Investigating Radio Frequency Vulnerabilities in the Internet of Things (IoT)
Abstract
1. Introduction
- A detailed experimental setup and methodology for assessing RF vulnerabilities in IoT devices.
- Launching popular RF-based attacks, including harmonic frequency attacks, using affordable hardware and open-source tools within a realistic attacker model.
- The behaviour of such attacks towards commercially available smart-home IoT devices.
- Recommendations for enhancing IoT device security based on our findings, which provide practical guidelines for manufacturers and developers.
2. Related Work
3. Radio Frequency Protocols in IoT Ecosystems
3.1. Wi-Fi
3.2. Zigbee
Zigbee Infrastructure
3.3. Bluetooth
4. Radio Frequency Attacks in IoT Ecosystems
- Replay attacks: replay a transmitted signal to the targeted device, causing IoT devices to respond to messages or commands that have already been issued. In the context of RF-based attacks, the adversary needs to be located between the transmitter and the targeted device [31].
- DoS (jamming) attacks: aim to make IoT devices unavailable to their intended users by temporarily or indefinitely disrupting their services [32]. In the context of RF-based attacks, to produce a jamming signal, the adversary uses a signal generator to produce a continuous wave, which is then sent to the target device. The adversary will also attempt to send out a stronger signal than the target signal, effectively making the target device non-operational.
- Sniffing: utilises specialised software that can be used to intercept and analyse the signal of a device to exploit information such as its modulation, sample rate, and bandwidth, to facilitate other cyber attacks.
- MITM: compromises the communication channel between the IoT device and the intended recipient of its data. Once the connection is compromised, the attacker can act as a proxy, and, therefore, read, insert, and modify the transmitted data [33]. One of the most common forms of MITM attacks is spoofing attacks, where the adversary takes on the identity of an authentic device, trying to lure the victim and intercept their data [34].
- Harmonic attacks: Every electronic device that utilises radio frequencies for communication and operation, such as Wi-Fi, Zigbee, LORA etc., is prone to harmonic frequency emissions [35]. In this case, this could allow attacks to be carried out by using even less sophisticated equipment by transmitting on lower frequencies [35]. More specifically, when a wave oscillates, it produces harmonic waves with a reduction in bandwidth each time. This results in an oscillation on a different frequency. Harmonic Spurious emissions are also problematic in electronic devices as they produce unwanted oscillations close to the fundamental frequency as well as harmonic frequencies, which can cause interference. For example, a device transmitting at exactly 433 MHz with a bandwidth of 25 kHz will also bleed onto other frequencies well over its bandwidth without proper filtering [36]. This is especially prominent in dual-side mode modulations such as Frequency Modulation (FM). Many of these spurious emissions are generated by low-noise amplifiers embedded in the devices, which are used to amplify the low-powered signal transmitted from the device. Using this type of amplification causes not only the desired transmission signal to be amplified but also any harmonics or “noise” it generates [37].
5. Methodology
5.1. IoT Devices
- The Belkin Nestcam HD is a small, compact wireless camera used for personal surveillance, employing a 720p resolution for video capture. Its maximum transmission power stands at 67.5 mW, which is notably below the 100 mW limit set by the FCC to ensure safety and minimise interference. Given its transmission power and the use of a small PCB antenna, the camera’s signals can primarily be received nearby [43]. This design choice emphasises its intended close-range surveillance application while also reducing potential interference.
- The NEST smoke alarm is a smart sensor alarm that uses both Bluetooth and Wi-Fi to connect to the Internet and a Nest Hub. It uses Bluetooth 4.0 with a maximum transfer rate of 1 Mbps as well as a modulation type of GFSK, operating between 2.402 and 2.480 GHz. The channel spacing used by the device is 2 MHz, allowing a HackRF to sniff at least one channel [44].
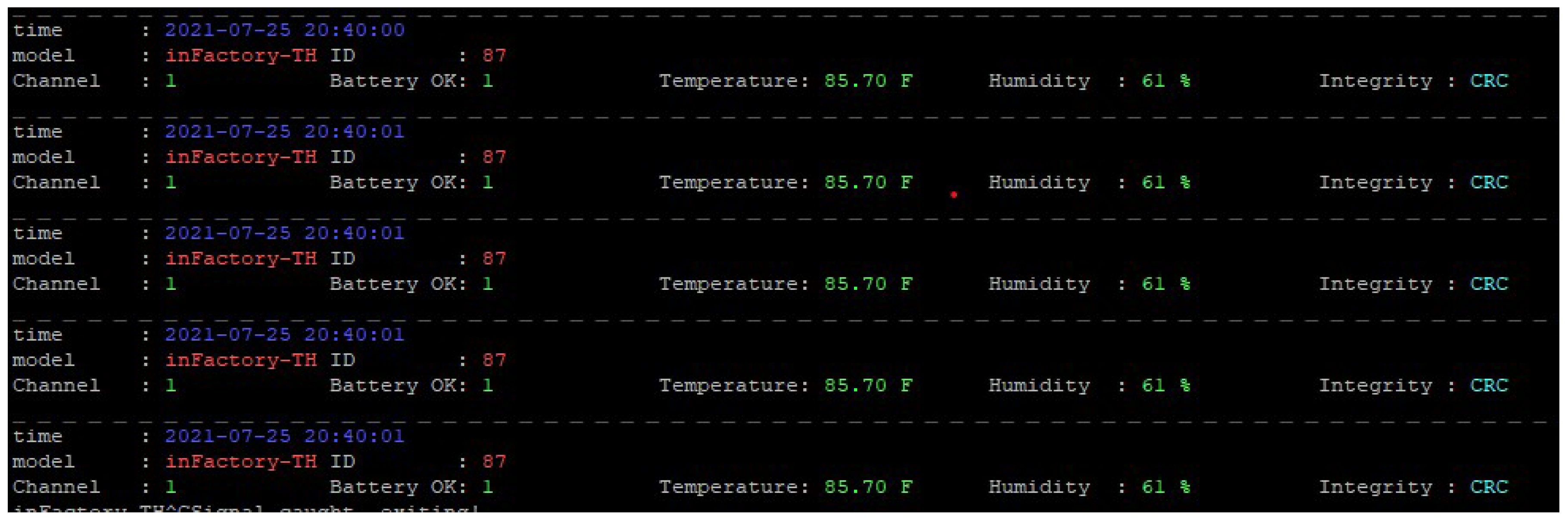
- inFactory sensors are widely used and can often be found in many weather stations. To send data over the Internet, such stations either have built-in functionality or they use a third-party device. They often operate at 433.920 MHz using FSK modulation, which sends out packets to neighbouring monitoring devices that display the data. These data are often sent using an unencrypted signal, which can be decoded using the rtl_433 software [45].
- The Sonoff SNZB-02 is a small temperature and humidity sensor that utilises the ZigBee protocol. The device uses a standard 2.4 GHz RF frequency and uses GFSK modulation, which is very low bandwidth and low power modulation. The device itself is housed in a small plastic casing with minimal shielding from other forms of RF interference. The device itself sends out a beaconing packet, which alerts any receiving device of the current temperature and humidity of the area [46].
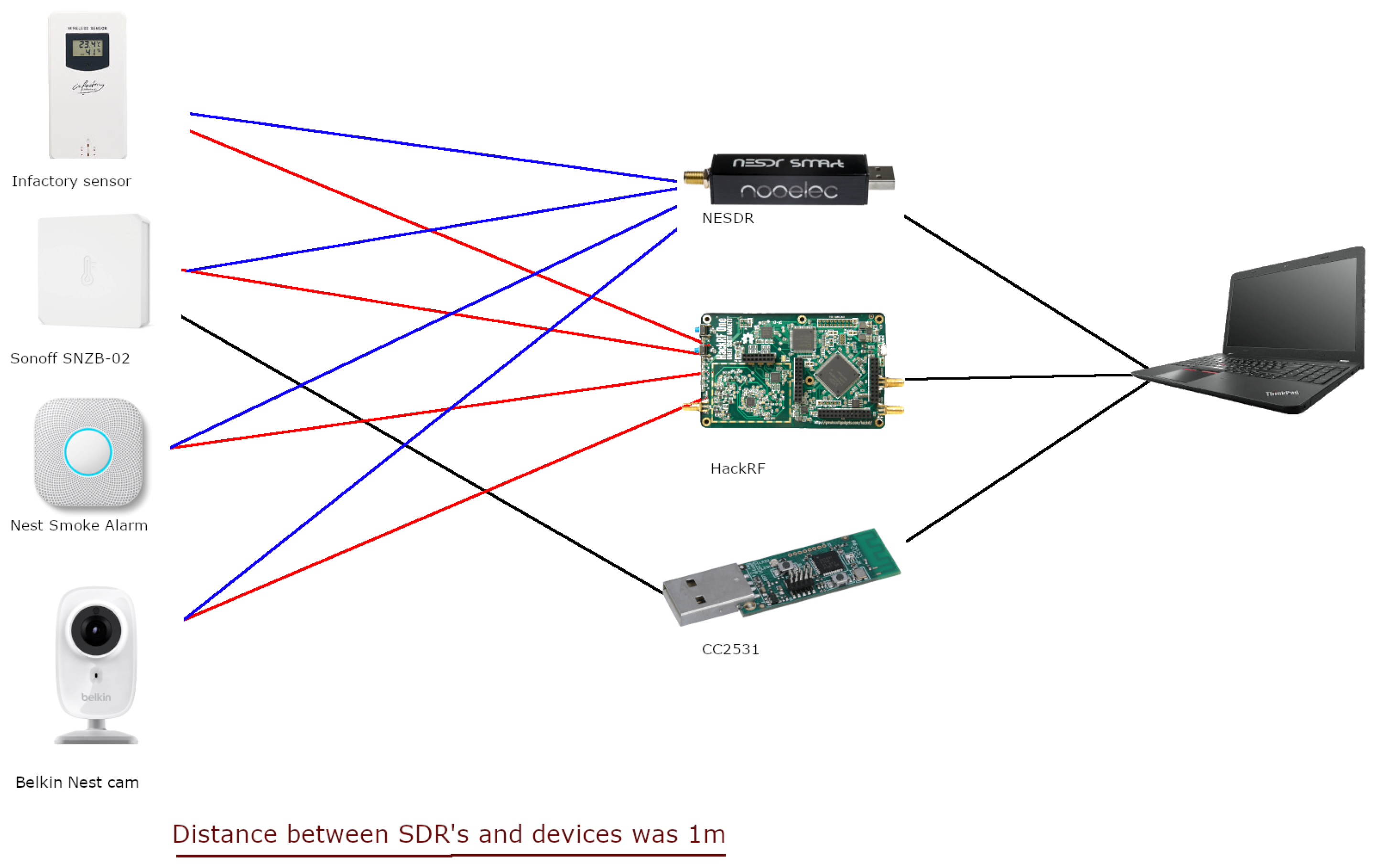
5.2. Radio Frequency Attack Equipment
- The HackRF is a half-duplex SDR transceiver designed for RF investigation. It has an operating frequency of 1 MHz to 6 GHz with an 8-bit quadrature sample rate. It has a maximum transmission power of 30 mW, which makes it suitable for transmitting at close ranges. Nonetheless, it is prone to sporadic emissions, which could compromise nearby equipment if used in combination with amplification equipment. In addition, the HackRF is compatible with GNU-Radio, allowing it to be calibrated to work with multiple other equipment and protocols. One of the main disadvantages of the HackRF is its long-range receiving performance. In this case, a Temperature Compensated Crystal Oscillator (TCXO) was added to the HackRF to increase its reception performance and minimise frequency drift while receiving for long periods. TCXOs are often used to correct the voltage of the tuner chip, which results in variations in frequency over temperature. The voltage correction is applied to a varactor diode located on the crystal circuit, which varies the crystal frequency by a minuscule amount. This results in a more stable frequency [47]. An important factor to consider is that TCXO chips reside when they have experienced extreme temperatures for long periods. This may demonstrate a frequency shift when the chip returns to its normal ambient room temperature.
- The RTL-SDR (NESDR) is a low-cost SDR receiver capable of receiving from 25 MHz up to 1.7 GHz. Its wide popularity has given rise to multiple software packages which support a wide range of decoding protocols, such as Digital mobile radio (DMR), Automatic Packet Reporting System (APRS), Long Range (LORA), Project 25 (P25), and FSK [48]. When compared with the HackRF, the NESDR is only capable of receiving transmissions but has overall better community support. RTL-SDR-based devices are based on two chips: the RTL2832U demodulator chip and the R820T2 tuner chip. It also features a 0.5 PPM (parts per million) low-noise TCXO chip, which is capable of keeping the tuner in sync with the demodulator as it heats up. Since heat is a major factor in the signal stability of the tuner, it is important to keep the device in a stable temperature range [48].
- The CC2531 USB Evaluation Module Kit provides an easy and convenient way to interface with the 802.15.4 ZigBee protocol. It allows the decoding and syncing of ZigBee devices and provides verbose logging data that enable the exploration of any vulnerabilities of the IoT devices [49]. The small PCB antenna allows the testing of IoT devices within a small range without having to expose them to unauthorised third parties. The onboard CC2531 chip is one of the standard chips used for the ZigBee protocol, along with the CC2530, which is a discrete-level chip without the USB interface, and the CC2538, which features an Arm Cortex-M3, which allows it to handle many more simultaneous devices [49]. The small eight-pin headers on the board allow custom firmware to be flashed on the board. In the experiments herein, the CC2531 board was flashed with the sniffing firmware to be compatible with “ZigBee to MQTT”, which provided verbose logging of the testing process. This eliminated the need for third-party servers and software, which become unresponsive at any time. After flashing the firmware, a Linux-based (Parrot OS 4.11) [50] device was loaded to act as an MQTT server for connecting to the ZigBee devices via the board.
- GNU Radio is an open-source software development platform used to create virtual signal processing blocks which can be implemented with software-defined radio such as the HackRF. Using GNU Radio creates more complex RF signal simulations without the need for expensive hardware, thus reducing the cost of the testing equipment. Many of the components of GNU Radio are interchangeable and allow it to interface with multiple programs, which expands its functionality. Such software includes SDRangel [51], Sparrow Wi-Fi [52], zigbee2MQTT [53], rtl_433 [45], and Universal Radio Hacker [54,55].
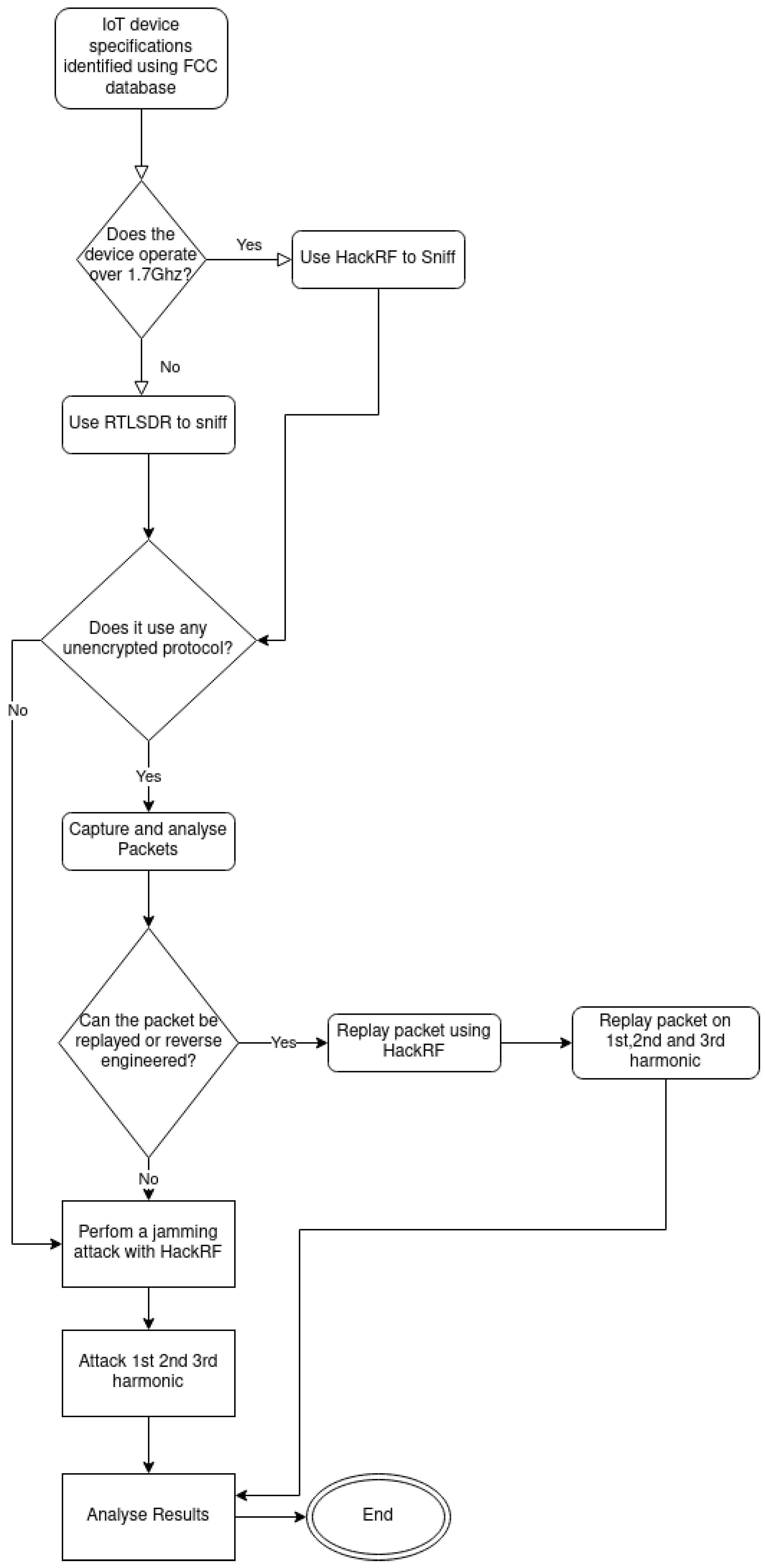
5.3. Identifying the Attack Vector of IoT Devices
- What protocols does the device use?By identifying the device’s protocol, an investigation into known vulnerabilities was conducted.
- What frequencies does the device operate on?By using either the FCC listing or software-defined radios, the device’s frequency of operation was determined and investigated for harmonic or spurious emissions. More specifically, an investigation into the inner workings of the device and its components was implemented to identify which attributes of the device could be exploited. This was crucial in identifying and launching relevant and effective low-skill and low-effort attacks.
- Does the device contain sufficient filtering?Smaller devices with limited space for hardware often lack sufficient filtering and protection from outside interference. This was the case with the Sonoff SNZB-02 tested in this work, where it was possible to interfere with its normal operation by physically obstructing the device’s antenna.
- Is the device dependent on a third-party application?Many IoT devices depend on third-party applications, without which they are not operational. In this case, custom firmware may be installed on the receiving device to make them usable. This was the case with the Sonoff SNZB-02 tested herein, which required the receiver to be flashed with Z-Stack-firmware to allow the receiver to act as a coordinator [56].
- What other unique characteristics does the device possess?Some devices, such as the inFactory sensor, use a specific protocol tailored to the unique characteristics of the device. This meant that a custom attack vector was needed so that it would conform to the specifications of the device.
5.4. Experimental Setup
6. Experiments and Results
6.1. Belkin NestCam HD
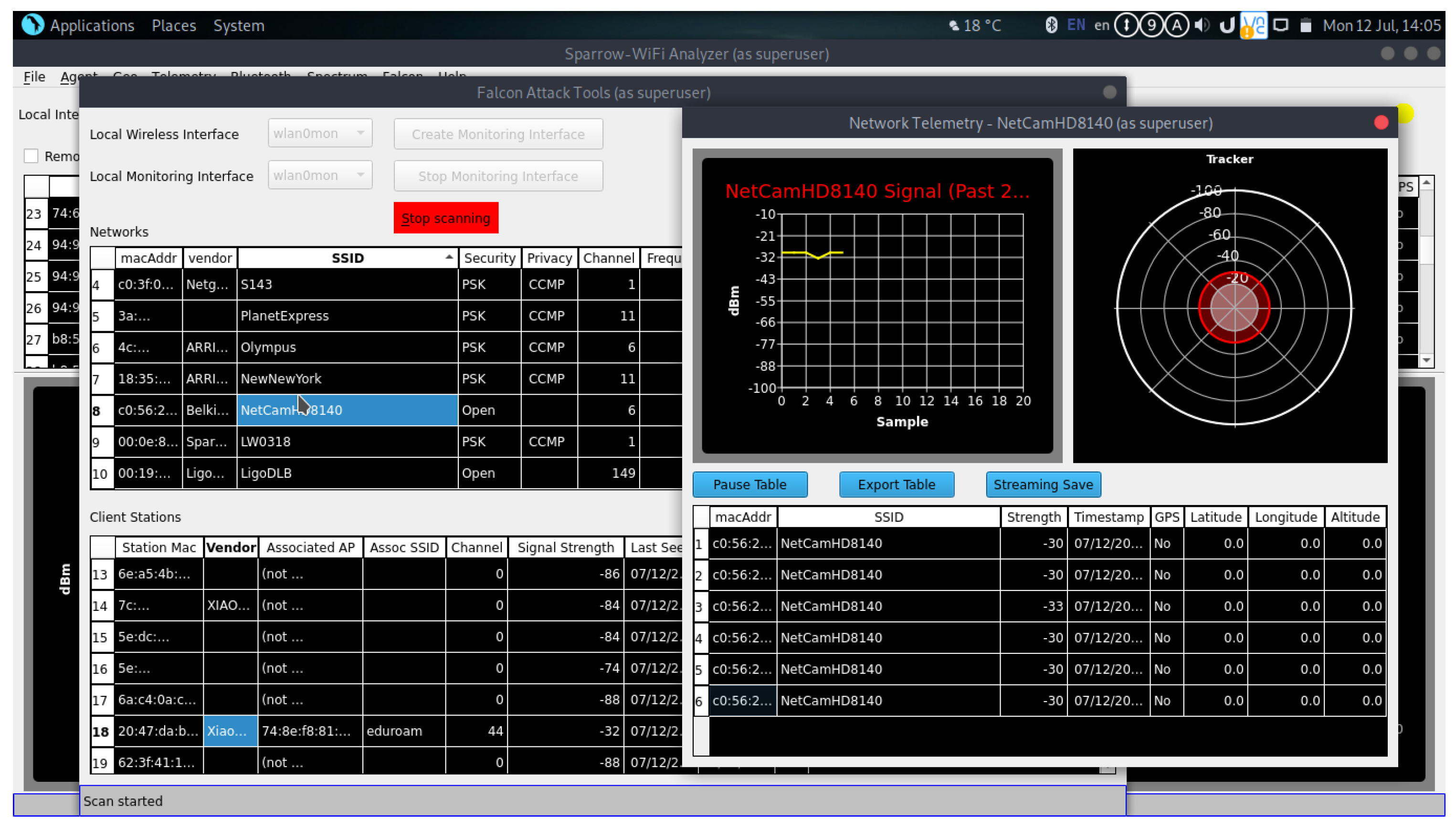
- Deauthentication—Figure 3 illustrates the interface of the Sparrow Wi-Fi software, which was used to launch a de-authentication attack from both the computer’s internal Wi-Fi adaptor and the HackRF. When using the computer’s inbuilt Wi-Fi, the graph demonstrates a disconnection of the camera from the network, successfully preventing RF attack equipment from gaining any further connections. The HackRF was also used on its own to perform the attack by monitoring the frequency of ICMP packets. Using “hackrf_transfer”, a “.bin” file was saved containing the IQ data and then re-transmitted at 2 Mega samples per second. This resulted in a minor increase in latency. Subsequently, Sparrow Wi-Fi covers the whole channel of operation of the targeted IoT device using the computer’s built-in Wi-Fi adaptor. This is due to its larger bandwidth capabilities in comparison to the HackRF.
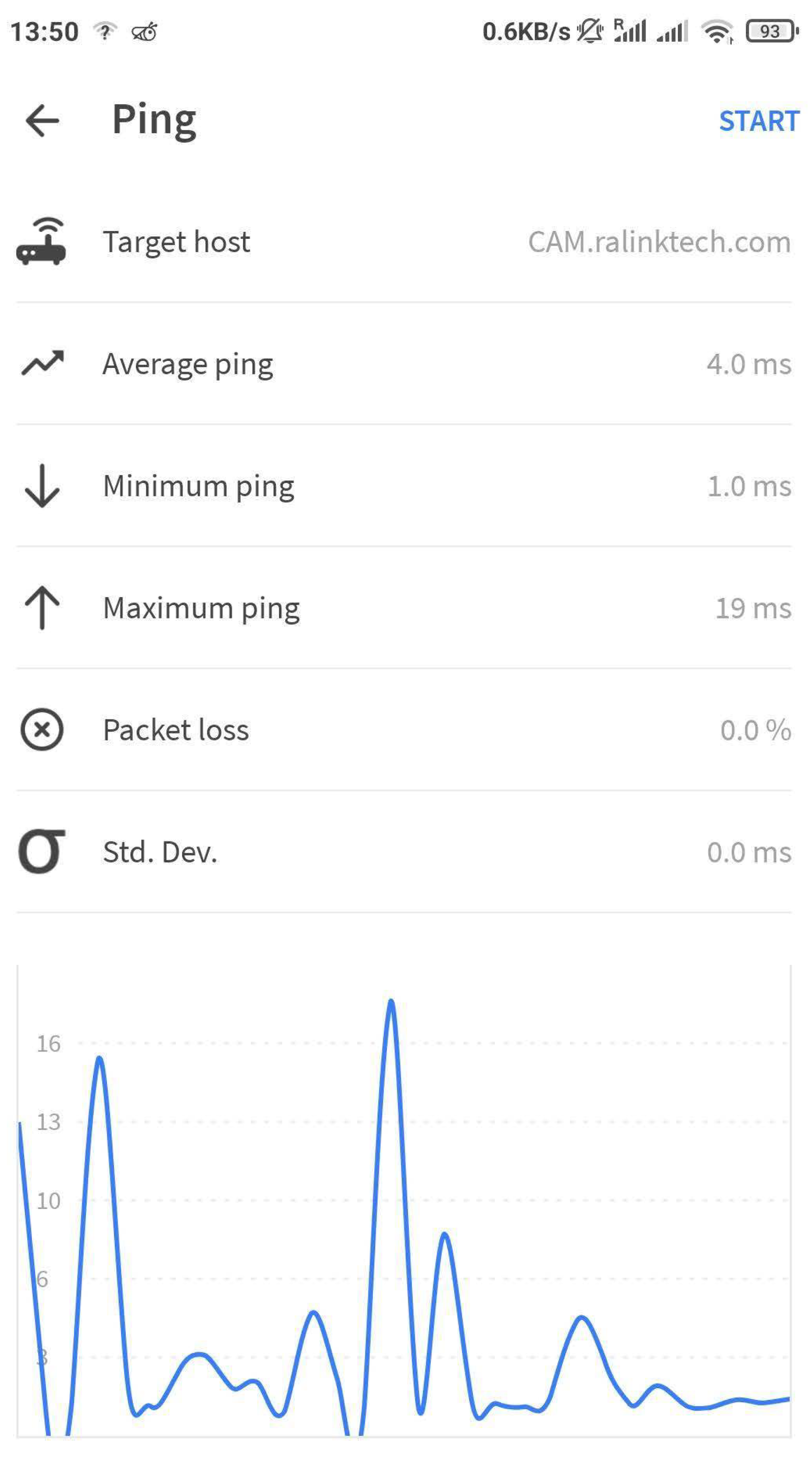
- Attacking First Harmonic—To evaluate the harmonic attack, ICMP packets were sent on the harmonic frequency of 1.2185 GHz, which also has a second harmonic of 2.437 GHz. The results demonstrated a minor increase in latency, but not enough to cause disruption or any packet loss. These results can be observed from Figure 4 and Figure 5, where high peaks in the latency were observed while attacking via the harmonic, but the attack was not strong enough to cause any disruption. By using the HackRF to send ICMP packets in an attempt to jam the signal, it was observed that there was no impact on the signal quality of the device, indicating its resilience and capability to communicate effectively without any interference-induced degradation. This may be explained by the fact that the HackRF does not transmit at a bandwidth large enough to cover the whole channel on its own; the low power transmitted by the HackRF is not enough to completely overshadow the transmission of the camera; the Wi-Fi changes between modulation types; therefore, if jamming is performed using only one form of modulation, disruption may be temporary.
- Signal Sniffing—The laptop’s inbuilt Wi-Fi adaptor was used with monitor mode enabled to capture and inspect the camera’s packets. However, no obvious vulnerability to exploits was detected. The HackRF’s lack of bandwidth was a limitation for its ability to sniff packets directly.
6.2. NEST Smoke Alarm
- Deauthentication—Similar to the Belkin NestCam HD, the Sparrow Wi-Fi software was used to launch a de-authentication attack on the NEST Smoke Alarm from both the computer’s internal Wi-Fi adaptor and the HackRF. When using the computer’s inbuilt Wi-Fi, no obvious vulnerability to exploit was detected. However, an interesting observation was the large number of beaconing packets being transmitted. The HackRF was also used on its own to perform the attack. The only observation was the increase in latency between the access point and the camera.
- Bluetooth Sniffing—The computer’s internal Bluetooth device and the HackRF was used to sniff the Bluetooth spectrum and monitor the packets between the NEST Smoke Alarm. The HackRF’s lack of bandwidth did not allow complete packets to be received. In this case, an attempt was made to receive a channel using Channel 37, which is the default starting channel for Bluetooth. This resulted in the reception of multiple malformed packets, with only the NEST’s broadcast packets being those that could be decoded successfully. When using the computer’s internal Bluetooth device to monitor the packets, it was observed that beaconing packets are mostly transmitted by the NEST device. This demonstrates the limitation of the HackRF’s bandwidth and its inability to attack the IoT device using Bluetooth.
- Jamming—The HackRF’s lack of bandwidth removes its capability to sniff Wi-fi packets as they are too large. It is also not able to replay the handshake signal for this reason. Using the “hackrf_transfer” function to re-transmit a capture signal did not yield any substantial results.
6.3. inFactory Sensors
- –
- d: Device number
- –
- R: Device ID
- –
- a: Analyze mode 4
- –
- A: Pulse Analysis
- –
- S: Store all raw signals
- –
- rtl_433 -d 1 -R 91 -a 4 -A -S all
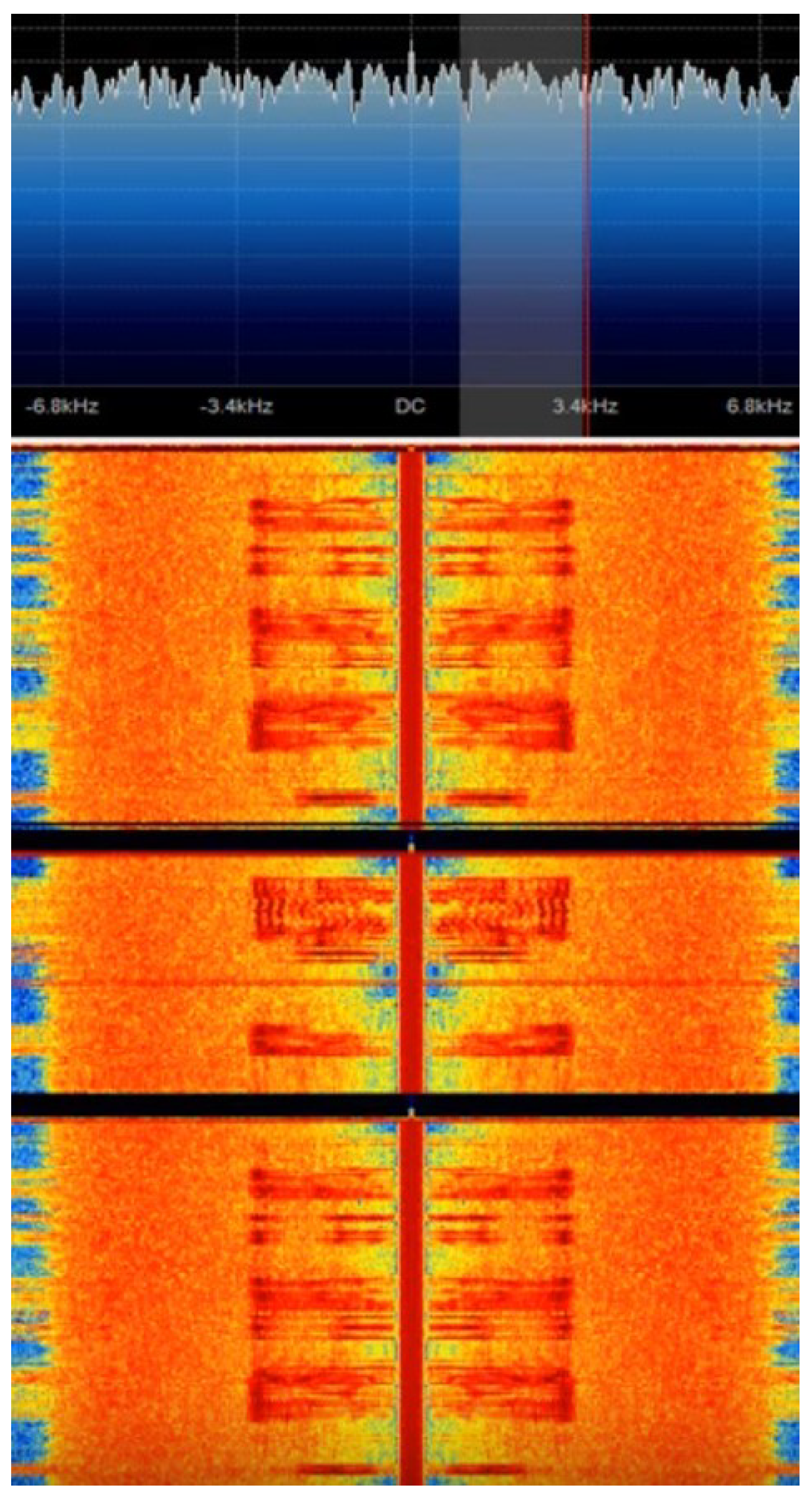
- Jamming—Many of these sensors are housed in thin plastic casing with little or no shielding from external RF interference. This makes the device vulnerable to jamming attacks. To investigate the effectiveness of this attack, a signal irrelevant to the modulation mode from the HackRF was sent to the sensor. This jammed the connection between the HackRF and the sensor. This attack was escalated further by utilising a handheld transceiver to transmit a carrier wave on 433.920 MHz with more than 1 watt. This has the potential to jam multiple devices on the same frequency and at a much larger distance.
- Replay Attack—To conduct a replay attack and gauge its success, the sensor was first placed inside a freezer. This chilling process was essential to create an abnormal condition, causing the temperature to drop to an unusually low −9 degrees Celsius, and thereby triggering the sensor to transmit an alert signal. Once the sensor was removed, the Universal Radio Hacker was used to capture this alert signal. Six separate samples were collected for consistency. Leveraging the software’s integrated features, the signal was then relayed to the receiver. However, this attack attempt did not succeed. Subsequently, to further examine the feasibility of a replay attack, the following methods—which were designed based on the constraints of the environment and the limitations posed by the physical conditions of the experiment—were attempted:
- Removing the batteries from the sensor and sending the signal to the receiver without the sensor present. This method tests the hypothesis that the receiver might recognise a valid signal even in the absence of the actual sensor, offering a basic but essential step in validating the integrity of the receiver.
- Resetting the receiver and then sending the signal.
- Sending the signal at 30 s intervals.
- Capturing the handshake signal sent out by the sensor, disabling the sensor by turning it off, and using the signal we have captured in the hopes that the handshake signal would be enough to trigger the receiver to display an output.
6.4. Sonoff SNZB-02
- Jamming—Like many devices, the Sonoff SNZB-02 started sending a beaconing packet on Channel 11 (2.405 GHz). This channel is the most frequently used channel by devices that operate in the 2.4 GHz band, as it initiates the time synchronisation of the devices. This channel is also used by the ZigBee protocol to send out the beaconing packets. But, as the Zigbee protocol is designed to use frequency hopping, it becomes difficult to jam the channel. After further investigation, the signal was successfully jammed using the SDRANGEL and its 802.15.4 module. More specifically, by transmitting a random ZigBee packet, it was possible to stop the receiver from gathering telemetry from the device. It is worth noting that this was successful only after synchronising the device with the coordinator. However, as the HackRF has greater transmission power in comparison to the Sonoff device, its signal was overpowering. A bandwidth of 10 MHz was used to jam channels 11 and 12, preventing the device from hopping to other channels. The attack was successful as the device was not responsive and was unable to receive a signal for three minutes. Furthermore, the HackRF’s transmission power and LNA gain were set to 61 and 47, respectively, which led to the jamming of both 11 and 12 channels.
- Replay Attack—Using Universal Radio Hacker, it was possible to capture the signal of the device. However, due to the nature of the Zigbee protocol and its use of frequency hopping, it was not possible to successfully replay the initialisation packet. Subsequently, it was not possible to connect to the coordinator using the HackRF. However, although it was possible to capture part of the packet, it was not large enough to be decoded or analysed. With this in mind, it was possible to briefly replay the packet back to the device when it was listening to channel 11. This was only momentary and only happened for a few minutes; after that, we were unable to do the same thing again for some time. This is likely due to the Zigbee protocol using spread spectrum, hence, when the signal was transmitted, only the current channel was monitored for a brief period before it switched to another one. This finding is important, as from an adversary’s perspective, being able to capture the full packet in such attacks significantly increases the severity of the possible consequences. For example, if the sensor was connected to a thermostat, the results could be catastrophic as the temperature could be changed uncontrollably, causing bodily harm.
- The replay attack was successful, as the temperature and battery values were the same throughout the attack.
- The link quality is calculated by Zigbee2MQTT and not by the sensor.
- The values for humidity are inconsistent, which could be due to malformed packets being sent out by HackRF or the use of spread spectrum, which caused only a part of the packet to be received.
7. Discussion
8. Towards Defending IoT Devices against Radio Frequency-Based Attacks
8.1. Encryption
8.2. Frequency Hopping Spread Spectrum (FHSS)
8.3. Scrambling
8.4. Split-Band Inversion
8.5. IoT Security Standards
9. Limitations
10. Conclusions
11. Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Anthi, E.; Williams, L.; Malgortzata, G.; Theodorakopoulos, G.; Burnap, P. A supervised Intrusion Detection System for Smart Home IoT. IEEE Internet Things J. 2018, 78, 477–490. [Google Scholar] [CrossRef]
- Das, R.; Gündüz, M.Z. Analysis of cyber-attacks in IoT-based critical infrastructures. Int. J. Inf. Secur. Sci. 2019, 8, 122–133. [Google Scholar]
- Hamid, H.; Noor, R.M.; Omar, S.N.; Ahmedy, I.; Anjum, S.S.; Shah, S.A.; Kaur, S.; Othman, F.; Tamil, E.M. IOT-based botnet attacks systematic mapping study of literature. Scientometrics 2021, 126, 2759–2800. [Google Scholar] [CrossRef]
- Sadiq, A.; Anwar, M.; Butt, R.A.; Masud, F.; Shahzad, M.K.; Naseem, S.; Younas, M. A review of phishing attacks and countermeasures for internet of things-based smart business applications in industry 4.0. Hum. Behav. Emerg. Technol. 2021, 3, 854–864. [Google Scholar] [CrossRef]
- Bastille. Mousejack Technical Details. 2016. Available online: https://www.bastille.net/research/vulnerabilities/mousejack/technical-details (accessed on 27 May 2024).
- Shing, L.; Astacio, J.; Figueroa, A.; Shing, C.C. Vulnerabilities of radio frequencies. In Proceedings of the 2015 12th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD), Zhangjiajie, China, 15–17 August 2015; pp. 2682–2686. [Google Scholar] [CrossRef]
- Pauli, D. IoT Worm Can Hack Philips Hue Lightbulbs, Spread across Cities. 2016. Available online: https://www.theregister.com/2016/11/10/iot_worm_can_hack_philips_hue_lightbulbs_spread_across_cities/ (accessed on 20 May 2024).
- Bukhari, S.M.S.; Zafar, M.H.; Abou Houran, M.; Moosavi, S.K.R.; Mansoor, M.; Muaaz, M.; Sanfilippo, F. Secure and privacy-preserving intrusion detection in wireless sensor networks: Federated learning with SCNN-Bi-LSTM for enhanced reliability. Ad Hoc Netw. 2024, 155, 103407. [Google Scholar] [CrossRef]
- Rugeles, J.d.J.; Guillen, E.P.; Cardoso, L.S. A Technical Review of Wireless security for the Internet of things: Software Defined Radio perspective. arXiv 2020, arXiv:2009.10171. [Google Scholar] [CrossRef]
- COX, J. NSO Group Closes Cyprus Office of Spy Firm. 2020. Available online: https://www.vice.com/en/article/ep48kp/nso-group-cyprus-circles-bulgaria-ss7 (accessed on 12 January 2024).
- AFP. Cyprus Arrests Three in ’Israeli Spy Van’ Probe. 2019. Available online: https://www.securityweek.com/cyprus-arrests-three-israeli-spy-van-probe/ (accessed on 12 January 2024).
- ASP. Cyprus Police Investigate Israeli Owner’s ‘spy’ Van. 2019. Available online: https://apnews.com/general-news-9dd96df20fce433ca86b62228c0016fb (accessed on 12 January 2024).
- Barnickel, J.; Wang, J.; Meyer, U. Implementing an Attack on Bluetooth 2.1+ Secure Simple Pairing in Passkey Entry Mode. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, TRUSTCOM ’12, Liverpool, UK, 25–27 June 2012; pp. 17–24. [Google Scholar] [CrossRef]
- Mottola, L.; Hameed, A.; Voigt, T. Energy Attacks in the Battery-less Internet of Things: Directions for the Future. In Proceedings of the 17th European Workshop on Systems Security, Athens, Greece, 22 April 2024; pp. 29–36. [Google Scholar]
- Karagiannis, D.; Argyriou, A. Jamming attack detection in a pair of RF communicating vehicles using unsupervised machine learning. Veh. Commun. 2018, 13, 56–63. [Google Scholar] [CrossRef]
- Zhang, W.; Yan, X.; Cao, C.; Zeng, X.; Feng, Z.; Ning, J.; Wang, T.; Wu, Z.; Zhang, X. Research on simulation methods for Doppler frequency shift of a coherent inter-satellite laser link in a ground test system. Infrared Phys. Technol. 2021, 113, 103627. [Google Scholar] [CrossRef]
- Gul, O.M.; Kulhandjian, M.; Kantarci, B.; Touazi, A.; Ellement, C.; D’amours, C. Secure industrial iot systems via rf fingerprinting under impaired channels with interference and noise. IEEE Access 2023, 11, 26289–26307. [Google Scholar] [CrossRef]
- Shahroz, M.; Mushtaq, M.F.; Ahmad, M.; Ullah, S.; Mehmood, A.; Choi, G.S. IoT-Based Smart Shopping Cart Using Radio Frequency Identification. IEEE Access 2020, 8, 68426–68438. [Google Scholar] [CrossRef]
- Hung, P.D.; Vinh, B.T. Vulnerabilities in IoT Devices with Software-Defined Radio. In Proceedings of the 2019 IEEE 4th International Conference on Computer and Communication Systems (ICCCS), Singapore, 23–25 February 2019; pp. 664–668. [Google Scholar] [CrossRef]
- Öst, A. Evaluating LoRa and WiFi Jamming. Ph.D. Thesis, Mid Sweden University, Faculty of Science, Technology and Media, Department of Information Systems and Technology, 2018. Available online: https://www.diva-portal.org/smash/record.jsf?pid=diva2%3A1223787&dswid=-4233 (accessed on 12 January 2024).
- Oukas, N.; Boulif, M.; Abbas, A.; Bahmed, K.; Mosteghanemi, Y. Mitigating Jamming Attacks in IoT RF-Devices through Dynamic Channel Hopping: A Novel Petri-nets Formulation. In Proceedings of the 2023 International Conference on Computer and Applications (ICCA), Yangon, Myanmar, 27–28 February 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Rojas, P.; Alahmadi, S.; Bayoumi, M. Physical Layer Security for IoT Communications—A Survey. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 95–100. [Google Scholar] [CrossRef]
- Beal, V. WiFi. 2021. Available online: https://www.webopedia.com/definitions/wifi/ (accessed on 12 January 2024).
- Electronic Code of Federal Regulations. 2021. Available online: https://www.ecfr.gov/ (accessed on 12 January 2024).
- IEEE SA—IEEE 802.15.4-2020. Available online: https://standards.ieee.org/ieee/802.15.4/7029/ (accessed on 4 June 2024).
- Amin, I.; Saeed, A. 5.10 Wireless Technologies in Energy Management. In Comprehensive Energy Systems; Dincer, I., Ed.; Elsevier: Oxford, UK, 2018; pp. 389–422. [Google Scholar] [CrossRef]
- Watteyne, T. 4-Lower-power wireless mesh networks for machine-to-machine communications using the IEEE802.15.4 standard. In Machine-to-Machine (M2M) Communications; Antón-Haro, C., Dohler, M., Eds.; Woodhead Publishing: Oxford, UK, 2015; pp. 63–77. [Google Scholar] [CrossRef]
- Farahani, S. Chapter 2-ZigBee/IEEE 802.15.4 Networking Examples. In ZigBee Wireless Networks and Transceivers; Farahani, S., Ed.; Newnes: Burlington, NJ, USA, 2008; pp. 25–32. [Google Scholar] [CrossRef]
- ScientificAmerican. How Does Bluetooth Work? 2007. Available online: https://www.scientificamerican.com/article/experts-how-does-bluetooth-work/#:~:text=Bluetooth%20technology%20uses%20the%20principles,devices%20that%20are%20actively%20inquiring (accessed on 20 January 2024).
- Techspirited. A Beginner’s Guide to Bluetooth Technology and How Does It Work. 2008. Available online: https://techspirited.com/how-does-bluetooth-work (accessed on 20 January 2024).
- Chen, J.; Zhang, S.; Wang, H.; Zhang, X. Practicing a record-and-replay system on USRP. In Proceedings of the Second Workshop on Software Radio Implementation Forum-SRIF 13, Hong Kong, China, 12–16 August 2013. [Google Scholar] [CrossRef]
- Andrea, I.; Chrysostomou, C.; Hadjichristofi, G. Internet of Things: Security vulnerabilities and challenges. In Proceedings of the 2015 IEEE symposium on computers and communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 180–187. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Mallik, A. Man-In-The-Middle-Attack: Understanding In Simple Words. Cyberspace J. Pendidik. Teknol. Inf. 2019, 2, 109. [Google Scholar] [CrossRef]
- Punchthrough. Harmonics Part 1-Introduction to Harmonics & BLE. 2020. Available online: https://punchthrough.com/harmonics-part-1-introduction-to-harmonics-ble-2/ (accessed on 12 January 2024).
- Wi-Fi-Radio Modulation. Tutorials Point. 2011. Available online: https://www.tutorialspoint.com/wi-fi/wifi_radio_modulation.htm (accessed on 12 January 2024).
- RF Wireless World. 2021. Available online: https://www.rfwireless-world.com/Terminology/spurious-vs-harmonics.html (accessed on 20 January 2024).
- Chairwoman, J.R. 2023. Available online: https://www.fcc.gov/ (accessed on 12 January 2024).
- CE Marking—Obtaining the Certificate, EU Requirements. Available online: https://europa.eu/youreurope/business/product-requirements/labels-markings/ce-marking/index_en.htm (accessed on 24 May 2024).
- ecommerceDB. E-Commerce Revenue Analytics belkin.com. Available online: https://ecommercedb.com/store/belkin.com (accessed on 12 January 2024).
- Alibaba Sonoff Revenue. Available online: https://sonoff.en.alibaba.com/company_profile/transaction_history.html?spm=a2700.shop_cp.13934.2.502d1c9d9tBxHc (accessed on 19 January 2024).
- Google Nest Protect-Smoke Alarm and Carbon Monoxide Detector (Battery). Available online: https://www.amazon.co.uk/Nest-Protect-Generation-Monoxide-Battery/dp/B00ZC5F9W2 (accessed on 19 December 2023).
- FCCID. Belkin. NetCam HD F7D7602V2 FCC ID K7SF7D7602V2. 2014. Available online: https://fccid.io/K7SF7D7602V2 (accessed on 19 December 2023).
- FFCID. Nest Labs Inc Wireless Protect S30. 2014. Available online: https://fccid.io/ZQAS30 (accessed on 19 December 2023).
- Larsson, B. MerbananRTL_433: Program to Decode Radio Transmissions from Devices on the ISM Bands (and Other Frequencies). 2016. Available online: https://github.com/merbanan/rtl_433 (accessed on 19 January 2024).
- Shenzhen Sonoff Technologies Co., Ltd. Temperature and Humidity Sensor SNZB-02. 2020. Available online: https://fccid.io/2APN5SNZB-02 (accessed on 19 December 2023).
- Huang, X.; Liu, D.; Wang, Y.; Chen, P.; Fu, W. 100-MHz Low-Phase-Noise Microprocessor Temperature-Compensated Crystal Oscillator. IEEE Trans. Circuits Syst. II Express Briefs 2015, 62, 636–640. [Google Scholar] [CrossRef]
- Nooelec NESDR SMArt v4 SDR-Premium RTL-SDR w/Aluminum Enclosure, 0.5PPM TCXO, SMA Input. RTL2832U & R820T2-Based. Available online: https://www.nooelec.com/store/sdr/sdr-receivers/smart.html (accessed on 19 December 2023).
- CC2531EMK. Available online: https://www.ti.com/tool/CC2531EMK (accessed on 19 January 2024).
- How to Sniff Zigbee Traffic. Available online: https://www.zigbee2mqtt.io/advanced/zigbee/04_sniff_zigbee_traffic.html (accessed on 19 January 2024).
- f4exb. f4exb/Sdrangel: SDR Rx/Tx Software for Airspy, Airspy HF, BladeRF, HackRF, LimeSDR, PlutoSDR, RTL-SDR, SDRplay RSP1 and FunCube. Available online: https://github.com/f4exb/sdrangel (accessed on 19 January 2024).
- ghostop14. ghostop14/Sparrow-wifi: Next-Gen GUI-based WiFi and Bluetooth Analyzer for Linux. Available online: https://github.com/ghostop14/sparrow-wifi (accessed on 19 January 2024).
- Koenkk. Koenkk/zigbee2mqtt: Zigbee to MQTT Bridge, Get Rid of Your Proprietary Zigbee Bridges. Available online: https://github.com/Koenkk/zigbee2mqtt (accessed on 19 January 2024).
- Pohl, J.; Noack, A. Universal Radio Hacker: A Suite for Analyzing and Attacking Stateful Wireless Protocols. In Proceedings of the 12th USENIX Workshop on Offensive Technologies (WOOT 18), Baltimore, MD, USA, 13–14 August 2018. [Google Scholar]
- Universal Radio Hacker (URH): Investigating Wireless Protocols like a Boss. Available online: https://github.com/jopohl/urh (accessed on 4 June 2024).
- Kanters, K. Z-Stack-Firmware. 2021. Available online: https://github.com/Koenkk/Z-Stack-firmware (accessed on 19 January 2024).
- Aju, O.G. A survey of zigbee wireless sensor network technology: Topology, applications and challenges. Int. J. Comput. Appl. 2015, 130, 47–55. [Google Scholar]
- Sarker, M.Z.H.; Parvez, M.S. A Cost Effective Symmetric Key Cryptographic Algorithm for Small Amount of Data. In Proceedings of the 2005 Pakistan Section Multitopic Conference, Karachi, Pakistan, 24–25 December 2005. [Google Scholar] [CrossRef]
- Advanced Encryption Standard (AES). Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197-upd1.pdf (accessed on 27 May 2024).
- Nannipieri, P.; Di Matteo, S.; Baldanzi, L.; Crocetti, L.; Zulberti, L.; Saponara, S.; Fanucci, L. VLSI design of Advanced-Features AES CryptoProcessor in the framework of the European Processor Initiative. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 30, 177–186. [Google Scholar] [CrossRef]
- Barker, E.; Barker, W. Recommendation for Key Management, Part 2: Best Practices for Key Management Organization; Technical Report; National Institute of Standards and Technology, U.S. Department of Commerce: Washington, DC, USA, 2018.
- National Institute of Standards and Technology. Available online: https://www.nist.gov/ (accessed on 27 May 2024).
- Marin, L.; Piotr Pawlowski, M.; Jara, A. Optimized ECC implementation for secure communication between heterogeneous IoT devices. Sensors 2015, 15, 21478–21499. [Google Scholar] [CrossRef] [PubMed]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A practical performance comparison of ECC and RSA for resource-constrained IoT devices. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- RFC 8031: Curve25519 and Curve448 for the Internet Key Exchange Protocol Version 2 (IKEv2) Key Agreement. Available online: https://www.rfc-editor.org/rfc/rfc8031.html (accessed on 27 May 2024).
- Torrieri, D. Principles of Spread-Spectrum Communication Systems; Springer: Cham, Switzerland, 2005. [Google Scholar] [CrossRef]
- IEEE SA-IEEE 802.11-2016. Available online: https://standards.ieee.org/ieee/802.11/5536/ (accessed on 27 May 2024).
- VOCAL. VOCAL Technologies. 2021. Available online: https://vocal.com/ (accessed on 27 May 2024).
- Räisänen, O.R. Descrambling Split-Band Voice Inversion with Deinvert. 2017. Available online: http://www.windytan.com/2017/09/descrambling-split-band-voice-inversion.html (accessed on 27 May 2024).
- Windytan. Windytan/Deinvert: A Voice Inversion Descrambler (and Scrambler). Available online: https://github.com/windytan/deinvert (accessed on 27 May 2024).
- ISO/IEC 27400:2022-Cybersecurity—IoT Security and Privacy—Guidelines. Available online: https://www.iso.org/standard/44373.html (accessed on 27 May 2024).



| Work | Devices Used | Devices Type | No. of Devices | Attacks |
|---|---|---|---|---|
| [9] | USRP, UberTooth, RTL-SDR, HackRF | Homebrew, Commercial | N/A | Sniffing, R.E, Replay, DoS |
| [15] | USRP | Commercial | 1 | DoS |
| [18] | Arduino | Homebrew | 1 | Sniffing, R.E, Replay, DoS |
| [19] | Arduino, HackRF | Homebrew | 1 | R.E |
| [20] | Arduino, HackRF | Homebrew | 1 | Sniffing, R.E, Replay, DoS |
| This paper | HackRF, NESDR, CC2531 | Commercial | 4 | Sniffing, R.E, Replay, DoS |
| Manufacturer & IoT Device | Type | Protocol (s) |
|---|---|---|
| Belkin—NestCam HD | Multimedia | Wi-Fi |
| Nest—Smoke Alarm | Sensors | Bluetooth and Wi-Fi |
| inFactory—Sensors | Sensors | 433.920 MHz |
| Sonoff—SNZB-02 Sensor | Sensors | ZigBee |
| Attack | Belkin NestCam HD | Nest Smoke Alarm | inFactory Sensors | Sonoff SNZB-02 Sensors |
|---|---|---|---|---|
| Deauthentication | X | X | ✓ | ✓ |
| Attacking first harmonic | ✓ | ✓ | ✓ | X |
| Signal sniffing | ✓ | ✓ | ✓ | ✓ |
| Bluetooth sniffing | N/A | ✓ | N/A | N/A |
| Jamming | ✓ | X | ✓ | ✓ |
| Replay | X | X | ✓ | X |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anthi, E.; Williams, L.; Ieropoulos, V.; Spyridopoulos, T. Investigating Radio Frequency Vulnerabilities in the Internet of Things (IoT). IoT 2024, 5, 356-380. https://doi.org/10.3390/iot5020018
Anthi E, Williams L, Ieropoulos V, Spyridopoulos T. Investigating Radio Frequency Vulnerabilities in the Internet of Things (IoT). IoT. 2024; 5(2):356-380. https://doi.org/10.3390/iot5020018
Chicago/Turabian StyleAnthi, Eirini, Lowri Williams, Vasilis Ieropoulos, and Theodoros Spyridopoulos. 2024. "Investigating Radio Frequency Vulnerabilities in the Internet of Things (IoT)" IoT 5, no. 2: 356-380. https://doi.org/10.3390/iot5020018
APA StyleAnthi, E., Williams, L., Ieropoulos, V., & Spyridopoulos, T. (2024). Investigating Radio Frequency Vulnerabilities in the Internet of Things (IoT). IoT, 5(2), 356-380. https://doi.org/10.3390/iot5020018






