Abstract
In this paper, we propose and evaluate the performance of fountain codes (FCs) based secure transmission protocols in multiple-input-multiple-output (MIMO) wireless systems, in presence of a passive eavesdropper. In the proposed protocols, a source selects its best antenna to transmit fountain encoded packets to a destination that employs selection combining (SC) or maximal ratio combing (MRC) to enhance reliability of the decoding. The transmission is terminated when the destination has a required number of the encoded packets to reconstruct the original data of the source. Similarly, the eavesdropper also has the ability to recover the source data if it can intercept a sufficient number of the encoded packets. To reduce the number of time slots used, the source can employ non-orthogonal multiple access (NOMA) to send two encoded packets to the destination at each time slot. For performance analysis, exact formulas of average number of time slots (TS) and intercept probability (IP) over Rayleigh fading channel are derived and then verified by Monte-Carlo simulations. The results presented that the protocol using NOMA not only reduces TS but also obtains lower IP at medium and high transmit signal-to-noise ratios (SNRs), as compared with the corresponding protocol without using NOMA.
1. Introduction
Secure communication is one of the critical issues of wireless communication systems due to the broadcast nature of wireless channels. Conventionally, cryptographic methods at upper layers are used to obtain wireless security via generating cryptographic keys. However, eavesdroppers can decode the encrypted signals if they are equipped with advanced equipment and have enough time for the decoding operation. In [1,2,3,4,5,6], the authors introduced a new security method, called physical-layer security (PLS), where characteristics of wireless channels, i.e., distances and channel state information (CSI), can be exploited to ensure confidentiality of the data transmission. To obtain the security in PLS, the secrecy capacity must be greater than zero or the channel capacity of the data link must be better than that of the eavesdropping link. For example, joint transmit and receive diversity methods [7,8,9,10] were proposed to enhance secrecy performances for multiple-input-multiple-output (MIMO) secure communication protocols, in terms of secrecy outage probability (SOP) and probability of non-zero secrecy capacity (PNSC). Particularly, the transmitters in [7,8,9,10] select the best transmit antenna (transmit antenna selection (TAS)) to maximize post-processed signal-to-noise ratios (SNRs) obtained at the intended receivers that use maximal ratio combining (MRC) or selection combining (SC). Because the eavesdroppers in [7,8,9,10] only obtain the receive diversity with their MRC or SC combiners, the diversity order of the data links can be higher than that of the eavesdropping ones. In [11], the secrecy outage performance of the TAS/MRC method in underlay cognitive radio networks (CRNs) was evaluated. In the underlay spectrum sharing approach, transmit power of the secondary transmitters is limited by a pre-determined interference level so that quality of service (QoS) of the primary network is not harmful. In contrast to [11], the authors in [12] proposed a secure transmission protocol in overlay CRNs. In this system model, a full-duplex secondary transmitter employs TAS/MRC to transmit the secondary data and receive the primary data at the same time. Moreover, it can use an interactive zero forcing beam-forming method to simultaneously broadcast both the primary and secondary data. The protocol proposed in [12] not only enhances the SOP performance for the primary network but also improves throughput of the secondary transmission. Published works [13,14] introduced the PLS schemes in radio frequency energy harvesting (RF-EH) environment. In [13], one multi-antenna base station adopts TAS to send information and energy to one desired receiver and EH receivers, respectively. Since the EH receivers can illegally decode the information of the intended receiver, there exists a trade-off between energy harvested and security of the data transmission. In [14], an energy-limited source harvests the RF energy from a dedicated power beacon for transmitting the data in presence of multiple eavesdroppers. In addition, the source can employ TAS or maximal ratio transmission (MRT) to enhance the secrecy diversity order. Recently, secure transmission approaches for non-orthogonal multiple access (NOMA) systems have been studied. In contrast to conditional transmission techniques, the source using NOMA can send multiple signals to the destinations at the same time, frequency and code. Indeed, the signals that are linearly combined with different transmit power levels are then sent to the destinations which use successive interference cancellation (SIC) to extract the desired signals. In [15], the authors proposed various TAS methods to enhance the secrecy performance for two-user down-link NOMA networks. Reference [16] investigated the SOP performance of a secure NOMA system using max-min TAS method, in presence of non-colluding and colluding eavesdroppers.
Cooperative relaying protocols with efficient relay selection methods [17,18,19] also provide high secrecy performance for PLS-based wireless networks. The advantages of these schemes are that (i) the data transmission on short hops is more reliable, (ii) the relay selection provides high diversity gain. However, because the source data can be overheard over multiple hops, the channel capacity obtained at the eavesdroppers can be significantly increased by using the MRC combiner [20]. To solve this problem, a randomize-and-forward strategy [20,21] is often employed by the transmitters including the source and the relays to confuse the eavesdroppers. In [22], a secure transmission protocol in a dual-hop MIMO relay system using TAS/MRC over Nakagami-m fading channels was proposed and analyzed. The authors of [23] considered a buffer-aided MIMO cooperative system in the presence of a passive eavesdropper. Particularly, due to lack of the CSI of the eavesdropping channel, a joint transmit antenna and relay selection scheme was proposed to only enhance the quality of the main channel. Published works [24,25] analyzed SOP of dual-hop cooperative underlay CRNs with and without direct link between the secondary source and the secondary destination. In [26], secure communication protocols in multi-hop underlay CRNs were considered. In addition, the authors in [26] introduced an efficient cooperative routing method to enhance the end-to-end secrecy performance, as compared with the traditional mutli-hop transmission one. To further enhance the secrecy performance for cooperative cognitive networks, cooperative jamming (CJ) [27,28] can be used. With CJ, jammers are employed to transmit interference on the eavesdroppers, while the intended receivers can remove the interference from their received signals via cooperation with jammers. However, the implementation of the CJ methods is very complex due to a high synchronization between the jammer and receiver nodes. Moreover, the jamming signals can cause co-channel interference on other wireless devices in the network. In [29], the authors proposed a secure two-way relaying protocol, where two legitimate users exchange data with each other via the help of amplify-and-forward cooperative relays, with presence of an eavesdropper, and imperfect CSI of the eavesdropping channels. References [30,31,32] considered secure transmission protocols in RF-EH relay systems, in which the relay nodes have to harvest energy from the RF signals to forward the source data to the destination. In [32], the destination plays a role as a jammer for obtaining positive secrecy rate with presence of the untrusted relay. In [33,34,35], wireless powered CJ methods are employed to improve the secrecy rate. In these methods, called harvest-to-jam (HJ), the jammer nodes first harvest energy from ambient RF sources and then use the harvested energy to generate noises. References [36,37] investigated the secrecy performance of cooperative NOMA systems with various relay selection methods. In [38], the source performs the jamming operation to enhance the security for dual-hop relaying networks using NOMA. In [39,40], secure NOMA transmission strategies in CRNs were proposed and analyzed. In [41], the trade-off between security and reliability of cooperative cognitive NOMA systems was evaluated via SOP and connection outage probability (COP).
Fountain codes (FCs) or rateless codes [42,43] have gained much attention due to low decoding complexity. In contrast to typical fixed-rate codes, a FC transmitter can generate a limitless stream of fountain encoded packets from a finite number of the source packets. The encoded packets are then continuously sent to the desired receivers until each receiver can receive a sufficient number of the encoded packets for recovering the original data (regardless of which encoded packets are received). Therefore, FCs do not require knowledge of CSI, automatically adapt the channel conditions, and avoid the feedback channel. In [44], the authors proposed a FCs based cooperative relaying network, where energy consumption and transmission time significantly decrease due to mutual information accumulation. Published work [45] presented the advantage of applying FCs on wireless broadcast systems, in terms of transmission efficiency. In [46], a rateless code based spectrum access model in overlay CRNs was proposed. In the scheme proposed in [46], the secondary transmitters help a primary transmitter forward the fountain packets to a primary receiver, and then they can find opportunities to access licensed bands. The authors of [47] considered cooperative relay networks using FCs and RF-EH, where the source and relay nodes use FCs, and hence, the destination can perform the mutual information accumulation and energy accumulation. However, due to broadcast of wireless channels, the eavesdroppers can also receive enough number of the encoded packets for intercepting the original data. Hence, security in FCs based PLS system becomes a critical issue.
1.1. Related Work
Until now, there have been many published works concerned with performance analysis of diversity based secure communication using MIMO techniques, e.g., [7,8,9,10,11,12,13,14,15,16], and cooperative relaying methods [17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41]. However, to the best of our knowledge, several existing literatures studying secure transmission protocols using FCs have been reported. The basic idea of the FC-based PLS protocols is that when the intended destination can receive enough encoded packets before the eavesdroppers, the data transmission is successful and secure [48]. In [49], the authors evaluated the intercept probability which is defined as the probability that the eavesdropper can intercept enough coded packets to recover the original data. In [50], the authors proposed a multicast model to attain the wireless security for Internet of Things (IoT) networks using FCs. In [51], the secrecy performance of the FCs aided PLS protocol is significantly enhanced with the TAS and CJ techniques when the transceiver hardware of the destination and the eavesdropper are not perfect. Reference [52] considered a FCs aided relaying network using the CJ method to enhance the transmission secrecy, in terms of quality-of-service violating probability (QVP). In [53], the authors proposed various relay selection and jammer selection methods to enhance both outage performance and IP performance for dual-hop multiple-relay decode-and-forward networks. The authors of [54] proposed a FCs based transmission protocol to secure the source-destination communication. Moreover, a new FC construction method, which opportunistically adapts the coding strategy following outage prediction, is proposed in [54]. In [55], the authors analyzed the security-reliability trade-off for multi-hop low-energy adaptive clustering hierarchy (LEACH) networks employing FCs and CJ. The authors of [56] proposed a rateless codes-based communication protocol to provide security for wireless systems. In this protocol, a source uses the TAS technique to transmit the encoded packets to a destination, and a cooperative jammer harvests energy from the RF signals of the source and interference sources to generate jamming noises on an eavesdropper.
1.2. Motivations and Contributions
In this paper, we propose a MIMO secure communication system exploiting FCs. In the proposed protocol, a multi-antenna source uses TAS to transmit the encoded packets to a multi-antenna destination in presence of a multi-antenna eavesdropper. The receivers including the destination and the eavesdropper can use the MRC or SC combiner to enhance the reliability of the decoding operation. When a required number of the encoded packets can be obtained by the destination, it sends a feedback to the source for stopping the transmission. Therefore, the security is guaranteed as the eavesdropper cannot sufficiently intercept the encoded packets. The main motivations and contributions of this paper can be summarized as follows:
- In contrast to [48,49,50,54], in the proposed protocol, all the nodes including the source, the destination and eavesdropper are equipped with multiple antennas and use the MRC or SC technique to combine the received signals. Although the source nodes in [51,56] have multi-antenna and employ TAS to transmit the encoded packets, the destinations in [51,56] are only single-antenna nodes. Moreover, References [52,53,55] considered single-input-single-output (SISO) relaying protocols where all the terminals are deployed with a single antenna.
- In contrast to [48,49,50,51,52,53,54,55,56], the source in the proposed protocol can employ NOMA to transmit two packets to the destination in each time slot to reduce the number of time slots used. Moreover, reducing the number of time slots also means reducing the delay time and transmit power, which are important metrics of the wireless systems.
- We compare the performance of the proposed protocols in two cases where the source uses NOMA (named NOMA) and does not use NOMA (named Wo-NOMA), in terms of average number of time slots (TS) and intercept probability (IP). The results shows that the FCs based secure transmission protocol exploiting NOMA can decrease both TS and IP, as compared with the corresponding protocol without using NOMA.
- We derive exact expressions of TS and IP for the NOMA and Wo-NOMA protocols over Rayleigh fading channels and realize computer simulations to verify.
The remainder of this paper is organized as follows. The system model of NOMA and Wo-NOMA is described in Section 2. In Section 3, the TS and IP performances of NOMA and Wo-NOMA over Rayleigh fading channel are evaluated. The simulation and theoretical results are shown in Section 4. Finally, this paper is concluded in Section 5.
2. System Model
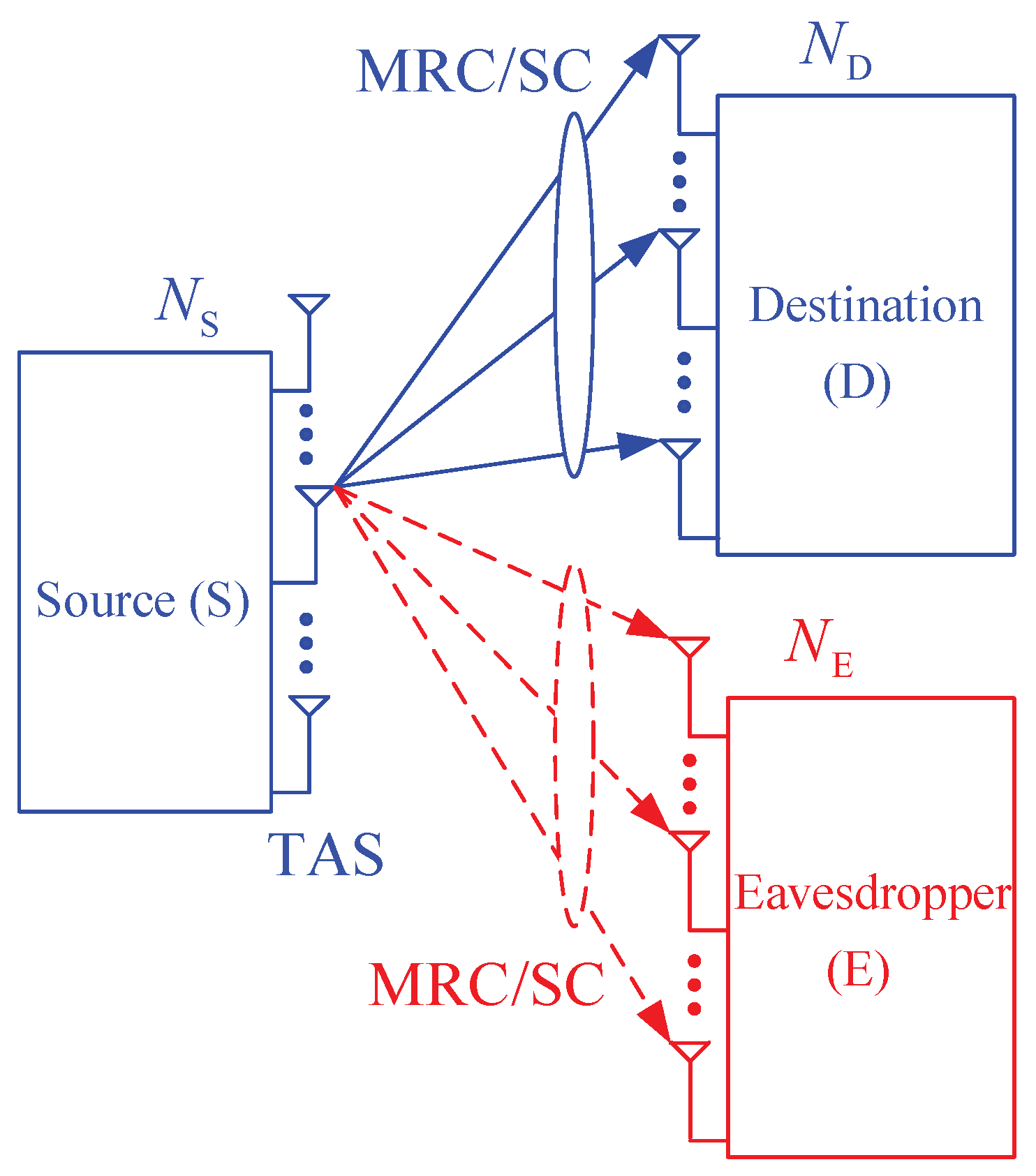
Figure 1 presents system model of the proposed protocol, where a source node (S) equipped with antennas uses FCs to transmit its data to an -antenna destination (D), in presence of an -antenna passive eavesdropper (E). The original data of the source is divided into L packets which are then encoded by the FC encoder. At each time slot, the source selects its best antenna to transmit two (or one) encoded packets to the destination, which are also received by the eavesdropper. Then, the D and E nodes attempt to decode the encoded packets. To recover the original data, the destination and eavesdropper have to correctly receive at least encoded packets, where , and is the decoding overhead which depends on concrete code design [48,49,50,51,52,53,54,55,56]. After receiving a sufficient number of the encoded packets for reconstructing the original data, the destination sends an ACK message to inform the source, and then the source stops its transmission. In this case, if the eavesdropper successfully receives at least encoded packets, it can also recover the original data, and hence the source data is intercepted.
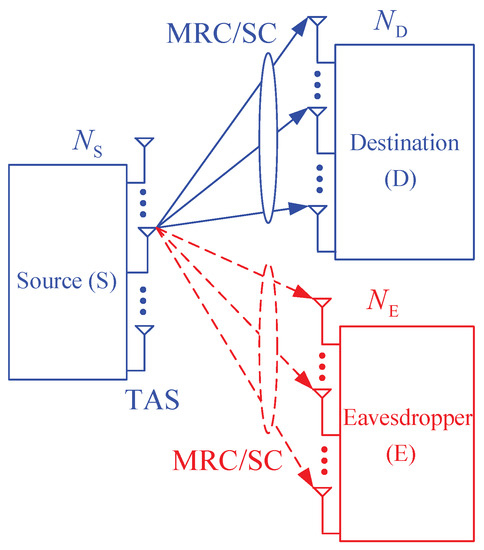
Figure 1.
System model of the proposed scheme.
Next, we introduce notations and assumptions used through this paper. Let us denote and as channel coefficients between the m-th antenna of the source and n-th antenna of the destination and between the m-th antenna of the source and t-th antenna of the eavesdropper, respectively, where , , . We assume that all the channels are independent and identically distributed (i.i.d.), block and flat Rayleigh fading, where they keep constant in one time slot but independently changes at other time slots. Therefore, the channel gains and are exponential random variables (RVs) whose cumulative distribution functions (CDFs) are expressed respectively as [57]:
where and , and is an expected operator.
Therefore, probability density function (PDF) of and can be given respectively as
Let denote number of time slots used by the source to transmit the encoded packets to the destination. We denote and as number of the encoded packets that the destination and the eavesdropper can successfully receive, respectively.
Function gives the greatest integer less than or equal to x, and function gives the smallest integer equal to or greater than x.
2.1. Without Using NOMA (Wo-NOMA)
If the source does not use NOMA, at each time slot, it transmits one encoded packet to the destination. Assume that each encoded packet, e.g., p, includes U symbols, i.e., , where is a symbol of p, and . When the source uses the m-th antenna to transmit to the destination, the received signal at the n-th antenna of the destination is expressed as
where P is transmit power of all the antennas of the source, is additive white Gaussian noise (AWGN) at D. For ease of presentation and analysis, we assume that all the additive noises are modeled as Gaussian RVs with zero mean and variance of .
From (3), the instantaneous signal-to-noise ratio (SNR) of the link is given as
where is transmit SNR.
When the destination uses the SC technique, the SNR obtained at the output of the combiner can be formulated similarly to Equation (3) of [58] as
where b denotes index of the receive antenna at D used to decode , .
Then, the source selects its best antenna to maximize the instantaneous SNR of the data link (see [51]):
where a denotes index of the selected transmit antenna at the source.
For a fair comparison, the eavesdropper also uses the SC combiner for decoding p. Similar to (5), the obtained SNR of the eavesdropping link is computed as
where .
If the destination uses MRC, the combined signal at D can be given as
where is conjugate of the complex number .
From (9), the SNR obtained at D is calculated as
Then, the TAS technique is employed to provide the highest SNR for the data link, i.e.,
Similar to (10), the instantaneous SNR of the eavesdropping link is computed as
where a denotes index of the selected antenna at the source.
Remark 1.
Due to the block fading channel, the instantaneous SNRs of the symbols are the same for all u. Hence, in (7), (8), (11) and (12), we skip the index u as presenting SNRs of the data and eavesdropping channels. Next, we assume that the encoded packet p can be decoded successfully if the instantaneous SNRs received at the destination and the eavesdropper are higher than a predetermined threshold denoted by , which can be formulated respectively as
where and .
Then, the probabilities that D and E nodes cannot correctly be decoded the encoded packet p are given as and , respectively.
2.2. Using NOMA
To reduce the number of time slots used to transmit the encoded packets, the source can use NOMA to transmit two encoded packets, e.g., and , to the destination in one time slot. We can assume that and , where and are symbols of and , respectively, and . Indeed, the source linearly combines two signals and [36], i.e., , and it then sends to the destination, where and are power allocation coefficients with , . Similar to (3), the received signal at D can be expressed as
Follows the SIC principle, the destination first decodes by treating as noise. After successfully decoding , D removes the component including , i.e., , from . Then, the signal used to decode can be expressed as (see [36])
When the TAS/SC technique is employed, similar to (7), the obtained SNRs of the data link for decoding and can be expressed respectively as
Similarly, the eavesdropper E first decodes , and then performs SIC before decoding . With the SC combiner, the instantaneous SNRs of the eavesdropping channel used to decode and are given respectively as
In the case that the MRC technique is used, the combined signal at D can be given as
After canceling the components including from the signals received at all the antennas, the destination again uses MRC to decode using the following combined signal:
Since the source uses TAS to optimize quality of the data link, the obtained SNRs used to decode and can be calculated respectively as
Similarly, for the eavesdropping channel, the instantaneous SNRs, with respect to and , can be formulated respectively as
where the source selects the a-th antenna to transmit data to the destination.
Remark 2.
To further decrease the number of time slots used for the transmission, the source can send more than two encoded packets to the destination at each time slot. However, when more signals are combined by the source, the implementation is more complex. Moreover, the fraction of the transmit power allocated to the signals is lower, which can degrade the system performance. For example, let us consider in (17) which can be approximated as
It is obvious from (24) that to obtain high SNR , should be much higher than , (or is small). For another example, if the source combines 3 signals using the coefficients , and , where > > and , similarly, we have >> >> , and hence the transmit power allocated to the third signal is very small.
Remark 3.
It is obvious that to obtain the packet , the destination must correctly decode the packet first. If the decoding status of is not successful, cannot also be decoded successfully. Therefore, the probabilities that in one time slot the destination cannot obtain any packet only obtains , and obtains and are formulated respectively as
where .
Similarly, the probabilities that the eavesdropper cannot obtain any packet only obtains , and obtains both and are formulated respectively as
where .
3. Performance Analysis
In this section, we derive exact expressions of average number of time slots (TS) and intercept probability (IP) of the proposed protocols. At first, the probabilities and () are calculated.
3.1. Derivation of and
- Case 1: The SC combiner is used by D and E
- Case 2: The MRC combiner is used by D and E
Using CDF of sum of identical and independent exponential RVs [59], we can obtain
Similarly, we can calculate the probability in this case as follows:
3.2. Derivation of and
- Case 1: The SC combiner is used by D and E
Remark 4.
As mentioned in Remark 2, should be much higher than so that the obtained SNR is high enough. Therefore, it can be assumed that , which yields the following result: . Then, the probability is calculated as
Next, we can calculate and respectively as
Similarly, we can calculate , , and , respectively as
- Case 2: The MRC combiner is used by D and E
In this case, it is straightforward to obtain the following results:
3.3. Average Number of Time Slots (TS)
3.3.1. Without Using NOMA (Wo-NOMA)
The average number of time slots of the Wo-NOMA protocol can be formulated as
where is the probability that the destination obtains encoded packets after time slots, which follows a negative binomial distribution (see Equation (9) of [60]):
and denotes the binomial coefficient:
3.3.2. Using NOMA
In this protocol, we formulate the average number of time slots used by the source as
where is the probability that the destination can obtain or encoded packets after time slots.
Let us denote and as the number of time slots that the destination correctly receives one encoded packet and two encoded packets, respectively. Now, to calculate , we consider three cases as follows:
- Case 1: After time slots, the destination obtains encoded packets, and at the last time slot, it obtains two encoded packets.
In this case, after the transmission is terminated, the destination has encoded packets, i.e., and . Moreover, the probability of Case 1 can be calculated as follows:
where , .
- Case 2: After time slots, the destination obtains encoded packets, and at the last time slot, it only obtains one encoded packet.
In Case 2, we also have and . Then, the probability of this event is computed as
where .
- Case 3: After time slots, the destination obtains encoded packets, and at the last time slot, it obtains two encoded packets.
In this case, the destination can successfully receive encoded packets after time slots: . Therefore, the probability that this event occurs can be calculated exactly as
where , .
Then, from (42), we can write the average number of time slots used in the NOMA protocol as follows:
Remark 5.
From (41) and (46), we can observe that when the transmit SNR is high enough, i.e., , the values of TS in the Wo-NOMA and NOMA protocols converge to and , respectively. It is due to the fact that at high Δ regimes, all of the encoded packet(s) can be correctly received by the destination. Therefore, by using NOMA, the proposed protocol can reduce a half of time slots used for transmitting the encoded packets.
3.4. Intercept Probability (IP)
In this subsection, we calculate the intercept probability of the proposed protocols with and without using NOMA.
3.4.1. Without Using NOMA (Wo-NOMA)
At first, we see that the source data is intercepted if the eavesdropper can sufficiently obtain the number of the encoded packets for recovering the original data before or at the same time with the destination. Mathematically speaking, we can write
Equation (47) implies that the eavesdropper can obtain encoded packets after time slots, while the destination can sufficiently receive or not. In (47), is calculated as in (40), and similarly, is also given as
Considering in (47); this is the probability that the destination cannot sufficiently receive the number of the encoded packets for the data recovery after time slots and is calculated as
Remark 6.
When the eavesdropper obtains encoded packets, it does not decode the encoded packets any more, regardless of whether the source still transmits the encoded packets to the destination. This also means that after having encoded packets, it stops overhearing the data transmission and starts the data recovery.
3.4.2. Using NOMA
In (52), we note that , , and are obtained by replacing in (43)–(45) by . For , , and , with the same method as deriving , , , we can obtain
where and are the number of time slots that the eavesdropper correctly receives one encoded packet and two encoded packets, respectively.
Considering ; this is probability that the destination cannot obtain encoded packets after time slots, and is computed as
Remark 7.
Equations (50) and (55) exactly express the IP performance of the Wo-NOMA and NOMA protocols. To obtain the IP values, we truncate the infinite series by 500 first terms. Moreover, because (50) and (55) are in closed-form formulas, which can be used efficiently in designing and optimizing the networks.
4. Simulation Results
In this section, we present simulation results using the Monte-Carlo approach to verify the theoretical results obtained in Section 3 as well as to compare the performances of the proposed protocols with and without using NOMA, in terms of TS and IP. All of the simulation and theoretical results are drawn by MATLAB R2014a software (MathWorks, Natick, MA, USA). For Monte-Carlo simulations, we perform trials in which the Rayleigh channel coefficients of the X-Y links are generated by , where , (or ) is the parameter of the X-Y channel, and is a MATLAB function which generates Gaussian distributed pseudo-random numbers with zero-mean and unit variance. Then, using the given system parameters (we summarize the system parameters and their value ranges in Table 1), we obtain the simulation results of TS and IP. For the theoretical results, the expressions of TS and IP derived in the previous section are used to present them. As mentioned in Remark 7, the infinite series in the derived formulas are truncated by 500 first terms.

Table 1.
System parameters.
4.1. Average Number of Time Slots (TS)
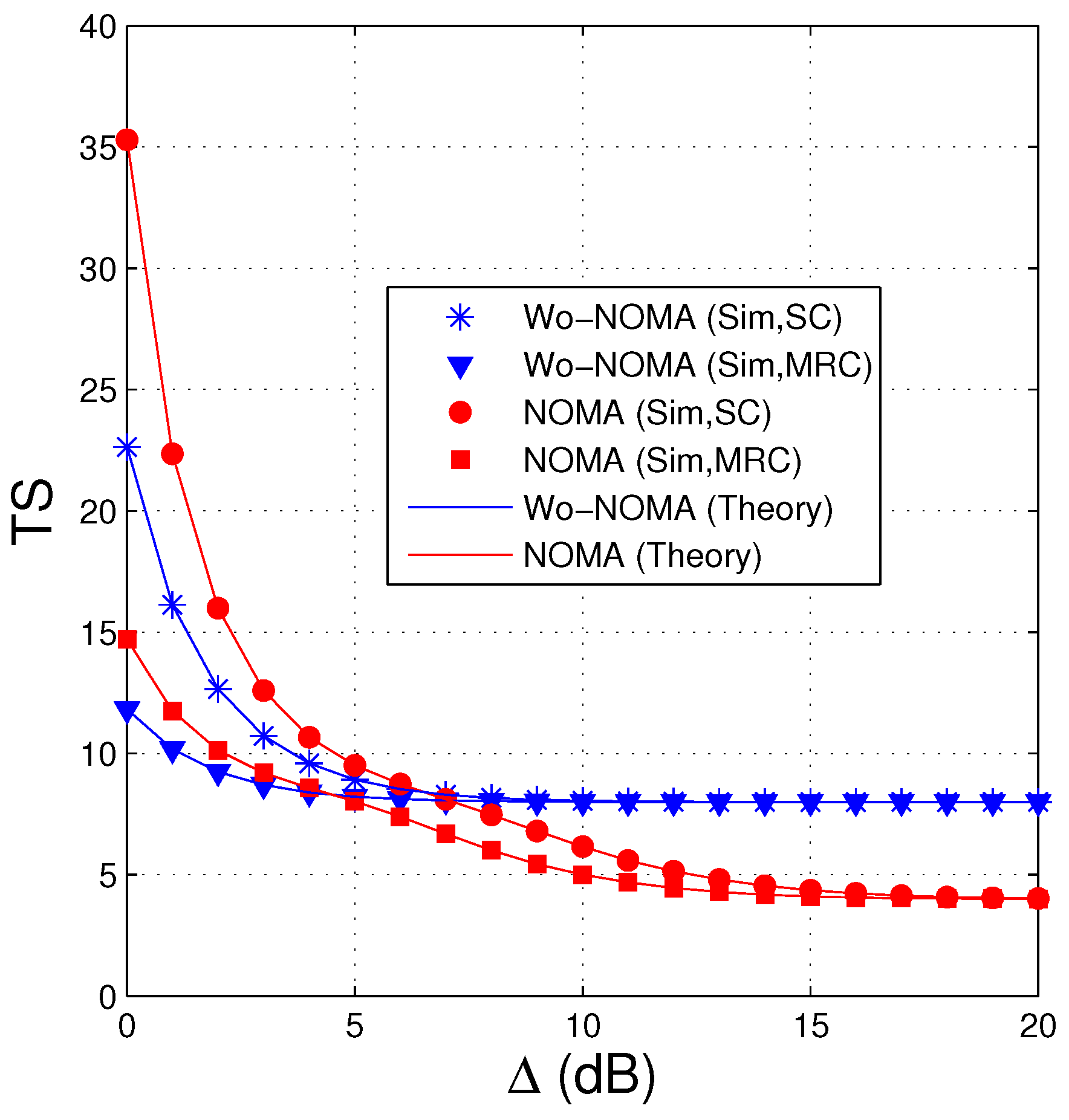
In Figure 2, we present average number of time slots that the source uses to transmit the encoded packets to the destination as a function of the transmit SNR () in dB. In this figure, the number of antennas at the source () and the destination () is 1 and 3, respectively, the parameter of the data link () is fixed by 2, the required number of the encoded packets for successfully recovering the original data () is set by 8, and the threshold is set to 1. As mentioned in Remark 4, the value of has to satisfy the condition: or , hence we can select (). We can see from Figure 2 that the TS values of the Wo-NOMA and NOMA protocols decrease with the increasing of and are lower when the destination is equipped with the MRC combiner. However, at high regions, the TS values of the Wo-NOMA protocol converge to , while those of the NOMA protocol reach to . It is due to the fact that at high transmit SNR, the destination in the NOMA scheme can obtain two encoded packets at each time slot, and hence the source only uses time slots for the data transmission. However, we can observe that the NOMA protocol does not perform well at low values when it uses more time slots than the Wo-NOMA protocol. It is worth noting that the simulation results (Sim) match very well with the theoretical ones (Theory), which verifies our derivations.
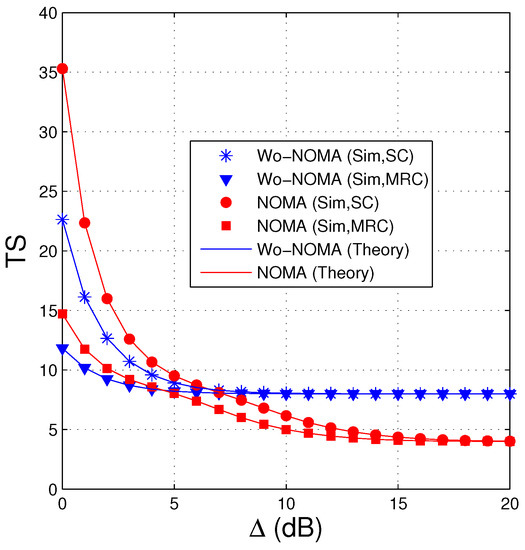
Figure 2.
Average number of time slots as a function of (dB) when , , , , , .
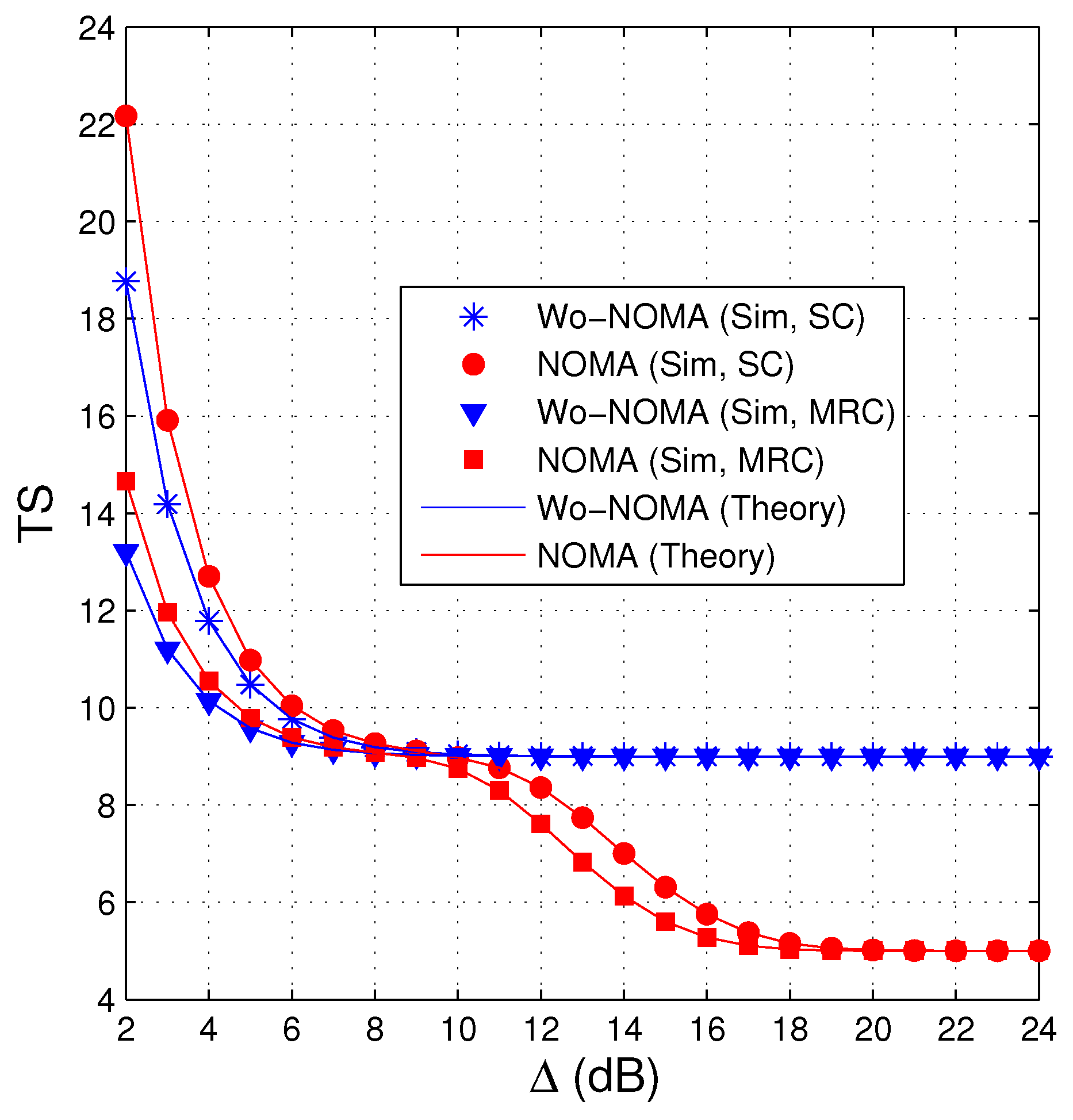
Figure 3 shows similar results to Figure 2, i.e., the performance of the NOMA protocol is better than that of the Wo-NOMA protocol at medium and high transmit SNRs. We also see from Figure 3 that the TS values of Wo-NOMA and NOMA at high regimes converge to and , respectively. In addition, as shown in Figure 2 and Figure 3, the TS performance of Wo-NOMA more rapidly converges than that of NOMA. Again, the simulation results validate the correction of the theoretical ones.
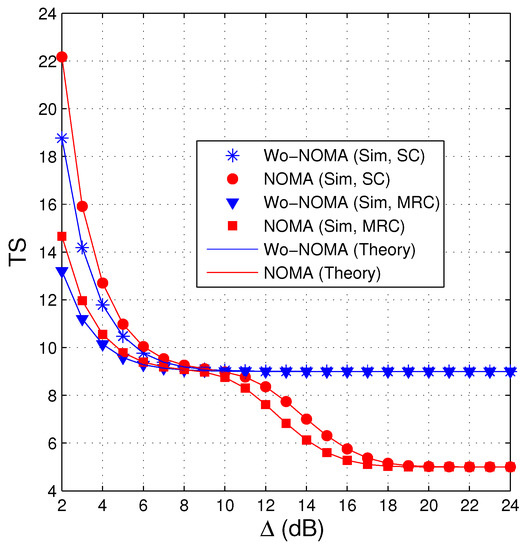
Figure 3.
Average number of time slots as a function of (dB) when , , , , , .
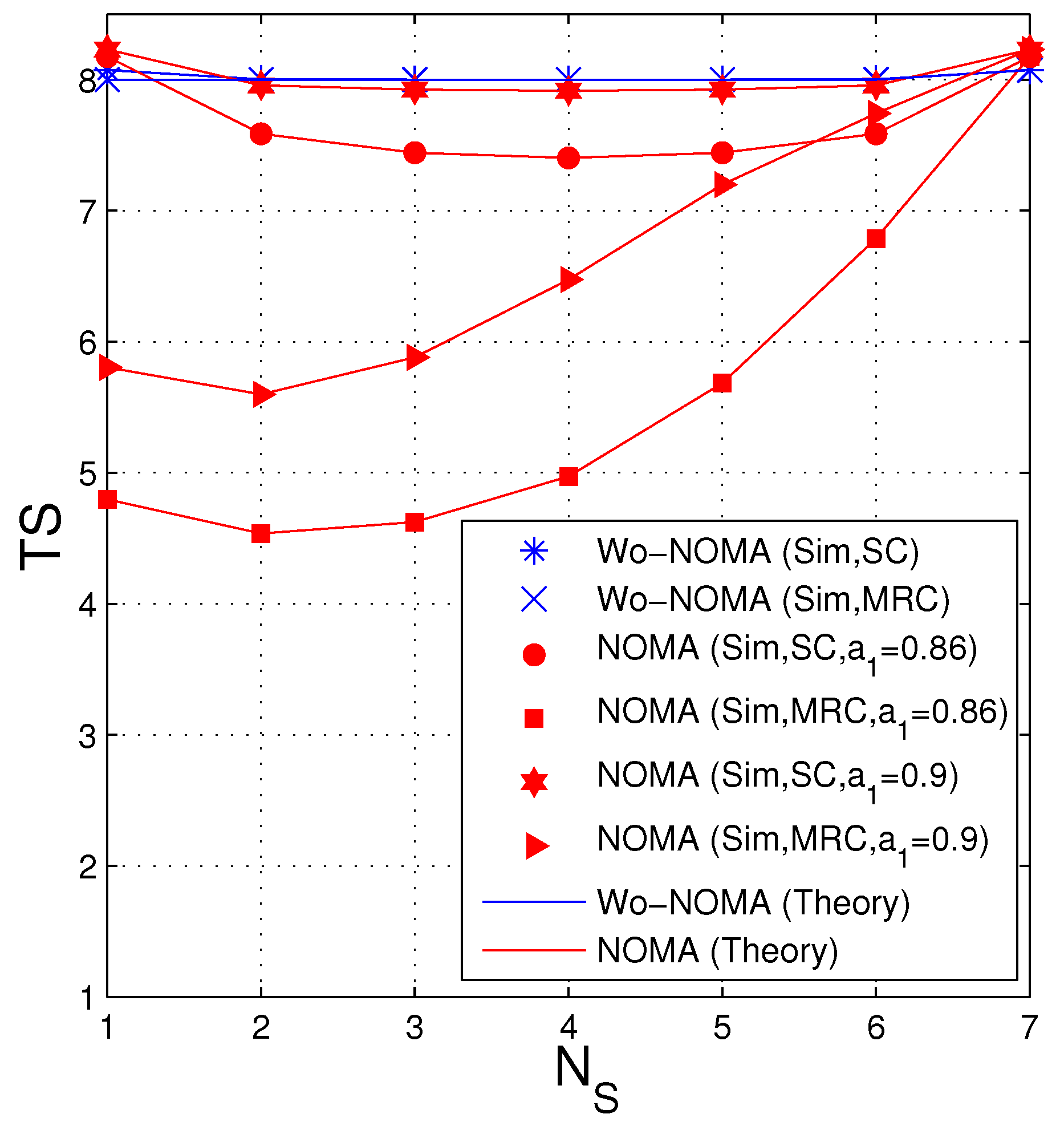
In Figure 4, we fix the total number of antennas at the source and the destination, i.e., , and present TS as a function of . In this figure, the Wo-NOMA protocol almost uses 8 time slots for transmitting the encoded packets, for all . In the NOMA protocol, the average number of time slots significantly varies as changing from 1 to 7. We can see that with the SC technique, the TS performance of the NOMA protocol is same when the number of antennas at the source is and . Moreover, in this case, the value of TS is lowest when . However, in the case where the destination is equipped with MRC, the optimal value of is 2 (), and the TS performance is worst as . It is due to the fact that the MRC combiner is better than the SC one, and hence more antennas should be allocated to the destination to optimize the TS performance. Finally, it is seen that the TS values of the NOMA scheme with () are lower than those with (). This can be explained as follows: Reducing means that the transmit power of the second signal is lower, which hence decreases the probability that the destination can obtain two encoded packets in each time slot (see in (35) and (38)), as well as increases the average number of the time slots used.
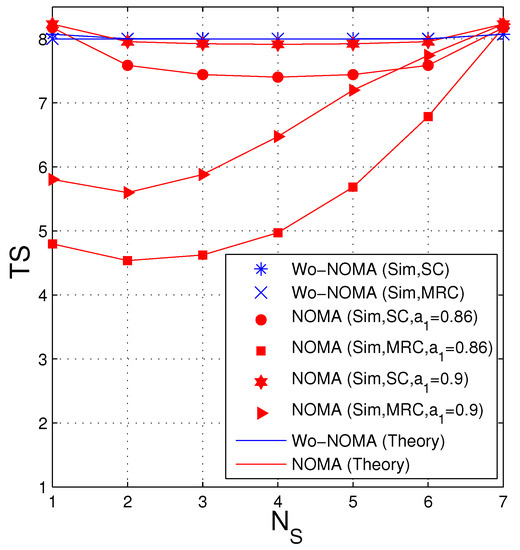
Figure 4.
Average number of time slots as a function of when dB, , , , .
4.2. Intercept Probability (IP)
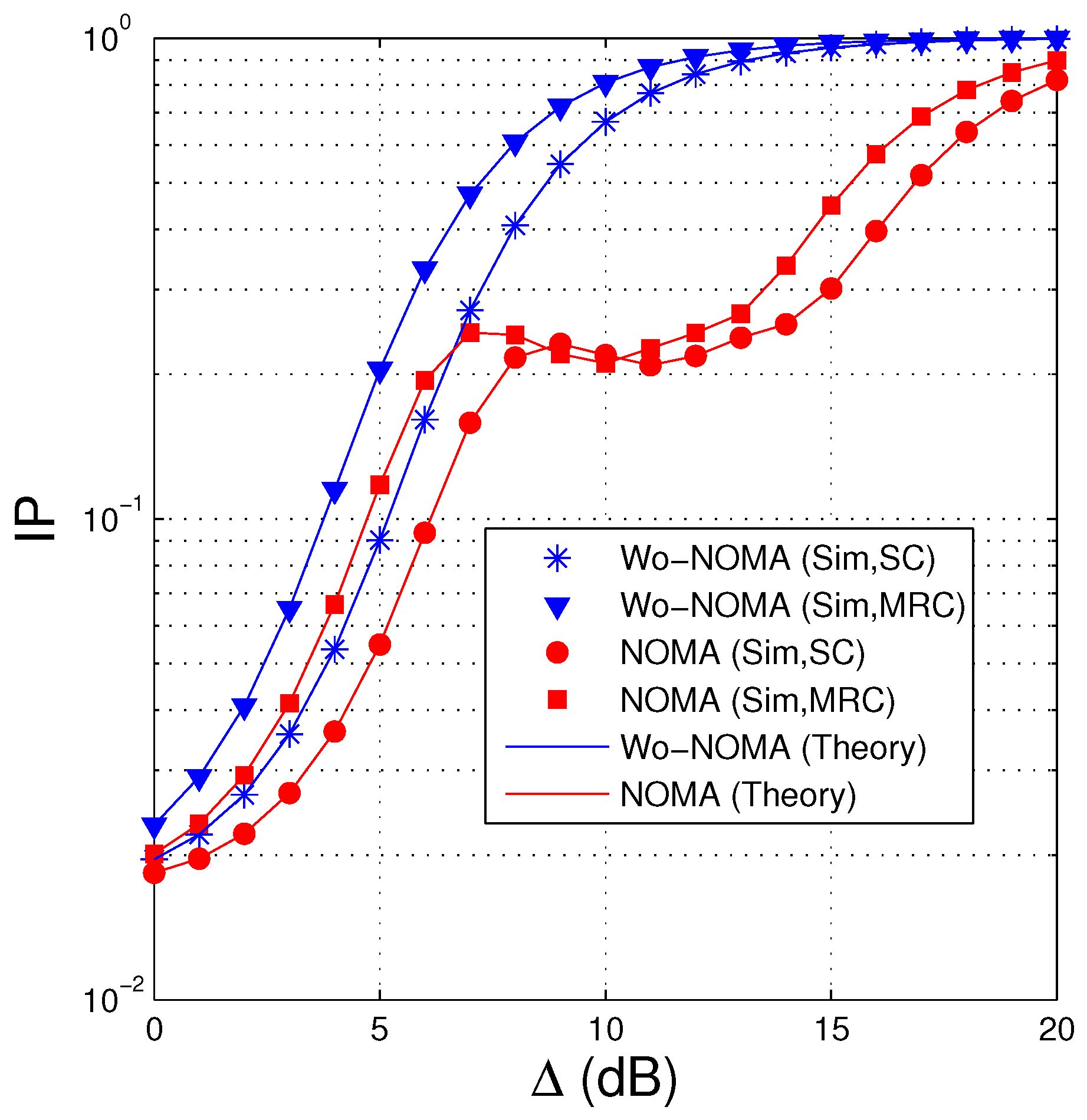
In Figure 5, we present IP of the proposed protocols as a function of in dB. We can see that IP of the Wo-NOMA and NOMA protocols almost increases as increasing the transmit SNR. It is due to the fact that when the transmit power of the source is high, SNR of the eavesdropping link also increases, which enhances the intercept probability. However, in the NOMA scheme, when belongs to interval of (8 dB, 10 dB), IP slightly decreases with the increasing of , and hence, there exists a high performance gap between Wo-NOMA and NOMA in this interval. Because the intercept probability at the eavesdropper depends on the decoding at the destination and the interference between the signals, the changing of IP in the NOMA protocol, with respect to , is more complex. Indeed, from (17), (18), (22) and (23), it is observed that as increases, the interference from to also increases, which leads to a slow increase of SNR of obtained at the D and E nodes. Because D and E must decode first, the slow increase of SNRs can make IP slightly increase. However, when is high enough, all the encoded packets can be correctly obtained by D and E. In this case, D and E can obtain encoded packets at the same time, and hence the IP value converges to 1, as shown in Figure 5. Next, we can observe that when the destination and the eavesdropper use MRC, the IP values of the proposed protocols are higher. It is because the intercept possibility of the eavesdropper is better when it is equipped with MRC. Finally, it is seen that the NOMA protocol obtains better IP performance compared with the Wo-NOMA one.
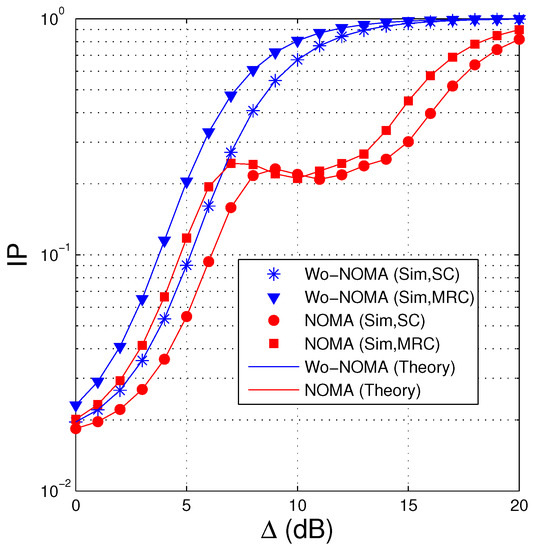
Figure 5.
Intercept probability as a function of (dB) when , , , , , , , .
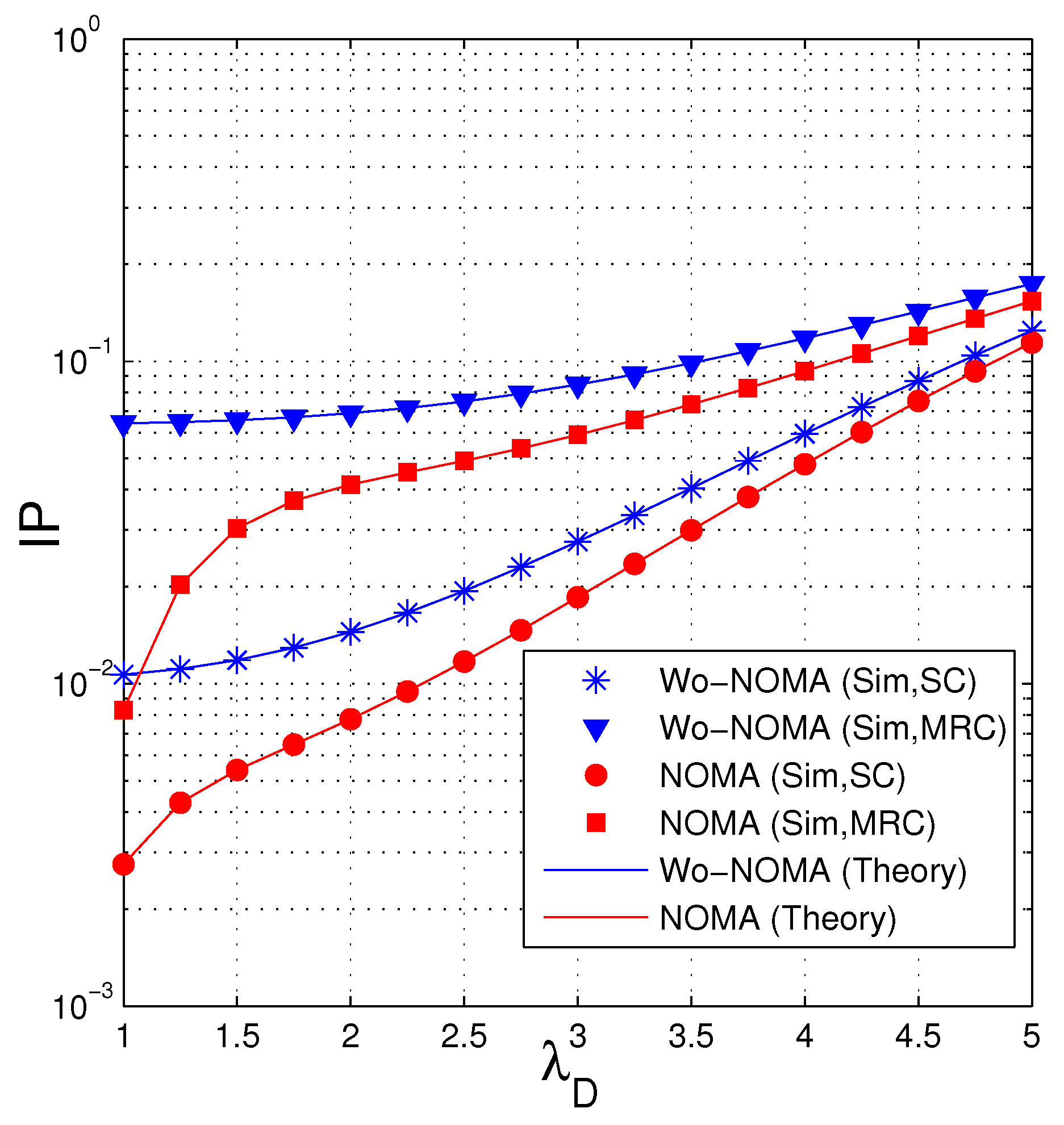
In Figure 6, we investigate the impact of the parameter of the data link () on the IP performance. As we can see, IP of the proposed protocols increases as increases. It is due to the fact that when the quality of the data channel is worse ( is high), the eavesdropper has more opportunity to obtain sufficient number of the encoded packets for recovering the original data. We also see that the IP performance of the Wo-NOMA protocol is worse than that of the NOMA protocol. Similar to Figure 5, the intercept probability of the eavesdropper increases when it uses MRC.
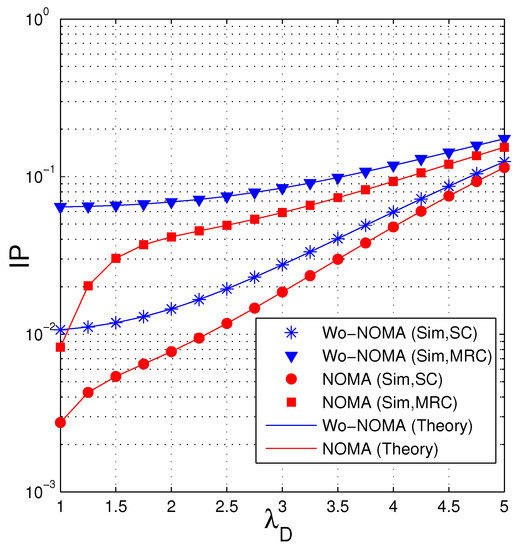
Figure 6.
Intercept probability as a function of when (dB), , , , , , , .
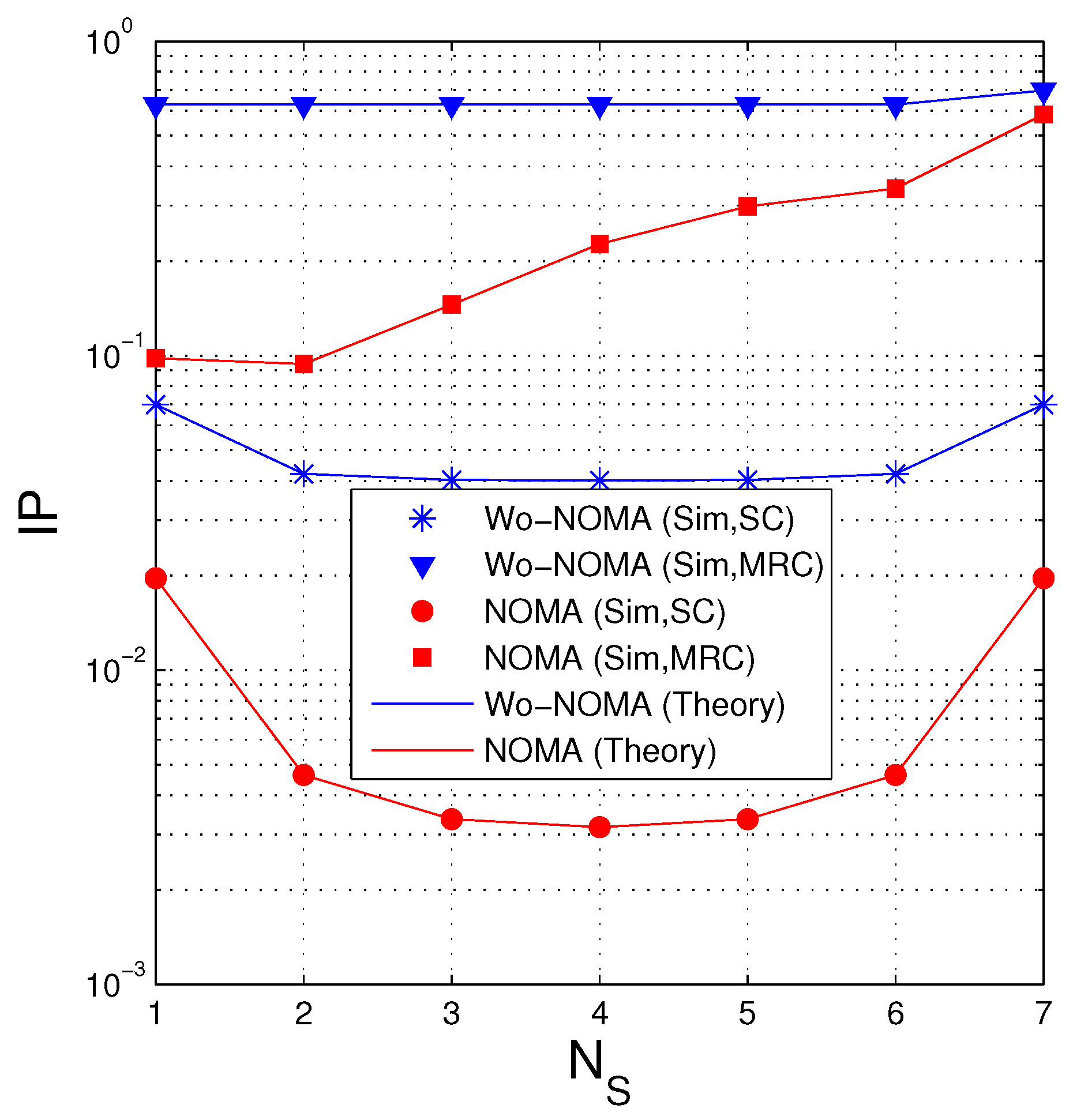
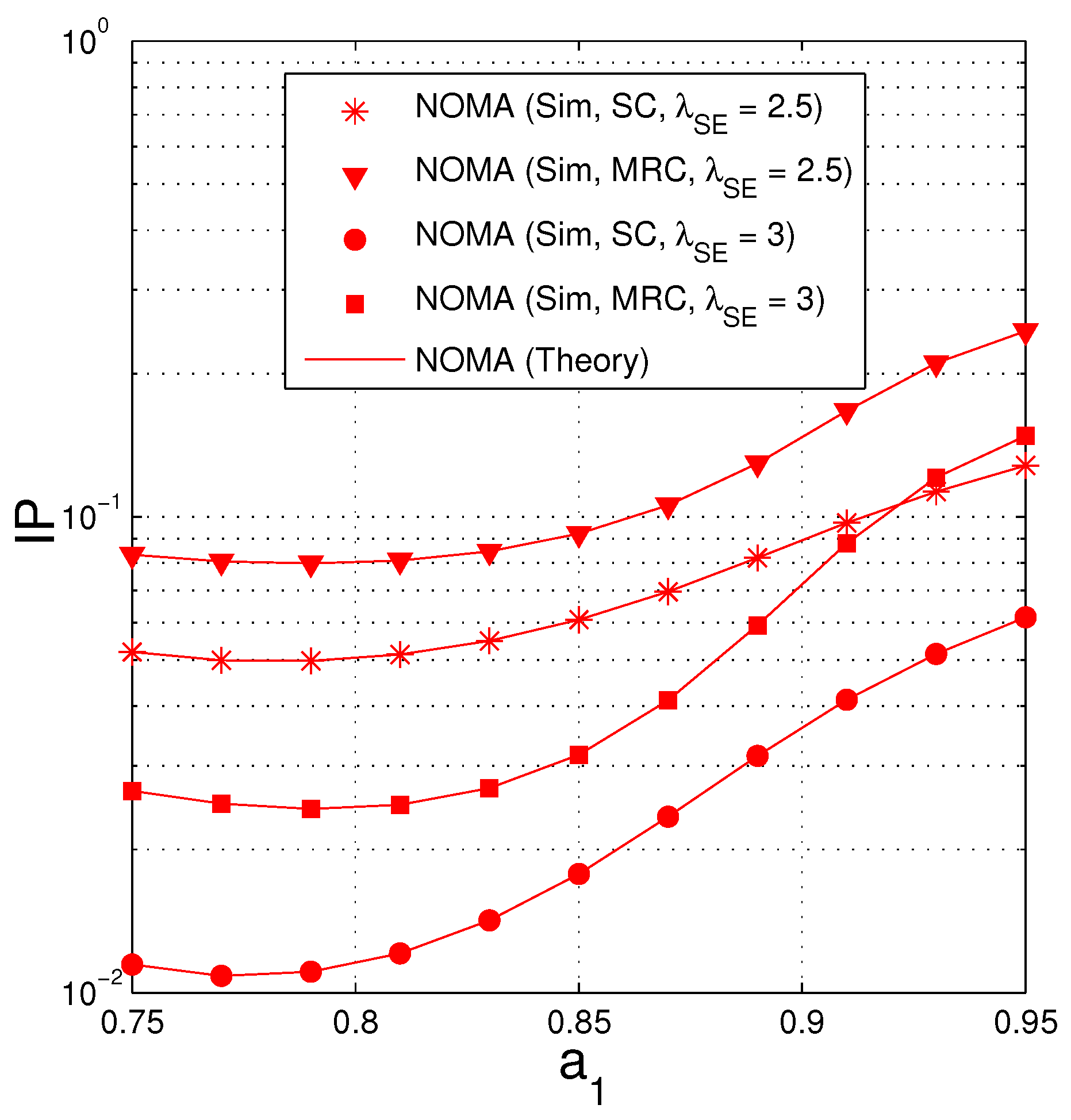
Figure 7 presents IP as a function of when . Similar to Figure 4, in the case where the D and E nodes use SC, the IP value is lowest when , and when MRC is employed, the optimal value of is 2. It is also seen that the IP performance of the Wo-NOMA protocol slightly varies with the changing of but that of the NOMA protocol significantly varies. Again, the NOMA protocol obtains better performance compared with the Wo-NOMA one. Moreover, we can see from this figure that when the MRC technique is used by the eavesdropper, the IP performance is not good. Indeed, if the desired value of IP is (below) 0.1, it is seen that both Wo-NOMA and NOMA cannot be practically implemented. In this case, to reduce IP, the source can reduce its transmit power or appropriately design the systems parameters and (see Figure 8 and Figure 9 below).
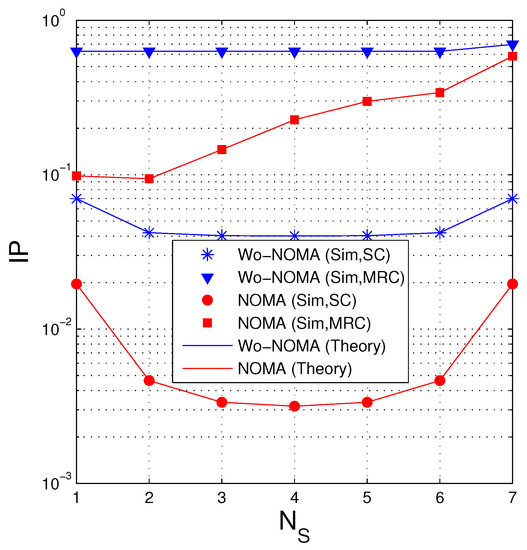
Figure 7.
Intercept probability as a function of when (dB), , , , , , , .
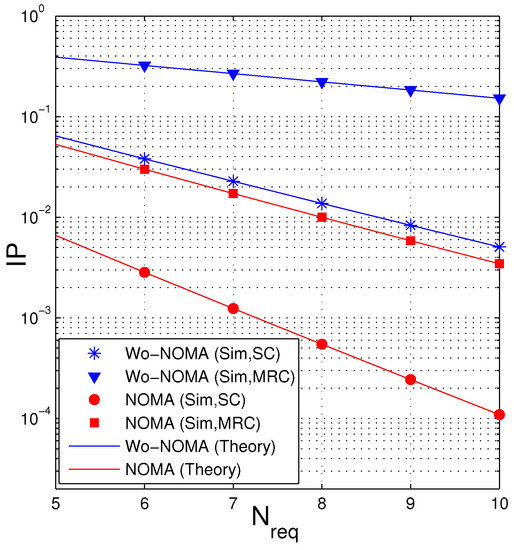
Figure 8.
Intercept probability as a function of when (dB), , , , , , , .
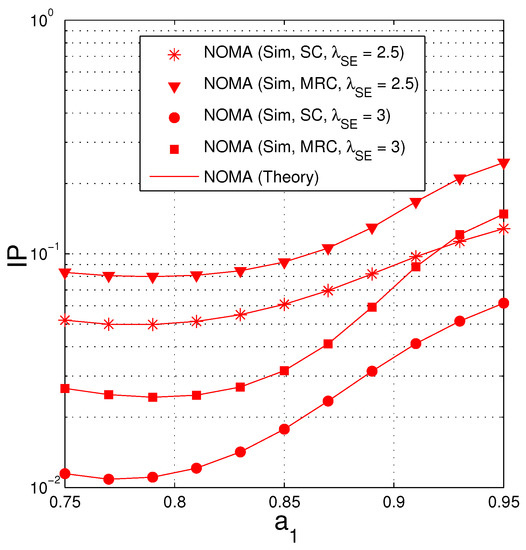
Figure 9.
Intercept probability as a function of when (dB), , , , , , .
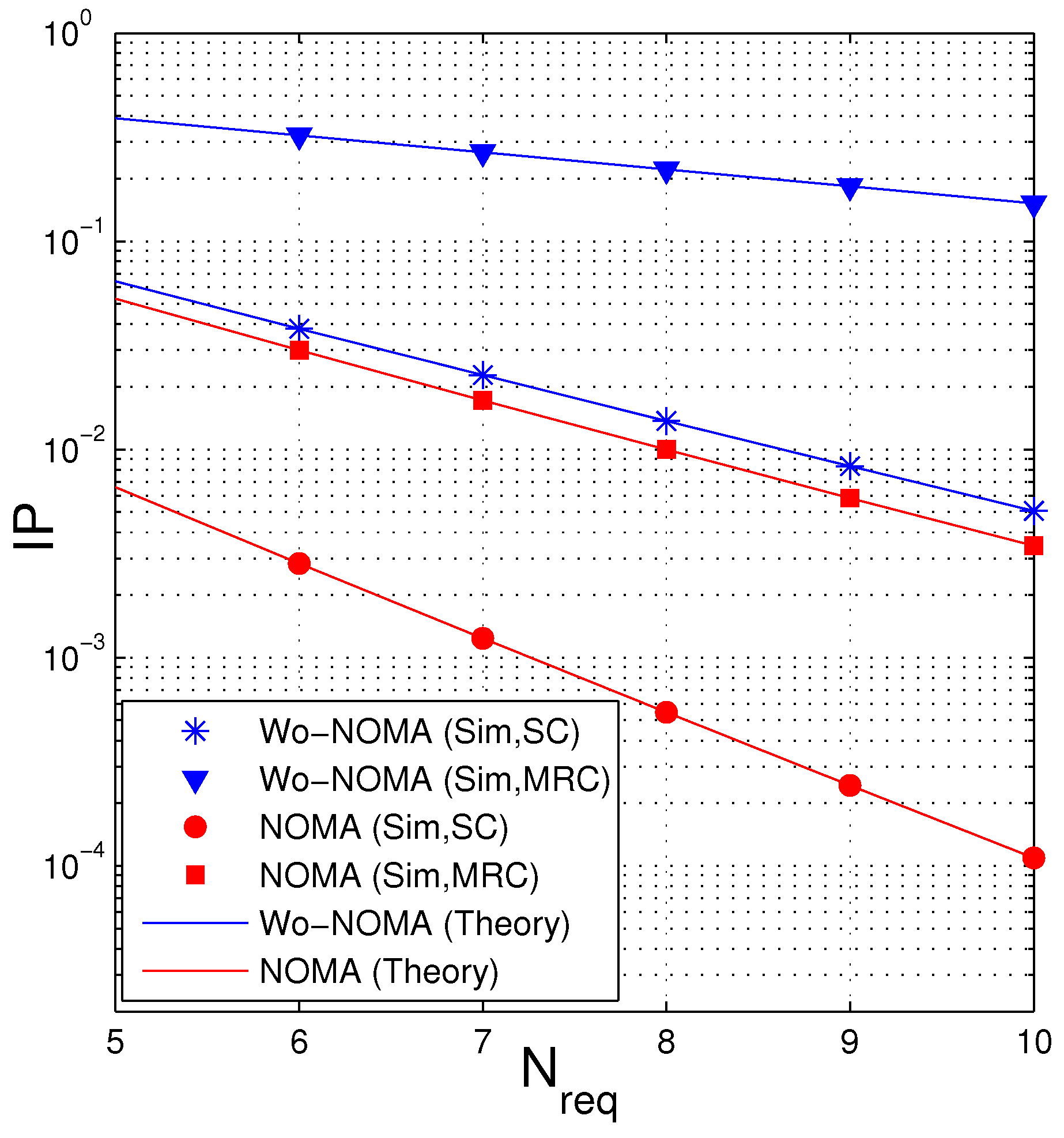
In Figure 8, we present IP of the proposed protocols as a function of . For ease of observation, we only change from 5 to 10. We can see that the values of IP decrease as increases. It is due to the fact that as is higher, the probability that the destination can obtain encoded packets before the eavesdropper increases, which hence reduces the intercept probability at the eavesdropper. The obtained results in this figure can be used to design the considered network. For example, we assume that the D and E nodes are equipped with the MRC combiner, and hence Wo-NOMA cannot be used due to high IP value (higher than 0.1). Instead of Wo-NOMA, the NOMA scheme can be used to obtain higher security for the source data. For another example, assume that the system cannot use NOMA due to limited hardware and processing capacity. In this case, the source in the Wo-NOMA protocol can increase the number of to reduce IP. However, we note that increasing does increase the number of time slots and the delay time.
Figure 9 investigates the impact of the fractions of the transmit power (, ) on the IP performance of the NOMA protocol by changing , and presenting IP as a function of . Again, from Remark 4, the value of must be designed so that . Hence, in this figure, we can select the interval of as . As we can see, there exist optimal values of at which the IP value is lowest. It is also observed that the IP values are higher as the decreases because the average channel gain of the eavesdropping is higher.
5. Conclusions
This paper showed that applying the NOMA technique into FCs secure communication protocols not only reduces the number of time slots used but also enhances security. Particularly, the NOMA protocol can reduce by half the number of time slots compared with the Wo-NOMA one. For the secure transmission, IP of the eavesdropper significantly decreases as the source uses NOMA to transmit two encoded packets to the destination at each time slot. For performance illustration, we derived exact expressions of TS and IP, which were validated by computer simulations. The results showed that the performance for the Wo-NOMA and NOMA protocols can be significantly enhanced by increasing or optimally designing the number of antennas at the source and the destination, appropriately selecting the faction of transmit power allocated to the NOMA signals and increasing the number of the encoded packets required for the data recovery.
Author Contributions
The main contributions of D.T.H. and T.T.D. were to create the main ideas and execute performance evaluation by simulations, while the main contributions of P.T.T., D.Q.T., and T.H. were to discuss, create, and advise in regard to the main ideas and performance evaluations.
Funding
This research is funded by Posts and Telecommunications Institute of Technology (PTIT) under grant number 11-HV-2019-RD_VT2.
Acknowledgments
This work was supported by the Domestic PhD Scholarship Programme of Vingroup Innovation Foundation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wyner, A.D. The Wire-tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast Channels with Confidential Messages. IEEE Trans. Inf. Theory 1978, 2, 339–348. [Google Scholar] [CrossRef]
- Liu, R.; Maric, I.; Spasojevic, P.; Yates, R.D. Discrete Memoryless Interference and Broadcast Channels with Conffdential Messages: Secrecy Rate Regions. IEEE Trans. Inf. Theory 2008, 2, 2493–2507. [Google Scholar] [CrossRef]
- Gopala, P.K.; Lai, L.; Gamal, H.E. On the Secrecy Capacity of Fading Channels. IEEE Trans. Inf. Theory 2008, 2, 4687–4698. [Google Scholar] [CrossRef]
- Zhang, J.; Duong, T.Q.; Woods, R.; Marshall, A. Securing Wireless Communications of the Internet of Things from the Physical Layer, An Overview. Entropy 2017, 19, 420. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Zhang, J.; Jorswieck, E.; Xiao, B.; Hu, A. Physical Layer Key Generation in 5G and Beyond Wireless Communications: Challenges and Opportunities. Entropy 2019, 21, 497. [Google Scholar] [CrossRef]
- Yang, N.; Yeoh, P.L.; Elkashlan, M.; Schober, R.; Collings, I.B. Transmit Antenna Selection for Security Enhancement in MIMO Wiretap Channels. IEEE Trans. Commun. 2013, 61, 144–154. [Google Scholar] [CrossRef]
- Yang, N.; Suraweera, H.A.; Collings, I.B.; Yuen, C. Physical Layer Security of TAS/MRC with Antenna Correlation. IEEE Trans. Inf. Forensics Secur. 2013, 8, 254–259. [Google Scholar] [CrossRef]
- Xiong, J.; Tang, Y.; Ma, D.; Xiao, P.; Wong, K.-K. Secrecy Performance Analysis for TAS-MRC System with Imperfect Feedback. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1617–1629. [Google Scholar] [CrossRef]
- Yang, L.; Hasna, M.O.; Ansari, I.S. Physical Layer Security for TAS/MRC Systems with and without Co-Channel Interference Over η − μ Fading Channels. IEEE Trans. Veh. Technol. 2018, 67, 12421–12426. [Google Scholar] [CrossRef]
- Zhao, H.; Tan, Y.; Pan, G.; Chen, Y.; Yang, N. Secrecy Outage on Transmit Antenna Selection/Maximal Ratio Combining in MIMO Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2016, 65, 10236–10242. [Google Scholar] [CrossRef]
- Li, M.; Huang, Y.; Yin, H.; Wang, Y.; Cai, C. Improving the Security and Spectrum Efficiency in Overlay Cognitive Full-Duplex Wireless Networks. IEEE Access 2019, 7, 68359–68372. [Google Scholar] [CrossRef]
- Pan, G.; Lei, H.; Deng, Y.; Fan, L.; Yang, J.; Chen, Y.; Ding, Z. On Secrecy Performance of MISO SWIPT Systems With TAS and Imperfect CSI. IEEE Commun. 2016, 64, 3831–3843. [Google Scholar] [CrossRef]
- Huang, Y.; Zhang, P.; Wu, Q.; Wang, J. Secrecy Performance of Wireless Powered Communication Networks With Multiple Eavesdroppers and Outdated CSI. IEEE Access 2018, 6, 33774–33788. [Google Scholar] [CrossRef]
- Lei, H.; Zhang, J.; Park, K.H.; Xu, P.; Ansari, I.S.; Pan, G.; Alomair, B.; Alouini, M.S. On Secure NOMA Systems with Transmit Antenna Selection Schemes. IEEE Access 2017, 5, 33774–33788. [Google Scholar] [CrossRef]
- Lei, H.; Zhang, J.; Park, K.H.; Xu, P.; Zhang, Z.; Pan, G.; Alouini, M.S. Secrecy Outage of Max–Min TAS Scheme in MIMO-NOMA Systems. IEEE Trans. Veh. Technol. 2018, 67, 6981–6990. [Google Scholar] [CrossRef]
- Krikidis, I. Opportunistic Relay Selection For Cooperative Networks With Secrecy Constraints. IET Commun. 2010, 4, 1787–1791. [Google Scholar] [CrossRef]
- Zhong, B.; Zhang, Z. Secure Full-Duplex Two-Way Relaying Networks With Optimal Relay Selection. IEEE Commun. Lett. 2017, 21, 1123–1126. [Google Scholar] [CrossRef]
- Kuhestani, A.; Mohammadi, A.; Mohammadi, M. Joint Relay Selection and Power Allocation in Large-Scale MIMO Systems with Untrusted Relays and Passive Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2018, 13, 341–355. [Google Scholar] [CrossRef]
- Mo, J.; Tao, M.; Liu, Y. Relay Placement for Physical Layer Security: A Secure Connection Perspective. IEEE Commun. Lett. 2012, 16, 878–881. [Google Scholar]
- Yao, J.; Liu, Y. Secrecy Rate Maximization With Outage Constraint in Multihop Relaying Networks. IEEE Commun. Lett. 2018, 22, 304–307. [Google Scholar] [CrossRef]
- Zhao, R.; Lin, H.; He, Y.C.; Chen, D.H.; Huang, Y.; Yang, L. Secrecy Performance of Transmit Antenna Selection for MIMO Relay Systems with Outdated CSI. IEEE Trans. Commun. 2018, 66, 546–559. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W.; Yang, W. Secrecy Outage Analysis of Buffer-Aided Cooperative MIMO Relaying Systems. IEEE Trans. Veh. Technol. 2018, 67, 2035–2048. [Google Scholar] [CrossRef]
- Tang, C.; Pan, G.; Li, T. Secrecy Outage Analysis of Underlay Cognitive Radio Unit Over Nakagami-m Fading Channels. IEEE Wirel. Commun. Lett. 2014, 3, 609–612. [Google Scholar] [CrossRef]
- Chakraborty, P.; Prakriya, S. Secrecy Outage Performance of a Cooperative Cognitive Relay Network. IEEE Commun. Lett. 2017, 21, 326–329. [Google Scholar] [CrossRef]
- Tin, P.T.; Hung, D.T.; Tan, N.N.; Duy, T.T.; Voznak, M. Secrecy Performance Enhancement for Underlay Cognitive Radio Networks Employing Cooperative Multi-hop Transmission With and Without Presence of Hardware Impairments. Entropy 2019, 21, 217. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, L.; Tran, T.D.; Elkashlan, M.; Duong, T.Q. Relay Selection for Security Enhancement in Cognitive Relay Networks. IEEE Wirel. Commun. Lett. 2015, 4, 46–49. [Google Scholar] [CrossRef]
- Jia, S.; Zhang, J.; Zhao, H.; Zhang, R. Relay Selection for Improved Security in Cognitive Relay Networks With Jamming. IEEE Wirel. Commun. Lett. 2017, 6, 662–665. [Google Scholar] [CrossRef]
- Sun, C.; Liu, K.; Zheng, D.; Ai, W. Secure Communication for Two-Way Relay Networks with Imperfect CSI. Entropy 2017, 19, 522. [Google Scholar] [CrossRef]
- Chang, S.; Li, J.; Fu, X.; Zhang, L. Energy Harvesting for Physical Layer Security in Cooperative Networks Based on Compressed Sensing. Entropy 2017, 19, 462. [Google Scholar] [CrossRef]
- Kalamkar, S.S.; Banerjee, A. Secure Communication via a Wireless Energy Harvesting Untrusted Relay. IEEE Trans. Veh. Technol. 2017, 66, 2199–2213. [Google Scholar] [CrossRef]
- Yin, C.; Nguyen, H.T.; Kundu, C.; Kaleem, Z.; Emiliano, G.P.; Duong, T.Q. Secure Energy Harvesting Relay Networks with Unreliable Backhaul Connections. IEEE Access 2018, 6, 12074–12084. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Vo, N.S.; Kundu, C. Physical Layer Security in Cooperative Energy Harvesting Networks with a Friendly Jammer. IEEE Wirel. Commun. Lett. 2017, 6, 174–177. [Google Scholar] [CrossRef]
- Zhang, G.; Xu, J.; Wu, Q.; Cui, M.; Li, X.; Lin, F. Wireless Powered Cooperative Jamming for Secure OFDM System. IEEE Trans. Veh. Technol. 2018, 2, 1331–1346. [Google Scholar] [CrossRef]
- Hu, G.; Cai, Y. Analysis and Optimization of Wireless-Powered Cooperative Jamming for Sensor Network Over Nakagami- m Fading Channels. IEEE Commun. Lett. 2019, 23, 926–929. [Google Scholar] [CrossRef]
- Yu, C.; Ko, H.L.; Peng, X.; Xie, W. Secrecy Outage Performance Analysis for Cooperative NOMA Over Nakagami-m Channel. IEEE Access 2019, 7, 79866–79876. [Google Scholar] [CrossRef]
- Wang, Z.; Peng, Z. Secrecy Performance Analysis of Relay Selection in Cooperative NOMA Systems. IEEE Access 2019, 7, 86274–86287. [Google Scholar] [CrossRef]
- Yuan, C.; Tao, X.; Li, N.; Ni, W.; Liu, R.P.; Zhang, P. Analysis on Secrecy Capacity of Cooperative Non-Orthogonal Multiple Access with Proactive Jamming. IEEE Trans. Veh. Technol. 2019, 68, 2682–2696. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Song, Y. Physical Layer Security in Cognitive Radio Inspired NOMA Network. IEEE J. Sel. Top. Sig. Process. 2019, 13, 700–714. [Google Scholar] [CrossRef]
- Huynh, T.P.; Son, P.N.; Voznak, M. Secrecy Performance of Underlay Cooperative Cognitive Network Using Non-Orthogonal Multiple Access with Opportunistic Relay Selection. Symmetry 2019, 11, 385. [Google Scholar] [CrossRef]
- Li, B.; Qi, X.; Huang, K.; Fei, Z.; Zhou, F.; Hu, R.Q. Security-Reliability Tradeoff Analysis for Cooperative NOMA in Cognitive Radio Networks. IEEE Trans. Commun. 2018, 67, 83–96. [Google Scholar] [CrossRef]
- MacKay, D. Fountain Codes. IEE Proc. Commun. 2005, 2, 1331–1346. [Google Scholar] [CrossRef]
- Castura, J.; Mao, Y. Rateless Coding over Fading Channels. IEEE Commun. Lett. 2006, 2, 46–48. [Google Scholar] [CrossRef]
- Molisch, A.F.; Mehta, N.B.; Yedidia, J.S.; Zhang, J. Performance of Fountain Codes in Collaborative Relay Networks. IEEE Trans. Wirel. Commun. 2007, 6, 4108–4119. [Google Scholar] [CrossRef]
- Nguyen, H.D.T.; Tran, L.N.; Hong, E.K. On Transmission Efficiency for Wireless Broadcast Using Network Coding and Fountain Codes. IEEE Commun. Lett. 2011, 2, 569–571. [Google Scholar] [CrossRef]
- Duy, T.T.; Kong, H.Y. Secondary Spectrum Access in Cognitive Radio Networks Using Rateless Codes over Rayleigh Fading Channels. Wirel. Pers. Commun. 2014, 2, 963–978. [Google Scholar] [CrossRef]
- Di, X.; Xiong, K.; Fan, P.; Yang, H.C. Simultaneous Wireless Information and Power Transfer in Cooperative Relay Networks With Rateless Codes. IEEE Trans. Veh. Technol. 2017, 66, 2981–2996. [Google Scholar] [CrossRef]
- Niu, H.; Iwai, M.; Sezaki, K.; Sun, L.; Du, Q. Exploiting Fountain Codes for Secure Wireless Delivery. IEEE Commun. Lett. 2014, 2, 777–780. [Google Scholar] [CrossRef]
- Khan, A.S.; Tassi, A.; Chatzigeorgiou, I. Rethinking the Intercept Probability of Random Linear Network Coding. IEEE Commun. Lett. 2015, 19, 1762–1765. [Google Scholar] [CrossRef]
- Du, Q.; Xu, Y.; Li, W.; Song, H. Security Enhancement for Multicast over Internet of Things by Dynamically Constructed Fountain Codes. Wirel. Commun. Mob. Comput. 2018, 2018, 8404219. [Google Scholar] [CrossRef]
- Hung, D.T.; Duy, T.T.; Trinh, D.Q.; Bao, V.N.Q. Secrecy Performance Evaluation of TAS Protocol Exploiting Fountain Codes and Cooperative Jamming under Impact of Hardware Impairments. In Proceedings of the 2018 2nd International Conference on Recent Advances in Signal Processing, Telecommunications & Computing (SigTelCom), Ho Chi Minh City, Vietnam, 29–31 January 2018; pp. 164–169. [Google Scholar]
- Sun, L.; Ren, P.; Du, Q.; Wang, Y. Fountain-coding Aided Strategy for Secure Cooperative Transmission in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2016, 2, 291–300. [Google Scholar] [CrossRef]
- Khan, A.S.; Chatzigeorgiou, I. Opportunistic Relaying and Random Linear Network Coding for Secure and Reliable Communication. IEEE Trans. Wirel. Commun. 2018, 17, 223–234. [Google Scholar] [CrossRef]
- Sun, L.; Xu, H. Fountain-Coding-Based Secure Communications Exploiting Outage Prediction and Limited Feedback. IEEE Trans. Veh. Technol. 2019, 68, 740–753. [Google Scholar] [CrossRef]
- Hung, D.T.; Duy, T.T.; Trinh, D.Q. Security-Reliability Analysis of Multi-hop LEACH Protocol with Fountain Codes and Cooperative Jamming. EAI Trans. Ind. Netw. Int. Syst. 2019, 6, 1–7. [Google Scholar] [CrossRef][Green Version]
- Tin, P.T.; Tan, N.N.; Sang, N.Q.; Duy, T.T.; Phuong, T.T.; Voznak, M. Rateless Codes based Secure Communication Employing Transmit Antenna Selection and Harvest-To-Jam under Joint Effect of Interference and Hardware Impairments. Entropy 2019, 21, 700. [Google Scholar] [CrossRef]
- Papoulis, A.; Pillai, S.U. Probability, Random Variables and Stochastic Processes, 4th ed.; McGraw-Hill Europe: London, UK, 2002. [Google Scholar]
- Qin, D.; Wang, Y.; Zhou, F.; Wong, K.K. Performance Analysis of AF Relaying With Selection Combining in Nakagami-m Fading. IEEE Syst. J. 2019, 13, 2375–2385. [Google Scholar] [CrossRef]
- Amari, S.V.; Misra, R.B. Closed-form Expressions for Distribution of Sum of Exponential Random Variables. IEEE Trans. Reliab. 1997, 46, 519–522. [Google Scholar] [CrossRef]
- Wang, X.; Chen, W.; Cao, Z. A Rateless Coding Based Multi-relay Cooperative Transmission Scheme for Cognitive Radio Networks. In Proceedings of the IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009; pp. 164–169. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).