A Comparative UAV Forensic Analysis: Static and Live Digital Evidence Traceability Challenges †
Abstract
1. Introduction
- What type of challenges are present in the forensic discovery process that depend on the method of attack or intrusion?
- How do technical forensic challenges impact the forensic soundness of digital evidence recovered from UAVs?
- How do different attack scenarios change the potential ability to discover tractability or evidence?
- What are the main identifiable factors of evidence and how can this be simulated in a red team or blue team scenario?
- A ‘Purple-Teaming’ exercise performed on a commercial off-the-shelf UAV.
- Discussing possible Anti-UAV forensic techniques based on the conducted experiments.
- Proposing a Kill Chain for UAVs.
- Highlighting the technical challenges pertaining to the decryption of digital evidence recovered from UAVs.
2. Literature Review
3. Methodology
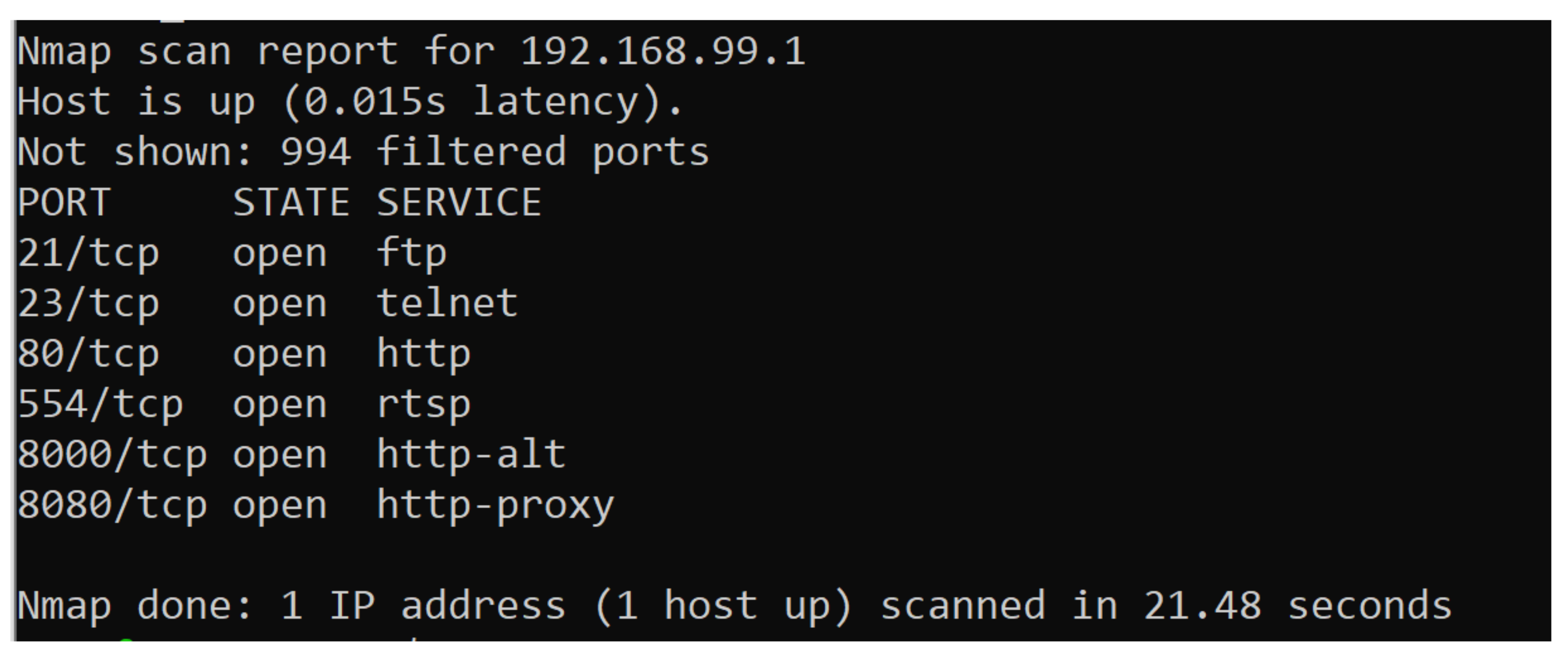
- Reconnaissance and Scanning,
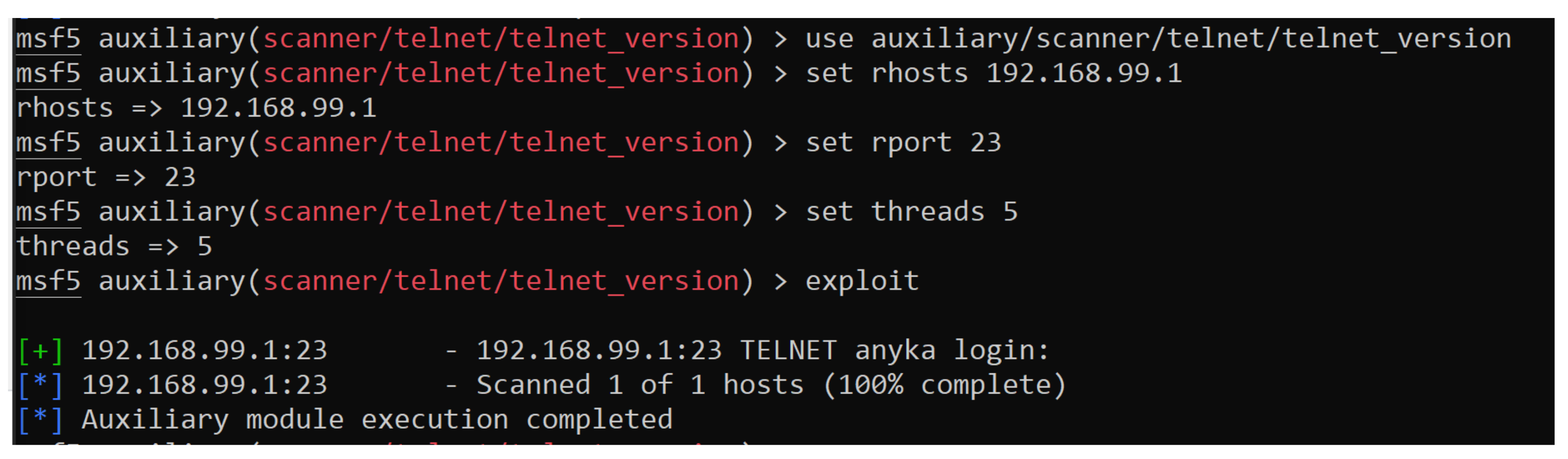
- Gaining Access,
- Maintaining Access, and
- Clearing Tracks
4. Findings
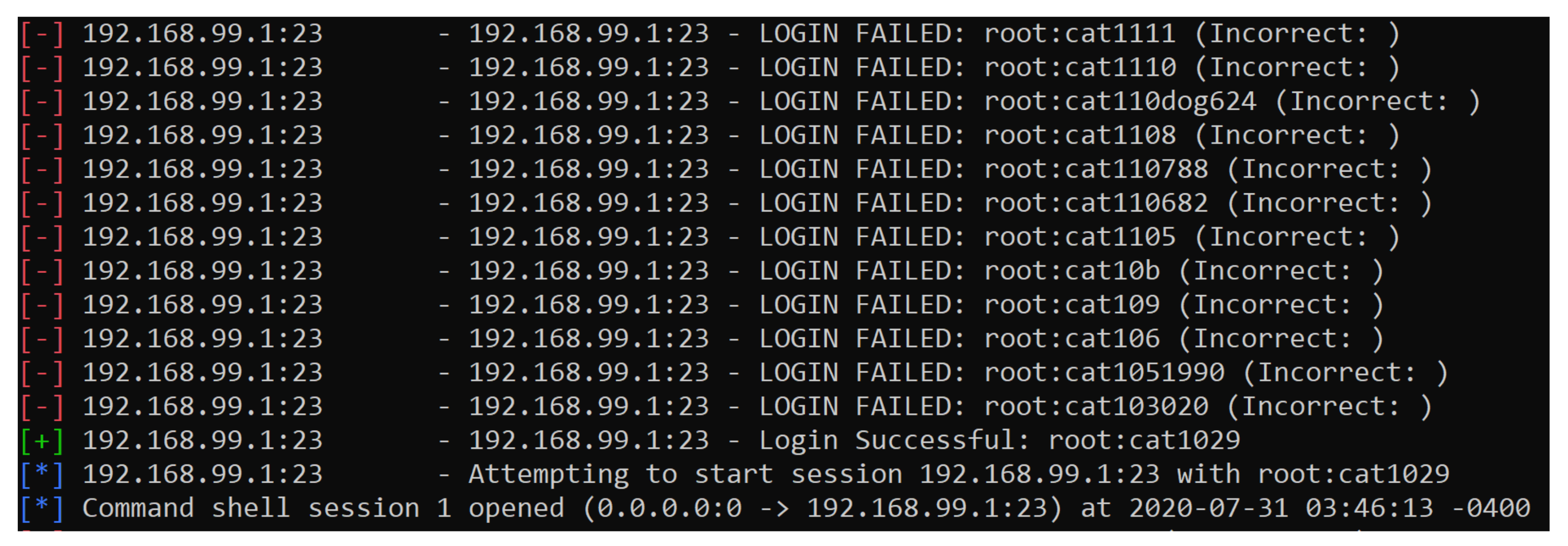
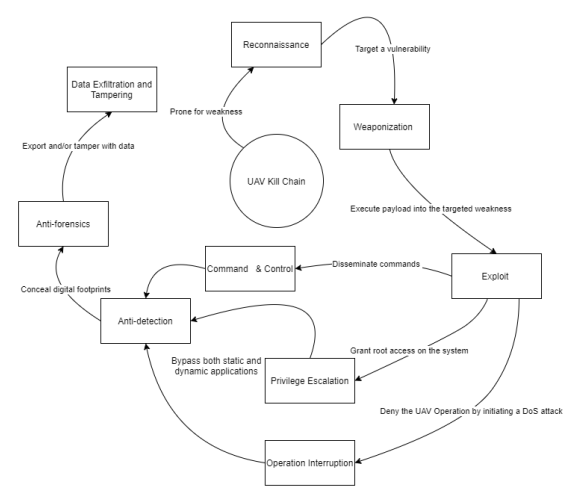
4.1. ‘Purple-Teaming’ Exercise
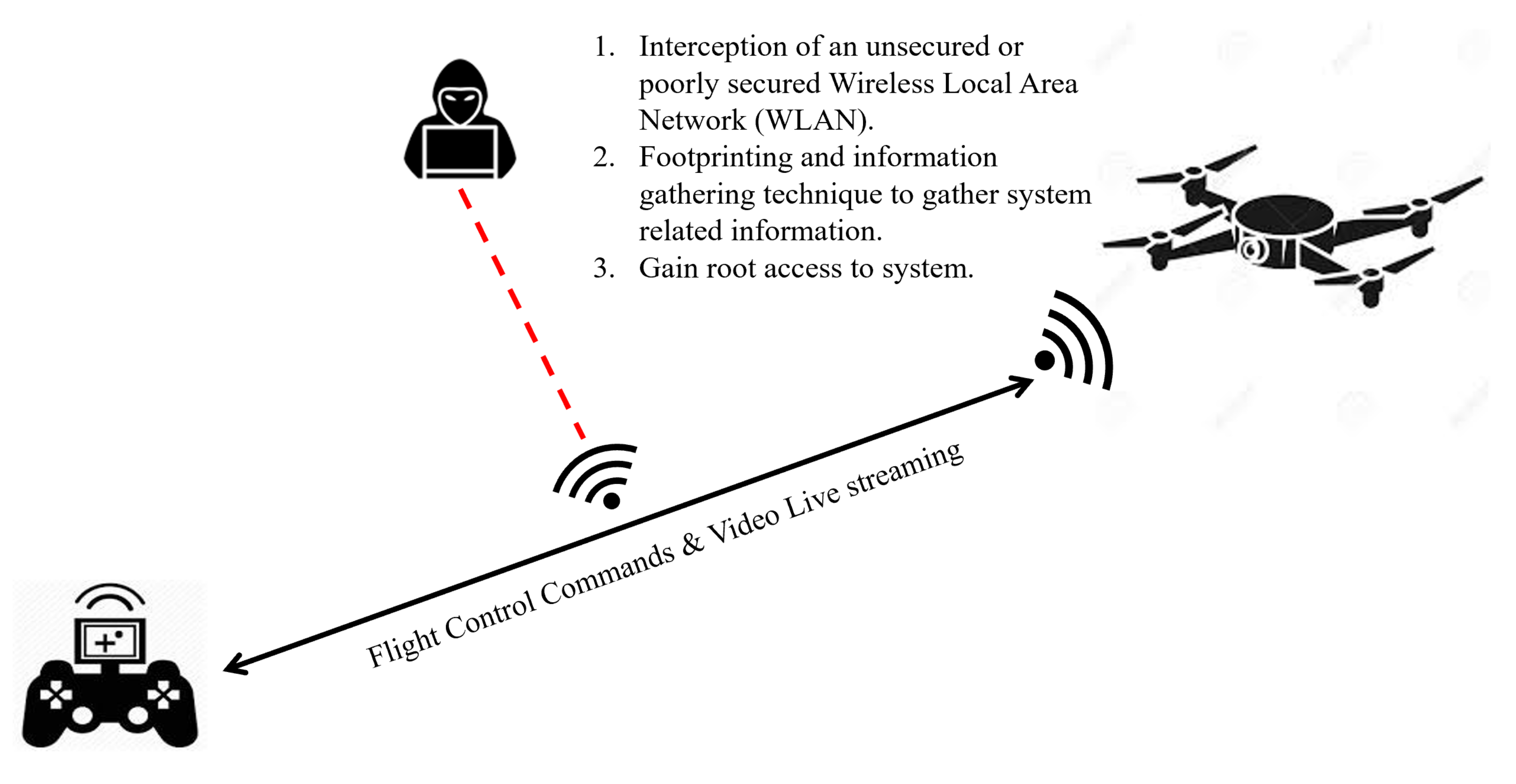
- Reconnaissance to probe for weakness.
- Weaponization to target a vulnerability that can be exploited.
- Exploit to execute the payload into the targeted weakness.
- Privilege escalation to grant root access to the systems.
- Operation Interruption to deny the service by initiating DoS or buffer overflow attacks.
- Anti-detection to bypass both static and dynamic applications
- Anti-forensics to conceal digital footprints and mislead forensic investigators in recovering the true digital evidence.
- Data Exfiltration & tampering to export data or attempt to alter metadata.
- Command & Control: to disseminate commands for different purposes (i.e., DDoS and Botnet).
- Communication protocols transmit data in motion, which keeps software related logs with no identifiable information.
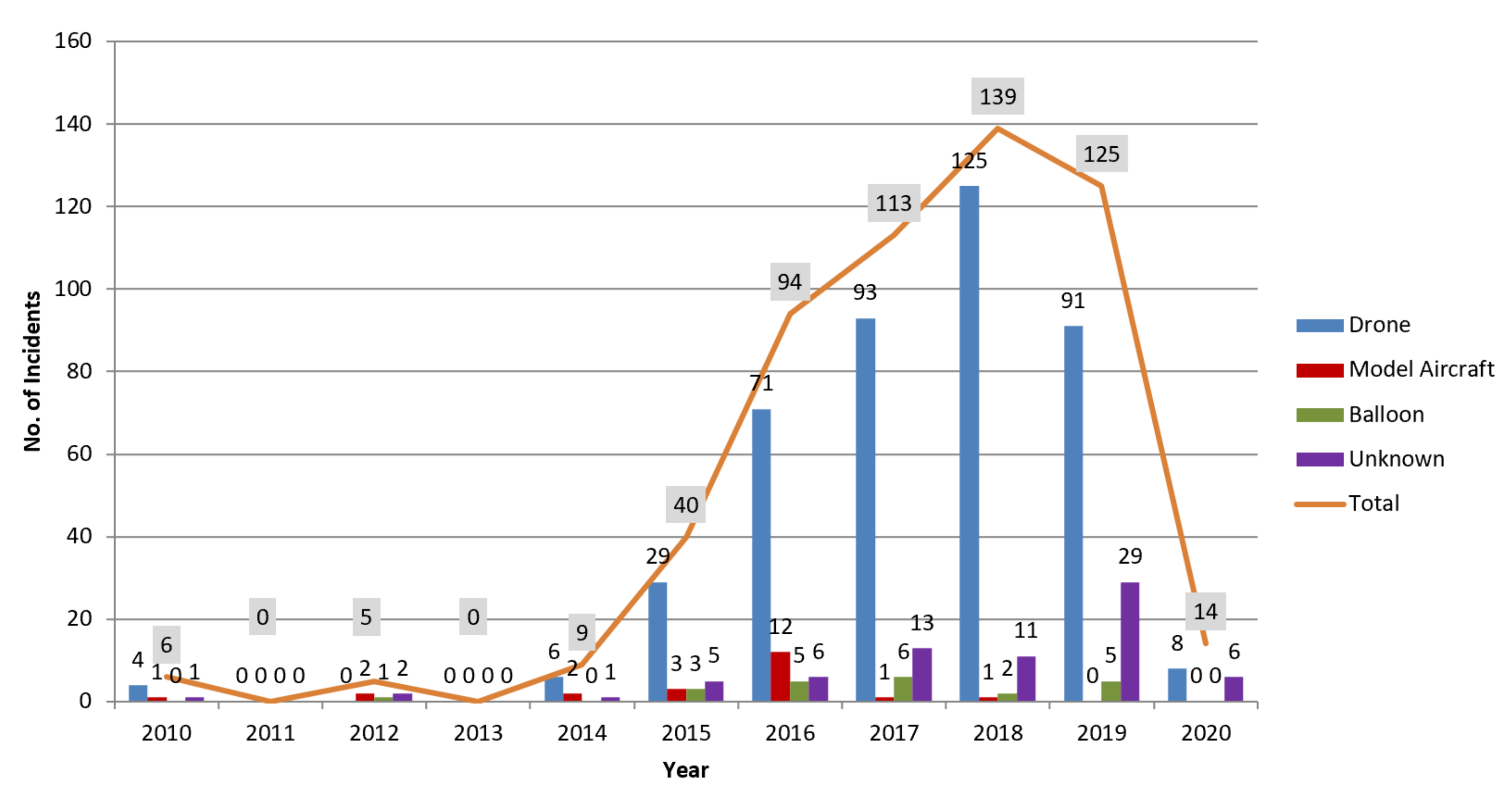
- Physical factors might lead to a better discovery of evidence because the current use of commercial drones is digitally semi-anonymous.
- The investment battle and cheap development in an emerging technology result in less secure systems where they do not meet minimum security requirements.
- Lack of third party monitoring services for UAVs.
- Challenges related to UAS customization.
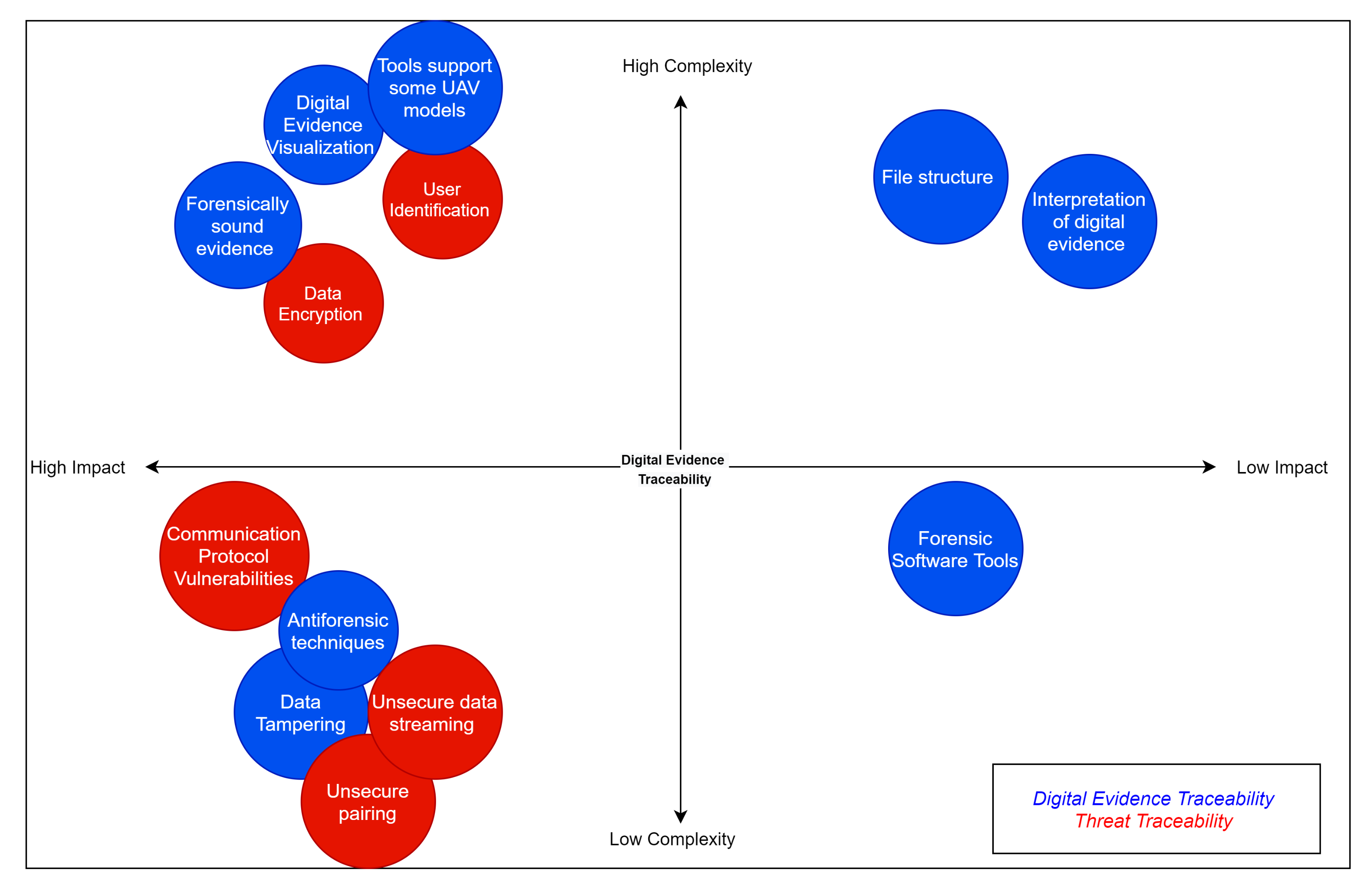
4.2. Discovery and Evaluation of UAV Forensic Technical Issues
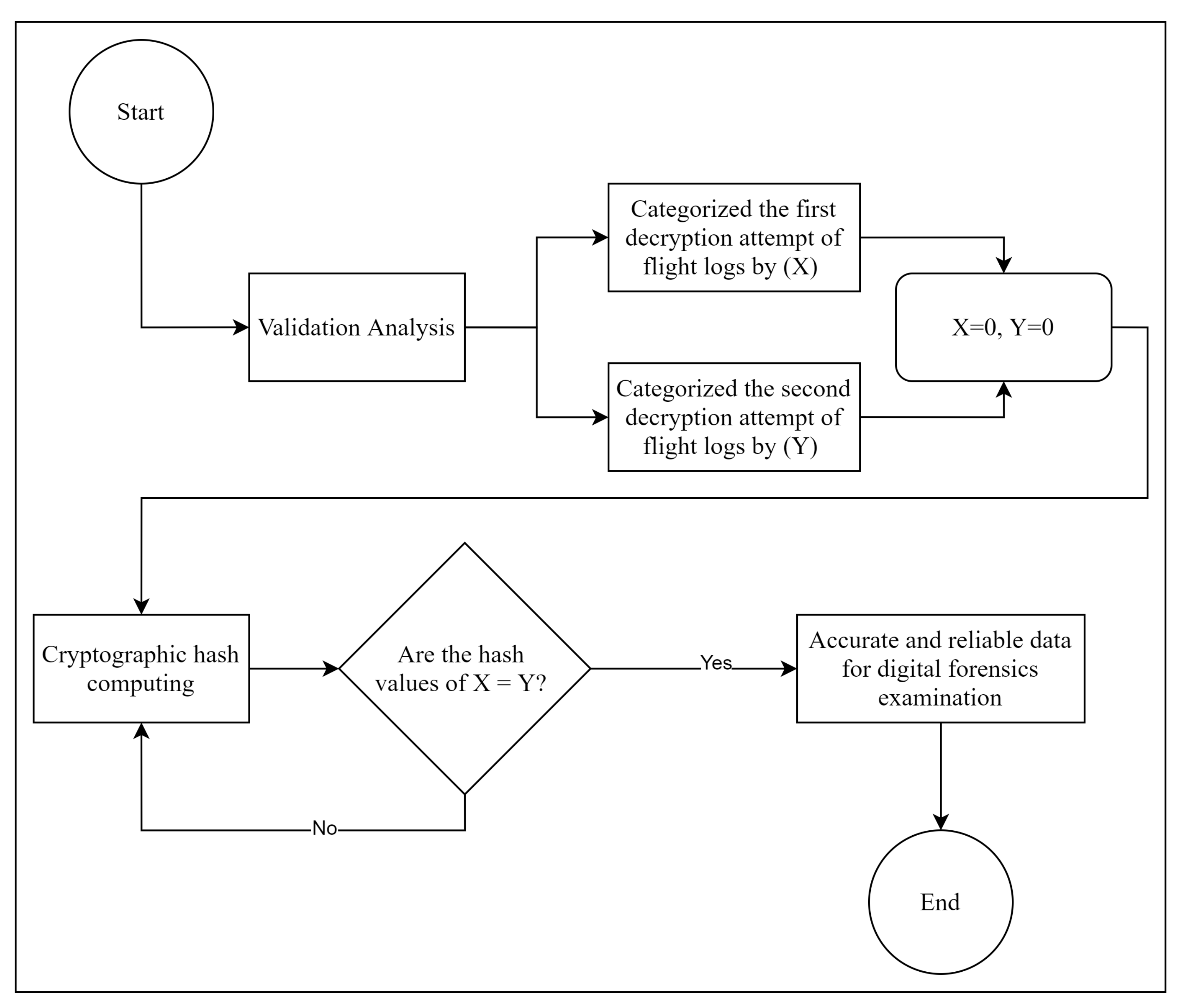
4.3. Cross-Validation Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Frost, S. Study Analysing the Current Activities in the Field of UAV. Technical Report, ENTR/2007/065. 2007. Available online: https://ec.europa.eu/home-affairs (accessed on 20 March 2021).
- Small Unmanned Air System (SUAS) Assessment. Available online: https://www.airproxboard.org.uk/Reports-and-analysis/Airprox-reports-2018/ (accessed on 18 March 2021).
- Goppert, J.M.; Wagoner, A.R.; Schrader, D.K.; Ghose, S.; Kim, Y.; Park, S.; Gomez, M.; Matson, E.T.; Hopmeier, M.J. Realization of an autonomous, air-to-air Counter Unmanned Aerial System (CUAS). In Proceedings of the 2017 First IEEE International Conference on Robotic Computing (IRC), Taichung, Taiwan, 10–12 April 2017; pp. 235–240. [Google Scholar]
- Koubaa, A.; Allouch, A.; Alajlan, M.; Javed, Y.; Belghith, A.; Khalgui, M. Micro air vehicle link (mavlink) in a nutshell: A survey. IEEE Access 2019, 7, 87658–87680. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M. A Constructive DIREST Security Threat Modeling for Drone as a Service. J. Digit. Forensics Secur. Law 2021, 16, 2. [Google Scholar]
- Choudhary, G.; Sharma, V.; You, I.; Yim, K.; Chen, R.; Cho, J.H. Intrusion detection systems for networked unmanned aerial vehicles: A survey. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 560–565. [Google Scholar]
- Tseng, C.Y.; Balasubramanyam, P.; Ko, C.; Limprasittiporn, R.; Rowe, J.; Levitt, K. A specification-based intrusion detection system for AODV. In Proceedings of the 1st ACM Workshop on Security of Ad Hoc and Sensor Networks, Fairfax, VA, USA, October 2003; pp. 125–134. [Google Scholar]
- Vaidya, V. Dynamic Signature Inspection-Based Network Intrusion Detection. U.S. Patent 6,279,113, 21 August 2001. [Google Scholar]
- Patcha, A.; Park, J.M. An overview of anomaly detection techniques: Existing solutions and latest technological trends. Comput. Netw. 2007, 51, 3448–3470. [Google Scholar] [CrossRef]
- Aydın, M.A.; Zaim, A.H.; Ceylan, K.G. A hybrid intrusion detection system design for computer network security. Comput. Electr. Eng. 2009, 35, 517–526. [Google Scholar] [CrossRef]
- Sharma, V.; Choudhary, G.; Ko, Y.; You, I. Behavior and vulnerability assessment of drones-enabled industrial internet of things (iiot). IEEE Access 2018, 6, 43368–43383. [Google Scholar] [CrossRef]
- Birnbaum, Z.; Dolgikh, A.; Skormin, V.; O’Brien, E.; Muller, D.; Stracquodaine, C. Unmanned aerial vehicle security using behavioral profiling. In Proceedings of the 2015 International Conference on Unmanned Aircraft Systems (ICUAS), Denver, CO, USA, 9–12 June 2015; pp. 1310–1319. [Google Scholar]
- Birnbaum, Z.; Dolgikh, A.; Skormin, V.; O’Brien, E.; Muller, D.; Stracquodaine, C. Unmanned aerial vehicle security using recursive parameter estimation. J. Intell. Robot. Syst. 2016, 84, 107–120. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Ansari, N. A hierarchical detection and response system to enhance security against lethal cyber-attacks in UAV networks. IEEE Trans. Syst. Man Cybern. Syst. 2017, 48, 1594–1606. [Google Scholar] [CrossRef]
- Choudhary, G.; Sharma, V.; Gupta, T.; Kim, J.; You, I. Internet of drones (iod): Threats, vulnerability, and security perspectives. arXiv 2018, arXiv:1808.00203. [Google Scholar]
- Fox-Brewster, T. Maldrone: Watch Malware That Wants To Spread Its Wings Kill A Drone Mid-Flight. Forbes Magazine. 27 January 2015. Available online: http://www.forbes.com/sites/bernardmarr/2015/09/01/7-technologytrends-that-will-make-or-break-many-careers/ (accessed on 22 March 2021).
- Javaid, A.Y.; Sun, W.; Devabhaktuni, V.K.; Alam, M. Cyber security threat analysis and modeling of an unmanned aerial vehicle system. In Proceedings of the 2012 IEEE Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 13–15 November 2012; pp. 585–590. [Google Scholar]
- Chabukswar, R. Secure Detection in Cyberphysical Control Systems. Available online: https://chabukswar.in/projects/thesis.pdf (accessed on 10 March 2021).
- Altawy, R.; Youssef, A.M. Security, privacy, and safety aspects of civilian drones: A survey. ACM Trans. Cyber Phys. Syst. 2016, 1, 1–25. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.; Al-Hazemi, F. Drone Disrupted Denial of Service Attack (3DOS): Towards an Incident Response and Forensic Analysis of Remotely Piloted Aerial Systems (RPASs). In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 704–710. [Google Scholar]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K. RPAS Forensic Validation Analysis Towards a Technical Investigation Process: A Case Study of Yuneec Typhoon H. Sensors 2019, 19, 3246. [Google Scholar] [CrossRef] [PubMed]
- Salamh, F.E.; Mirza, M.M.; Karabiyik, U. UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies. Electronics 2021, 10, 733. [Google Scholar] [CrossRef]
- DatCon Downloads. Available online: https://datfile.net/DatCon/downloads.html (accessed on 18 March 2021).
- Jain, U.; Rogers, M.; Matson, E.T. Drone forensic framework: Sensor and data identification and verification. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–6. [Google Scholar]
- Armando, A.; Henauer, M.; Rigoni, A. Next, Generation CERTs; IOS Press: Amsterdam, The Netherlands, 2019; Volume 54. [Google Scholar]
- Watson, S. Drone Forensic Program. Available online: https://dfrws.org/wp-content/uploads/2019/06/pres_drone_forensics_program.pdf (accessed on 1 March 2021).
- Martin, L. Cyber Kill Chain®. Available online: http://cyber.lockheedmartin.com/hubfs/GainingtheAdvantageCyberKillChain.pdf (accessed on 3 May 2021).
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K.; Matson, E.T. Unmanned Aerial Vehicle Kill Chain: Purple-Teaming Tactics. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Virtual Conference, 27–30 January 2021; pp. 1081–1087. [Google Scholar]
- Clark, D.R.; Meffert, C.; Baggili, I.; Breitinger, F. DROP (DRone Open source Parser) your drone: Forensic analysis of the DJI Phantom III. Digit. Investig. 2017, 22, S3–S14. [Google Scholar] [CrossRef]
- V3.CSV Column Descriptions. Available online: http://www.datfile.net/DatCon/fieldsV3.html (accessed on 16 March 2021).


| Purpose | Software Tool | Version |
|---|---|---|
| Fingerprinting | Nmap | 7.80 |
| Network Sniffing | Wireshark | 3.2.4 |
| Gain Access | Metasploit Framework | 5.0 |
| Escalation of Privilege (install and modify data) | Kali Linux Commands | 2020.2 |
| Evaluation/Attack Lifecycle | Detection | Prevention | Response |
|---|---|---|---|
| Reconnaissance | ✓ | ✓ | ✓ |
| Weaponization | ✓ | N/A | ✓ |
| Delivery | ✓ | ✓ | ✓ |
| Exploitation | ✓ | N/A | ✓ |
| Privilege Escalation | ✓ | N/A | ✓ |
| Operation Interruption | X | ✓ | ✓ |
| Anti-detection & Anti-forensic | ✓ | ✓ | ✓ |
| Data Exfiltration & Tempering | ✓ | ✓ | ✓ |
| Command & Control | X | ✓ | ✓ |
| File Name | MD5 Hash Value (1st Attempt) | MD5 Hash Value (2nd Attempt) |
|---|---|---|
| 0 | 2601969f36bd0d59d1cc3624361c5730 | 2b36f21fcfced76ca36e9fe87ec8b08b |
| 1 | 741f5bda2f425fc925e3fda798718e63 | 741f5bda2f425fc925e3fda798718e63 |
| 2 | ccc366d53cda2507ef3ae7e0a4568462 | ccc366d53cda2507ef3ae7e0a4568462 |
| 3 | 6b53a66e3ada5a9cd9ca491be48676ea | 6b53a66e3ada5a9cd9ca491be48676ea |
| 4 | ded81b528dd9cd38d11e0a6955a95301 | ded81b528dd9cd38d11e0a6955a95301 |
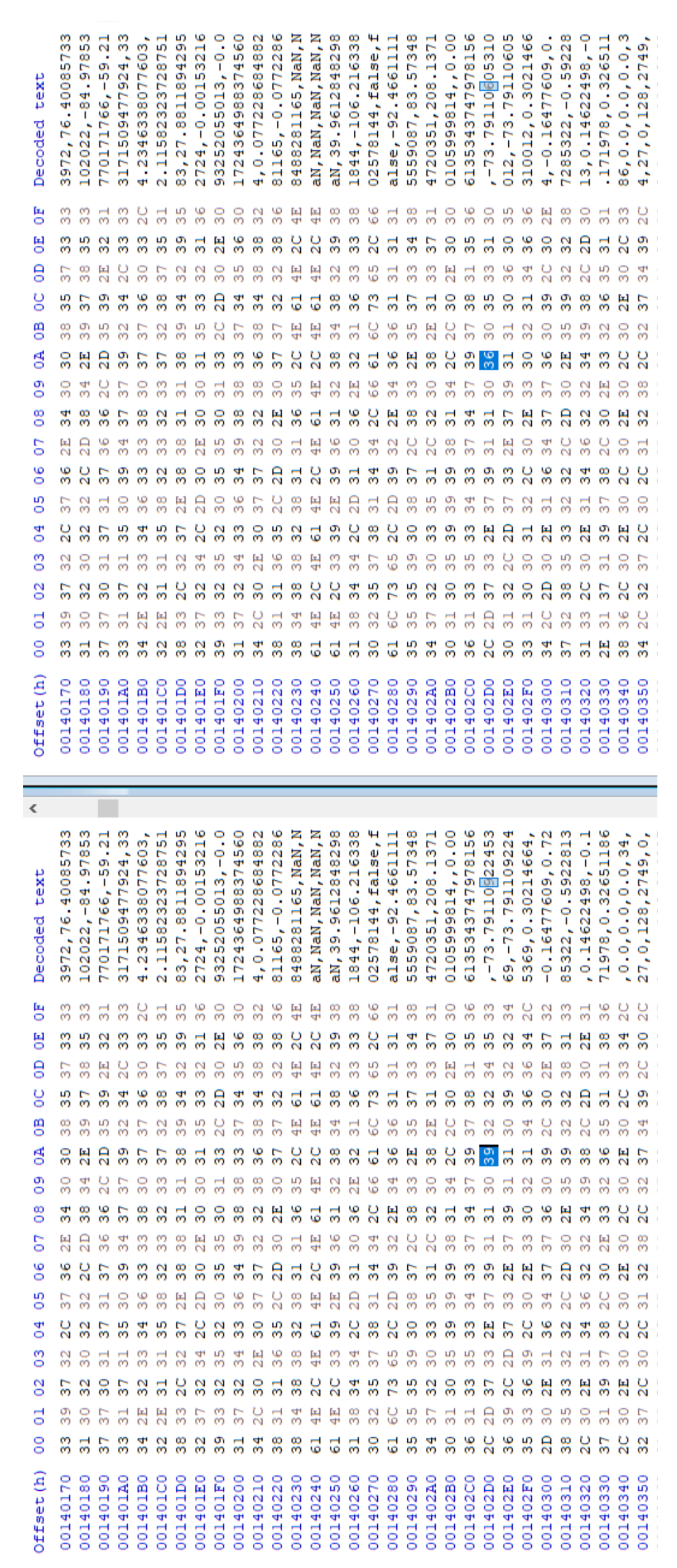
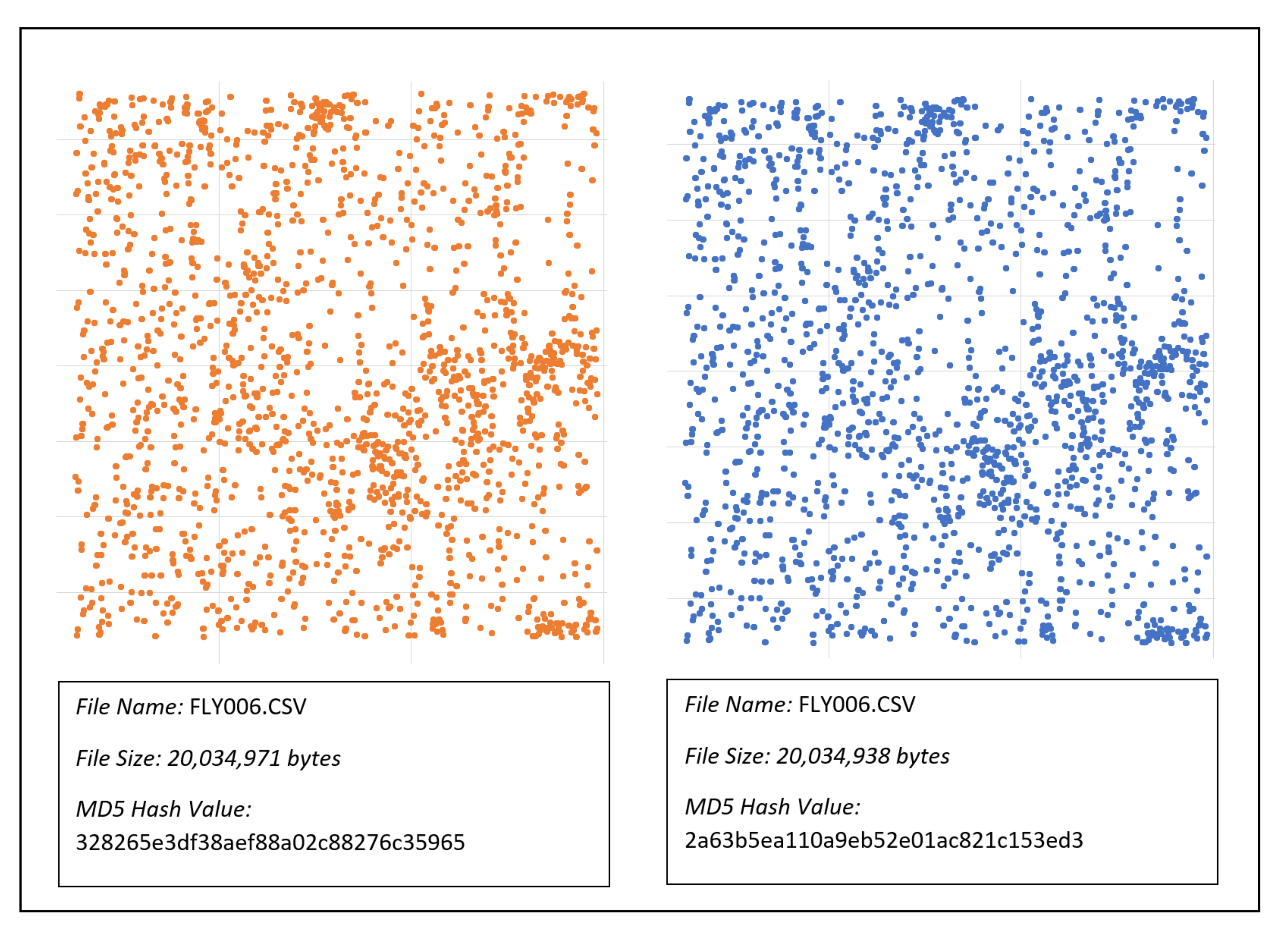
| 6 | 328265e3df38aef88a02c88276c35965 | 2a63b5ea110a9eb52e01ac821c153ed3 |
| 7 | 72f861e485392b1baeebccb4352bdfa3 | 72f861e485392b1baeebccb4352bdfa3 |
| 8 | 72adbc023cdda648da869b4f2c259072 | 72adbc023cdda648da869b4f2c259072 |
| 9 | b200e480194e2f85b2ce6b8553fbceb2 | b200e480194e2f85b2ce6b8553fbceb2 |
| 10 | 49dd94e6c3bf5c2e353255817c4641b0 | 671ef418fd30485807a7838285574723 |
| 11 | d79f99896fe5f6c36d904802189b7605 | d79f99896fe5f6c36d904802189b7605 |
| 12 | 42ce82bc1924724a8adefbf6e63c23d7 | 42ce82bc1924724a8adefbf6e63c23d7 |
| 13 | 7126cef458de088d62bcc6051b22d7d7 | 7126cef458de088d62bcc6051b22d7d7 |
| 14 | 496edcd1ea228fa97f1efe029ebba860 | 496edcd1ea228fa97f1efe029ebba860 |
| 15 | 4496fb7a4d63b2fa7fbf01940b2d0d93 | 4496fb7a4d63b2fa7fbf01940b2d0d93 |
| 16 | 44b03594b87089979033f9044155d77e | 44b03594b87089979033f9044155d77e |
| 17 | 8a5348afdca2ffc90f1dd50bdeef7820 | 8a5348afdca2ffc90f1dd50bdeef7820 |
| 18 | a441434fbecb87e451b134a606831120 | a441434fbecb87e451b134a606831120 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Salamh, F.E.; Karabiyik, U.; Rogers, M.K.; Matson, E.T. A Comparative UAV Forensic Analysis: Static and Live Digital Evidence Traceability Challenges. Drones 2021, 5, 42. https://doi.org/10.3390/drones5020042
Salamh FE, Karabiyik U, Rogers MK, Matson ET. A Comparative UAV Forensic Analysis: Static and Live Digital Evidence Traceability Challenges. Drones. 2021; 5(2):42. https://doi.org/10.3390/drones5020042
Chicago/Turabian StyleSalamh, Fahad E., Umit Karabiyik, Marcus K. Rogers, and Eric T. Matson. 2021. "A Comparative UAV Forensic Analysis: Static and Live Digital Evidence Traceability Challenges" Drones 5, no. 2: 42. https://doi.org/10.3390/drones5020042
APA StyleSalamh, F. E., Karabiyik, U., Rogers, M. K., & Matson, E. T. (2021). A Comparative UAV Forensic Analysis: Static and Live Digital Evidence Traceability Challenges. Drones, 5(2), 42. https://doi.org/10.3390/drones5020042







