Intrusion Detection in Critical Infrastructures: A Literature Review
Abstract
:1. Introduction
- We present some of the most used and well-known attacks which could harm a critical infrastructure and cause serious problems and damages;
- We present a short analysis of machine learning and deep learning models and methods which are used in intrusion detection systems, as shown in the literature;
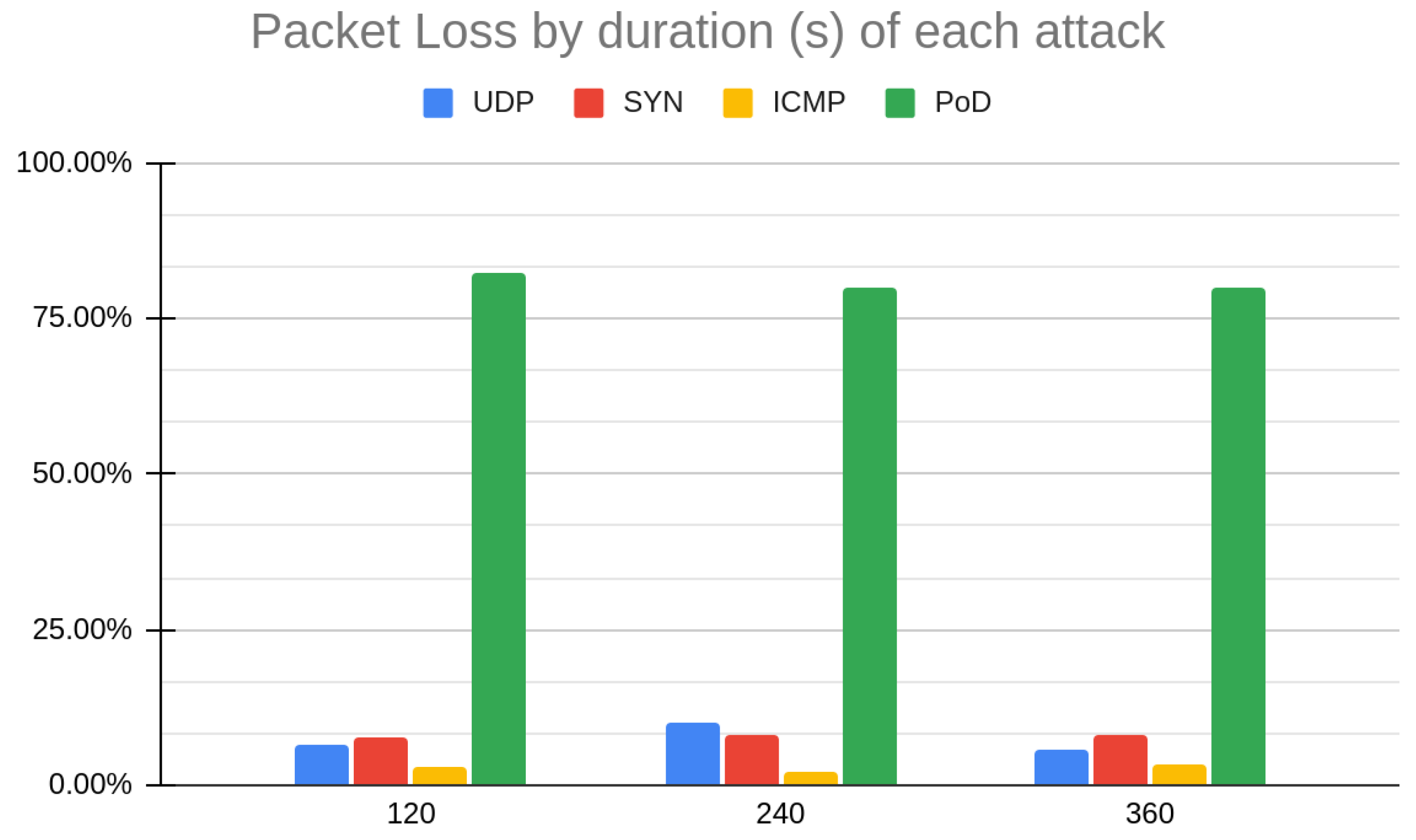
- We conduct several experiments by generating DoS (Denial of Service Attacks) attacks in order to measure packet loss and response delay;
- We evaluate the efficiency of several machine learning techniques against several attacks by using a publicly available dataset;
- We discuss our findings and propose several future research directions.
2. Related Work
3. Intrusion Attack Methods
- Clone phishing;
- Spear phishing;
- Social networking on mobile;
- Gaming phishing;
- DNS base phishing;
- Live chat;
- Whaling;
- Filter evasion.
4. Intrusion Detection Systems
4.1. Machine Learning Models
- From the dataset, D are randomly chosen K data points to be the centers of the K clusters;
- Every data point in D are assigned in the cluster whose centers is nearest to the examined data point;
- After the completion of step 2, we recalculate the center of each cluster only based on the data point which belongs to the cluster;
- When the new cluster’s centers are the same as the cluster’s centers of previous iteration, the algorithm output the clusters. Otherwise, we iterate from step 2.
4.2. Deep Learning Models
- Number of hidden CNN and MLP layers;
- Kernel size in each CNN layer;
- Subsampling factor in each CNN layer;
- The chosen pooling and activation functions.
5. Evaluation of Attacks and Detection Mechanisms
5.1. Attacks
5.2. Evaluation Results
5.3. Intrusion Detection Systems
6. Conclusions—Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Çimen, H.; Palacios-García, E.J.; Kolaek, M.; Çetinkaya, N.; Vasquez, J.C.; Guerrero, J.M. Smart-Building Applications: Deep Learning-Based, Real-Time Load Monitoring. IEEE Ind. Electron. Mag. 2020, 15, 4–15. [Google Scholar] [CrossRef]
- Santiago, I.; Moreno-Munoz, A.; Quintero-Jiménez, P.; Garcia-Torres, F.; Gonzalez-Redondo, M. Electricity demand during pandemic times: The case of the COVID-19 in Spain. Energy Policy 2021, 148, 111964. [Google Scholar] [CrossRef]
- Coffey, K.; Maglaras, L.A.; Smith, R.; Janicke, H.; Ferrag, M.A.; Derhab, A.; Mukherjee, M.; Rallis, S.; Yousaf, A. Vulnerability assessment of cyber security for SCADA systems. In Guide to Vulnerability Analysis for Computer Networks and Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 59–80. [Google Scholar]
- Lewis, T.G. Critical Infrastructure Protection in Homeland Security: Defending a Networked Nation; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Kushner, D. The real story of stuxnet. IEEE Spectr. 2013, 50, 48–53. [Google Scholar] [CrossRef]
- Upadhyay, D.; Sampalli, S. SCADA (Supervisory Control and Data Acquisition) systems: Vulnerability assessment and security recommendations. Comput. Secur. 2020, 89, 101666. [Google Scholar] [CrossRef]
- Maglaras, L.; Ferrag, M.; Derhab, A.; Mukherjee, M.; Janicke, H.; Rallis, S. Threats, countermeasures and attribution of cyber attacks on critical infrastructures. EAI Endorsed Trans. Secur. Saf. 2018, 5, e1. [Google Scholar] [CrossRef]
- Robles, R.J.; Choi, M.K.; Cho, E.S.; Kim, S.S.; Park, G.C.; Lee, J. Common threats and vulnerabilities of critical infrastructures. Int. J. Control Autom. 2008, 1, 17–22. [Google Scholar]
- Prabadevi, B.; Jeyanthi, N. A review on various sniffing attacks and its mitigation techniques. Indones. J. Electr. Eng. Comput. Sci. 2018, 12, 1117–1125. [Google Scholar] [CrossRef]
- Halfond, W.G.; Viegas, J.; Orso, A. A classification of SQL-injection attacks and countermeasures. In Proceedings of the IEEE International Symposium on Secure Software Engineering, Raleigh, NC, USA, 7–10 November 2006; Volume 1, pp. 13–15. [Google Scholar]
- Alabdan, R. Phishing attacks survey: Types, vectors, and technical approaches. Future Internet 2020, 12, 168. [Google Scholar] [CrossRef]
- Stiawan, D.; Idris, M.; Malik, R.F.; Nurmaini, S.; Alsharif, N.; Budiarto, R. Investigating brute force attack patterns in IoT network. J. Electr. Comput. Eng. 2019, 2019, 4568368. [Google Scholar] [CrossRef]
- Tewari, A.; Gupta, B.B. Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework. Future Gener. Comput. Syst. 2020, 108, 909–920. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Derhab, A.; Janicke, H. Authentication schemes for smart mobile devices: Threat models, countermeasures, and open research issues. Telecommun. Syst. 2020, 73, 317–348. [Google Scholar] [CrossRef] [Green Version]
- Wen, H.; Tang, J.; Wu, J.; Song, H.; Wu, T.; Wu, B.; Ho, P.H.; Lv, S.C.; Sun, L.M. A cross-layer secure communication model based on Discrete Fractional Fourier Fransform (DFRFT). IEEE Trans. Emerg. Top. Comput. 2014, 3, 119–126. [Google Scholar] [CrossRef]
- Mishra, A.; Gupta, N.; Gupta, B. Defense mechanisms against DDoS attack based on entropy in SDN-cloud using POX controller. Telecommun. Syst. 2021, 77, 47–62. [Google Scholar] [CrossRef]
- Hamedani, K.; Liu, L.; Atat, R.; Wu, J.; Yi, Y. Reservoir computing meets smart grids: Attack detection using delayed feedback networks. IEEE Trans. Ind. Inform. 2017, 14, 734–743. [Google Scholar] [CrossRef]
- Bhushan, K.; Gupta, B.B. Distributed denial of service (DDoS) attack mitigation in software defined network (SDN)-based cloud computing environment. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 1985–1997. [Google Scholar] [CrossRef]
- Ayodeji, A.; Liu, Y.K.; Chao, N.; Yang, L.Q. A new perspective towards the development of robust data-driven intrusion detection for industrial control systems. Nucl. Eng. Technol. 2020, 52, 2687–2698. [Google Scholar] [CrossRef]
- Clotet, X.; Moyano, J.; León, G. A real-time anomaly-based IDS for cyber-attack detection at the industrial process level of critical infrastructures. Int. J. Crit. Infrastruct. Prot. 2018, 23, 11–20. [Google Scholar] [CrossRef]
- Agrawal, S.; Agrawal, J. Survey on anomaly detection using data mining techniques. Procedia Comput. Sci. 2015, 60, 708–713. [Google Scholar] [CrossRef] [Green Version]
- Oh, S.H.; Lee, W.S. Anomaly intrusion detection based on dynamic cluster updating. In Proceedings of the Pacific-Asia Conference on Knowledge Discovery and Data Mining, Nanjing, China, 22–25 May 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 737–744. [Google Scholar]
- Bae, G.; Jang, S.; Kim, M.; Joe, I. Autoencoder-based on anomaly detection with intrusion scoring for smart factory environments. In Proceedings of the International Conference on Parallel and Distributed Computing: Applications and Technologies, Jeju Island, Korea, 20–22 August 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 414–423. [Google Scholar]
- Jeong, S.Y.; Koh, Y.S.; Dobbie, G. Phishing detection on Twitter streams. In Proceedings of the Pacific-Asia Conference on Knowledge Discovery and Data Mining, Auckland, New Zealand, 19–22 April 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 141–153. [Google Scholar]
- Zhou, W.; Wen, J.; Koh, Y.S.; Alam, S.; Dobbie, G. Attack detection in recommender systems based on target item analysis. In Proceedings of the 2014 International Joint Conference on Neural Networks (IJCNN), Beijing, China, 6–11 July 2014; pp. 332–339. [Google Scholar]
- De Santis, R.B.; Costa, M.A. Extended Isolation Forests for Fault Detection in Small Hydroelectric Plants. Sustainability 2020, 12, 6421. [Google Scholar] [CrossRef]
- Kim, J.; Kim, J.; Thu, H.L.T.; Kim, H. Long short term memory recurrent neural network classifier for intrusion detection. In Proceedings of the 2016 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea, 15–17 February 2016; pp. 1–5. [Google Scholar]
- Gomes, S.R.; Saroar, S.G.; Mosfaiul, M.; Telot, A.; Khan, B.N.; Chakrabarty, A.; Mostakim, M. A comparative approach to email classification using Naive Bayes classifier and hidden Markov model. In Proceedings of the 2017 4th International Conference on Advances in Electrical Engineering (ICAEE), Dhaka, Bangladesh, 28–30 September 2017; pp. 482–487. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Janicke, H.; Smith, R. Deep learning techniques for cyber security intrusion detection: A detailed analysis. In Proceedings of the 6th International Symposium for ICS & SCADA Cyber Security Research, Athens, Greece, 10–12 September 2019; pp. 126–136. [Google Scholar]
- Almseidin, M.; Alzubi, M.; Kovacs, S.; Alkasassbeh, M. Evaluation of machine learning algorithms for intrusion detection system. In Proceedings of the 2017 IEEE 15th International Symposium on Intelligent Systems and Informatics (SISY), Subotica, Serbia, 14–16 September 2017; pp. 277–282. [Google Scholar]
- Aldwairi, T.; Perera, D.; Novotny, M.A. An evaluation of the performance of Restricted Boltzmann Machines as a model for anomaly network intrusion detection. Comput. Netw. 2018, 144, 111–119. [Google Scholar] [CrossRef]
- Anwar, S.; Mohamad Zain, J.; Zolkipli, M.F.; Inayat, Z.; Khan, S.; Anthony, B.; Chang, V. From intrusion detection to an intrusion response system: Fundamentals, requirements, and future directions. Algorithms 2017, 10, 39. [Google Scholar] [CrossRef] [Green Version]
- Bhavsar, V.; Kadlak, A.; Sharma, S. Study on phishing attacks. Int. J. Comput. Appl. 2018, 182, 27–29. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. An anomaly-based intrusion detection system for the smart grid based on cart decision tree. In Proceedings of the 2018 Global Information Infrastructure and Networking Symposium (GIIS), Thessaloniki, Greece, 23–25 October 2018; pp. 1–5. [Google Scholar]
- Kiranyaz, S.; Avci, O.; Abdeljaber, O.; Ince, T.; Gabbouj, M.; Inman, D.J. 1D convolutional neural networks and applications: A survey. Mech. Syst. Signal Process. 2021, 151, 107398. [Google Scholar] [CrossRef]
- Stewart, B.; Rosa, L.; Maglaras, L.; Cruz, T.J.; Simões, P.; Janicke, H. Effect of network architecture changes on ocsvm based intrusion detection system. In Proceedings of the International Conference on Industrial Networks and Intelligent Systems, Hanoi, Vietnam, 27–28 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 90–100. [Google Scholar]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Panagiotis, F.; Taxiarxchis, K.; Georgios, K.; Maglaras, L.; Ferrag, M.A. Intrusion Detection in Critical Infrastructures: A Literature Review. Smart Cities 2021, 4, 1146-1157. https://doi.org/10.3390/smartcities4030061
Panagiotis F, Taxiarxchis K, Georgios K, Maglaras L, Ferrag MA. Intrusion Detection in Critical Infrastructures: A Literature Review. Smart Cities. 2021; 4(3):1146-1157. https://doi.org/10.3390/smartcities4030061
Chicago/Turabian StylePanagiotis, Fountas, Kouskouras Taxiarxchis, Kranas Georgios, Leandros Maglaras, and Mohamed Amine Ferrag. 2021. "Intrusion Detection in Critical Infrastructures: A Literature Review" Smart Cities 4, no. 3: 1146-1157. https://doi.org/10.3390/smartcities4030061
APA StylePanagiotis, F., Taxiarxchis, K., Georgios, K., Maglaras, L., & Ferrag, M. A. (2021). Intrusion Detection in Critical Infrastructures: A Literature Review. Smart Cities, 4(3), 1146-1157. https://doi.org/10.3390/smartcities4030061








