Radio Frequency Fingerprinting Authentication for IoT Networks Using Siamese Networks
Abstract
1. Introduction
- Extensive experiments using ten ADALM-PLUTO Software-Defined Radios (SDRs) collected from 19,920 frames, each containing 72 I/Q samples in the header and 1728 I/Q samples in the payload. The dataset is made publicly available through a GitHub repository (https://github.com/rajudhakal1/Adalm-Pluto-RF-fingerprinting-dataset, acceessed on 17 August 2025).
- The Siamese network was adapted and trained with I/Q samples from seven ADALM-PLUTO devices using data from two devices: one as an unknown device and the other as a validation device.
- A novel algorithm called Similarity-Based Embedding Classification (SBEC) was developed to identify both in-library and out-of-library devices, and its performance was evaluated using a real-world dataset collected from SDRs.
- SBEC can identify in-library and out-of-library devices with an impressive accuracy of approximately 98%.
2. Related Work
3. Background
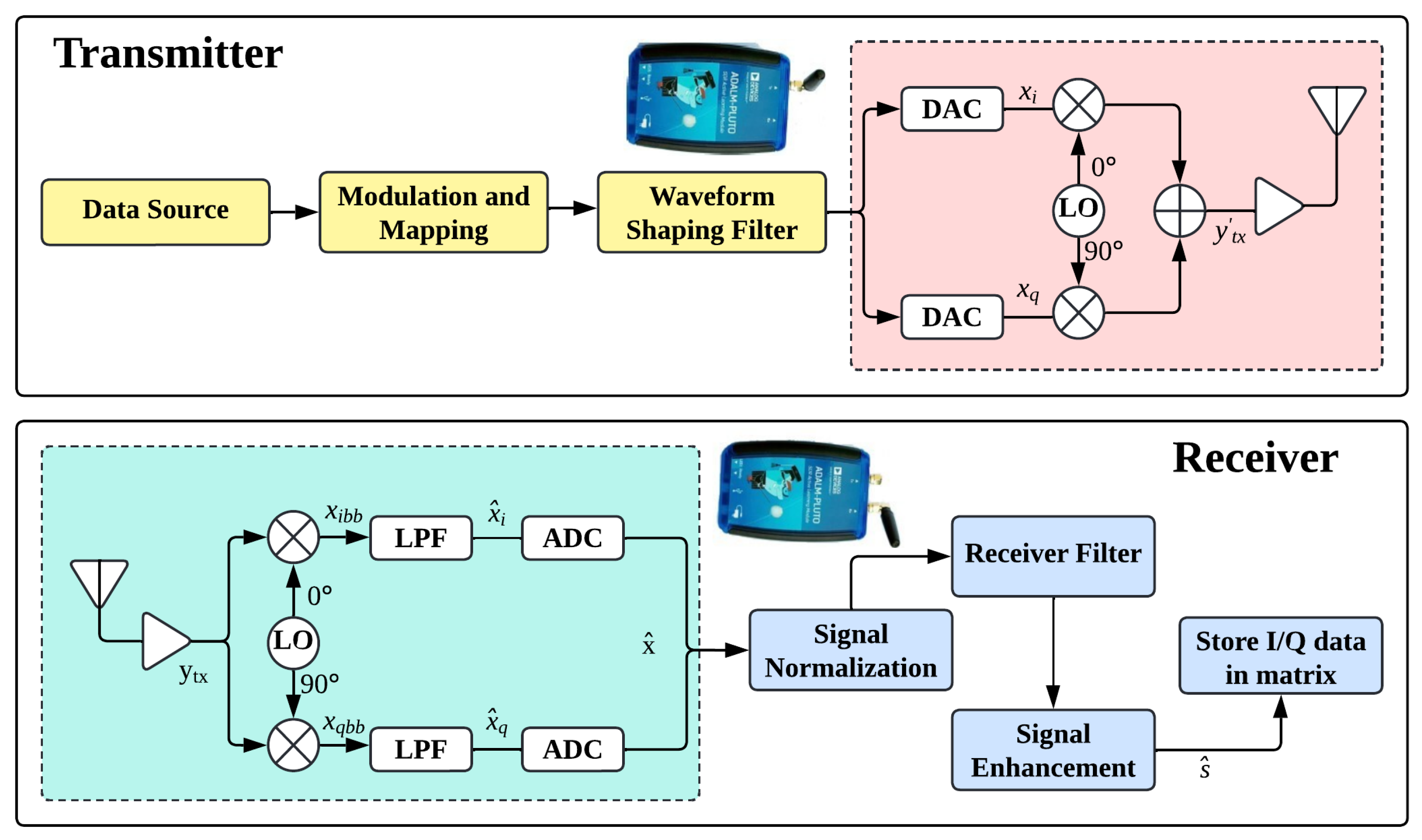
3.1. Transmitter-Side Signal Modeling
3.2. Receiver-Side Signal Modeling
3.3. I/Q Data Storage and Formatting
3.4. System Model
4. Methodology
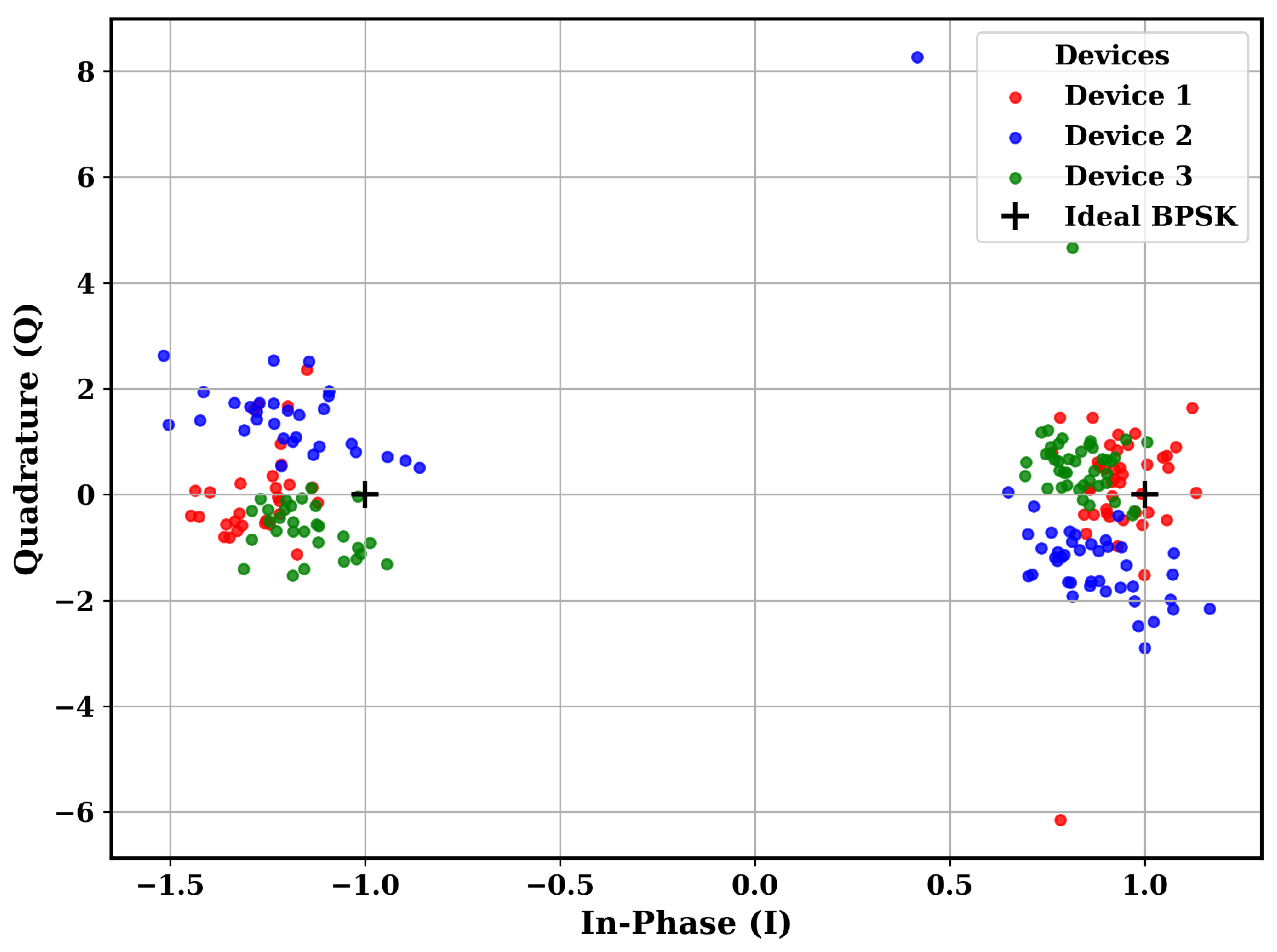
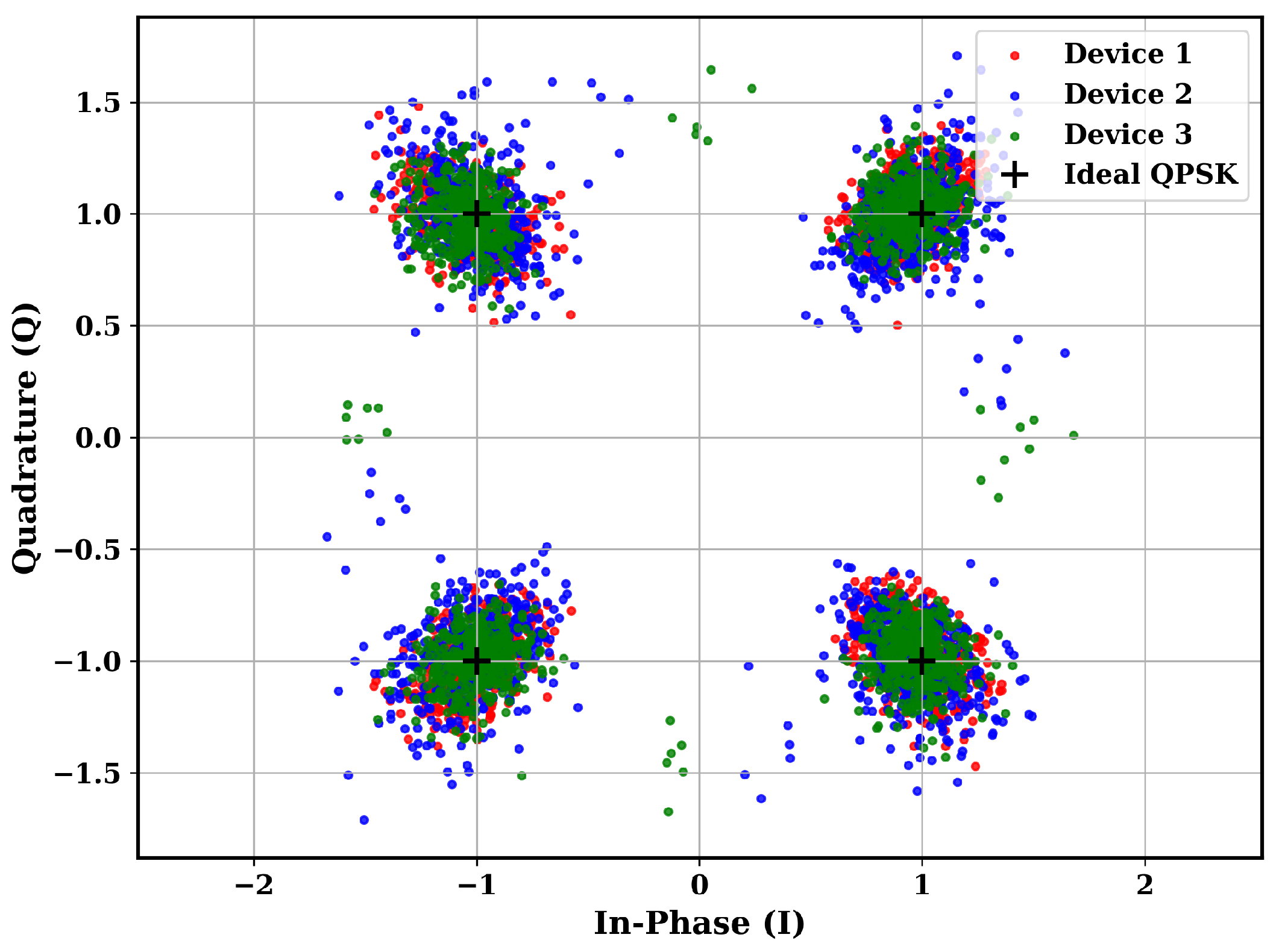
4.1. ADALM-PLUTO Dataset
4.2. Base Model for Siamese Network
4.3. Siamese Network
- and represent the outputs from the two CNNs;
- is the Manhattan or L1 distance between and ;
- The indices i range from 1 to r, where r is the dimensionality of the fingerprint vectors.
4.4. Contrastive Loss
- For similar pairs (), the loss reduces to , which penalizes the model when similar pairs are far apart, encouraging the network to bring their embeddings closer together.
- For dissimilar pairs (), the loss becomes , which penalizes the model only when the distance between dissimilar pairs is less than the margin m. This pushes embeddings of dissimilar pairs at least m units apart in the learned space.
4.5. Similarity-Based Embedding Classification (SBEC)
| Algorithm 1: Similarity-Based Embedding Classification (SBEC) |
 |
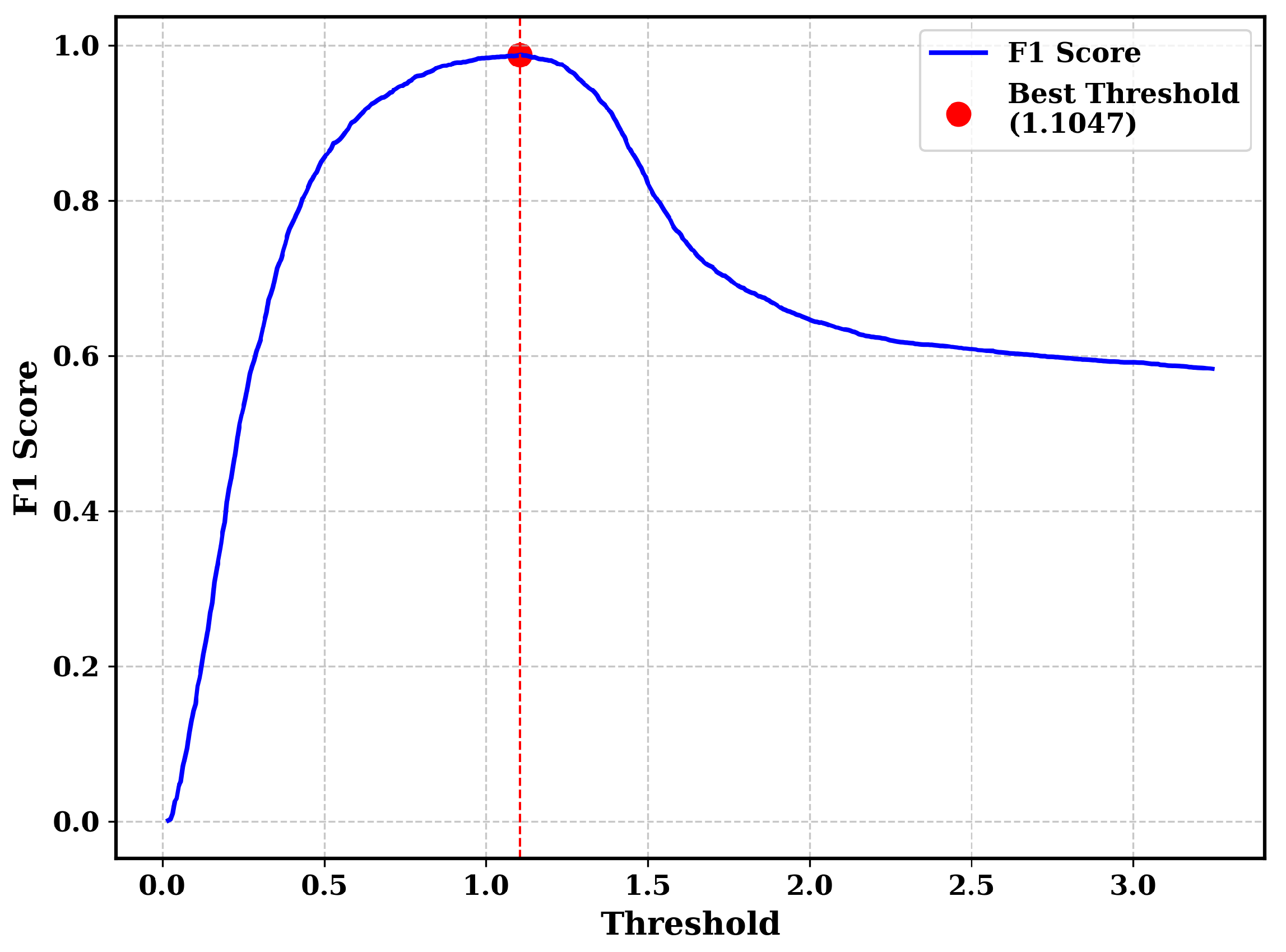
4.6. Threshold Calculation
5. Results and Discussion
5.1. Siamese Network Training and Learning Curve
5.2. Threshold Calculation
5.3. Performance of SBEC
5.3.1. Classification Dynamics with Confusion Matrices
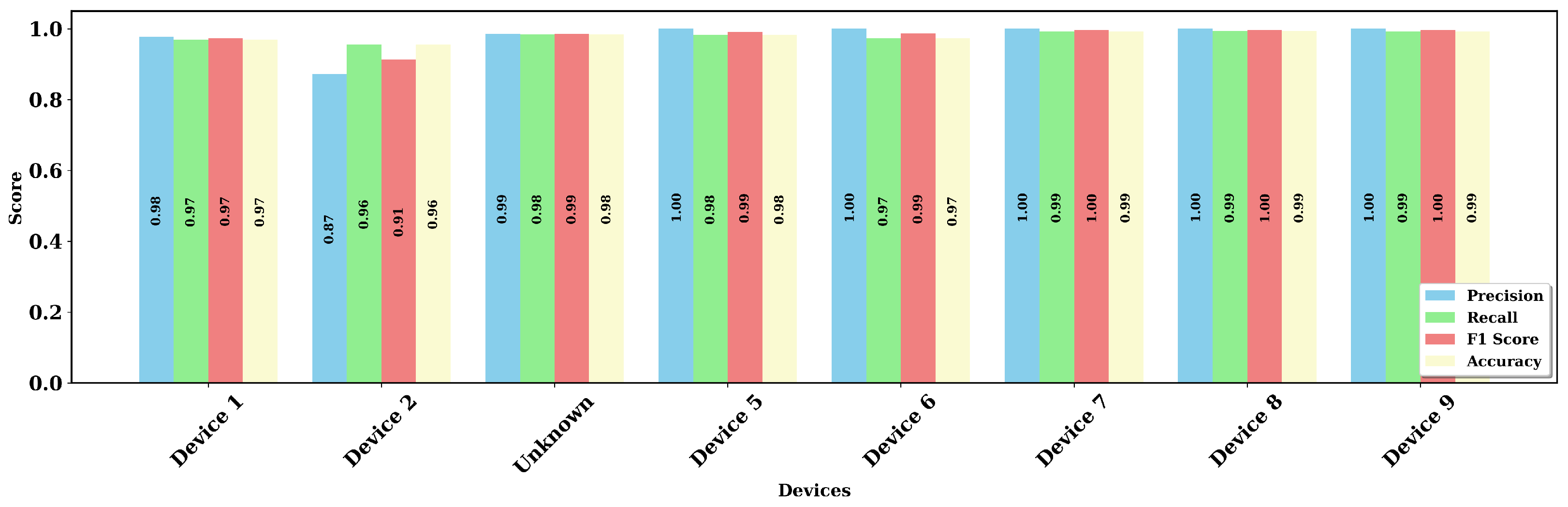
5.3.2. Comparison of Precision, Recall, F1-Score, and Accuracy of Each Class
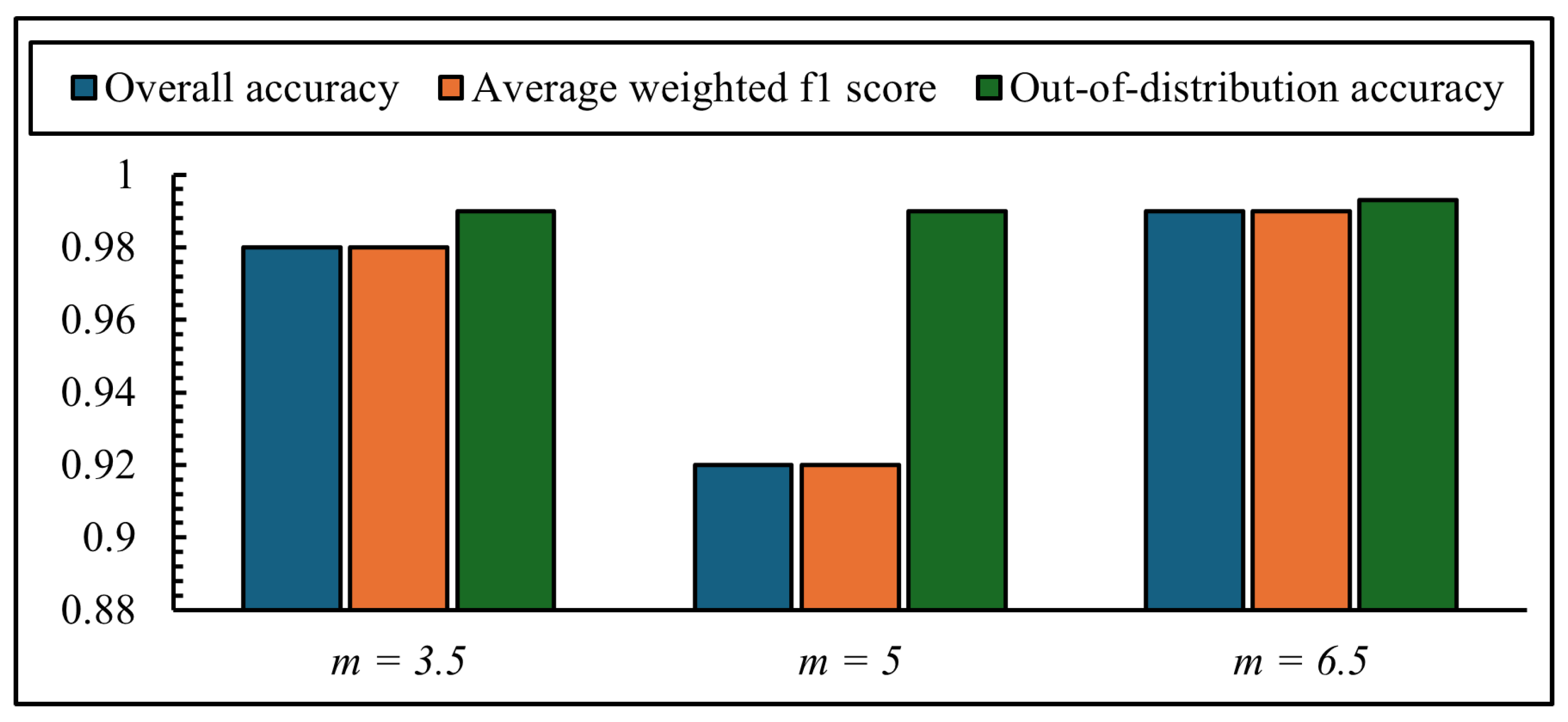
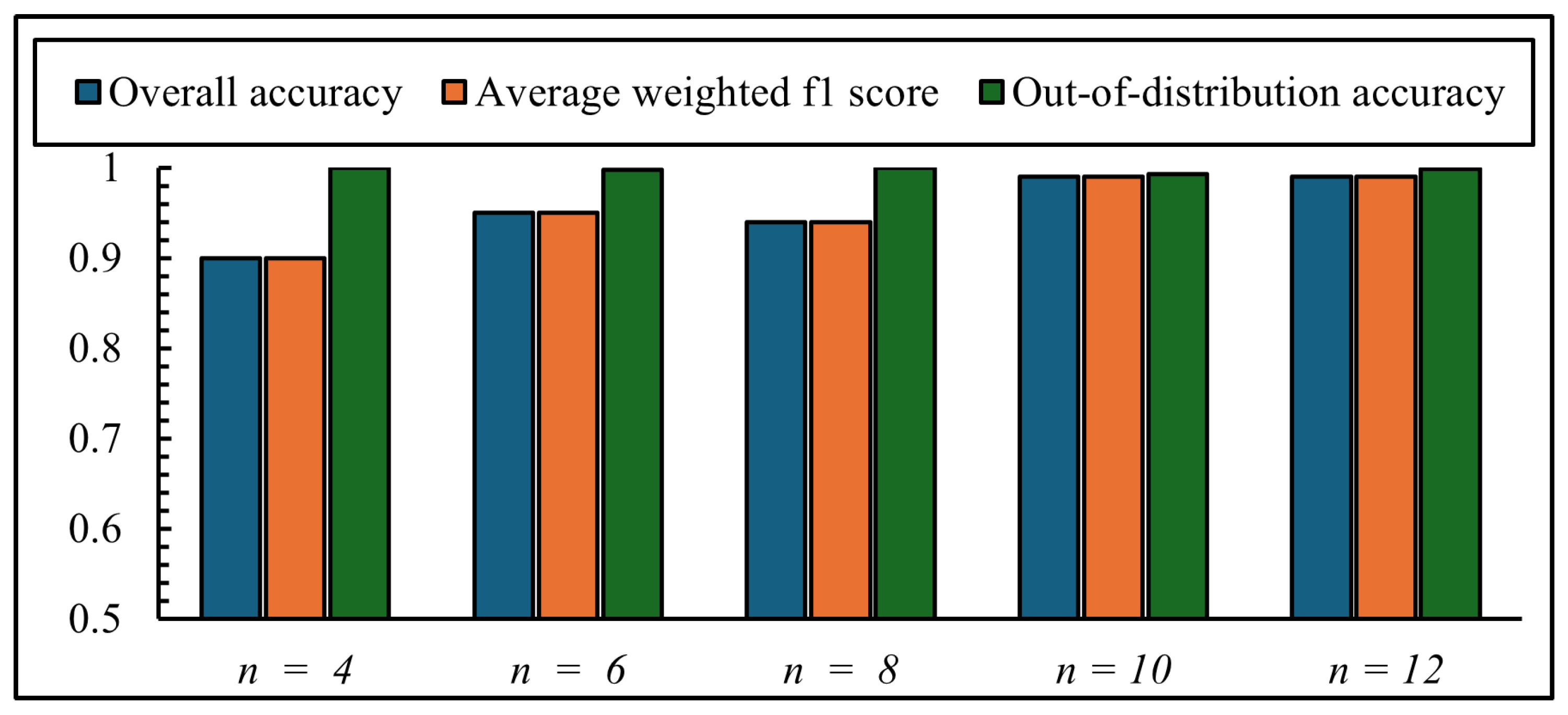
5.4. Tuning Values of Margin (m) and Numbers of Frames Combined (n)
5.5. Performance with Each Device as Unknown
5.6. Comparison with Existing RF Fingerprinting Methods
5.7. Model Complexity and Deployment Within IoT Security Architectures
6. Limitations and Future Works
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Anani, W.; Ouda, A.; Hamou, A. A survey of wireless communications for IoT echo-systems. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019. [Google Scholar] [CrossRef]
- Premkumar, M.; Arun, M.; Prathipa, R.; Badri Narayanan, D. Signal Transmission and Reception in Wireless Smart Cities. Mater. Today Proc. 2023, 80, 3837–3840. [Google Scholar]
- Seçkin, A.Ç.; Ateş, B.; Seçkin, M. Review on Wearable Technology in sports: Concepts, Challenges and opportunities. Appl. Sci. 2023, 13, 10399. [Google Scholar] [CrossRef]
- Pereira, C.E.; Diedrich, C.; Neumann, P. Communication protocols for automation. In Springer Handbook of Automation; Springer: Berlin/Heidelberg, Germany, 2023; pp. 535–560. [Google Scholar]
- Bout, E.; Loscri, V.; Gallais, A. How Machine Learning Changes the Nature of Cyberattacks on IoT Networks: A Survey. IEEE Commun. Surv. Tutorials 2022, 24, 248–279. [Google Scholar] [CrossRef]
- Ali, B.S.; Ullah, I.; Al Shloul, T.; Khan, I.A.; Khan, I.; Ghadi, Y.Y.; Abdusalomov, A.; Nasimov, R.; Ouahada, K.; Hamam, H. ICS-IDS: Application of big data analysis in AI-based intrusion detection systems to identify cyberattacks in ICS networks. J. Supercomput. 2024, 80, 7876–7905. [Google Scholar] [CrossRef]
- Bhat, M.I.; Giri, K.J. Impact of computational power on cryptography. In Multimedia Security: Algorithm Development, Analysis and Applications; Springer: Singapore, 2021; pp. 45–88. [Google Scholar]
- Zhang, J.; Shen, G.; Saad, W.; Chowdhury, K. Radio frequency fingerprint identification for device authentication in the internet of things. IEEE Commun. Mag. 2023, 61, 110–115. [Google Scholar] [CrossRef]
- Abbas, S.; Abu Talib, M.; Nasir, Q.; Idhis, S.; Alaboudi, M.; Mohamed, A. Radio frequency fingerprinting techniques for device identification: A survey. Int. J. Inf. Secur. 2024, 23, 1389–1427. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT security through authentication of wireless nodes using in-situ machine learning. IEEE Internet Things J. 2018, 6, 388–398. [Google Scholar] [CrossRef]
- Ezuma, M.; Erden, F.; Anjinappa, C.K.; Ozdemir, O.; Guvenc, I. Micro-UAV Detection and Classification from RF Fingerprints Using Machine Learning Techniques. In Proceedings of the 2019 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2019. [Google Scholar] [CrossRef]
- Jagannath, A.; Jagannath, J.; Kumar, P.S.P.V. A comprehensive survey on radio frequency (RF) fingerprinting: Traditional approaches, deep learning, and open challenges. Comput. Netw. 2022, 219, 109455. [Google Scholar] [CrossRef]
- Guo, G.; Wang, H.; Bell, D.; Bi, Y.; Greer, K. KNN model-based approach in classification. In Proceedings of the On The Move to Meaningful Internet Systems 2003: CoopIS, DOA, and ODBASE: OTM Confederated International Conferences, CoopIS, DOA, and ODBASE 2003, Catania, Sicily, Italy, 3–7 November 2003; pp. 986–996. [Google Scholar]
- Vishwanathan, S.; Narasimha Murty, M. SSVM: A simple SVM algorithm. In Proceedings of the 2002 International Joint Conference on Neural Networks. IJCNN’02 (Cat. No.02CH37290), Honolulu, HI, USA, 12–17 May 2002; Volume 3, pp. 2393–2398. [Google Scholar] [CrossRef]
- Li, Z.; Liu, F.; Yang, W.; Peng, S.; Zhou, J. A Survey of Convolutional Neural Networks: Analysis, Applications, and Prospects. IEEE Trans. Neural Netw. Learn. Syst. 2022, 33, 6999–7019. [Google Scholar] [CrossRef] [PubMed]
- Kandel, L.N.; Zhang, Z.; Yu, S. Exploiting CSI-MIMO for Accurate and Efficient Device Identification. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Jian, T.; Rendon, B.C.; Ojuba, E.; Soltani, N.; Wang, Z.; Sankhe, K.; Gritsenko, A.; Dy, J.; Chowdhury, K.; Ioannidis, S. Deep learning for RF fingerprinting: A massive experimental study. IEEE Internet Things Mag. 2020, 3, 50–57. [Google Scholar] [CrossRef]
- Zhao, C.; Yu, J.; Luo, G.; Wu, Z. Radio Frequency Fingerprinting Identification of Few-Shot Wireless Signals Based on Deep Metric Learning. Wirel. Commun. Mob. Comput. 2023, 2023, 2132148. [Google Scholar] [CrossRef]
- Soltani, N.; Reus-Muns, G.; Salehi, B.; Dy, J.; Ioannidis, S.; Chowdhury, K. RF Fingerprinting Unmanned Aerial Vehicles with Non-Standard Transmitter Waveforms. IEEE Trans. Veh. Technol. 2020, 69, 15518–15531. [Google Scholar] [CrossRef]
- Cai, Z.; Wang, Y.; Gui, G.; Sha, J. Toward Robust Radio Frequency Fingerprint Identification via Adaptive Semantic Augmentation. IEEE Trans. Inf. Forensics Secur. 2025, 20, 1037–1048. [Google Scholar] [CrossRef]
- Al-Shawabka, A.; Pietraski, P.; Pattar, S.B.; Restuccia, F.; Melodia, T. DeepLoRa: Fingerprinting LoRa Devices at Scale Through Deep Learning and Data Augmentation. In Proceedings of the MobiHoc ’21, Shanghai, China, 26–29 July 2021; pp. 251–260. [Google Scholar] [CrossRef]
- Gu, J.; Soltani, N.; Naderi, M.Y.; Chowdhury, K.R. It’s a Bird, It’s a Plane, It’s “That” UAV: RF Fingerprinting During Flight. In Proceedings of the 2021 55th Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 31 October–3 November 2021; pp. 300–304. [Google Scholar] [CrossRef]
- Tian, Q.; Lin, Y.; Guo, X.; Wang, J.; AlFarraj, O.; Tolba, A. An Identity Authentication Method of a MIoT Device Based on Radio Frequency (RF) Fingerprint Technology. Sensors 2020, 20, 1213. [Google Scholar] [CrossRef]
- Chicco, D. Siamese neural networks: An overview. In Artificial Neural Networks; Humana: New York, NY, USA, 2021; pp. 73–94. [Google Scholar]
- Wang, S.; Peng, L.; Fu, H.; Hu, A.; Zhou, X. A convolutional neural network-based RF fingerprinting identification scheme for mobile phones. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 115–120. [Google Scholar]
- Shen, G.; Zhang, J.; Marshall, A.; Peng, L.; Wang, X. Radio frequency fingerprint identification for LoRa using deep learning. IEEE J. Sel. Areas Commun. 2021, 39, 2604–2616. [Google Scholar] [CrossRef]
- Huang, D.; Al-Hourani, A.; Sithamparanathan, K.; Rowe, W.S.; Bulot, L.; Thompson, A. Deep learning methods for device authentication using RF fingerprinting. In Proceedings of the 2021 15th International Conference on Signal Processing and Communication Systems (ICSPCS), Sydney, Australia, 13–15 December 2021. [Google Scholar] [CrossRef]
- Yu, J.; Hu, A.; Li, G.; Peng, L. A multi-sampling convolutional neural network-based RF fingerprinting approach for low-power devices. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019. [Google Scholar] [CrossRef]
- Yang, J.; Gu, H.; Hu, C.; Zhang, X.; Gui, G.; Gacanin, H. Deep complex-valued convolutional neural network for drone recognition based on RF fingerprinting. Drones 2022, 6, 374. [Google Scholar] [CrossRef]
- Li, B.; Cetin, E. Design and evaluation of a graphical deep learning approach for RF fingerprinting. IEEE Sens. J. 2021, 21, 19462–19468. [Google Scholar] [CrossRef]
- Lee, W.; Baek, S.Y.; Kim, S.H. Deep-learning-aided RF fingerprinting for NFC security. IEEE Commun. Mag. 2021, 59, 96–101. [Google Scholar] [CrossRef]
- Jafari, H.; Omotere, O.; Adesina, D.; Wu, H.H.; Qian, L. IoT devices fingerprinting using deep learning. In Proceedings of the MILCOM 2018-2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar] [CrossRef]
- Otto, A.; Rananga, S.; Masonta, M. Deep Learning vs. Traditional Learning for Radio Frequency Fingerprinting. In Proceedings of the 2024 IST-Africa Conference (IST-Africa), Dublin, Ireland, 20–24 May 2024. [Google Scholar] [CrossRef]
- Morge-Rollet, L.; Le Roy, F.; Le Jeune, D.; Gautier, R. Siamese network on I/Q signal for RF fingerprinting. In Proceedings of the Conference on Artificial Intelligence for Defense (CAID) 2020, Rennes, France, 26–28 August 2020. [Google Scholar]
- Alhoraibi, L.; Alghazzawi, D.; Alhebshi, R.; Rabie, O.B.J. Physical layer authentication in wireless networks-based machine learning approaches. Sensors 2023, 23, 1814. [Google Scholar] [CrossRef]
- Langford, Z.; Eisenbeiser, L.; Vondal, M. Robust Signal Classification Using Siamese Networks. In Proceedings of the WiseML 2019: Proceedings of the ACM Workshop on Wireless Security and Machine Learnin, Miami, FL, USA, 15–17 May 2019. [Google Scholar] [CrossRef]
- Meng, Q.; Li, G.; Shi, J.; Hu, A. Enhancing RF Fingerprinting with a Simulated Attack Detection Strategy for Few Labeled Signals. In Proceedings of the 2023 IEEE 23rd International Conference on Communication Technology (ICCT), Wuxi, China, 20–22 October 2023; pp. 281–285. [Google Scholar] [CrossRef]
- Sun, G. RF Transmitter Identification Using Combined Siamese Networks. IEEE Trans. Instrum. Meas. 2022, 71, 1–13. [Google Scholar] [CrossRef]
- Sankhe, K.; Belgiovine, M.; Zhou, F.; Angioloni, L.; Restuccia, F.; D’Oro, S.; Melodia, T.; Ioannidis, S.; Chowdhury, K. No radio left behind: Radio fingerprinting through deep learning of physical-layer hardware impairments. IEEE Trans. Cogn. Commun. Netw. 2019, 6, 165–178. [Google Scholar] [CrossRef]
- Huang, D.; Al-Hourani, A.; Sithamparanathan, K.; Rowe, W.S.T. Deep Learning Methods for IoT Device Authentication Using Symbols Density Trace Plot. IEEE Internet Things J. 2024, 11, 18167–18179. [Google Scholar] [CrossRef]
- Birnbach, S.; Smailes, J.; Baker, R.; Martinovic, I. Adaptable Hardware Fingerprinting for Radio Data Links and Avionics Buses in Adversarial Settings. In Proceedings of the 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain, 1–5 October 2023. [Google Scholar] [CrossRef]
- Nixon, M.S.; Aguado, A.S. 12 - Distance, classification and learning. In Feature Extraction and Image Processing for Computer Vision, 4th ed.; Nixon, M.S., Aguado, A.S., Eds.; Academic Press: Cambridge, MA, USA, 2020; pp. 571–604. [Google Scholar] [CrossRef]
- Hadsell, R.; Chopra, S.; LeCun, Y. Dimensionality reduction by learning an invariant mapping. In Proceedings of the 2006 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’06), New York, NY, USA, 17–22 June 2006; Volume 2, pp. 1735–1742. [Google Scholar]
- Dhakal, R.; Devkota, B.P.; Niure Kandel, L. Radio Frequency Fingerprinting with Siamese Network. In Proceedings of the 2025 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 17–20 February 2025; pp. 212–216. [Google Scholar] [CrossRef]
- Jiang, R.; Hu, J.; Huang, H.; Zhang, C.; Wang, L.; Xu, S. A Generalized Radio Frequency Fingerprint-Based Wireless Device Identification Using Siamese-Based Neural Network. IEEE Sens. J. 2025, 25, 23262–23275. [Google Scholar] [CrossRef]
- Goutte, C.; Gaussier, E. A Probabilistic Interpretation of Precision, Recall and F-Score, with Implication for Evaluation. In Proceedings of the Advances in Information Retrieval, Santiago de Compostela, Spain, 21–23 March 2005; pp. 345–359. [Google Scholar]
- Roy, D.; Mukherjee, T.; Chatterjee, M.; Blasch, E.; Pasiliao, E. RFAL: Adversarial Learning for RF Transmitter Identification and Classification. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 783–801. [Google Scholar] [CrossRef]
- Khari, M.; Garg, A.K.; Gandomi, A.H.; Gupta, R.; Patan, R.; Balusamy, B. Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 73–80. [Google Scholar] [CrossRef]
- Mustafa, G.; Ashraf, R.; Mirza, M.A.; Jamil, A.; Muhammad. A review of data security and cryptographic techniques in IoT based devices. In Proceedings of the ICFNDS ’18, Amman, Jordan, 26–27 June 2018. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, Z.; Chang, J. Survey of Mobile Device Authentication Methods Based on RF Fingerprint. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019. [Google Scholar] [CrossRef]










| Parameter | Value | Parameter | Value |
|---|---|---|---|
| FFT Length | 128 | Cyclic Prefix Length | 32 |
| Number of Subcarriers | 72 | Subcarrier Spacing | 30 KHz |
| Channel Bandwidth | 3 MHz | Pilot Subcarrier Spacing | 9 |
| Header Modulation | 2 (BPSK) | Payload Modulation | 4 (QPSK) |
| Coding Rate | 1/2 | Symbols per Frame | 30 |
| Frames Transmitted | 19,920 | Sample Rate | 3.84 MHz |
| Tx Center Frequency | 1 GHz | Rx Center Frequency | 1 GHz |
| Transmit Gain | 60 dB | Receive Gain | 71 dB |
| Frames per device | 19,920 | Samples per frame in header | 72 |
| Samples per frame in payload | 1728 | Number of transmitters | 10 |
| Out-of-Distribution Devices | Overall Accuracy (%) | Average Weighted f1-Score | Out-of-Distribution Accuracy (%) |
|---|---|---|---|
| Device 1 | 93.60 | 0.94 | 96.80 |
| Device 2 | 95.73 | 0.96 | 90.30 |
| Device 3 | 99.33 | 0.99 | 99.00 |
| Device 4 | 97.72 | 0.98 | 100.00 |
| Device 5 | 96.12 | 0.96 | 100.00 |
| Device 6 | 98.76 | 0.99 | 100.00 |
| Device 7 | 98.32 | 0.98 | 100.00 |
| Device 8 | 98.76 | 0.99 | 100.00 |
| Device 9 | 89.76 | 0.90 | 100.00 |
| Device 10 | 92.80 | 0.92 | 91.00 |
| Study | Model/Method | Devices | Overall Accuracy (%) | Out-of-Distribution Accuracy (%) | Remarks |
|---|---|---|---|---|---|
| Huang et al. [40] | 2D-CNN, 2D-CNN combined with bidirectional LSTM, and 3D-CNN | 5 ADALM-PLUTO | 97.6 | N/A | No mechanism for rogue detection. |
| G. Sun et al. [38] | Combined Siamese networks | 12 radios | 87 | 87 | Requires the N numbers of Siamese networks for N known devices. |
| Birnbarch et al. [41] | Siamese network | ADSB/RS485 | N/A | 81 | Limited to differentiating legitimate and adversarial samples. |
| Roy et al. [47] | GAN, CNN, DNN, RNN | 8 USRP B210 | 97.85 (classification excluding rogue) | 99.99 | Synthetic samples are considered as rogue. |
| This work (Proposed) | Siamese network | 10 ADALM-PLUTO SDR | 98.25 | 98.4 | Learns pairwise similarity; scalable and effective for unseen device detection. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dhakal, R.; Kandel, L.N.; Shekhar, P. Radio Frequency Fingerprinting Authentication for IoT Networks Using Siamese Networks. IoT 2025, 6, 47. https://doi.org/10.3390/iot6030047
Dhakal R, Kandel LN, Shekhar P. Radio Frequency Fingerprinting Authentication for IoT Networks Using Siamese Networks. IoT. 2025; 6(3):47. https://doi.org/10.3390/iot6030047
Chicago/Turabian StyleDhakal, Raju, Laxima Niure Kandel, and Prashant Shekhar. 2025. "Radio Frequency Fingerprinting Authentication for IoT Networks Using Siamese Networks" IoT 6, no. 3: 47. https://doi.org/10.3390/iot6030047
APA StyleDhakal, R., Kandel, L. N., & Shekhar, P. (2025). Radio Frequency Fingerprinting Authentication for IoT Networks Using Siamese Networks. IoT, 6(3), 47. https://doi.org/10.3390/iot6030047






