related work | |||||
| 1 CPU, 2.7 GHz [73] | N/A | N/A | N/A | N/A | |
| 1 CPU, 2.5 GHz [32] | N/A | N/A | N/A | N/A | |
| 1 CPU 2.0 GHz [36] | N/A | N/A | N/A | N/A | |
| 1 CPU, 1.9 GHz [35] | N/A | N/A | N/A | N/A | |
| 1 CPU, 2.8 GHz [39] | N/A | N/A | N/A | N/A | |
| 1 CPU, 2.1 GHz [39] | N/A | N/A | N/A | N/A | |
| 1 CPU, 2.4 GHz [11] | N/A | N/A | N/A | N/A | |
| 1 CPU, 3.0 GHz [15] | N/A | N/A | N/A | N/A | |
| Octa core CPU, 2.5 GHz [41] | N/A | N/A | N/A | ||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Flores-Vergara, A.; Inzunza-González, E.; García-Guerrero, E.E.; López-Bonilla, O.R.; Rodríguez-Orozco, E.; Hernández-Ontiveros, J.M.; Cárdenas-Valdez, J.R.; Tlelo-Cuautle, E. Implementing a Chaotic Cryptosystem by Performing Parallel Computing on Embedded Systems with Multiprocessors. Entropy 2019, 21, 268. https://doi.org/10.3390/e21030268
Flores-Vergara A, Inzunza-González E, García-Guerrero EE, López-Bonilla OR, Rodríguez-Orozco E, Hernández-Ontiveros JM, Cárdenas-Valdez JR, Tlelo-Cuautle E. Implementing a Chaotic Cryptosystem by Performing Parallel Computing on Embedded Systems with Multiprocessors. Entropy. 2019; 21(3):268. https://doi.org/10.3390/e21030268
Chicago/Turabian StyleFlores-Vergara, Abraham, Everardo Inzunza-González, Enrique Efren García-Guerrero, Oscar Roberto López-Bonilla, Eduardo Rodríguez-Orozco, Juan Miguel Hernández-Ontiveros, José Ricardo Cárdenas-Valdez, and Esteban Tlelo-Cuautle. 2019. "Implementing a Chaotic Cryptosystem by Performing Parallel Computing on Embedded Systems with Multiprocessors" Entropy 21, no. 3: 268. https://doi.org/10.3390/e21030268
APA StyleFlores-Vergara, A., Inzunza-González, E., García-Guerrero, E. E., López-Bonilla, O. R., Rodríguez-Orozco, E., Hernández-Ontiveros, J. M., Cárdenas-Valdez, J. R., & Tlelo-Cuautle, E. (2019). Implementing a Chaotic Cryptosystem by Performing Parallel Computing on Embedded Systems with Multiprocessors. Entropy, 21(3), 268. https://doi.org/10.3390/e21030268








