1. Introduction
Modeling, analysis and control of the spreading of information and of infectious diseases have become a relevant problem of an interdisciplinary nature. Studies on spreading range from propagation of computer viruses in networks [
1,
2,
3,
4], epidemics in human populations [
5,
6,
7,
8,
9,
10,
11,
12], to spreading of rumors and information [
13,
14,
15,
16].
One of the early works for epidemic spreading [
17] gave birth to the so-called SIRmodel that divides the population into three different compartments or groups: susceptible, infected and recover (or removed); and later, as many diseases do not confer any immunity, a simplified version of the SIR model was created, the so-called SIS (Susceptible-Infected-Susceptible) model, which has become one of the classical model of disease spreading. Although this model was proposed for modeling spreading in populations with no structure, nowadays, the SIS model has been extended to model the spreading process in a population mapped on a complex network.
In the field of computer virus propagation, Kephart and White [
18,
19] proposed one of the first models on networks, the so-called homogeneous model. This model is called homogeneous because every node of the network has the same probability of interaction with other nodes. Using a rate of infection and a death rate, they were able to calculate the infection threshold. Unfortunately, this model fails to capture real-world complexity. Data available show that real-world computer networks are not homogeneous and, instead, follow a power law structure in the number of connections of the nodes [
20,
21,
22].
Another important method to study disease propagation is the so-called Degree Mean Field Approximation model (DMFA), which considers nodes with the same degree as dynamically equivalent [
23]. Using this model, it is possible to calculate the epidemic threshold. Although this approach is quite interesting, it is not applicable in many realistic cases because nodes with the same degree do not necessarily behave the same way. Besides, the model does not provide information about the probability of individual nodes.
In recent years, Markov chain-based models for a Susceptible-Infected-Susceptible (SIS) dynamics over complex networks have been used [
8,
9,
10,
11,
12,
24]. Using these models, it is possible to determine the macroscopic properties of the system, as well as the description of the dynamics of individual nodes. One interesting result is that the calculated infection threshold depends on the value of the spectral radius of the adjacency matrix.
In spite of the fact that an increasing number of studies on the analysis of epidemic spreading have been published in the last decade, the studies dedicated to the control of these process are not very great in number. Different authors with interesting insights have been working on this subject, but at the end, we have three main categories for controlling complex networks (see also [
25]): spectral control, optimal control and heuristic feedback control.
In the spectral optimization control methods, one of the goals is to make the eigenvalue
of the adjacency matrix
A as small as possible. This could be achieved removing nodes from
A that could be feasible by either immunizing or quarantining certain individuals [
26]. The removal of links to reduce
is also possible isolating cities or, more difficultly, restricting interactions among individuals.
In the optimization control methods for complex networks, the necessary and sufficient condition for spreading extinction poses an optimal control problem, where the curing rates are allowed to vary over time, depending on the evolving state of the system.
In [
27], the linearization of the non-linear Markovian equation for the SIR model is studied around the extinction state and showed that the optimal solution is a bang-bang controller with at most one switch. This kind of control deserves further research, although, up to this date, it presents several flaws: it assumes that direct control over infection and recovery rates is always possible. These assumptions considered that these probabilities can be controlled for an entire population in an instantaneous way, which generally is unfeasible in a human population. This method is considered in different works [
28,
29].
In the heuristic feedback control extensions of the SIS and SIRS (Susceptible-Infectious-Recovered- Susceptible) model are considered. In this case, the model and its control are developed concurrently in such a way that the stability conditions can be derived. For example, in these models, we can have states corresponding to individuals that disconnect themselves from the net when they suspect that they have become infected (Protected state (P)). This means that control structures are already built in and available in the model itself in a heuristic fashion. As examples in the literature, we have the works of [
30,
31], which gives humans the possibility to take actions once they are in an Aware state (A). One of the flaws of these models is their great specificity.
In this work, we will study the spreading of information (diseases, rumors, gossip) using a Markov chain-based model for a Susceptible-Infected-Susceptible (SIS) dynamics over complex networks that has been used by different authors [
8,
9,
10,
11,
12].
Using this model, we present a solution for the long-standing problem of epidemic spreading extinction. First of all, we present a model that generalizes the interaction among nodes and reproduces results after choosing some particular interaction. Afterwards, we determine sufficient conditions for stabilizing the spreading of information to the extinction state in complex networks of arbitrary topology. At the same time, these conditions give us a clue about how viruses are propagated, allowing us to identify the nodes that do not need any control to reach the extinction state and to distinguish them from the nodes that need to be controlled. Inspired by the ideas of control theory, we associate the set of nodes that do not need to be controlled (in order to reach the extinction state) with the zero dynamics of the system [
32]. The set of nodes to be monitored and controlled are identified, as well, and a feedback control is applied to them in order to stabilize the extinction state. Accordingly, we have proven that the extinction state is an asymptotically-stable fixed point for the zero dynamics.
We performed numerical simulations using a scale-free complex network constructed as disused by Barabasi et al. [
22] with one million nodes and show a complete agreement of the numerical results with our theoretical findings.
The remainder of this paper is organized as follows:
Section 2 presents the problem statement and definitions. In
Section 3, we determine sufficient conditions that allow us to identify the set of nodes that need to be controlled in order to reach the extinction state. In
Section 4, we propose a linear feedback control to stabilize the system. Simulations and results are shown in
Section 5. Finally, in
Section 6, the conclusions are presented.
2. Problem Formulation
In this section, (i) the considered class of systems is introduced and the underlying model discussed, and (ii) the specific control problem addressed in this study is introduced.
2.1. System Class
Consider a network of
N nodes described by an undirected graph
with
being the set of nodes and
the connecting edges, together with the corresponding adjacency matrix
where
if
, and zero otherwise. According to the graph
, the neighbors’ set
of a node
is defined as:
and the number of neighbors (or degree) is given by
.
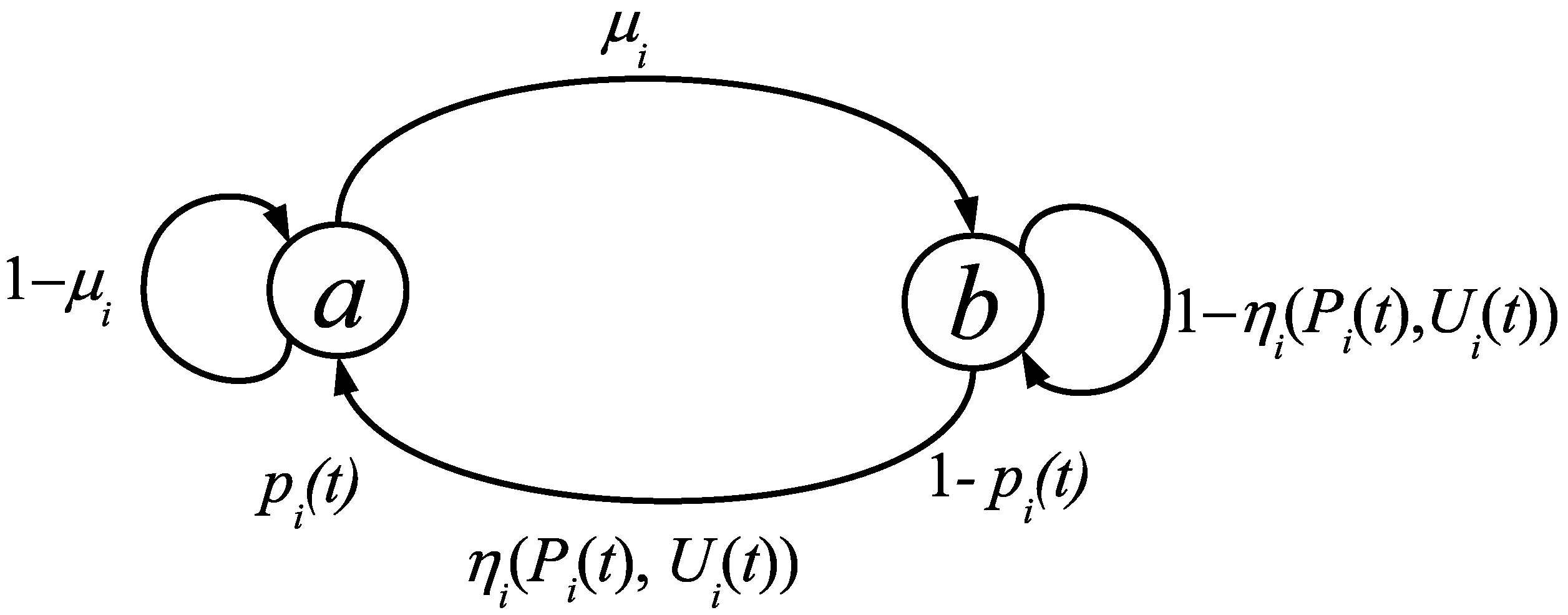
The underlying process for every node is depicted in
Figure 1, as a discrete time Markov process.
According to
Figure 1, a node
can be in state
a with probability
or in state
b with probability
, where
denotes the discrete time. The state
a represents that the node
has or knows the information to spread, and the state
b represents the opposite. Any node
is able to spread information by interacting with some neighbor node
, but if the node
does not know the information (i.e.,
), then it does not contribute to spreading the information. Furthermore, each node has a manipulable variable
, which is amenable for feedback control.
The probability
is updated as follows: at each time step, every node
can transit from
b to
a with probability
under the influence of its neighbors, or transit from state
a to
b with a probability
, where:
and
are vectors such that:
with:
The transition probability depends on the state of the neighbors given by and a set of parameters that are amenable to manipulation and models the interaction that spreads the information over due to its neighbor nodes. Note that despite the interaction between and its neighbor nodes, if , then for any value of , because in this case, the neighbor nodes do not know the information, and therefore, they do not contribute to spreading it.
Any change in
with respect to
is assumed bounded and depends on
such that for each pair
where
and
, there exists a function
such that:
or in terms of entries of the adjacency matrix:
The above means that the transition probability is a continuous function with bounded slope, which do not change abruptly.
Furthermore, throughout the paper, it is assumed that for all
,
strictly monotonically increases with
, i.e.,
Finally, in order to be consistent with (
3), it is assumed that:
The dynamics for the probability
of node
to be in state
a is given by (compare with [
8,
10,
12]):
or in vector form:
where
is the system state, and
the control parameters are given by:
with
being a vector with unity entries and:
Additionally, for later use:
2.2. Control Problem
The purpose of the control design is to bring the state of the network to the extinction state. When the extinction state is not stable, the control must be designed in such a way that destabilizing components are compensated and self-stabilization mechanisms are enhanced. This can be accomplished in different ways, e.g., by changing the network structure [
33,
34,
35] or node-specific parameters [
27,
36,
37,
38]. As for complex networks, not all node parameters are subject to control, and a systematic adaptation of parameters also implies computational complexity and may imply necessary communication structures, a set of nodes whose parameters should be adapted in order to achieve stabilization must be chosen. Once this set of nodes has been defined, it must be clarified what kind of adaptation mechanism provides the desired stabilization. A central question in this step is the decision about whether implementing a central computation structure, which decides on all parameters, or implementing a local, so-called decentralized control structure, which implies that the decision about how the control parameters are adapted, is computed locally at the node level. The implementation of this control on the other side requires some sensory information about the network state. Locating sensors in all nodes again implies high costs and complex communication structures, in particular if a centralized control structure is implemented that has to collect all the sensory data. Thus, a set of nodes for which sensor information must be provided in order to implement the control must be specified. In the sequel, the nodes for which sensor data are available are said to be monitored. A feedback control that depends on knowledge of the complete network state is called a state-feedback, while a control scheme that only requires the existing sensor information from the monitored nodes is called output-feedback control.
On the basis of the above discussion and terminology, the problem considered in this paper consists of designing a decentralized output-feedback control strategy to ensure the stabilization of the desired extinction state over the complex network . In particular, this includes the determination of:
the set of
M nodes that have to be monitored, i.e.,
where the number
M has to be determined and
is the measurement vector,
the set of
K nodes to be controlled, i.e.,
where the number
K has to be determined and,
the feedback control laws for the nodes
where
is the part of the measurement vector
that has to be accessible to node
.
The approach for achieving this objective follows the constructive (passivity-based) control idea and consists of two steps: (i) assigning the necessary outputs so that the associated zero dynamics, i.e., the dynamics constrained to a submanifold:
is asymptotically stable, and (ii) designing the controllers
so that for some
, it holds that:
The decision about which nodes need to be measured will depend on the control laws to be designed and is addressed in the subsequent analysis.
3. Selection of Monitored and Controlled Nodes
In this section, the central question about which nodes should be monitored in order to ensure a stabilization of the desired state probability distribution
is addressed by determining a condition for exponential stability on the associated zero dynamics. Before analyzing this, notice that the fixed points associated with the dynamics (
5) for some constant
can be determined substituting the relation
. After some algebra, it follows that:
According to the above equation, we point out that the extinction state
is a fixed point when
; however, it is not clear if the extinction state or any other fixed point given by (
11) is stable. The extinction state means that no information is spreading. In the virus spreading context, this condition plays an important role in order to explain how a virus is propagated.
The following lemma gives an important basis for the subsequent analysis.
Lemma 1. The set is positively invariant for the dynamics (
6)
. Proof. Consider the case that for some
, it holds that
for some
. By (
5), it follows that
. On the other hand, assume that
for some
. It follows that
. Thus, for all
, it holds that
for all
, showing that
is a positively invariant set for the dynamics (
6). ☐
For the purpose of analyzing the stability properties, consider a constant
in the dynamics (
6) with the fixed point given by (
11). The following fundamental result on the stability of the origin of the dynamics (
6) is obtained using a similar reasoning as in the analysis of epidemic spreading in [
8].
Lemma 2. Consider the dynamics (
6)
on a complex network with graph and adjacency matrix , and let be a function satisfying (
2)
and (
4)
. Then, the origin of the dynamical system (
6)
is globally asymptotically stable if the constants are such that:where and are defined in (
7)
and is the spectral radius of a matrix. Proof. Using the mean value theorem [
39] over
in order to proof the Lemma, one obtains:
where
denotes the gradient with respect to the vector
P.
Recalling that when
, the neighbor nodes of
do not contribute to spreading the information and, therefore,
, it follows from the mean value theorem that:
Substituting the above equation into (
5), one obtains:
Taking the absolute values on both sides of (
14) yields:
By (
2), the slope of
is bounded, so it holds that:
Consider the auxiliary states
, so that
and:
These dynamics can be written in vector form as:
with
and
and
defined in (
7). It follows that
if and only if
, i.e., all eigenvalues of
are within the unit circle around the origin in the complex plane. As for all
, it holds that
, and it follows that
for all initial values
. ☐
The asymptotic stability condition (
12) is of a very general nature, given that it involves the complete network. One can refine it to gain insight into the conditions that every node
has to satisfy in order to ensure that the complete state
converges to
.
Lemma 3. For a constant and for every , the state vector globally asymptotically converges to the desired state if: Proof. The proposition is proven according to Gerschgorin’s theorem [
40], which provides an upper-bound estimate for the spectral radius of a given matrix. For the matrix
, the theorem yields the following inequality:
where
represents an eigenvalue of matrix
. The above inequality is bounded as follows:
Now, the solution of (
16) converges asymptotically to zero if
. Therefore, we bound the above inequality as follows:
Given that for all
, it holds that
, a sufficient condition to ensure asymptotic convergence in (
15), and therefore in (
5), is given by:
This completes the proof. ☐
Note that if this condition does not hold, it gives a hint about how to choose the nodes to be monitored. Under this hypothesis, it seems appropriate to consider the set of controlled nodes
as those nodes that do no satisfy the condition (
17) and the monitored nodes as those neighbor nodes
of the controlled node
including the controlled node
. As we will show later, it is sufficient to take
.
Provided a controller exists, which steers the controlled nodes
exponentially to
, the dynamics converges exactly to the submanifold
defined in (
9), called the zero dynamics [
32,
41]. By the control action, this manifold is a positively invariant subspace of
. Furthermore, note that with the monitored nodes
, they no longer influence the spreading process, so that the zero dynamics correspond to a spreading process over a reduced network, from which the monitored nodes have been withdrawn. As the nodes included in this reduced network by construction satisfy Condition (
17), the desired state vector
is the unique attractor fixed point in
. This is summarized in the following corollaries.
Corrollary 1. If the nodes that do not satisfy the condition (
17)
are controlled, then the zero-dynamics has as the unique asymptotically stable fixed-point. Note that the establishment of the asymptotic stability of
for the zero dynamics is a key step in the constructive control approach [
41], but does not yet ensure the asymptotic stability of
. This will be addressed later.
The condition (
17), for a given node
, establishes a relation between the amount of the interaction neighbors-to-node, with the properties of the node (given by
). A high interaction neighbors-to-node, regardless of the number of neighbors, can produce the spreading of information over the network. Thus, these nodes should be controlled.
On the other hand, it is possible to establish an alternative bounding dynamics for (
5) in the same sense of Lemma 3, which yields the stability condition stated next.
Lemma 4. For a constant , the state vector globally asymptotically converges to the desired state if: Proof. Consider the average probability of (
5) and (
13) as follows:
Taking the absolute value on the above equation and recalling (
2) as in the proof of Lemma 2, it follows that:
The last term in the above inequality includes the entries of the matrix
and the state vector
as follows:
Note that the summation in (
19) is performed over each entry of the vector
, where
i represents the
i-th row entry. Therefore, it is possible to rearrange the above vector as follows:
Summing over each entry of the column vector, and later over each column, we have:
Associating the corresponding terms for every node
, we obtain:
Consider the auxiliary states
,
, so that
and:
A condition to ensure asymptotic convergence to zero in (
20) is given by:
Hence, given that
, the above inequality is a sufficient condition to ensure asymptotic convergence in the dynamics (
5). ☐
The preceding result gives another criterion about how to choose nodes to be monitored. In this case, the set of controlled nodes
contains those nodes
that do not satisfy (
18), but it is not clear which nodes have to be monitored. However, the vectors
(
) in (
18) have something in common: all have the same entry
. Thus, in this case, it seems appropriate considering that
. Finally, the dynamics (
20) establishes an alternative upper bound for (
5).
In the same sense of the condition of Lemma 3, if the controlled nodes are chosen as those that do not satisfy the condition (
18), then by construction, the zero-dynamics has the origin as the asymptotically-stable fixed point, and this is summarized in the following corollary.
Corrollary 2. If the nodes that do not satisfy the condition (
18)
are controlled, then the zero-dynamics is asymptotically stable. Note that the condition (
18) has a similar interpretation as the condition (
17). In this case, a high interaction node-to-neighbors, regardless of the number of neighbors, can produce information spreading over the network. Therefore, those nodes that do not satisfy the above condition should be controlled.
4. Feedback Control Design
In this section, the question is addressed about how to design the feedback control (
8) for the nodes
so that
. Up to this point, the dependency of the transition probability
on the control input
has been neglected, given that
was considered as a set of constant parameters. For the nodes to be controlled, it is now supposed that the dependency of
on
is of a certain structure, which allows one to explicitly determine a control law that steers the nodes
to their desired values
. Before addressing the control design step, the following helpful result is established.
Lemma 5. Let with and , then for all j such that .
Proof. By virtue of the mean value theorem, it holds that:
where
,
. Recalling the condition (
4), having
, it follows that:
This completes the proof. ☐
On the basis of the above developments, the set
of nodes to be controlled is determined either according to Corollary 1 or Corollary 2, i.e., those nodes that do not satisfy either (
17) or (
18). For both cases, a sufficient condition for the asymptotic stability of the closed-loop system is provided next.
Theorem 1. Consider the dynamics (
5)
where the set of nodes to be controlled is determined according either according to Corollary 1 or 2, i.e., is the set of those nodes that do not satisfy either (
17)
or (
18)
, respectively. Let , i.e., all controlled nodes are monitored, and let for all the value be such that the condition (
17)
or (
18)
, respectively, holds true. If the controls satisfy:then . Proof. Let
be such that for all nodes
whose control input appears in
, its value is replaced by
. Given
, it follows from Lemma 5 that
, and thus:
The above inequalities satisfy Lemmas 3 and 4, respectively, so . ☐
From Theorem 1, in order to stabilize the system (
5) to the extinction state, it is necessary to design a feedback control
,
, that takes values below the upper-bound
. This can be ensured, e.g., by the linear feedback control:
5. Feedback Control Example
To corroborate our results, we design a feedback control in the model proposed by Gomez [
11] in order to stabilize the system to the extinction state. This is a discrete-time Markov contact-based epidemic spreading model that establishes the probability of infection of each node. However, we do not consider reinfection in the same time step, and in contrast with Gomez’s model, each node has different values for the recovery probability (
), infection rate (
) and contact probability (
r).
The probability of infection of each node
i at time
is given by:
where
is the probability for node
i to be not infected by any neighbor and
are the entries of the corresponding adjacency matrix. The network is described by the set of nodes
V, and the set of neighbors of node
i is given by
,
. There are
nodes in the network, and each node
i has a degree
. According to our framework,
is given by:
Suppose that the parameters that are amenable to manipulation are
and/or
, i.e., we assume that it is possible to improve the health of the nodes or avoid a node performing several contact attempts with its neighbors. Accordingly, the entries of the vector
are given by the infection rate (
) and the contact probability (
r), i.e.,
The fixed points
associated with the dynamics (
21) are:
for some constant values
and
. Note that
is a fixed point that represents the extinction state, but its stability is unknown. However, Lemmas (3) and (4) give us sufficient conditions to ensure asymptotic stability in the extinction state of the system (
21).
According to our definition for
, it is necessary to determine if
satisfy conditions (
2) and (
4), i.e., we have to prove that
strictly monotonically increases with
and to find a
strictly monotonically increases with
.
Condition (
2) can be established taking the derivative with respect to
as follows:
The above equation shows that monotonically increases with , and its arguments are reduced to .
The second condition is proven taking the derivative with respect to
(
):
and then with respect to
(
):
In both cases, monotonically increases with or r.
Using Lemmas (3) and (4), we can conclude that the system (
21) globally asymptotically converges to the desired state
, if all nodes
satisfy any of the following conditions:
or:
Note that the above conditions give us a hint about how to design a feedback control to stabilize the extinction state and to assign the output of the system:
or:
5.1. Simulations
We perform several simulations of the dynamical system (
21) for different initial conditions, with the following considerations:
We incorporate preferential attachment in a network with
nodes, according to [
22]. To incorporate the growing character of the network, we started with a small number
of vertices (linked randomly), and at every time step, we add a new vertex with
edges until we reach
nodes. In spite of the fact that we are using a scale-free network, we emphasize that our results are independent of the network’s topology.
The constant values for the recovery probability (), infection rate () and contact probability () were distributed uniformly over the nodes with values into the interval .
In order to verify our results, we calculated the average probability as follows:
The system simulated is given by:
where:
where
is the set of those nodes
i that do not satisfy (
25) and
is the set of those nodes
i that do not satisfy (
26).
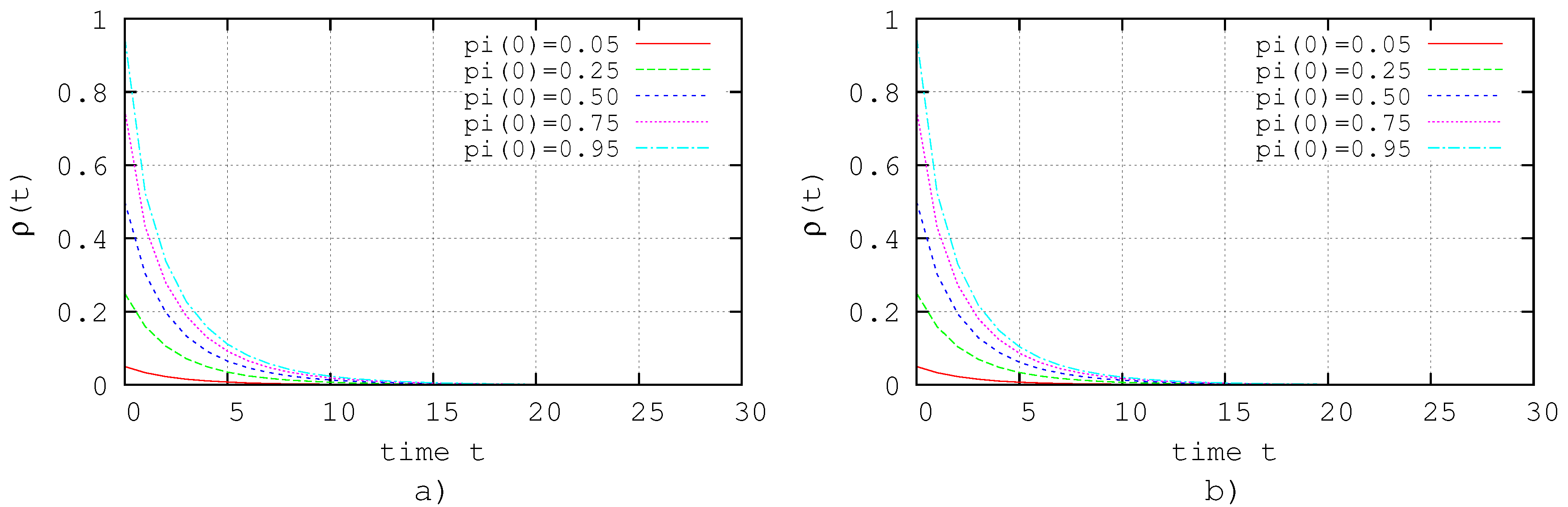
5.1.1. Behavior of the System in the Absence of Control
Figure 2 shows the simulations results for the system (
30) in the absence of control. The result shows that the system (
30) presents an endemic state independent of the initial conditions, and it shows that about 30% of the nodes are probably infected.
Our results give us 495,091 nodes do not satisfy Condition (
25) and 477,061 nodes that do no satisfy (
26); therefore, we identify these nodes as the nodes to be controlled and monitored in order to steer the system to the extinction state.
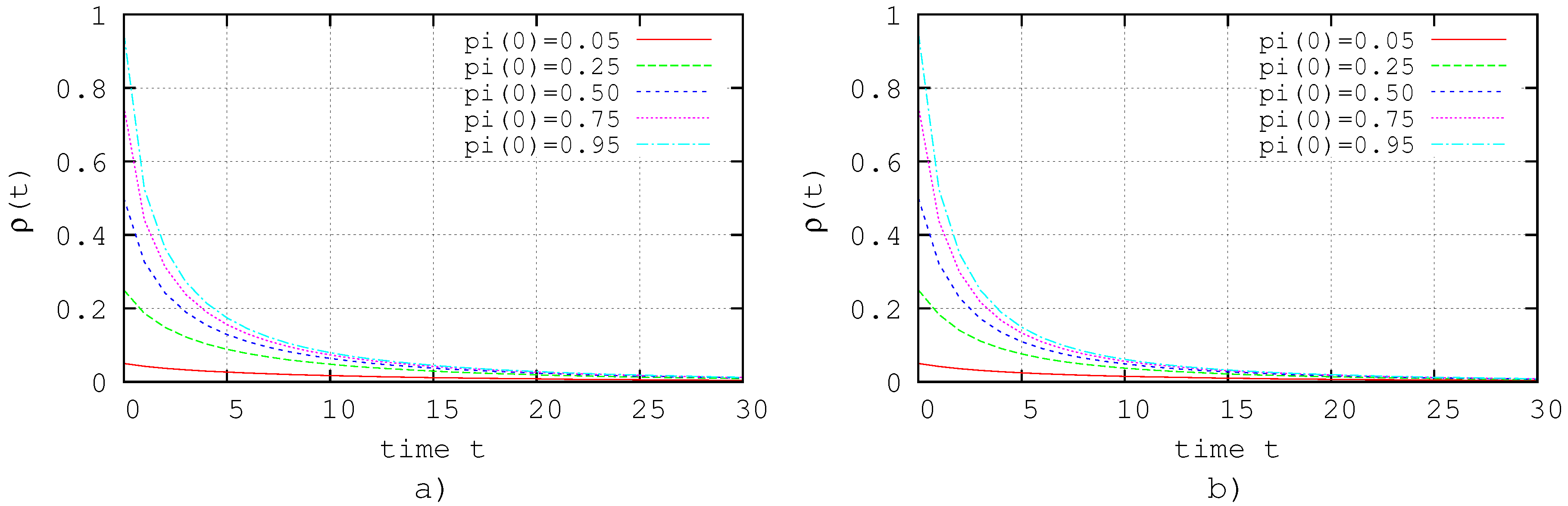
5.1.2. Behavior of the Nodes Associated with the Zero Dynamics
In order to corroborate that the associated zero dynamics is asymptotically stable, we set
, i.e., for those nodes that do not satisfy (
25), we consider
, and for those nodes that do not satisfy (
26), we consider
; the action of considering
or
is equivalent to unlinking the node
i.
Under this conditions, the dynamical evolution of the system (
30) is shown in
Figure 3a,b. Note that, in both cases, the extinction state is reached after 15 time steps approximately.
5.1.3. Behavior of the System with a Linear Feedback Control
We perform two separate simulations that will show the dynamical evolution of the system when a control is implemented. In the first one, we propose a linear control that will act only on those nodes that do not satisfy Condition (
25). In the second one, a linear control will act only on those nodes that do not satisfy Condition (
26). According to Theorem 1, we must establish an upper bound, in either case, namely
and
, respectively. These upper bounds can be determined using Equation (
25) or (
26). For Condition (
25), we have:
and for Condition (
26):
Note that (
31) relates the infection probability
of the node
i with its recovery probability
and the contact capacity of its neighbor nodes, given by
. On the other hand, Equation (
32) relates the contact probability
of the node
i, with its recovery probability
and the infection capacity of its neighbor nodes, given by
. This means that a node with a high rate of contact can be infected with a great probability; besides, a node with weak neighbor nodes (those with a high probability of infection) can be a focus of infection, as is intuitively clear.
Thus, the controls proposed should be such that:
It follows that for the nodes that do not satisfy (
25), the control proposed could be given by:
and for those nodes that do not satisfy (
26):
Note that both controls above depend on the state of the node
i given by
and the properties of its neighbor nodes given by
and
. The value
must be in the interval
in order to satisfy (
33).
Figure 4a,b shows the results of the simulation of the system (
30) with the applied controls (
34) and (
35), respectively, with
. In both cases, it is shown that the extinction state is a closed-loop attractor, although not as fast as in the case of
Figure 3a,b, corresponding to the evolution of the zero dynamics.