Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos
Abstract
:1. Introduction
- (1)
- Its pixel diffusion is invalid for attackers.
- (2)
- The combination of DNA encoding and DNA decoding can be equivalently simplified.
- (3)
- The sequences for DNA-base permutation are fixed for different plain-images.
2. The Encryption Algorithm under Study
2.1. DNA Coding Rules
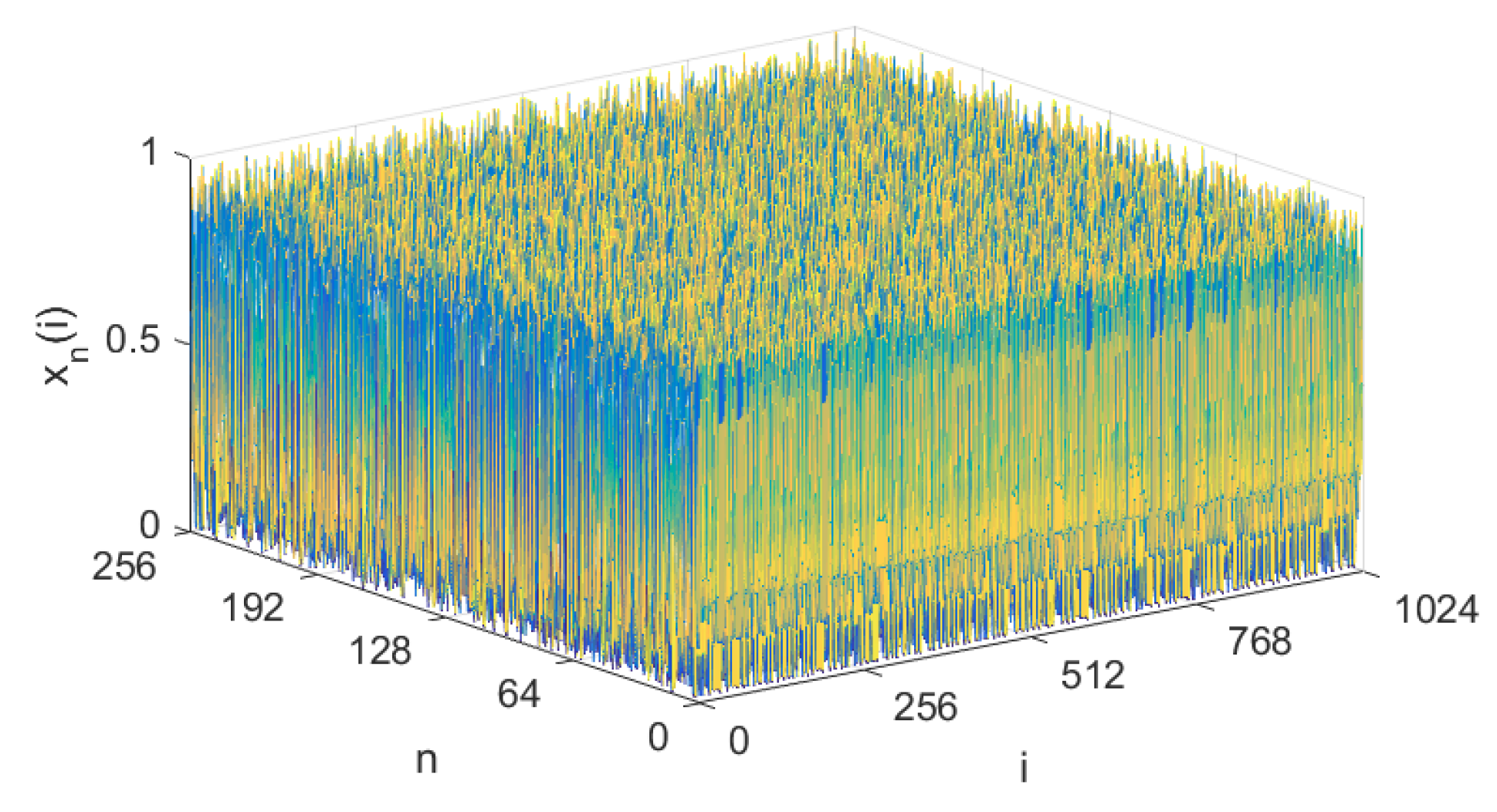
2.2. Spatiotemporal Chaos
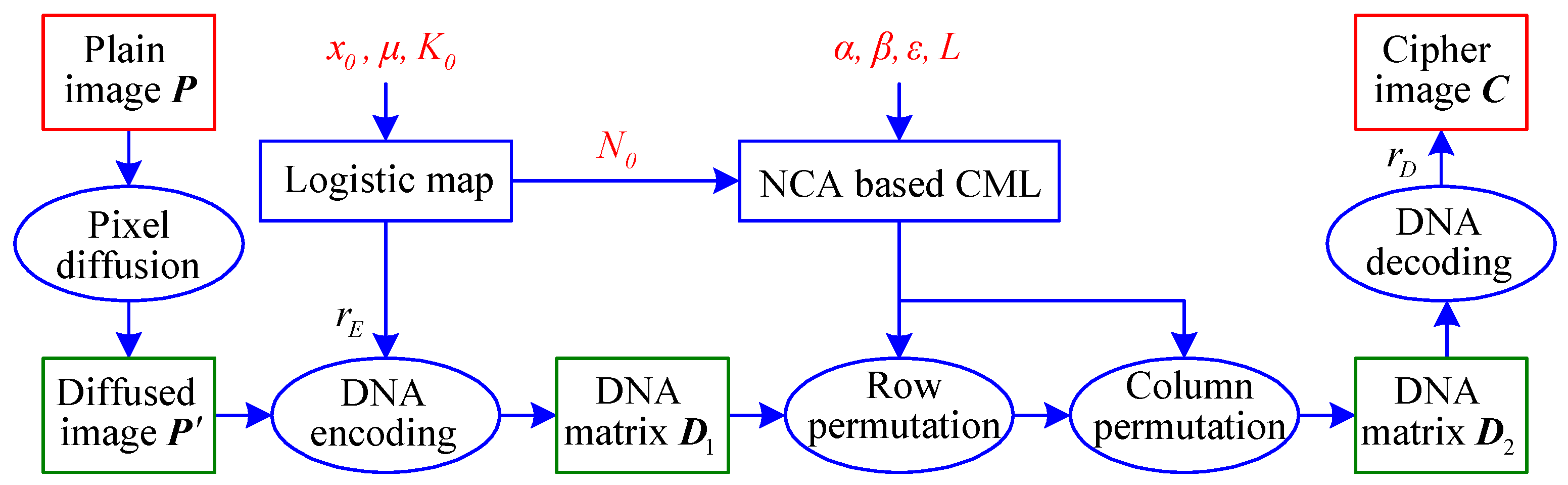
2.3. Description of IEA-DESC
2.3.1. Secret Key
2.3.2. Encryption Process
- Phase 1. Pixel Diffusion:By converting the plain-image into the corresponding sequence in raster scanning order, the pixel diffusion equation is defined aswhere , and ⊕ represents the bitwise XOR operation. Thus, the diffused image of size is obtained from the diffused sequence .
- Phase 2. DNA Encoding:Calculating the sum of the plain-image pixels, the -th iteration value is obtained by Equation (1) under the initial value and the control parameter . The DNA encoding rule , as in Table 1, is further determined bywhere , and rounds the element a to the nearest integer toward minus infinity. Then, by the -th encoding rule in Table 1, the diffused image of size is firstly converted into the corresponding binary matrix of size , and then encoded as the DNA matrix of size .
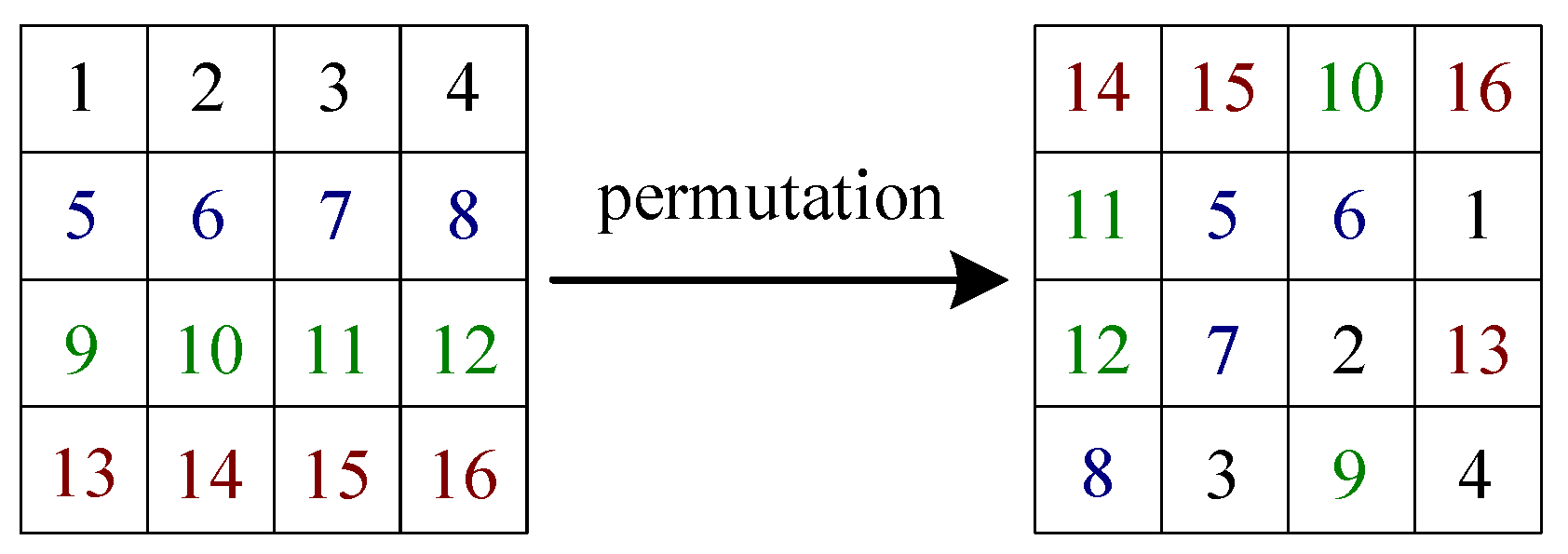
- Phase 3. DNA-Base Permutation:First, by iterating Equation (1) times and then discarding the front elements under the initial value and the control parameter , a sequence of length is obtained. Here, the sequence is taken as an initial value of the spatiotemporal chaos called NCA-based CML. Thus, by iterating Equation (2) H times under the parameters , and L, a real matrix of size is achieved.Then, by sorting each row’s elements of in ascending order, the corresponding H row position index sequences are obtained as . Using to perform permutation for each row on the DNA matrix , the corresponding row permuted DNA matrix is obtained, given bywhere , , indicates a position index of the k-th element in the i-th row, and . Similarly, by sorting each column’s elements of in ascending order, the corresponding column position index sequences are obtained as . Using to perform permutation for each column on the DNA matrix , the corresponding column permuted DNA matrix is obtained, represented aswhere , , indicates a position index of the k-th element in the j-th column, and .
- Phase 4. DNA Decoding:
2.3.3. Decryption Process
3. Cryptanalysis of IEA-DESC
3.1. Preliminary Analysis of IEA-DESC
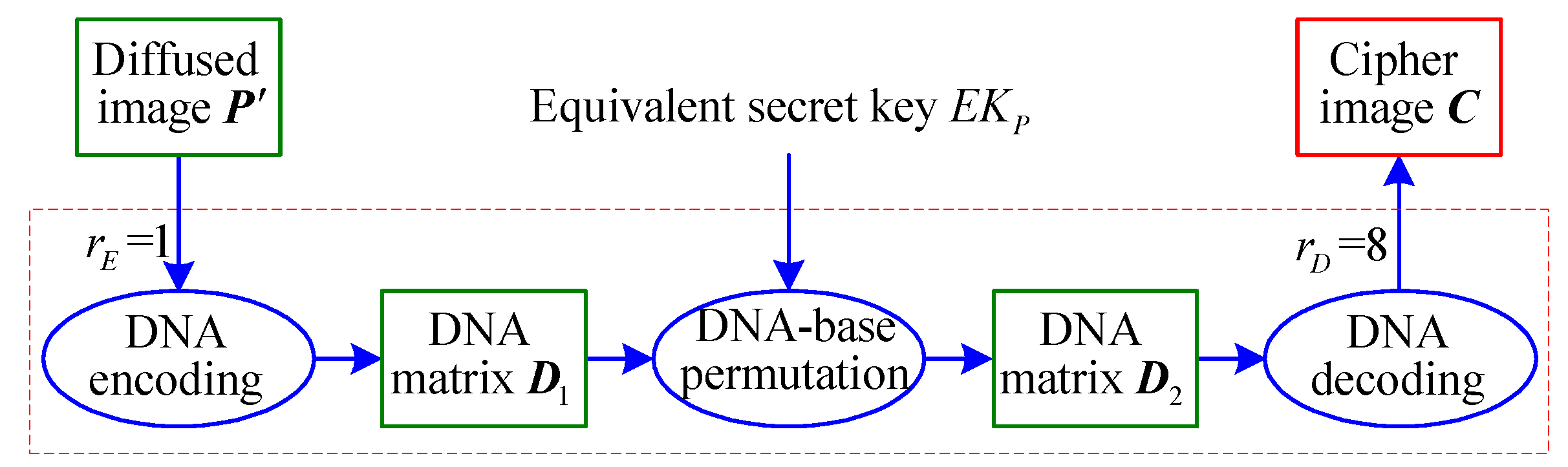
3.2. Analysis of DNA-Base Permutation
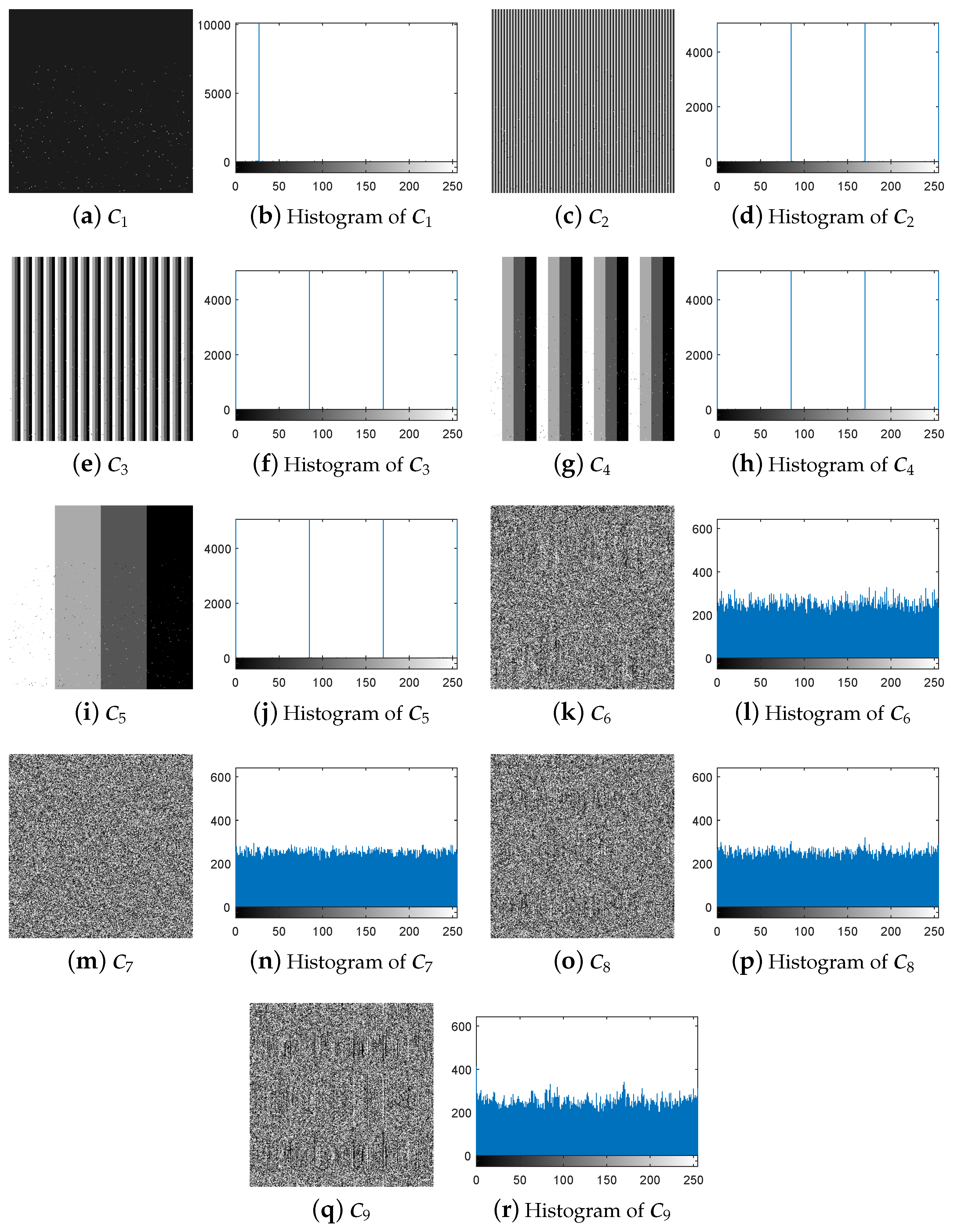
- Step 1.
- Decompose the virtual matrix of size into some quaternary matrices of the same size.
- Step 2.
- Transform these quaternary matrices into the 8-bit images of size , respectively.
- Step 3.
- Temporarily use the encryption machine to obtain the corresponding cipher-images.
- Step 4.
- Convert these 8-bit cipher-images into the quaternary matrices of size , respectively.
- Step 5.
- Compose the complementary quaternary matrices into a virtual matrix of size .
- Step 6.
- Obtain the equivalent secret key .
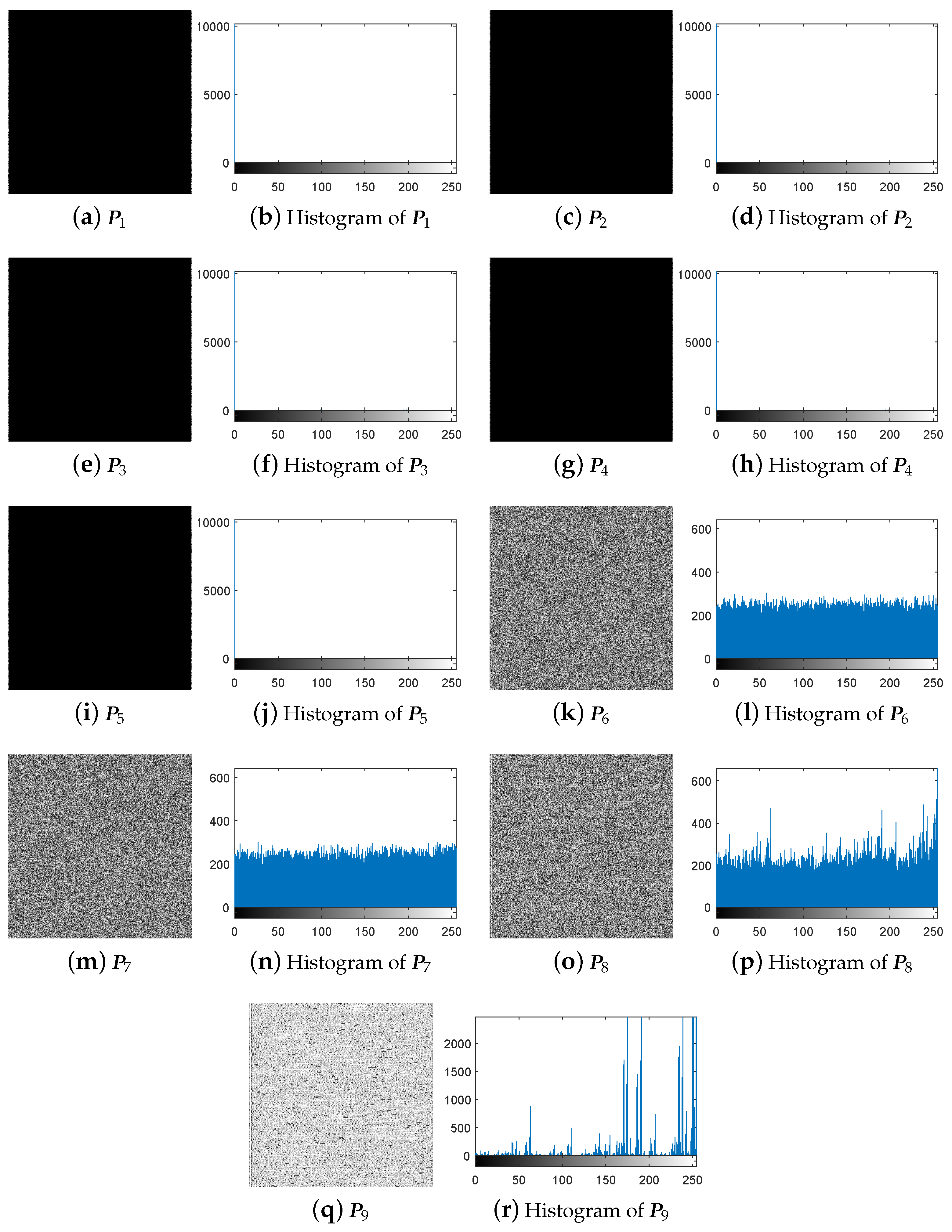
3.3. Breaking IEA-DESC Using the Chosen-Plaintext Attack
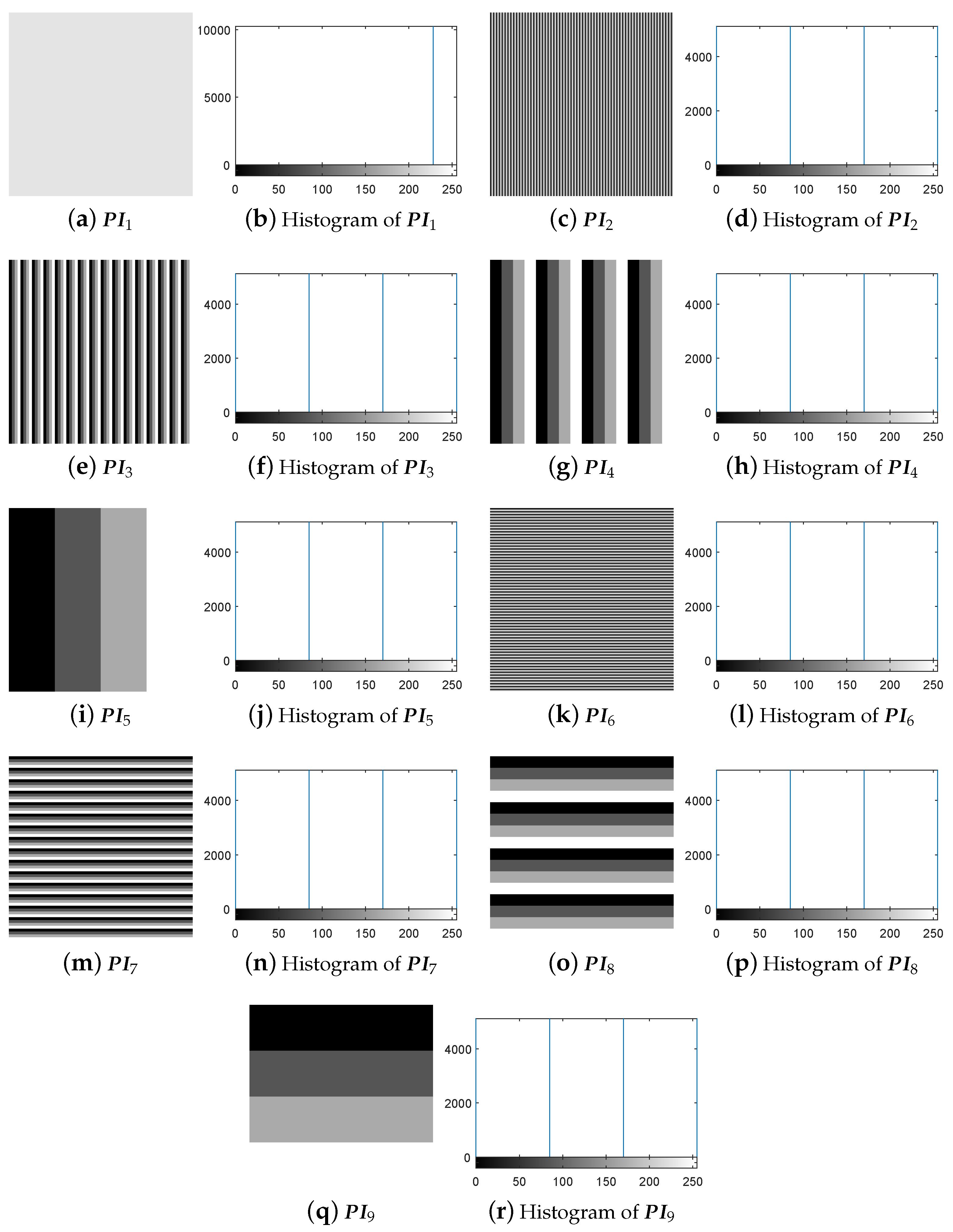
- Step 1.
- Choose some special plain-images.
- Step 2.
- Temporarily use the encryption machine to get the corresponding cipher-images.
- Step 3.
- Achieve the equivalent DNA-base permutation secret key.
- Step 4.
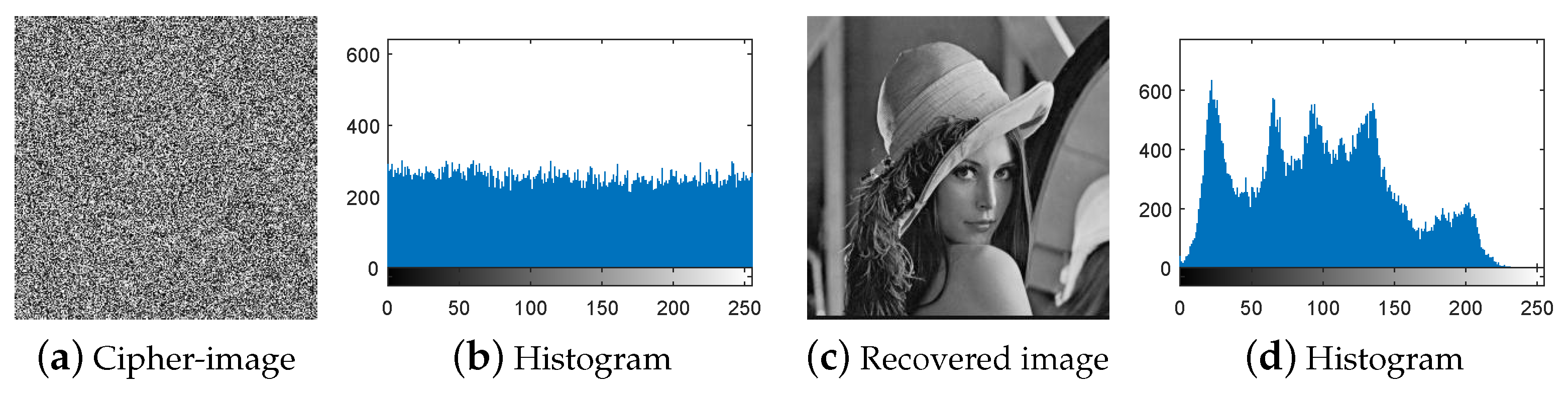
- Recover the images with the equivalent secret key.
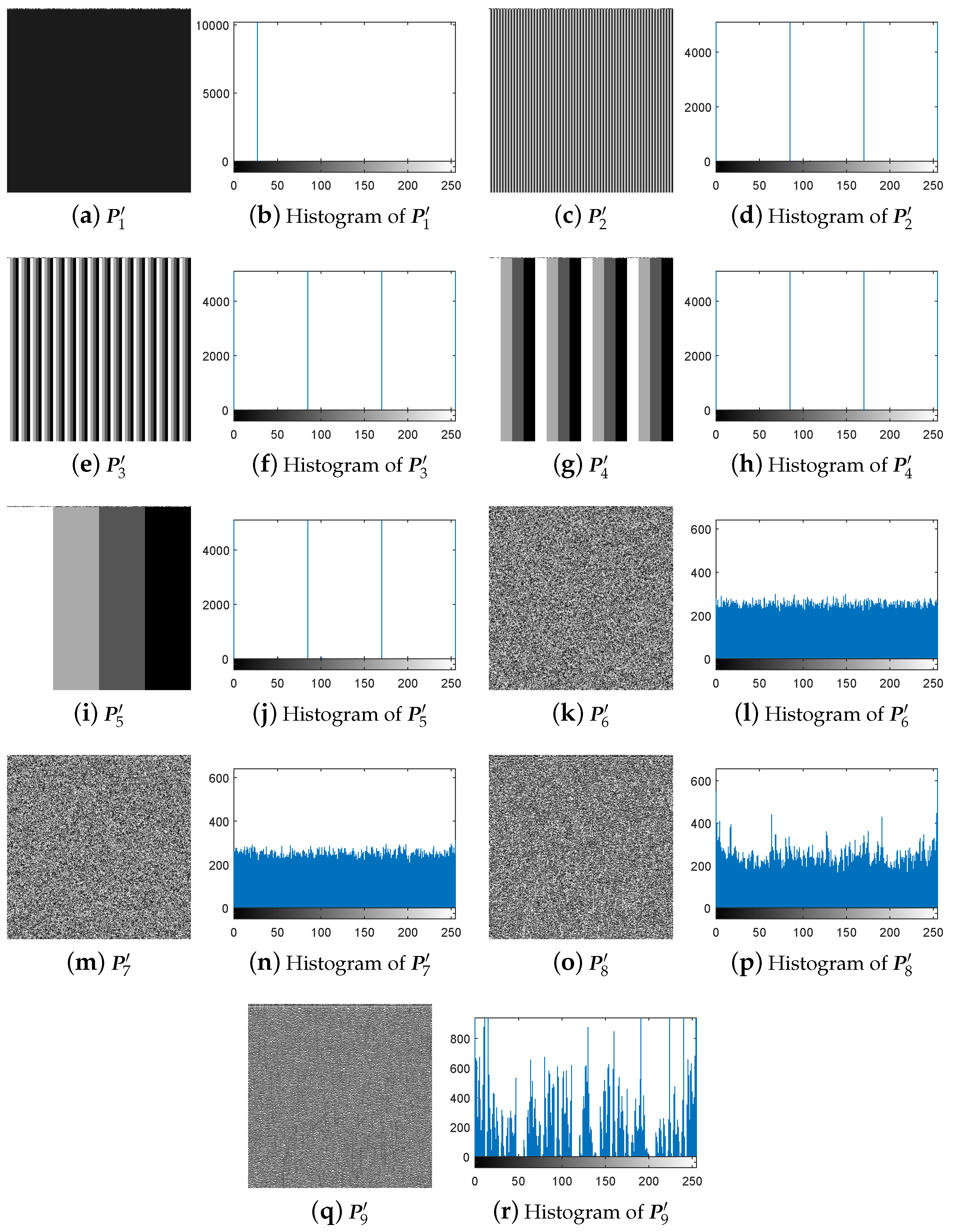
3.4. Breaking IEA-DESC Using the Chosen-Ciphertext Attack
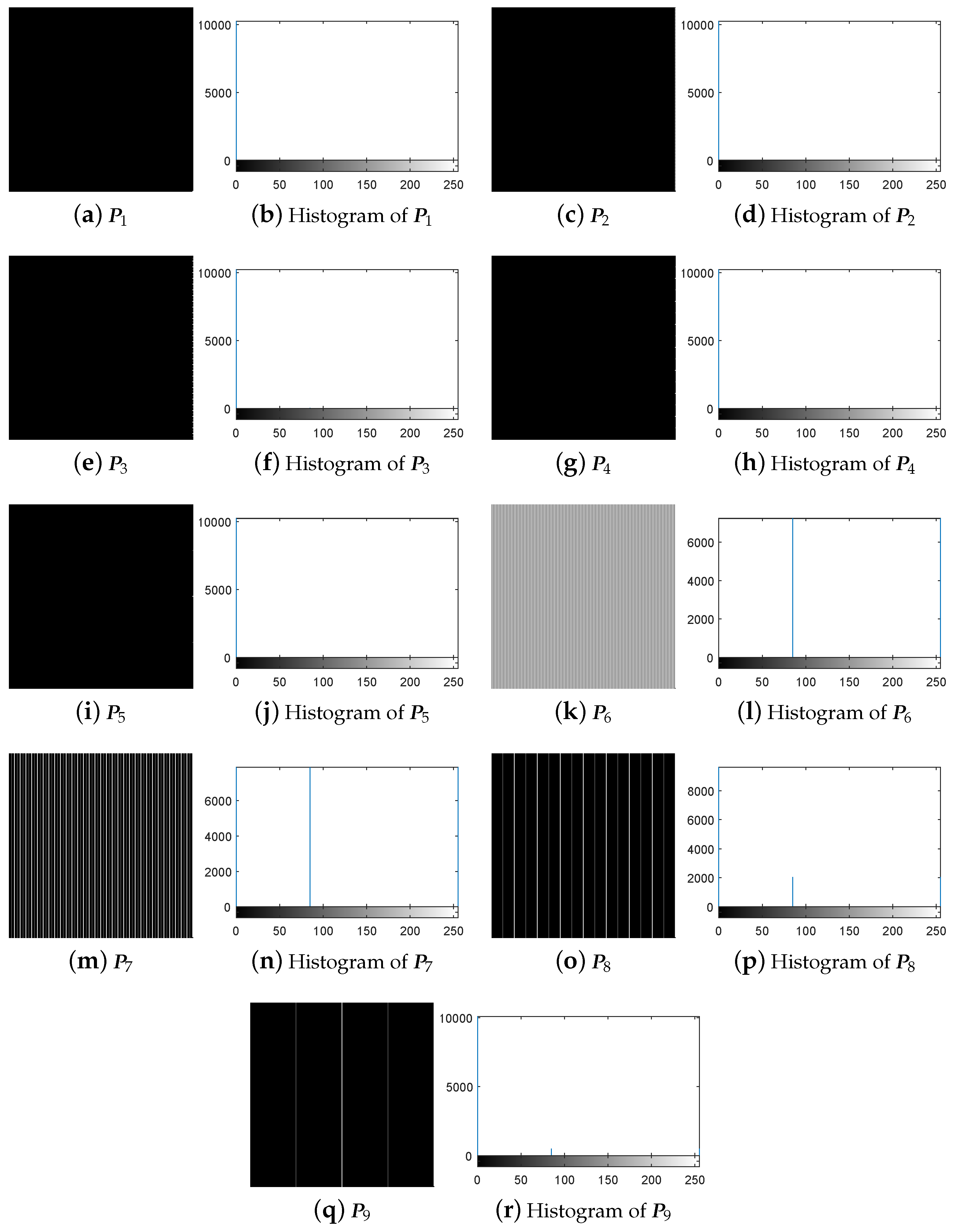
- Step 1.
- Choose some specific cipher-images and temporarily use the decryption machine to get the corresponding plain-images.
- Step 2.
- Get the corresponding diffused images.
- Step 3.
- Achieve the equivalent secret key.
- Step 4.
- Recover images with the equivalent secret key:
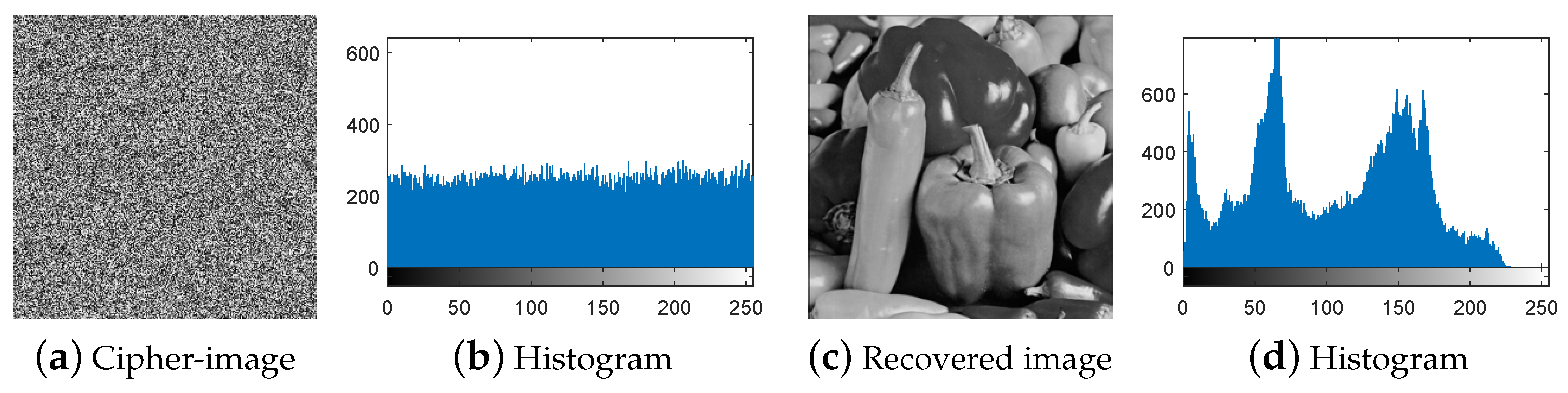
4. The Experiments for Breaking IEA-DESC
4.1. Breaking IEA-DESC by Chosen-Plaintext Attack
4.2. Breaking IEA-DESC Using the Chosen-Ciphertext Attack
4.3. Attack Complexity
5. Suggestions for Improvement
- (1)
- Checking the validity of each encryption component is significant.
- (2)
- Exploiting some novel permutation mechanisms to enhance the security.
- (3)
- Avoiding the existence of an equivalent secret key in the algorithm.
- (4)
- Appropriately increasing the number of encryption rounds.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Özkaynak, F. Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dyn. 2018, 92, 305–313. [Google Scholar] [CrossRef]
- Wen, H.; Yu, S.; Lü, J. Encryption algorithm based on hadoop and non-degenerate high-dimensional discrete hyperchaotic system. Acta Phys. Sin. 2017, 66, 230503. [Google Scholar] [CrossRef]
- Chen, S.; Yu, S.; Lü, J.; Chen, G.; He, J. Design and FPGA-based realization of a chaotic secure video communication system. IEEE Trans. Circuits Syst. Video Technol. 2018, 28, 2359–2371. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Chen, G.; Mao, Y.; Chui, C.K. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Lorenz, E.N. Deterministic nonperiodic flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef]
- Gehani, A.; LaBean, T.; Reif, J. DNA-based cryptography. In Aspects of Molecular Computing; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2950, pp. 167–188. [Google Scholar]
- Abdo, A.; Lian, S.; Ismail, I.; Amin, M.; Diab, H. A cryptosystem based on elementary cellular automata. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 136–147. [Google Scholar] [CrossRef]
- Yang, Y.G.; Tian, J.; Lei, H.; Zhou, Y.H.; Shi, W.M. Novel quantum image encryption using one-dimensional quantum cellular automata. Inf. Sci. 2016, 345, 257–270. [Google Scholar] [CrossRef]
- Akhshani, A.; Akhavan, A.; Lim, S.C.; Hassan, Z. An image encryption scheme based on quantum logistic map. Commun. Nonlinear Sci. Numer. Simul. 2012, 17, 4653–4661. [Google Scholar] [CrossRef]
- Askar, S.S.; Karawia, A.; Al-Khedhairi, A.; Al-Ammar, F.S. An algorithm of image encryption using logistic and two-dimensional chaotic economic maps. Entropy 2019, 21, 44. [Google Scholar] [CrossRef]
- Karawia, A. Encryption algorithm of multiple-image using mixed image elements and two dimensional chaotic economic map. Entropy 2018, 20, 801. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X. Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt. Commun. 2011, 284, 3895–3903. [Google Scholar] [CrossRef]
- He, S.; Sun, K.; Wang, H. Complexity analysis and DSP implementation of the fractional-order lorenz hyperchaotic system. Entropy 2015, 17, 8299–8311. [Google Scholar] [CrossRef]
- Chen, C.; Sun, K.; Peng, Y.; Alamodi, A.O. A novel control method to counteract the dynamical degradation of a digital chaotic sequence. Eur. Phys. J. Plus 2019, 134. [Google Scholar] [CrossRef]
- Li, C.; Feng, B.; Li, S.; Kurths, J.; Chen, G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Yang, K.; Chen, Y.; Liu, X. An image encryption algorithm based on the memristive hyperchaotic system, cellular automata and DNA sequence operations. Signal Process. Image Commun. 2017, 52, 6–19. [Google Scholar] [CrossRef]
- Zhang, L.; Sun, K.; Liu, W.; He, S. A novel color image encryption scheme using fractional-order hyperchaotic system and DNA sequence operations. Chin. Phys. B 2017, 26, 100504. [Google Scholar] [CrossRef]
- Chai, X.; Fu, X.; Gan, Z.; Lu, Y.; Chen, Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 2019, 155, 44–62. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Lin, Z.; Yu, S.; Feng, X.; Lü, J. Cryptanalysis of a chaotic stream cipher and its improved scheme. Int. J. Bifurc. Chaos 2018, 28, 1850086. [Google Scholar] [CrossRef]
- Zhu, C.; Wang, G.; Sun, K. Improved cryptanalysis and enhancements of an image encryption scheme using combined 1D chaotic maps. Entropy 2018, 20, 843. [Google Scholar] [CrossRef]
- Li, C.; Liu, Y.; Zhang, L.Y.; Wong, K.W. Cryptanalyzing a class of image encryption schemes based on Chinese Remainder Theorem. Signal Process. Image Commun. 2014, 29, 914–920. [Google Scholar] [CrossRef]
- Zhang, Q.; Guo, L.; Wei, X. Image encryption using DNA addition combining with chaotic maps. Math. Comput. Model. 2010, 52, 2028–2035. [Google Scholar] [CrossRef]
- Hermassi, H.; Belazi, A.; Rhouma, R.; Belghith, S.M. Security analysis of an image encryption algorithm based on a DNA addition combining with chaotic maps. Multimed. Tools Appl. 2014, 72, 2211–2224. [Google Scholar] [CrossRef]
- Zhen, P.; Zhao, G.; Min, L.; Jin, X. Chaos-based image encryption scheme combining DNA coding and entropy. Multimed. Tools Appl. 2016, 75, 6303–6319. [Google Scholar] [CrossRef]
- Su, X.; Li, W.; Hu, H. Cryptanalysis of a chaos-based image encryption scheme combining DNA coding and entropy. Multimed. Tools Appl. 2017, 76, 14021–14033. [Google Scholar] [CrossRef]
- Jain, A.; Rajpal, N. A robust image encryption algorithm resistant to attacks using DNA and chaotic logistic maps. Multimed. Tools Appl. 2016, 75, 5455–5472. [Google Scholar] [CrossRef]
- Dou, Y.; Liu, X.; Fan, H.; Li, M. Cryptanalysis of a DNA and chaos based image encryption algorithm. Optik-Int. J. Light Electron Opt. 2017, 145, 456–464. [Google Scholar] [CrossRef]
- Sun, S. A novel hyperchaotic image encryption scheme based on DNA encoding, pixel-level scrambling and bit-level scrambling. IEEE Photonics J. 2018, 10, 1–14. [Google Scholar] [CrossRef]
- Feng, W.; He, Y. Cryptanalysis and improvement of the hyper-chaotic image encryption scheme based on DNA encoding and scrambling. IEEE Photonics J. 2018, 10, 1–15. [Google Scholar] [CrossRef]
- Özkaynak, F.; Yavuz, S. Analysis and improvement of a novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Nonlinear Dyn. 2014, 78, 1311–1320. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D.; Wen, W.; Wong, K.W. On the security of symmetric ciphers based on DNA coding. Inf. Sci. 2014, 289, 254–261. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lü, J. Cryptanalyzing an Image-Scrambling Encryption Algorithm of Pixel Bits. IEEE Multimed. 2017, 24, 64–71. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lü, J.; Hao, F. Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimed. 2018, 25, 46–56. [Google Scholar] [CrossRef]
- Song, C.; Qiao, Y. A novel image encryption algorithm based on DNA encoding and spatiotemporal chaos. Entropy 2015, 17, 6954–6968. [Google Scholar] [CrossRef]
- Schneier, B. Applied Cryptography—Protocols, Algorithms, and Souce Code in C, 2nd ed.; John Wiley & Sons, Inc.: New York, NY, USA, 1996. [Google Scholar]
- Li, C.; Lo, K.T. Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process. 2011, 91, 949–954. [Google Scholar] [CrossRef]
- Jolfaei, A.; Wu, X.W.; Muthukkumarasamy, V. On the security of permutation-only image encryption schemes. IEEE Trans. Inf. Forensics Secur. 2016, 11, 235–246. [Google Scholar] [CrossRef]
- Gao, H.; Zhang, Y.; Liang, S.; Li, D. A new chaotic algorithm for image encryption. Chaos Solitons Fractals 2006, 29, 393–399. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Xie, E.Y.; Li, C.; Yu, S.; Lü, J. On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 2017, 132, 150–154. [Google Scholar] [CrossRef]
- Li, C. Cracking a hierarchical chaotic image encryption algorithm based on permutation. Signal Process. 2016, 118, 203–210. [Google Scholar] [CrossRef]
| Rules | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| A | 00 | 00 | 01 | 01 | 10 | 10 | 11 | 11 |
| T | 11 | 11 | 10 | 10 | 01 | 01 | 00 | 00 |
| G | 01 | 10 | 00 | 11 | 00 | 11 | 01 | 10 |
| C | 10 | 01 | 11 | 00 | 11 | 00 | 10 | 01 |
| Attack Methods | Available Resources for Cryptanalysis |
|---|---|
| Ciphertext-only attack | The attacker only knows the ciphertext. |
| Known-plaintext attack | The attacker knows any given plaintext, and also knows the corresponding ciphertext. |
| Chosen-plaintext attack | The attacker can choose the plaintext that would be useful for deciphering, and also knows the corresponding ciphertext. |
| Chosen-ciphertext attack | The attacker can choose the ciphertext that is useful for deciphering, and also knows the corresponding plaintext. |
| 2-Bit Input | DNA-Base with Encoding Rule | 2-Bit Output with Decoding Rule | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | ||
| 00 | A | A | G | C | G | C | T | T | 11 |
| 01 | G | C | A | A | T | T | C | G | 10 |
| 10 | C | G | T | T | A | A | G | C | 01 |
| 11 | T | T | C | G | C | G | A | A | 00 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, H.; Yu, S.; Lü, J. Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos. Entropy 2019, 21, 246. https://doi.org/10.3390/e21030246
Wen H, Yu S, Lü J. Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos. Entropy. 2019; 21(3):246. https://doi.org/10.3390/e21030246
Chicago/Turabian StyleWen, Heping, Simin Yu, and Jinhu Lü. 2019. "Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos" Entropy 21, no. 3: 246. https://doi.org/10.3390/e21030246
APA StyleWen, H., Yu, S., & Lü, J. (2019). Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos. Entropy, 21(3), 246. https://doi.org/10.3390/e21030246





