CO-TSM: A Flexible Model for Secure Embedded Device Ownership and Management
Abstract
Highlights
- CO-TSM enables decentralised application management across smart cards, embedded devices, HCE-TEE smartphones, IoT devices, and RFID-enabled supply chains.
- The model enhances security through continuous evaluation and remote attestation while empowering users with greater device control.
- CO-TSM can revolutionize secure embedded device management by addressing market fragmentation and interoperability challenges.
- Its adoption could lead to more flexible, scalable, and user-centric approaches in managing secure applications across industries.
Abstract
1. Introduction
2. Trusted Service Manager (TSM)
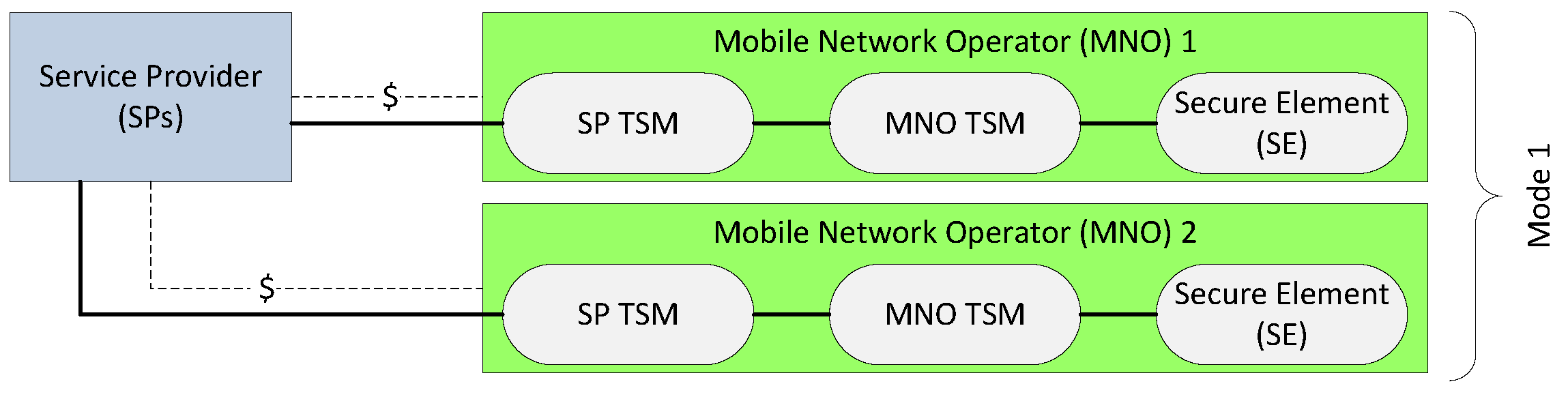
2.1. Overview of TSM Architecture
2.2. Summary of Key Points
3. Analysis of TSM-Based Deployment Models
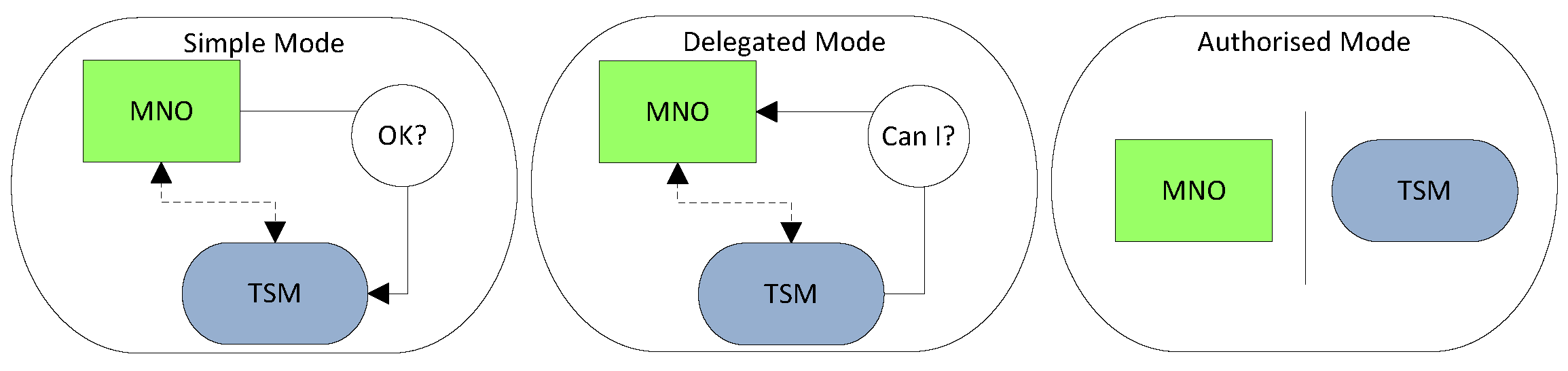
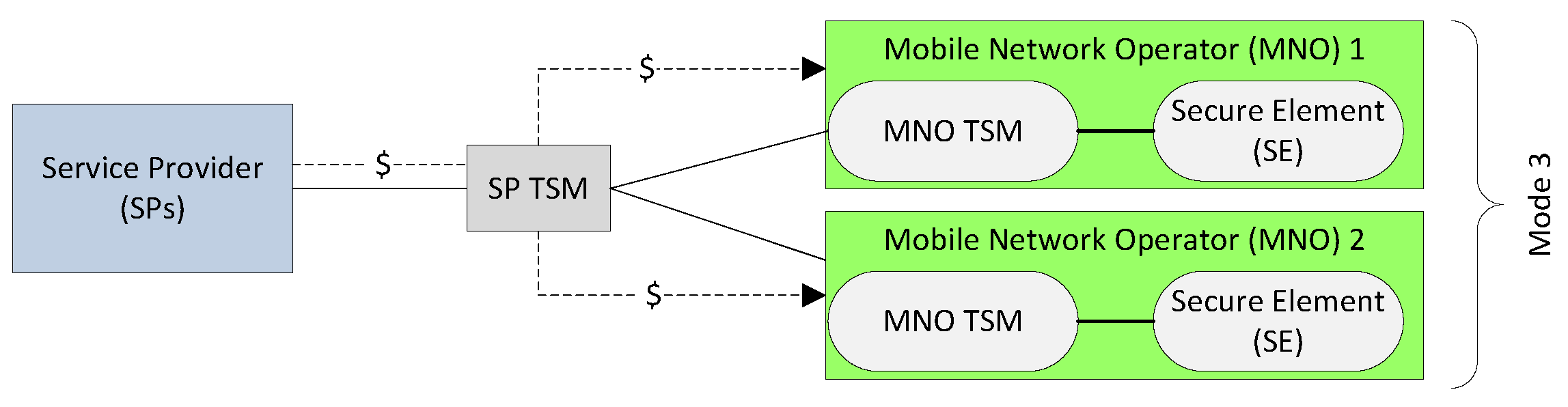
3.1. Traditional and Evolving TSM Models
3.2. Challenges and Limitations of TSM Models
3.3. Summary of Key Points
- Market Fragmentation: Traditional TSM models, with their centralised control structures, contribute to market fragmentation. This fragmentation limits consumer choice and forces service providers to engage in multiple partnerships to reach a broad audience, thereby restricting the overall interoperability and adoption of smart card technologies.
- Scalability Issues: As the number of connected devices and services continues to grow, the centralised nature of traditional TSM models poses significant scalability challenges. These bottlenecks hinder the deployment of new services and complicate the management of large-scale networks, making it difficult to meet the demands of modern, interconnected environments.
- Lack of Flexibility: Traditional TSM models often fail to accommodate the diverse needs of modern consumers and service providers. Their rigid structures can slow the deployment of innovative services and typically prioritise the needs of issuers and service providers over those of end-users, limiting consumer empowerment and control over their devices.
- Need for User-Centric Approaches: The limitations of traditional TSM models underscore the need for a more flexible and user-centric approach to smart card application management. Such an approach should empower consumers, enhance interoperability, and support the seamless integration of diverse services and devices.
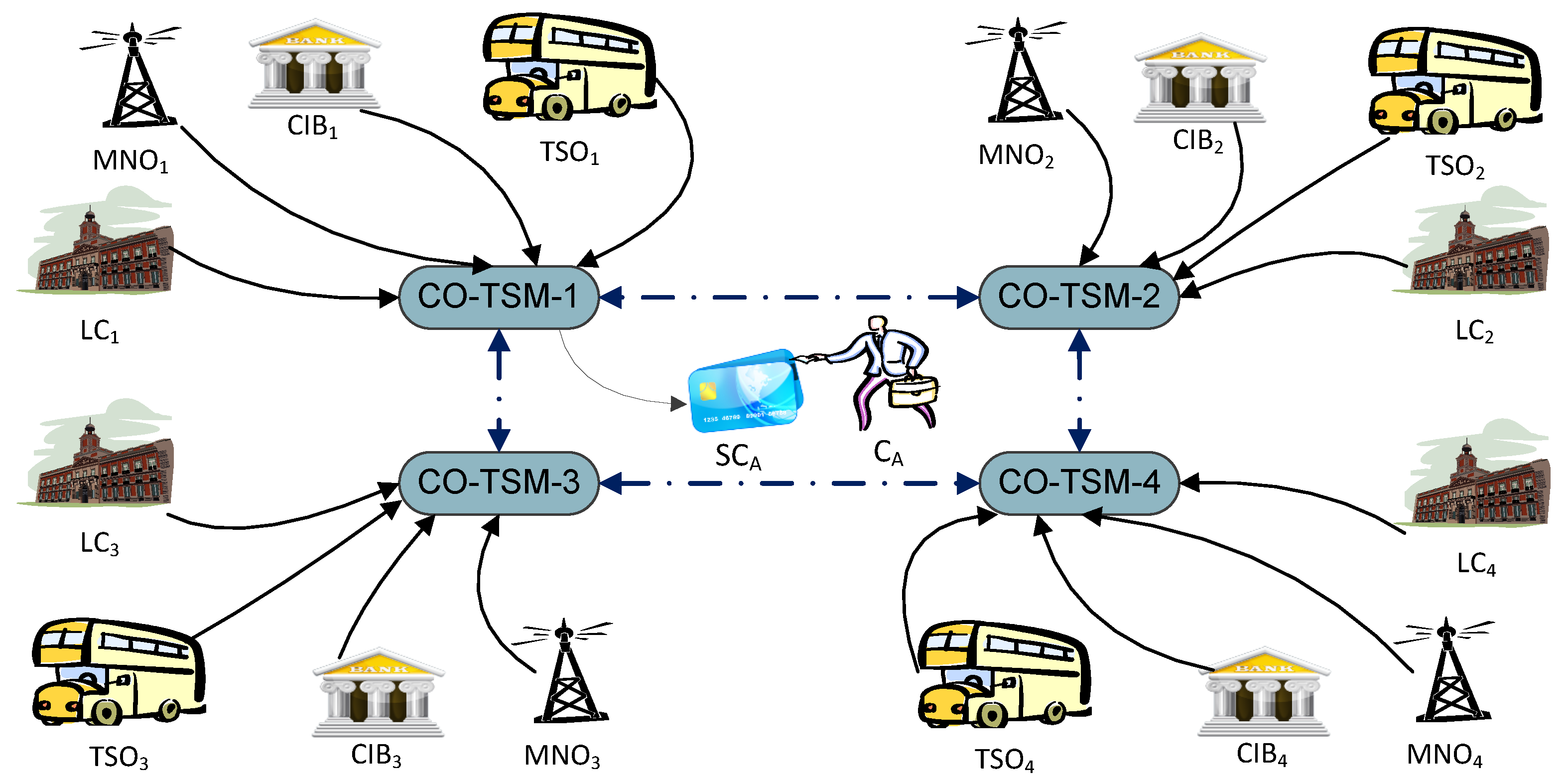
4. Consumer-Oriented Trusted Service Manager Model
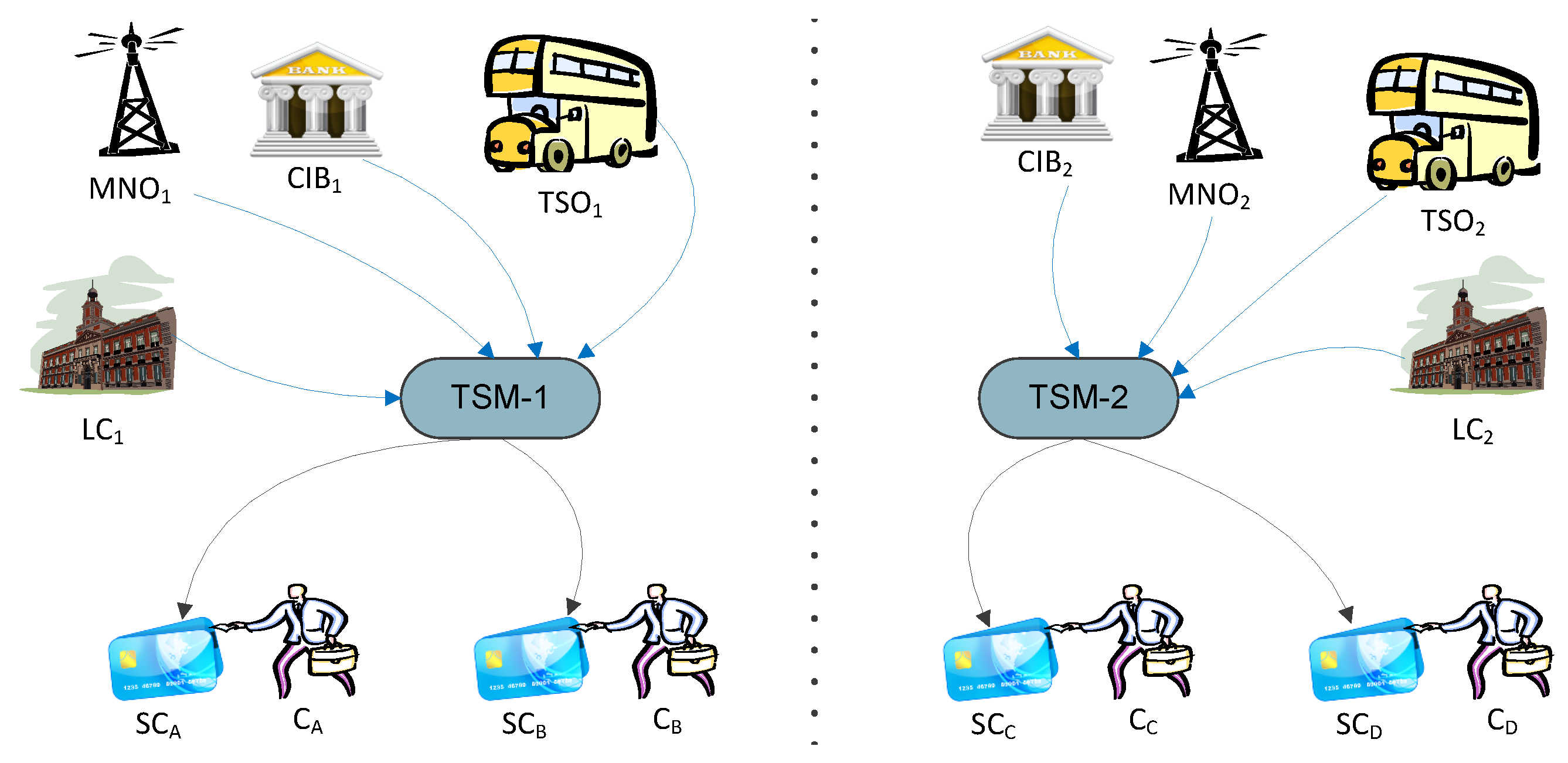
4.1. Architecture
- (a)
- The threat of new entrants
- (b)
- The threat of substitute products or services
- (c)
- Consumer power (culture)
- [F1]
- Management of relationships between card issuers, service providers (SPs), and users, acting as a neutral broker to protect each stakeholder’s interests.
- [F2]
- Serving as a security attestation and validation broker, ensuring that smart cards meet SP security requirements.
- [F3]
- Ensuring that applications do not compromise smart card integrity.
- [F4]
- Users’ freedom to install any application, regardless of the SP’s membership in any CO-TSM.
- [F5]
- Users’ ability to acquire their own smart card and delegate its management to a CO-TSM.
- [F6]
- Users’ privilege to choose and switch CO-TSMs, providing flexibility and control over their smart card management.
4.2. Deployment Challenges and Opportunities
- Ensuring smart card security and providing assurances to SPs without direct agreements.
- Establishing secure and trusted protocols for application downloads, including remote security attestation, validation, and fee processing.
- Enabling users to manage applications and fulfil their requests for installations and deletions.
4.3. Comparing ICOM- and UCOM-Based CO-TSM
4.4. Summary of Strengths and Weaknesses
5. Case Studies of CO-TSM Deployments
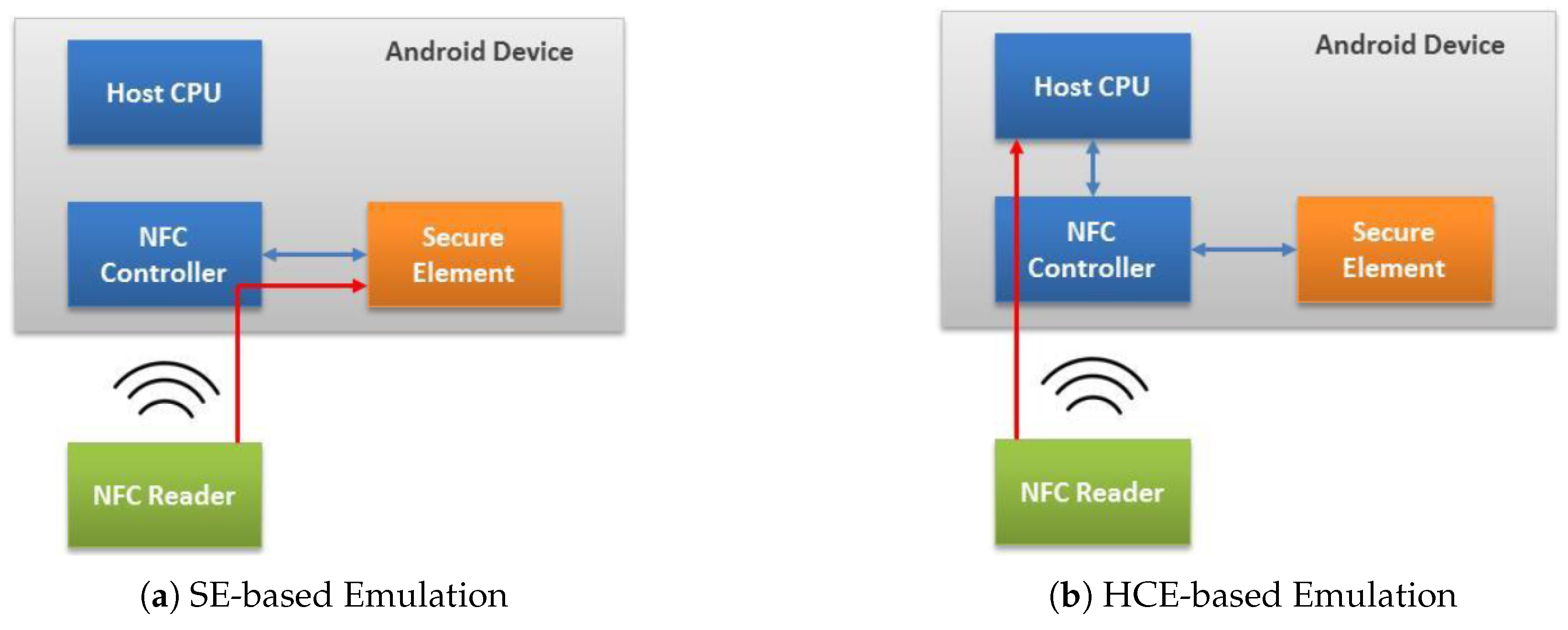
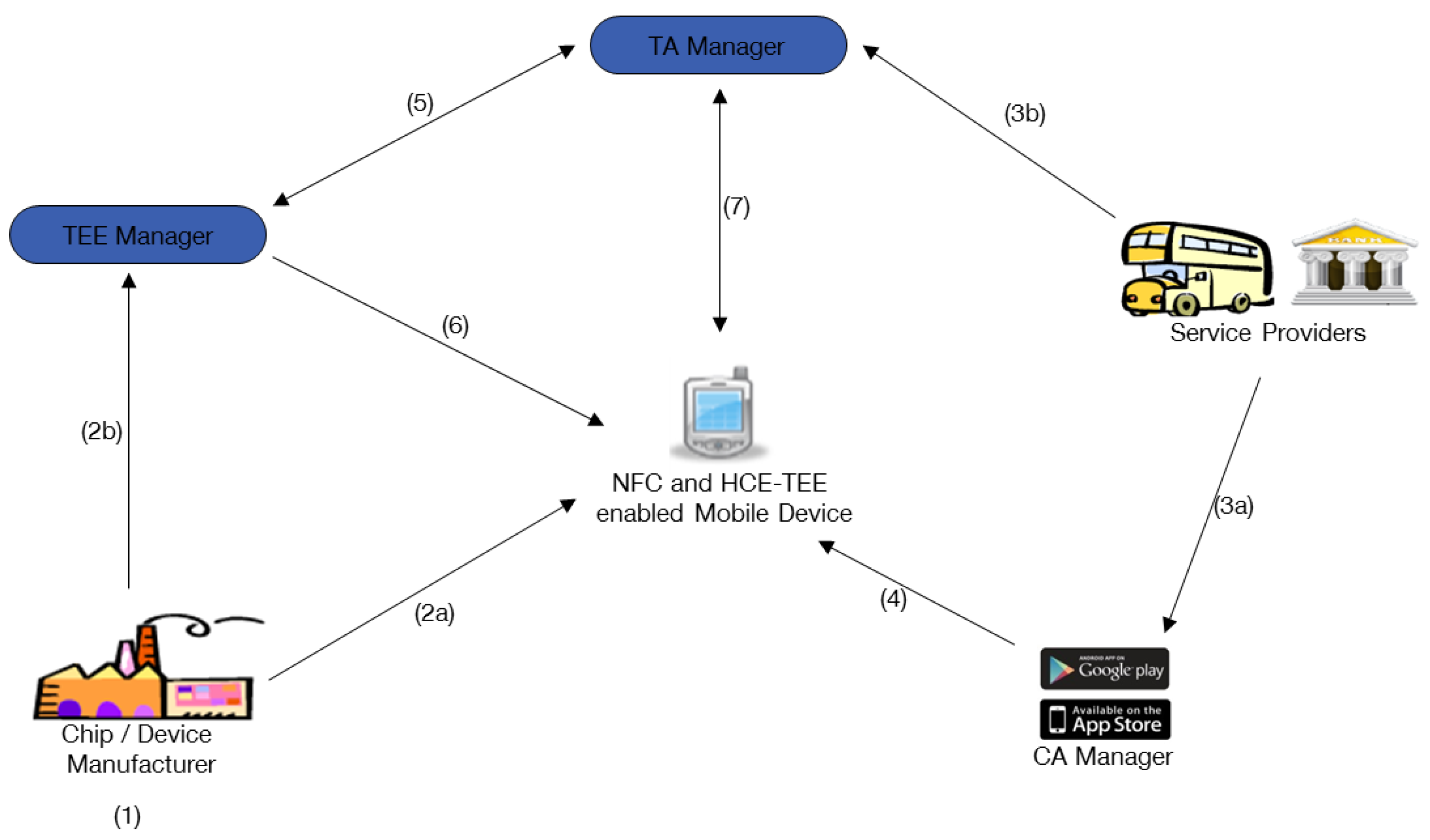
5.1. CO-TSM UCOM Based HCE-TEE Smart Phone Deployment
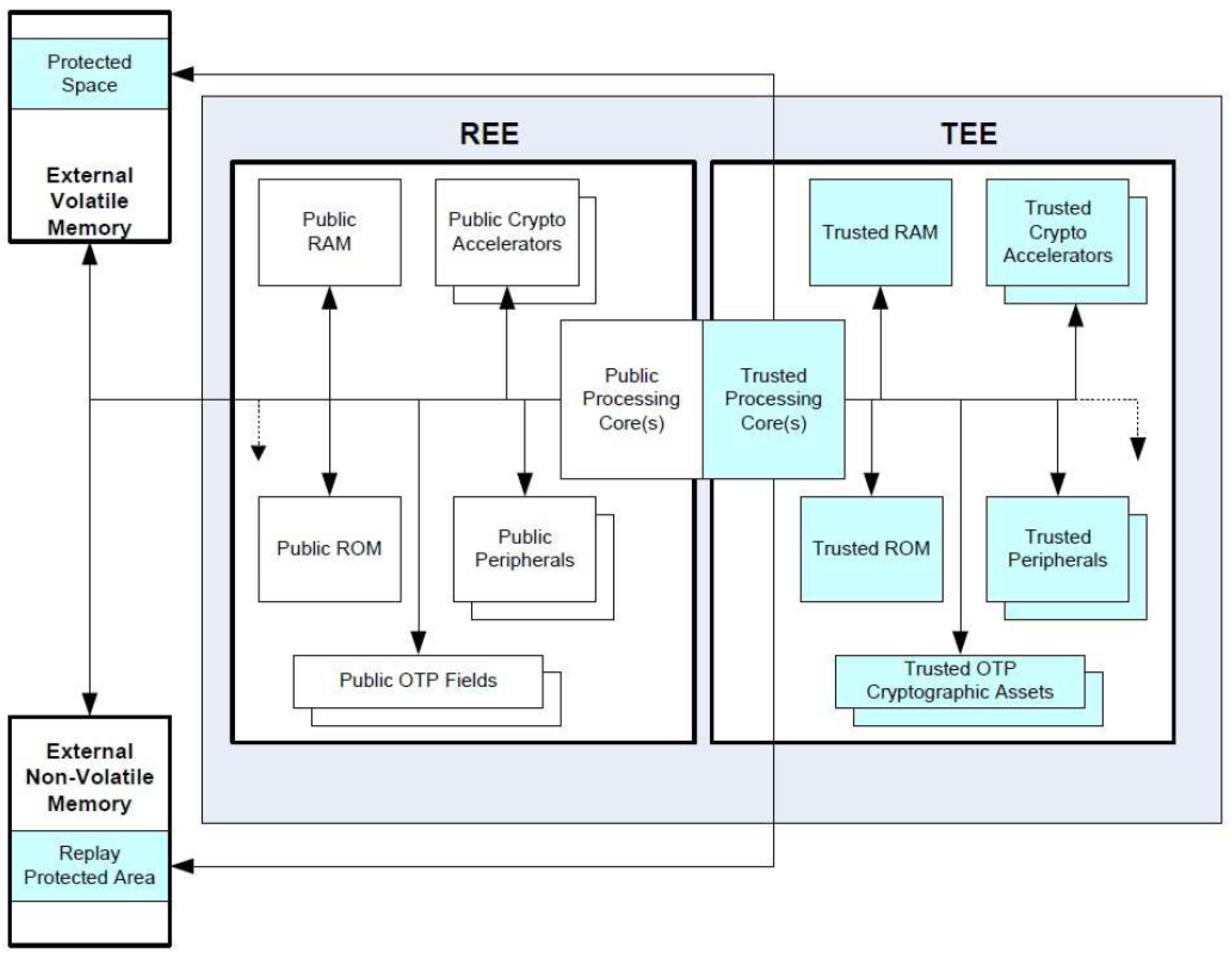
5.1.1. CO-TSM UCOM-Based HCE-TEE Architecture
- Establishing a unique per-chip root key for each TEE.
- Device delivery and preliminary key distribution.
- Application development and distribution.
- TEE initialisation and key establishment.
- CO-TSM authorisation and key management.
- Update TEE Manager and HCE-TEE key management.
- Update TA Manager and HCE-TEE key management.
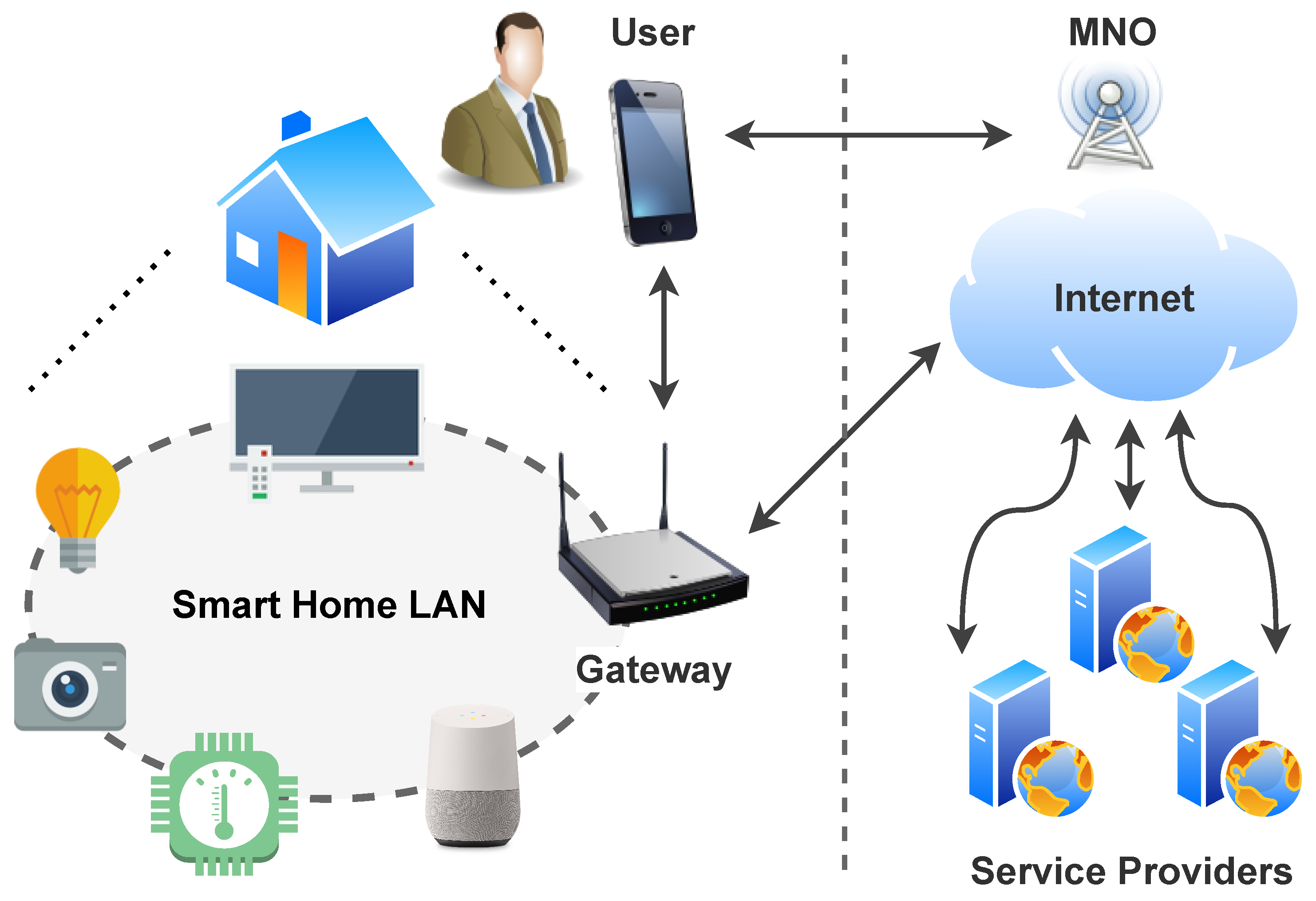
5.2. CO-TSM UCOM-Based Smart Home
5.2.1. Smart Home Architecture
5.2.2. CO-TSM UCOM-Based Smart Home Architecture
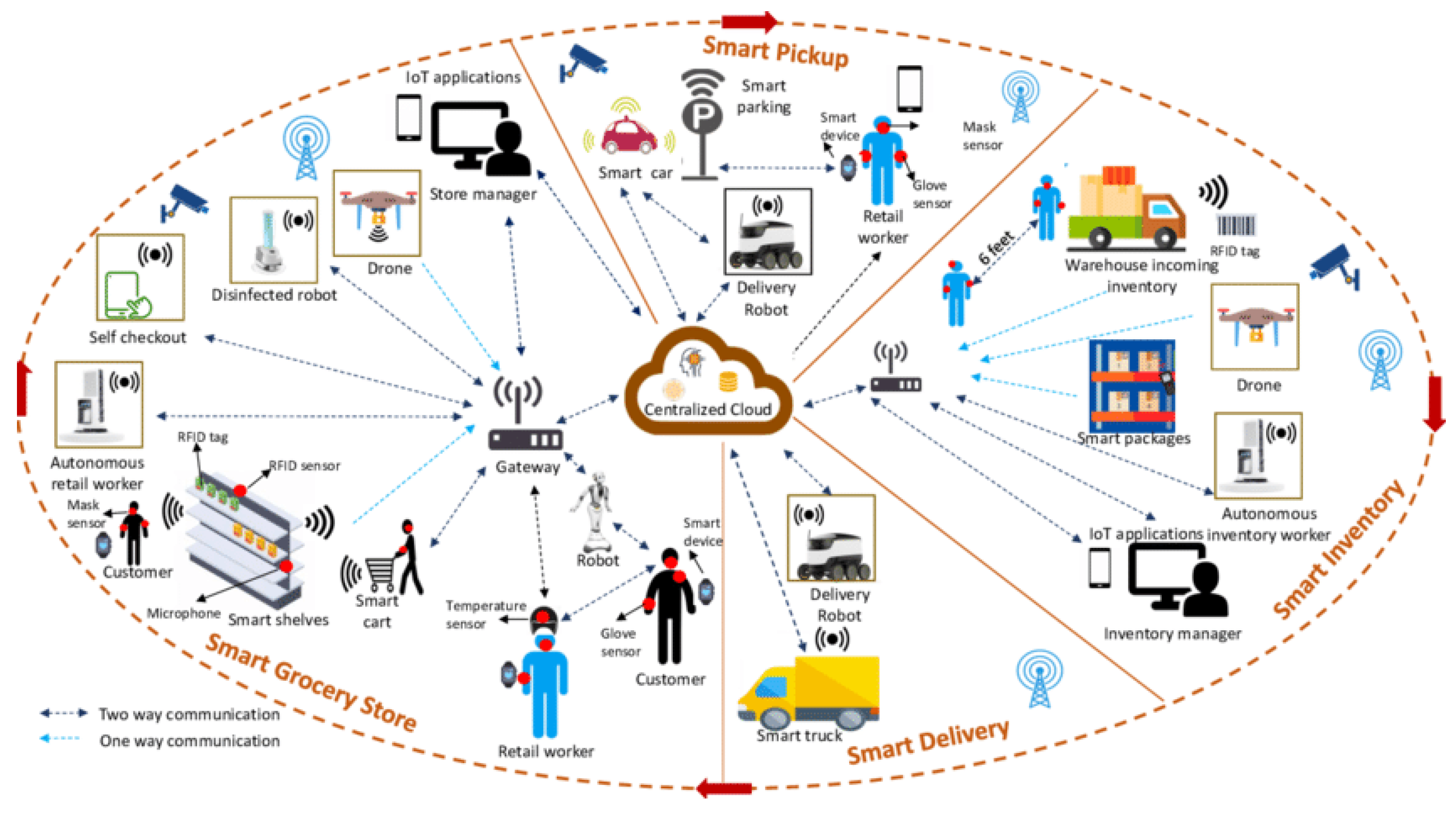
5.3. CO-TSM UCOM-Based RFID Architecture for Smart Supply Environments
5.3.1. What Are Smart Supply Environments?
5.3.2. RFID Technology and Smart Supply Architecture
- Enhanced Asset Utilisation: Efficient ownership updates reflect the updated status of items in the supply chain, preventing assets from becoming ’lost’ or misallocated between entities. This promotes proactive optimisation with redeployments and rentals.
- Circular Economy Facilitation: RFID-enabled ownership information helps in the recovery, repurposing, and proper end-of-life disposal of assets. This supports a sustainable and waste-reductive circular economy model.
- Reduction of Carbon Footprint: Optimal asset utilisation and circular economy practices, powered by the data visibility fostered by RFID, directly contribute to reducing waste and greenhouse gas emissions associated with redundant manufacturing and resource depletion.
- Improved Collaboration and Trust: Transparent tracking of ownership promotes supply chain transparency, encouraging greater collaboration and building trust among stakeholders.
5.3.3. Blockchain Technology
- Decentralisation: Eliminating central intermediaries through blockchain decentralisation mitigates bottlenecks and single points of failure, bolstering the scalability and resilience of RFID-based ownership management systems.
- Security and Immutability: Blockchain’s inherent cryptographic functions secure ownership data, making it resistant to tampering. Any attempts to alter records create inconsistencies that the network flags, enhancing trustworthiness.
- Automation: Smart contracts automate ownership updates when associated RFID tags trigger predefined conditions, minimising manual intervention and associated delays or errors. This streamlines supply chain operations, improving overall efficiency.
- Transparency: Blockchain’s distributed ledger offers a shared, immutable view of ownership data across multiple stakeholders in the supply chain. This visibility reinforces trust and promotes proactive conflict resolution.
5.3.4. CO-TSM-Based Smart Supply Chain
- Detailed Operational Walkthrough is list below and illustrated in Figure 13.
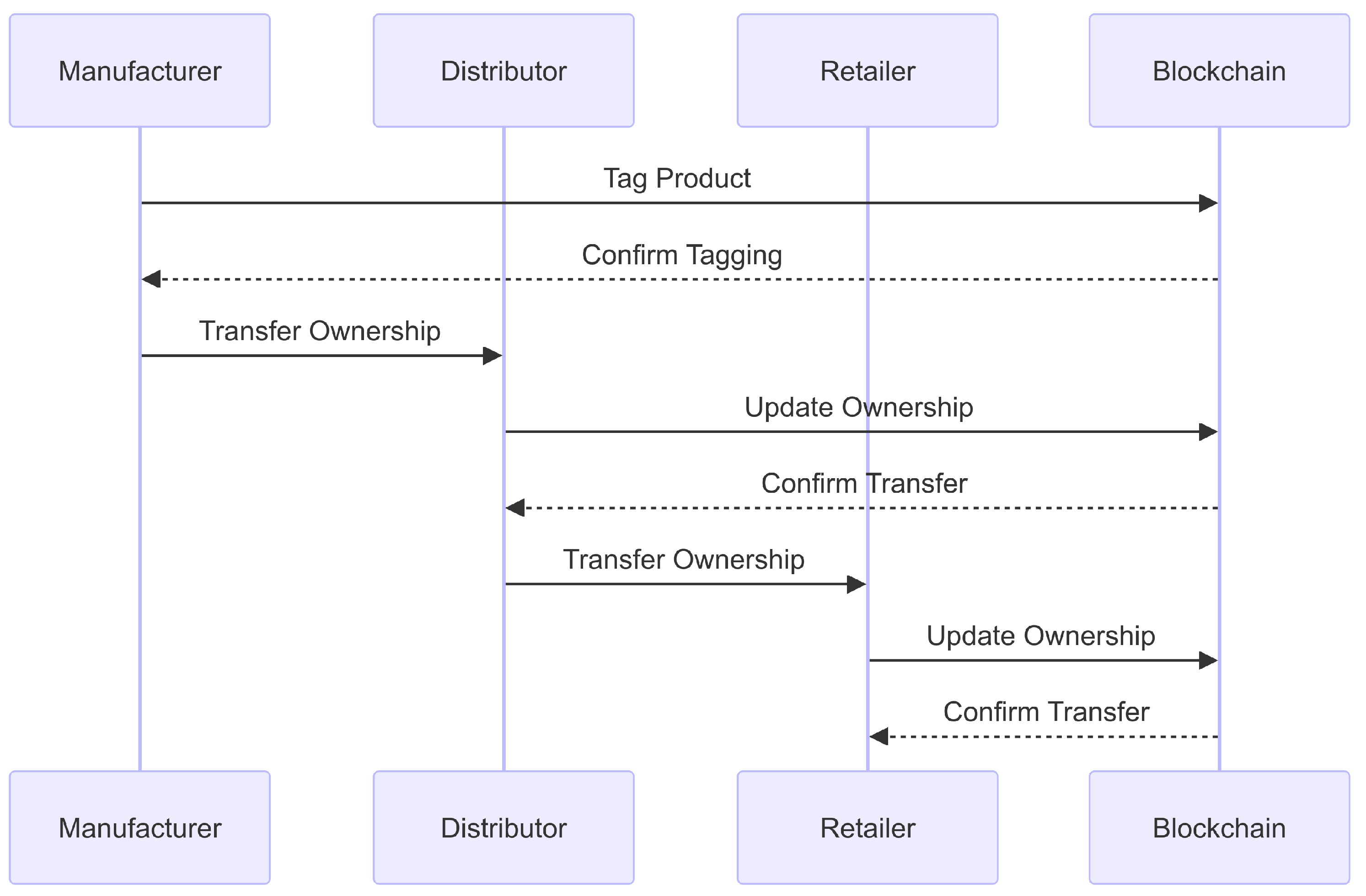
- Step 1: Initialisation and Tagging: The journey begins with the tagging of physical products with RFID tags. Each tag is encoded with unique identifiers that link to a digital twin on the blockchain. This digital twin houses essential information about the product, including its provenance, current ownership, and transaction history.
- Step 2: Ownership Transfer Mechanism: As products traverse through various stages of the supply chain, their ownership status is poised for transfer. The smart contracts, designed with pre-defined rules for ownership transfer, play a critical role here. They automatically execute upon the fulfilment of specified conditions, such as a sale or consignment agreement, thereby initiating the ownership transfer process on the blockchain.
- Step 3: Smart Contract Execution: Upon activation, the smart contract verifies the transaction against its conditions, ensuring all criteria are met for a legitimate transfer. It then updates the blockchain ledger, reflecting the new ownership of the RFID tag. This process is immutable and transparent, providing an incontrovertible record of the transaction.
- Step 4: Notification and Verification: Stakeholders involved in the transaction receive notifications of the ownership change. They can independently verify the updated ownership status through the blockchain, ensuring transparency and trust among parties.
- In-Depth Analysis of System Benefits
- Enhanced Security and Immutability: By leveraging blockchain’s inherent security features, the system ensures that all transactions are secure and immutable, significantly reducing the risk of fraud and tampering.
- Decentralisation and Trust: The decentralised nature of blockchain eliminates reliance on central authorities, fostering a trustless environment where transactions are verified by consensus.
- Efficiency and Reduction of Errors: Automation through smart contracts minimises manual handling, streamlining operations, and reducing the likelihood of errors.
- Transparency and Traceability: The system provides unparalleled transparency, allowing stakeholders to trace the history and ownership of products in real-time.
6. Limitations of the CO-TSM Model
6.1. Technical Limitations
- Scalability and Performance: The CO-TSM model introduces a decentralised architecture that requires robust key management and secure communication protocols. While this decentralisation enhances security and flexibility, it can also lead to scalability challenges, particularly in environments with a large number of devices. For instance, in smart supply chains, managing thousands of RFID tags and their associated cryptographic keys can become cumbersome. The overhead of secure communication and key management protocols may impact the performance of the system, especially in real-time applications. This is also evident in HCE-TEE smartphone deployments, where the increased battery consumption due to frequent secure communications and TEE operations can degrade the user experience.
- Energy Consumption: Implementing CO-TSM in devices with limited power resources, such as IoT devices and RFID tags, can be challenging. The energy consumption associated with cryptographic operations and secure communications can significantly reduce the battery life of these devices. In the context of smart homes, where numerous IoT devices need to operate efficiently, the increased energy demands can strain the overall system and impact device longevity.
- Interoperability Issues: The CO-TSM model aims to provide a flexible and user-centric approach to device management. However, achieving seamless interoperability between devices from different manufacturers and service providers remains a significant challenge. Different devices may use varying communication protocols, security standards, and TEE implementations, leading to compatibility issues. This is particularly evident in smart home environments, where diverse devices from multiple vendors need to work together harmoniously. In smart supply chains, the integration of RFID technology with existing systems requires overcoming interoperability barriers to ensure smooth operation across the supply network.
- Complexity of Integration: Integrating the CO-TSM model into existing infrastructures can be complex and resource-intensive. Organisations may need to overhaul their current systems to accommodate the decentralised architecture and secure communication protocols of CO-TSM. This integration complexity can act as a barrier to adoption, especially for small and medium-sized enterprises with limited technical expertise and resources. In HCE-TEE smartphone deployments, the integration of TEE with existing mobile applications and infrastructure requires significant effort and coordination.
6.2. Operational Limitations
- Management Overhead: The CO-TSM model decentralises the management of devices and applications, which can increase the operational overhead for service providers. Managing a distributed network of devices, ensuring secure key management, and handling updates and maintenance tasks require significant effort and resources. In smart supply chains, the continuous monitoring and updating of RFID tags across multiple stages of the supply chain can strain operational capabilities. Similarly, in smart home environments, the decentralised management of numerous IoT devices necessitates robust and efficient operational strategies.
- Responsibility and Accountability: Decentralisation introduces ambiguity in responsibility and accountability. Determining which entity is responsible for security breaches, device malfunctions, or data integrity issues can be challenging. In traditional TSM models, a central authority assumes responsibility, but the CO-TSM model’s decentralised nature necessitates clear agreements and accountability frameworks among stakeholders. This complexity is evident in the smart home case study, where multiple entities, including device manufacturers, service providers, and users, share responsibilities.
6.3. Strategic Limitations
- Resistance to Change: Organisations accustomed to traditional centralised TSM models may resist adopting the CO-TSM model due to its fundamental shift in architecture and management practices. Convincing stakeholders of the benefits and addressing concerns related to decentralisation, security, and control requires substantial effort. This resistance is particularly pronounced in industries with established practices and long-standing relationships with central TSM providers. For example, in the smart supply chain industry, shifting to a decentralised CO-TSM model may face resistance due to entrenched centralised systems and practices.
- Monopolistic Tendencies: The CO-TSM model aims to empower consumers and foster a competitive market environment. However, it does not address the behaviour of aggressive, non-cooperating entities that may seek to establish monopolies. These entities could selectively establish relationships with service providers, limiting consumer choice and undermining the model’s flexibility. For instance, in the HCE-TEE smartphone deployment, a dominant service provider might restrict access to certain applications, thereby reducing the overall effectiveness of the CO-TSM model.
6.4. Case Study Insights and General Implications
6.4.1. HCE-TEE Smartphone Deployments
6.4.2. IoT Deployments and Smart Home Environments
6.4.3. RFID-Enabled Smart Supply Chains
6.4.4. General Implications for CO-TSM Adoption
6.4.5. Benefits of CO-TSM Adoption across Use Cases
6.5. Future Research Directions
- Improving Scalability: Developing efficient key management and communication protocols to enhance the scalability of CO-TSM in large networks of devices.
- Optimising Energy Consumption: Designing energy-efficient cryptographic operations and secure communication mechanisms to reduce the impact on battery life for IoT and RFID devices.
- Enhancing Interoperability: Standardising protocols and frameworks to ensure seamless interoperability between devices from different manufacturers and service providers.
- Simplifying Integration: Creating tools and methodologies to simplify the integration of CO-TSM into existing infrastructures, reducing the technical and resource barriers for adoption.
- Establishing Accountability: Developing clear accountability frameworks to manage responsibility and address security breaches, device malfunctions, and data integrity issues in decentralised environments.
7. Conclusions and Key Takeaways
7.1. Key Contributions and Value to Knowledge
- Decentralisation of Application Management: The CO-TSM model decentralises the management of applications, allowing users and service providers greater autonomy and flexibility. This approach mitigates the centralised control bottlenecks that have historically plagued traditional TSM models.
- Integration Across Technological Domains: By exploring the application of the CO-TSM model across various technological ecosystems—including HCE-TEE smartphones, IoT environments, and RFID-enabled smart supply chains—this paper demonstrates the model’s versatility and adaptability. Each case study highlights the unique challenges and benefits associated with deploying CO-TSM in different contexts, offering valuable insights for future implementations.
- Enhancement of Security Mechanisms: The CO-TSM model strengthens security by incorporating constant evaluation, remote attestation mechanisms, and robust key management practices. These enhancements ensure that the security needs of modern, interconnected devices are met without compromising performance or user experience.
- Addressing Market Fragmentation: By fostering greater interoperability and reducing reliance on centralised control, the CO-TSM model helps overcome market fragmentation issues. This allows for a more seamless integration of services across different platforms and devices, ultimately benefiting both service providers and consumers.
- Identification of Challenges and Future Research Directions: The paper does not merely present the CO-TSM model as a solution; it also critically evaluates its limitations and identifies areas where further research and development are necessary. These insights provide a roadmap for advancing the CO-TSM model and ensuring its successful deployment in real-world scenarios.
7.2. Summary of Findings
- Scalability and Flexibility: The CO-TSM model’s decentralised architecture provides a scalable solution for managing secure applications across a wide range of devices and platforms. This flexibility is particularly valuable in IoT and RFID environments, where the number of connected devices is continually growing.
- User Empowerment: By allowing users to choose and switch CO-TSMs and install applications from any service provider, the CO-TSM model empowers consumers with greater control over their devices. This user-centric approach aligns with the growing demand for personalised and adaptable technology solutions.
- Security and Trust: The CO-TSM model enhances security through continuous evaluation, remote attestation, and secure key management. These mechanisms help maintain the integrity of smart cards, IoT devices, and RFID systems, reducing the risk of breaches and ensuring that applications remain secure.
- Operational Challenges: While the CO-TSM model offers significant benefits, its implementation is not without challenges. Managing decentralised networks, ensuring interoperability between diverse devices, and overcoming resistance to change are critical areas that require careful consideration.
- Potential for Broad Application: The versatility of the CO-TSM model makes it applicable across various industries and technological domains. From enhancing the security of HCE-TEE smartphones to improving the efficiency of RFID-enabled supply chains, the CO-TSM model offers a robust framework for the future of secure embedded device management.
7.3. Future Outlook
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Markantonakis, K. The Case for a Secure Multi-Application Smart Card Operating System. In Information Security: First International Workshop, ISW’97, Tatsunokuchi, Ishikawa Japan, September 17–19, 1997, Proceedings; Springer: Berlin/Heidelberg, Germany, 1998; pp. 188–197. [Google Scholar]
- Girard, P. Which Security Policy for Multiplication Smart Cards? In Proceedings of the USENIX Workshop on Smartcard Technology on USENIX Workshop on Smartcard Technology, Berkeley, CA, USA, 10–11 May 1999; p. 3. [Google Scholar]
- Chaumette, S.; Sauveron, D. Some Security Problems Raised by Open Multiapplication Smart Cards. In Proceedings of the 10th Nordic Workshop on Secure IT-Systems: NordSec 2005, Tartu, Estonia, 20–21 October 2005; Citeseer: Princeton, NJ, USA, 2005; pp. 20–21. [Google Scholar]
- Foundation for Information Policy Research. Framework for Smart Card Use in Government; Technical Report; Foundation for Information Policy Research: Bedfordshire, UK, 1999. [Google Scholar]
- Lindly, R.A. The Age of Smart Cards: An Exploratory Investigation of the Sociotechnical Factors Influencing Smart Card Innovation. Ph.D. Thesis, Department of Information and Communication Technology, Universtiy of Wollongong, Wollongong, NSW, Australia, 1996. [Google Scholar]
- M’Chirgui, Z. The Economics of the Smart Card Industry: Towards Coopetitive Strategies. Econ. Innov. New Technol. 2005, 14, 455–477. [Google Scholar] [CrossRef]
- NFCW. NFC Trials, Pilots, Tests and Live Services around the World. Technical Report. Available online: https://www.nfcw.com/list-of-nfc-trials-pilots-tests-and-commercial-services-around-the-world/ (accessed on 20 June 2024).
- Pay-Buy-Mobile: Business Opportunity Analysis; White Paper 1.0; GSM Association: London, UK, 2007; Available online: http://www.gsmworld.com/documents/gsma_nfc_tech_guide_vs1.pdf (accessed on 20 June 2024).
- Commerce, G.M. The Role of the Trusted Service Manager in Mobile Commerce; Technical Report; GSM Association: London, UK, 2013; Available online: http://www.gsma.com/digitalcommerce/wp-content/uploads/2013/12/GSMA-TSM-White-Paper-FINAL-DEC-2013.pdf (accessed on 20 June 2024).
- The Role and Scope of EMVCo in Standardising the Mobile Payments Infrastructure; Technical Report; EMVCo.: Foster City, CA, USA, 2007.
- GlobalPlatform TEE Management Framework; Technical Report v1.0; GlobalPlatform: Redwood City, CA, USA, 2016.
- Alattar, M.; Achemlal, M. Host-Based Card Emulation: Development, Security, and Ecosystem Impact Analysis. In Proceedings of the 2014 IEEE International Conference on High Performance Computing and Communications, 6th IEEE International Symposium on Cyberspace Safety and Security, 11th IEEE International Conference on Embedded Software and Systems, HPCC/CSS/ICESS 2014, Paris, France, 20–22 August 2014; pp. 506–509. [Google Scholar] [CrossRef]
- Host Card Emulation (HCE) 101; Whitepaper; A Smart Card Alliance Mobile & NFC Council: Redwood City, CA, USA, 2014; Available online: http://iqdevices.com/pdfFiles/HCE-101-WP-FINAL-081114-clean.pdf (accessed on 20 June 2024).
- GlobalPlatform. Technical Report. 2016. Available online: https://www.globalplatform.org/ (accessed on 20 June 2024).
- GlobalPlatform. TEE System Architecture, Version 1.0; GlobalPlatform Specifications; GlobalPlatform: Redwood City, CA, USA, 2011; Available online: https://www.globalplatform.org/specificationsdevice.asp (accessed on 20 June 2024).
- The Trusted Execution Environment: Delivering Enhanced Security at a Lower Cost to the Mobile Market; Whitepaper; GlobalPlatform: Redwood City, CA, USA, 2015; Available online: http://www.globalplatform.org/documents/whitepapers/GlobalPlatform_TEE_Whitepaper_2015.pdf (accessed on 20 June 2024).
- Statista. Arm’s Market Share and Targets Across Key Technology Markets in 2019 and 2028 Fiscal Years. Technical Report. 2020. Available online: https://www.statista.com/statistics/1132112/arm-market-share-targets/ (accessed on 20 June 2024).
- ARM Holdings. Record Shipments of Arm-Based Chips in Previous Quarter. Technical Report. 2020. Available online: https://www.arm.com/company/news/2020/02/record-shipments-of-arm-based-chips-in-previous-quarter (accessed on 20 June 2024).
- Shepherd, C.; Arfaoui, G.; Gurulian, I.; Lee, R.P.; Markantonakis, K.; Akram, R.N.; Sauveron, D.; Conchon, E. Secure and trusted execution: Past, present, and future—A critical review in the context of the internet of things and cyber-physical systems. In Proceedings of the 15th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Tianjin, China, 23–26 August 2016; pp. 168–177. [Google Scholar]
- Cerdeira, D.; Santos, N.; Fonseca, P.; Pinto, S. Sok: Understanding the prevailing security vulnerabilities in trustzone-assisted tee systems. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 18–21 May 2020; pp. 1416–1432. [Google Scholar]
- Shepherd, C. Techniques for Establishing Trust in Modern Constrained Sensing Platforms with Trusted Execution Environments. Ph.D. Thesis, Information Security Group, Royal Holloway, University of London, Egham, UK, 2019. [Google Scholar]
- Zheng, S.; Apthorpe, N.; Chetty, M.; Feamster, N. User perceptions of smart home IoT privacy. Proc. ACM Hum.-Comput. Interact. 2018, 2, 200. [Google Scholar] [CrossRef]
- Albrecht, K.; Mcintyre, L. Privacy nightmare: When baby monitors go bad. IEEE Technol. Soc. Mag. 2015, 34, 14–19. [Google Scholar] [CrossRef]
- Bastos, D.; Shackleton, M.; El-Moussa, F. Internet of Things: A survey of technologies and security risks in smart home and city environments. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar] [CrossRef]
- Smart Camera and Baby Monitor Warning Given by UK’s Cyber-Defender. BBC News, 3 March 2020. Available online: https://www.bbc.co.uk/news/technology-51706631 (accessed on 20 June 2024).
- Hackers Claim to Have Access to 50,000 Home Security Cameras. Infosecurity Magazine, 14 October 2020. Available online: https://www.infosecurity-magazine.com/news/hackers-access-50000-home-security/ (accessed on 20 June 2024).
- Somebody’s Watching: Hackers Breach Ring Home Security Cameras. New York Times, 15 December 2019. Available online: https://www.nytimes.com/2019/12/15/us/Hacked-ring-home-security-cameras.html (accessed on 20 June 2024).
- Department for Digital, Culture, Media and Sport—UK Government. Code of Practice for Consumer IoT Security. Technical Report. 2018. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/773867/Code_of_Practice_for_Consumer_IoT_Security_October_2018.pdf (accessed on 20 June 2024).
- Morgner, P.; Mai, C.; Koschate-Fischer, N.; Freiling, F.; Benenson, Z. Security update labels: Establishing economic incentives for security patching of IoT consumer products. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 18–21 May 2020; pp. 429–446. [Google Scholar]
- Noura, M.; Atiquzzaman, M.; Gaedke, M. Interoperability in internet of things: Taxonomies and open challenges. Mob. Netw. Appl. 2019, 24, 796–809. [Google Scholar] [CrossRef]
- Costa, C.; Antonucci, F.; Pallottino, F.; Aguzzi, J.; Sarriá, D.; Menesatti, P. A review on agri-food supply chain traceability by means of RFID technology. Food Bioprocess Technol. 2013, 6, 353–366. [Google Scholar] [CrossRef]
- Gupta, D.; Bhatt, S.; Gupta, M.; Tosun, A.S. Future Smart Connected Communities to Fight COVID-19 Outbreak. Internet Things 2021, 13, 100342. [Google Scholar] [CrossRef] [PubMed]
- Fan, K.; Jiang, W.; Li, H.; Yang, Y. Lightweight RFID protocol for medical privacy protection in RFID-enabled healthcare environment. IEEE/ACM Trans. Comput. Biol. Bioinform. 2015, 12, 362–371. [Google Scholar]
- Bottani, E.; Rizzi, A. Economical assessment of the impact of RFID technology and EPC system on the fast-moving consumer goods supply chain. Int. J. Prod. Econ. 2008, 112, 548–569. [Google Scholar] [CrossRef]
- Chang, V.; Ramachandran, M.; Li, C.S.; Cruz, R.S. Blockchain-based trust management and authentication for distributed traceability in food supply chain. In Proceedings of the International Workshop on Security, Fukui, Japan, 2–4 September 2020; Springer: Cham, Switzeland, 2020; pp. 81–97. [Google Scholar]
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A survey on consensus mechanisms and mining strategy management in blockchain networks. IEEE Access 2019, 7, 22328–22370. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]


| Aspect | ICOM-Based CO-TSM | UCOM-Based CO-TSM |
|---|---|---|
| Security Assurance for SPs | Relies on evaluation and certification at issuance and installation | Includes mechanisms for constant security evaluation and potential revocation |
| Detecting Simulator Attacks | Not fully addressed | Proposes countermeasures using remote attestation |
| Addressing Parasite Application Issues | Needs further development | Proposes countermeasures |
| Flexible Charging for Application Installations | Limited by offline relationships | Supports online fee processing during installation |
| Secure Application Sharing | Uses traditional firewalls | Proposes modifications to the traditional firewall mechanism |
| Platform Protection | Limited | Proposes run-time security mechanisms to prevent malicious behaviour |
| Recovery Mechanism for Lost Smart Cards | Not specifically addressed | Proposes an instant recovery mechanism |
| Category | Strengths | Weaknesses |
|---|---|---|
| Flexibility | Users can install applications from any Service Provider (SP), regardless of partnership with the CO-TSM. | The increased flexibility might introduce new attack vectors that need to be carefully addressed. |
| Security | Incorporates constant security evaluation and remote attestation mechanisms. | Requires significant changes to existing smart card architectures and protocols. |
| User Empowerment | Allows users to choose and switch CO-TSMs, providing greater control over their smart card management. | The increased control given to users necessitates better education about security implications. |
| Scalability | Supports online fee processing and eliminates the need for offline partnerships between CO-TSMs and SPs. | Implementing a unified CO-TSM model across different stakeholders may require extensive standardisation efforts. |
| Comprehensive Approach | Addresses issues such as parasite applications and platform protection that are not fully resolved in traditional models. | May face resistance from established players in the smart card ecosystem who benefit from current ICOM-based models. |
| Use Case | Enhanced Security | Increased User Control and Flexibility | Improved Operational Efficiency |
|---|---|---|---|
| HCE-TEE Smartphones | Secure isolation of critical operations within TEE; Reduced attack surface; Robust key management. | Users can switch CO-TSMs and install apps from any SP, providing flexibility. | Decentralised key management reduces dependency on a single entity, potentially lowering operational risks. |
| IoT/Smart Home | Consistent security protocols across diverse devices; Secure communication channels. | Users have control over device management and service providers, enhancing personalisation. | Efficient management of updates and security across numerous devices; Reduces complexity for service providers. |
| RFID-Enabled Smart Supply Chains | Decentralised verification of transactions; Enhanced traceability and accountability; Secure ownership transfers. | Enables stakeholders to manage their assets and transactions with greater autonomy. | Streamlined processes for tracking and managing goods; Real-time data processing without bottlenecks. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Markantonakis, K.; Arfaoui, G.; Ghazalah, S.A.; Shepherd, C.; Akram, R.N.; Sauveron, D. CO-TSM: A Flexible Model for Secure Embedded Device Ownership and Management. Smart Cities 2024, 7, 2887-2909. https://doi.org/10.3390/smartcities7050112
Markantonakis K, Arfaoui G, Ghazalah SA, Shepherd C, Akram RN, Sauveron D. CO-TSM: A Flexible Model for Secure Embedded Device Ownership and Management. Smart Cities. 2024; 7(5):2887-2909. https://doi.org/10.3390/smartcities7050112
Chicago/Turabian StyleMarkantonakis, Konstantinos, Ghada Arfaoui, Sarah Abu Ghazalah, Carlton Shepherd, Raja Naeem Akram, and Damien Sauveron. 2024. "CO-TSM: A Flexible Model for Secure Embedded Device Ownership and Management" Smart Cities 7, no. 5: 2887-2909. https://doi.org/10.3390/smartcities7050112
APA StyleMarkantonakis, K., Arfaoui, G., Ghazalah, S. A., Shepherd, C., Akram, R. N., & Sauveron, D. (2024). CO-TSM: A Flexible Model for Secure Embedded Device Ownership and Management. Smart Cities, 7(5), 2887-2909. https://doi.org/10.3390/smartcities7050112






