A Pervasive Collaborative Architectural Model at the Network’s Periphery
Abstract
:1. Introduction
- Reduce the risk of total or partial interruption of network connectivity caused by breakdowns or overwhelming (a huge number of) connections. This involves the improvement and continuity of maintaining the connectivity between mobile devices, regardless of the state of the network.
- Increase the resilience and reliability of sharing data, information and computations between these devices (objects).
- (a)
- Design an architecture sample to maintain connectivity, even during extreme events and harsh environments.
- (b)
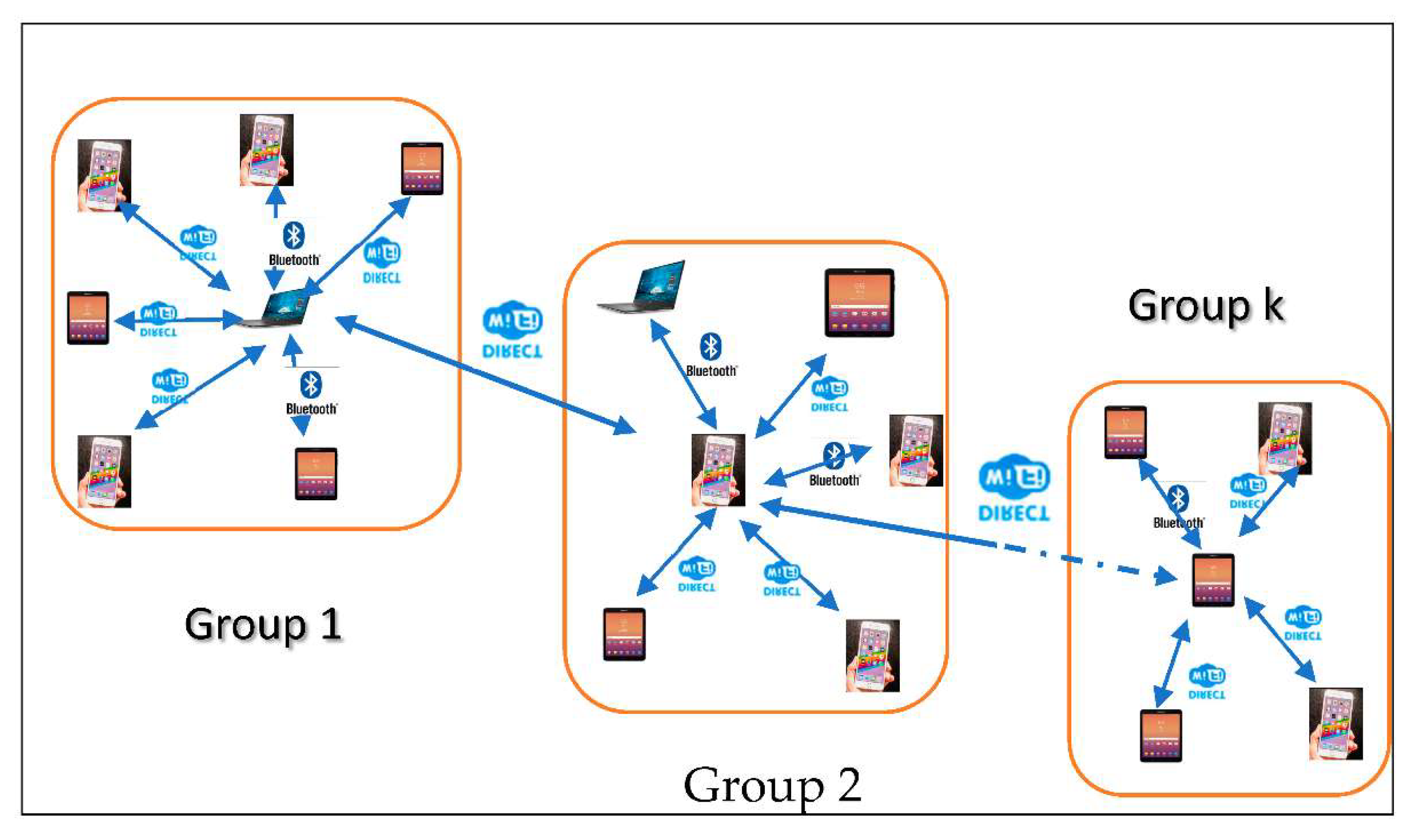
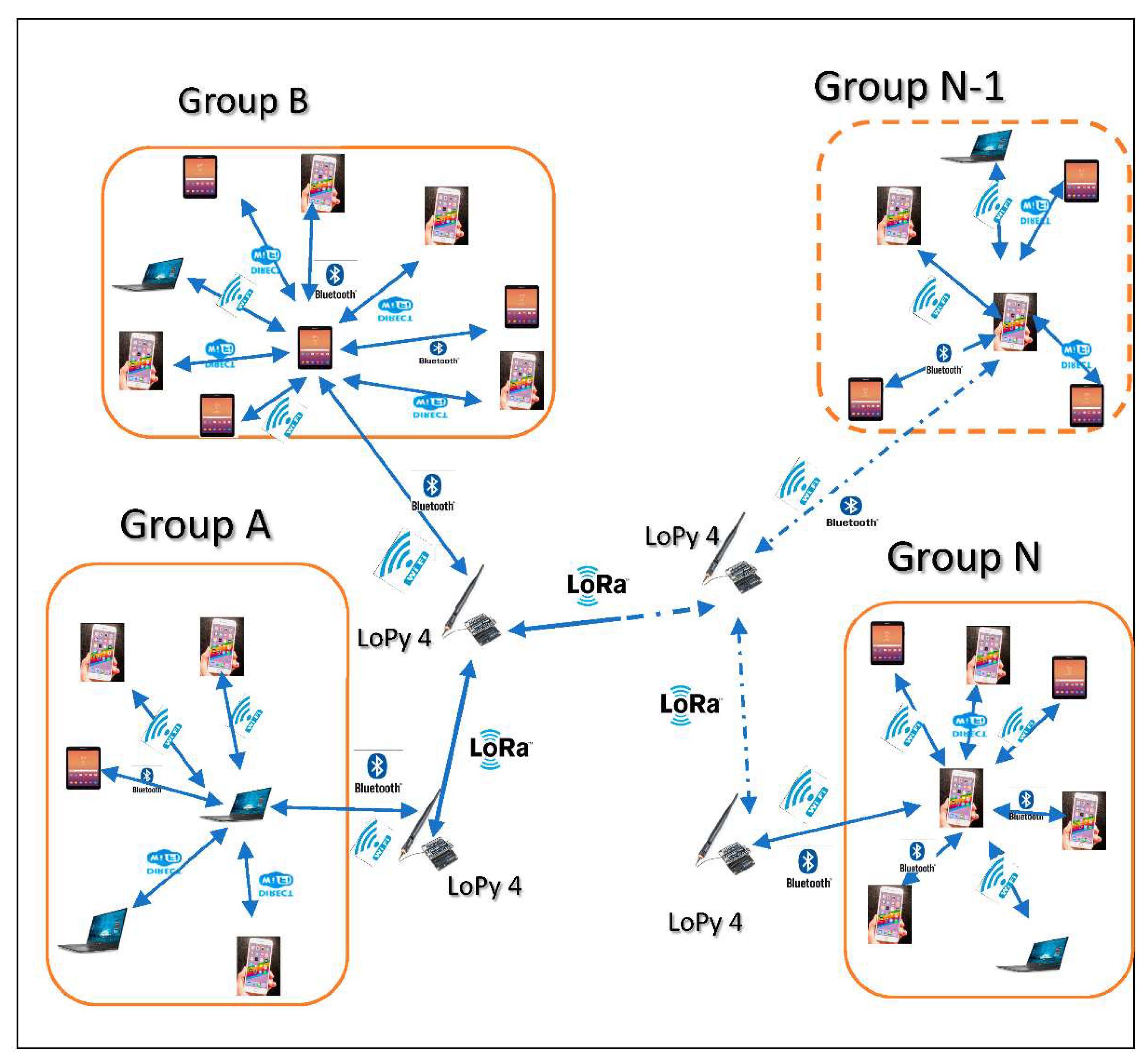
- Establish a multi-group network connected by device-to-device communication, such as Wi-Fi Direct and other communication technologies that have a larger range connection, such as those of Pycom’s LoPy4.
- (c)
- Propose four new algorithms and validate them through the required applications needed to manage the proposed model, such as dividing tasks and balancing their load. Among these applications is one to program the Lopys as transmitter, bridge and receiver.
2. Related Works on Pervasive Architectural Models and Their Limits
2.1. Pervasive Architectural Models
2.2. Issues of Pervasive Architectural Models at the Periphery of a Network
- -
- How to maintain the connectivity of network devices in various situations?
- -
- How to reduce the tasks of loading and unloading these small peripheral devices with central or intermediate service centers (cloud, fog, edge) to avoid the communication bottleneck?
- -
- How to reduce the energy consumption of these devices by minimizing their time of use and improving task scheduling and load balancing algorithms?
- (1)
- Limited connection bandwidth because of congestion from loading and unloading messages (tasks and data) to fixed or mobile center servers [29].
- (2)
- The limitations of mobile devices in terms of power, computing ability and data storage [39].
- (3)
- The reduced range of mobile network devices in terms of device-to-device connection when wireless connectivity with base stations is lost.
- (4)
- The complete loss of operability or effectiveness of these devices during severe events such as natural disasters and terrorist attacks because of malfunctions or failures in the base network stations.
- (5)
- The gap in performing relatively large jobs using these devices. This is partly due to the inadequate partitioning and scheduling tasks relative to the capabilities and loads of the equipment.
3. Collaborative Architectural Model of Mobile Pervasive Computing
3.1. Specific Objectives
- (1)
- Maintain the device’s connectivity in harsh environments and at any time.
- (2)
- Make objects (devices) and their networks more autonomous.
- (3)
- Compensate for loading/unloading to/from the service centers of cloud and other edge (middle and peripheral) architectures.
- (4)
- Maintain the capacity of the devices such as energy, computing ability and storage.
- (a)
- Smart mobile network peripheral architectures in terms of technologies, protocols, and applications of networking. There is a variety of devices such as sensors, smartphones, and tablets, in addition to small laptops, that have a capacity to be used as local micro-servers. These devices can be grouped according to their ranges. In this way, a chain of groups is established in several zones, taking advantage of the available connection modes such as wireless, device-to-device and those offered by Pycom’s LoPy4 technologies.
- (b)
- Software in the form of algorithms and applications to carry out tasks such as the creation of groups, the election of a group manager, and exchanging data and messages between nodes, as well as partitioning, scheduling and load balancing of tasks. These algorithms and applications are tested and validated by simulating harsh situations, for example, by sending messages from one device to another far away by combining the P2P connection technologies of devices and by establishing a proper mode of wireless technology based on communication technologies offered by Pycom’s LoPy4.
3.2. Autonomous Pervasive Collaborative Architectural Model (APCAM)
3.3. Structure of the Connectivity Model
3.4. Communication Behaviours of the APCAM Model
- (i)
- Bluetooth: LoPy4 can receive the information by Bluetooth using any device opening its Bluetooth option.
- (ii)
- Wi-Fi: we created LoPy4 as a Wi-Fi access point such that any device (Android, IOS, Windows or Linux) that connects to this Wi-Fi can communicate with LoPy4 at this address: http://192.168.4.1/test using HTTP post socket.
- (iii)
- Wi-Fi Direct: The devices are split into groups using mobile applications that we have implemented there based on Wi-Fi Direct technology. They use these applications to indicate their group owners. The group owner stores all information received from other group members in a local database. Then, it sends this information to the LoPy4 using a HTTP post socket.
3.5. Constructing Connectivity Algorithms to Manage the APCAM Model
- (1)
- Algorithm 1 to calculate the score of device d: CalculatingScores(d): This algorithm, as presented in [54], calculates the score of each device based on five criteria. This score is required to select a group manager (or a group owner) and in the process of routing messages between devices. For the sake of clarity and completeness, it is described below.
| Algorithm 1. CalculatingScores(d) |
| Begin |
| get factor capacity values of d; |
| ValScore = ValBattery ∗ PrcBattery + ValStock ∗ PrcStock + ValBandwidth ∗ PrcBandwidth + ValRam ∗ PrcRam + ValCPU ∗ PrcCPU; |
| return ValScore; |
| End |
- (2)
- Algorithm 2 that allows a device to create a list of its connected devices and their scores: This algorithm allows a device such as “d” to create a list of devices connected to it with their scores. When device “q” is connected to device “d”, it sends its resource information to device “d.” Then, device “d” calculates the score of device “q” by applying the algorithm CalculatingScores(q), then it adds device q to its list identified by two parameters: IP address and score.
| Algorithm 2. Creating_List_Devices_Scores(d) |
| int i = 0, j = 0, score = 0; |
| while connection is active and // In case of Wifi and P2P, a group does not exceed n = 12 devices |
| { |
| If device q is connecting to device d { |
| ; |
| score = CalculatingScores(q); |
| j = j+1 |
| ; |
| i = i+1; |
| j = j-1; // value of j is 0 or 1, ex: , |
| // , , , etc. |
| }//End if |
| } //End while |
| Return |
| End |
- (3)
- Algorithm 3 to sort the list device scores (Sorting_Devices_by_Scores): Bubble sorting is an algorithm that progressively moves up the largest elements of an array [55].
| Algorithm 3. Sorting_Devices_By_Scores () |
| // sorting based on the scores |
| int i, j, n, k; |
| Begin |
| ; |
| For (i = n; i> = 1; i --) |
| { |
| For (j = 2; j <= i; j ++) |
| { |
| k = 1; // rank of the line |
| If [k][j−1] > [k][j] Then |
| { |
| tmp_scr = [k][j−1]; |
| tmp_dvc = [k+1][j−1]; |
| [k][j−1] = [list]_d [k][j]; |
| [k][j] = tmp_scr; |
| [k+1][j] = tmp_dvc; |
| } End If |
| } End For |
| } End For |
| return ; |
| End |
- (4)
- Algorithm 4 to select the group manager: Selecting_Group_Manager: Let us randomly choose one of the n-connected devices , to be the group owner (GO). It periodically receives data, including scores, from other members at various moments in time, such as every 5 min. At each of these moments, the GO begins to compare iteratively the scores of the members of its group. It starts by comparing itself with resources and scores such as with . Consequently, the new GO becomes the device with the highest score. Again, by increasing index i by 1, the group owner GO will be compared with to determine the new group owner until i = n − 1.
| Algorithm 4. Selecting_Group_Manager |
| int n; |
| Begin |
| ; |
| ; // Max( |
| return ip_go; // Go: group owner |
| End |
- (5)
- Algorithm 5 Sending_Message (IP, IP) uses the previous algorithms to reach the target user (object). This algorithm routes a message from device A to target device B in areas covered by device-to-device radio connections such as Lora and Wi-Fi Direct. This algorithm is an iterative algorithm in which the device that has the message (at the beginning it is A) creates its list of devices connected to it with their scores. Then, it looks for device B to check if B can be reached using this device’s list to send it the message and accomplish its task. Otherwise, it searches through its list to find the device with the next highest score to B. This algorithm takes advantage of the device’s mobility to allow the device carrying the message to move to find in its list of connected devices the appropriate one to send this message. It keeps doing this until it meets the intended device B. We have a dynamic graph because the nodes can be entered in and out of it continuously. These devices are all in constant motion. Therefore, the device carrying the message must move to communicate with the others. Depending on the latitude and longitude of the nodes between B, the device carrying the message and the candidate to carry it, we determine their positions relative to each other. Then, the distances are compared between B and each of the two nodes. The carrier of the message sends it to the other if it has the shortest distance to B. For example, let M be the device carrying the message and N be the candidate to carry it. We calculate the distances MB and NB, and if NB < MB then M sends the message to N.
| Algorithm 5. for Sending_Message (, ) |
| Local variables: |
| int n; |
| double n = 0; ; ; ; ; |
| ; |
| String ;// IP of the device being processed |
| String [][] // Array of the devices connected to the device being processed |
| String [][] // Array of devices sorted according to scores and connected to the device being processed |
| String min_scr; // threshold score Boolean flag = false |
| Begin |
| ip = ;; |
| ; ; |
| ; // distance between transmitter and receiver (Here, A and B) |
| While ip != |
| = Creating_List_Devices_Scores(ip); // creating the list connected to the device |
| = Sorting_Devices_By_Scores(ip, ); |
| n =.length; // number elements in this array |
| // check if B belongs to the list of devices connected to the device being processed |
| For (i = n−1; i ≥ n; i--) { |
| = // starting by the device having the maximum score |
| If //the device being processed can |
| //communicate the message directly to B |
| Exit //as the message has arrived at its |
| // destination B |
| Else{ |
| ; |
| ; |
| // distance between ip and B |
| // distance between and B |
| < and min_scr ≤ { |
| // is closer to B and its score > threshold score |
| // the message is deposited at |
| }//End If |
| }//End If |
| } // End For |
| } // End While |
| End Algorithm |
3.6. Operating Mechanism and Security Controls
4. Experimental Study
- Mobiles: (i) Smartphone Samsung Galaxy S21: CPU Octa-core (1 × 2.9 GHz Cortex-X1 & 3 × 2.80 GHz Cortex-A78 & 4 × 2.2 GHz Cortex-A55)—International, OS Android 11, One UI 3.1, 256 GB RAM, 512 GB storage. (ii) Smartphone Samsung Galaxy S6: Processor Octa-core, 2100 MHz, ARM Cortex-A57 and ARM Cortex-A53, 64-bit—14 nm, RAM 3 GB LPDDR4, OS Android 7.0 Nougat, 64 GB storage. (iii) Smartphone LG K40: OS Android 8.1 (Oreo), LG UX 7, CPU Octa-core 2.0 GHz Cortex-A53, 2 GB RAM, 32 GB storage.
- Tablets: (i) Samsung Galaxy Tab A 10.1: Samsung Exynos 7904 CPU, 2 GB RAM, Operating System Android 9 with One UI, 32 GB storage. (ii) Samsung Galaxy Tab A 8.0: Processor Qualcomm Snapdragon 429 4 × 2 GHz, Cortex-A53, 2 GB RAM, Operating System Android 9.0 Pie, 32 GB storage. (iii) Samsung Galaxy Tab 7.0 Plus: processor 1.5 GHz quad-core, 1.5 GB of RAM, Operating System Android, 8 GB storage.
- Laptops: (i) Laptop 1 with the following characteristics: Intel® Core™ i7 processor, x64-based processor, Windows 10 Pro 64-bit OS, 2.3 GHz CPU, and 16 GB of RAM. (ii) Laptop 2 with the following characteristics: Intel® Core™ i7 6820HP CPU, 2.7 GHz, x64-based processor, 64-bit OS, and 16 GB of RAM. (iii) MacBook Pro with the following characteristics: Intel Core i7 quad core 2.8 GHz, macOS High Sierra and 16 Go of integrated memory LPDDR3 2 133 MHz.
4.1. Category A
- (1)
- Finding the shortest path of maintained communication between two devices in the network through which information can be transferred as messages from one device to another. Ensuring the connectivity of the shortest path nodes are presented in the following three case studies [56]:
- (i)
- The nodes are obviously connected.
- (ii)
- Nodes must be moved.
- (iii)
- Using and moving a drone with the capability of P2P wireless technology.
- (2)
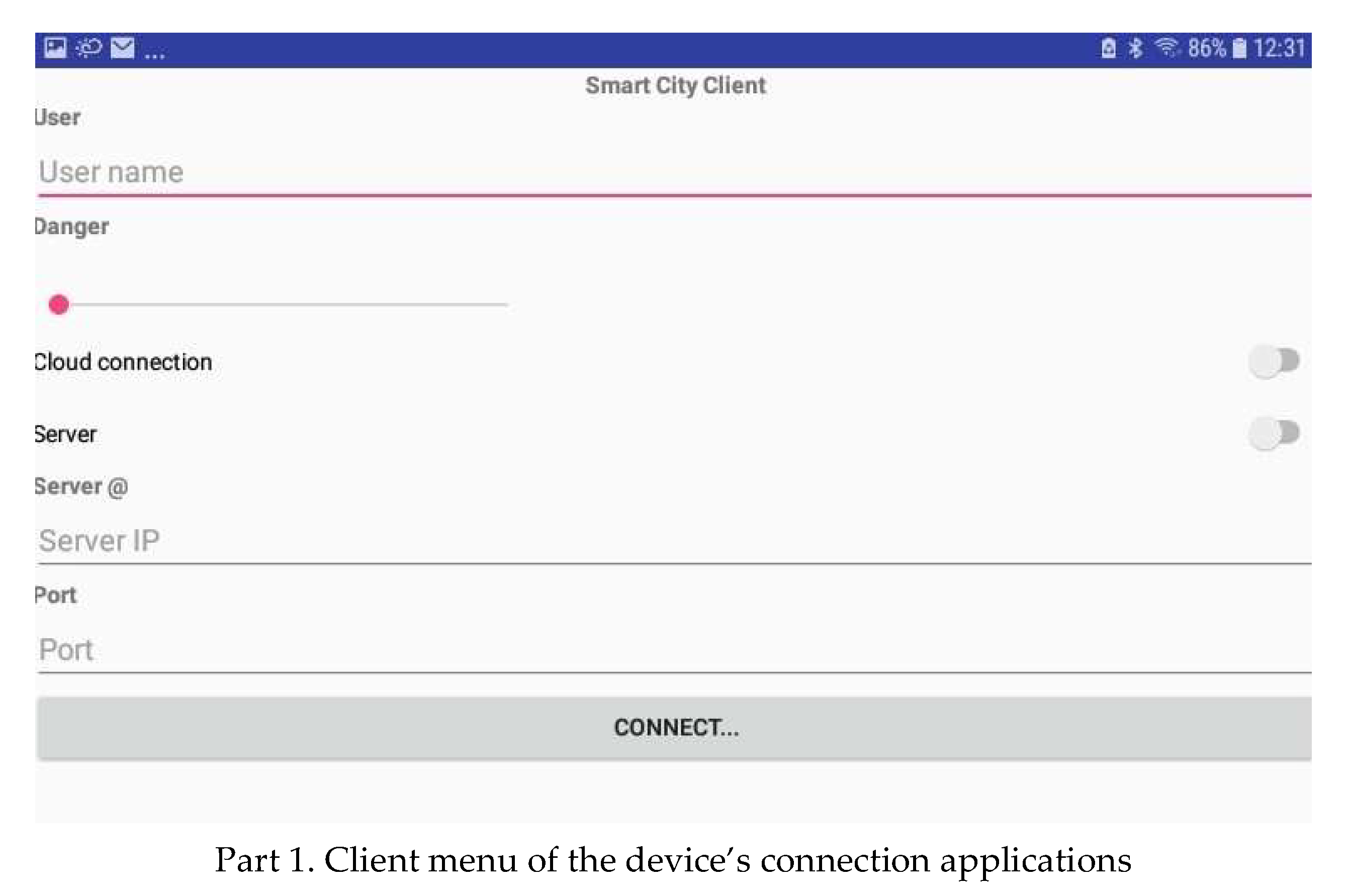
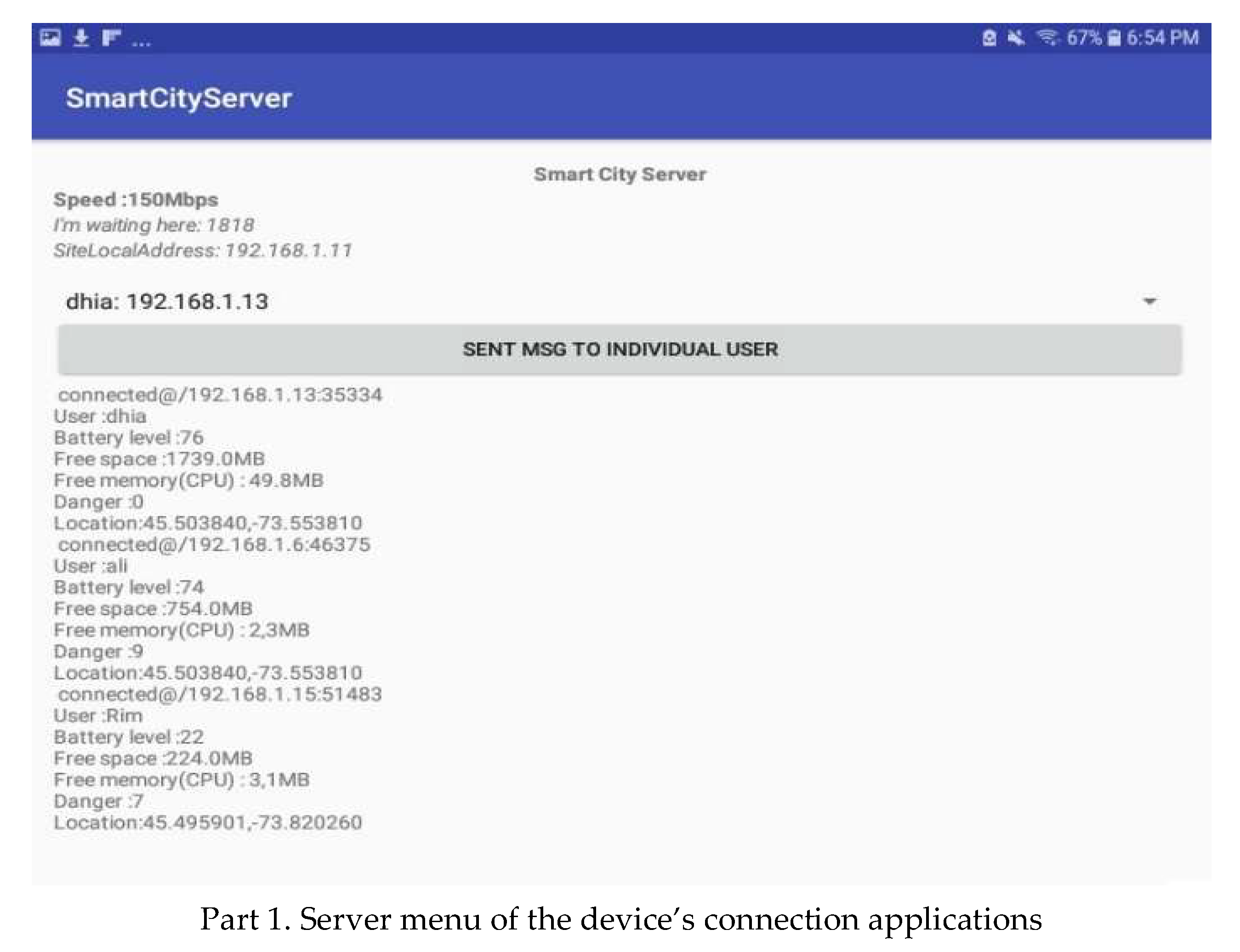
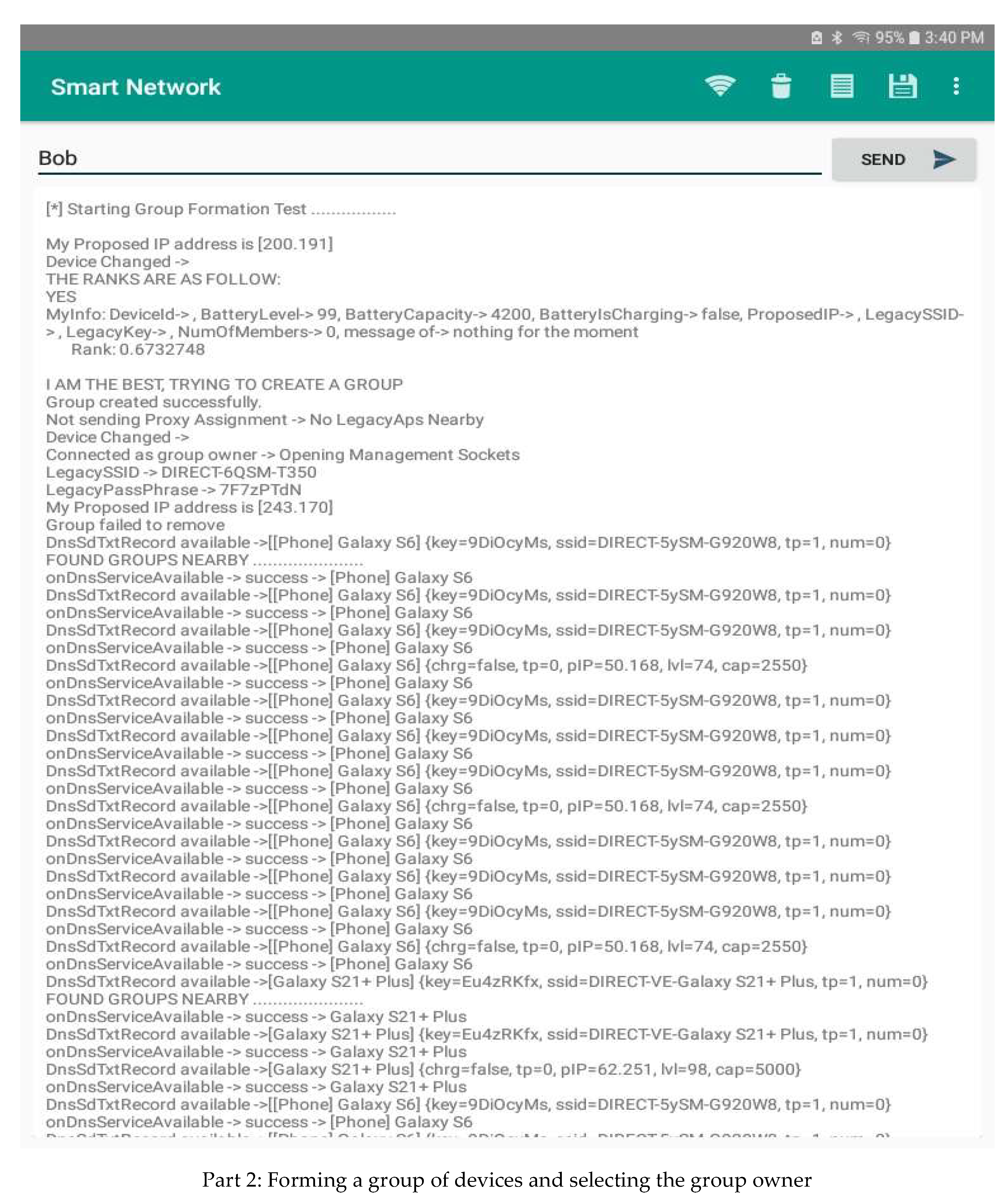
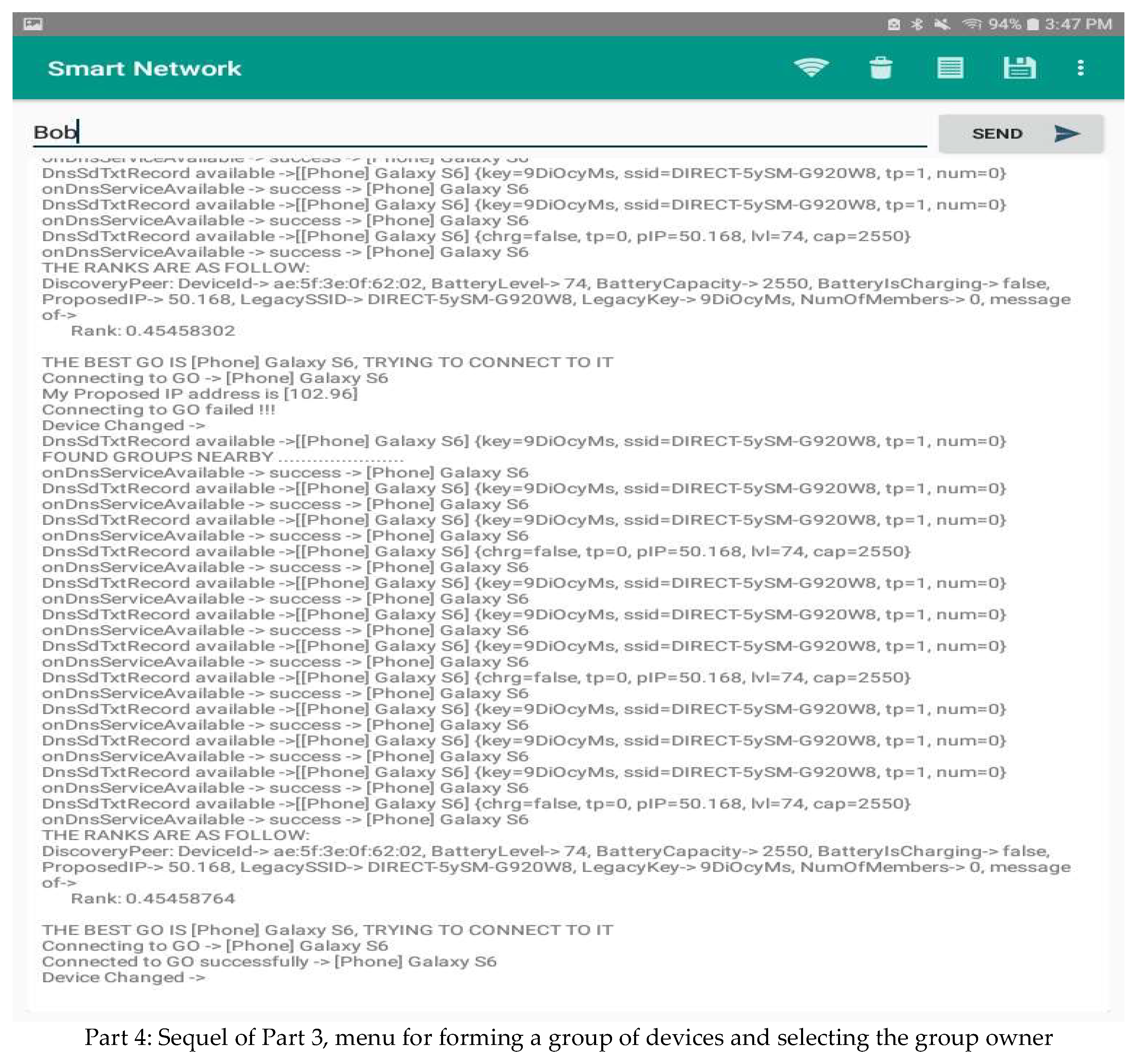
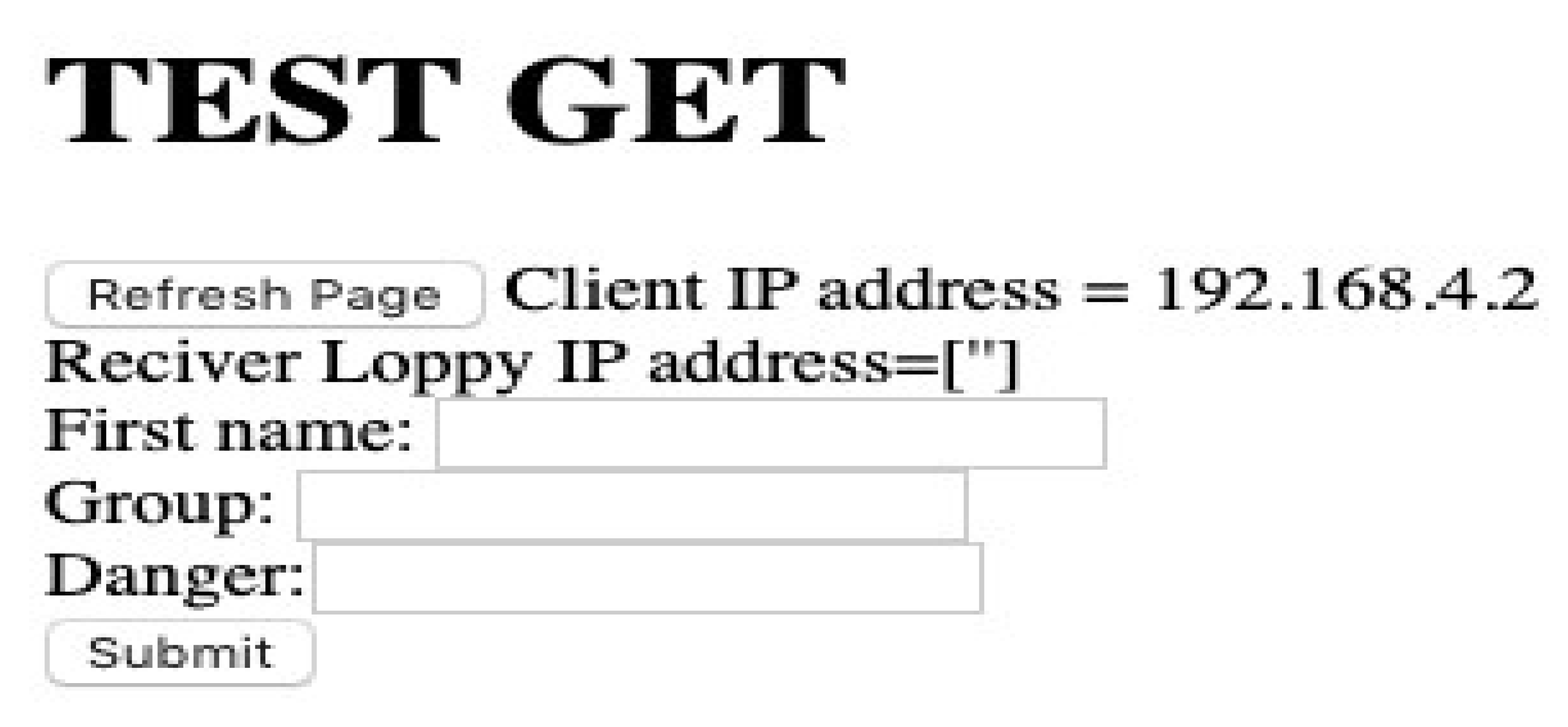
- Establishing a network by forming a chain of adjacent groups of interfering devices within the available communication range. A device belonging to two groups can act as a gateway between the owners of these groups. The message must be sent in an intelligent way, taking into consideration the distance to the destination device and the continuity of communication through nearby devices. In the following, we present the application interface of forming groups and selecting their owner. An analysis of the data available from the device’s interface in Figure 6 shows that the information about devices in its connection range is periodically communicated to it. In addition, the GO is also changed when the score varies. Different parts are used to show the most important components of the graphical interfaces of our system.
4.2. Category B
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kramp, T.; van Kranenburg, R.; Lange, S. Introduction to the Internet of Things. In Enabling Things to Talk; Bassi, A., Bauer, M., Fiedler, M., Kramp, T., van Kranenburg, R., Lange, S., Meissner, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar] [CrossRef] [Green Version]
- Coulouris, G.; Dollimore, J.; Kindberg, T.; Blair, G. Distributed Systems: Concepts and Design, 5th ed.; Addison Wesley: Boston, MA, USA, 2012. [Google Scholar]
- L’Informatique de Poche dans l’Entreprise; Les Cahiers d’e-Caria. Available online: https://dochero.tips/linformatique-de-poche-dans-lentreprise.html (accessed on 3 September 2021).
- Fadlallah, G.; Rebaine, D.; Mcheick, H. Scheduling problems from workshop to collaborative mobile computing: A state of the art. Int. J. Comput. Sci. Inf. Secur. 2018, 16, 47–69. [Google Scholar]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef] [Green Version]
- Kai, K.; Cong, W.; Tao, L. Fog computing for vehicular ad hoc networks: Paradigms, scenarios, and issues. J. China Univ. Posts Telecommun. 2016, 23, 56–96. [Google Scholar] [CrossRef]
- Kar, U.N.; Sanyal, D.K. An overview of device-to-device communication in cellular networks. ICT Express 2018, 4, 203–208. [Google Scholar] [CrossRef]
- 3GPP, 3rd Generation Partnership Project (3GPP). Available online: http://www.3gpp.org/ (accessed on 11 April 2021).
- Saranya, A.; Rajasekaran, K.; Chandra, S. An Overview of Mobile Ad Hoc Networks. Int. J. Comput. Sci. Inf. Technol. Res. 2016, 4, 245–250. [Google Scholar]
- Rakshith, G.; Mahesh, R. New Technology for Machine to Machine Communication in Softnet Towards 5G. Int. J. Wirel. Mobile Netw. 2017, 9, 1–23. [Google Scholar]
- Jones, R. The International Telecommunication Union; IEEE: New York, NY, USA, 2019; p. 1248. [Google Scholar]
- Hennebert, C.; Baldini, G.; Peirce, T.; Botterman, M.; Talacchini, M.; Guimaraes Pereira, A.; Handte, M.; Rotondi, D.; Pohls, H. IoT Governance, Privacy and Security Issues. Available online: https://www.researchgate.net/publication/275540220_IoT_Governance_Privacy_and_Security_Issues (accessed on 3 September 2021).
- Weiwen, Z.; Yonggang, W.; Dapeng, W. Collaborative Task Execution in Mobile Cloud Computing Under a Stochastic Wireless Channel. IEEE Trans. Wirel. Commun. 2015, 14, 81–93. [Google Scholar] [CrossRef]
- Wang, C.M.; Hong, S.F.; Wang, S.T.; Chen, H.C. A dual-mode exerciser for a collaborative computing environment. In Proceedings of the 11th Asia-Pacific, Software Conference, IEEE Computer Society, Busan, Korea, 30 November–3 December 2004; pp. 240–248. [Google Scholar] [CrossRef] [Green Version]
- Radicati, S. Mobile Statistics Report: 2014–2018, The Radicati Group, INC. Available online: https://www.radicati.com/?page_id=54 (accessed on 3 February 2014).
- Available online: https://www.statista.com/statistics/274774/forecast-of-mobile-phone-users-worldwide/ (accessed on 3 September 2021).
- Rose, C.; Eldridge, S.; Chapin, L. The Internet of Things: An Overview-Understanding the Issues and Challenges of a More Connected World. Internet Soc. 2015. Available online: https://www.internetsociety.org/wp-content/uploads/2017/08/ISOC-IoT-Overview-20151221-en.pdf (accessed on 3 September 2021).
- Fadlallah, G.; Mcheick, H.; Rebaine, D. Layered Architectural Model for Collaborative Computing in Peripheral Autonomous Networks of Mobile Devices. In Proceedings of the 16th International Conference on Mobile Systems and Pervasive Computing (MobiSPC), Halifax, NS, Canada, 19–21 August 2019. [Google Scholar]
- Abdelaziz, J. Un Cadre Architectural Pour la Collaboration dans L’internet Des Objets. Uneapproche Basée sur L’informatique en Brouillard. Ph.D. Thesis, Université du Québec à Chicoutimi, Chicoutimi, QC, Canada, 2018. [Google Scholar]
- Steen, M.V.; Tanenbaum, A.S. Distributed Systems, 3rd ed.; Pearson Education: London, UK, 2017. [Google Scholar]
- Lora Technology. Available online: https://canada.newark.com/wireless-lora-technology (accessed on 3 September 2021).
- Elhoseny, M.; Hassanien, A.E. Expand Mobile WSN Coverage in Harsh Environments. In Dynamic Wireless Sensor Networks; Springer: Cham, Switzerland, 2019; pp. 29–52. [Google Scholar]
- Gupta, H.P.; Tyagi, P.K.; Singh, M.P. Regular Node Deployment for k -Coverage in m -Connected Wireless Networks. IEEE Sens. J. 2015, 15, 7126–7134. [Google Scholar] [CrossRef]
- Sharma, D.; Gupta, V. Improving coverage and connectivity using harmony search algorithm in wireless sensor network. In Proceedings of the 2017 International Conference on Emerging Trends in Computing and Communication Technologies (ICETCCT), Dehradun, India, 17–18 November 2017; pp. 1–7. [Google Scholar]
- Hasson, S.T.; Finjan, A.A.R. A suggested angles-based sensors deployment algorithm to develop the coverages in WSN. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 547–552. [Google Scholar]
- Mcheick, H.; Hatoum, M.S.B.; Ghaddar, A. CMHWN: Coverage Maximization of Heterogeneous Wireless Network. In Proceedings of the 16th ACS/IEEE International Conference on Computer Systems and Applications AICCSA’19, Abu Dhabi, United Arab Emirates, 3–7 November 2019. [Google Scholar]
- Ghaddar, A.; Hattoum, M.A.; Fadlallah, G.; Mcheick, H. MCCM: An Approach for Connectivity and Coverage Maximization. Future Internet 2020, 12, 19. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; Li, F.; Wang, X.; Li, T.; Hong, T. A WiFi-Direct Based Local Communication System. In Proceedings of the 2018 IEEE/ACM 26th International Symposium on Quality of Service (IWQoS), Banff, AB, Canada, 4–6 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Ferrer, A.J.; Marques, J.M.; Jorba, J. Towards the decentralized cloud: Survey on approaches and challenges for mobile, ad hoc, and edge computing. ACM Comput. Survey 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Fadlallah, G.; Mcheick, H.; Rebaine, D.; Adda, M. Towards Mobile Collaborative Autonomous Networks Using Peer-to-Peer Communication. In Proceedings of the 7th International Conference on Software Engineering and New Technologies (ICSENT 2018), Hammamet, Tunisia, 26–28 December 2018; ACM: New York, NY, USA, 2018. ISBN 978-1-4503-6101-9. [Google Scholar] [CrossRef]
- Ahmed, A.; Ahmed, E. A Survey on Mobile Edge Computing. In Proceedings of the 2016 10th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 7–8 January 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Jararweh, Y.; Doulat, A.; Darabseh, A.; Alsmirat, M.; Al-Ayyoub, M.; Benkhelifa, E. Sdmec: Software defined system for mobile edge computing. In Proceedings of the 2016 IEEE International Conference on Cloud Engineering Workshop (IC2EW), 4–8 April 2016; pp. 88–93. [Google Scholar]
- Beck, M.T.; Feld, S.; Fichtner, A.; Linnhoff-Popien, C.; Schimper, T. Me-volte: Network functions for energy-efficient video transcoding at the mobile edge. In Proceedings of the 2015 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; pp. 38–44. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Bahl, P.; Caceres, R.; Davies, N. The case for vm-based cloudlets in mobile computing. Pervasive Comput. 2009, 8, 14–23. [Google Scholar] [CrossRef]
- Fesehaye, D.; Gao, Y.; Nahrstedt, K.; Wang, G. Impact of cloudlets on interactive mobile cloud applications. In Proceedings of the IEEE 16th International Enterprise Distributed Object Computing Conference (EDOC), Beijing, China, 10–14 September 2012; pp. 123–132. [Google Scholar] [CrossRef]
- Masson, A.M.G. MoCCA: A Mobile Cellular Cloud Architecture. J. Cyber Secur. Mobil. 2013, 2, 105–125. [Google Scholar] [CrossRef] [Green Version]
- Miluzzo, E.; Cáceres, R.; Chen, Y.F. Vision: mClouds Computing on Clouds of Mobile Devices. In Proceedings of the Third ACM Workshop on Mobile Cloud Computing and Services MCS, Lake District, UK, 25 June 2012. [Google Scholar] [CrossRef]
- Hammam, A.; Senbel, S. A reputation trust management system for ad hoc mobile clouds. Intell. Syst. Ref. Libr. 2014, 70, 519–539. [Google Scholar]
- Mehanna, A.A.; Abdel-Fattah, M.A.; Abdel-Gaber, S.M. Cloudlet: A Mobile Cloudlet Model Using Wi-Fi Direct. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 972. [Google Scholar]
- Wi-Fi Alliance, P2P Task Group. Wi-Fi Peer-to-Peer (P2P) Technical Specification; Version 1.5. Available online: https://cse.iitkgp.ac.in/~bivasm/sp_notes/wifi_direct_2.pdf (accessed on 3 September 2021).
- Funai, C.; Tapparello, C.; Heinzelman, W. Enabling Multi-hop Ad Hoc Networks Through Wi-Fi Direct Multi-group Networking. In Proceedings of the International Conference on Computing, Networking and Communications, Santa Clara, CA, USA, 26–29 January 2017; pp. 491–497. [Google Scholar]
- Casetti, C.; Chiasserini, C.F.; Duan, Y.; Giaccone, P.; Manriquez, A.P. Data Connectivity and Smart Group Formation in Wi-Fi Direct Multi-group Networks. IEEE Trans. Netw. Serv. Manag. 2018, 15, 245–259. [Google Scholar] [CrossRef]
- Yaqoob, I.; Ahmed, E.; Gani, A.; Mokhtar, S.; Imran, M. Mobile ad hoc cloud: A survey. Wirel. Commun. Mob. Comput. 2016, 16, 2572–2589. [Google Scholar] [CrossRef]
- Balasubramanian, V.; Karmouch, A. An Infrastructure as a Service for Mobile Ad hoc Cloud. In Proceedings of the IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 9–11 January 2017. [Google Scholar]
- Yaqoob, I.; Ahmed, E.; Gani, A.; Mokhtar, S.; Imran, M. Heterogeneity Aware Task Allocation in Mobile Ad Hoc Cloud. IEEE Access 2017, 5, 1779–1795. [Google Scholar] [CrossRef]
- Kirby, G.; Dearle, A.; Macdonald, A.; Fernandes, A. An Approach to Ad hoc Cloud Computing. arXiv 2010, arXiv:1002.4738. [Google Scholar]
- Shiraz, M.; Gani, A.; Khokhar, R.H.; Buyya, R. A Review on Distributed Application Processing Frameworks in Smart Mobile Devices for Mobile Cloud Computing. IEEE Commun. Surv. Tutor. 2013, 15, 1294–1313. [Google Scholar] [CrossRef] [Green Version]
- Hoang, D.T.; Lee, C.; Niyato, D.; Wang, P. A survey of mobile cloud computing: Architecture, applications, and approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar]
- Sherin, B.C.; Anita, E.A.M. A Survey of Scheduling Algorithms for Wireless Ad-hoc Networks. Int. J. Adv. Sci. Eng. 2018, 4, 776–787. Available online: www.mahendrapublications.com (accessed on 3 September 2021). [CrossRef]
- Pervasive and Mobile Computing, Science Direct Journal Publisher: Elsevier. Available online: https://www.researchgate.net/journal/Pervasive-and-Mobile-Computing-1574-1192 (accessed on 3 September 2021).
- Rappaport, T.S.; Xing, Y.; MacCartney, G.R., Jr.; Molisch, A.F.; Mellios, E.; Zhang, J. Overview of Millimeter Wave Communications for Fifth-Generation (5G) Wireless Networks-with a focus on Propagation Models. IEEE Trans. Antennas Propag. 2017, 65, 6213–6230. [Google Scholar] [CrossRef]
- Oide, T.; Abe, T.; Suganuma, T. Infrastructure-Less Communication Platform for Off-The-Shelf Android Smartphones. Sensors 2018, 18, 776. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Pycom Enterprise, Description and Technical Details of Pycom’s Lopy4. Available online: https://static6.arrow.com/aropdfconversion/c500cfa0a971d49ac7d694a083bb5f20650e211a/pgurl_6269436244227100.pdf (accessed on 12 April 2021).
- Fadlallah, G.; Rebaine, D.; Mcheick, H. A Greedy Scheduling Approach for Peripheral Mobile Intelligent Systems. IoT 2021, 2, 14. [Google Scholar] [CrossRef]
- Le Tri a Bulle. Available online: https://rmdiscala.developpez.com/cours/LesChapitres.html/Cours4/TBchap4.6.htm (accessed on 3 September 2021).
- Fadlallah, G.; Mcheick, H.; Rebaine, D. Internet-of-Things (IoT) Shortest Path Algorithms and Communication Case Studies for Maintaining Connectivity in Harsh Environments. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC2020), Montreal, QC, Canada, 20–22 October 2020; pp. 1–8. [Google Scholar]
- Viavi Enterprise, Technologie 5G. Available online: https://www.viavisolutions.com/fr-fr/technologie-5g (accessed on 3 September 2021).



| Architectural Model | Description and Analysis of These Models |
|---|---|
| Mobile edge computing (MEC) | The main advantage of MEC is to deploy mini cloud servers in each communication base station, especially at the edge of mobile networks. MEC is applied to mobile devices in these edge networks to reduce delays by allowing computational and storage capabilities at the edge of mobile networks instead of being at central servers [5,31]. MEC has better discharge techniques to edge servers, giving the network low latency and high bandwidth [6]. In addition, it provides efficient storage and energy consumption through many architectures such as the software-defined system for mobile edge computing (SDMEC) for storage [32] and ME-VoLTE for computing, which integrates MEC with long-term evolution (LTE) [33]. |
| Cloudlet | A cloudlet is a proximal cloud that brings computing capacities closer to the mobile devices it serves to avoid latency. A cloudlet is formed by a cluster of multi-core computers, a very powerful multi-core server and a high bandwidth wireless LAN with high connectivity [34,35]. “Cloudlets are decentralized and widely dispersed Internet infrastructure whose compute cycles and storage resources can be leveraged by nearby mobile computers [34].” |
| Collaborative fog computing (CoFog) | CoFog provides dynamic services based on predefined templates using formal mechanisms called operations. An operation represents a relationship between a collaboration request and the services that can fulfill that request. There are two types of operations: conservative, which retains the same type of data, and non-conservative, which creates a new type. CoFog relies on the ability to discover, recover and provide security services using role-based and attribute-access models [19]. |
| Mobile cellular cloud architecture (MoCCA) | MoCCA [29,36] uses small scale micro-servers loaded on mobile phones to build its own mobile cloud architecture. Its resources are smartphones, base stations, base station controllers and mobile switching centers. Its main concerns are (i) connectivity, (ii) computational limitations, (iii) churn, because of user mobility and device volatility, (iv) lack of power; and (v) user incentives. |
| mClouds | With mClouds [29,37], mobile devices become essential components of cloud computing architectures. An mCloud uses specific resource-discovery procedures, incentive management and distributed processing to execute locally whenever possible. |
| MobiCloud | MobiCloud [29,38] is a trustworthy collaborative mobile cloud administration system that enables the efficient and collaborative management of mobile smart phone resources. Its objective is to use mobile devices even when there is no internet connectivity. MobiCloud architecture has participant nodes and a field control node (a cloud agent) that provides centralized cloud controller functionalities by locating the required resources. |
| Mobile cloudlet (M.Cloudlet) | M.Cloudlet uses its own servers without base station services to provide cloud services in order to dispense the connection to remote cloud central servers or central ones of fixed cloudlets. To build a network of mobile cloudlet, M.Cloudlet uses Wi-Fi Direct to connect nearby mobile devices [39]. The M.Cloudlet architecture has two main phases: (i) build M.Cloudlet by discovering and negotiating neighboring devices to form their groups and choose their owners, then exchange information, (ii) control and manage devices, including their tasks and spontaneous lists of participating devices [39]. |
| Multi-group networking | This supports Wi-Fi Direct connections between multiple devices in groups, then interconnects different groups to create ad hoc multi-hop networks. However, the Wi-Fi Direct standard [40] defines only intra-group communications, where the group owner (GO) is central to all communications in its group. A Wi-Fi Direct device called a gateway node can operate as a member of more than one group at a time. In a proposed time-sharing mechanism, the gateway node can switch between two or more groups to implement multi-group communication scenarios using only Wi-Fi Direct [41]. |
| Building smart multi-group networks by Wi-Fi Direct | Independent group formation aims to achieve the efficient use of devices while maintaining connectivity. The main obstacle to the widespread adoption of P2P communication is the lack of coordination of services. Efforts are focused on the potential of Wi-Fi Direct as a P2P communication technology in medium- and large-level frameworks using unrooted Android devices. It functions by (i) designing multi-groups interconnected logical topology by tunnelling the application layer and (ii) proposing a fully distributed intelligent group formation mechanism to construct networks, considering the group’s durability, the devices’ power consumption, the bandwidth average and network extent [42]. |
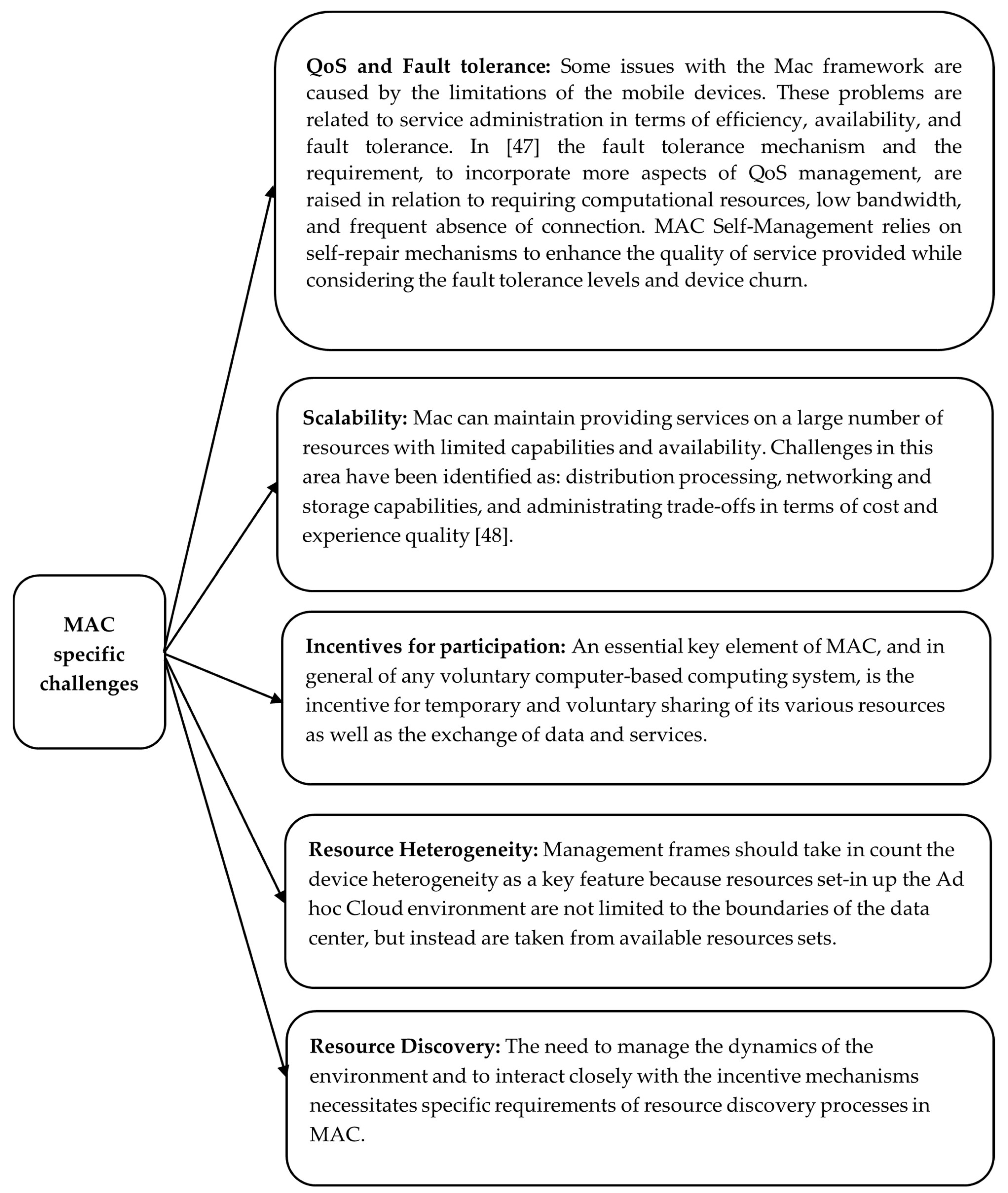
| Mobile ad hoc cloud computing (MAC) | MAC computing “is still in its infancy” [29]. Several definitions of MAC have been proposed [43,44,45], such as “MAC enables the use of many nearby resource-rich mobile devices to provide computational services in the vicinity” [45]. MAC roots are in mobile cloud computing (MCC) but also in opportunistic computing [43] or distributed computing with the caveats of intermittent connectivity and delay tolerance. The ad hoc cloud features are developed by Kirby et al. [46] as self-administration in terms of flexibility, performance and balancing potentially contradictory policy goals. MAC challenges include (i) limited computing and energy resources of mobile devices and their ability to perceive context and location, (ii) network connectivity, (iii) security and (iv) partitioning and application loading. In addition, there are specific challenges, as shown in Figure 1, introduced in the MAC context as mobile devices are the only resources [29]. |
| Variable | Description |
|---|---|
| ValBattery | Battery energy |
| ValStock | Storage capacity |
| ValBandwidth | Bandwidth |
| ValRam | RAM capacity |
| ValCPU | CPU capacity |
| ValScore | Score value |
| PrcBattery | Percentage of battery influence |
| PrcStock | Percentage of storage influence |
| PrcBandwidth | Percentage of bandwidth influence |
| PrcRam | Percentage of RAM influence |
| PrcCPU | Percentage of CPU influence |
| Ip_d, ip_q, or ip_go | The IP address of device d, q or group owner |
| An array of two rows and n columns for device d | |
| Number of devices in | |
| tmp_dvc | Temporary device |
| tmp_scr | Temporary score |
| Full Name | Group | Danger | IP |
|---|---|---|---|
| Eric Bouchard | G1 | 5 | 192.168.4.2 |
| DIRECT-H8SM-G920W8 | G1 | 1 | 192.168.4.3 |
| Jad Tremblay | G2 | 3 | 192.168.4.6 |
| Jean Richard | G2 | 4 | 192.168.4.2 |
| Hugo Michel | G3 | 7 | 192.168.4.2 |
| Hanna Hugo | G3 | 6 | 192.168.4.2 |
| Luc Besson | G3 | 6 | 192.168.4\xae2 |
| Full Name | Group | Danger | IP |
|---|---|---|---|
| Ali Jabril | G7 | 7 | 192.168.4.3 |
| Mohamad Mickeal | G4 | 2 | 192.168.4.3 |
| Alain Legof | N/A | 4 | Bluetooth |
| Sam | G5 | 3 | 192.168.4.2 |
| Alain April | G3 | 7 | 192.168.4.3 |
| DIRECT-ueSM-G920W8 | G1 | 1 | 192.168.4.5 |
| Dihya Messaoudi | N/A | 4 | Bluetooth |
| DIRECT-ueSM-G920W8 | G1 | 1 | 192.168.4.5 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fadlallah, G.; Mcheick, H.; Rebaine, D. A Pervasive Collaborative Architectural Model at the Network’s Periphery. IoT 2021, 2, 524-548. https://doi.org/10.3390/iot2030027
Fadlallah G, Mcheick H, Rebaine D. A Pervasive Collaborative Architectural Model at the Network’s Periphery. IoT. 2021; 2(3):524-548. https://doi.org/10.3390/iot2030027
Chicago/Turabian StyleFadlallah, Ghassan, Hamid Mcheick, and Djamal Rebaine. 2021. "A Pervasive Collaborative Architectural Model at the Network’s Periphery" IoT 2, no. 3: 524-548. https://doi.org/10.3390/iot2030027
APA StyleFadlallah, G., Mcheick, H., & Rebaine, D. (2021). A Pervasive Collaborative Architectural Model at the Network’s Periphery. IoT, 2(3), 524-548. https://doi.org/10.3390/iot2030027