An IoT-Based Mobile System for Safety Monitoring of Lone Workers
Abstract
:1. Introduction
- Uncomfortable.
- Too hot.
- Blamed for decreased productivity or an inability to perform tasks.
- Unavailable near the work task.
- Ill-fitting.
- Unattractive looking.
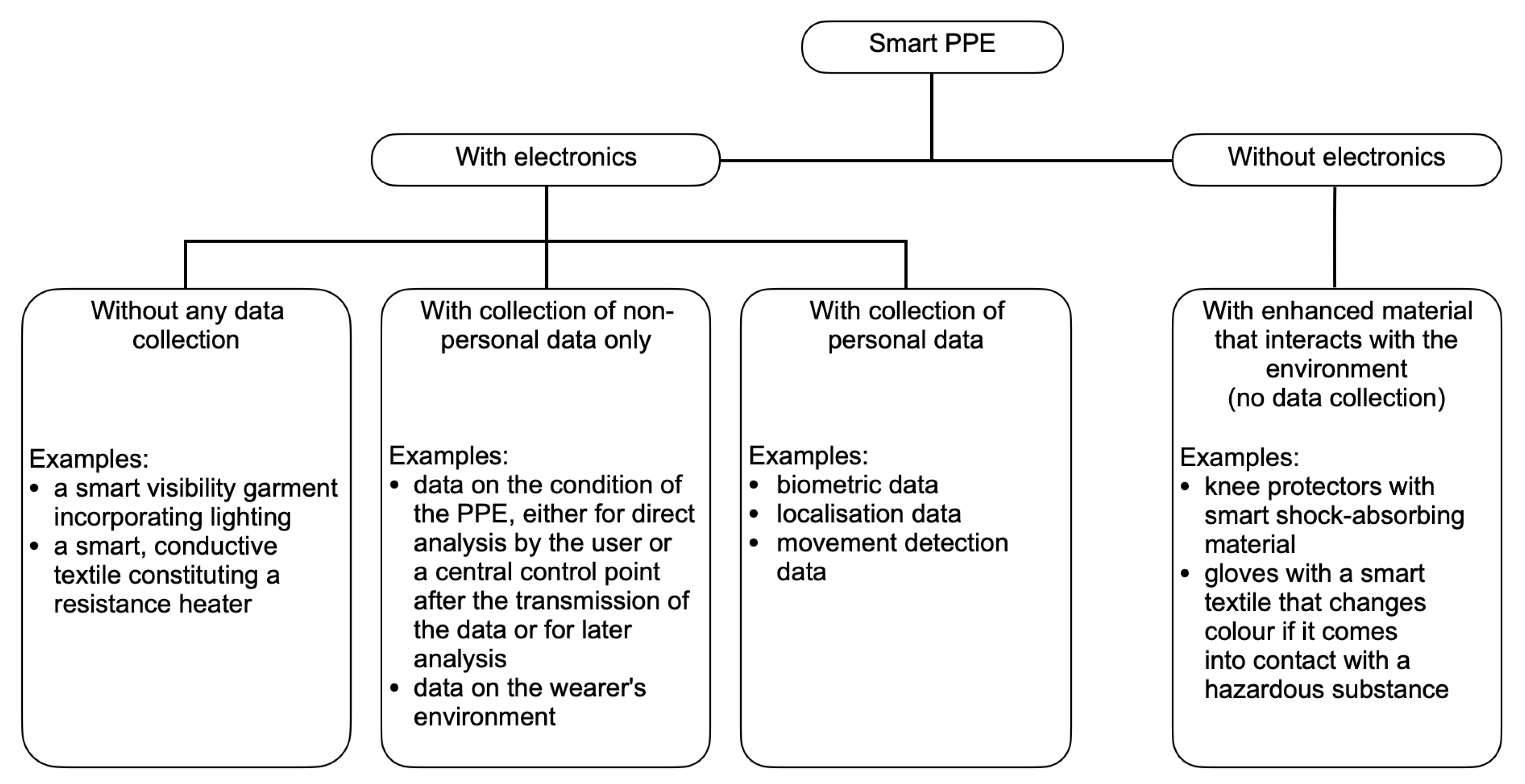
Smart Personal Protective Equipment
2. Related Work
2.1. IoT Technologies
2.2. Machine Learning Solutions
2.3. Wearable Sensors
2.4. Recap
3. Preliminaries
3.1. Fog-Computing
3.2. IoT Protocols
4. The Monitoring System for Lone Workers
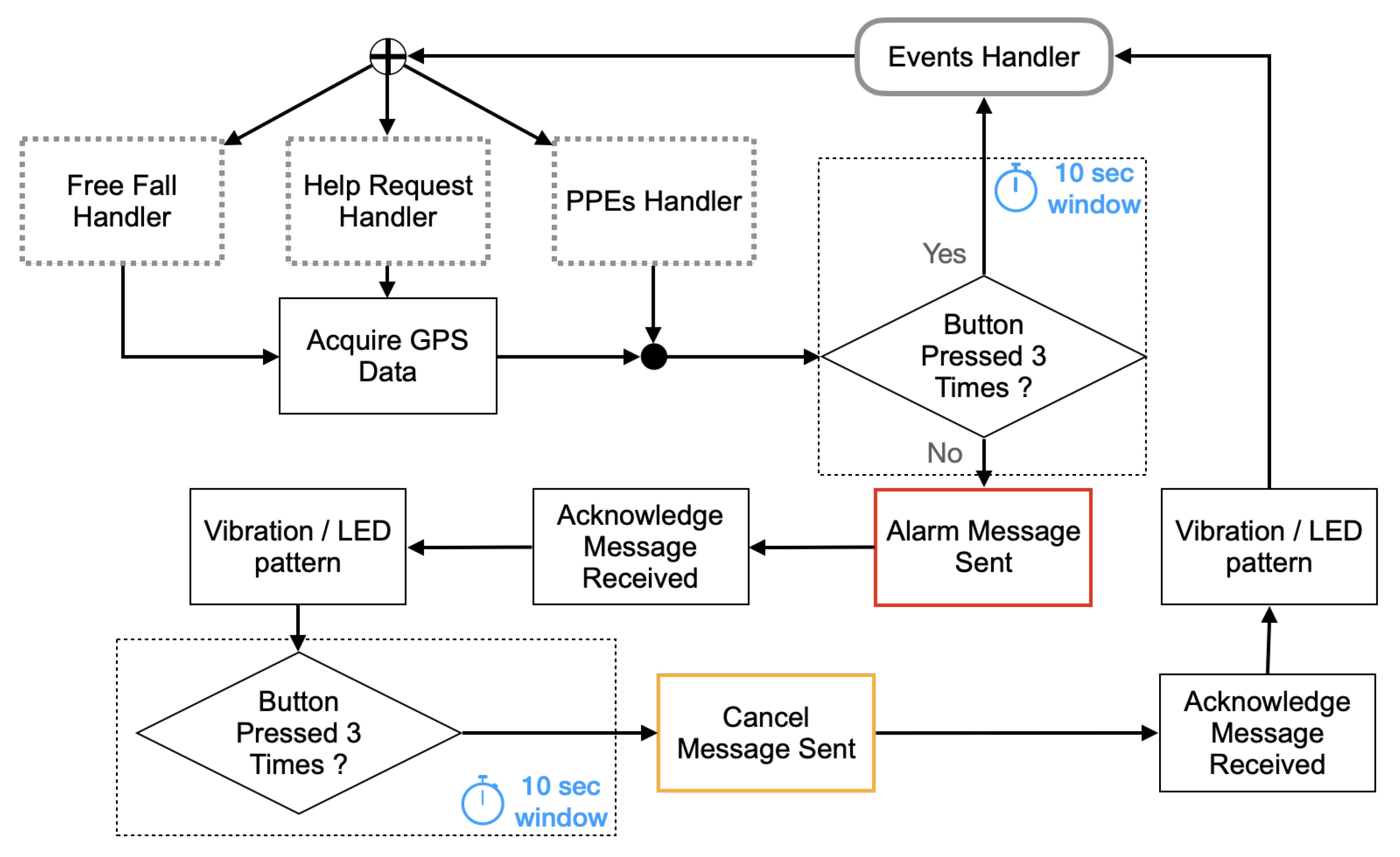
- Verifying that workers effectively wear the helmet, gloves, and protective footwear to prevent accidents, and alerting the safety professionals if these conditions are not met;
- Alerting the rescuers as soon as the sensor detects a human fall or a worker deliberately calls for help, informing rescuers of the victim’s position for a fast response.
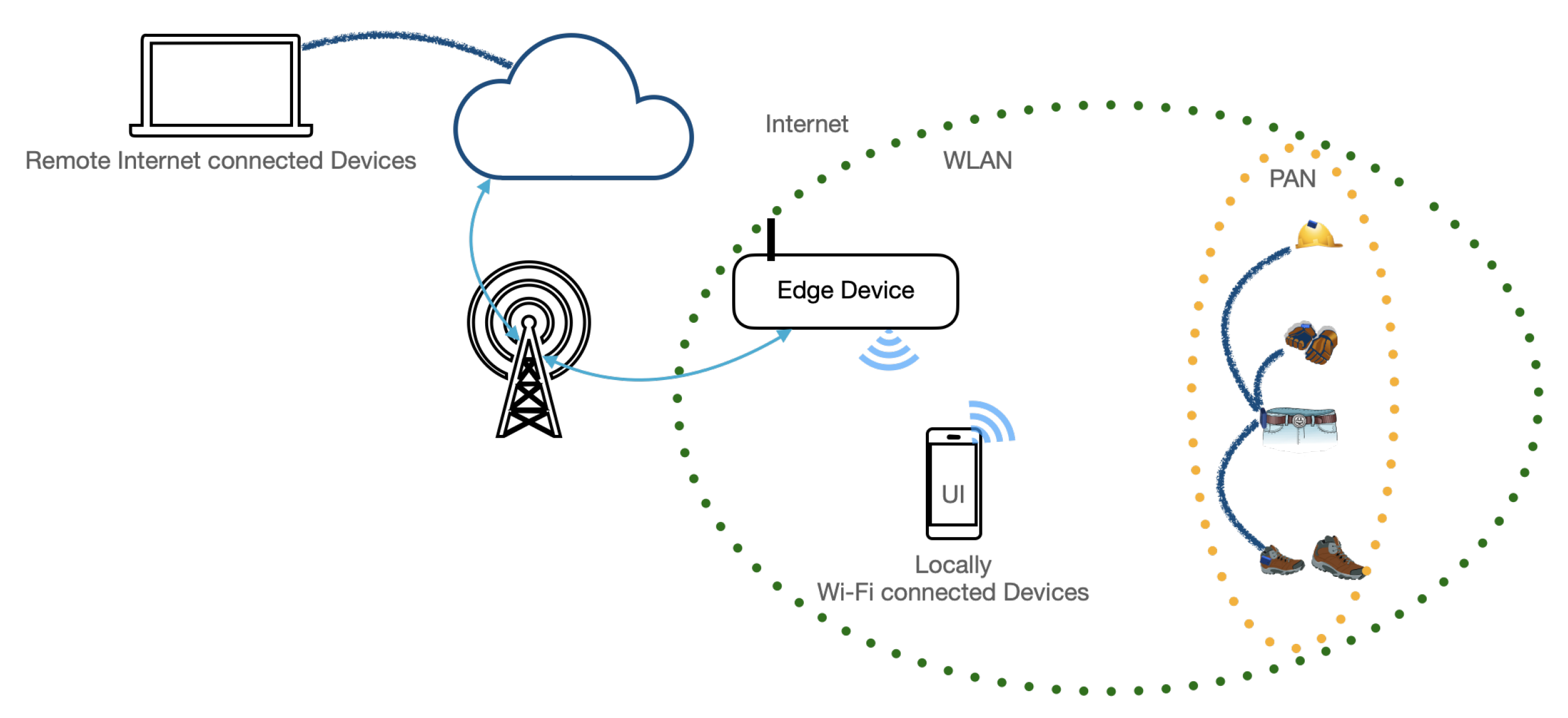
4.1. The Underlying Architecture
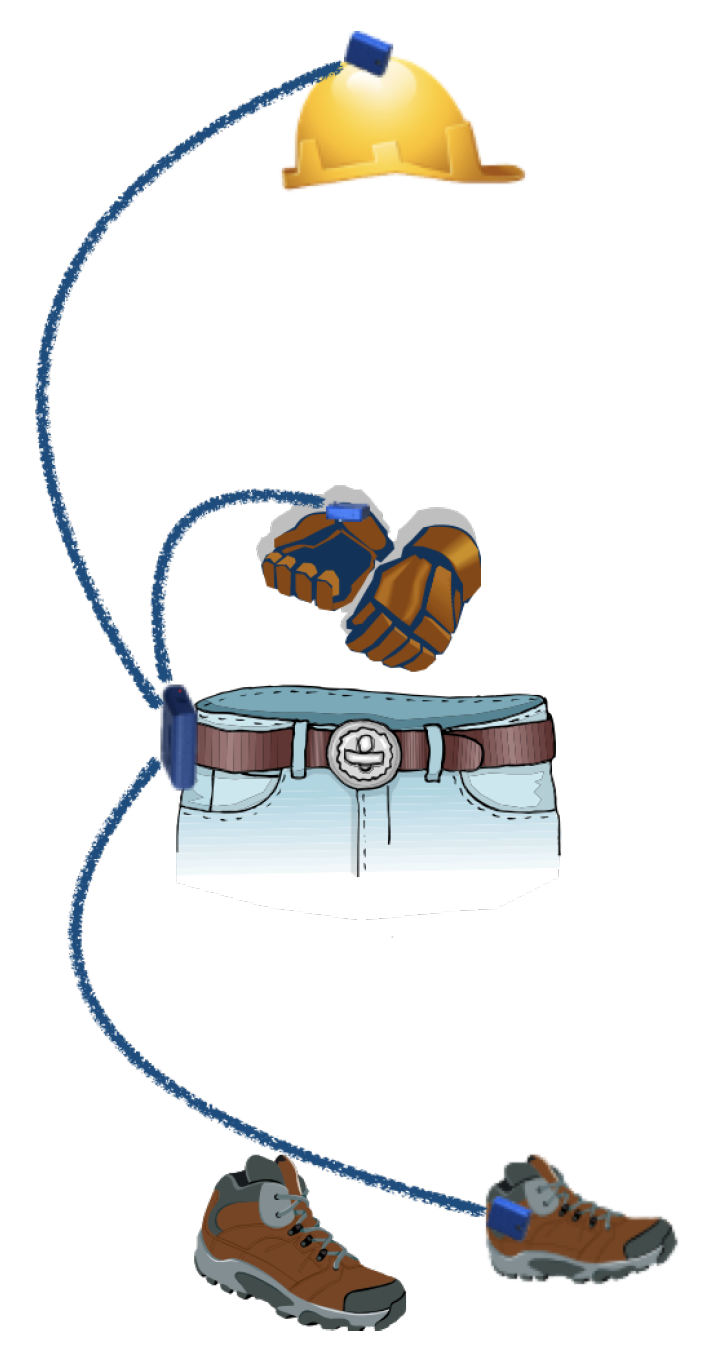
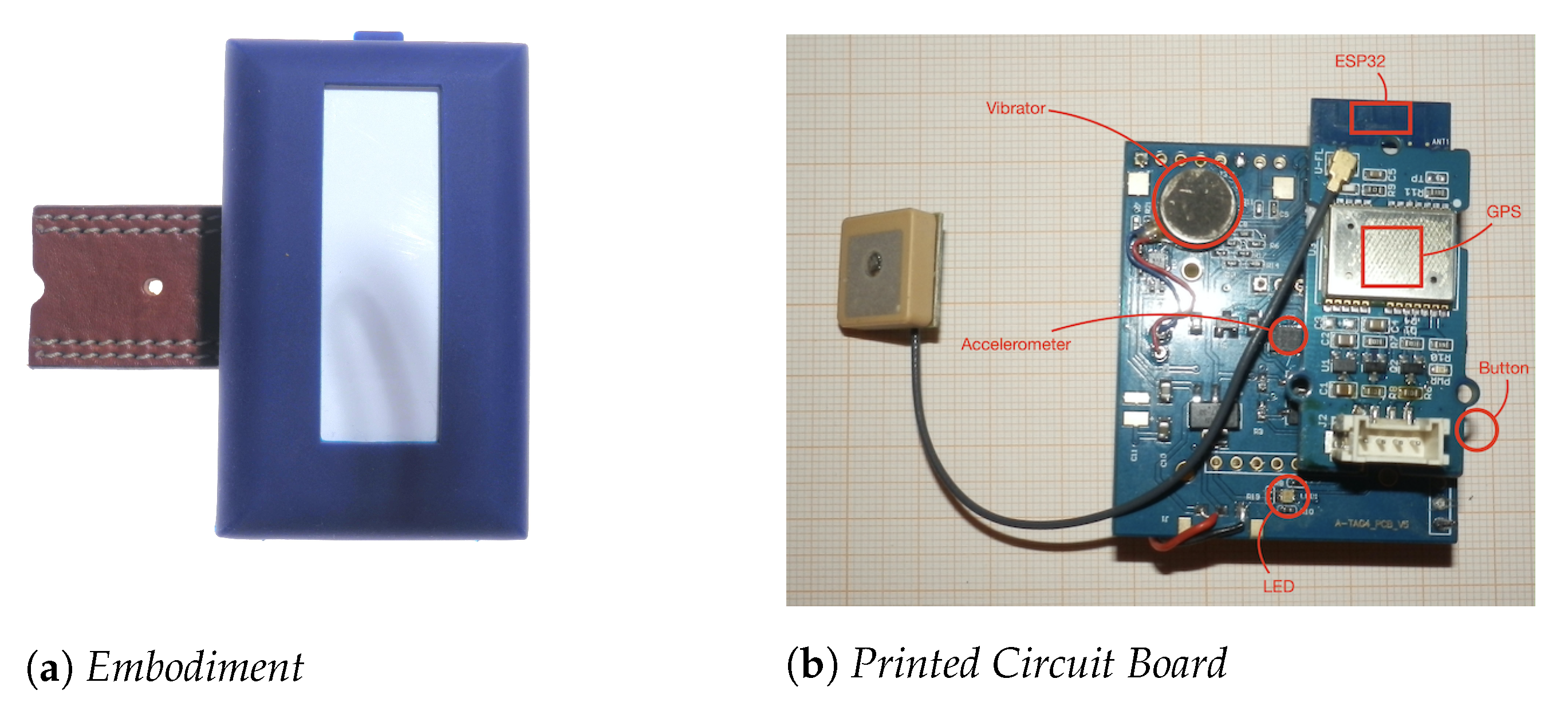
4.2. The Hardware Components
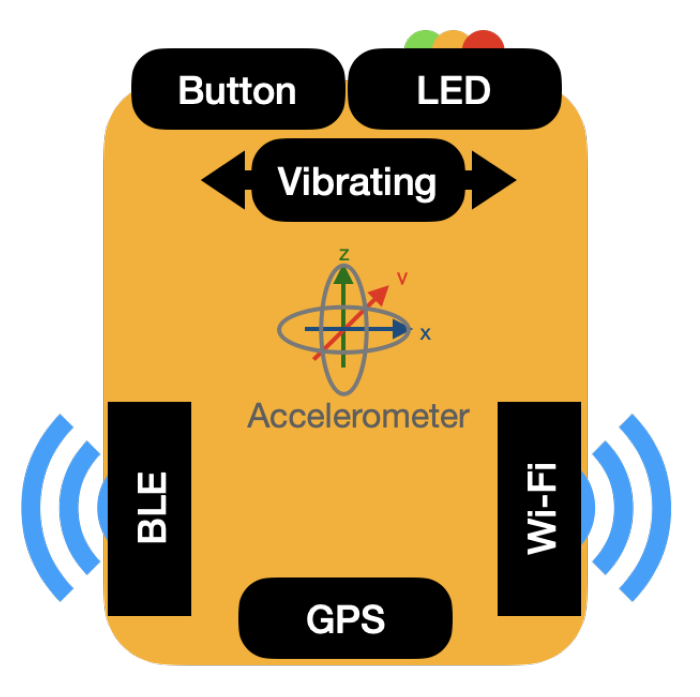
4.2.1. Small Embedded Devices
4.2.2. Belt-Devices
4.2.3. The Edge-Device
4.3. Networking
4.4. The Software
4.4.1. Communication between Small-Devices and Belt-Device
4.4.2. Communication between Belt-Devices and Edge-Device
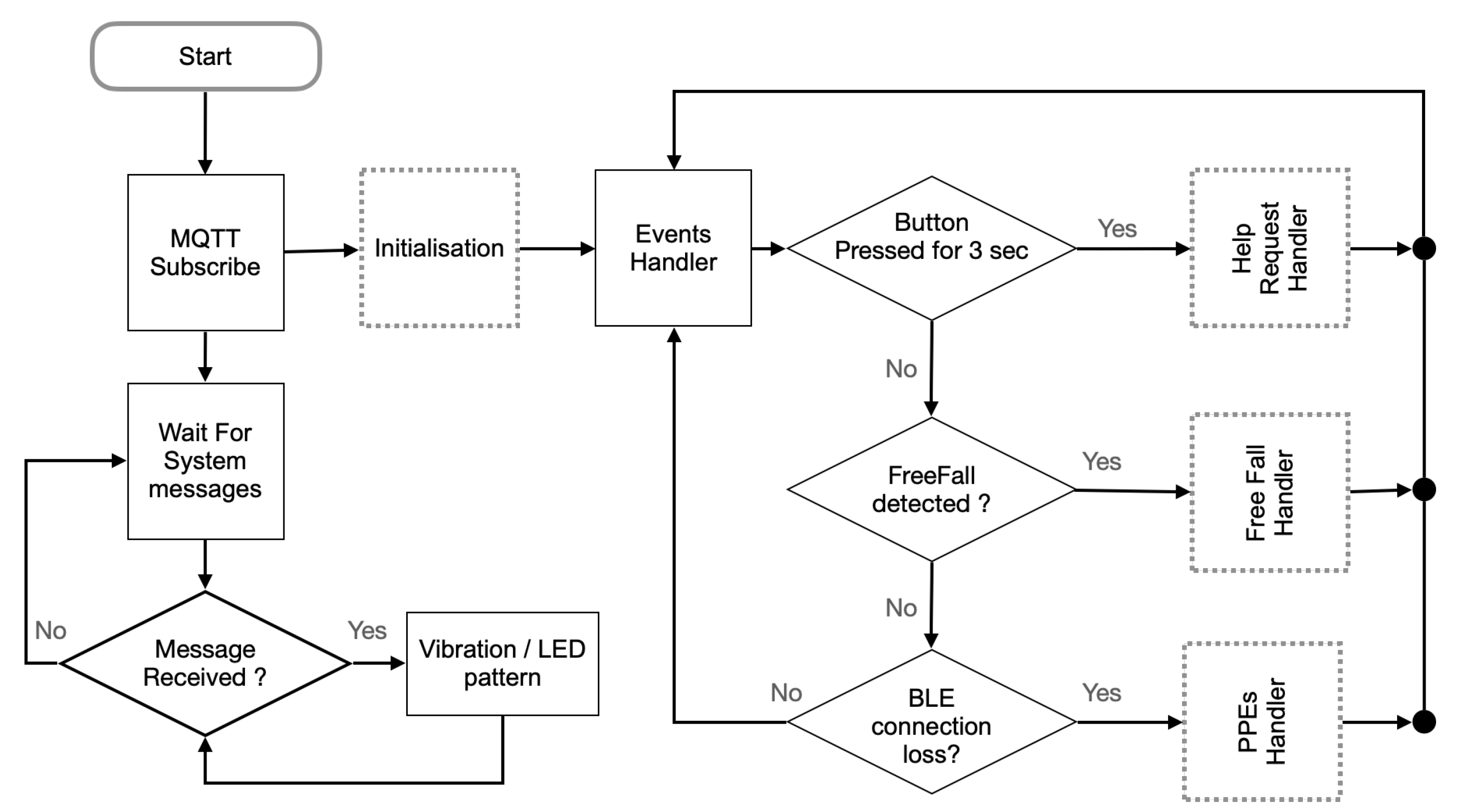
4.4.3. The Firmware
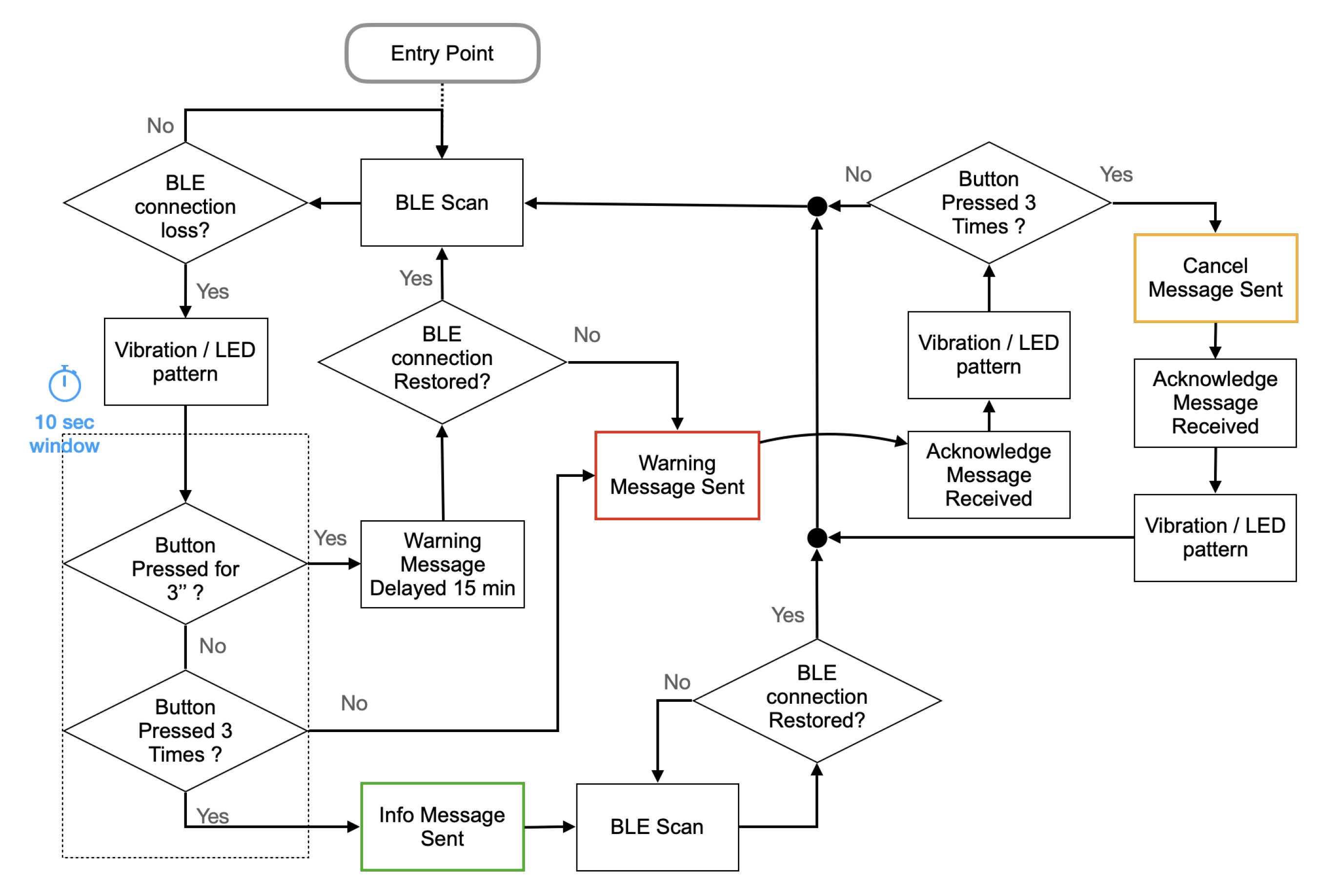
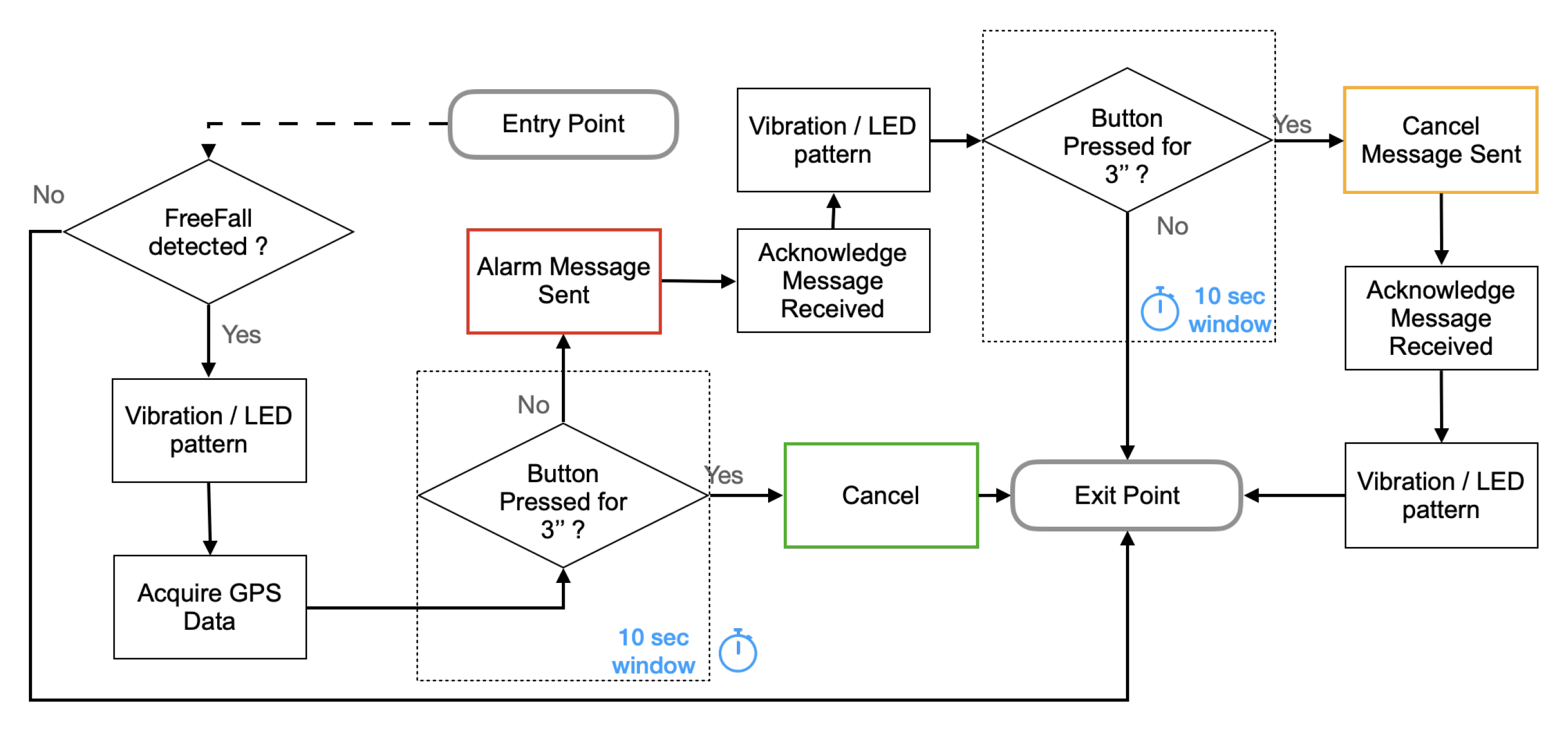
- To call for help and rescue the worker can press the button of the Belt-Device. When the Button Press Event is detected, the firmware verifies that the button is kept pressed for at least three seconds before publishing an Emergency message to the Edge-Device. This precaution prevents the raising of alarms due to involuntary temporary button press.
- To cancel a false alarm the worker can press the button of the Belt-Device after receiving from the Edge-Device the acknowledgment that the previously published alarm message has been received. The acknowledgment is communicated to the worker by actuating the vibrating device of the Belt-Device for three seconds. If the worker presses the Belt-Device button within ten seconds, a new message from the Belt-Device to the Edge-Device will abort the Emergency condition (Figure 14).
- Time: 235317.000 is 23:53 and 17.000 s in Greenwich Mean Time.
- Longitude: 4003.9040 N is latitude in degrees.decimal minutes, North.
- Latitude: 10512.5792 W is longitude in degrees.decimal minutes, West.
- Number of satellites seen: 08.
- Altitude: 1577 m.
4.4.4. The Web Application
4.4.5. Microservices
4.4.6. Security Essentials
- At Network level, the data between Belt-Devices and Edge-Device is exchanged on a local Wi-Fi area network. Thus, all the Wi-Fi security protocols are used to prevent the man in the middle attack. The connection with the Cloud resource, if applied, can occur through a VPN connection for additional security, when required.
- At Transport level, TLS/SSL is used for encryption. This method ensures that data cannot be read during transmission and provides client certificate authentication to verify the identity of both parties.
- At Application Level, the MQTT protocol provides client identification and username/password credentials to authenticate devices.
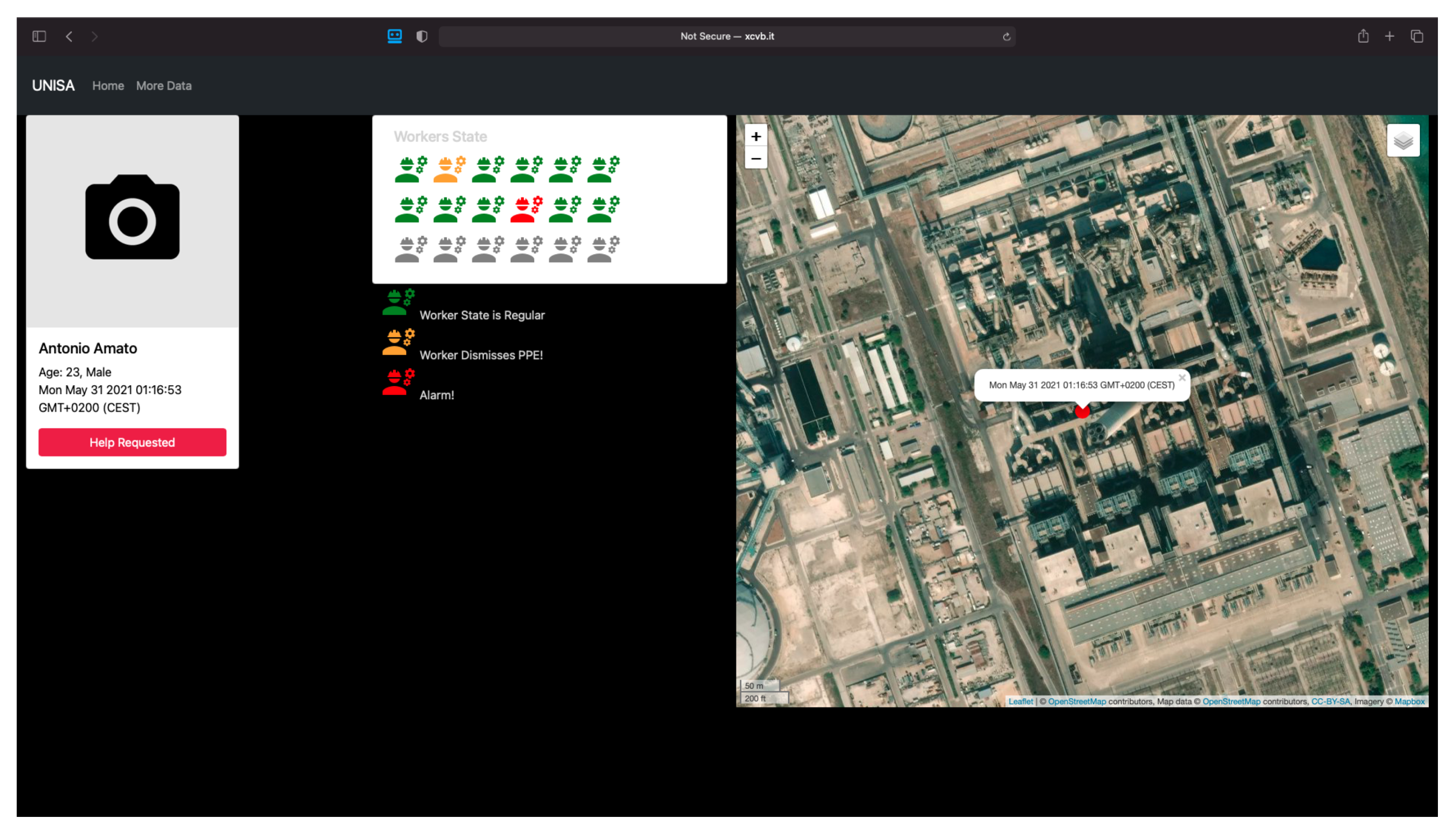
5. Running the Monitoring System
6. Discussion and Conclusions
- it verifies the continuous use of smart PPE during the work shift;
- it automatically detects an accidental human fall and calls the rescue without the intervention of the injured person;
- it accelerates the rescue when an accident occurs or a help request is performed.
- The solution is complete and addresses all the primary requirements, especially crucial for Lone Workers, as the localization, the verification of continuous use of PPE, and the possibility to be in contact with remote workers to seek help.
- The solution is based on the Fog-Computing architecture, offering autonomy from the unreliable and costly Internet connection for all the essential features.
- The solution is simple to deploy, even at large and temporary work sites. It has reduced recurring maintenance costs and guarantees the workers’ privacy while having little impact on the usual activities.
6.1. In-Lab Test Conclusions
6.2. Distinctive Technical Features
6.2.1. Sensors Scalability
6.2.2. Low-Cost Solution
- the electronic components, which are readily available on the shelf, thus making the costs of the electronics part of smart PPE affordable and the cost of the Edge-Device negligible;
- the installation costs, which could be limited to some additional Wi-Fi expander installation for the large work sites;
- the low recurring costs for maintenance and ownership, which consist of battery changes of the Small-Devices, limited to once every few years, due to BLE technology.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| ANS | Alert Notification Services of BLE protocol |
| BLE | Bluetooth Low Energy |
| EEC | European Economic Community |
| Fog-Computing | A specific architecture of Edge-Computing |
| GPIO | General Purpose Input/Output Ports |
| GPS | Global Positioning System |
| HTTP | Hypertext Transfer Protocol |
| HTTPS | Hypertext Transfer Protocol Secure |
| IoT | Internet of Things |
| LabGIS | Laboratory of Geographic Information Systems (University of Salerno) |
| LAMP | Linux, Apache, MySql, PHP |
| LAN | Local Area Network |
| LED | Light-emitting diode |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| OASIS | Organization for the Advancement of Structured Information Standards |
| OSH | European Occupational Health and Safety |
| PAN | Personal Area Network |
| PPE | Personal Protective Equipment. AKA helmets, gloves, shoes |
| QoS | Quality of Service |
| RFID | Radio-frequency Identification |
| Smart PPE | PPE with electronics |
| SMS | Short Message Service |
| SSL | Secure Sockets Layer |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security Protocol |
| TTL | A serial signaling standard based on a transistor–transistor logic interface |
| WAN | Wide Area Network |
| Wi-Fi | A family of wireless network protocols, based on the IEEE 802.11 |
| WLAN | Wireless Local Area Network |
Appendix A. Description of the In-Lab Tests
Appendix A.1. Materials for the Tests
- One Access Point (AP) TP-Link TL-MR3040.
- One Belt-Device prototype.
- Five Small-Devices to embed on two PPEs.

Appendix A.2. Evaluation of the Communication Capacity
Appendix A.2.1. Methods
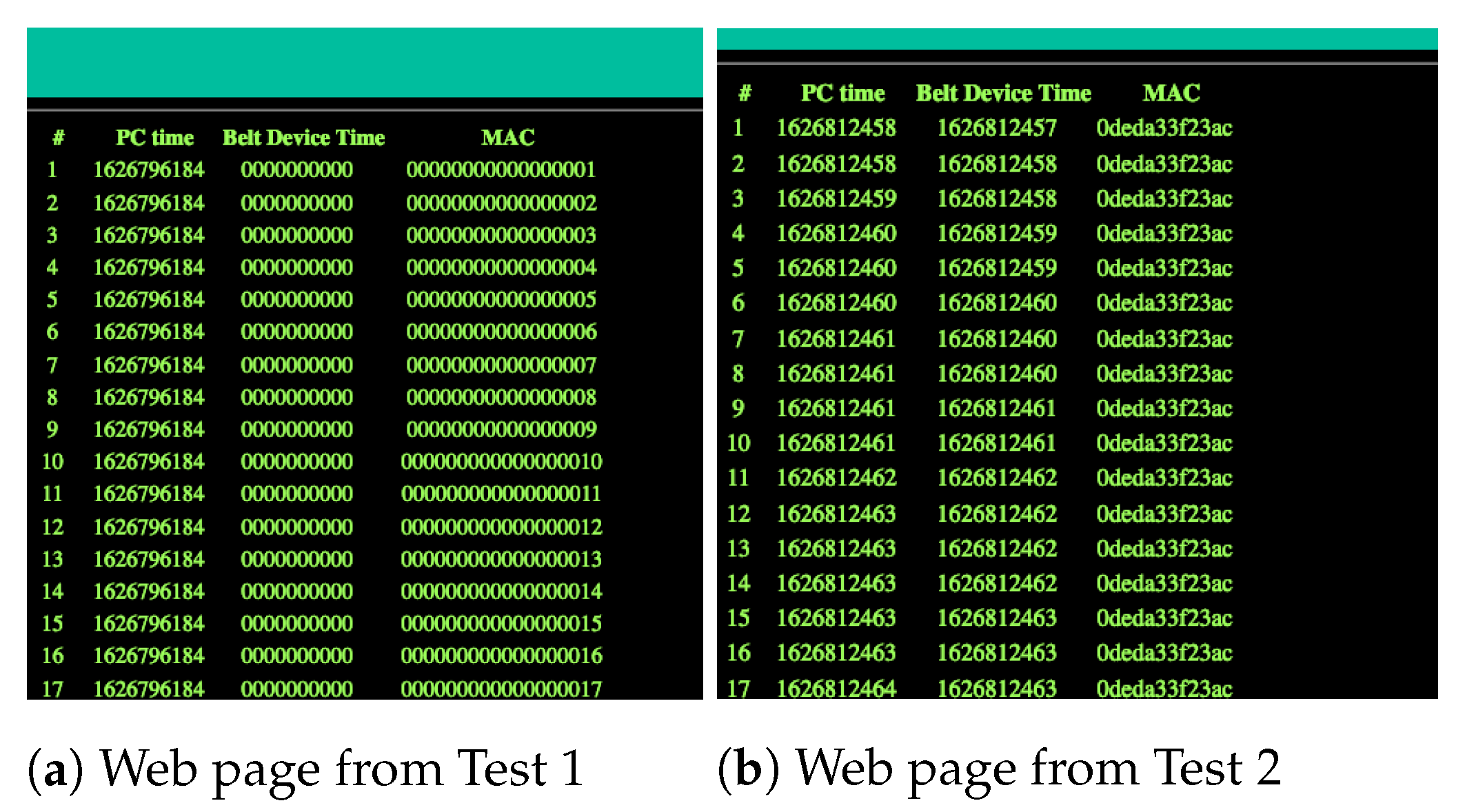
Appendix A.2.2. Conclusions
Appendix A.3. Stress Tests on BLE Proximity Detection
Appendix A.3.1. Methods
Appendix A.3.2. Conclusions

References
- European Union’s Occupational Safety and Health. OSH in General. Available online: https://oshwiki.eu/wiki/OSH_in_general#Costs_of_work_accidents_and_occupational_diseases (accessed on 14 December 2020).
- European Agency for Safety and Healt at Work. Directive 89/656/EEC-Use of Personal Protective Equipment. Available online: https://osha.europa.eu/en/legislation/directives/4 (accessed on 14 December 2020).
- Kimberly-Clark Professional. Alarming Number of Workers Fail to Wear Required Protective Equipment. Available online: https://investor.kimberly-clark.com/news-releases/news-release-details/alarming-number-workers-fail-wear-required-protective-equipment (accessed on 14 December 2020).
- European Agency for Safety and Health at Work. Smart Personal Protective Equipment: Intelligent Protection for the Future. Available online: https://osha.europa.eu/en/publications/smart-personal-protective-equipment-intelligent-protection-future/view (accessed on 25 May 2021).
- Shabina, S. Smart Helmet Using RF and WSN Technology for Underground Mines Safety. In Proceedings of the 2014 International Conference on Intelligent Computing Applications, Coimbatore, India, 6–7 March 2014; pp. 305–309. [Google Scholar] [CrossRef]
- Kanan, R.; Elhassan, O.; Bensalem, R.; Husein, A. A wireless safety detection sensor system. In Proceedings of the 2016 IEEE SENSORS, Orlando, FL, USA, 30 October–3 November 2016; pp. 1–3. [Google Scholar] [CrossRef]
- Li, H. Research on safety monitoring system of workers in dangerous operation area of port. In Proceedings of the 2017 4th International Conference on Transportation Information and Safety (ICTIS), Alberta, Canada, 8–10 August 2017; pp. 400–408. [Google Scholar] [CrossRef]
- Cho, C.; Park, J. An Embedded Sensory System for Worker Safety: Prototype Development and Evaluation. Sensors 2018, 18, 1200. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Jeong, M.; Lee, H.; Bae, M.; Shin, D.; Lim, S.; Lee, K.B. Development and Application of the Smart Helmet for Disaster and Safety. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 17–19 October 2018; pp. 1084–1089. [Google Scholar] [CrossRef]
- Faramondi, L.; Bragatto, P.; Fioravanti, C.; Gnoni, M.G.; Guarino, S.; Setola, R. A Wearable Platform to Identify Workers Unsafety Situations. In Proceedings of the 2019 II Workshop on Metrology for Industry 4.0 and IoT (MetroInd4.0 IoT), Naples, Italy, 4–6 June 2019; pp. 339–343. [Google Scholar] [CrossRef]
- Wu, F.; Wu, T.; Yuce, M.R. Design and Implementation of a Wearable Sensor Network System for IoT-Connected Safety and Health Applications. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 87–90. [Google Scholar] [CrossRef]
- Luo, W.; Wang, Q. Hardhat-Wearing Detection with Cloud-Edge Collaboration in Power Internet-of-Things. In Proceedings of the 2019 4th International Conference on Mechanical, Control and Computer Engineering (ICMCCE), Hohhot, China, 24–26 October 2019; pp. 681–6813. [Google Scholar] [CrossRef]
- Long, X.; Cui, W.; Zheng, Z. Safety Helmet Wearing Detection Based On Deep Learning. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Article and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 2495–2499. [Google Scholar] [CrossRef]
- Ravikiran, M.; Sen, S. Improving Industrial Safety Gear Detection through Re-ID conditioned Detector. In Proceedings of the 2019 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), Washington, DC, USA, 15–17 October 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Mehata, K.M.; Shankar, S.K.; Karthikeyan, N.; Nandhinee, K.; Hedwig, P.R. IoT Based Safety and Health Monitoring for Construction Workers. In Proceedings of the 2019 1st International Conference on Innovations in Information and Communication Technology (ICIICT), Chennai, India, 25–26 April 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Park, M.; Park, S.; Song, M.; Park, S. IoT-based Safety Recognition Service for Construction Site. In Proceedings of the 2019 Eleventh International Conference on Ubiquitous and Future Networks (ICUFN), Zagreb, Croatia, 2–5 July 2019; pp. 738–741. [Google Scholar] [CrossRef]
- Jayasree, V.; Kumari, M.N. IOT Based Smart Helmet for Construction Workers. In Proceedings of the 2020 7th International Conference on Smart Structures and Systems (ICSSS), Chennai, India, 23–24 July 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Battistoni, P.; Di Gregorio, M.; Giordano, D.; Sebillo, M.; Tortora, G.; Vitiello, G. Wearable Interfaces and Advanced Sensors to Enhance Firefighters Safety in Forest Fires. In Proceedings of the International Conference on Advanced Visual Interfaces, AVI ’20, Salerno, Italy, 28 September–2 October 2020; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Int. Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Cisco. Cisco Annual Internet Report (2018–2023) White Paper. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 16 December 2020).
- Yousefpour, A.; Ishigaki, G.; Jue, J.P. Fog Computing: Towards Minimizing Delay in the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Edge Computing (EDGE), Honolulu, HI, USA, 25–30 June 2017; pp. 17–24. [Google Scholar]
- Iorga, M.; Feldman, L.; Barton, R.; Martin, M.J.; Goren, N.S.; Mahmoudi, C. Fog Computing Conceptual Model. NIST Pubs 500–325, National Istitute of Standards and Techology. 2018; Techreport. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.500-325.pdf (accessed on 31 May 2021).
- Battistoni, P.; Sebillo, M.; Vitiello, G. Computation Offloading with MQTT Protocol on a Fog-Mist Computing Framework; Number 11874 in Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2019. [Google Scholar]
- Battistoni, P.; Sebillo, M.; Vitiello, G. Experimenting with a Fog-Computing Architecture for Indoor Navigation. In Proceedings of the 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC), Rome, Italy, 10–13 June 2019; pp. 161–165. [Google Scholar] [CrossRef]
- Banks, A.; Briggs, E.; Borgendale, K.; Gupta, R. MQTT Version 5.0. Available online: https://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.html (accessed on 25 November 2020).
- Jacobsen, H.A. Publish/Subscribe. In Encyclopedia of Database Systems; Springer: New York, NY, USA, 2009; pp. 2208–2211. [Google Scholar]
- Light, R.A. Mosquitto: Server and client implementation of the MQTT protocol. J. Open Source Softw. 2017, 2, 265. [Google Scholar] [CrossRef]
- Nordic Semiconductor. The nRF52 Series Multiprotocol SoCs. Available online: https://www.nordicsemi.com/Products/Low-power-short-range-wireless/Bluetooth-5 (accessed on 30 November 2020).
- Espressif. A Feature-Rich MCU with Integrated Wi-Fi and Bluetooth. Available online: https://www.espressif.com/en/products/socs/esp32 (accessed on 30 November 2020).
- Analog Devices. 3-Axis Digital Accelerometer. Available online: https://www.analog.com/media/en/technical-documentation/data-sheets/ADXL345.pdf (accessed on 30 November 2020).
- Quectel. GNSS Module with Chip Antenna. Available online: https://www.quectel.com/product/l96.htm (accessed on 30 November 2020).
- Hillar, G.C. MQTT Essentials: A Lightweight IoT Protocol: The Preferred IoT Publish-Subscribe Lightweight Messaging Protocol; Packt Publishing: Birmingham, UK, 2017. [Google Scholar]
- Internet Engineering Task Force. The WebSocket Protocol. Available online: https://tools.ietf.org/html/rfc6455 (accessed on 30 November 2020).
- Lee, S.; Kim, H.; Hong, D.k.; Ju, H. Correlation analysis of MQTT loss and delay according to QoS level. In Proceedings of the The International Conference on Information Networking 2013 (ICOIN), Bangkok, Thailand, 28–30 January 2013; pp. 714–717. [Google Scholar] [CrossRef]
- Bluetooth SIG. Core Specification. Available online: https://www.bluetooth.com/specifications/bluetooth-core-specification/ (accessed on 24 November 2020).
- Bluetooth SIG. Alert Notification Service. Available online: https://www.bluetooth.com/specifications/gatt/ (accessed on 24 November 2020).
- Jia, N. Detecting Human Falls with a 3-Axis Digital Accelerometer. Available online: https://www.analog.com/en/analog-dialogue/articles/detecting-falls-3-axis-digital-accelerometer.html (accessed on 10 December 2020).
- Gakstatter, E. What Exactly Is GPS NMEA Data? Available online: https://www.gpsworld.com/what-exactly-is-gps-nmea-data/ (accessed on 2 December 2020).
- U.S. Department of Labor. Suspension Trauma/Orthostatic Intolerance. Available online: https://www.osha.gov/sites/default/files/publications/shib032404.pdf (accessed on 23 June 2021).
- Overview-NodeMCU Documentation. Available online: https://nodemcu.readthedocs.io/en/dev-esp32/ (accessed on 18 July 2021).
- ESP8266 Non-OS SDK API References. Available online: https://www.espressif.com/sites/default/files/documentation/2c-esp8266_non_os_sdk_api_reference_en.pdf (accessed on 18 July 2021).
- ESPlorer. Available online: https://esp8266.ru/esplorer/ (accessed on 18 July 2021).






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Battistoni, P.; Sebillo, M.; Vitiello, G. An IoT-Based Mobile System for Safety Monitoring of Lone Workers. IoT 2021, 2, 476-497. https://doi.org/10.3390/iot2030024
Battistoni P, Sebillo M, Vitiello G. An IoT-Based Mobile System for Safety Monitoring of Lone Workers. IoT. 2021; 2(3):476-497. https://doi.org/10.3390/iot2030024
Chicago/Turabian StyleBattistoni, Pietro, Monica Sebillo, and Giuliana Vitiello. 2021. "An IoT-Based Mobile System for Safety Monitoring of Lone Workers" IoT 2, no. 3: 476-497. https://doi.org/10.3390/iot2030024
APA StyleBattistoni, P., Sebillo, M., & Vitiello, G. (2021). An IoT-Based Mobile System for Safety Monitoring of Lone Workers. IoT, 2(3), 476-497. https://doi.org/10.3390/iot2030024







