Distributed One Time Password Infrastructure for Linux Environments
Abstract
:1. Introduction
2. Related Works
3. Fundamentals
3.1. Pluggable Authentication Modules (PAM)
- auth: This module verifies the user identity.
- account: This verifies the authenticated user has the required access permissions.
- password: This module allows to update the token associated to the user.
- session: This module allows implementing the required actions for the user before and after access to the service.
- required: Returns an error after all modules are executed. The error is associated to the first module generated an error.
- requisite: An error is returned after the first module failure.
- sufficient: If a sufficient module succeeds, it is enough to satisfy the requirements of sufficient modules in that realm for use of the service, and modules below it that are also listed as sufficient are not invoked. If it fails, the operation fails unless a module is invoked after it succeeds. If a required module fails before a “sufficient” one succeeds, the operation will fail anyway, ignoring the status of any “sufficient” modules.
- optional: An optional module will only cause an operation to fail if it is the only module in the stack for that facility.
int misc_conv(int num_msg, const struct pam_message** msgm, struct pam_response** response, void* appdata_ptr)
int qr_conv(int num_msg, const struct pam_message** msgm, struct pam_response** response, void* appdata_ptr)
3.2. JWT
- Header: Used to identify the signing algorithm.
- Payload: Contains the claims to make.
- Signature: The signature of the JWT. The signature is generated obtaining at first the unsigned token as encodeBase64Url(header) + “.” + encodeBase64Url(payload). Then, the signature algorithm is applied over the unsigned token.
token = encodeBase64Url(header) + “.” + encodeBase64Url(payload) + “.” + encodeBase64Url(signature).
- Token Type (typ): Constant field set t “JWT”. This claim is placed at the header.
- Message authentication code algorithm (alg): The algorithm required to verify the signature. This claim is placed at the header.
- Issuer (iss): The identifier of the device asking for the password.
- Subject (sub): Constant field set to “challenge”.
- Audience (aud): The identifier of the user or group asking for authentication.
- Expiration time (exp): The expiration time of challenge defined in the current JWT set by the source using its clock.
- Issued at (iat): The time of challenge generation.
- JWT ID (jti): The identifier of the current authentication session.
- Challenge: The generated number for the challenge.
- Seed: The random number used to generate the challenge.
QR
- QR Code Mode 1 y Mode 2.
- Micro QR Code: This QR code only requires a one direction detection pattern. This allows printing it on a smaller surface. This QR can be used if the width of the image is module 2. The largest version of this code is M4 (17 × 17) and it can store about 35 characters.
- iQR Code.
- SQRC.
- Frame QR: This QR code contains a canvas area that can be used in various ways. Because this area can be used with characters and images, it can be used for multiple purposes such as authentication, promotions, etc.
3.3. Zero-Knowledge Proofs
3.4. Base 64
4. Design and Implementation
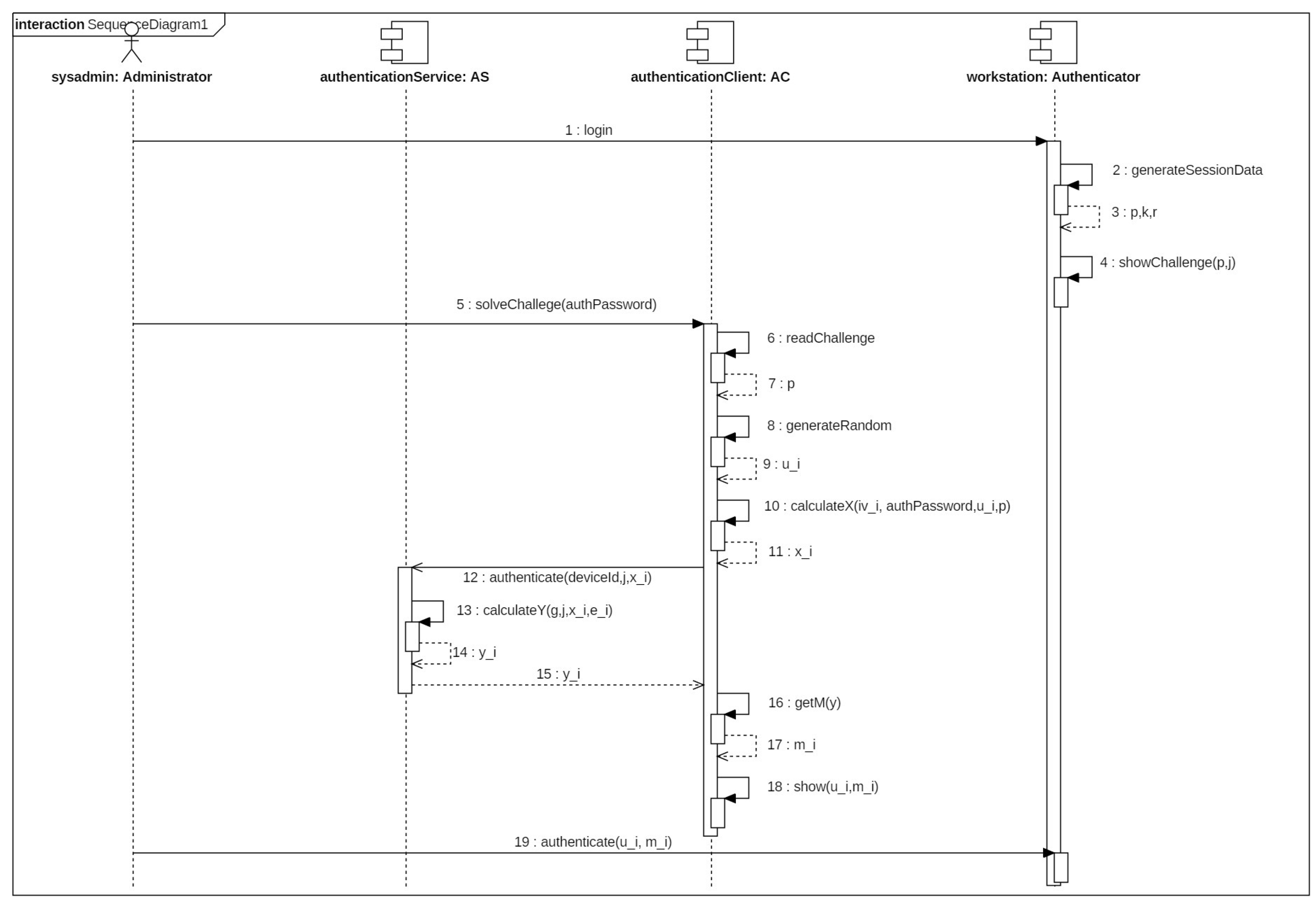
4.1. Algorithm
- Key length (): The length in bits of the key pair generated for the current authenticator.
- Password length (): The number of characters of the password requested by the authenticator.
- Number of users (m): Number of required users to complete authentication.
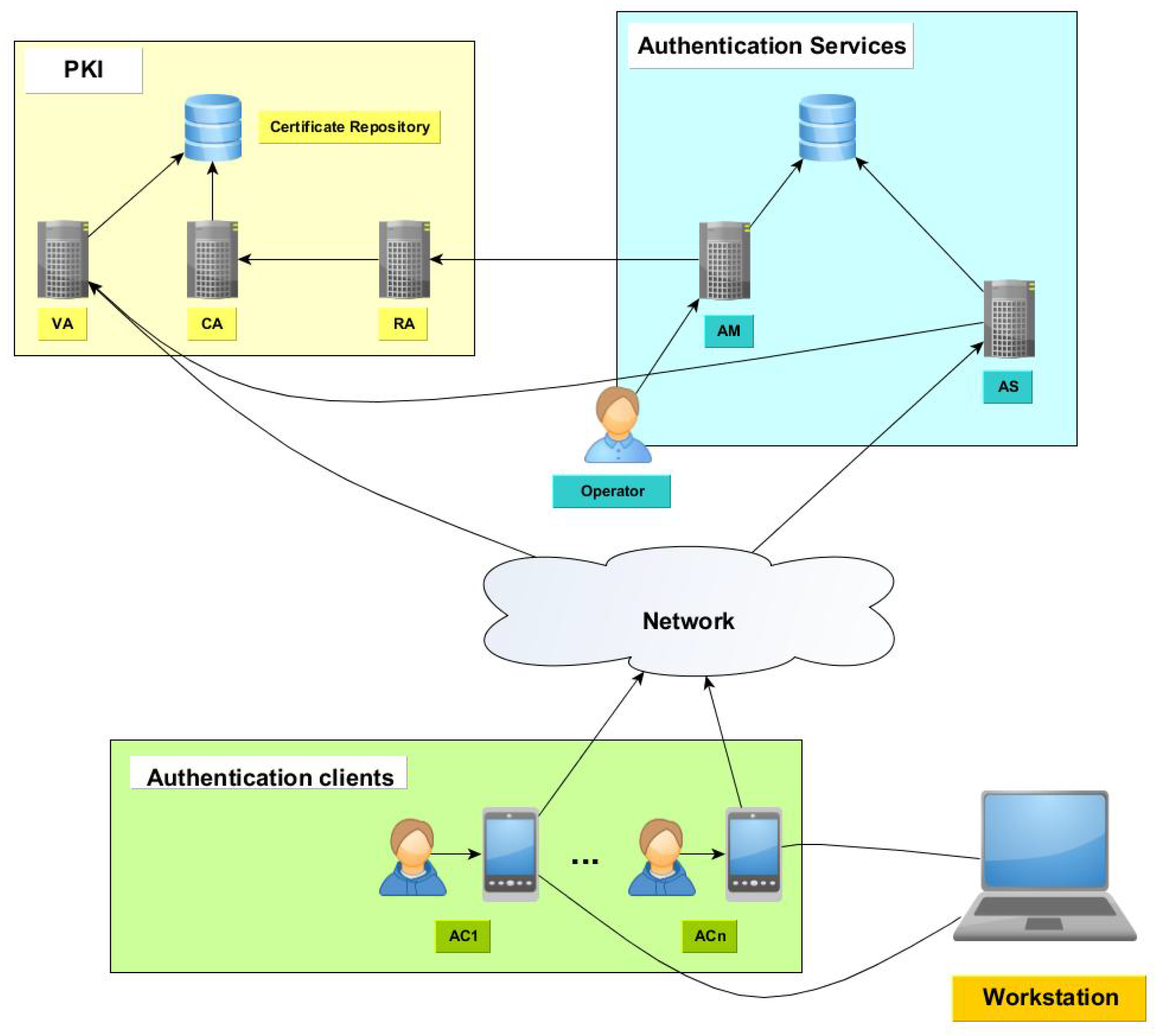
4.2. Solution Architecture
- Workstations: The devices whose access control is managed using the distribution managed system. A workstation that has been registered is called Authenticator (A).
- Client components: The devices hosting a client application used by the workstation administrators to solve authentication challenges and generate passwords. They connect to the server components to complete the authentication operation. The device is called Authentication Device (AD) and the application is called Authentication Client (AC).
- Server components: The server components provide services to register new clients and workstations and to verify client permissions. The authentication services must be accessible by the client devices.
- Certification Authority (CA): Issues, signs, stores and manages digital certificates for the requesting entities.
- Registration Authority (RA): Verifies the identity of entities requesting digital certificates. The RA application requests to CA to issue a new digital certificate.
- Validation Authority (VA): Provides services to verify the status of digital certificates. A digital certificate can be revoked, suspended or expired. Thus, in those cases, the digital certificated is not valid and it cannot be used to perform public key operations.
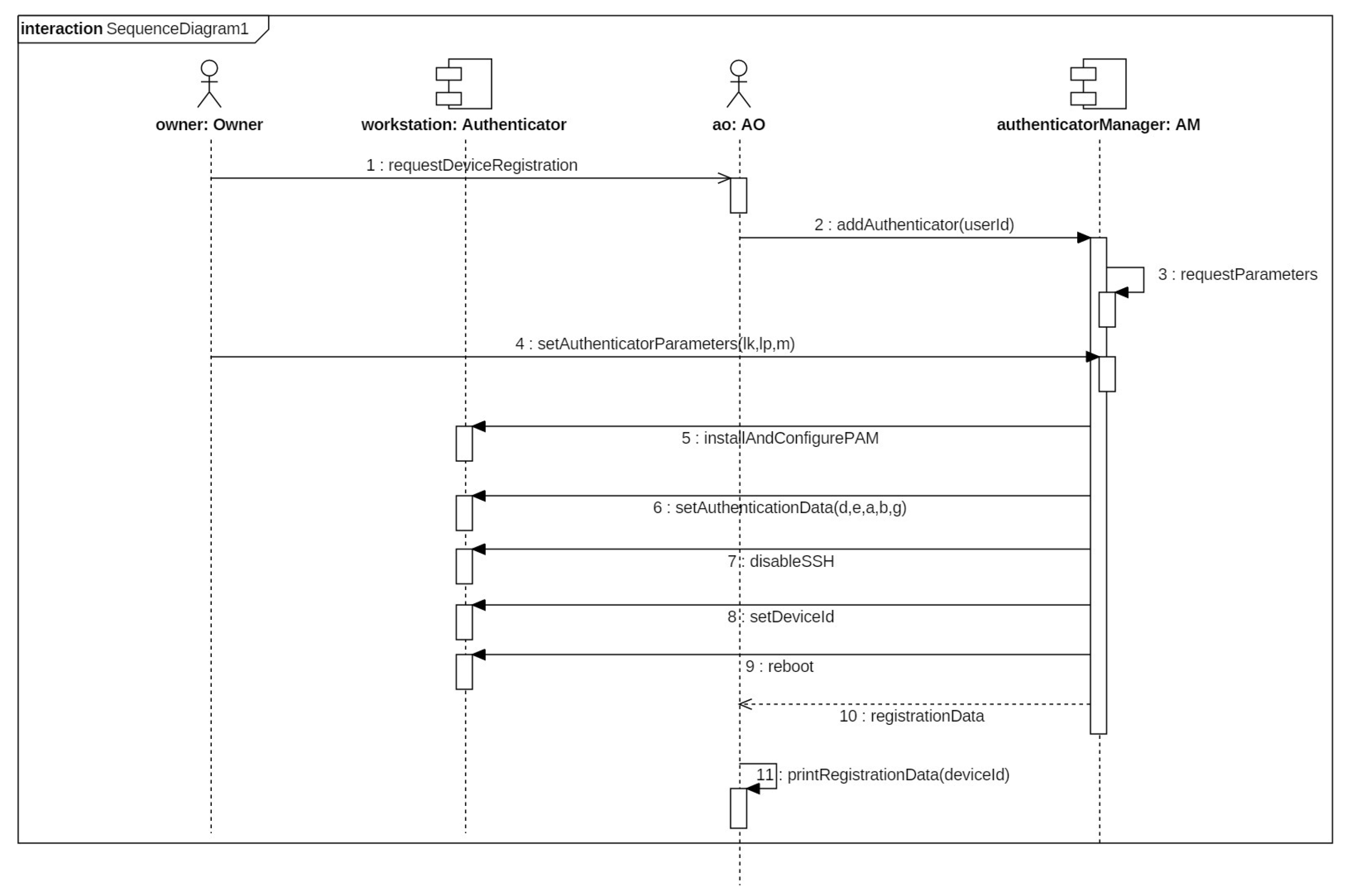
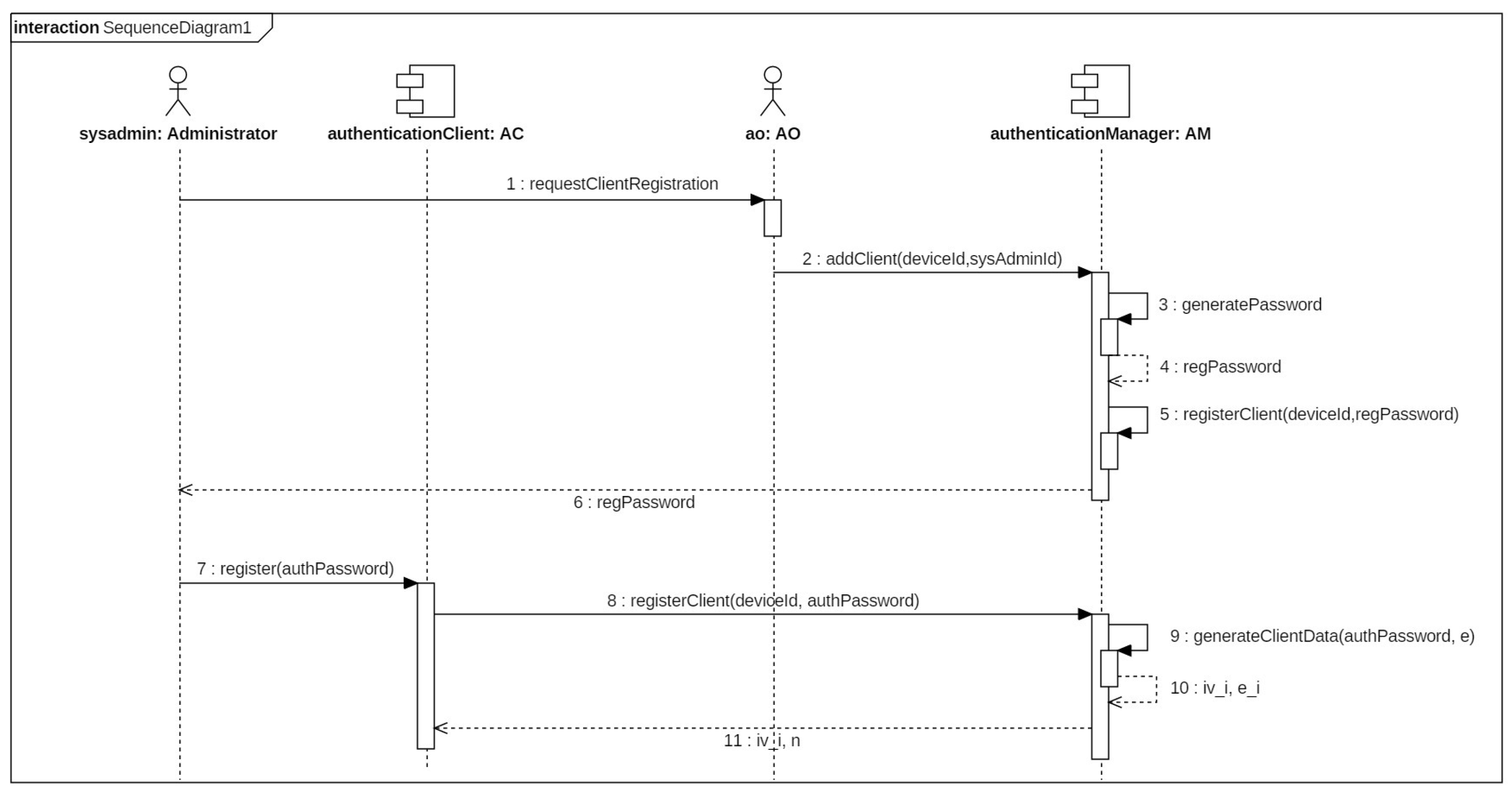
- Register the workstations that use the proposed authentication solution in the system.
- Register system administrators for a given workstation.
4.3. Security Aspects
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
Abbreviations
| AM | Authentication Manager |
| AS | Authentication Service |
| AO | Authentication Operator |
| AC | Authentication Client |
| AD | Authentication Device |
| A | Authenticator |
| CA | Certification Authorty |
| RA | Registration Authority |
| VA | Validation Authority |
| PKI | Public Key Infrastructure |
| OTP | One Time Password |
| MITM | Man in the Middle |
| HMAC | Hash based Message Authentication Code |
| CRL | Certificate Revocation List |
| OCSP | Online Certificate Status Protocol |
References
- Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R. Internet X509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. RFC 5280. 2008. Available online: https://tools.ietf.org/html/rfc5280 (accessed on 24 April 2018).
- Santesson, S.; Myers, M.; Ankney, R.; Malpani, A.; Galperin, S.; Adams, C. X509 Internet Public Key Infrastructure Online Certificate Status Protocol—OCSP. RFC 6960. 2013. Available online: http://www.rfc-editor.org/info/rfc6960 (accessed on 24 April 2018).
- Haller, N. The S/KEY One-Time Password System. In Proceedings of the ISOC Symposium on Network and Distributed System Security, San Diego, CA, USA, 2–4 February 1994. [Google Scholar]
- Haller, N. The S/KEY One-Time Password System. RFC 1760. 1995. Available online: http://buildbot.tools.ietf.org/html/rfc1760 (accessed on 24 April 2018).
- Haller, N.; Metz, C.; Nesser, P.; Straw, M. A One-Time Password System. RFC 2289. 1998. Available online: http://www.rfc-editor.org/info/rfc2289 (accessed on 24 April 2018).
- M’Raihi, D.; Bellare, M.; Hoornaert, F.; Naccache, D.; Rannen, O. HOTP: An HMAC-Based One-Time Password Algorithm. RFC 4226. 2005. Available online: https://tools.ietf.org/html/rfc4226 (accessed on 24 April 2018).
- M’Raihi, D.; Machani, S.; Pei, M.; Rydell, J. TOTP: Time-Based One-Time Password Algorithm. RFC 6238. 2011. Available online: http://www.rfc-editor.org/info/rfc6238 (accessed on 24 April 2018).
- Krawczyk, H.; Bellare, M.; Canetti, R. HMAC: Keyed-Hashing for Message Authentication. RFC 2104. 1997. Available online: https://tools.ietf.org/html/rfc2104 (accessed on 24 April 2018).
- Johnsson, J.; Kaliski, B. Public-Key Cryptography Standards (PKCS) #1: RSA Cryptography Specifications Version 2.1. RFC 3447. 2003. Available online: http://buildbot.tools.ietf.org/html/rfc3447 (accessed on 24 April 2018).
- ElGamal, T. Cryptography and logarithms over finite fields. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 1984. [Google Scholar]
- ElGamal, T. A public key Cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Gibson, S. Revolutionizing Website Login and Authentication with SQRL. In Proceedings of the DigiCert Security Summit 2014, Las Vegas, NV, USA, 21 November 2014. [Google Scholar]
- Guillou, L.C.; Quisquater, J.J. A Practical Zero-Knowledge Protocol Fitted to Security Microprocessor minimizing both transmission and memory. In Advances in Cryptology—Eurocrypt’88; Springer-Verlag: Berlin/Heidelberg, Germany, 1988; pp. 123–128. [Google Scholar]
- Chase, M.; Ganesh, C.; Mohassel, P. Efficient Zero-Knowledge Proof of Algebraic and Non-Algebraic Statements with Applications to Privacy Preserving Credentials. In Advances in Cryptology—CRYPTO 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 499–530. [Google Scholar]
- Ben-Sasson, E.; Chiesa, A.; Tromer, E.; Virza, M. Scalable Zero Knowledge Via Cycles of Elliptic Curves. Algorithmica 2017, 79, 1102–1160. [Google Scholar] [CrossRef]
- Cramer, R.; Damgård, I.; Xing, C.; Yuan, C. Amortized Complexity of Zero-Knowledge Proofs Revisited: Achieving Linear Soundness Slack. In Advances in Cryptology—EUROCRYPT 2017; Coron, J.S., Nielsen, J., Eds.; Springer: Cham, Switzerland, 2017; pp. 479–500. [Google Scholar]
- Espejel-Trujillo, A.; Castillo-Camacho, I.; Nakano-Miyatake, M.; Perez-Meana, H. Identity Document Authentication Based on VSS and QR Codes. Procedia Technol. 2012, 3, 241–250. [Google Scholar]
- Maestre, D.P. QRP: An Improved Secure Authentication Method Using QR Codes. Master’s Thesis, Universitat Oberta de Catalunya, Barcelona, Spain, 2012. [Google Scholar]
- Dolev, S.; Gilboa, N.; Kopeetsky, M. Efficient private multi-party computations of trust in the presence of curious and malicious user. J. Trust Manag. 2014, 1. [Google Scholar] [CrossRef]
- Jones, M.; Bradley, J.; Sakimura, N. JSON Web Token (JWT). RFC 7519. 2015. Available online: http://www.rfc-editor.org/info/rfc7519 (accessed on 24 April 2018).
- Ong, H.; Schnorr, C.P.; Shamir, A. An Efficient Signature Schemes Based on Quadratic Equations. In Proceedings of the Sixteenth Annual ACM Symposium on Theory of Computing; Lecture Notes in Computer Science; ACM: New York, NY, USA, 1984. [Google Scholar]
- Estes, D.; Adleman, L.M.; Kompella, K.; McCurley, K.S.; Miller, G.L. Breaking the Ong-Schnorr-Shamir Signature Scheme for Quadratic Number Fields. In Advances in Cryptology—CRYPTO’85 Proceedings; Springer-Verlag: Berlin/Heidelberg, Germany, 1986; pp. 3–13. [Google Scholar]
- Feige, U.; Fiat, A.; Shamir, A. Zero-Knowledge Proofs of Identity. J. Cryptol. 1988, 1, 77–94. [Google Scholar] [CrossRef]
- Josefsson, S. The Base16, Base32, and Base64 Data Encodings. RFC 4648. 2006. Available online: https://tools.ietf.org/html/rfc4648 (accessed on 24 April 2018).
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Benito Peral, A.; Sandoval Orozco, A.L.; García Villalba, L.J.; Kim, T.-H. Distributed One Time Password Infrastructure for Linux Environments. Entropy 2018, 20, 319. https://doi.org/10.3390/e20050319
Benito Peral A, Sandoval Orozco AL, García Villalba LJ, Kim T-H. Distributed One Time Password Infrastructure for Linux Environments. Entropy. 2018; 20(5):319. https://doi.org/10.3390/e20050319
Chicago/Turabian StyleBenito Peral, Alberto, Ana Lucila Sandoval Orozco, Luis Javier García Villalba, and Tai-Hoon Kim. 2018. "Distributed One Time Password Infrastructure for Linux Environments" Entropy 20, no. 5: 319. https://doi.org/10.3390/e20050319
APA StyleBenito Peral, A., Sandoval Orozco, A. L., García Villalba, L. J., & Kim, T.-H. (2018). Distributed One Time Password Infrastructure for Linux Environments. Entropy, 20(5), 319. https://doi.org/10.3390/e20050319






