Abstract
In the literature, there are many image encryption algorithms that have been constructed based on different chaotic maps. However, those algorithms do well in the cryptographic process, but still, some developments need to be made in order to enhance the security level supported by them. This paper introduces a new cryptographic algorithm that depends on a logistic and two-dimensional chaotic economic map. The robustness of the introduced algorithm is shown by implementing it on several types of images. The implementation of the algorithm and its security are partially analyzed using some statistical analyses such as sensitivity to the key space, pixels correlation, the entropy process, and contrast analysis. The results given in this paper and the comparisons performed have led us to decide that the introduced algorithm is characterized by a large space of key security, sensitivity to the secret key, few coefficients of correlation, a high contrast, and accepted information of entropy. In addition, the results obtained in experiments show that our proposed algorithm resists statistical, differential, brute-force, and noise attacks.
MSC:
68P25; 68U10; 94A60
1. Introduction
Converting secret information such as images from a decipherable form to an undecipherable one has been recently investigated to fulfill the demand of a secure route of image transmission through different communications channels such as Internet and wireless networks. Encryption schemes have been introduced based on chaotic models to handle that issue and to provide such secure routes [1,2]. The Data Encryption Standard (DES) algorithm is a traditional scheme and has been used for encrypting images [3]. It has some drawbacks, among which is that the algorithm’s efficiency is low when dealing with large images [4,5]. The theory of chaos is an important theory that possesses some complex features such as sensitivity to the initial conditions, unpredictability, and bifurcation. It has been recently adopted by researchers in the process of encryption [1,2]. Chaos has presented some popular models, which include some complex properties that help provide a robust encryption scheme. Such models include the logistic map, Lorenz attractor, the Hénon map, and some chaotic economic systems [6]. Such complex properties of chaotic maps may be reflected in an analogy to certain properties of the cryptographic process of ideal ciphers like diffusion, confusion, balance, and avalanche.
The cipher schemes proposed based on chaotic characteristics have shown a robust and efficient way to tackle image broadcast very quickly with highly secured routes via different types of telecommunications. Since Matthews [7] published his first algorithm of encryption in 1989, which depended on some chaotic characteristics, a number of chaos-based image encryption schemes with have been developed in literature. For instance, in [8], the authors created a cipher image by dividing it into some blocks and used some kind of permutations applied to each block using the logistic map. A two-dimensional discrete chaotic system has been introduced in [9]. It used the Chebyshev chaotic sequences to scramble each pixel in the novel image. Increasing the key space is another aspect that makes the algorithm used for encryption very difficult to break, and this has been performed in [10]. A multi-chaotic system has been adopted in the process of encryption in [10]. In [11], the Rossler system has been included in an encryption algorithm and has been used to change the image’s pixel values and position in order to make the ciphered images have high uncertainty. A logistic chaotic function has been used in [12] with the one-time pads in order to increase the encryption space, and hence, robust cipher images can be obtained. The shuffling approach has been introduced in [13], presenting a good scheme of encryption based on the cat map. It is a one-dimensional chaotic map with some advantages such as simplicity and high efficiency [14]. However, it has some weaknesses that may make it possible for the encryption scheme to be easily broken. This weakness includes a small key space and a weak security [15,16].
It is important here to highlight some of the recent and state-of-the-art algorithms in cryptography that will be used in comparison with our proposed algorithm. For example, in [17], Sivakumar et al. introduced a new image encryption algorithm based on pixel position permutation and a random key stream. In [18], the authors combined DNA sequences with a chaotic map to introduce an image algorithm of encryption. Based on discrete wavelet transform and multi-chaos, an image algorithm was proposed in [19]. The Arnold transformation has been used to encrypt images with high security in [20]. The idea in [20] depended on splitting the image randomly into several parts, and then, each part was coded by the Arnold transformation to increase the security level. Adopting the classical confusion-diffusion structure, an image encryption algorithm has been introduced by Hua et al. based on a 2D logistic-sine-coupling map [21]. In [22], a simple piecewise linear chaotic map has been utilized to construct a bit-level image encryption algorithm. Recently, a robust image encryption/decryption algorithm via 1D chaotic economic map was proposed in [1]. The advantage of that algorithm is that the periodic recovery of the plain image is removable.
Some of the disadvantages existing in those algorithms have led us to propose a new 2D chaotic algorithm for image encryption. The algorithm published in [1] is constructed based on a one-dimensional chaotic map, but this one depends on a two-dimensional chaotic system. The number of parameters in the current algorithm is more than that in [1], and therefore, the security level is higher than the one in [1]. The current paper is organized as follows. In Section 2, a brief introduction about the 2D chaotic map used in the algorithm is presented. In Section 3, the algorithm’s steps are introduced in detail. In Section 4, we discuss our obtained results due to applying the algorithm on some popular images and make some comparisons with the results obtained by existing algorithms in the literature. In Section 5, we give some conclusions.
2. The Two-Dimensional Map
Recently, the adoption of chaotic dynamical systems to encrypt images has drawn researchers’ attention. Such systems possess many parameters that have influences on the systems’ behaviors and are suitable in the encryption scheme. Those parameters have some important usage, as they are used as security keys in the process of encryption. Small changes in the value of the system’s parameters may make the system enter a region where chaos arises. The chaotic behavior of such systems is an important aspect when cryptographic algorithms are constructed. In this work, we adopt the chaotic economic map introduced in [23] that takes the following form:
where:
Equation (1) shows the chaotic behavior of a map with six distinct parameters. These parameters are important in the economy. First, a stands for the market size and should always be positive, while the parameter represents the change of price within the market. Economically, the condition and should be always satisfied. The parameter is called the cost of producing one unit of a good, and is known as the speed adjustment. The chaotic behavior of the economic map (1) is detected at the parameter values: , and . Figure 1a shows the bifurcation diagram of Equation (1) with respect to the parameter k for these parameters. Numerical simulation has shown that when the system (1) approaches the value , a two-cycle period appears, and so on, for other different cycle periods until the system becomes chaotic. This is clear in the Lyapunov exponents plotted in Figure 1c at the same values of the parameters. Lyapunov exponents tell us the rate of divergence of nearby trajectories, a key component of chaotic dynamics. Figure 1b shows the time series for both variables and . Finally, Figure 1d shows the complex chaotic behavior of the system (1).
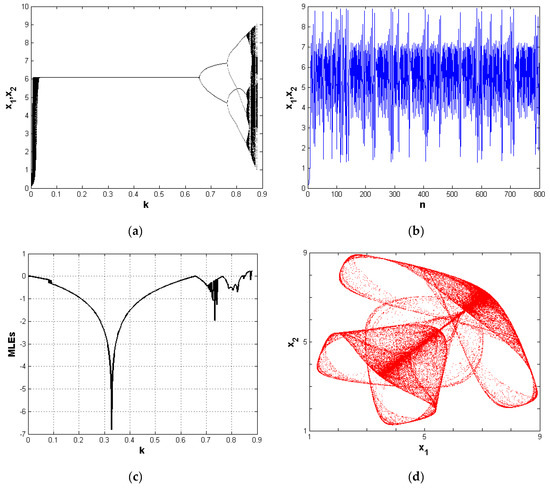
Figure 1.
(a) Bifurcation diagram with respect to the parameter k at ; (b) time series for the system’s variables at ; (c) the Lyapunov exponent with respect to the parameter k at ; (d) chaotic behavior of the system at the parameters .
3. The Algorithm
It is known that any original image has strong correlations among its pixels. In the encryption process, it is important to scatter the pixels to break their correlations. The well-known approach to do that is the shuffling process, which is applied to each array of the original image. Suppose that the original image has the dimension and is the array of its pixel positions. To produce the shuffling array, , we continue as follows:
- (Shuffling of rows) In this step, we recall the logistic map . The logistic map is used to generate a set of random values in the interval , say . The rows of the array are changed according to those random values, and hence, a new array is obtained:
- (Shuffling of columns) Using a similar technique as in (1), we generate a new set of random values in the interval , say . The columns of take the following form:
Now, the steps of our encryption algorithm are constructed as follows:
- Step 1:
- Read the original image, then convert it to a gray image, say .
- Step 2:
- Perform row and column shuffling to generate the shuffling array, say .
- Step 3:
- Convert the pixel values of from decimal to binary, .
- Step 4:
- Use the two-dimensional chaotic economic map (1) to generate values as follows:
- (i)
- For i = , Compute:. End.
- (ii)
- Set and as initial values.
- (iii)
- Generate values and using the two-dimensional chaotic economic map (1).
- Step 5:
- Do the following preprocessing for the generated values in Step 4:
- Step 6:
- Convert the preprocessing values in Step 5 from decimal to binary, and for and , respectively.
- Step 7:
- Perform the bit-wise between the values of and , , where equals the value of the array after reshaping it to be a vector of size .
- Step 8:
- Perform the bit-wise between the values of and , .
- Step 9:
- Perform the bit-wise between the values of and , .
- Step 10:
- Convert the values of from binary to decimal, say .
- Step 11:
- The cipher pixel set is denoted by .
- Step 12:
- Reshape the set to be an array of size , say as the cipher image.
In addition, the steps of our decryption algorithm are described as follows:
- Step 1:
- Read the cipher image, with size .
- Step 2:
- Reshape to the cipher pixel set .
- Step 3:
- Convert the values of from decimal to binary, say .
- Step 4:
- Repeat in the encryption algorithm to generate values for the two vectors, and .
- Step 5:
- Do the following preprocessing for the generated values in Step 4:
- Step 6:
- Convert the preprocessing values in Step 5 from decimal to binary, and for and , respectively.
- Step 7:
- Perform the bit-wise between the values of and , .
- Step 8:
- Perform the bit-wise between the values of and ,
- Step 9:
- Perform the bit-wise between the values of and ,
- Step 10:
- Convert the values of from binary to decimal, say .
- Step 11:
- Reshape to be an array of size , say .
- Step 12:
- Perform row and column shuffling to get the decryption image, say .
The Secret Key Generation
Assume that , , is the plain image, where refers to the value of the pixel at the position and is the size of the plain image . The secret key will be calculated via the key mixing proportion factor as follows:
Then, we change the initial condition according to the following formula:
where and , respectively.
After that, take two initial values for the logistic map, , two parameters for the logistic map, , two initial values for the system, , and four system parameters, .
Remark 1.
It is not difficult to note that . Therefore, the value of on the right-hand side of Equation (3) must satisfy the conditions of Map (1).
4. Experimental Analysis
In the current section, we apply the introduced algorithm on several types of images to test its robustness. Ten well-known images, lena (128 × 128, 256 × 256, 512 × 512), barbara (256 × 256), airplane (512 × 512), boat (512 × 512), house (256 × 256), baboon (512 × 512), moon surface (256 × 256), and resolution chart (256 × 256) are tested as plain images. The plain images and their corresponding histograms are displayed in the first and second columns in Figure 2.
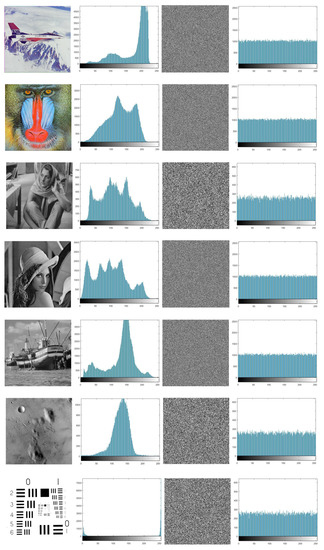
Figure 2.
Histogram diagram for plain and cipher images at , and .
The security keys of our encryption algorithm are chosen as follows. In the logistic map, , for row shuffling and , for column shuffling. In the two-dimensional chaotic economic map (1), and . Our experiments are carried out under MATLAB R2016a running on a laptop with the following features: Intel(R) Core(TM) i7-4700MQ 2.40 GHz, 12.0 GB memory, and 1.0 TB capacity.
5. Security Analysis
A good encryption algorithm possesses the following properties: (i) histograms of cipher images that are completely uniform; (ii) good information entropy; (iii) very low relationship between two adjoining pixels; (iv) resistance to statistical and differential attacks; (v) sensitivity to the secret keys; (vi) huge key space; (vii) high contrast; (viii) resisting noise attacks. Those aspects are tested for the proposed algorithm.
5.1. Statistical Analysis
Statistically, plain and cipher images must be different and therefore similarity must be hidden in order to avoid the attempts of attackers to break the algorithm.
5.1.1. Analysis of the Histogram
The distribution of pixel values in the image is shown by a histogram analysis. The histogram of the cipher image should be uniformly distributed. Therefore, obtaining any useful statistical information will be very hard. The third and fourth columns of Figure 2 display cipher images and their corresponding histograms.
The histograms of the obtained encrypted images are approximately uniform, are different from those histograms of the plain images, and show that the proposed algorithm is secure enough for image encryption. The cipher images have histograms that have an approximately uniform distribution. The chi-square test [24] is used to check this uniformity using the following formula:
where the gray level number is and and represent the observed and the expected occurrence frequencies of each gray level (0–255). Using a level of significance that , the chi-square values of the cipher images are given in Table 1.

Table 1.
values of plain and cipher images at , and .
It is easy to see that . Therefore, our null hypothesis is accepted with this level of significance, and the cipher histograms have a uniform distribution. It is shown in Table 1 that the value of is less than the tabulated value .
5.1.2. Entropy Process of Information
For a source with symbol S, the process of entropy is denoted by H and is calculated by the following formula [25].
where refers to the probability of symbol and the bits are used for entropy. The theoretical result of entropy is eight if gray values for an image with equal probability. The information entropy shows the distribution of gray values. The information entropy for the cipher images is exhibited in Table 2. The obtained values are near the theoretical value of eight. Recently, the authors in [26] proposed a statistical test for the block entropy and introduced qualitative and quantitative results. We have selected 100 non-overlapped blocks of size randomly from each cipher image. We have calculated the information entropy for each block based on Equation (5), and the average entropy was recorded. From Table 2, all actual block entropy values are passed the theoretical block entropy values at and . Therefore, we may conclude that the cipher images is random-like after applying our proposed encryption algorithm.

Table 2.
Information entropy tests for cipher images at , and .
5.1.3. Examination of Correlation
In this subsection, the vertical, horizontal, and diagonal correlations between two adjacent pixels in a cipher image are evaluated. This examination can be carried out by selecting randomly 5000 pairs of two neighboring pixels from the original and cipher images. The coefficient of correlation for each pair is obtained using [4,27]:
where:
and:
where the gray values of any two neighboring pixels of an image are denoted by x and y. Figure 3 demonstrates the horizontal distribution of the relationship between two neighboring pixels in the original image and its corresponding ciphered image. Table 3 shows the relationship of two neighboring pixels in the original and cipher images. Figure 3 presents those correlations for the plain and the cipher one. The correlation coefficients of the cipher image for our proposed algorithm and other algorithms are shown in Table 4. The correlation coefficients of two adjacent pixels of the cipher image are close to zero.
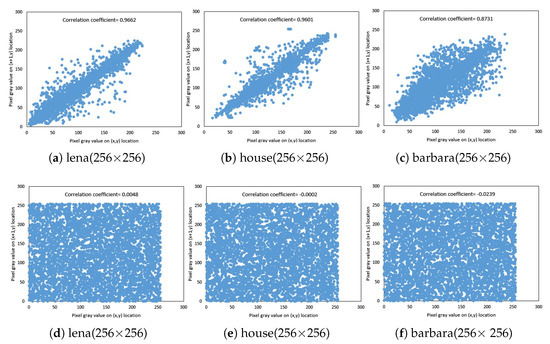
Figure 3.
(a–c) Correlation analysis of plain images and (d–f) correlation analysis of cipher images at , and .

Table 3.
Correlation coefficients of two adjacent pixels of the plain image and cipher image at , and .

Table 4.
Correlation coefficients of two adjacent pixels of the cipher image for the proposed algorithm at , and and other algorithms.
5.2. Sensitivity Analysis
One of the important features of a good encryption algorithm is the sensitivity to the security key and the plain image. Therefore, any small change in the security key or the plain image tends to a completely different cipher image [28].
5.2.1. Differential Attack
In order to get some insights about the influence of changing one pixel in the cipher image, some measures such as (Number of Pixels Change Rate) and (Unified Average Changing Intensity) are used. They have the following formulae:
where:
The width and height of the two ciphered images and are denoted by W and H.
In Table 5, each gray level is coded in such a way that only eight bits are used in the coding. The obtained calculations demonstrate that the percentage of the is acceptable, as it is close to , while the percentage of the is close to is also acceptable for the assigned images. Therefore, we can conclude that our encryption algorithm can survive against differential attack.

Table 5.
Comparison of the Number of Pixels Change Rate () and Unified Average Changing Intensity () of the lena, barbara, and house images with size using our proposed algorithm and other algorithms.
5.2.2. Key Sensitivity Test
Some key sensitivity tests are carried out in this subsection in order to check our proposed algorithm. Figure 4a–c shows the decrypted images of the ciphered images of lena, barbara, and house using the proper values of the secret key. In the secret key, if the value of a is changed to and the other values of the secret key are unchanged, the results give the decrypted images shown in Figure 4d–f, which are completely unreadable and different from the original ones. Figure 4g–i shows the decrypted images of the ciphered images with a similar security key except . Based on those obtained results, one can conclude that any small change in one of the security keys leads to a bad image being produced, and then, the original plain image cannot be retrieved. Therefore, our algorithm possesses strong security keys.
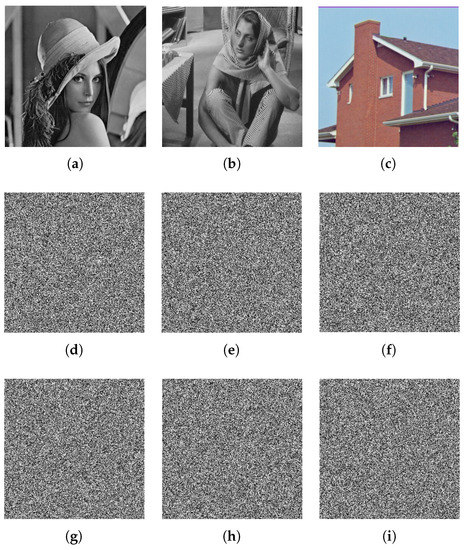
Figure 4.
Decrypted images of lena, barbara, and house for the proper secret key (a–c), (d–f) decrypted images at , and , and (g–i) decrypted images at , and .
5.3. The Analysis of Our Key Space
A strong encryption algorithm has a large enough key space. For high security, the key space should be greater than [2,29]. The proposed algorithm uses two initial values for and two initial values for . The logistic map is utilized for row shuffling and column shuffling. In addition, there are six initial values, , and k, which are used in the two-dimensional chaotic economic map. Therefore, our security keys consist of ten values. Therefore, using a precision of [2], the size of the proposed algorithm key space is , and it is more than . Table 6 shows that our proposed algorithm has a key space larger than the key spaces in [1,6,21,22]. Therefore, the key space of our algorithm is large enough to resist brute-force attacks. This makes our proposed algorithm sufficiently robust to oppose a wide range of brute-force attacks.

Table 6.
Key space comparison.
5.4. Noise Attacks
The security of our algorithm against noise is tested. Two famous types of noises are incorporated into the encrypted images. The first is Gaussian noise with variances of 0.01 and 0.1. The second is salt and pepper with densities of 0.05 and 0.1. The Mean Square Error (MSE) and Peak Signal to Noise Ratio (PSNR) are used for measuring.
Assume that X and Y denote the plain image and decrypted image for the ciphered image after the noise is incorporated. MSE and PSNR are calculated by the following equations:
and:
where I is the maximum possible pixel value of an image.
The high similarity between the plain image and the decrypted image has been measured using the PSNR. Table 7 and Figure 5 show the results. The results show that the images with salt and pepper noise are better than the images with Gaussian noise because the PSNR is greater than 18.6. In addition, the histograms of the decrypted images and the plain images are approximately similar.

Table 7.
Noise attack results.
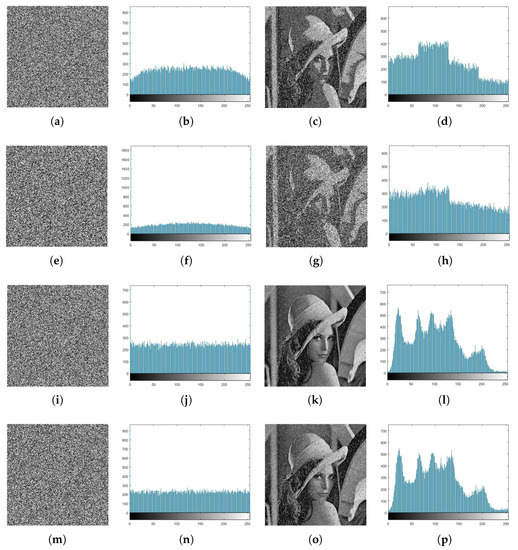
Figure 5.
(a,e,i,m) Encrypted images after adding Gaussian and salt and pepper, (b,f,j,n) corresponding histograms of the encrypted images, (c,g,k,o) decrypted images at , and , and (d,h,l,p) corresponding histograms of decrypted images.
5.5. Contrast Analysis
The difference investigation of the image permits the observer to entirely understand the texture of images. The ciphered image has high contrast levels as a result of the high randomness given by the map (1) in the process of encryption. We have evaluated the contrast of the ciphered image and the effectiveness of Map (1) in image encryption applications. This can be carried out by the following formula:
where is used to refer to the number of gray levels in the co-occurrence matrices.
The contrast analyses of both the plain and cipher images for lena (), barbara (), and house () are shown in Table 8. Table 9 shows that the contrast analysis of the introduced algorithm overcomes the algorithm in [6]. It has the best result.

Table 8.
Contrast analysis of plain and cipher images at , and .

Table 9.
Contrast analysis of the plain (lena ()) and cipher image using the proposed algorithm at , and and other algorithms.
5.6. Gray Value Degree Analysis
Measuring the gray difference of a pixel requires one to know its four neighbors. This can be carried out using the following formula:
where refers to the value of a pixel at location and denotes its four neighboring pixels. Now, the average difference of the whole image is measured by the following:
where M and N refer to the row and column numbers in an image. Using (11) and (12), the Gray Value Degree (GVD) is defined as,
where the average neighborhood gray difference of an original image is denoted by , while refers to those of the encrypted image. Table 10 presents the degree values of the computed gray value degree for distinct images using the proposed algorithm. One can see from Table 10 that our obtained degree values are close to the ideal value, which is one. Table 11 shows some validations of the proposed algorithm versus existing algorithms in the literature.

Table 10.
Gray Value Degree (GVD for different test images.

Table 11.
GDV analysis of the proposed algorithm with other algorithms.
5.7. Peak Signal to Noise Ratio Analysis
PSNR is used to carry out the evaluation of the encryption algorithms. It is applied to both images, the original image and the encrypted one. It considers the original image as a signal, while the encrypted image as a noise. PSNR is calculated by using Equation (11). Table 12 shows the PSNR values of some different images. It is shown that those values are low, which means it is difficult to retrieve the original image from the encrypted one in the case of hacker attacks.

Table 12.
PSNR values for different test images.
5.8. Computational Complexity
We make a comparison of the computational complexity between the traditional DES, AES, and other algorithms in the literature including our proposed algorithm. The results appear in Table 13. Based on Table 13, we can concluded that the time of our algorithm is less than the traditional DES and AES algorithms and the other algorithms in the literature and is completely acceptable for encryption of an image.

Table 13.
The speed of encryption for each algorithm. DES, Data Encryption Standard.
6. Conclusions
The current paper introduced a new cryptographic algorithm based on a two-dimensional chaotic economic map and logical operator bit-wise . The size of the key space for our proposed algorithm is , which allows our algorithm to survive against attacks. The numerical experiments have shown that the algorithm is very sensitive to the security keys, and hence, any bit change or random guessing about the proper value of the security keys fails to retrieve the original image. The obtained results by the proposed algorithm have shown that the ciphered image is random-like since the information entropy of the cipher image of size is very close to the theoretical value of eight, the is close to , and is close to . Therefore, our algorithm is extremely sensitive to any small change in the original image. According to the obtained results, we may conclude that the proposed algorithm owns a high level of security that allows it to prevent any attempts of attack by hackers.
Author Contributions
Conceptualization, methodology, and writing, original draft preparation, S.S.A. and A.A.K.; software, validation, formal analysis, and investigation, A.A.K. and F.S.A.-A.; writing, review and editing, S.S.A., A.A.K. and A.A.-K.
Funding
This research was funded by Deanship of Scientific Research at King Saud University for funding this research group number (RG-1435-054).
Acknowledgments
The authors would like to extend their sincere appreciation to the Deanship of Scientific Research at King Saud University for funding this research group number (RG-1435-054).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Askar, S.S.; Karawia, A.A.; Alammar, F. Cryptographic algorithm based on pixel shuffling and dynamical chaotic economic map. IET Image Process. 2018, 12, 158–167. [Google Scholar] [CrossRef]
- Zhu, C. A novel image encryption scheme based on improved hyperchaotic sequences. Opt. Commun. 2012, 285, 29–37. [Google Scholar] [CrossRef]
- Abomhara, M.; Zakaria, O.; Khalifa, O. An Overview of Video Encryption Techniques. Int. J. Comput. Theory Eng. 2010, 2, 1793–8201. [Google Scholar] [CrossRef]
- Chen, G.; Mao, Y.; Chui, C. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Chiaraluce, F.; Ciccarelli, L.; Gambi, E.; Pierleoni, P.; Reginelli, M. A new chaotic algorithm for video encryption. IEEE Trans. Consum. Electron. 2002, 48, 838–843. [Google Scholar] [CrossRef]
- Askar, S.S.; Karawia, A.A.; Alshamrani, A. Image encryption algorithm based on chaotic economic model. Math. Probl. Eng. 2015, 2015, 341729. [Google Scholar] [CrossRef]
- Matthews, R. On the derivation of a chaotic encryption algorithm. Cryptologia 1989, 13, 29–42. [Google Scholar] [CrossRef]
- Xu, E.; Shao, L.; Cao, G.; Ren, Y.; Qu, T. A New Method of Information Encryption. In Proceedings of the International Colloquium on Computing, Communication, Control, and Management, Sanya, China, 8–9 August 2009; Volume 4, pp. 583–586. [Google Scholar]
- Zhang, D.; Gu, Q.; Pan, Y.; Zhang, X. Discrete Chaotic Encryption and Decryption of Digital Images. In Proceedings of the International Conference on Computer Science and Software Engineering, Wuhan, China, 12–14 December 2008; Volume 3, pp. 849–852. [Google Scholar]
- Nien, H.; Huang, W.; Hung, C.; Chen, S.; Wu, S.; Huang, C.; Hsu, Y. Hybrid image encryption using multi-chaos-system. In Proceedings of the International Conference on Information, Communications and Signal Processing (ICICS), Macau, China, 8–10 December 2009; pp. 1–5. [Google Scholar]
- Cao, Y.; Fu, C. An image encryption scheme based on high dimension chaos system. In Proceedings of the International Conference on Intelligent Computation Technology and Automation, Changsha, China, 20–22 October 2008; Volume 2, pp. 104–108. [Google Scholar]
- Jeyamala, J.; GrpiGranesh, S.; Raman, S. An image encryption scheme based on one time pads—A chaotic approach. In Proceedings of the International Conference on Computing, Communication and Networking Technologies, Karur, India, 29–31 July 2010; pp. 1–6. [Google Scholar]
- Zhu, W.; Shen, Y. Encryption Algorithms Using Chaos and CAT Methodology. In Proceedings of the International Conference of Anti-Counterfeiting Security and Identification in Communication (ASID), Chengdu, China, 18–20 July 2010; pp. 20–23. [Google Scholar]
- Elnashaie, S.; Abashar, M. On the chaotic behavior of forced fluidized bed catalytic reactors. Chaos Solitons Fractals 1995, 5, 797–831. [Google Scholar] [CrossRef]
- Kocarev, L. Chaos-based cryptography: A brief overview. IEEE Circuits Syst. Mag. 2001, 1, 6–21. [Google Scholar] [CrossRef]
- Ponomarenko, V.; Prokhorov, M. Extracting information masked by the chaotic signal of a time-delay system. Phys. Rev. E 2002, 66, 1–7. [Google Scholar] [CrossRef]
- Sivakumar, T.; Venkatesan, R. Image Encryption Based on Pixel Shuffling and Random Key Stream. Int. J. Comput. Inf. Technol. 2014, 3, 1468–1476. [Google Scholar]
- Zhang, J.; Fang, D.; Ren, H. Image Encryption Algorithm Based on DNA Encoding and Chaotic Maps. Math. Probl. Eng. 2014, 2014, 917147. [Google Scholar] [CrossRef]
- Wang, W.; Tan, H.; Pang, Y.; Li, Z.; Ran, P.; Wu, J. Novel Encryption Algorithm Based on DWT and Multichaos Mapping. J. Sens. 2016, 2016, 2646205. [Google Scholar] [CrossRef]
- Zou, J.; Weng, T. A New Image Encryption Instant Communication Method Based On Matrix Transformation. In Advances in Intelligent Information Hiding and Multimedia Signal Processing. Smart Innovation, Systems and Technologies; Pan, J.S., Tsai, P.W., Huang, H.C., Eds.; Springer: Berlin, Germany, 2017; Volume 63, pp. 321–329. [Google Scholar]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
- Askar, S.S. Complex dynamic properties of Cournot duopoly games with convex and log-concave demand function. Oper. Res. Lett. 2014, 42, 85–90. [Google Scholar] [CrossRef]
- Kwok, H.; Tang, W. A fast image encryption system based on chaotic maps with finite precision representation. Chaos Solitons Fractals 2007, 32, 1518–1529. [Google Scholar] [CrossRef]
- Sobhy, M.; Shehata, A. Methods of attacking chaotic encryption and countermeasures. In Proceedings of the IEEE International Conference on Acoustics, Speech, and Signal Processing, Salt Lake City, UT, USA, 7–11 May 2001; Volume 2, pp. 1001–1004. [Google Scholar]
- Tao, X.; Liao, X.; Tang, G. A novel block cryptosystem based on iterating a chaotic map. Phys. Lett. A 2006, 349, 109–115. [Google Scholar]
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Pareek, N.; Patidar, V.; Sud, K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Song, C.; Qiao, Y.; Zhang, X. An image encryption scheme based on new spatiotemporal chaos. Opt.—Int. J. Light Electron Opt. 2013, 124, 3329–3334. [Google Scholar] [CrossRef]
- Parvin, Z.; Seyedarabi, H.; Shamsi, M. A new secure and sensitive image encryption scheme based on new substitution with chaotic function. Multimedia Tools Appl. 2016, 75, 10631–10648. [Google Scholar] [CrossRef]
- Hanchinamani, G.; Kulakarni, L. Image Encryption Based on 2-D Zaslavskii Chaotic Map and Pseudo Hadmard Transform. Int. J. Hybrid Inf. Technol. 2014, 7, 185–200. [Google Scholar] [CrossRef]
- Rhouma, R.; Solak, E.; Belghith, S. Cryptanalysis of a new substitution-diffusion based image cipher. Commun. Nonlinear Sci. Numer. Simul. 2010, 15, 1887–1892. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).