Call Blocking Probabilities under a Probabilistic Bandwidth Reservation Policy in Mobile Hotspots
Abstract
1. Introduction
2. The Probabilistic BR Loss Model
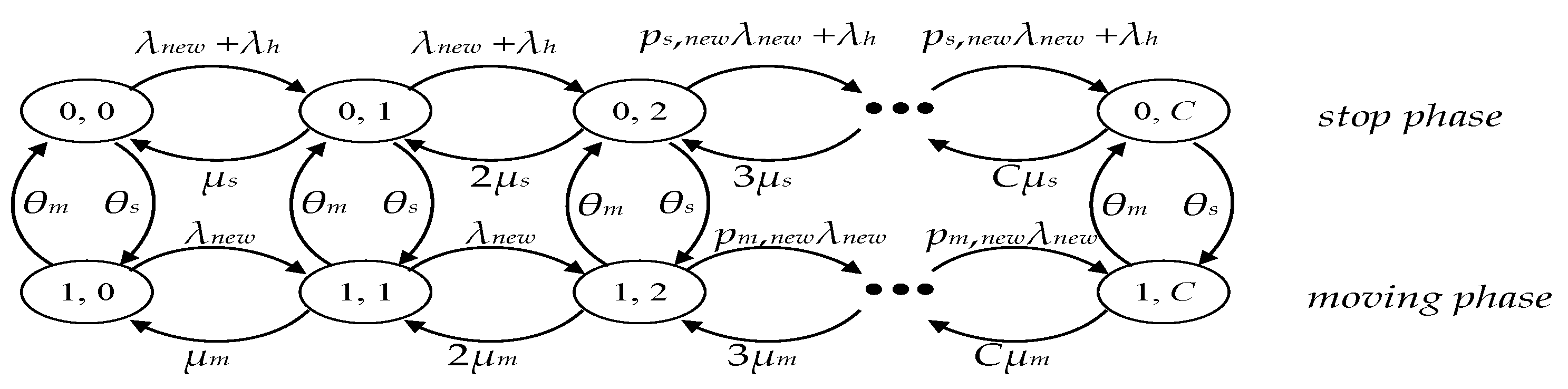
2.1. The Analytical Model
2.2. An Iterative Algorithm for the Determination of P(i,n)
2.3. CBP Determination of New and Handover Calls
3. The Generalized Probabilistic BR Loss Model
3.1. The Analytical Model
3.2. CBP Determination of New and Handover Calls
4. Performance Evaluation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| b.u. | Bandwidth unit |
| AP | Access point |
| BR | Bandwidth reservation |
| CAC | Call admission control |
| CBP | Call blocking probabilities |
| CS | Complete sharing |
| NB | NodeB |
| QoS | Quality of service |
| WLAN | Wireless local area network |
Notation
| CBP of new calls (stop phase) | |
| CBP of new calls (moving phase) | |
| Total CBP of new calls | |
| CBP of handover calls (stop phase) | |
| CBP of handover calls given stop phase | |
| CBP of new calls (stop phase—generalized loss model) | |
| CBP of new calls (moving phase—generalized loss model) | |
| Total CBP of new calls (generalized loss model) | |
| CBP of handover calls (stop phase—generalized loss model) | |
| CBP of handover calls given stop phase (generalized loss model) | |
| C | AP’s WLAN capacity (in b.u.) |
| j | occupied b.u. (j = 0, …, C) |
| P(i,n) | Steady-state probability of phase i (i = 0—stop phase, i = 1—moving phase) with n users in-service |
| Pg(i,n) | Steady-state probability of phase i (i = 0—stop phase, i = 1—moving phase) with n users in-service (generalized loss model) |
| ps,new | Probabilistic BR parameter for new calls in the stop phase |
| pm,new | Probabilistic BR parameter for new calls in the moving phase |
| tnew | BR parameter for new calls (in b.u.) |
| U | Link utilization |
| Ug | Link utilization (generalized loss model) |
| Duration of the stop phase | |
| Duration of the moving phase | |
| λnew | Arrival rate of new calls |
| λh | Arrival rate of handover calls |
| λi(n) | Arrival rate of calls in phase i with n users in-service |
| Service time in the stop phase (exponentially distributed) | |
| Service time in the moving phase (exponentially distributed) |
Appendix A
- state (0,0): P(0,1) + 0.01P(1,0) − 2.05P(0,0) = 0
- state (1,0): 0.05P(0,0) + P(1,1) − 1.01P(1,0) = 0
- state (0,1): 2P(0,0) + 0.01P(1,1) + 2P(0,2) − 3.05P(0,1) = 0
- state (1,1): P(1,0) + 0.05P(0,1) + 2P(1,2) − 2.01P(1,1) = 0
- state (0,2): 2P(0,1) + 0.01P(1,2) + 3P(0,3) − 3.05P(0,2) = 0
- state (1,2): P(1,1) + 0.05P(0,2) + 3P(1,3) − 3.01P(1,2) = 0
- state (0,3): P(0,2) + 0.01P(1,3) + 4P(0,4) − 4.05P(0,3) = 0
- state (1,3): P(1,2) + 0.05P(0,3) + 4P(1,4) − 4.01P(1,3) = 0
- state (0,4): P(0,3) + 0.01P(1,4) − 4.05P(0,4) = 0
- state (1,4): P(1,3) + 0.05P(0,4) − 4.01P(1,4) = 0
- state (0,0):
- state (1,0):
- state (0,1):
- state (1,1):
- state (0,2):
- state (1,2):
- state (0,3):
- state (1,3):
- state (0,0):
- state (1,0):
- state (0,1):
- state (1,1):
- state (0,2):
- state (1,2):
- state (0,3):
- state (1,3):
References
- Halabian, H.; Rengaraju, P.; Lung, C.-H.; Lambadaris, I. A reservation-based call admission control scheme and system modeling in 4G vehicular networks. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 125. [Google Scholar] [CrossRef]
- Głąbowski, M.; Kaliszan, A.; Stasiak, M. Modelling overflow systems with distributed secondary resources. Comput. Netw. 2016, 108, 171–183. [Google Scholar] [CrossRef]
- Chousainov, I.-A.; Moscholios, I.; Kaloxylos, A.; Logothetis, M. Performance Evaluation in Single or Multi-Cluster C-RAN Supporting Quasi-Random Traffic. J. Commun. Softw. Syst. 2020, 16, 170–179. [Google Scholar] [CrossRef]
- Chousainov, I.-A.; Moscholios, I.; Sarigiannidis, P.; Kaloxylos, A.; Logothetis, M. An analytical framework of a C-RAN sup-porting random, quasi-random and bursty traffic. Comput. Netw. 2020, 180, 107410. [Google Scholar] [CrossRef]
- Vazquez-Avila, J.; Cruz-Perez, F.; Ortigoza-Guerrero, L. Performance analysis of fractional guard channel policies in mobile cellular networks. IEEE Trans. Wirel. Commun. 2006, 5, 301–305. [Google Scholar] [CrossRef]
- Kim, Y.; Pack, S.; Lee, W. Mobility-Aware Call Admission Control Algorithm in Vehicular WiFi Networks. In Proceedings of the 2010 IEEE Global Telecommunications Conference, Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Kim, Y.; Ko, H.; Pack, S.; Lee, W.; Shen, X. Mobility-Aware Call Admission Control Algorithm with Handoff Queue in Mobile Hotspots. IEEE Trans. Veh. Technol. 2013, 62, 3903–3912. [Google Scholar] [CrossRef]
- Kim, C.; Klimenok, V.; Dudin, A. Analysis and optimization of Guard Channel Policy in cellular mobile networks with account of retrials. Comput. Oper. Res. 2014, 43, 181–190. [Google Scholar] [CrossRef]
- Moscholios, I.D.; Vassilakis, V.G.; Logothetis, M.D.; Boucouvalas, A.C. State-Dependent Bandwidth Sharing Policies for Wireless Multirate Loss Networks. IEEE Trans. Wirel. Commun. 2017, 16, 5481–5497. [Google Scholar] [CrossRef]
- Omheni, N.; Gharsallah, A.; Zarai, F. An enhanced radio resource management based MIH policies in heterogeneous wireless networks. Telecommun. Syst. 2017, 67, 577–592. [Google Scholar] [CrossRef]
- Panagoulias, P.I.; Moscholios, I.D. Congestion probabilities in the X2 link of LTE networks. Telecommun. Syst. 2019, 71, 585–599. [Google Scholar] [CrossRef]
- Efstratiou, P.; Moscholios, I. User Mobility in a 5G Cell with Quasi-Random Traffic under the Complete Sharing and Bandwidth Reservation Policies. Autom. Control. Comput. Sci. 2019, 53, 376–386. [Google Scholar] [CrossRef]
- Lee, D.-S.; Hsueh, Y.-H. Bandwidth-Reservation Scheme Based on Road Information for Next-Generation Cellular Networks. IEEE Trans. Veh. Technol. 2004, 53, 243–252. [Google Scholar] [CrossRef]
- Pati, H.K. A control-period-based distributed adaptive guard channel reservation scheme for cellular networks. Wirel. Netw. 2013, 19, 1739–1753. [Google Scholar] [CrossRef]
- Nadembega, A.; Hafid, A.; Taleb, T. Mobility Prediction-aware Bandwidth Reservation Scheme for Mobile Networks. IEEE Trans. Veh. Technol. 2014, 64, 2561–2576. [Google Scholar] [CrossRef]
- Moscholios, I.D.; Logothetis, M.D.; Vardakas, J.S.; Boucouvalas, A.C. Performance metrics of a multirate resource sharing teletraffic model with finite sources under the threshold and bandwidth reservation policies. IET Netw. 2015, 4, 195–208. [Google Scholar] [CrossRef]
- Keramidi, I.; Moscholios, I.; Sarigiannidis, P.; Logothetis, M. Blocking Probabilities in a Mobility-Aware CAC Algorithm of a Vehicular WiFi Network. In Proceedings of the 2021 IEEE Microwave Theory and Techniques in Wireless Communications (MTTW), Riga, Latvia, 7–8 October 2021. [Google Scholar]
- Stasiak, M.; Głąbowski, M.; Wisniewski, A.; Zwierzykowski, P. Modeling and Dimensioning of Mobile Networks: From GSM to LTE; John Wiley: Hoboken, NJ, USA, 2011. [Google Scholar]
- Logothetis, M.; Moscholios, I.D. Efficient Multirate Teletraffic Loss Models Beyond Erlang; John Wiley & IEEE Press: Hoboken, NJ, USA, 2019. [Google Scholar]
- Xu, Q.; Ji, H.; Li, X.; Zhang, H. Admission Control Scheme for Service Dropping Performance Improvement in High-Speed Railway Communication Systems. IEEE Trans. Veh. Technol. 2015, 65, 5251–5263. [Google Scholar] [CrossRef]
- Sun, N.; Zhao, Y.; Sun, L.; Wu, Q. Distributed and Dynamic Resource Management for Wireless Service Delivery to High-Speed Trains. IEEE Access 2017, 5, 620–632. [Google Scholar] [CrossRef]
- Kim, S. Bargaining-Based Spectrum Allocation Algorithm for High-Speed Railway Communications. IEEE Access 2021, 9, 71651–71659. [Google Scholar] [CrossRef]
- Huang, Q.; Ko, K.-T.; Iversen, V. Approximation of loss calculation for hierarchical networks with multiservice overflows. IEEE Trans. Commun. 2008, 56, 466–473. [Google Scholar] [CrossRef]
- Hanczewski, S.; Stasiak, M.; Zwierzykowski, P. Modelling of the access part of a multi-service mobile network with service priorities. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 194. [Google Scholar] [CrossRef]
- Rice, S.; Marjanski, A.; Markowitz, H.; Bailey, S. The SIMSCRIPT III programming language for modular object-oriented sim-ulation. In Proceedings of the Winter Simulation Conference, Orlando, FL, USA, 4 December 2005. [Google Scholar]
- Jain, R. The Art of Computer Systems Performance Analysis; John Wiley & Sons: Hoboken, NJ, USA, 1991. [Google Scholar]
- Robinson, S. A statistical process control approach to selecting a warm-up period for a discrete-event simulation. Eur. J. Oper. Res. 2007, 176, 332–346. [Google Scholar] [CrossRef]
- Kaufman, J. Blocking in a Shared Resource Environment. IEEE Trans. Commun. 1981, 29, 1474–1481. [Google Scholar] [CrossRef]
- Roberts, J. A service system with heterogeneous user requirements. In Performance of Data Communications Systems and Their Applications; Elsevier: Amsterdam, The Netherlands, 1981; pp. 423–431. [Google Scholar]
- Głąbowski, M.; Stasiak, M. Point-to-point blocking probability in switching networks with reservation. Ann. Telecommun. 2002, 57, 798–831. [Google Scholar]
- Moscholios, I.D.; Logothetis, M.D.; Nikolaropoulos, P.I. Engset multi-rate state-dependent loss models. Perform. Eval. 2005, 59, 247–277. [Google Scholar] [CrossRef]
- Vassilakis, V.G.; Moscholios, I.D.; Logothetis, M.D. The extended connection-dependent threshold model for call-level performance analysis of multi-rate loss systems under the bandwidth reservation policy. Int. J. Commun. Syst. 2012, 25, 849–873. [Google Scholar] [CrossRef]
- Parniewicz, D.; Stasiak, M.; Zwierzykowski, P. Traffic Engineering for Multicast Connections in Multiservice Cellular Networks. IEEE Trans. Ind. Inform. 2012, 9, 262–270. [Google Scholar] [CrossRef]
- Moscholios, I.; Logothetis, M.; Shioda, S. Performance Evaluation of Multirate Loss Systems Supporting Cooperative Users with a Probabilistic Behavior. IEICE Trans. Commun. 2017, E100.B, 1778–1788. [Google Scholar] [CrossRef]
- Nowak, B.; Piechowiak, M.; Stasiak, M.; Zwierzykowski, P. An analytical model of a system with priorities servicing a mixture of different elastic traffic streams. Bull. Pol. Acad. Sci. Tech. Sci. 2020, 68, 263–270. [Google Scholar]
- Hanczewski, S.; Stasiak, M.; Weissenberg, J. A Model of a System with Stream and Elastic Traffic. IEEE Access 2021, 9, 7789–7796. [Google Scholar] [CrossRef]






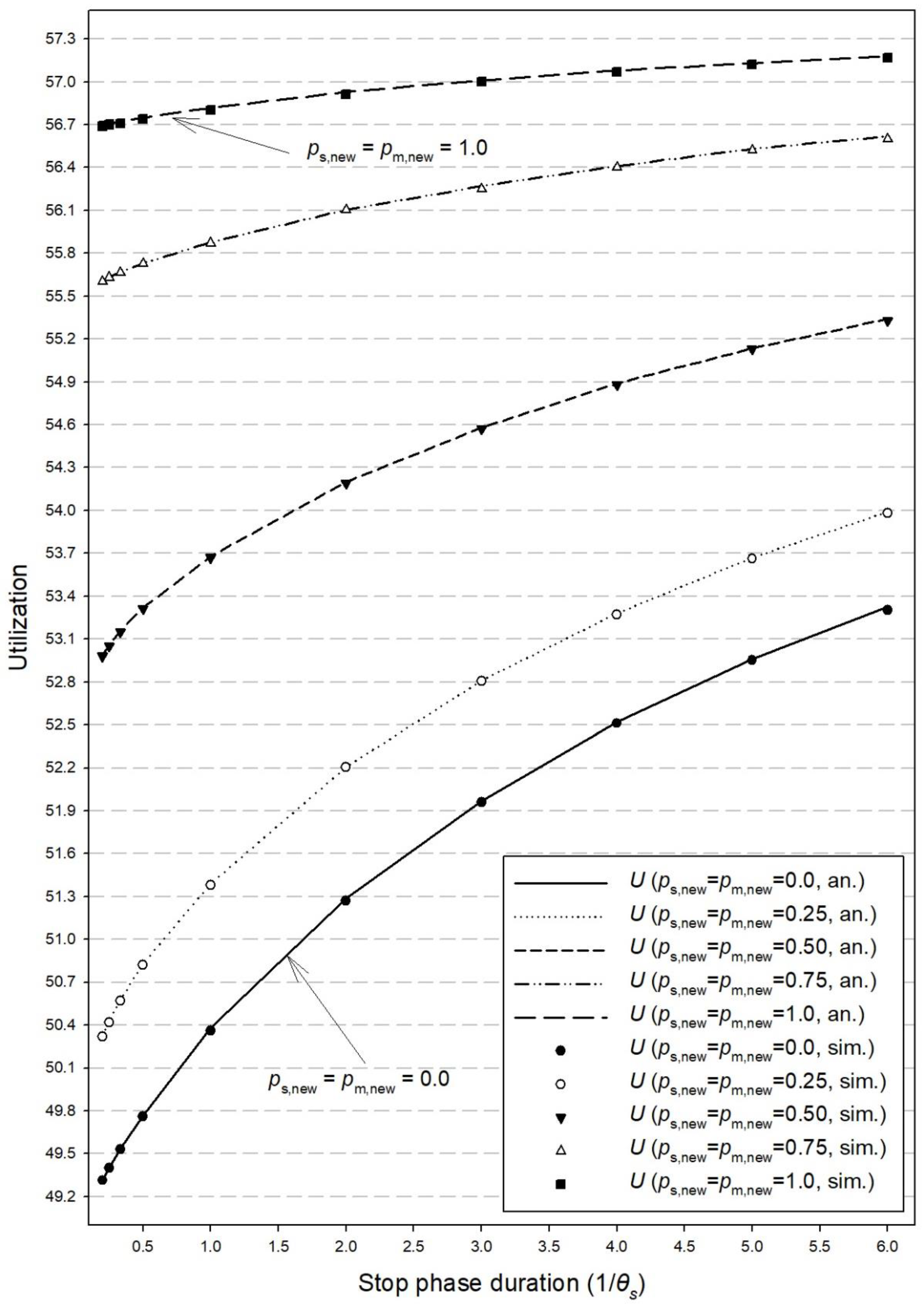
| AP’s WLAN capacity | C = 58 b.u. |
| Duration of the stop phase (exponentially distributed) | = 3 (mean value) |
| Duration of the moving phase (exponentially distributed) | = 6 (mean value) |
| Arrival rate of handover calls (Poisson arrivals) | λh = 24 (fixed value) |
| Arrival rate of new calls (Poisson arrivals) | λnew = 2, 4, 6, 8, 10, 12, 14, 16, 18, 20 (variable value) |
| Service time in the stop phase (exponentially distributed) | = 6 (mean value) |
| Service time in the moving phase (exponentially distributed) | = 6 (mean value) |
| BR parameter (for new calls) | tnew = 8 b.u. |
| Probabilistic BR parameters (stop phase) | ps,new = 0.0, 0.25, 0.50, 0.75, 1.0 |
| Probabilistic BR parameters (moving phase) | pm,new = 0.0, 0.25, 0.50, 0.75, 1.0 |
| Number of simulation runs and generated calls/run | Mean values of eight runs with 106 generated calls/run and 5% of them not taken into account (warm-up period) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Keramidi, I.P.; Moscholios, I.D.; Sarigiannidis, P.G. Call Blocking Probabilities under a Probabilistic Bandwidth Reservation Policy in Mobile Hotspots. Telecom 2021, 2, 554-573. https://doi.org/10.3390/telecom2040031
Keramidi IP, Moscholios ID, Sarigiannidis PG. Call Blocking Probabilities under a Probabilistic Bandwidth Reservation Policy in Mobile Hotspots. Telecom. 2021; 2(4):554-573. https://doi.org/10.3390/telecom2040031
Chicago/Turabian StyleKeramidi, Irene P., Ioannis D. Moscholios, and Panagiotis G. Sarigiannidis. 2021. "Call Blocking Probabilities under a Probabilistic Bandwidth Reservation Policy in Mobile Hotspots" Telecom 2, no. 4: 554-573. https://doi.org/10.3390/telecom2040031
APA StyleKeramidi, I. P., Moscholios, I. D., & Sarigiannidis, P. G. (2021). Call Blocking Probabilities under a Probabilistic Bandwidth Reservation Policy in Mobile Hotspots. Telecom, 2(4), 554-573. https://doi.org/10.3390/telecom2040031








