A Machine Learning-Based Hybrid Encryption Approach for Securing Messages in Software-Defined Networking
Abstract
1. Introduction
- GA-based hybrid encryption approach as a network-wide policy is implemented.
- A comparative performance analysis with AES, DES, and RSA in terms of cryptographic strength is carried out.
- A discussion of the trade-off between security and network performance and strategies are presented.
2. Background and the Related Work
2.1. Background
2.2. Related Works
2.2.1. Encryption and Network Security in SDN
2.2.2. Security Policy Deployment in SDN
2.2.3. GA-Based Encryption
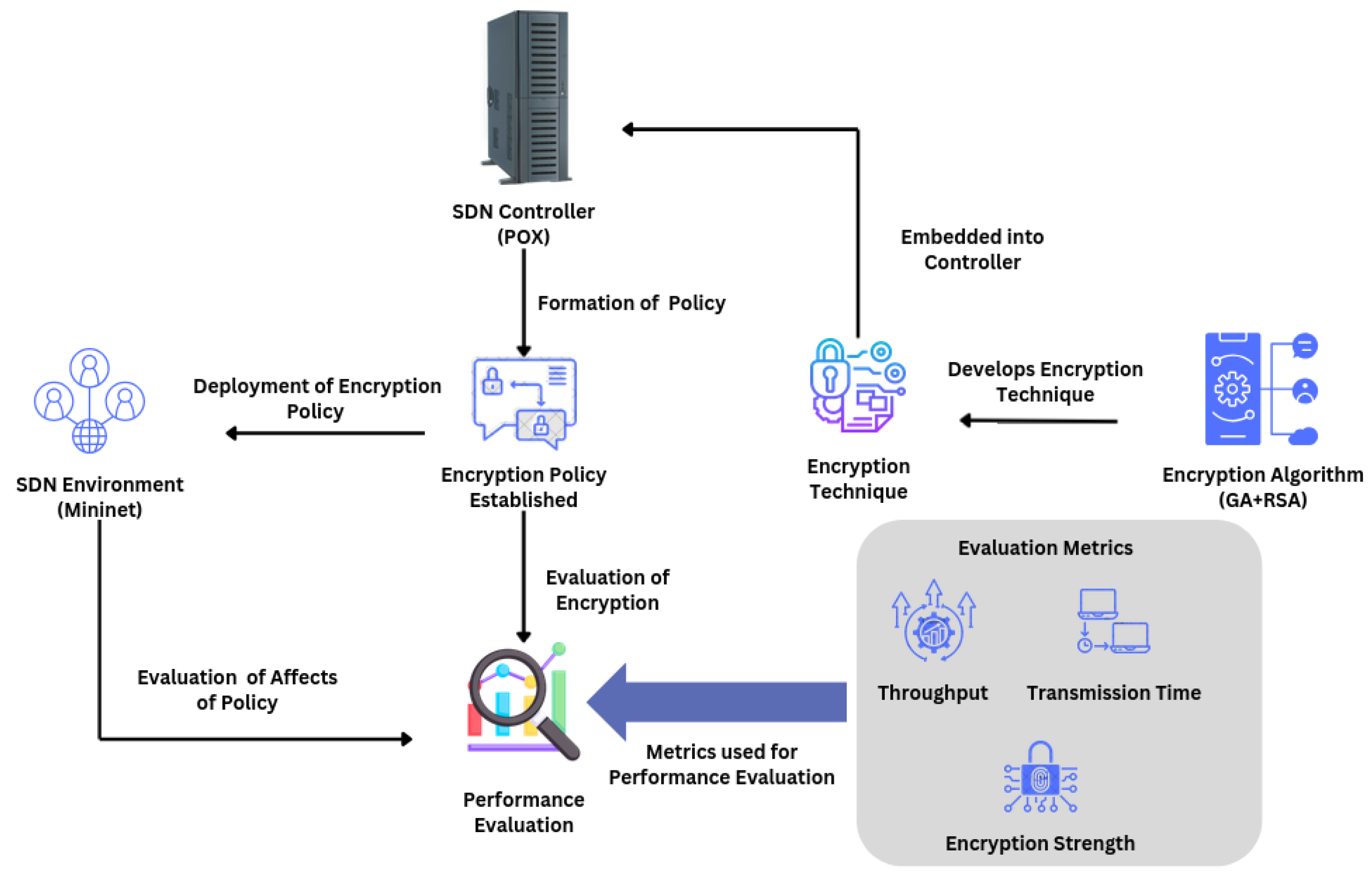
3. Methodology
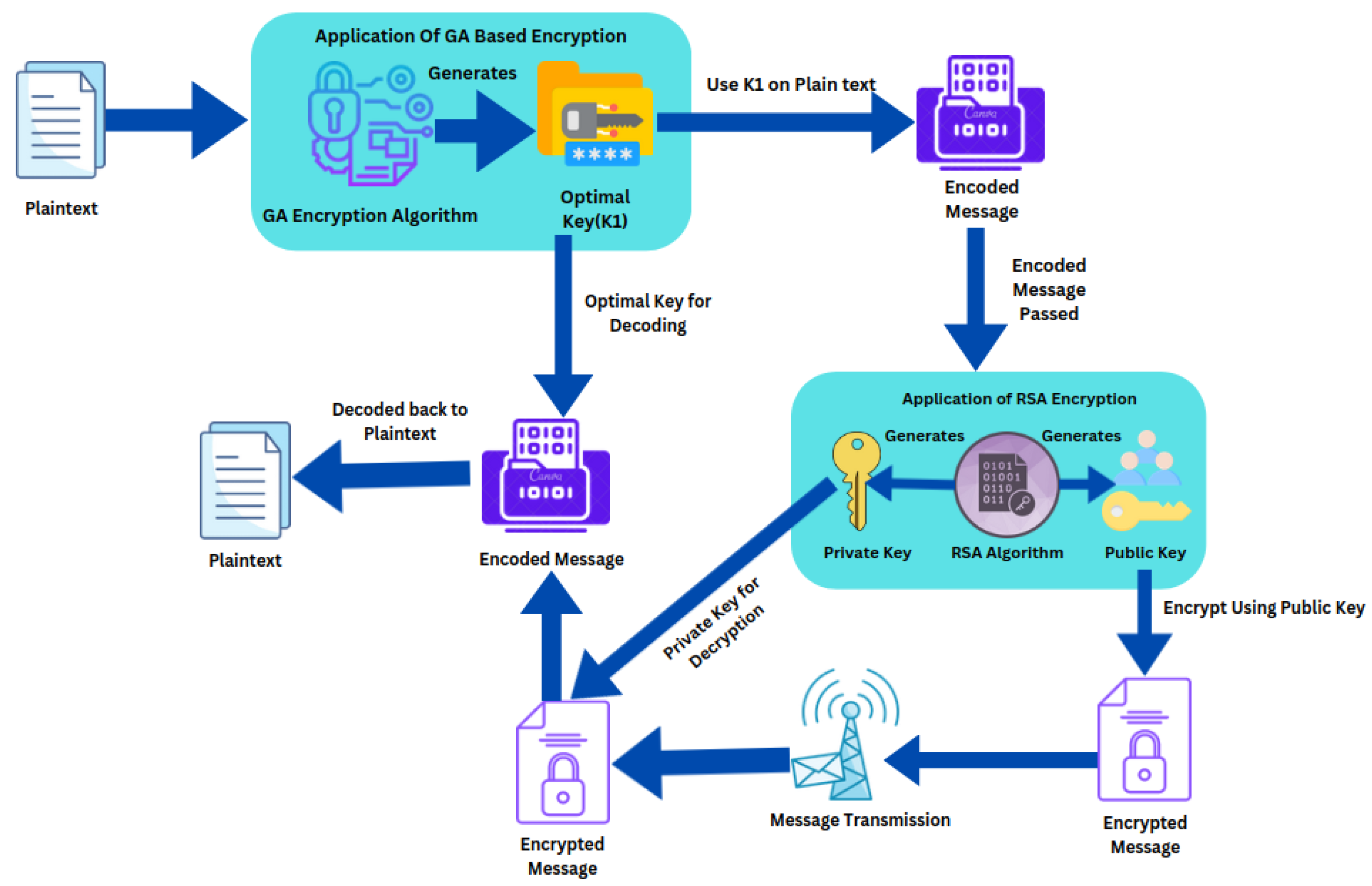
3.1. Development of Hybrid Encryption Technique
| Algorithm 1 Genetic algorithm-based encryption process. |
|
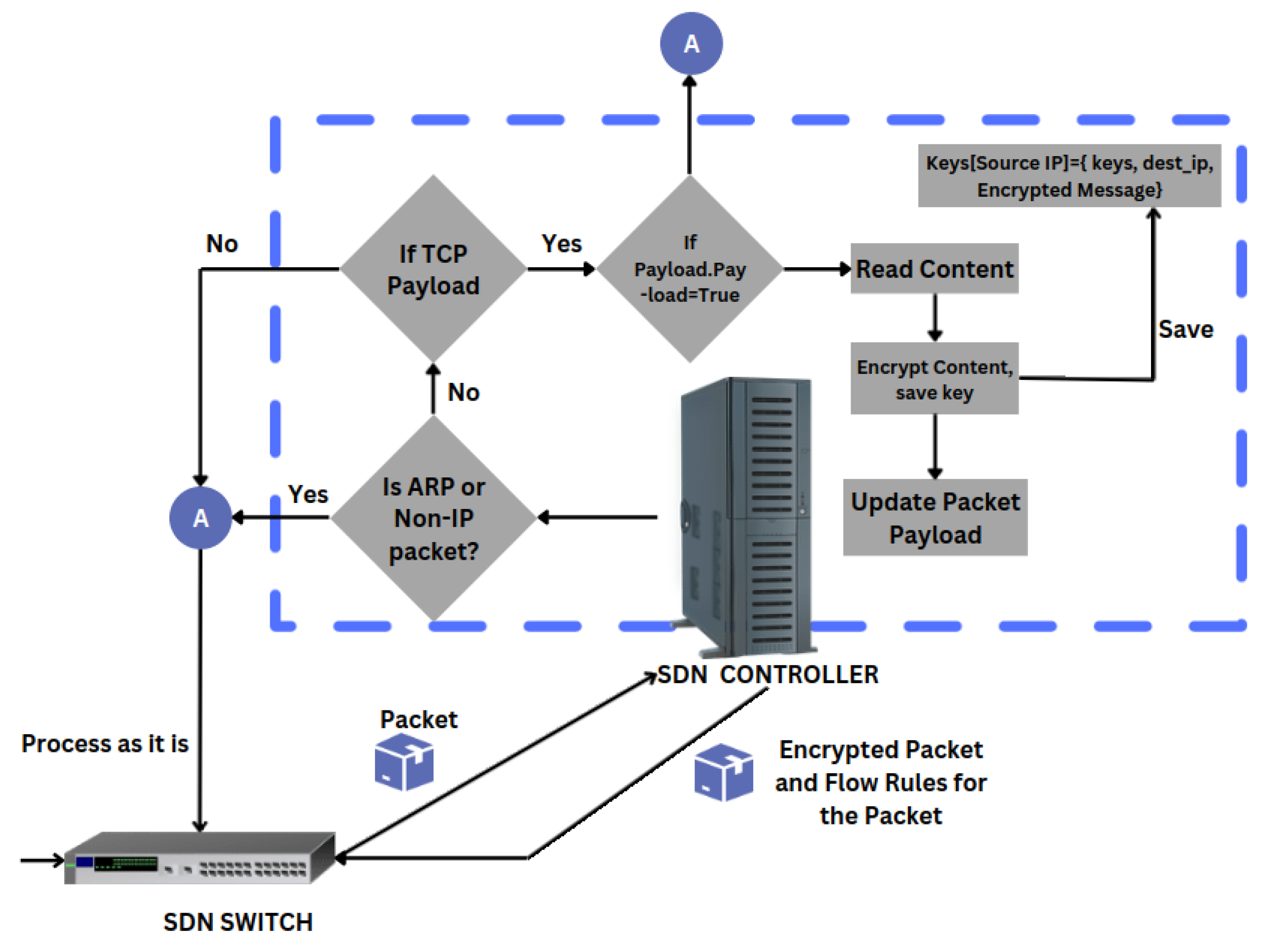
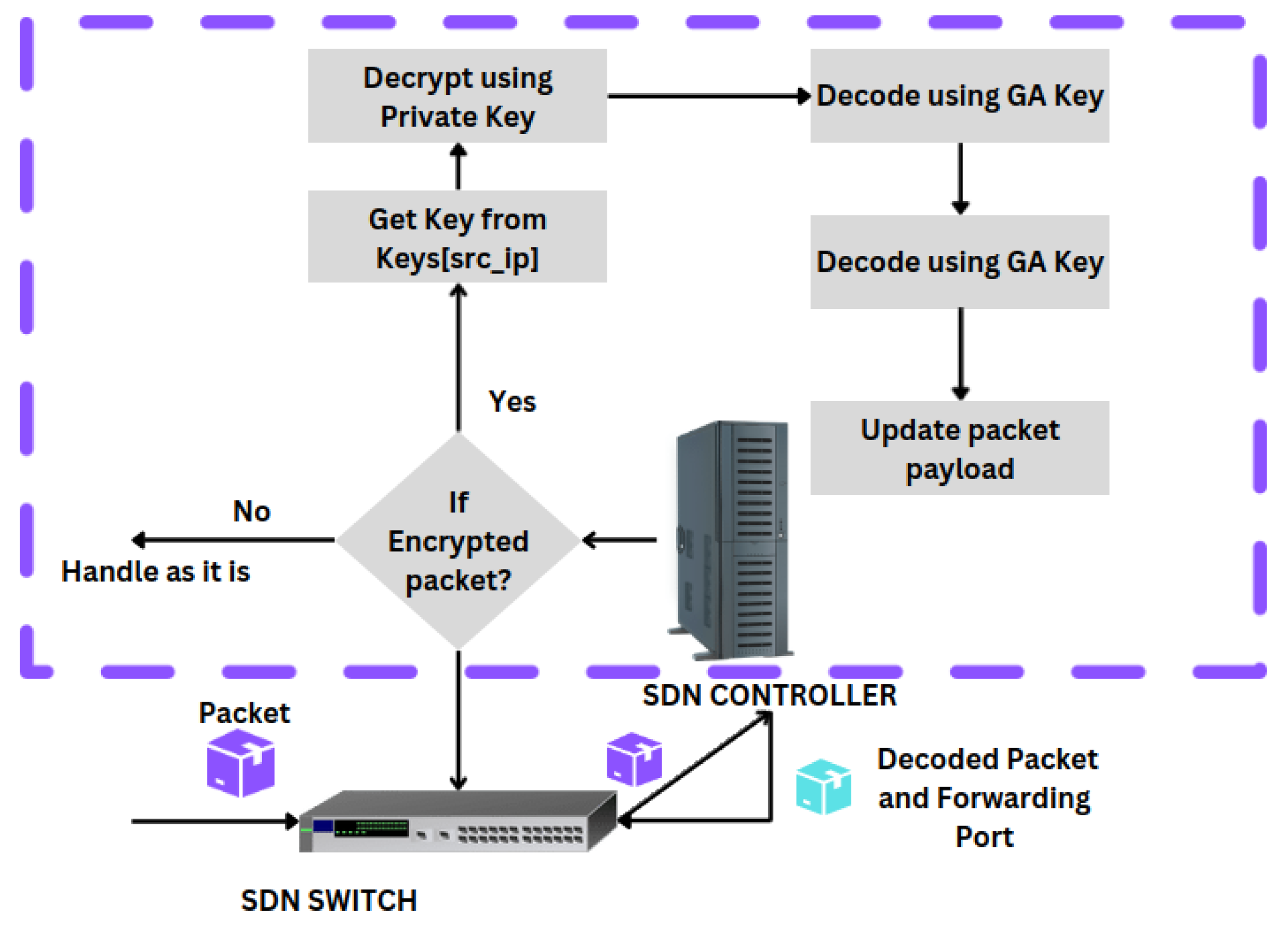
3.2. Programming the Controller
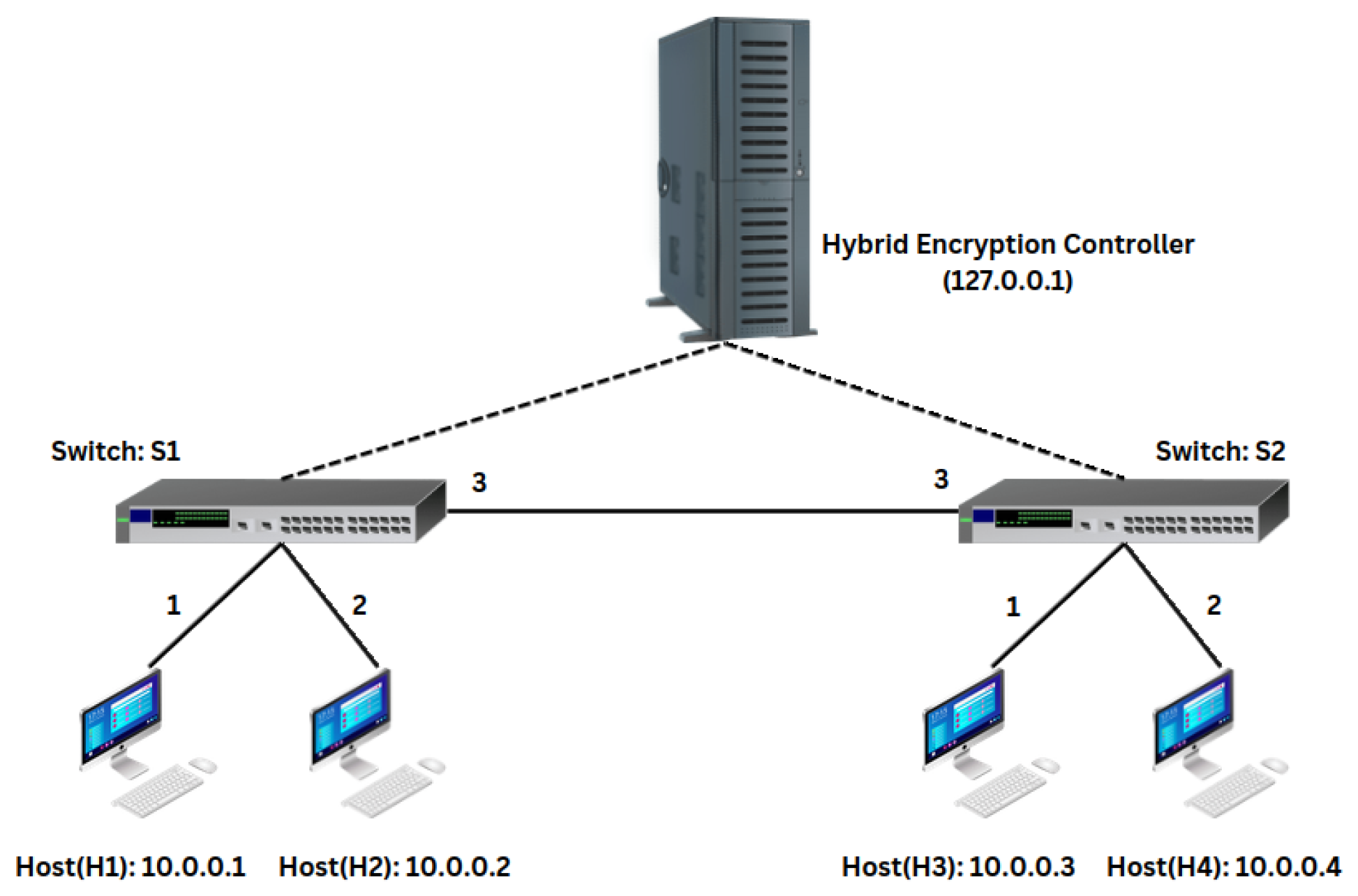
3.3. Encryption Logic Deployment in SDN Environment and Performance Evaluation
4. Results and Analysis
4.1. Evaluation of Hybrid Encryption Algorithm Strength
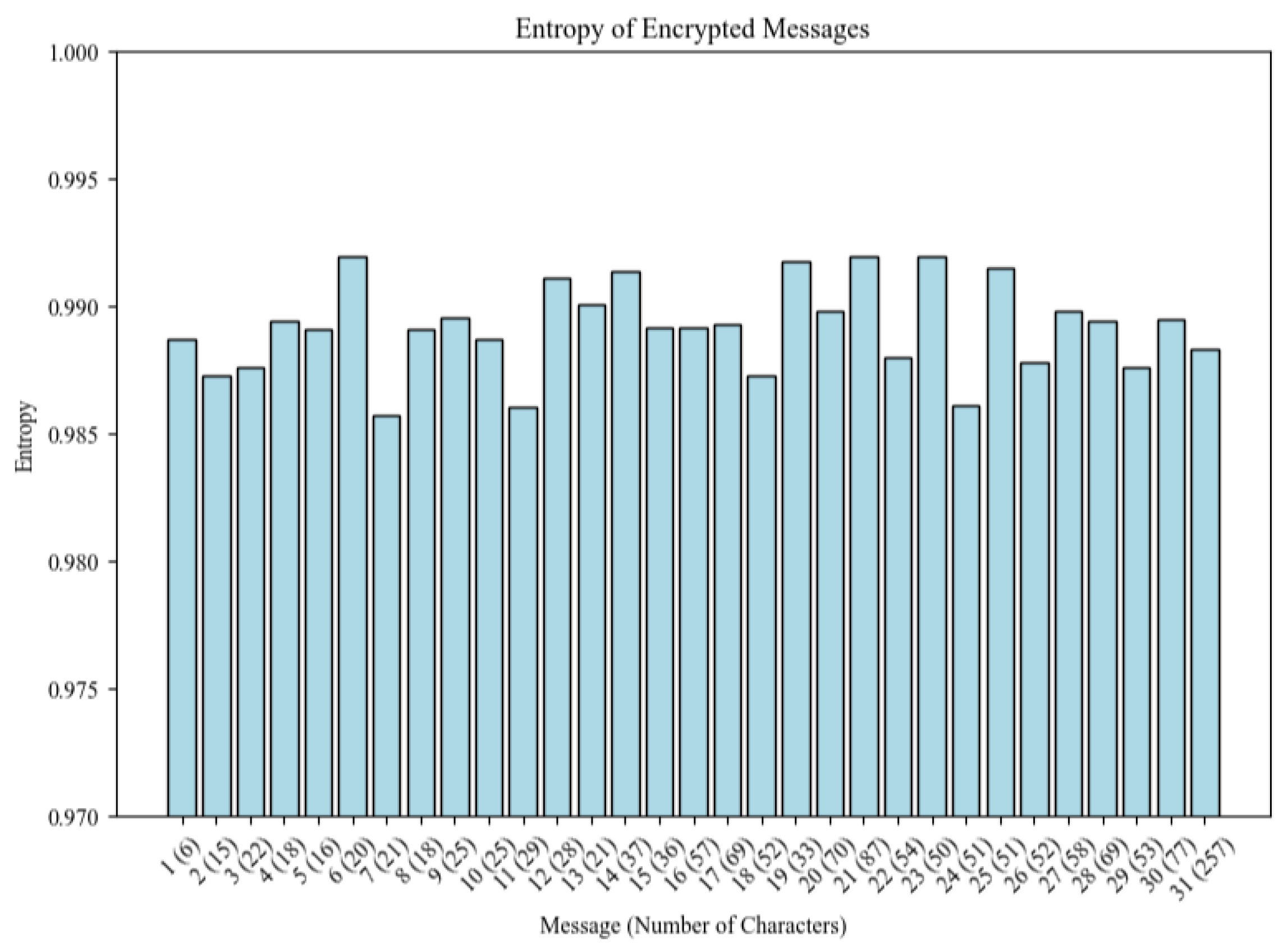
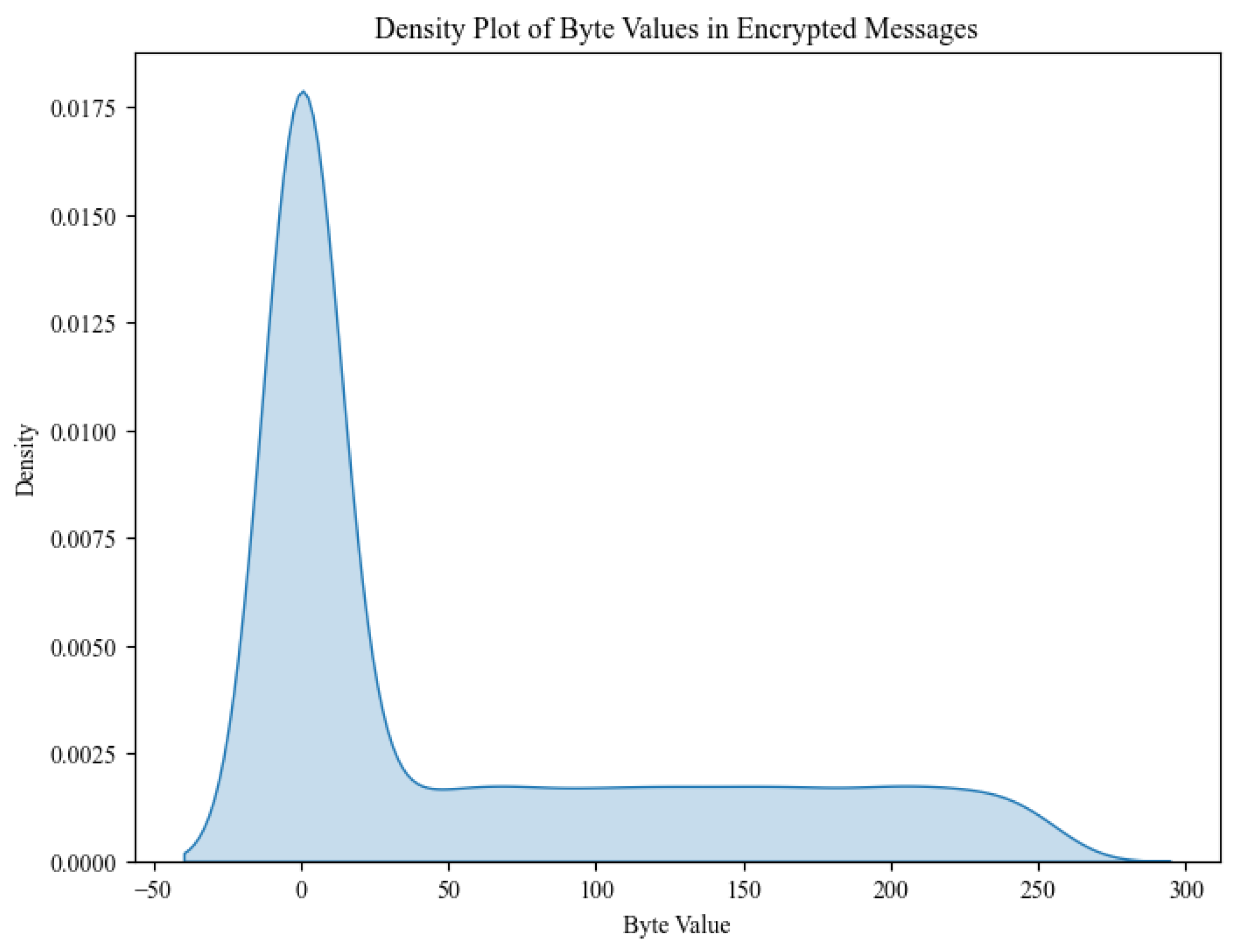
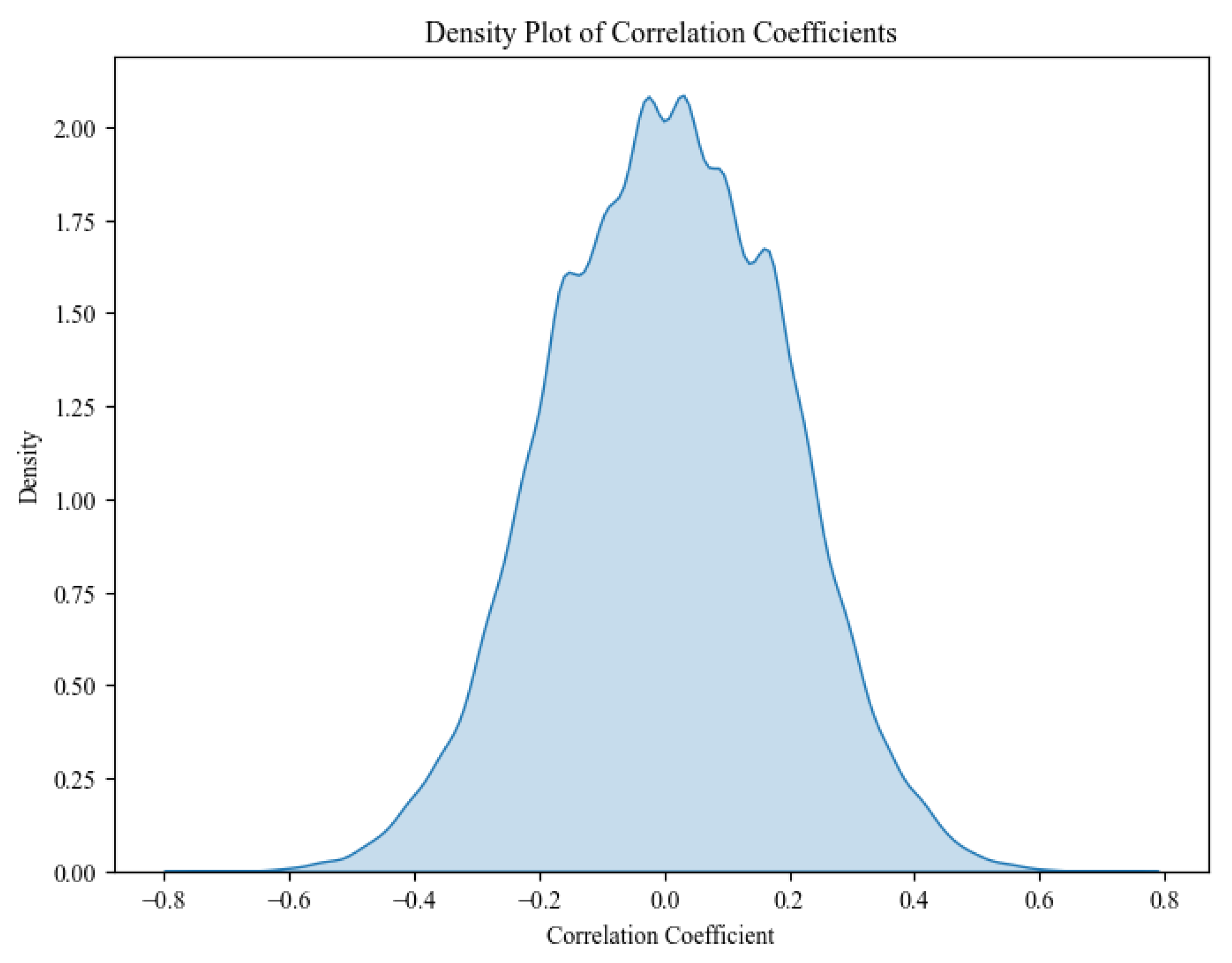
4.1.1. Entropy Analysis of Encryption
- -
- is the entropy of the random variable X.
- -
- is the probability of the outcome occurring.
- -
- n is the total number of possible outcomes for X.
- -
- denotes the logarithm to the base b, typically (binary entropy) or (natural entropy).
4.1.2. Pattern Analysis of Encryption Algorithm
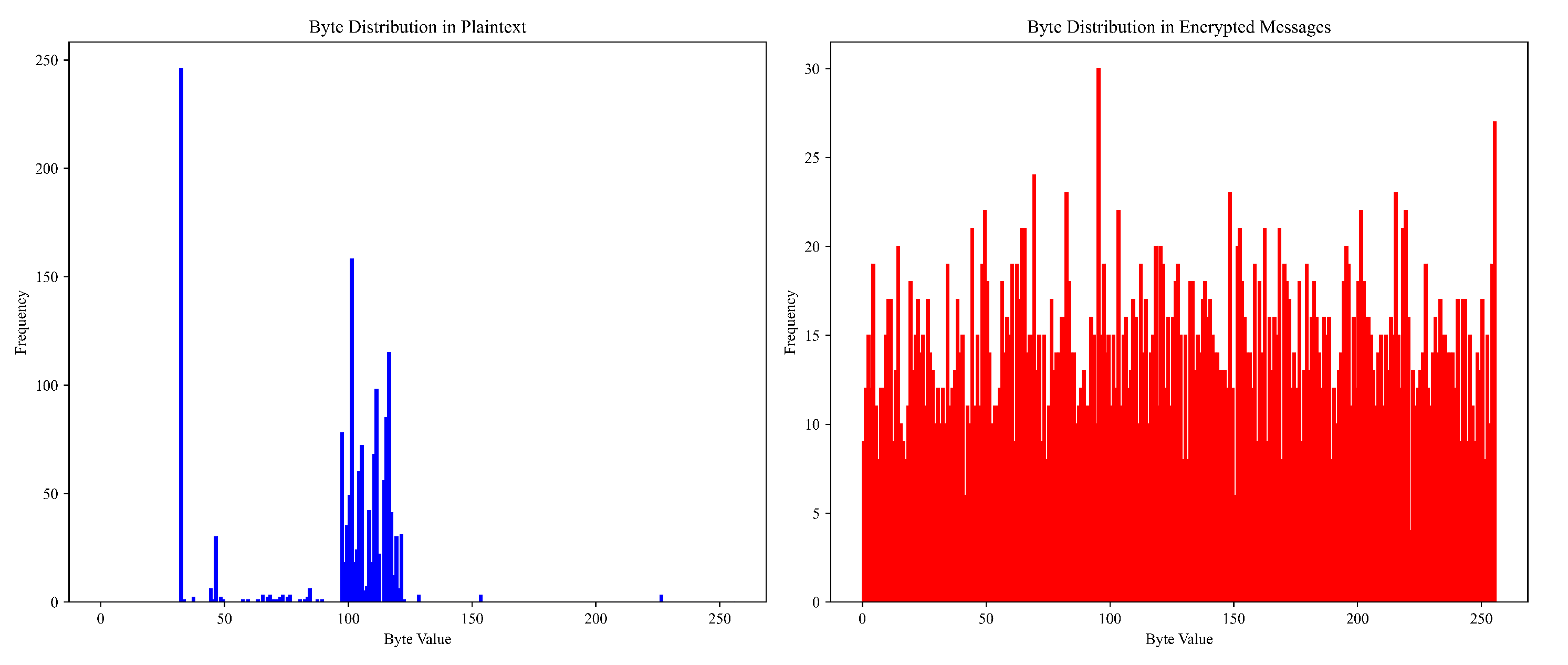
4.1.3. Comparative Statistical Byte Distribution Analysis of Plain- and Ciphertext
4.1.4. Differential Cryptanalysis
4.1.5. Linear Cryptanalysis
4.2. Network Parameter Evaluation
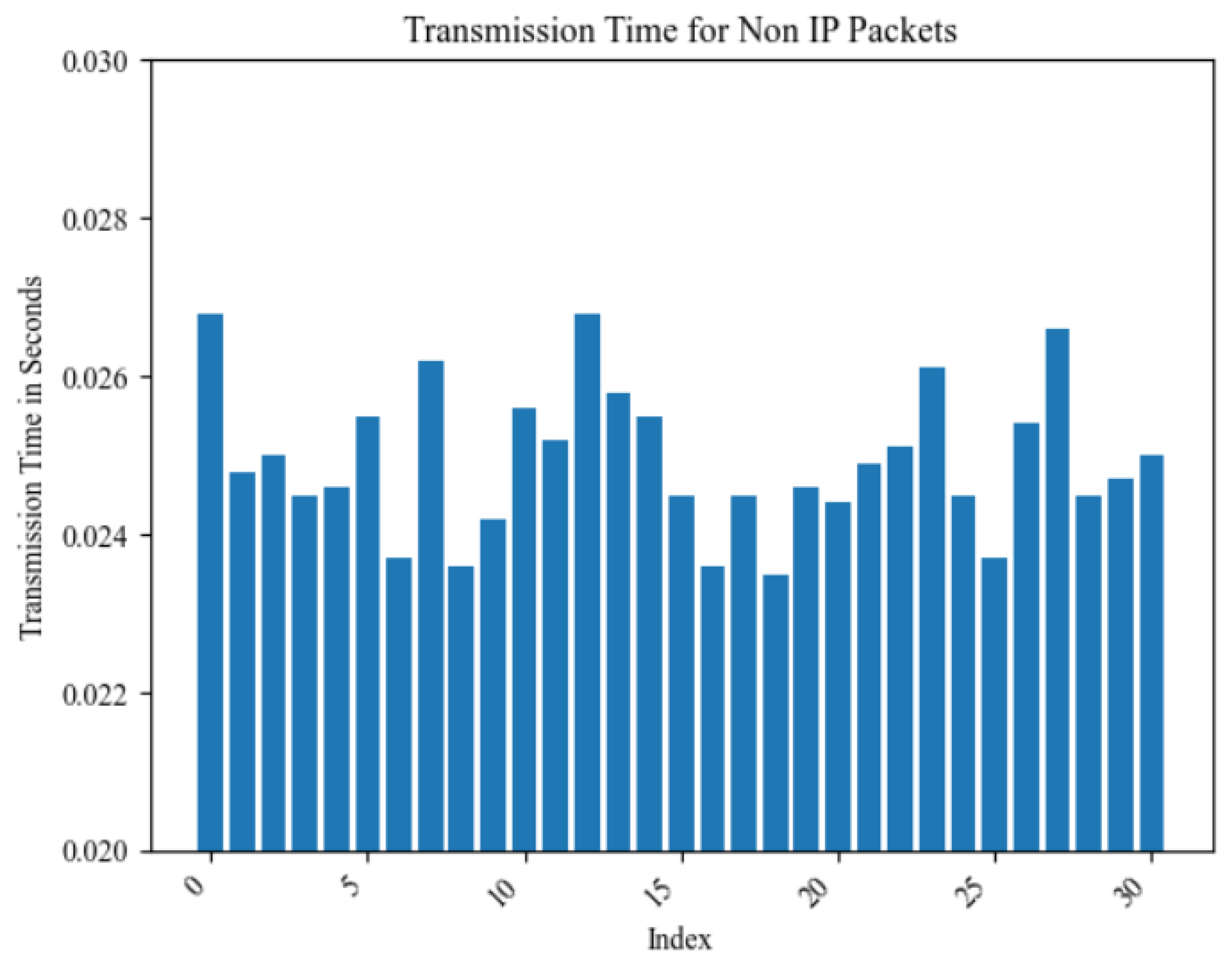
4.2.1. Study of Transmission Time in SDN Environment
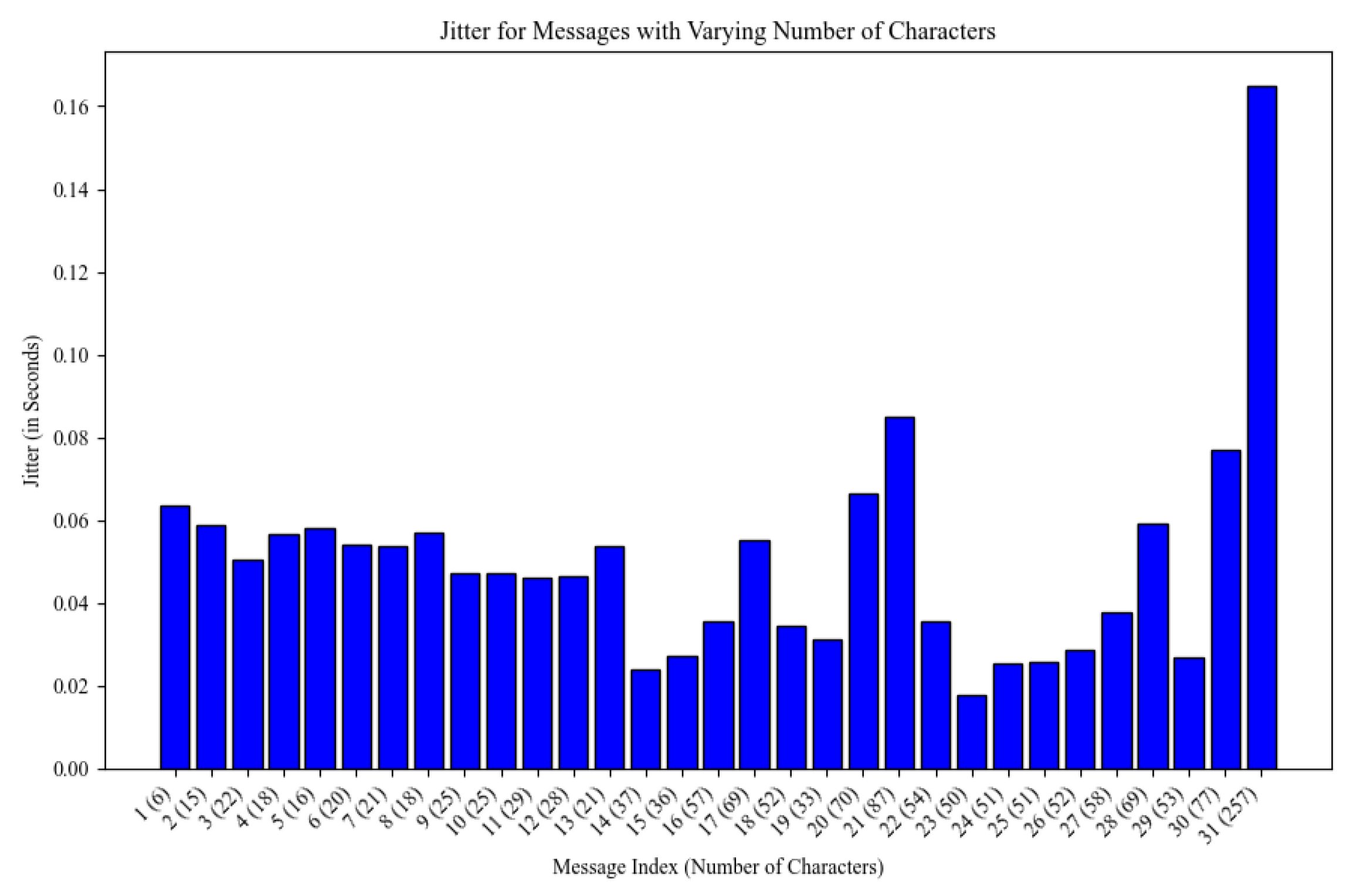
4.2.2. Study of the Jitter in SDN
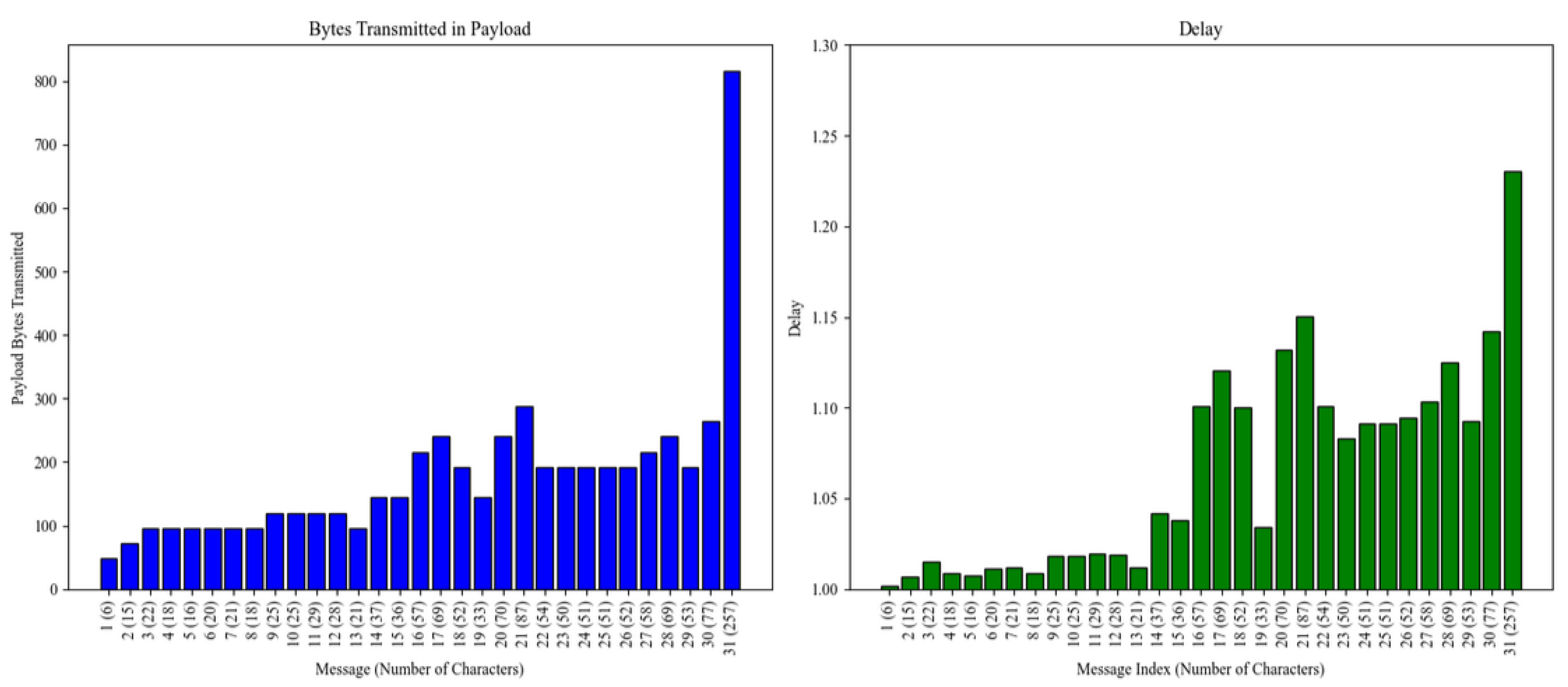
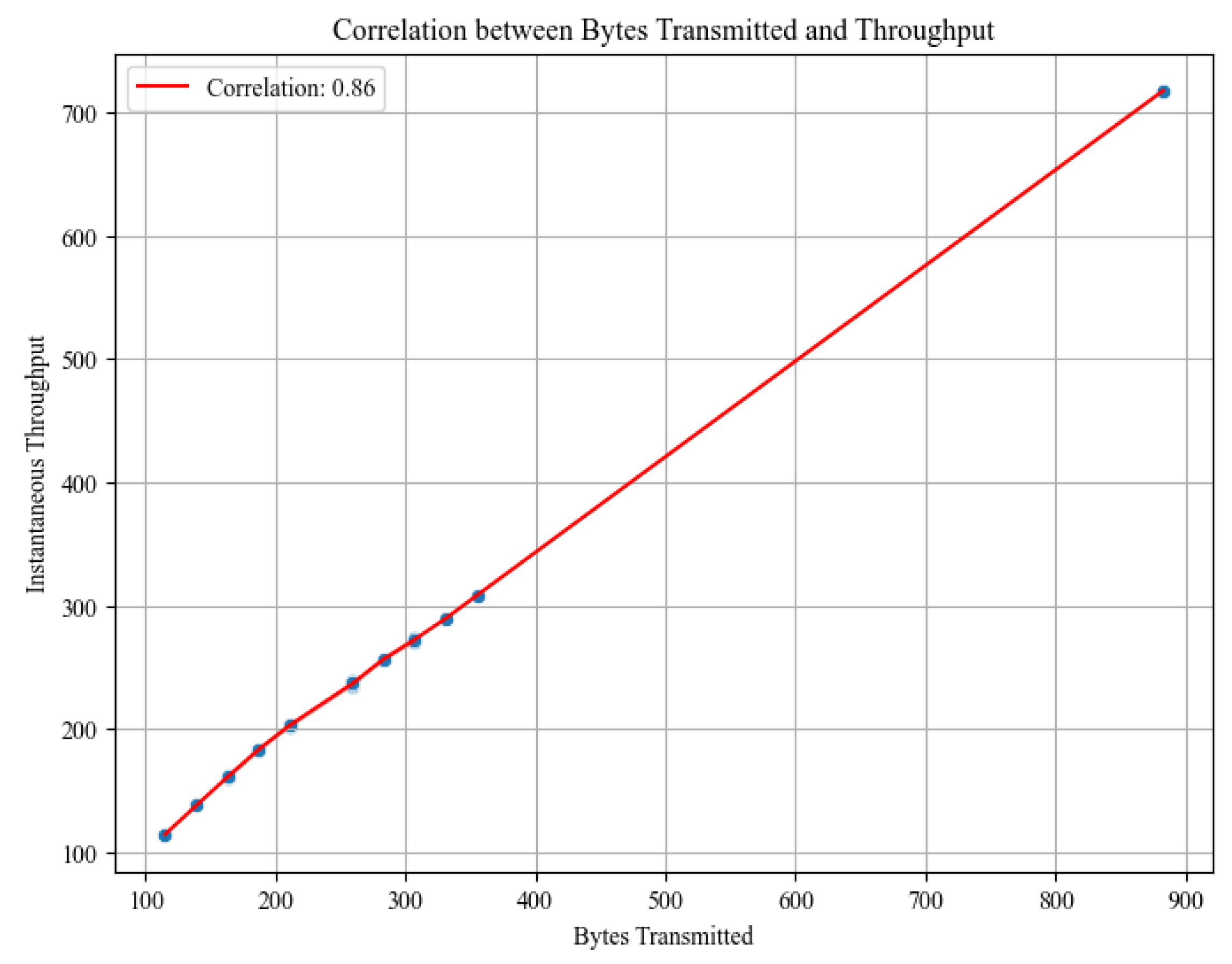
4.2.3. Study of Bytes Transmitted in Payload and Transmission Time
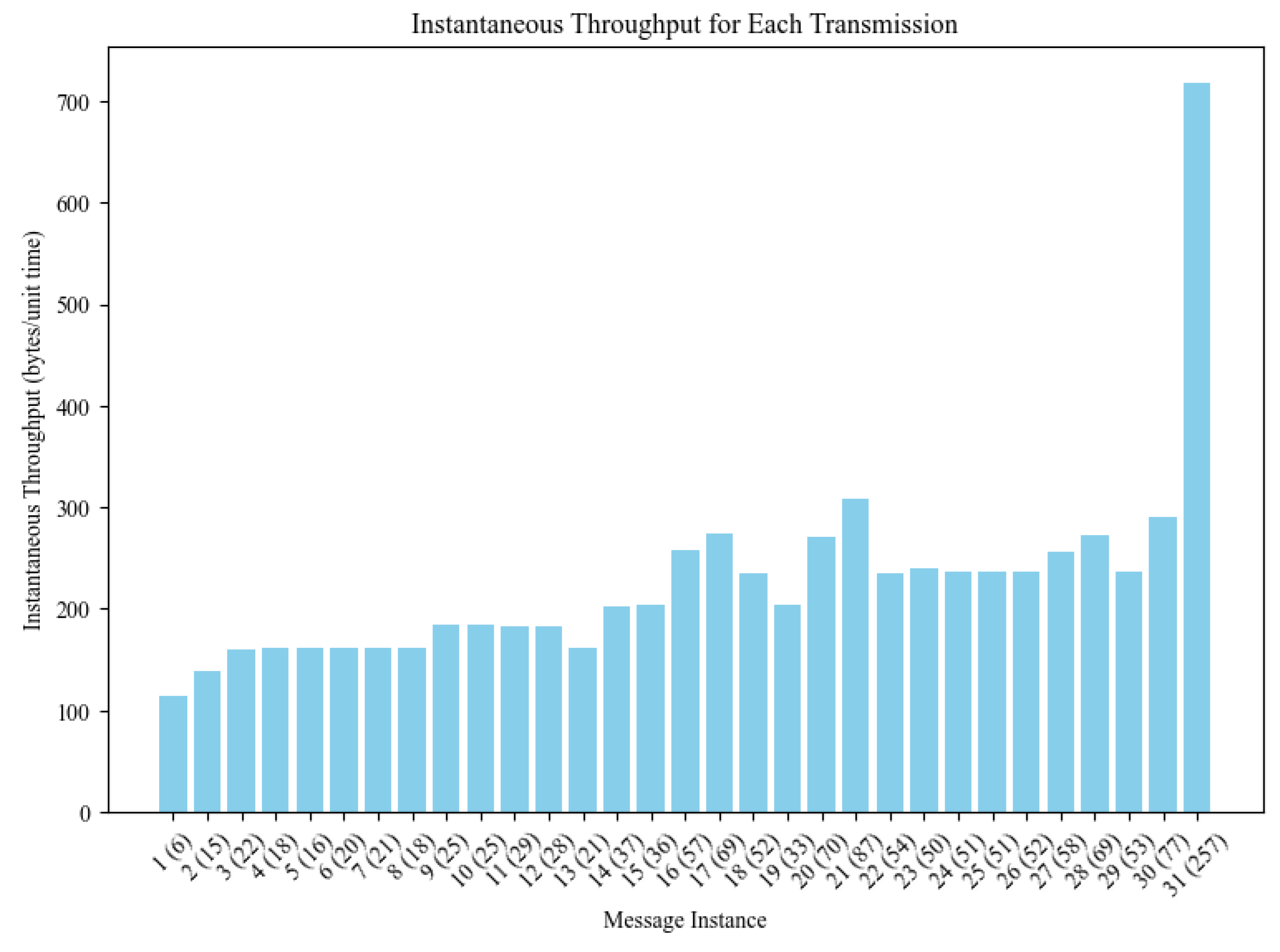
4.2.4. Study on Instantaneous Throughput
4.3. Evaluation of System Performance
4.4. Comparative Entropy and Pattern Analysis with Standalone Legacy Encryption
4.5. Impact of Genetic Operators on Cryptographic Performance
5. Conclusions and Future Works
- Network Topology: The network topology in the study is relatively small and, therefore, was easier to manage with the static method to derive a global network view in the controller. For the larger network dynamic, the OpenFlow discovery method would be more suitable, which may lead to added complexity.
- Limited Cryptanalysis: Although the cryptanalysis performed to evaluate the strength of the encryption algorithm was sufficient to draw a preliminary conclusion on strength, the complete conclusive statement can only be provided after considering the encryption algorithms against the APTs and quantum attacks.
- Optimization of Load and Network Parameters: The optimization of load distribution and network parameters, such as bandwidth, was not performed, and the observation of the performance of the SDN environment was performed on default settings.
- Application to Real-World SDN: This study is focused on analyzing the performance, strength, and efficiency of an encryption mechanism, using a controlled environment of Mininet for the emulation process to mimic the real-world SDN. The real-world application would introduce constraints including hardware limitations, heterogeneous device compatibility, network congestion, and unpredictable traffic patterns.
- More Detailed Comparative Study: Although the current study includes the encryption strength’s test against the standalone algorithm, there is still a need for a proper benchmark algorithm analysis of network performance under the same network conditions. Furthermore, the extension needs to include comparisons with other data protection mechanisms.
- Exploration with Approaches for Improvements in Network Parameters: The current study scope is focused on the deployment of encryption as a policy. Therefore, the issues with network parameters, such as delay, throughput, and jitter underperforming, which require different approaches to be combined with existing methods, have not been explored. This shall be a major concern of our future work, together with the security issues.
- Implementation of the GA-based hybrid encryption in a large network in a real SDN environment involving a multi-controller setup.
- Exploration of a lightweight GA for encryption policy implementation in networks involving IOT devices.
- Adaptive encryption strategies for sensitive and non-sensitive packets utilizing a traffic-based load balancing mechanism in a multi-controller setup.
- Integrate post-quantum cryptographic techniques to improve resilience against quantum attacks.
- Exploration of utilizing GPU-accelerated parallel processing to reduce encryption and decryption latency.
- Extend security evaluation to include resistance against APTs and evolving attack models.
- Development of an intelligent SDN-based load balancing mechanism to optimize encryption workload distribution by distributing computationally intensive tasks across available resources.
- Conduct explorations to fine-tune SDN parameters such as bandwidth allocation and congestion control to enhance network efficiency.
- Performance evaluation against the traditional standalone and hybrid algorithms over the SDN network.
- Conduct a detail evaluation of the strength and performance of the proposed mechanism against other data protection methods.
- Integration of different strategies for enhancing network performance in high-load and high-data-transmitting network settings.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhu, L.; Karim, M.M.; Sharif, K.; Xu, C.; Li, F.; Du, X.; Guizani, M. SDN controllers: A comprehensive analysis and performance evaluation study. ACM Comput. Surv. (CSUR) 2020, 53, 1–40. [Google Scholar] [CrossRef]
- Shaghaghi, A.; Kaafar, M.A.; Buyya, R.; Jha, S. Software-defined network (SDN) data plane security: Issues, solutions, and future directions. In Handbook of Computer Networks and Cyber Security: Principles and Paradigms; Springer: Berlin/Heidelberg, Germany, 2020; pp. 341–387. [Google Scholar]
- Kim, J.; Seo, M.; Lee, S.; Nam, J.; Yegneswaran, V.; Porras, P.; Gu, G.; Shin, S. Enhancing security in SDN: Systematizing attacks and defenses from a penetration perspective. Comput. Netw. 2024, 241, 110203. [Google Scholar] [CrossRef]
- Gupta, B.B.; Dahiya, A.; Benkhelifa, E. Sdn And Nfv: A New Dimension To Virtualization; World Scientific: Singapore, 2024; Volume 2. [Google Scholar]
- Mijumbi, R.; Serrat, J.; Gorricho, J.L.; Bouten, N.; De Turck, F.; Boutaba, R. Network Function Virtualization: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 236–262. [Google Scholar] [CrossRef]
- Bavani, K.; Deepalakshmi, P.; Kalaimannan, E. Comprehensive Survey of Implementing Multiple Controllers in a Software-Defined Network (SDN). In Software-Defined Network Frameworks; CRC Press: Boca Raton, FL, USA, 2024; pp. 155–179. [Google Scholar]
- Mughal, A.A. Cyber Attacks on OSI Layers: Understanding the Threat Landscape. J. Humanit. Appl. Sci. Res. 2020, 3, 1–18. [Google Scholar]
- Usman, M.; Amin, R.; Aldabbas, H.; Alouffi, B. Lightweight challenge-response authentication in SDN-based UAVs using elliptic curve cryptography. Electronics 2022, 11, 1026. [Google Scholar] [CrossRef]
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: A survey, some research issues, and challenges. IEEE Commun. Surv. Tutor. 2015, 18, 602–622. [Google Scholar] [CrossRef]
- Jimenez, M.B.; Fernandez, D.; Rivadeneira, J.E.; Bellido, L.; Cardenas, A. A survey of the main security issues and solutions for the SDN architecture. IEEE Access 2021, 9, 122016–122038. [Google Scholar] [CrossRef]
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in software defined networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 2317–2346. [Google Scholar] [CrossRef]
- Alanazi, H.; Zaidan, B.B.; Zaidan, A.A.; Jalab, H.A.; Shabbir, M.; Al-Nabhani, Y. New comparative study between DES, 3DES and AES within nine factors. arXiv 2010, arXiv:1003.4085. [Google Scholar]
- Radhi, S.M.; Ogla, R. In-Depth Assessment of Cryptographic Algorithms Namely DES, 3DES, AES, RSA, and Blowfish. Iraqi J. Comput. Commun. Control. Syst. Eng. 2023, 23, 125–138. [Google Scholar]
- Mohammad, N. Enhancing Security and Privacy in Multi-Cloud Environments: A Comprehensive Study on Encryption Techniques and Access Control Mechanisms. Int. J. Comput. Eng. Technol. (IJCET) 2021, 12, 51–63. [Google Scholar]
- Atadoga, A.; Farayola, O.A.; Ayinla, B.S.; Amoo, O.O.; Abrahams, T.O.; Osasona, F. A Comparative Review of Data Encryption Methods in the USA and Europe. Comput. Sci. IT Res. J. 2024, 5, 447–460. [Google Scholar] [CrossRef]
- Fauri, D.; de Wijs, B.; den Hartog, J.; Costante, E.; Zambon, E.; Etalle, S. Encryption in ICS networks: A blessing or a curse? In Proceedings of the 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm), Dresden, Germany, 23–27 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 289–294. [Google Scholar]
- Alves, T.; Das, R.; Morris, T. Embedding encryption and machine learning intrusion prevention systems on programmable logic controllers. IEEE Embed. Syst. Lett. 2018, 10, 99–102. [Google Scholar] [CrossRef]
- Pothireddy, S.; Peddisetty, N.; Yellamma, P.; Botta, G.; Gottipati, K.N. Data Security in Cloud Environment by Using Hybrid Encryption Technique: A Comprehensive Study on Enhancing Confidentiality and Reliability. Int. J. Intell. Eng. Syst. 2024, 17, 159–170. [Google Scholar]
- Yan, L.; Wang, G.; Yin, T.; Liu, P.; Feng, H.; Zhang, W.; Hu, H.; Pan, F. Attribute-Based Searchable Encryption: A Survey. Electronics 2024, 13, 1621. [Google Scholar] [CrossRef]
- Durner, R.; Kellerer, W. The cost of security in the SDN control plane. In Proceedings of the ACM CoNEXT 2015-Student Workshop, Heidelberg, Germany, 1–4 December 2015. [Google Scholar]
- Chen, Y.; Jia, H.; Huang, K.; Lan, J.; Yan, X. A secure network coding based on broadcast encryption in sdn. Math. Probl. Eng. 2016, 2016, 7145138. [Google Scholar] [CrossRef]
- Ghaly, S.; Abdullah, M.Z. Design and implementation of a secured SDN system based on hybrid encrypted algorithms. TELKOMNIKA (Telecommun. Comput. Electron. Control) 2021, 19, 1118–1125. [Google Scholar] [CrossRef]
- Alzahrani, B.; Chaudhry, S.A. [Retracted] An Identity-Based Encryption Method for SDN-Enabled Source Routing Systems. Secur. Commun. Netw. 2022, 2022, 1942097. [Google Scholar] [CrossRef]
- Abdi, A.H.; Audah, L.; Salh, A.; Alhartomi, M.A.; Rasheed, H.; Ahmed, S.; Tahir, A. Security Control and Data Planes of SDN: A Comprehensive Review of Traditional, AI and MTD Approaches to Security Solutions. IEEE Access 2024. [Google Scholar]
- Pisharody, S.; Natarajan, J.; Chowdhary, A.; Alshalan, A.; Huang, D. Brew: A security policy analysis framework for distributed SDN-based cloud environments. IEEE Trans. Dependable Secur. Comput. 2017, 16, 1011–1025. [Google Scholar] [CrossRef]
- Dong, L.; Chen, L.; Zhang, Y.; He, B.; Zhou, J.; Wang, W.; Leung, V.C. Dynamic Policy Deployment in SDN Switch Based on Monitoring and Analysis of User Behaviors. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [Google Scholar]
- Syed, A.; Anwer, B.; Gopalakrishnan, V.; Van der Merwe, J. Depo: A platform for safe deployment of policy in a software defined infrastructure. In Proceedings of the 2019 ACM Symposium on SDN Research, San Jose, CA, USA, 3–4 April 2019; pp. 98–111. [Google Scholar]
- Ahmed, B.; Ahmed, N.; Malik, A.W.; Jafri, M.; Hafeez, T. Fingerprinting SDN policy parameters: An empirical study. IEEE Access 2020, 8, 142379–142392. [Google Scholar] [CrossRef]
- Qazi, Z.A.; Tu, C.C.; Chiang, L.; Miao, R.; Sekar, V.; Yu, M. SIMPLE-fying middlebox policy enforcement using SDN. In Proceedings of the ACM SIGCOMM 2013 Conference on SIGCOMM, Hong Kong, China, 12–16 August 2013; pp. 27–38. [Google Scholar]
- Sindhuja, K.; Devi, S.P. A symmetric key encryption technique using genetic algorithm. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 414–416. [Google Scholar]
- Naik, P.G.; Naik, G.R. Asymmetric key encryption using genetic algorithm. Int. J. Latest Trends Eng. Technol. (IJLTET) 2014, 3, 118–128. [Google Scholar]
- Arshad, M.J.; Umair, M.; Munawar, S.; Naveed, N.; Naeem, H. Improving cloud data encryption using customized genetic algorithm. Int. J. Intell. Syst. Appl. 2020, 12, 46. [Google Scholar] [CrossRef]
- El-Shafai, W.; Mohamed, F.A.H.E.; Elkamchouchi, H.M.; Abd-Elnaby, M.; Elshafee, A. Efficient and secure cancelable biometric authentication framework based on genetic encryption algorithm. IEEE Access 2021, 9, 77675–77692. [Google Scholar] [CrossRef]
- Alhassan, S. Audio cryptography via enhanced genetic algorithm. Int. J. Multimed. Its Appl. (IJMA) Vol. 2021, 13. [Google Scholar] [CrossRef]
- Mawla, N.A.; Khafaji, H.K. Protein Motifs to Hide GA-Based Encrypted Data. Sci. Program. 2022, 2022, 1846788. [Google Scholar] [CrossRef]
- Vie, A.; Kleinnijenhuis, A.M.; Farmer, D.J. Qualities, challenges and future of genetic algorithms: A literature review. arXiv 2020, arXiv:2011.05277. [Google Scholar]
- Schott, J.R. Fault Tolerant Design Using Single and Multicriteria Genetic Algorithm Optimization. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 1995. [Google Scholar]
- Matthias, D.; Osakwe, B.; Anireh, V. A Secure Model on Cloud using a Modified Rivest, Shamir and Adleman Algorithm along with Gray Codes. Int. J. Comput. Technol. 2021, 8, 207–214. [Google Scholar]
- Abdeldaym, R.S.; Abd Elkader, H.M.; Hussein, R. Modified RSA algorithm using two public key and Chinese remainder theorem. IJ Electron. Inf. Eng. 2019, 10, 51–64. [Google Scholar]
- Krantz, S.G.; Parks, H.R.; Krantz, S.G.; Parks, H.R. RSA encryption. In A Mathematical Odyssey: Journey from the Real to the Complex; Springer: New York, NY, USA, 2014; pp. 197–215. [Google Scholar]
- Pugila, D.; Chitrala, H.; Lunawat, S.; Vincent, P.D.R. An efficeient encrpytion algorithm based on public key cryptography. Int. J. Eng. Technol. 2013, 5, 3064–3067. [Google Scholar]
- Paar, C.; Pelzl, J. Understanding Cryptography; Springer: Berlin/Heidelberg, Germany, 2010; Volume 1. [Google Scholar]
- Monshizadeh, M.; Khatri, V.; Kantola, R. Detection as a service: An SDN application. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 19–22 February 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 285–290. [Google Scholar]
- Alsaeedi, M.; Mohamad, M.M.; Al-Roubaiey, A.A. Toward adaptive and scalable OpenFlow-SDN flow control: A survey. IEEE Access 2019, 7, 107346–107379. [Google Scholar] [CrossRef]
- Boukraa, L.; Mahrach, S.; El Makkaoui, K.; Esbai, R. SDN southbound protocols: A comparative study. In Proceedings of the International Conference on Networking, Intelligent Systems and Security, Bandung, Indonesia, 30–31 March 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 407–418. [Google Scholar]
- Fuller, B.; O’neill, A.; Reyzin, L. A unified approach to deterministic encryption: New constructions and a connection to computational entropy. J. Cryptol. 2015, 28, 671–717. [Google Scholar] [CrossRef]
- Easttom, W. Modern Cryptography: Applied Mathematics for Encryption and Information Security; Springer: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Kumar, V.; Pathak, V.; Badal, N.; Pandey, P.S.; Mishra, R.; Gupta, S.K. Complex entropy based encryption and decryption technique for securing medical images. Multimed. Tools Appl. 2022, 81, 37441–37459. [Google Scholar] [CrossRef]
- Kearns, L. Enhancing Data Security through Implementation of a Hybrid Cryptosystem with Emphasis on Levels of Entropy. Ph.D. Thesis, National College of Ireland, Dublin, Ireland, 2021. [Google Scholar]
- Garipcan, A.M.; Erdem, E. DESSB-TRNG: A novel true random number generator using data encryption standard substitution box as post-processing. Digit. Signal Process. 2022, 123, 103455. [Google Scholar] [CrossRef]
- Swenson, C. Modern Cryptanalysis: Techniques for Advanced Code Breaking; John Wiley & Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- Aumasson, J.P. Serious Cryptography: A Practical Introduction to Modern Encryption; No Starch Press: San Francisco, CA, USA, 2017. [Google Scholar]
- Kulkarni, N.S.; Raman, B.; Gupta, I. Multimedia encryption: A brief overview. In Recent Advances in Multimedia Signal Processing and Communications; Springer: Berlin/Heidelberg, Germany, 2009; pp. 417–449. [Google Scholar]
- Bhatia, D. Cryptography—The Hidden Message; Blue Rose Publishers: Noida, Uttar Pradesh, 2022. [Google Scholar]
- Jing, S.; Guo, Y.; Chen, W. Meaningful ciphertext encryption algorithm based on bit scrambling, discrete wavelet transform, and improved chaos. IET Image Process. 2021, 15, 1053–1071. [Google Scholar] [CrossRef]
- Verma, R.; Sharma, A.K. Cryptography: Avalanche effect of AES and RSA. Int. J. Sci. Res. Publ. 2020, 10, 119–122. [Google Scholar] [CrossRef]
- Heys, H.M. A tutorial on linear and differential cryptanalysis. Cryptologia 2002, 26, 189–221. [Google Scholar] [CrossRef]
- Daemen, J. Cipher and Hash Function Design Strategies Based on Linear and Differential Cryptanalysis. Ph.D. Thesis, KU Leuven, Leuven, Belgium, 1995. [Google Scholar]
- Andem, V.R. A Cryptanalysis of the Tiny Encryption Algorithm. Ph.D. Thesis, University of Alabama Alabama, Tuscaloosa, AL, USA, 2003. [Google Scholar]
- Lakshman, T.; Madhow, U. The performance of TCP/IP for networks with high bandwidth-delay products and random loss. IEEE/ACM Trans. Netw. 1997, 5, 336–350. [Google Scholar] [CrossRef]
- Arbuthnot, T. What are thresholds for good and poor network packet loss, jitter and round trip time for unified communications? Tom Talks May 2018, 17, 7. [Google Scholar]
- Pointurier, Y.; Benzaoui, N.; Lautenschlaeger, W.; Dembeck, L. End-to-end time-sensitive optical networking: Challenges and solutions. J. Light. Technol. 2019, 37, 1732–1741. [Google Scholar] [CrossRef]
- Kumar, A.; Manjunath, D.; Kuri, J. Communication Networking: An Analytical Approach; Elsevier: Amsterdam, The Netherlands, 2004. [Google Scholar]
- Li, Q.; Tang, X.; Peng, J.; Tan, Y.; Jiang, Y. Latency Reducing in Real-Time Internet Video Transport: A Survey. Available at SSRN 4654242. 2023. Available online: https://ssrn.com/abstract=4654242 (accessed on 5 August 2024).
- Gelberger, A.; Yemini, N.; Giladi, R. Performance analysis of software-defined networking (SDN). In Proceedings of the 2013 IEEE 21st International Symposium on Modelling, Analysis and Simulation of Computer and Telecommunication Systems, Online, 14–16 August 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 389–393. [Google Scholar]
- Peterson, L.L.; Davie, B.S. Computer Networks: A Systems Approach; Morgan Kaufmann: Burlington, MA, USA, 2007. [Google Scholar]
- Naman, A.T.; Wang, Y.; Gharakheili, H.H.; Sivaraman, V.; Taubman, D. Responsive high throughput congestion control for interactive applications over SDN-enabled networks. Comput. Netw. 2018, 134, 152–166. [Google Scholar] [CrossRef]
- Ryoo, S.; Rodrigues, C.I.; Baghsorkhi, S.S.; Stone, S.S.; Kirk, D.B.; Hwu, W.m.W. Optimization principles and application performance evaluation of a multithreaded GPU using CUDA. In Proceedings of the 13th ACM SIGPLAN Symposium on Principles and Practice of Parallel Programming, Salt Lake City, UT, USA, 20–23 February 2008; pp. 73–82. [Google Scholar]
- Kagami, N.S.; da Costa Filho, R.I.T.; Gaspary, L.P. Capest: Offloading network capacity and available bandwidth estimation to programmable data planes. IEEE Trans. Netw. Serv. Manag. 2019, 17, 175–189. [Google Scholar] [CrossRef]
- Rodrigues, B.B.; Riekstin, A.C.; Januário, G.C.; Nascimento, V.T.; Carvalho, T.C.; Meirosu, C. GreenSDN: Bringing energy efficiency to an SDN emulation environment. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 948–953. [Google Scholar]
- Jeyasekar, A.; Nanda, S.; Uthra, A. Green SDN: Trends of energy conservation in software defined network. Int. J. Eng. Technol. 2018, 7, 9–13. [Google Scholar] [CrossRef]
- Naseri, A.; Ahmadi, M.; PourKarimi, L. Reduction of energy consumption and delay of control packets in Software-Defined Networking. Sustain. Comput. Inform. Syst. 2021, 31, 100574. [Google Scholar] [CrossRef]
- Lambora, A.; Gupta, K.; Chopra, K. Genetic algorithm-A literature review. In Proceedings of the 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), Faridabad, India, 14–16 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 380–384. [Google Scholar]
- Saheed, Y.K.; Abdulganiyu, O.H.; Tchakoucht, T.A. Modified genetic algorithm and fine-tuned long short-term memory network for intrusion detection in the internet of things networks with edge capabilities. Appl. Soft Comput. 2024, 155, 111434. [Google Scholar] [CrossRef]
- El Menbawy, N.; Ali, H.A.; Saraya, M.S.; Ali-Eldin, A.M.; Abdelsalam, M.M. Energy-efficient computation offloading using hybrid GA with PSO in internet of robotic things environment. J. Supercomput. 2023, 79, 20076–20115. [Google Scholar] [CrossRef]
- Du, J.; Jiang, C.; Benslimane, A.; Guo, S.; Ren, Y. SDN-based resource allocation in edge and cloud computing systems: An evolutionary Stackelberg differential game approach. IEEE/ACM Trans. Netw. 2022, 30, 1613–1628. [Google Scholar] [CrossRef]
- Sapkota, B.; Dawadi, B.R.; Joshi, S.R.; Karn, G. Traffic-Driven Controller-Load-Balancing over Multi-Controller Software-Defined Networking Environment. Network 2024, 4, 523–544. [Google Scholar] [CrossRef]
- Semenov, S.; Davydov, V.; Voloshyn, D. Obfuscated Code Quality Measurement. In Proceedings of the 2019 XXIX International Scientific Symposium “Metrology and Metrology Assurance” (MMA), Cambridge, MA, USA, 14–16 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]


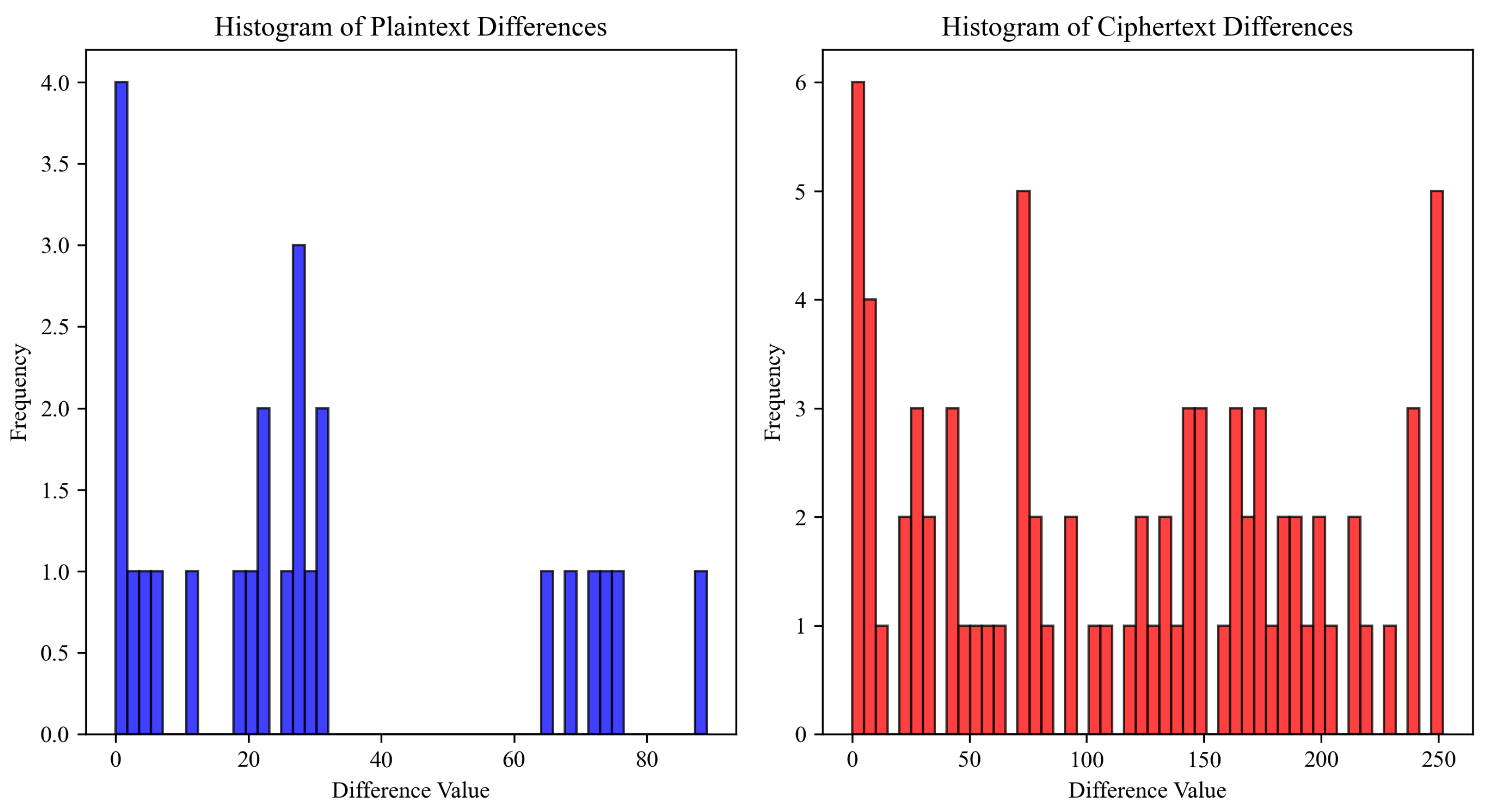
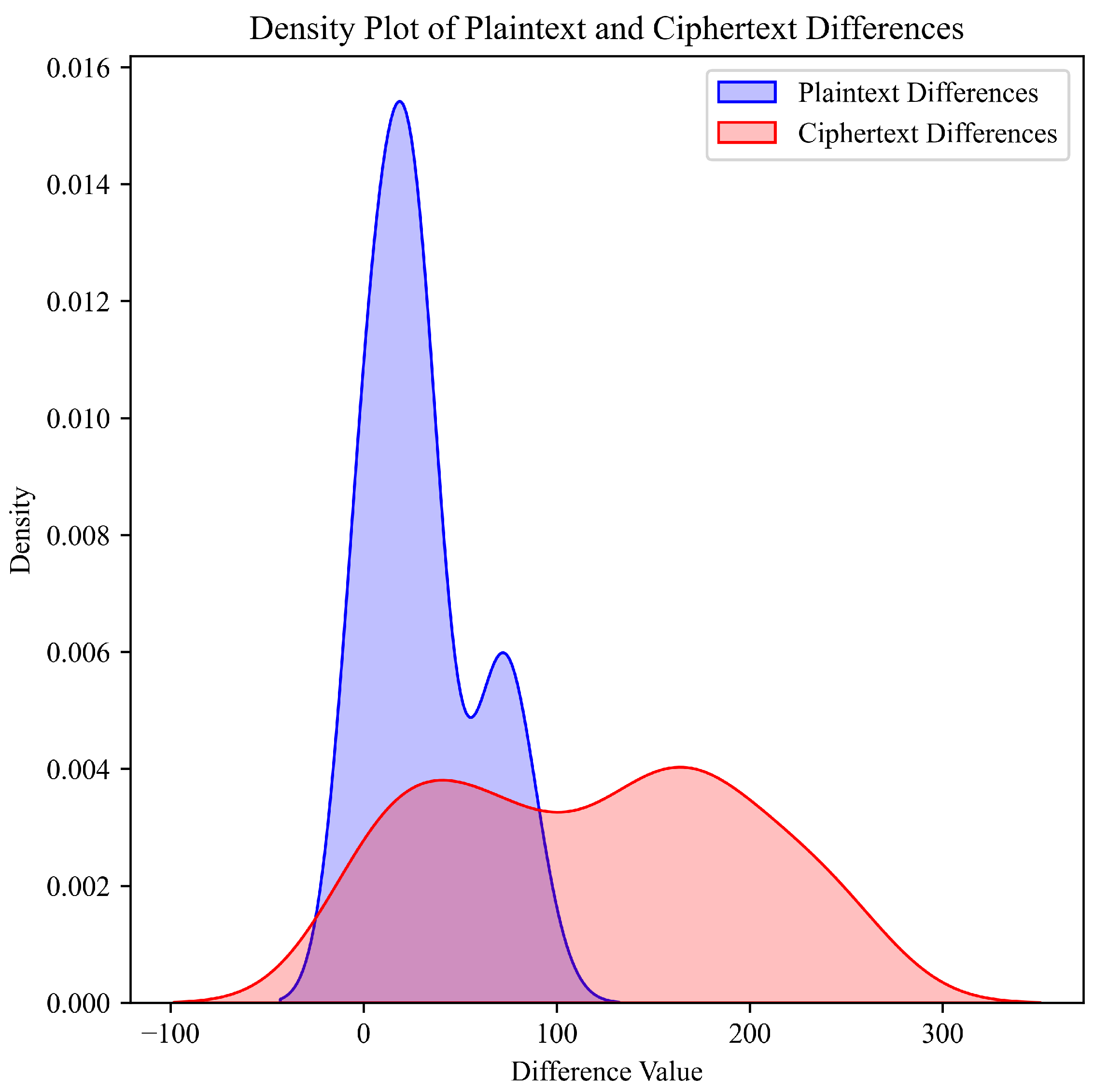
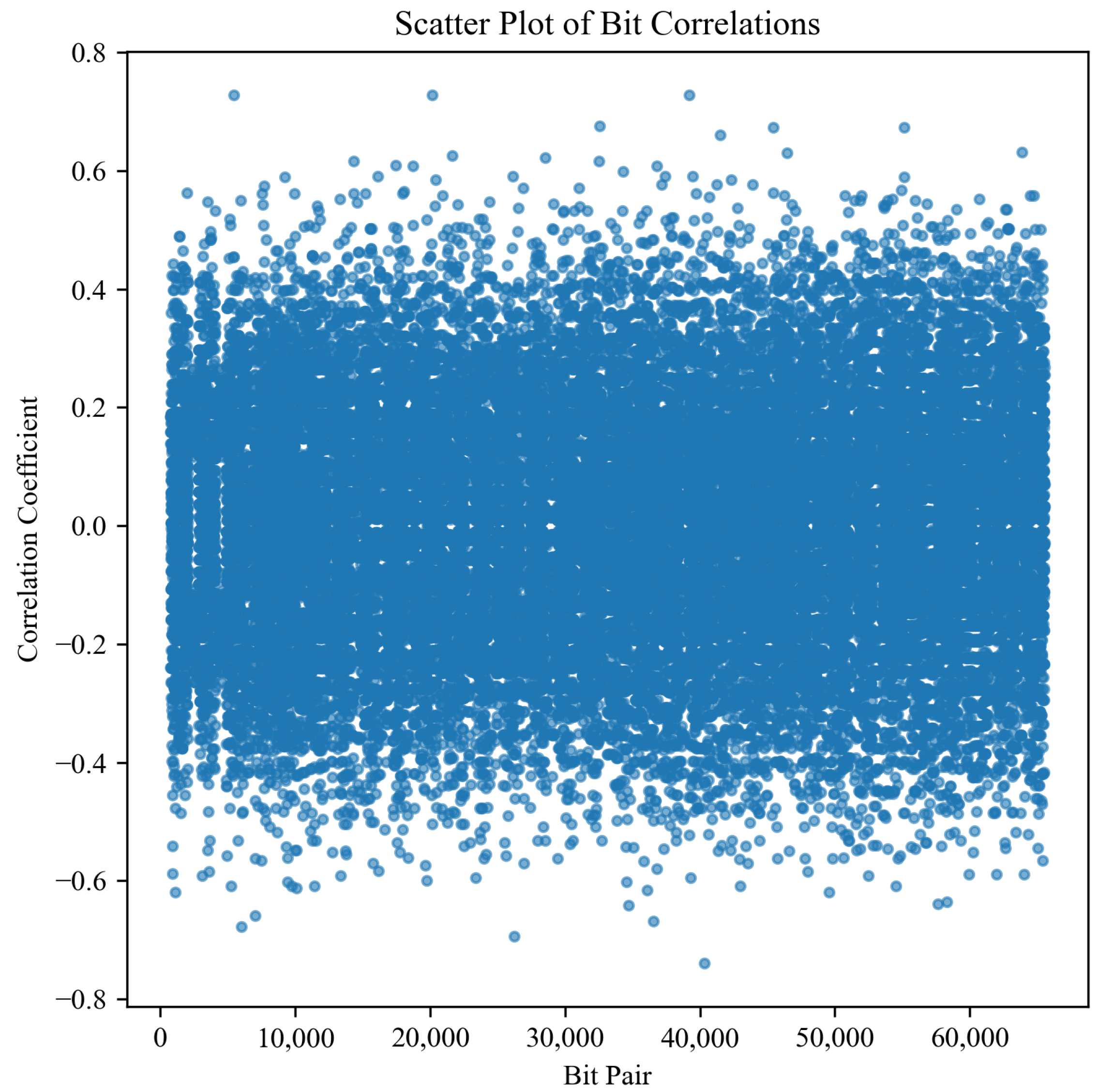
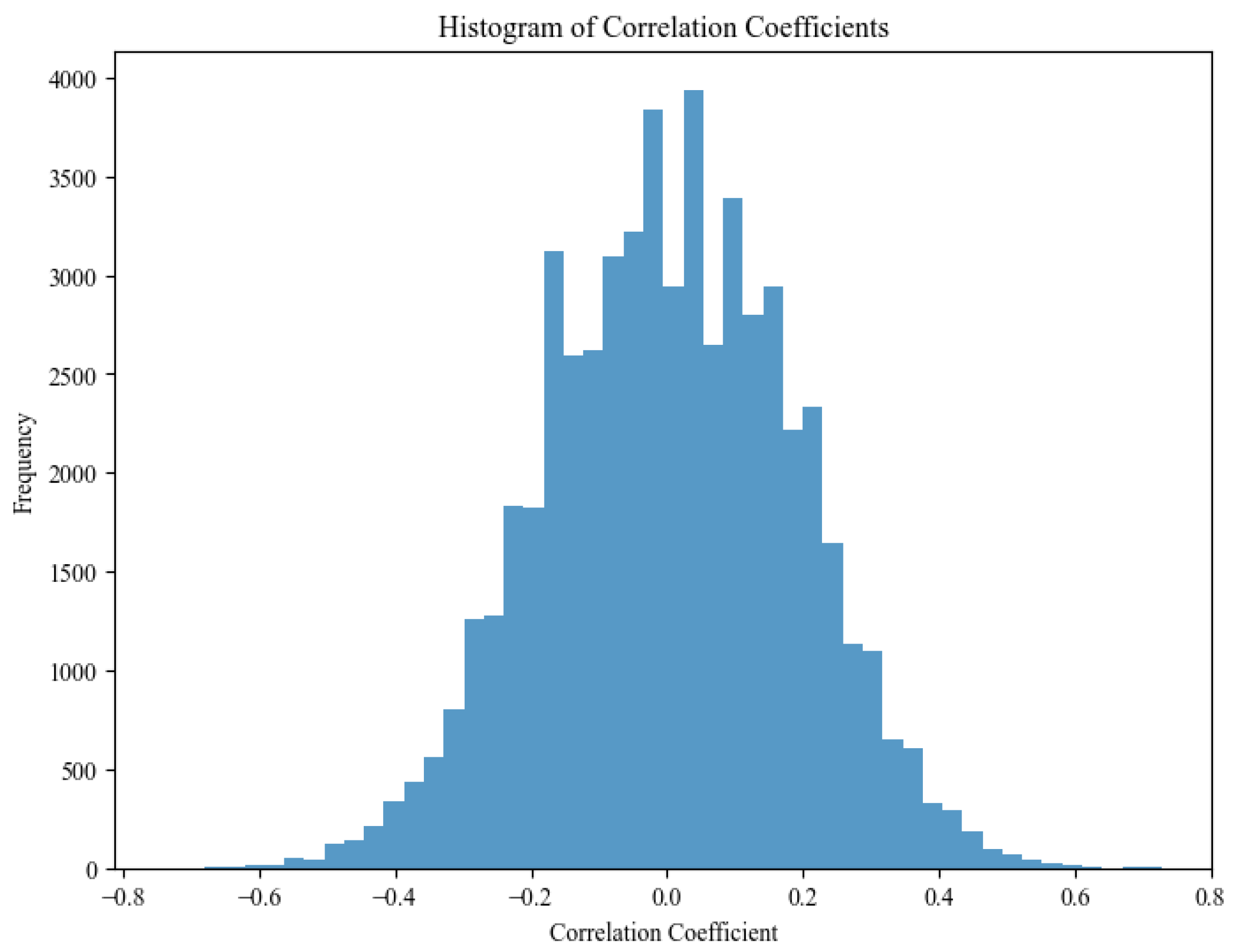




| Description | Value |
|---|---|
| Count (No. of Messages) | 31 |
| Mean | 0.989152 |
| Standard Deviation | 0.001774 |
| Minimum Entropy | 0.985688 |
| 25th Percentile | 0.987888 |
| Median | 0.989167 |
| 75th Percentile | 0.989937 |
| Maximum Entropy | 0.991961 |
| Description | Value (s) |
|---|---|
| Number of Messages | 31 |
| Mean | 1.065513 |
| Standard Deviation | 0.057506 |
| Minimum (Min) | 1.002 |
| 25th Percentile (25%) | 1.0135 |
| Median (50%) | 1.0416 |
| 75th Percentile (75%) | 1.101 |
| Maximum (Max) | 1.2304 |
| Description | Value |
|---|---|
| Number of Packets | 31 |
| Mean | 24.979 ms |
| Standard Deviation | 0.898 ms |
| Minimum (Min) | 23.571 ms |
| 25th Percentile (25%) | 24.452 ms |
| Median (50%) | 24.869 ms |
| 75th Percentile (75%) | 25.517 ms |
| Maximum (Max) | 26.783 ms |
| Statistic | Encryption Latency Time (s) | Decryption Latency Time (s) |
|---|---|---|
| Number of Data | 31 | 31 |
| Mean | 0.5342 | 0.3194 |
| Standard Deviation | 0.0393 | 0.0231 |
| Minimum (min) | 0.4895 | 0.2937 |
| Maximum (max) | 0.6399 | 0.3864 |
| Statistic | Value (ms) |
|---|---|
| Data Count | 31 |
| Mean Jitter | 50.026 |
| Standard Deviation | 26.851 |
| Range | 17.7–164.9 |
| 25th Percentile (Q1) | 32.800 |
| Median (Q2) | 47.313 |
| 75th Percentile (Q3) | 57.363 |
| Metric | Bytes Transmitted | Transmission Time (s) |
|---|---|---|
| Number of Data | 31 | 31 |
| Mean | 179.61 bytes | 1.0655 |
| Standard Deviation | 133.46 bytes | 0.0575 |
| Min | 48 bytes | 1.0020 |
| 25th Percentile | 96 bytes | 1.0135 |
| Median | 144 bytes | 1.0416 |
| 75th Percentile | 204 bytes | 1.1010 |
| Max | 816 bytes | 1.2304 |
| Statistic | Value (bytes/s) |
|---|---|
| Number of Observations | 31 |
| Mean | 226.83 |
| Standard Deviation | 103.29 |
| Minimum | 114.77 |
| 25th Percentile (Q1) | 161.68 |
| Median (Q2) | 203.98 |
| 75th Percentile (Q3) | 247.82 |
| Maximum | 717.65 |
| Statistic | Total Power (W) | Energy (Joules) | Energy (Wh) |
|---|---|---|---|
| Number of Data | 31 | 31 | 31 |
| Average | 10.044148 | 10.702168 | 0.002973 |
| Standard Deviation | 0.000608 | 0.577575 | 0.000160 |
| Min | 10.043039 | 10.065002 | 0.002796 |
| Max | 10.044945 | 12.359285 | 0.003433 |
| Statistic | Hybrid Encryption | AES | DES | RSA |
|---|---|---|---|---|
| Count | 31 | 31 | 31 | 22 |
| Mean Entropy | 0.98915 | 0.98752 | 0.98842 | 0.89580 |
| Standard Deviation | 0.00177 | 0.00272 | 0.00313 | 0.00254 |
| Minimum Entropy | 0.98568 | 0.98231 | 0.98141 | 0.89068 |
| 25% Entropy | 0.98788 | 0.98634 | 0.98685 | 0.89450 |
| Median (50%) Entropy | 0.98916 | 0.98723 | 0.98834 | 0.89576 |
| 75% Entropy | 0.98993 | 0.98869 | 0.99110 | 0.89749 |
| Maximum Entropy | 0.99196 | 0.99382 | 0.99416 | 0.90124 |
| Mutation Rate | Crossover Bits | Decryption Accuracy (%) | Total Time (s) |
|---|---|---|---|
| 0.02 | 1-bit | 90.00 | 0.454 |
| 0.02 | 3-bit | 89.67 | 0.454 |
| 0.02 | 5-bit | 87.42 | 0.440 |
| 0.02 | 7-bit | 87.42 | 0.435 |
| 0.05 | 1-bit | 95.00 | 0.654 |
| 0.05 | 3-bit | 96.72 | 0.645 |
| 0.05 | 5-bit | 98.82 | 0.670 |
| 0.05 | 7-bit | 99.20 | 0.703 |
| 0.10 | 1-bit | 99.99 | 0.740 |
| 0.10 | 3-bit | 99.99 | 0.780 |
| 0.10 | 5-bit | 100.00 | 0.853 |
| 0.10 | 7-bit | 96.72 | 0.857 |
| 0.15 | 1-bit | 0.00 | 1.220 |
| 0.15 | 3-bit | 0.00 | 1.340 |
| 0.15 | 5-bit | 0.00 | 1.520 |
| 0.15 | 7-bit | 0.00 | 1.653 |
| 0.20 | 1-bit | 0.00 | 1.682 |
| 0.20 | 3-bit | 0.00 | 1.702 |
| 0.20 | 5-bit | 0.00 | 1.732 |
| 0.20 | 7-bit | 0.00 | 1.753 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pokhrel, C.; Ghimire, R.; Dawadi, B.R.; Manzoni, P. A Machine Learning-Based Hybrid Encryption Approach for Securing Messages in Software-Defined Networking. Network 2025, 5, 8. https://doi.org/10.3390/network5010008
Pokhrel C, Ghimire R, Dawadi BR, Manzoni P. A Machine Learning-Based Hybrid Encryption Approach for Securing Messages in Software-Defined Networking. Network. 2025; 5(1):8. https://doi.org/10.3390/network5010008
Chicago/Turabian StylePokhrel, Chitran, Roshani Ghimire, Babu R. Dawadi, and Pietro Manzoni. 2025. "A Machine Learning-Based Hybrid Encryption Approach for Securing Messages in Software-Defined Networking" Network 5, no. 1: 8. https://doi.org/10.3390/network5010008
APA StylePokhrel, C., Ghimire, R., Dawadi, B. R., & Manzoni, P. (2025). A Machine Learning-Based Hybrid Encryption Approach for Securing Messages in Software-Defined Networking. Network, 5(1), 8. https://doi.org/10.3390/network5010008









