Fruit-80: A Secure Ultra-Lightweight Stream Cipher for Constrained Environments
Abstract
1. Introduction
“We would like to point out that, in our opinion, the existence of distinguishing attacks with a complexity below that of exhaustive key search should not be a knock-out criterion for stream ciphers targeting ultra-lightweight applications because such attacks might actually be tolerable depending on the application scenario”.[24]
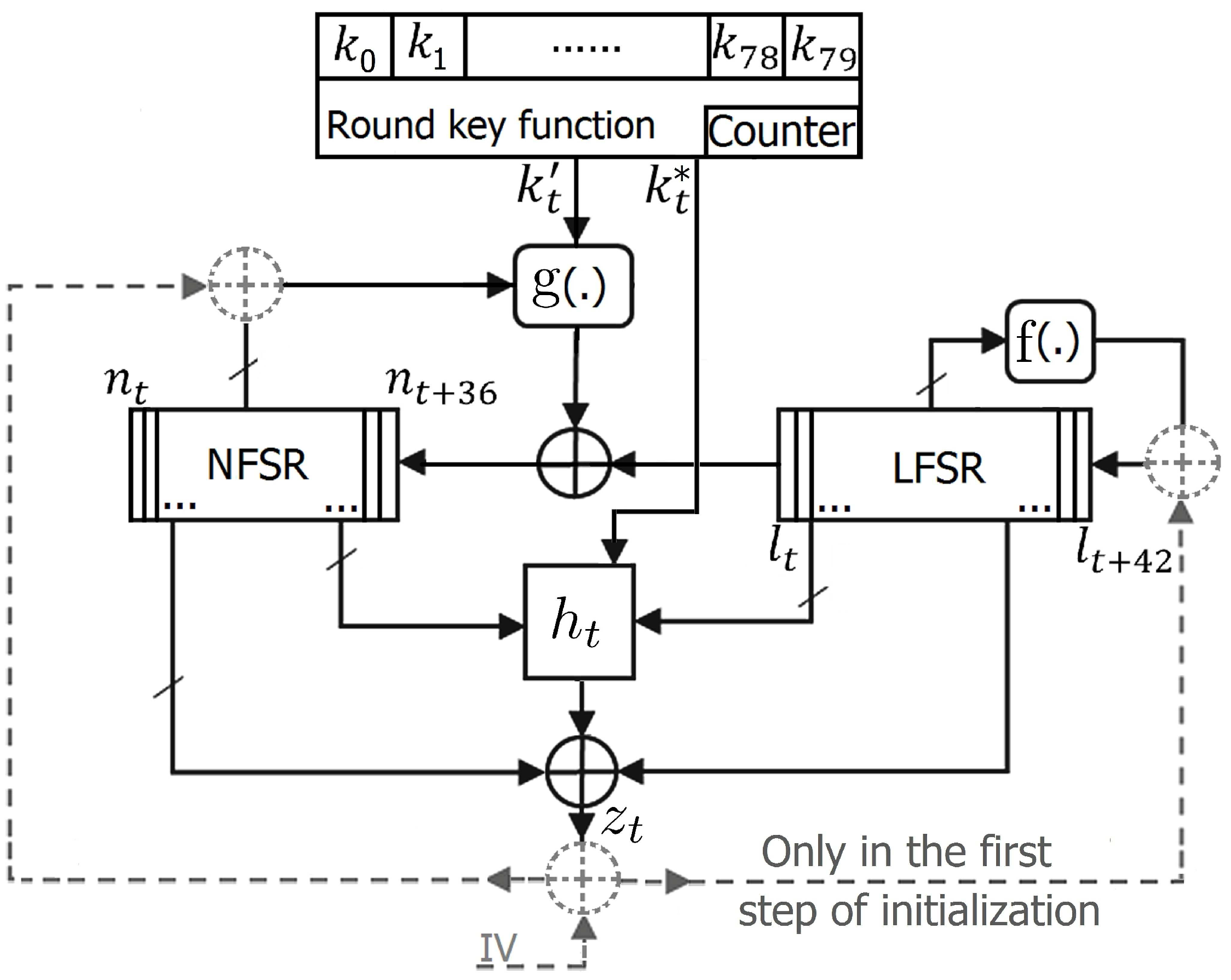
2. The Design of Fruit-80
2.1. Round Key Function
2.2. g Function
2.3. f Function
2.4. h Function
2.5. Output Function
2.6. Initialization of the Cipher
3. The Design Criteria
3.1. Limitation for Producing Keystream
3.2. Round Key Function
3.3. g Function
3.4. f Function
3.5. Number of Clocks in the Initialization
3.6. Output Function
4. The Resistance to Known Attacks
4.1. TMDTO Attacks
TMDTO Distinguishing Attacks
4.2. Guess and Determine Attacks
4.3. Linear Approximation Attacks
4.4. Related-Key Attacks
4.5. Cube Attacks
4.6. Algebraic Attacks
4.7. Fault Attacks
4.8. Weak Key-IVs
5. Hardware Implementation
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A. Test Vector for Fruit-80
References
- Cannière, C.D. Trivium: A Stream Cipher Construction Inspired by Block Cipher Design Principles. Lect. Notes Comput. Sci. 2006, 4176, 171–186. [Google Scholar]
- Babbage, S.; Dodd, M. The Stream Cipher MICKEY 2.0. ECRYPT Stream Cipher. 2006. Available online: http://www.ecrypt.eu.org/stream/p3ciphers/mickey/mickey_p3.pdf (accessed on 6 March 2018).
- Hell, M.; Johansson, T.; Meier, W. Grain: A stream cipher for constrained environments. Int. J. Wirel. Mob. Comput. 2007, 2, 86–93. [Google Scholar] [CrossRef]
- Lee, Y.; Jeong, K.; Sung, J.; Hong, S. Related-Key Chosen IV Attacks on Grain-v1 and Grain-128. Lect. Notes Comput. Sci. 2008, 5107, 321–335. [Google Scholar]
- Hell, M.; Johansson, T.; Maximov, A.; Meier, W. A stream cipher proposal: Grain-128. In Proceedings of the IEEE International Symposium on Information Theory (ISIT 2006), Seattle, WA, USA, 9–14 July 2006. [Google Scholar]
- Aumasson, J.; Dinur, I.; Henzen, L.; Meier, W.; Shamir, A. Efficient FPGA Implementations of High-Dimensional Cube Testers on the Stream Cipher Grain-128. IACR Cryptol. ePrint Arch. 2009, 2009, 218. [Google Scholar]
- Dinur, I.; Güneysu, T.; Paar, C.; Shamir, A.; Zimmermann, R. An Experimentally Verified Attack on Full Grain-128 Using Dedicated Reconfigurable Hardware. Lect. Notes Comput. Sci. 2011, 7073, 327–343. [Google Scholar]
- Dinur, I.; Shamir, A. Breaking Grain-128 with Dynamic Cube Attacks. Lect. Notes Comput. Sci. 2011, 6733, 167–187. [Google Scholar]
- Knellwolf, S.; Meier, W.; Naya-Plasencia, M. Conditional Differential Cryptanalysis of NLFSR-Based Cryptosystems. Lect. Notes Comput. Sci. 2010, 6477, 130–145. [Google Scholar]
- Mihaljevic, M.J.; Gangopadhyay, S.; Paul, G.; Imai, H. Generic cryptographic weakness of k-normal Boolean functions in certain stream ciphers and cryptanalysis of grain-128. Period. Math. Hung. 2012, 65, 205–227. [Google Scholar] [CrossRef]
- Stankovski, P. Greedy Distinguishers and Nonrandomness Detectors. Lect. Notes Comput. Sci. 2010, 6498, 210–226. [Google Scholar]
- Ågren, M.; Hell, M.; Johansson, T.; Meier, W. Grain-128a: A new version of Grain-128 with optional authentication. Int. J. Wirel. Mob. Comput. 2011, 5, 48–59. [Google Scholar] [CrossRef]
- Banik, S.; Maitra, S.; Sarkar, S. A Differential Fault Attack on Grain-128a Using MACs. Lect. Notes Comput. Sci. 2012, 7644, 111–125. [Google Scholar]
- Ding, L.; Guan, J. Related Key Chosen IV Attack on Grain-128a Stream Cipher. IEEE Trans. Inf. Forensics Secur. 2013, 8, 803–809. [Google Scholar]
- Armknecht, F.; Mikhalev, V. On Lightweight Stream Ciphers with Shorter Internal States. Lect. Notes Comput. Sci. 2015, 9054, 451–470. [Google Scholar]
- Banik, S. Some Results on Sprout. Lect. Notes Comput. Sci. 2015, 9462, 124–139. [Google Scholar]
- Esgin, M.F.; Kara, O. Practical Cryptanalysis of Full Sprout with TMD Tradeoff Attacks. Lect. Notes Comput. Sci. 2015, 9566, 67–85. [Google Scholar]
- Hao, Y. A Related-Key Chosen-IV Distinguishing Attack on Full Sprout Stream Cipher. IACR Cryptol. ePrint Arch. 2015, 2015, 231. [Google Scholar]
- Lallemand, V.; Naya-Plasencia, M. Cryptanalysis of Full Sprout. Lect. Notes Comput. Sci. 2015, 9215, 663–682. [Google Scholar]
- Maitra, S.; Sarkar, S.; Baksi, A.; Dey, P. Key Recovery from State Information of Sprout: Application to Cryptanalysis and Fault Attack. IACR Cryptol. ePrint Arch. 2015, 2015, 236. [Google Scholar]
- Zhang, B.; Gong, X. Another Tradeoff Attack on Sprout-Like Stream Ciphers. Lect. Notes Comput. Sci. 2015, 9453, 561–585. [Google Scholar]
- Dey, S.; Sarkar, S. Cryptanalysis of full round Fruit. IACR Cryptol. ePrint Arch. 2017, 2017, 87. [Google Scholar]
- Ghafari, V.A.; Hu, H.; Xie, C. Fruit: Ultra-Lightweight Stream Cipher with Shorter Internal State. eSTREAM, ECRYPT Stream Cipher Project. 2016. Available online: https://eprint.iacr.org/2016/355.pdf (accessed on 6 March 2018).
- Hamann, M.; Krause, M.; Meier, W.; Zhang, B. Design and analysis of small-state grain-like stream ciphers. Cryptogr. Commun. 2017. [Google Scholar] [CrossRef]
- Zhang, B.; Gong, X.; Meier, W. Fast Correlation Attacks on Grain-like Small State Stream Ciphers. IACR Trans. Symmetric Cryptol. 2017, 2017, 58–81. [Google Scholar]
- Mikhalev, V.; Armknecht, F.; Müller, C. On Ciphers that Continuously Access the Non-Volatile Key. IACR Trans. Symmetric Cryptol. 2017, 2016, 52–79. [Google Scholar]
- Hamann, M.; Krause, M.; Meier, W. LIZARD—A lightweight stream cipher for power-constrained devices. IACR Trans. Symmetric Cryptol. 2017, 2017, 45–79. [Google Scholar]
- Sohraby, K.; Minoli, D.; Znati, T. Wireless Sensor Networks: Technology, Protocols, and Applications; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Zhang, H.; Wang, X. Cryptanalysis of Stream Cipher Grain Family. IACR Cryptol. ePrint Arch. 2009, 2009, 109. [Google Scholar]
- Hu, H.; Gong, G. Periods on Two Kinds of nonlinear Feedback Shift Registers with Time Varying Feedback Functions. Int. J. Found. Comput. Sci. 2011, 22, 1317–1329. [Google Scholar] [CrossRef]
- Biryukov, A.; Shamir, A.; Wagner, D. Real Time Cryptanalysis of A5/1 on a PC. Lect. Notes Comput. Sci. 2000, 1978, 1–18. [Google Scholar]
- Maximov, A. Cryptanalysis of the “Grain” family of stream ciphers. In Proceedings of the 2006 ACM Symposium on Information, Computer and Communications Security, Taipei, Taiwan, 21–24 March 2006; ACM: New York, NY, USA, 2006; pp. 283–288. [Google Scholar]
- Roy, D.; Mukhopadhyay, S. Fault analysis and weak key-IV attack on Sprout. IACR Cryptol. ePrint Arch. 2016, 2016, 207. [Google Scholar]
- Banik, S.; Maitra, S.; Sarkar, S. A Differential Fault Attack on the Grain Family of Stream Ciphers. Lect. Notes Comput. Sci. 2012, 7428, 122–139. [Google Scholar]
- Berzati, A.; Canovas, C.; Castagnos, G.; Debraize, B.; Goubin, L.; Gouget, A.; Paillier, P.; Salgado, S. Fault analysis of GRAIN-128. In Proceedings of the IEEE International Workshop on Hardware-Oriented Security and Trust, Francisco, CA, USA, 27 July 2009; pp. 7–14. [Google Scholar]
- Good, T.; Benaissa, M. Hardware performance of eStream phase-III stream cipher candidates. In Proceedings of the Workshop on the State of the Art of Stream Ciphers (SACS 2008), Lausanne, Switzerland, 13–14 February 2008. [Google Scholar]
- Fan, X.; Mandal, K.; Gong, G. WG-8: A Lightweight Stream Cipher for Resource-Constrained Smart Devices. ICST Trans. Secur. Saf. 2015, 2, e4. [Google Scholar] [CrossRef][Green Version]
- Golic, J.D. Cryptanalysis of Alleged A5 Stream Cipher. Lect. Notes Comput. Sci. 1997, 1233, 239–255. [Google Scholar]
| Cipher | Area Size (GE) | Throughput | Platform | Source |
|---|---|---|---|---|
| Mickey [2] | 3188 | 100 | 0.13 m CMOS | [36] |
| Trivium [1] | 2580 | 100 | 0.13 m CMOS | [36] |
| Grain-v1 [3] | 1294 | 100 | 0.13 m CMOS | [36] |
| Lizard [27] | 1161 | 100 | 0.18 m CMOS | [27] |
| Grain-v1 [3] | 1221 | 100 | 0.18 m CMOS | [36] |
| Plantlet [26] | 928 | 100 | 0.18 m CMOS | [26] |
| Grain-v1 [3] | 1162 | 100 | 0.18 m CMOS | [26] |
| Grain-v1 [3] | 1270 | 100 | 0.18 m CMOS | Our work |
| Lizard [27] | 1218 | 100 | 0.18 m CMOS | Our work |
| Plantlet [26] | 996 | 100 | 0.18 m CMOS | Our work |
| Fruit-80 | 960 | 100 | 0.18 m CMOS | Our work |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amin Ghafari, V.; Hu, H. Fruit-80: A Secure Ultra-Lightweight Stream Cipher for Constrained Environments. Entropy 2018, 20, 180. https://doi.org/10.3390/e20030180
Amin Ghafari V, Hu H. Fruit-80: A Secure Ultra-Lightweight Stream Cipher for Constrained Environments. Entropy. 2018; 20(3):180. https://doi.org/10.3390/e20030180
Chicago/Turabian StyleAmin Ghafari, Vahid, and Honggang Hu. 2018. "Fruit-80: A Secure Ultra-Lightweight Stream Cipher for Constrained Environments" Entropy 20, no. 3: 180. https://doi.org/10.3390/e20030180
APA StyleAmin Ghafari, V., & Hu, H. (2018). Fruit-80: A Secure Ultra-Lightweight Stream Cipher for Constrained Environments. Entropy, 20(3), 180. https://doi.org/10.3390/e20030180





