Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination
Abstract
:1. Introduction
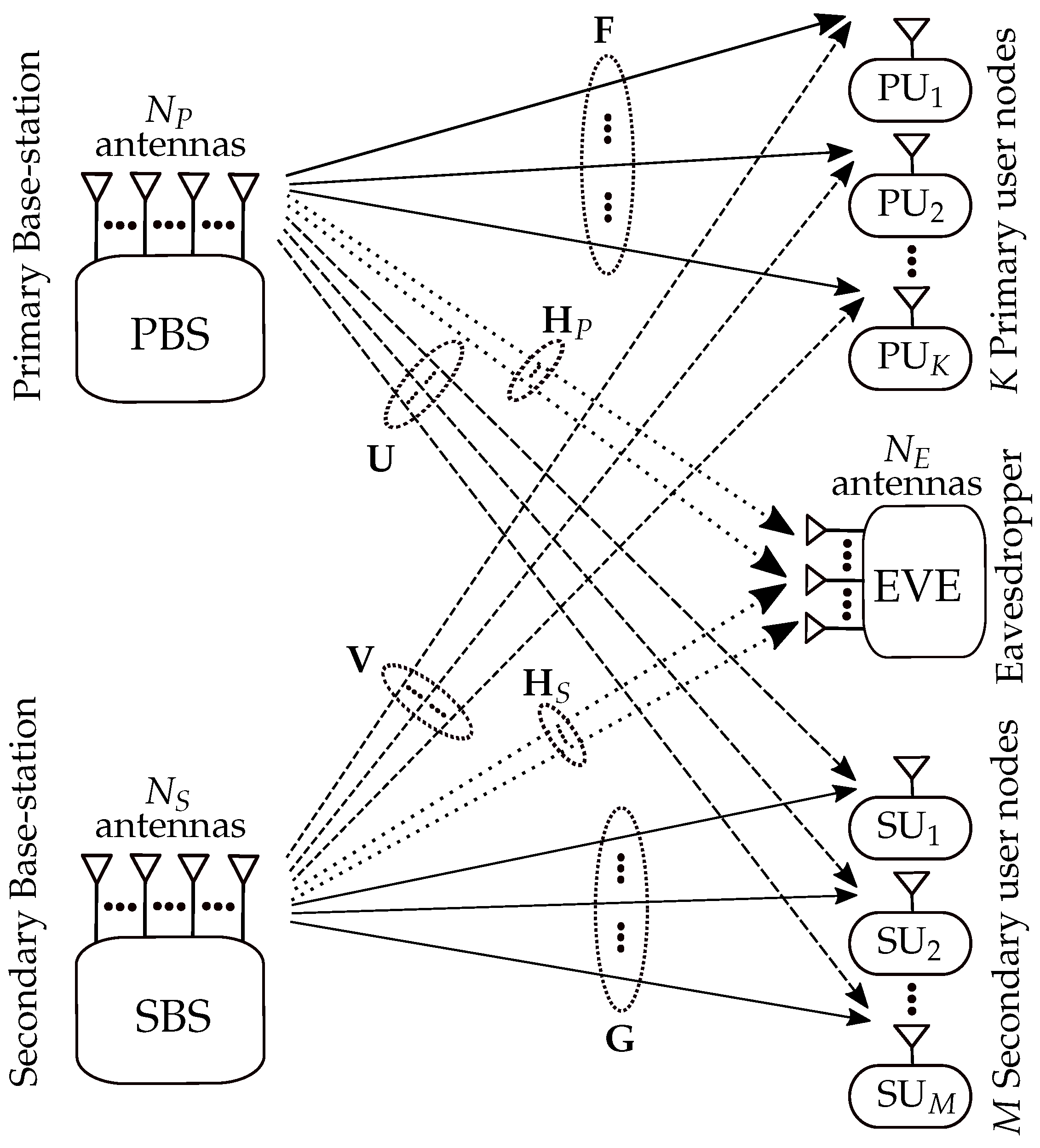
2. System, Channel, and Signal Models
2.1. System and Channel Model
2.2. Uplink Training and Channel Estimation
2.3. Signal Model
2.3.1. Transmit Power Constraint for the SBS
2.3.2. Signal Model for the Primary System
2.3.3. Signal Model for the Secondary System
2.3.4. Signal Model for the Eavesdropper
2.4. Achievable Rate Analysis
3. Secrecy Rate Analysis
4. Asymptotic Secrecy Rate Analysis
5. Performance Analysis for Perfect CSI
5.1. Secondary Transmit Power Constraint for Perfect CSI Case
5.2. Achievable Rate Analysis for Perfect CSI Case
5.3. Asymptotic Secrecy Rate Analysis for Perfect CSI Case
6. Numerical Results
7. Conclusions
Author Contributions
Conflicts of Interest
Appendix A. Derivations for the Performance Metrics for Imperfect CSI Case
Appendix A.1. Transmit Power Constraint at the Secondary System
Appendix A.2. for Finite Antenna Numbers
- Deriving : Similarly, can be derived as:
Appendix A.3. Asymptotic Achievable Rate at the Eavesdropper
Appendix B. Derivations the Asymptotic Performance Metrics for Perfect CSI
References
- Boccardi, F.; Heath, R.; Lozano, A.; Marzetta, T.; Popovski, P. Five disruptive technology directions for 5G. IEEE Commun. Mag. 2014, 52, 74–80. [Google Scholar] [CrossRef]
- Marzetta, T.L. Noncooperative Cellular Wireless with Unlimited Numbers of Base Station Antennas. IEEE Trans. Wirel. Commun. 2010, 9, 3590–3600. [Google Scholar] [CrossRef]
- Ngo, H.Q.; Larsson, E.G.; Marzetta, T.L. Energy and Spectral Efficiency of Very Large Multiuser MIMO Systems. IEEE Trans. Commun. 2013, 61, 1436–1449. [Google Scholar]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Liang, Y.; Poor, H.V.; Shamai, S. Information Theoretic Security. Found. Trends Commun. Inf. Theor. 2009, 5, 355–580. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- Kapetanovic, D.; Zheng, G.; Russek, F. Physical layer security for massive MIMO: An overview on passive eavesdropping and active attacks. IEEE Commun. Mag. 2015, 53, 21–27. [Google Scholar] [CrossRef]
- Schaefer, R.F.; Boche, H.; Khisti, A.; Poor, H.V. Information Theoretic Security and Privacy of Information Systems; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Poor, H.V.; Schaefer, R.F. Wireless physical layer security. Proc. Natl. Acad. Sci. USA 2016, 114, 19–26. [Google Scholar] [CrossRef] [PubMed]
- Goldsmith, A.; Jafar, S.A.; Maric, I.; Srinivasa, S. Breaking Spectrum Gridlock with Cognitive Radios: An Information Theoretic Perspective. Proc. IEEE 2009, 97, 894–914. [Google Scholar] [CrossRef]
- Liang, Y.; Somekh-Baruch, A.; Poor, H.V.; Shamai, S.; Verdú, S. Capacity of cognitive interference channels with and without secrecy. IEEE Trans. Inf. Theor. 2009, 55, 604–619. [Google Scholar] [CrossRef]
- Gabry, F.; Zappone, A.; Thobaben, R.; Jorswieck, E.A.; Skoglund, M. Energy Efficiency Analysis of Cooperative Jamming in Cognitive Radio Networks with Secrecy Constraints. IEEE Wirel. Commun. Lett. 2015, 4, 437–440. [Google Scholar]
- Zhu, J.; Schober, R.; Bhargava, V. Secure Transmission in Multicell Massive MIMO Systems. IEEE Trans. Wirel. Commun. 2014, 13, 4766–4781. [Google Scholar] [CrossRef]
- Zhu, J.; Schober, R.; Bhargava, V.K. Linear Precoding of Data and Artificial Noise in Secure Massive MIMO Systems. IEEE Trans. Wirel. Commun. 2016, 15, 2245–2261. [Google Scholar] [CrossRef]
- Guo, K.; Guo, Y.; Ascheid, G. Security-Constrained Power Allocation in MU-Massive-MIMO with Distributed Antennas. IEEE Trans. Wirel. Commun. 2016, 15, 8139–8153. [Google Scholar] [CrossRef]
- Wang, L.; Wong, K.K.; Elkashlan, M.; Nallanathan, A.; Lambotharan, S. Secrecy and Energy Efficiency in Massive MIMO Aided Heterogeneous C-RAN: A New Look at Interference. IEEE J. Sel. Top. Signal Process. 2016, 10, 1375–1389. [Google Scholar] [CrossRef]
- Yang, H.; Marzetta, T.L. Performance of Conjugate and Zero-Forcing Beamforming in Large-Scale Antenna Systems. IEEE J. Sel. Areas Commun. 2013, 31, 172–179. [Google Scholar] [CrossRef]
- Hassibi, B.; Hochwald, B.M. How much training is needed in multiple-antenna wireless links? IEEE Trans. Inf. Theor. 2003, 49, 951–963. [Google Scholar] [CrossRef]
- Tulino, A.M.; Verdú, S. Random matrix theory and wireless communications. Found. Trends Commun. Inf. Theor. 2004, 1, 1–128. [Google Scholar] [CrossRef]
- Cramer, H. Random Variables and Probability Distributions; Cambridge University Press: Cambridge, UK, 1970. [Google Scholar]




© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Hraishawi, H.; Baduge, G.A.A.; Schaefer, R.F. Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination. Entropy 2017, 19, 349. https://doi.org/10.3390/e19070349
Al-Hraishawi H, Baduge GAA, Schaefer RF. Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination. Entropy. 2017; 19(7):349. https://doi.org/10.3390/e19070349
Chicago/Turabian StyleAl-Hraishawi, Hayder, Gayan Amarasuriya Aruma Baduge, and Rafael F. Schaefer. 2017. "Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination" Entropy 19, no. 7: 349. https://doi.org/10.3390/e19070349
APA StyleAl-Hraishawi, H., Baduge, G. A. A., & Schaefer, R. F. (2017). Artificial Noise-Aided Physical Layer Security in Underlay Cognitive Massive MIMO Systems with Pilot Contamination. Entropy, 19(7), 349. https://doi.org/10.3390/e19070349




