Resource-Conserving Protection against Energy Draining (RCPED) Routing Protocol for Wireless Sensor Networks
Abstract
1. Introduction
- Route loop attack (carousel attack): In this attack mode, the adversary intentionally creates routing loops and repeatedly makes data packets travel over the same loop.
- Stretch attack: In this attack mode, the adversaries try to stretch the length of regular routes as much as possible and make data pass through as many unnecessary nodes as possible. Consequently, the average route length may increase noticeably, and so does the number of nodes initially not supposed to be involved in data transmission.
2. Related Works
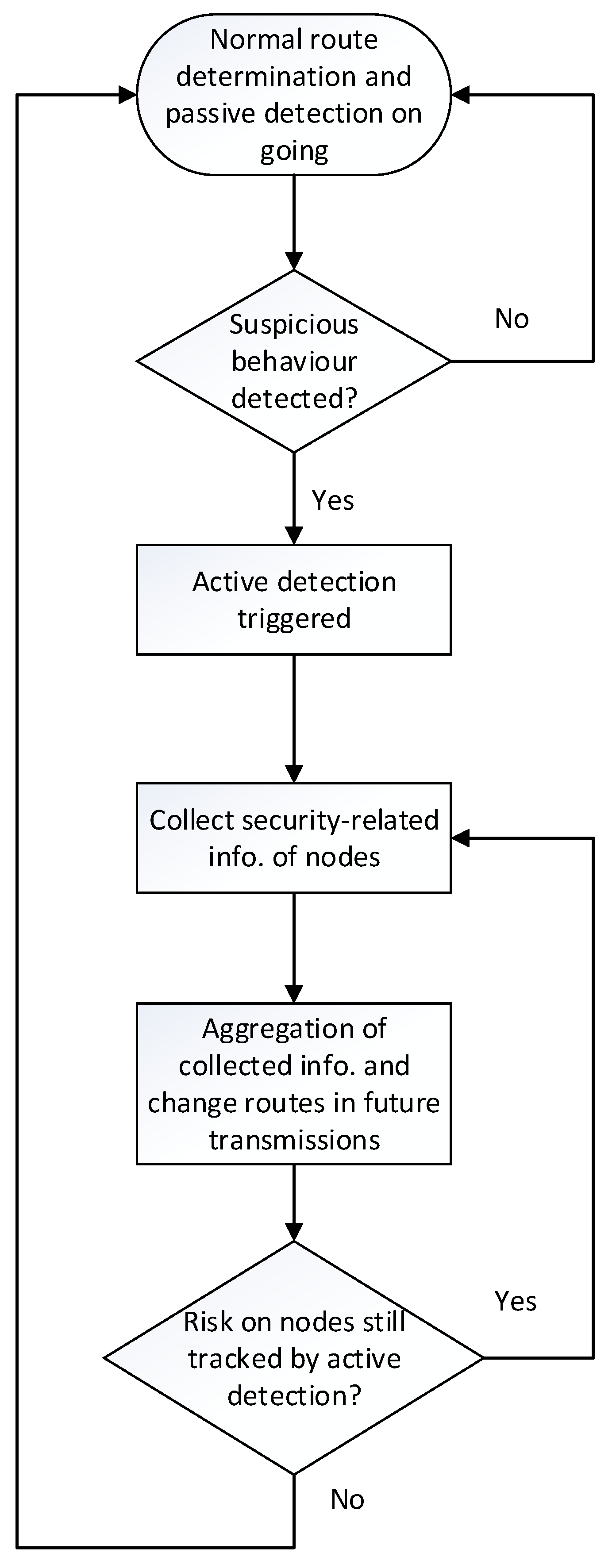
3. General Concept and Passive Detection
3.1. Defining Normal Case and Significant Deviation
3.2. Practical Issues in Passive Detection
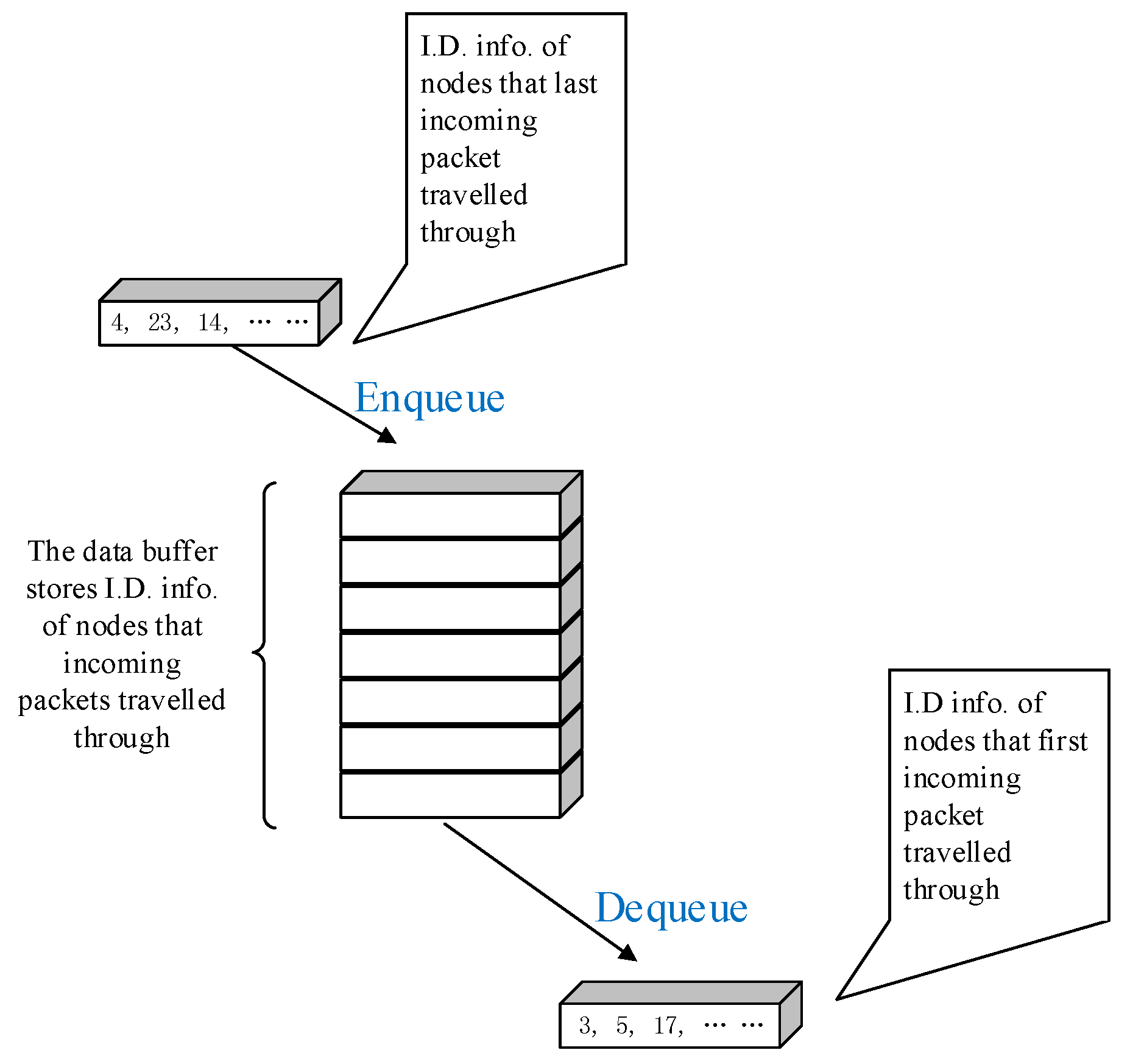
3.2.1. Estimation of Transmission Cost on a Specific Route
3.2.2. Node Localisation
4. Active Detection
4.1. Detection of Suspicious Routes
4.2. Detection of Route Loop Attackers (Carousel Attackers)
4.3. Detection of Route Stretch Attackers
5. Protection Against Vampire Attacks in Routing
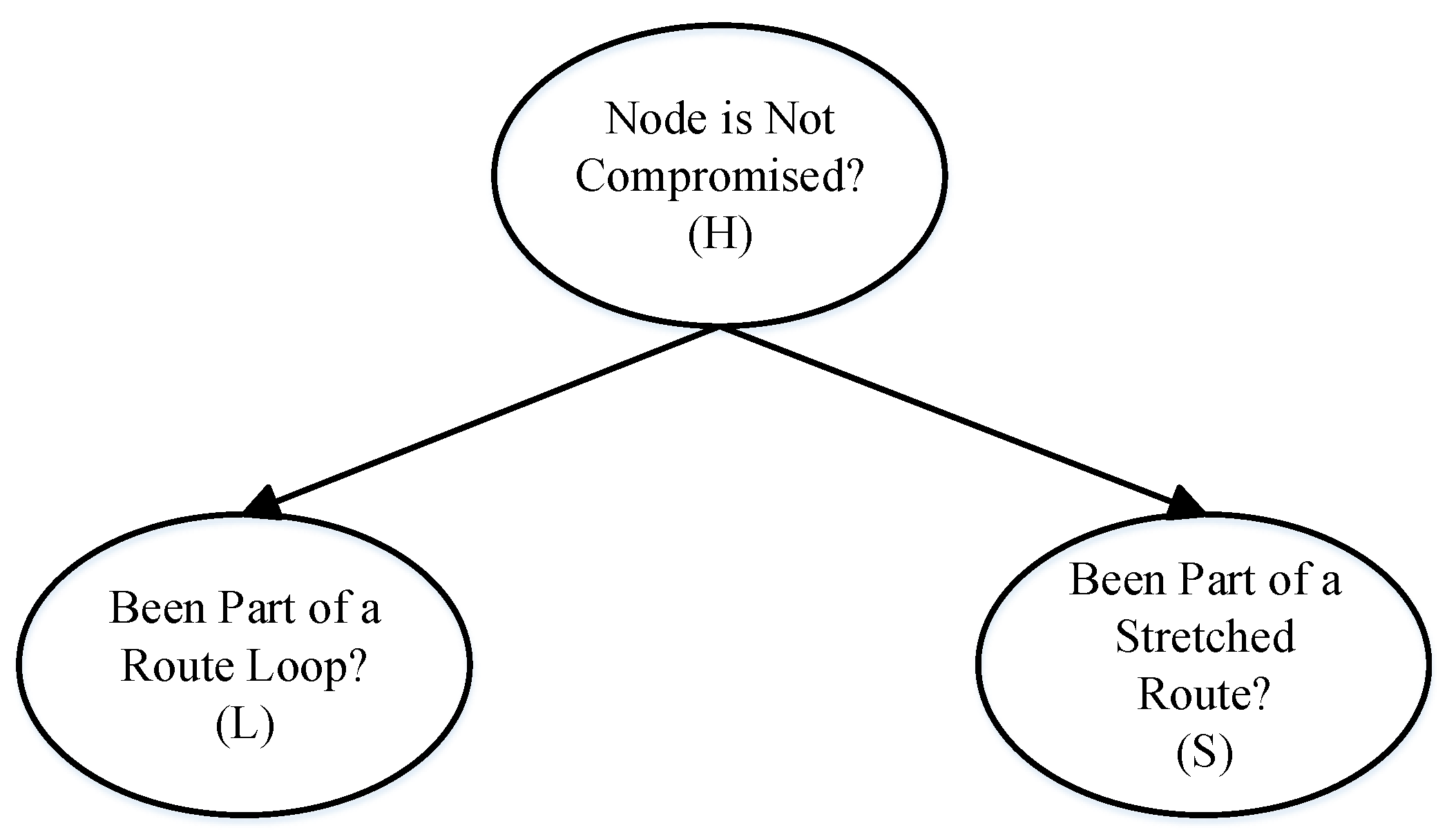
5.1. Monitoring Information Aggregation Utilizing Bayesian Network
5.2. Security Information Distribution
- Less vulnerable than other normal nodes in the network, since they do not directly participate in data transmissions (in other words, output only);
- More economical (in terms of both energy and cost) since they have already been deployed in the network, and adding some non-heavy duty task to them is preferable to deploy additional nodes for information distribution.
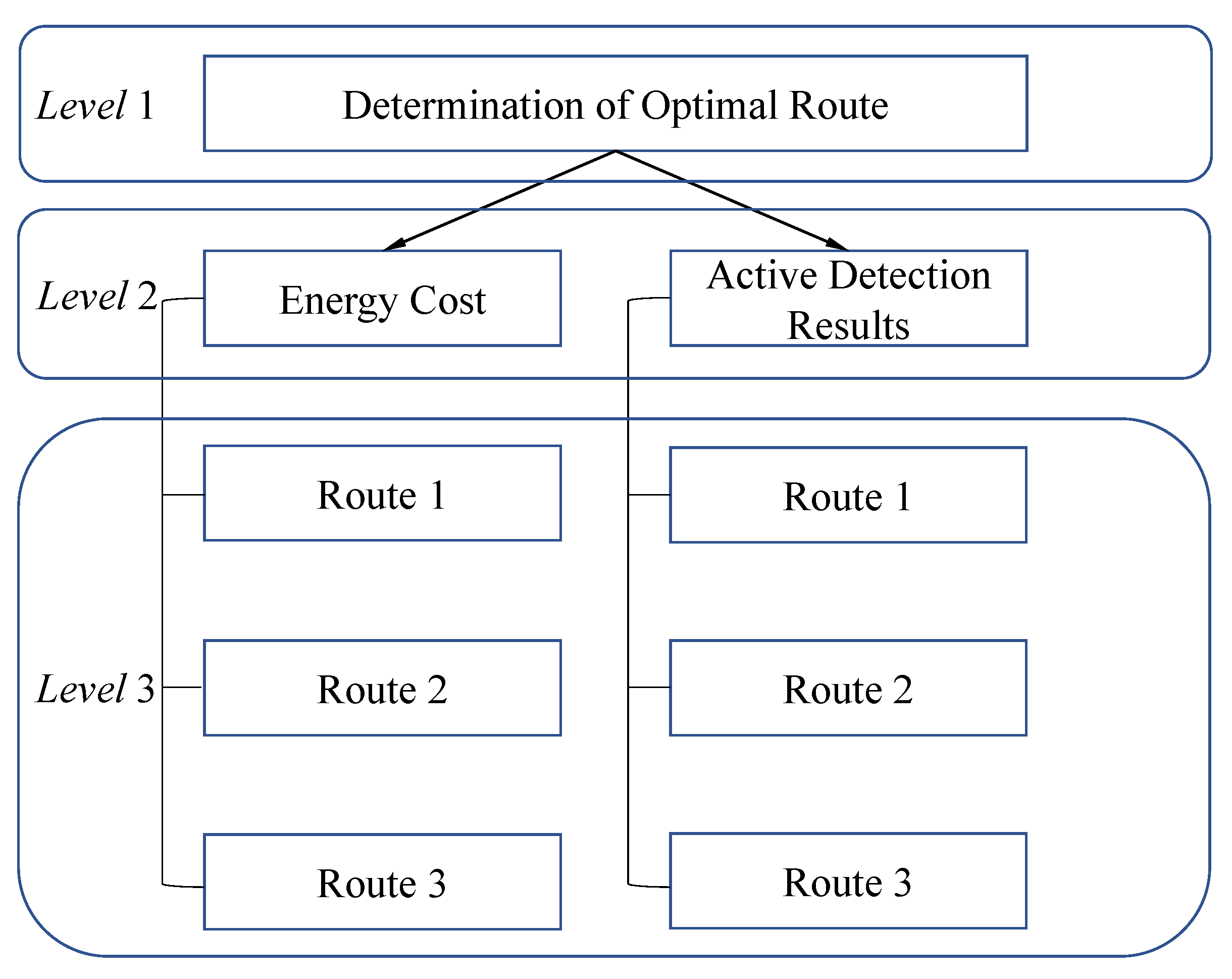
5.3. Route Discovery Based on AHP
5.4. Details of AHP
5.5. Priority Calculation in Optimal Route Determination
5.6. Optimal Route Determination
6. Simulation Results
6.1. Theoretical Definition of Performance
6.2. Theoretical Computational Complexities
6.3. Overview of PLGPa
6.4. Overview of AODV-EHA
6.5. Simulation Setup
6.6. Experimental Results
6.6.1. Energy Efficiency Performance
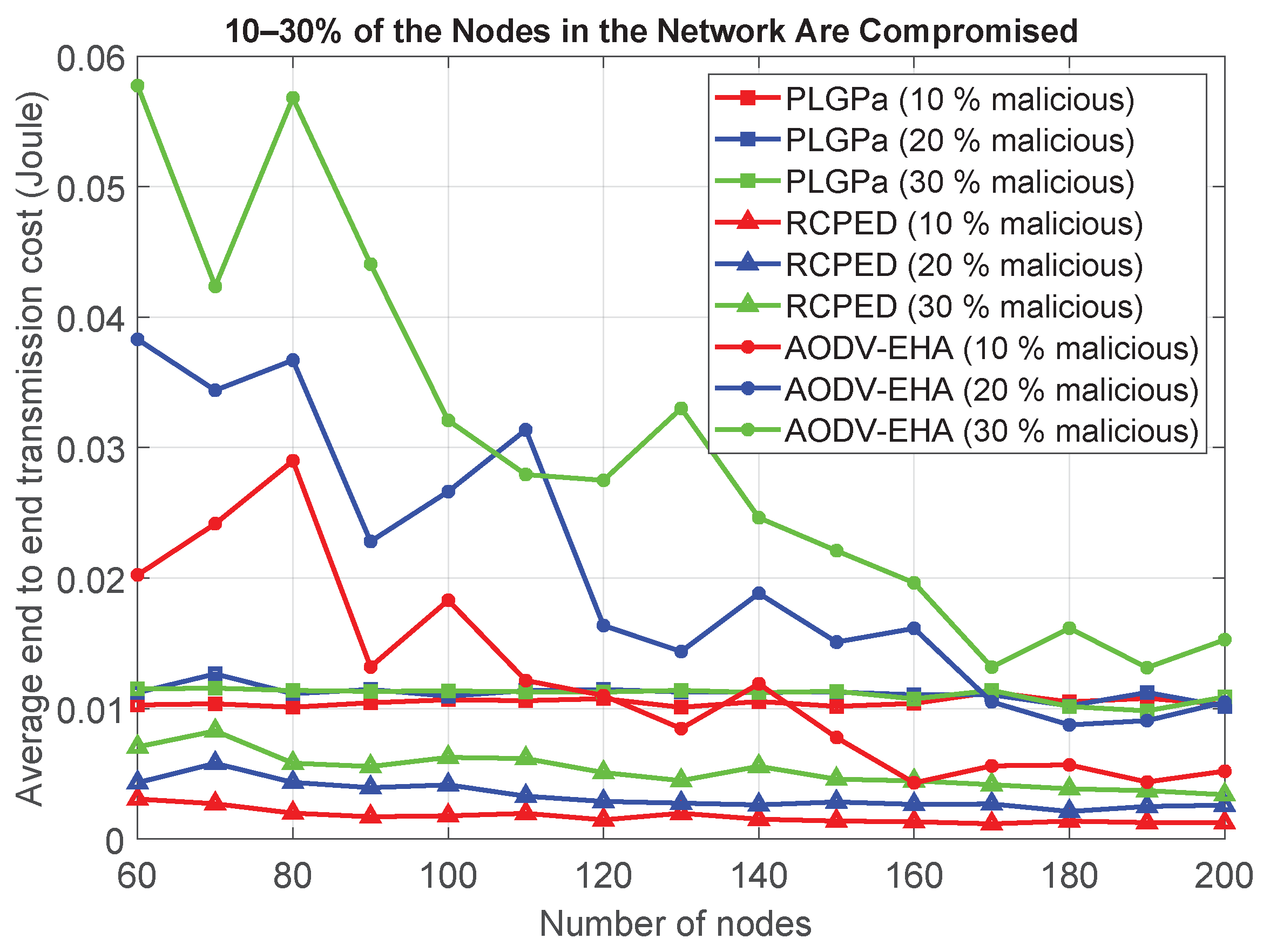
6.6.2. Security Performance
6.6.3. Average Route Length
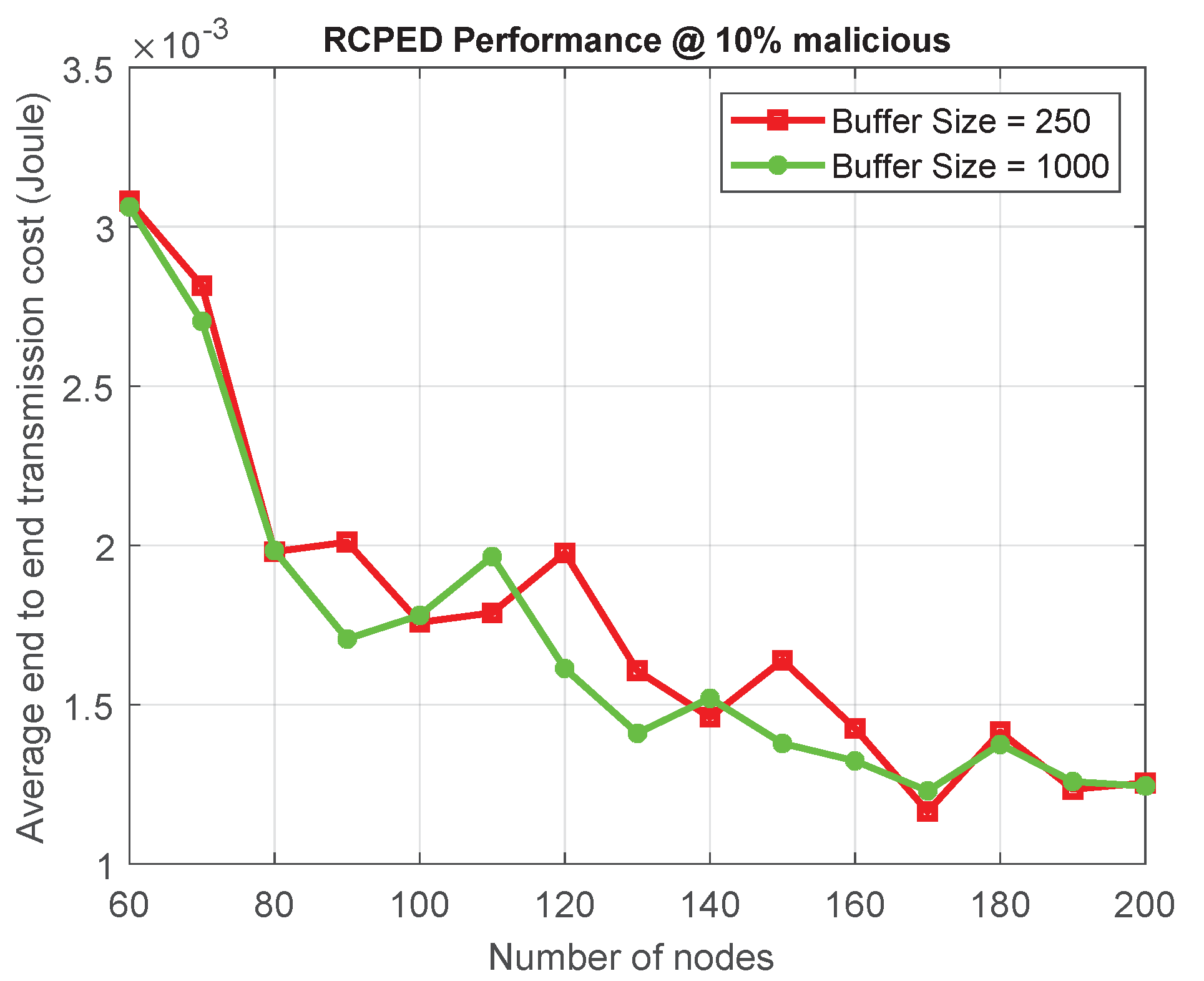
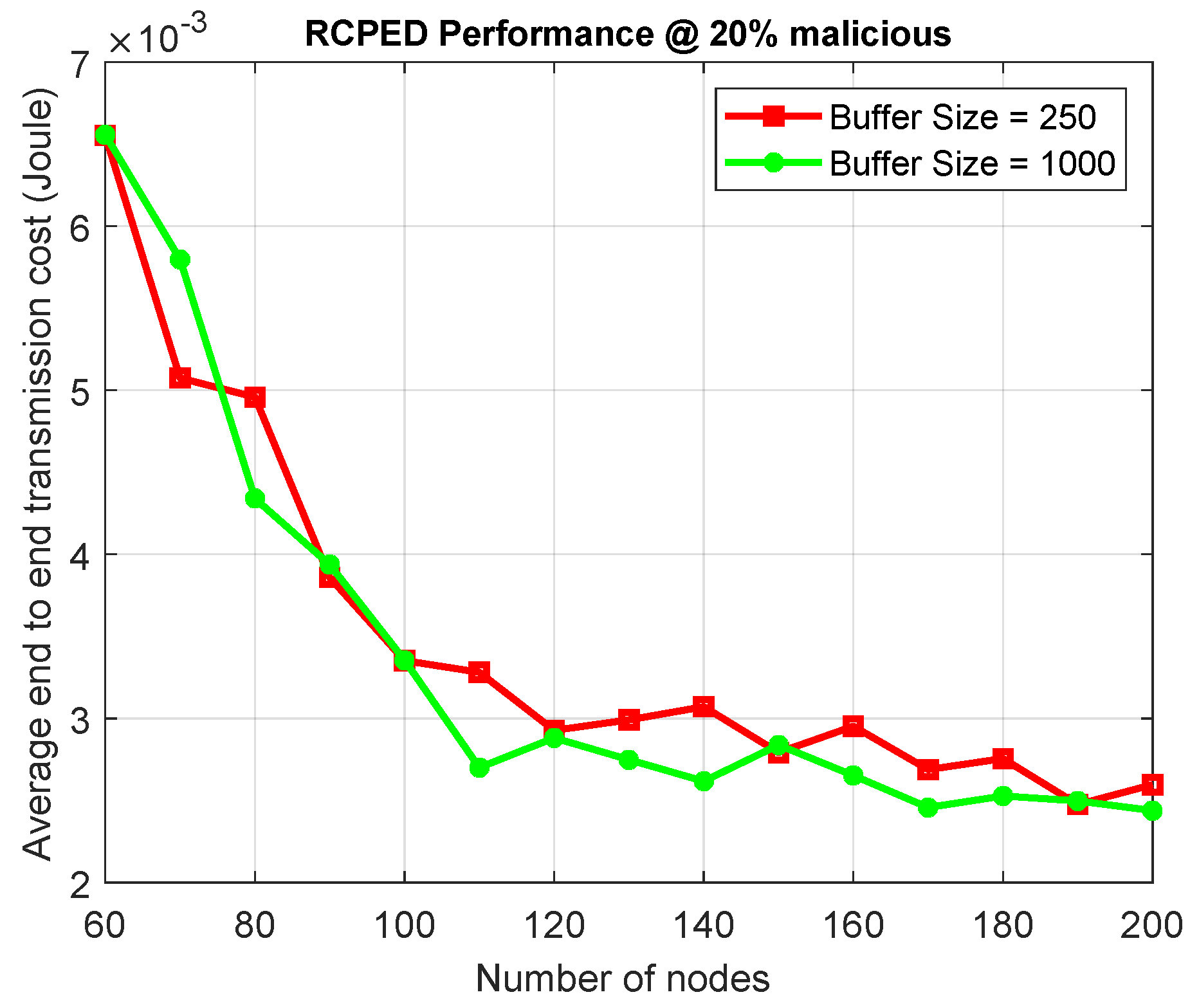
6.6.4. Effect of Buffer Size
7. Conclusions and Future-Work
Author Contributions
Funding
Conflicts of Interest
References
- Tanenbaum, A. Computer Networks, 4th ed.; Prentice Hall Professional Technical Reference; Pearson: London, UK, 2002. [Google Scholar]
- Awoyemi, B.S.; Alfa, A.S.; Maharaj, B.T. Network Restoration in Wireless Sensor Networks for Next-Generation Applications. IEEE Sens. J. 2019, 19, 8352–8363. [Google Scholar] [CrossRef]
- Dias, G.M.; Margi, C.B.; de Oliveira, F.C.; Bellalta, B. Cloud-Empowered, Self-Managing Wireless Sensor Networks: Interconnecting Management Operations at the Application Layer. IEEE Consum. Electron. Mag. 2019, 8, 55–60. [Google Scholar] [CrossRef]
- Yang, S.H. Wireless Sensor Networks: Principles, Design and Applications; Springer: London, UK, 2014. [Google Scholar]
- Liu, J.; Huang, K.; Yao, X. Common-Innovation Subspace Pursuit for Distributed Compressed Sensing in Wireless Sensor Networks. IEEE Sens. J. 2019, 19, 1091–1103. [Google Scholar] [CrossRef]
- Mabrouki, J.; Azrour, M.; Dhiba, D.; Farhaoui, Y.; Hajjaji, S.E. IoT-based data logger for weather monitoring using arduino-based wireless sensor networks with remote graphical application and alerts. Big Data Min. Anal. 2021, 4, 25–32. [Google Scholar] [CrossRef]
- Zhou, L.; Haas, Z. Securing ad hoc networks. Netw. IEEE 1999, 13, 24–30. [Google Scholar] [CrossRef]
- O’Mahony, G.D.; Curran, J.T.; Harris, P.J.; Murphy, C.C. Interference and Intrusion in Wireless Sensor Networks. IEEE Aerosp. Electron. Syst. Mag. 2020, 35, 4–16. [Google Scholar] [CrossRef]
- Xie, H.; Yan, Z.; Yao, Z.; Atiquzzaman, M. Data Collection for Security Measurement in Wireless Sensor Networks: A Survey. IEEE Internet Things J. 2019, 6, 2205–2224. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutor. 2020, 22, 616–644. [Google Scholar] [CrossRef]
- Yao, S.; Li, Z.; Guan, J.; Liu, Y. Stochastic Cost Minimization Mechanism Based on Identifier Network for IoT Security. IEEE Internet Things J. 2020, 7, 3923–3934. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Muta, O. A Game-Theoretic Approach for Enhancing Security and Data Trustworthiness in IoT Applications. IEEE Internet Things J. 2020, 7, 11250–11261. [Google Scholar] [CrossRef]
- Vasserman, E.; Hopper, N. Vampire Attacks: Draining Life from Wireless Ad Hoc Sensor Networks. IEEE Trans. Mob. Comput. 2013, 12, 318–332. [Google Scholar] [CrossRef]
- Gong, P. Energy Efficient and Secure Wireless Communications for Wireless Sensor Networks. Ph.D. Thesis, City, University of London, London, UK, 2017. [Google Scholar]
- Hei, X.; Du, X.; Wu, J.; Hu, F. Defending Resource Depletion Attacks on Implantable Medical Devices. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Malasri, K.; Wang, L. Securing wireless implantable devices for healthcare: Ideas and challenges. Commun. Mag. IEEE 2009, 47, 74–80. [Google Scholar] [CrossRef]
- Raymond, D.R.; Midkiff, S. Denial-of-Service in Wireless Sensor Networks: Attacks and Defenses. Pervasive Comput. IEEE 2008, 7, 74–81. [Google Scholar] [CrossRef]
- Deng, J.; Han, R.; Mishra, S. Defending Against Path-based DoS Attacks in Wireless Sensor Networks. In 3rd ACM Workshop on Security of Ad Hoc and Sensor Networks; SASN ’05; ACM: New York, NY, USA, 2005; pp. 89–96. [Google Scholar] [CrossRef]
- Chen, Y.; Hwang, K. Spectral Analysis of TCP Flows for Defense Against Reduction-of-Quality Attacks. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 24–28 June 2007; pp. 1203–1210. [Google Scholar] [CrossRef]
- Guirguis, M.; Bestavros, A.; Matta, I.; Zhang, Y. Reduction of quality (RoQ) attacks on Internet end-systems. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; Volume 2, pp. 1362–1372. [Google Scholar] [CrossRef]
- Sun, H.; Lui, J.; Yau, D. Defending against low-rate TCP attacks: Dynamic detection and protection. In Proceedings of the 12th IEEE International Conference on Network Protocols, Berlin, Germany, 8 October 2004; pp. 196–205. [Google Scholar] [CrossRef]
- Yang, G.; Gerla, M.; Sanadidi, M. Defense against low-rate TCP-targeted denial-of-service attacks. In Proceedings of the Ninth International Symposium on Computers And Communications (IEEE Cat. No. 04TH8769), Alexandria, Egypt, 28 June–1 July 2004; Volume 1, pp. 345–350. [Google Scholar] [CrossRef]
- Raymond, D.; Marchany, R.; Brownfield, M.; Midkiff, S. Effects of Denial of Sleep Attacks on Wireless Sensor Network MAC Protocols. IEEE Trans. Veh. Technol. 2006, 58, 367–380. [Google Scholar] [CrossRef]
- Li, X.; Jia, Z.; Zhang, P.; Zhang, R.; Wang, H. Trust-based on-demand multipath routing in mobile ad hoc networks. Inf. Secur. IET 2010, 4, 212–232. [Google Scholar] [CrossRef]
- Tang, J.; Cheng, Y.; Zhuang, W. Real-Time Misbehavior Detection in IEEE 802.11-Based Wireless Networks: An Analytical Approach. IEEE Trans. Mob. Comput. 2014, 13, 146–158. [Google Scholar] [CrossRef]
- Mpitziopoulos, A.; Gavalas, D.; Konstantopoulos, C.; Pantziou, G. A survey on jamming attacks and countermeasures in WSNs. Commun. Surv. Tutor. IEEE 2009, 11, 42–56. [Google Scholar] [CrossRef]
- Parno, B.; Luk, M.; Gaustad, E.; Perrig, A. Secure Sensor Network Routing: A Clean-slate Approach. In Proceedings of the 2006 ACM CoNEXT Conference, Lisboa, Portugal, 4–7 December 2006; CoNEXT ’06. ACM: New York, NY, USA, 2006; pp. 11:1–11:13. [Google Scholar] [CrossRef]
- Stajano, F.; Anderson, R.J. The Resurrecting Duckling: Security Issues for Ad-hoc Wireless Networks. In Proceedings of the 7th International Workshop on Security Protocols, Cambridge, UK, 3–5 April 2000; Springer: London, UK, 2000; pp. 172–194. [Google Scholar]
- Cao, X.; Shila, D.; Cheng, Y.; Yang, Z.; Zhou, Y.; Chen, J. Ghost-in-ZigBee: Energy Depletion Attack on ZigBee based Wireless Networks. Internet Things J. IEEE 2016, 3, 816–829. [Google Scholar] [CrossRef]
- Gong, P.; Xu, Q.; Chen, T. Energy Harvesting Aware routing protocol for wireless sensor networks. In Proceedings of the 2014 9th International Symposium on Communication Systems, Networks & Digital Sign (CSNDSP), Manchester, UK, 23–25 July 2014; pp. 171–176. [Google Scholar] [CrossRef]
- Chandola, V.; Banerjee, A.; Kumar, V. Anomaly Detection: A Survey. ACM Comput. Surv. 2009, 41. [Google Scholar] [CrossRef]
- DeGroot, M.; Schervish, M. Probability and Statistics; Addison-Wesley series in statistics; Addison-Wesley: Boston, MA, USA, 2002. [Google Scholar]
- Chatterjee, S.; Hadi, A. Regression Analysis by Example; Wiley Series in Probability and Statistics; Wiley: Hoboken, NJ, USA, 2006. [Google Scholar]
- Pozar, D. Microwave Engineering; Wiley: Hoboken, NJ, USA, 2004. [Google Scholar]
- NMEA-0183V20; Publications and Standards from the National Marine Electronics Association (NMEA)/NMEA 0183. NMEA: Severna Park, MD, USA, 2008.
- Sadek, A.K.; Yu, W.; Liu, K.J.R. On the energy efficiency of cooperative communications in wireless sensor networks. ACM Trans. Sen. Netw. 2010, 6, 5:1–5:21. [Google Scholar] [CrossRef]
- Karaki, S.; Chedid, R.; Ramadan, R. Probabilistic performance assessment of autonomous solar-wind energy conversion systems. Energy Convers. IEEE Trans. 1999, 14, 766–772. [Google Scholar] [CrossRef]
- Collins, R.D.; Crowther, K.G. Systems-based modeling of generation variability under alternate geographic configurations of photovoltaic (PV) installations in Virginia. Energy Policy 2011, 39, 6262–6270. [Google Scholar] [CrossRef]
- Kleinschmidt, J.; Borelli, W.; Pellenz, M. An Analytical Model for Energy Efficiency of Error Control Schemes in Sensor Networks. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 24–28 June 2007; pp. 3895–3900. [Google Scholar]
- Kim, K.; Lee, W.; Choi, C. DSML: Dual Signal Metrics for Localization in Wireless Sensor Networks. In Proceedings of the 2008 IEEE Wireless Communications and Networking Conference, Las Vegas, NV, USA, 31 March–3 April 2008; pp. 2355–2360. [Google Scholar] [CrossRef]
- Raskovic, D.; Giessel, D. Battery-Aware Embedded GPS Receiver Node. In Proceedings of the 2007 Fourth Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services (MobiQuitous), Philadelphia, PA, USA, 6–10 August 2007; pp. 1–6. [Google Scholar] [CrossRef]
- Huang, W.; Abu Qahouq, J.A. An Online Battery Impedance Measurement Method Using DC-DC Power Converter Control. IEEE Trans. Ind. Electron. 2014, 61, 5987–5995. [Google Scholar] [CrossRef]
- Jiang, J.A.; Zheng, X.Y.; Chen, Y.F.; Wang, C.H.; Chen, P.T.; Chuang, C.L.; Chen, C.P. A Distributed RSS-Based Localization Using a Dynamic Circle Expanding Mechanism. Sens. J. IEEE 2013, 13, 3754–3766. [Google Scholar] [CrossRef]
- Karagiannis, M.; Chatzigiannakis, I.; Rolim, J. Multilateration: Methods for Clustering Intersection Points for Wireless Sensor Networks Localization with Distance Estimation Error. Int. J. Innov. Manag. Technol. 2012, arXiv:1203.3704. [Google Scholar]
- Niculescu, D.; Nath, B. Ad hoc positioning system (APS). In Proceedings of the GLOBECOM’01, IEEE Global Telecommunications Conference (Cat. No.01CH37270), San Antonio, TX, USA, 25–29 November 2001; Volume 5, pp. 2926–2931. [Google Scholar] [CrossRef]
- Chen, R.; Snow, M.; Park, J.M.; Refaei, M.; Eltoweissy, M. NIS02-3: Defense against Routing Disruption Attacks in Mobile Ad Hoc Networks. In Proceedings of the Global Telecommunications Conference, GLOBECOM ’06, San Francisco, CA, USA, 27 November–1 December 2006; pp. 1–5. [Google Scholar] [CrossRef]
- Darwiche, P.A. Modeling and Reasoning with Bayesian Networks, 1st ed.; Cambridge University Press: New York, NY, USA, 2009. [Google Scholar]
- Yi, P.; Zhu, T.; Zhang, Q.; Wu, Y.; Li, J. Green firewall: An energy-efficient intrusion prevention mechanism in wireless sensor network. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 3037–3042. [Google Scholar] [CrossRef]
- Ishizaka, A.; Nemery, P. Multi-Criteria Decision Analysis: Methods and Software; John Wiley & Sons: Chichester, UK, 2013. [Google Scholar]
- Gong, P.; Chen, T.; Xu, Q. ETARP: An Energy Efficient Trust-Aware Routing Protocol for Wireless Sensor Networks. J. Sens. 2015, 2015, 469793. [Google Scholar] [CrossRef]
- Saaty, T.L. A scaling method for priorities in hierarchical structures. J. Math. Psychol. 1977, 15, 234–281. [Google Scholar] [CrossRef]
- Miller, G.A. The Magical Number Seven, Plus or Minus Two: Some Limits on Our Capacity for Processing Information. Psychol. Rev. 1956, 63, 81–97. [Google Scholar] [CrossRef]
- Salo, A.A.; Hämäläinen, R.P. On the measurement of preferences in the analytic hierarchy process. J. Multi-Criteria Decis. Anal. 1997, 6, 309–319. [Google Scholar] [CrossRef]
- Poyhonen, M.A.; Hamalainen, R.P.; Salo, A.A. An Experiment on the Numerical Modelling of Verbal Ratio Statements. J. Multi-Criteria Decis. Anal. 1997, 6, 1–10. [Google Scholar] [CrossRef]
- Lootsma, F.A. Scale sensitivity in the multiplicative AHP and SMART. J. Multi-Criteria Decis. Anal. 1993, 2, 87–110. [Google Scholar] [CrossRef]
- IEEE. P802.15.4m/D4, Oct 2013—IEEE Draft Standard for Local and Metropolitan Area Networks—Part 15.4: Low Rate Wireless Personal Area Networks (LR-WPANs)—Amendment 6: TV White Space Between 54 MHz and 862MHz Physical Layer; IEEE: Piscataway, NJ, USA, 2013; pp. 1–152. [Google Scholar]
- Bankovic, Z.; Fraga, D.; Moya, J.M.; Vallejo, J.C. Detecting Unknown Attacks in Wireless Sensor Networks That Contain Mobile Nodes. Sensors 2012, 12, 10834–10850. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Zhou, F.; Du, J. LDTS: A Lightweight and Dependable Trust System for Clustered Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 924–935. [Google Scholar] [CrossRef]
- Ganesh, S.; Amutha, R. Efficient and secure routing protocol for wireless sensor networks through SNR based dynamic clustering mechanisms. J. Commun. Netw. 2013, 15, 422–429. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Wang, F.; Shu, L.; Guizani, M. An Efficient Distributed Trust Model for Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1228–1237. [Google Scholar] [CrossRef]



| Papers | Main Topic | Comments |
|---|---|---|
| [15] | Resource depletion attacks | Introduction to resource depletion attacks, such as denial of service (DoS) attacks and forced authentication attacks. |
| [16,17,18] | DoS attacks threatening WSNs | General studies on DoS attacks. |
| [19] | Reduction in quality (RoQ) attacks | General studies on RoQ attacks, a downgraded version of distributed DoS attacks. |
| [20,21,22] | Countermeasures against RoQ attacks | Can offer protection against RoQ attacks. However, most of them can only be applied on transport layer and not in the routing layer. |
| [23,24,25,26,27,28,29] | Power-draining attacks | General discussions on power-draining attacks. This is a subcategory of resource depletion attacks. |
| [13] | Vampire attacks | General discussions on vampire attacks. This is an instance of power-draining attacks. |
| [13,27] | Countermeasures against vampire attacks | Both are clean-slate secure sensor network routing protocol that can offer protection against vampire attacks. However, they rely heavily on cryptographic methods and may incur extra energy costs. |
| H | L | S | |
|---|---|---|---|
| ? | F | T | |
| ? | T | F | |
| ? | T | T |
| H | F(h) | H | L | H | S | ||
|---|---|---|---|---|---|---|---|
| T | 0.8 | T | T | 0.1 | T | T | 0.1 |
| F | 0.2 | T | F | 0.9 | T | F | 0.9 |
| F | T | 0.8 | F | T | 0.9 | ||
| F | F | 0.2 | F | F | 0.1 |
| Degree of Importance | Definition |
|---|---|
| 1 | Equal Importance |
| 2 | Weak |
| 3 | Moderate Importance |
| 4 | Moderate Plus |
| 5 | Strong Importance |
| 6 | Strong Plus |
| 7 | Very Strong or demonstrated Importance |
| 8 | Very Very Strong |
| 9 | Extreme Importance |
| Scale Types | Equal Importance | Weak | Moderate Importance | Moderate Plus | Strong Importance | Strong Plus | Very Strong Importance | Very Very Strong | Extreme Importance |
|---|---|---|---|---|---|---|---|---|---|
| Linear | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 |
| Power | 1 | 4 | 9 | 16 | 25 | 36 | 49 | 64 | 81 |
| Geometric | 1 | 2 | 4 | 8 | 16 | 32 | 64 | 128 | 256 |
| Logarithmic | 1 | 1.58 | 2 | 2.32 | 2.58 | 2.81 | 3 | 3.17 | 3.32 |
| Square Root | 1 | 1.41 | 1.73 | 2 | 2.23 | 2.45 | 2.65 | 2.83 | 3 |
| Asymptotical | 0 | 0.12 | 0.24 | 0.36 | 0.46 | 0.55 | 0.63 | 0.70 | 0.76 |
| Inverse Linear | 1 | 1.13 | 1.29 | 1.5 | 1.8 | 2.25 | 3 | 4.5 | 9 |
| Balanced | 1 | 1.22 | 1.5 | 1.86 | 2.33 | 3 | 4 | 5.67 | 9 |
| Parameters | Descriptions |
|---|---|
| Simulation Area | 500 m × 500 m |
| Node Radio Range | 250 m |
| Traffic Type | CBR |
| Packet Size | 127 bytes |
| Data Rate | 20 kbps |
| SNR Threshold | 10 dB |
| Processing Power Level | W |
| Receiving Power Level | W |
| Outage Requirement | |
| Variance of AWGN | W/Hz |
| Path-loss Exponent | 2.33 |
| Maximum Output Power of Solar Cell on Sensor Nodes | W |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gong, P.; Chen, T.M.; Xu, P. Resource-Conserving Protection against Energy Draining (RCPED) Routing Protocol for Wireless Sensor Networks. Network 2022, 2, 83-105. https://doi.org/10.3390/network2010007
Gong P, Chen TM, Xu P. Resource-Conserving Protection against Energy Draining (RCPED) Routing Protocol for Wireless Sensor Networks. Network. 2022; 2(1):83-105. https://doi.org/10.3390/network2010007
Chicago/Turabian StyleGong, Pu, Thomas M. Chen, and Peng Xu. 2022. "Resource-Conserving Protection against Energy Draining (RCPED) Routing Protocol for Wireless Sensor Networks" Network 2, no. 1: 83-105. https://doi.org/10.3390/network2010007
APA StyleGong, P., Chen, T. M., & Xu, P. (2022). Resource-Conserving Protection against Energy Draining (RCPED) Routing Protocol for Wireless Sensor Networks. Network, 2(1), 83-105. https://doi.org/10.3390/network2010007






