1. Introduction
This paper addresses a need for autonomous decision making that involves two IoT devices or mobile devices with equal importance and equal rights of way. For example, there are two cars in a remote “stop” traffic junction and both cars have equal right of way but interferes with each other’s path, meaning they cannot negotiate the intersection without colliding unless one car favors the other. The proposed technique provides a fair decision-making process that involves both parties and a given protocol that can be included as standard in IoT devices or mobile devices. In addition, there are applications on mobile phones that will benefit from this decision-making process, for example, two mobile phones or tablets interacting in game mode without access to a server. Parents traveling long distances by car with children experience the need for interactive games without access to a network. Computer games running locally on devices can interact as peer-to-peer and make gaming choices using the protocols developed in this paper. The paper is structured as discussions on the methodology, decision-making protocol, and test results based on an 1D simulation.
Before discussing prior technical publications, the scope of this work is defined, as the field of IoT is big and there are many different aspects of communication that are being addressed by active research communities. This work can be applied to IoT, gaming, device-to-device communication, and mobile robots or cars. The conceptual research was developed in the context of autonomous vehicles but it has wider applicability. Clemson University has an iCar facility [
1] and there have been numerous publications on autonomous vehicles from that center. Therefore, examples used in the paper are illustrated with cars, but it is worth emphasizing that the protocols proposed here are suited for any participating smart devices that are self-allocating without an external decision maker. For an autonomous car, there are many decisions to be made by the car, such as speed, direction, safety considerations, etc., and those may not involve another car. However, when there are multiple cars involved, a central computing facility or a server could make the decision for them. For example, a busy intersection in a smart city will most likely have a central controller interacting with the vehicles, directing them and sequencing them based on some optimization algorithms. The present work excludes the central server and proposes techniques that can solve two-agent scarce resource allocation with built-in, democratic fairness. Note that car manufacturers have cheated before with algorithms; therefore, a robust data exchange and recording of those data exchanges are needed to document the contractual agreements for future legal analysis. It is essential that, if needed, the history of the data exchange can be reliably retrieved—most likely with blockchain-like, reliable record keeping. Note that it is blockchain-like and not exactly blockchain because that technology is designed for financial transactions and tends to be slow. Moreover, financial blockchain requires numerous participants to maintain the integrity of the records. In this work, the data exchange is between two parties, and third parties are not available to verify. This type of situation is recorded with light blockchain and several teams are working on this technology in different parts of the world [
2]. The scope of light record keeping is large and deserves deeper discussion in articles written on that topic. It is acknowledged that light but reliable and tamperproof record keeping will be required to mitigate legal issues in completely autonomous situations.
2. Related Work
The topic of decision making and negotiation is vast and key aspects on these are discussed by Thompson et al. [
3] and Dorazio and Johnson [
4]. The current paper makes an effort to resolve smaller decision making without strategy or big impacts, mostly depending on chance or probability. We face these small decisions in our daily lives, such as sharing a door passage, making a left turn in a two-way street, getting food in a crowded buffet, etc. In a machine or robotic environment, the proposed technique is more statistics based than emotion based, such as courtesy and rudeness/humbleness, which machines inherently lack.
There are many technical publications with centralized optimization. For example, Dollar et al. [
5] discussed the centralized optimization of energy efficiency for automated vehicles. They observed that centralized optimization was superior to decentralized schemes. Their proposed technique prioritized vehicles by their sensitivity to inter-vehicle constraints that relaxed constraints on vehicles with more difficult traffic situations. However, there are situations where implementation of the centralized control methodology is not practical, and decentralized control becomes necessary, which is more cost effective to implement. The present paper developed a collaborative algorithm that can be used for multi-lane guidance with local lower computational effort.
Car movement with local decision making in crowded spaces can arguably be compared to a swarm analogy. Birds follow simple rules to maintain swarm formations [
6] without a defined destination or track limitations. Lalena [
6] observed that complex swarm movement could be captured by three simple rules: separation—steer to avoid crowding birds; alignment—steer towards the average direction of birds; and cohesion—steer to move toward the average location of birds. Each bird also had a detection and separation range. The detection range is the distance at which birds can detect predators, obstacles, food, and other birds. The separation range is the distance at which a flock of birds may split to avoid predator, obstacle, or bird. Unfortunately, car movements are more restricted and involve heavier dynamics, fuel usage, passenger comfort, etc. These create constraints that are difficult to overcome with biomimicking. However, there are situations where we can benefit by observing how social behavior is developed to negotiate the identification and negotiation patterns based on those identifications.
Yoskioka et al. [
7] used an intelligent system based on autonomous guidance and precision-docking techniques of a public bus at a precise parking location at a bus stop. The operational improvements were the following: reduction in passenger boarding and deboarding time; increase in accessibility for users with disabilities, children and the elderly; possibility of eliminating access ramps for wheelchairs; possibility of operation on straight routes, enabling the implementation of exclusive routes in urban centers; and cost reduction in corridor construction. The following were estimated: road width reduction from 3.50 to 2.90 m; time reduction in the bus approach and exit at the stops; increase in passenger comfort based on the standardization of the vehicle’s path along the route; and importantly, driver’s stress reduction. The bus driver can concentrate on acceleration and braking control better with automatic guidance. There are complex signal and management rule processing involved, but this bus automation does not involve multiple buses competing for the same bus stop; they are perhaps friendly to other buses, as they are most likely serviced by the same bus company. However, if there is competition for bus stop access, the proposed technique will resolve access conflicts without bias. In large cities with millions of daily commuters, there is competition among buses and taxis to get passengers and disorganized risky maneuvers can take place in busy streets. An organized, smart parking solution is discussed by Lin et al. [
8]. The base assumption was that drivers could find satisfying parking spaces with smart parking services: essentially that the environment is friendly with enough resources to spare. It did not address if there was less parking available than the number of cars looking for them and how to allocate limited resources without bias to all eligible candidates.
Any decision protocol needs to have archival data exchange to detect fraud and foul play. Car companies are there for themselves and cannot be trusted to have friendly behavior with a “let others go first” attitude. CBS News published a history of cheating by car companies [
9]. Intentionally altering the outcome to pass inspections or providing better results than reality is called the use of defeat devices. The latest, most well-known and well-recorded event was with Volkswagen, who manipulated the diesel emission results in its built-in computer. Earlier GM also did fix emission-related problems and paid fines. Ford had a sophisticated electronic control strategy to up-predict the fuel economy in Econoline vans. Honda tried to suppress the engine malfunction indicator. So, car companies can put unfriendly code in their cars’ computers and may produce biased results if left to have a decision-making process involving themselves. A fair decision-making protocol is needed, and a few options are suggested in this paper. Vehicle manufacturers are not honest all the time and one cannot depend on them to be honest. Barrett et al. [
10] studied the impact of Volkswagen emission control on the regulations imposed by the U.S. VW has admitted the inclusion of defeat devices and was not caught for many years. The social cost of nearly USD 450 million was estimated and that impact may be bigger and more difficult to measure in software-based greedy behavior if applied by the manufacturer to please its customer base while unfairly depriving competitor vehicles from the fair allocation of limited resources. The objective of this discussion is not finger pointing, but to identify the fact that activities done by software are opaque and unfair practices were adopted to benefit certain players in the past. The proposed protocol built in this article takes input from involved parties and then makes a fair decision with proper transaction of records for future conflict resolution. Cheating is an adaptive process, much like a virus morphing itself to defeat the existing immune system. It is not possible to guarantee a cheat-proof solution but this technique provides recorded participation by both parties and makes both responsible for the decision taken, thus reducing conflict and oppressive arguments.
Recent autonomous vehicle research discusses game-theory based optimization on traffic flow, such as Bui and Jung [
11] who optimized traffic flow at multiple intersections. They proposed intersection controllers as smart agents to improve traffic flow. They used communication between intersection controller and individual car as the optimization framework, where the intersection controller makes the decision as to who will go first and at what rate. This is like a centralized computing framework and decision making is left to someone outside as a neutral third party. The focus of that study was on the different shapes of intersections. As a next step, the authors used the distributed traffic management approach, where automobiles decided for themselves to navigate through the intersections without a controller. The use of Social Internet of Vehicles was considered to enable smart transportation. IoT is evolving into Social Internet of Things (SIoT) and a subset of that is Social Internet of Vehicles (SIoV) [
12]. There exists a Vehicular ad hoc network (VANET) that is adding value to smart transportation technology. Later, Rath et al. [
13] presented an overview of social networking. They observed that the role of financial outcome of the subnetworks under a social group is very significant and at the same time, cooperation among members of the social network is equally important. Unfortunately, financial reward comes with dishonest attempts to win it unfairly. Mazar and Ariely [
14] discussed dishonesty that goes beyond the standard economic considerations of probability and value of external payoffs. They established that dishonesty is present in everyday life. They observed the existence of an internal reward mechanism for dishonesty; moreover, they observed that internal and external rewards were additive. They proposed that when the role of internal rewards is better understood, both preventions and punishments of dishonesty can be made more effective and efficient. In an IoT environment, the internal reward may be hard to achieve because that involves conscience, but with proper record keeping, external punishment for dishonesty can be achieved.
Distributed conflict resolution for connected autonomous vehicles is essential. Liu et al. [
15] proposed a methodology in which participating cars grab time slots to pass through zones of conflict. They showed improved traffic flow with larger throughput without a central traffic manager. Theoretically, it was a parallel algorithm to obtain a feasible solution of large-scale, combinatorial optimization in real time. All vehicles were requested to broadcast their arrival times in the conflict zone and the assumption was that participants were honest. They did not include the capacity difference of cars such as muscle cars with faster acceleration, providing a faster time to occupy than others. It was not clear how a tie would be handled. Liu et al. assumed a priority score and weighting based on emergency vehicles such as fire trucks. However, if both cars have the same priority, how to mitigate or pick one over the other was not discussed. In other notable studies, Elhenawy et al. [
16] used game-theory-based traffic control in a connected vehicle environment. They used cooperative adaptive cruise control at unmonitored intersections. However, it assumed vehicles interacting with a central agent that made decisions for them and vehicles obeyed that central system. Lin and Jabari [
17] introduced a free market mechanism to set the intersection priority. One could pay for faster movement in their model. However, none of these studies addressed what happens in a tie situation or the use of scarce resources.
Figure 1 (based on [
18]) shows an application that can use Device to Device (D2D) communication, where the proposed decision making is useful and local. An analysis of probabilistic collision assessment was performed by Laugier et al. [
19]. There are hundreds of situations that require two-device decisions to navigate through apparently simple events, but they become complicated when autonomous techniques are applied. Biomimicking on social interactions are not a perfect solution as was illustrated by the situation of the two-car standoff in a crowded city for a single parking spot. It was in the news, as the two cars (drivers) held their spots without a decision for more than an hour [
20]. More discussion on D2D are provided by Pawar and Trivedi [
21]. Prabhu [
22] discussed the blockchain implementation of decentralized decision making in which the RPSH protocol is applicable. Some of the D2D scenarios discussed in these references are emergency services, smart vehicles, ubiquitous computing, mobile phone interactions, medical services, gaming, automated delivery, autonomous drones, security and comfort.
The identification of IoT devices is essential to establish communication or to develop actionable items as is discussed by Ruiz et al. [
23]. They used multi-modal sensing-like body movements to tag an ID on the IoT device. That ID technique could link a device to a person without human intervention. The proposed methodology utilized ambient detectors in the smart sensing environment to tag the IoT device with the user or wearer of the device. The movement of the human was matched with the device response to link the two together. The system proposed was named IDIoT, indicating ID of an IoT device. The challenges that were overcame included absence of line of sight, multiple devices being used by the same user, and orientation sensing from 2D images. The motion parameters that were used are as follows: type (linear vs. circular), period (baseline of 15 bpm), amplitude (50 cm for linear and 90 degrees for circular), and duration (default of 10 s). This technique proved to be twice as effective than comparable technologies of motion and vision matching.
The pairing of IoT devices is important to exchange data and information. Han et al. [
24] proposed mounting onboard sensors to IoT equipment to pair them based on local context. The proposed model used event timing from IoT devices to make event fingerprints to be matched with a variety of neighboring IoT devices. The intention for the removal or minimization of human involvement in the pairing of devices helped context-based pairing to emerge. The on-board sensors were utilized to compare instantaneous signals to identify them to be in the same locale or domain. It became more difficult to pair when the mounted sensors were different from device to device. It is challenging to capture sensor modalities to identify contextual information, and hopefully future devices will agree on the types of sensors to help pairing with each other.
Trust and security are important for these devices, and this is an active area of research. It will not be possible to cover much of that domain, as there are too many publications and aspects to discuss. A few studies are included for the completeness of the discussion and to illustrate the need for the protocols used in this paper. An improved protocol for bluetooth was discussed by Singelee and Preneel [
25]. The authors recognized several security flaws in the bluetooth protocol and a new initiation mechanism for the key agreement protocol was proposed. Bluetooth devices create a unit key that is unique for the device based on a random number and the bluetooth hardware address. At the start of an improved communication, another temporary key is generated as the initiation key. This initiation key is then shared by the two devices. Note that no unalterable coded message is passed between the parties as proposed in this current paper. An improved pairing protocol as suggested by Singelee and Preneel uses an anonymous mode without hardware addresses in the packet headers. This anonymous mode of operation is supposed to solve the known security problems with bluetooth communication. The proposed pairing protocol was claimed to be energy efficient and user friendly and used the security features based on the Diffie–Hellman elliptic curve.
Trust modes in ubiquitous computing was discussed by Krukow et al. [
26]. They suggested probability-based models, but did not provide any final recommendation. Ubiquitous computing, referred to as UbiComp, is challenging in connectivity, omnipresence, autonomous decision making, mobile applications, scalability and more. Krukow et al. reviewed existing techniques, such as Kullback–Leibler divergence, to measure the performance of algorithms. Their paper discussed testing and measurement techniques but did not provide any new algorithms to improve trust modes. A thesis on decentralized trust reasoning was developed by Abdul-Rahman [
27]. The study was made up of two parts. The first part of the work discussed properties and dynamics of social trust and its role in computer systems. The second part involved establishment of a framework for trust reasoning in distributed systems. Abdul-Rahman identified that trust involves a combination of cognitive and non-cognitive constructs. The trust could be categorized based on social order, technical competency, and fiduciary obligations [
28]. The message structure was recommended to have two message types: RRQ, recommendation request, and REC, recommendation itself. This protocol depends on advice from others whether to trust a given device or not. If there are only two devices, this is not going to work.
Kwiatkowska and Lahijanian [
29] argued social trust to be a major challenge for autonomous systems. They laid out the groundwork needed to understand the human–robot relationship in an autonomous system. Their work was financially supported and applicable to humans as an agent and autonomous machines as another agent. This RPSH paper is based on autonomous-to-autonomous decision making without human interference to build trust and make fair decisions. Liu et al. [
30] discussed privacy preserving raw data collection for IoT. They proposed a fog-assisted raw data collection protocol with three phases, namely, the setup phase, slot generation phase, and reward phase with data collection. Their proposed methodology unlinked the data from their contributor and the performance was estimated with 1000 IoT participants. In contrast, the current work is targeted for lean IoT devices such that no decision makers or voting system can be employed.
The use of external decision maker or monitor was addressed in several publications. Gentili and Mirchandani [
31] studied the optimal location of traffic flow measurement. The collection of data and usage may be useful for traffic management and control but it can be intrusive if used for decision making or for conflict resolution. Different types of sensors, such as measurement of speed, density, volumes, occupancy, turning ratios, vehicle identification, etc., were studied. Those were important for a bigger picture, but the small-scale decision making as discussed by this paper was excluded from their work. In another publication, multi agent predictive control was studied by Negenborn et al. [
32]. They identified the following items to be of interest to the community: automated controls; automating nested layers; automated subproblem assignment; fewer conditions for multi-agent convergence; and the asynchronous cooperation protocol. The current work can be classified as asynchronous protocol development for automated decision controls.
The use of gaming logic in decision making is not new. Arunachalam [
33] used the Rock-Paper-Scissors game-based scheme for the P2P mobile ad hoc network (MANET). MANETs are formed with the objective that users will collaborate with each other to locate resources, for sharing information, for multicasting, etc. Interestingly, this game-based protocol substantially decreased the network traffic thus increasing battery life with reduced energy usage, and search latency was minimized.
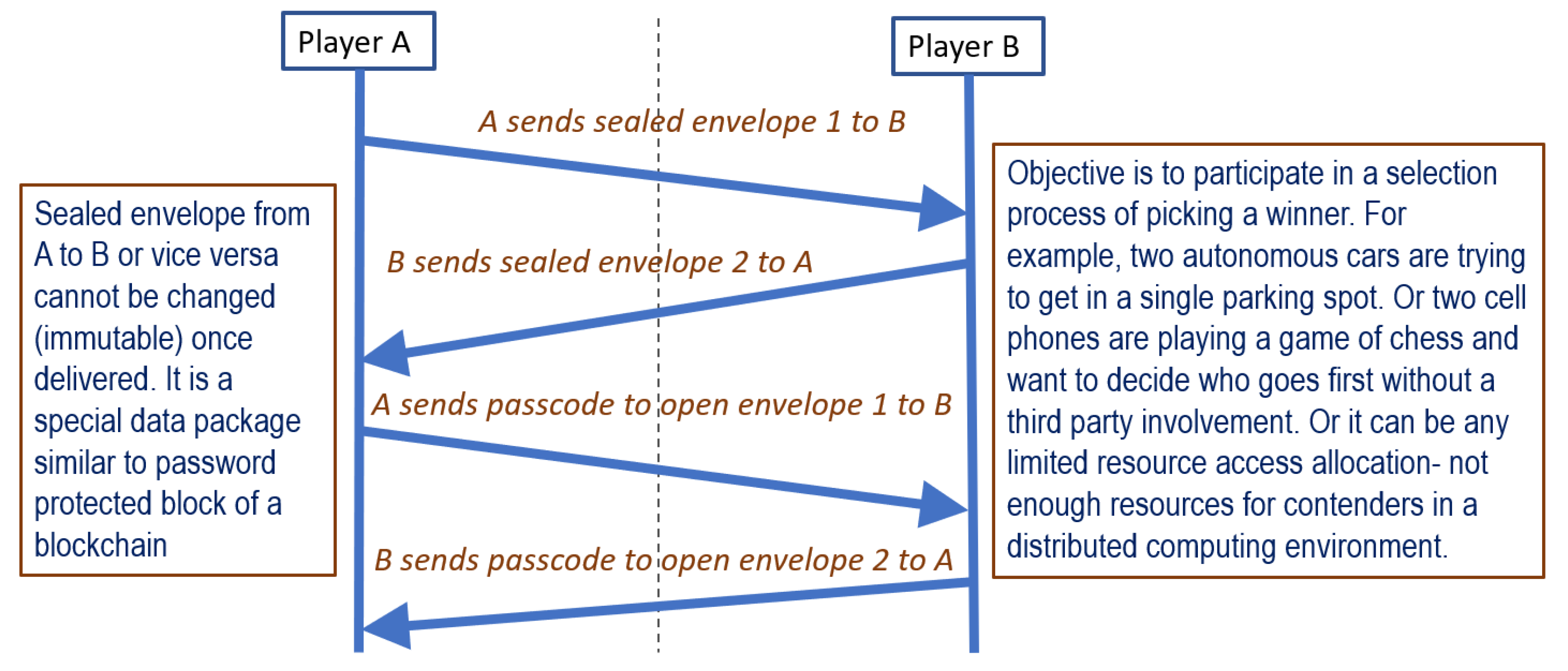
4. Decision-Making Protocol
After the sealed envelope technique is established between two players, there needs to be a protocol to decide on the winner where both players want to win. This win can be related to taking a parking space, yielding for a lane change, making a turn at an intersection, passing through a doorway, starting a move for a game, etc. Two protocols are compared in this article; the RPSH protocol showed clear advantage over the RPS protocol. The objective of using a decision-making protocol is that there is no need for a third-party decision maker and both players participate in decision making. Both players’ participation is crucial so that one player does not decide for the other. The most common, lean decision making can be resolved with a coin toss. This technique is familiar to most readers—a football game starts with a coin toss. There are two team captains present and the main referee tosses the coin as a neutral member. One of the team captains calls head or tail while the coin is in the air and a decision is made based on the toss outcome. There are several issues with implementing this in a digital, two-participant scenario. First, there is no third party or referee to be a neutral operator. Second, the coin toss process does not hang in the air for several seconds while the choice is being made. In digital decision making, the process is quick, the toss process is hidden, and there is plenty of opportunity for foul play. As a result, a conventional coin toss is not a viable solution. In one of the meetings, a graduate student suggested to let the two parties select an integer randomly from 1 to 10 and let the highest number picker win. This example clearly shows that the role of rogue player is overlooked by most researchers. The rogue player will pick the maximum number 10, bypassing the random selection and will win all the time. Hence a better technique is required to pick a winner randomly and fairly.
Another common protocol for such two-party decision making is Rock-Paper-Scissors (RPS). Even though it is a game played by children, this technique has been used in more serious decision-making schemes, such as in court and in starting a game [
22]. The winning protocol is that rock wins over scissors, scissors win over paper, and paper wins over rock. If both players select the same item, such as rock and rock, then it is a tie and the decision-making process needs to be repeated. So, a tie can be considered a waste of time and effort, and can be a significant influencer on the number of steps needed to resolve a complex system as illustrated in the results section.
A new technique proposed by this article is a modification of RPS as Rock-Paper-Scissors-Hammer (RPSH). The scheme is illustrated in
Figure 3. Player A can choose between 1 and 0, and Player B can also choose between 1 and 0. It is similar to flipping a coin, but both parties flip their own coin and then a decision is made by a predetermined logic. In RPS, each player gets to chose from three options, and RPSH reduces that to two options, similar to flipping a coin. A simple flipping coin actually needs a third party, who should be neutral and will select the winning choice before the flip. RPSH is suitable for two party involvement with the sealed envelope technique. For example, Player A selects heads or tails (1 or 0) and sends that to Player B, using sealed envelope data exchange. It is similar to assigning the winning option to Player A. Now Player B selects heads or tails (1 or 0), simulating the coin toss, and if the outcome matches Player A’s selection, A wins. So, essentially, RPSH can be considered a coin toss with two players without a third mediator. It is worth noting that RPSH does not add more data exchange, rather it is about how the exchanged data are processed. So, RPSH is not a four-step process, and instead, it can be considered that RPSH has two options (0 and 1) for each player and RPS has three (rock, paper, and scissors). However, the amount of data exchange is not different between the two protocols. RPS has tie situations and that increases the overall number of data exchanges as illustrated later in the results. The efficient implementation of the algorithm depends on the processor and system architecture. For the simulations, the decision-making process used Python-based matrix manipulations. However, the same logic could have been implemented with if-then-else ladder logic.