Social Engineering—The Hidden Control †
Abstract
1. Introduction
2. Methods
- 1.
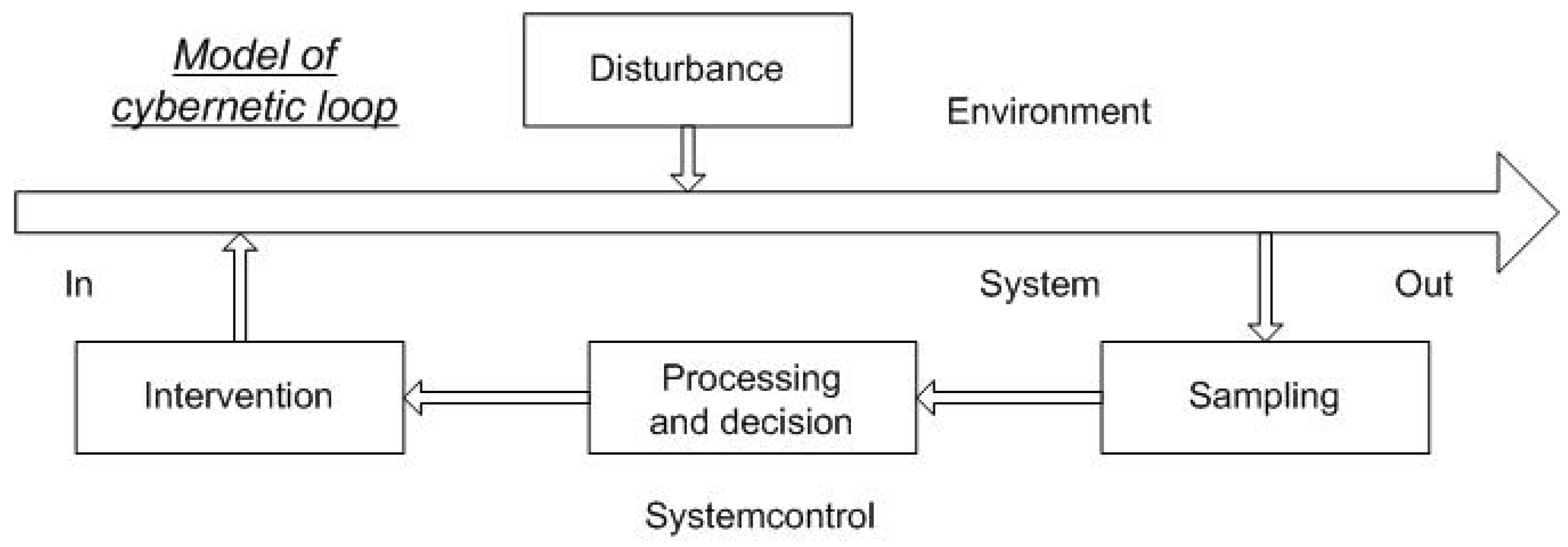
- It is worth simplifying the cybernetic loop model:
- a.
- The processes that interact with and independently of the system must be identified;
- b.
- The direction of signal flow for interacting with the system must be identified;
- 2.
- The processes of social engineering should be generalized from the aspect of the resulting simplified model:
- a.
- The processes that interact with and independently of the system must be identified;
- b.
- The social engineering toolkit needs to be typified in terms of interactivity;
- c.
- The direction of signal flow for interacting with the system must be identified;
- 3.
- The process model of social engineering should be synthesized according to the model of the cybernetic loop.
3. Results
- Based on the operational process of the cybernetic loop, the operational phases of social engineering can be identified;
- Based on the elements of the model of cybernetic loop, the toolbox of social engineering can be grouped and typified;
- Using the typified toolkit, the direction of signal flow could be determined;
- The process model of social engineering could be synthesized based on the model of the cybernetic loop.
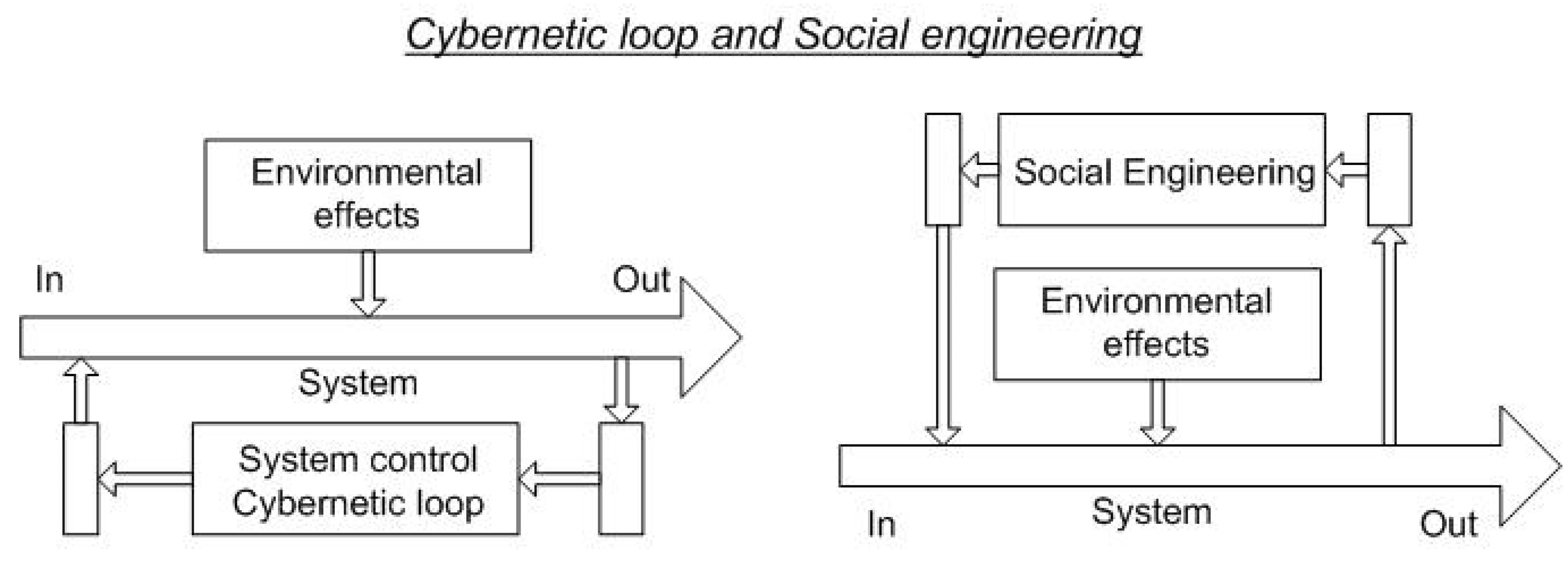
- The logical process of social engineering can be paralleled with the process of regulation;
- Based on the parallelism, social engineering is a manifestation of regulation;
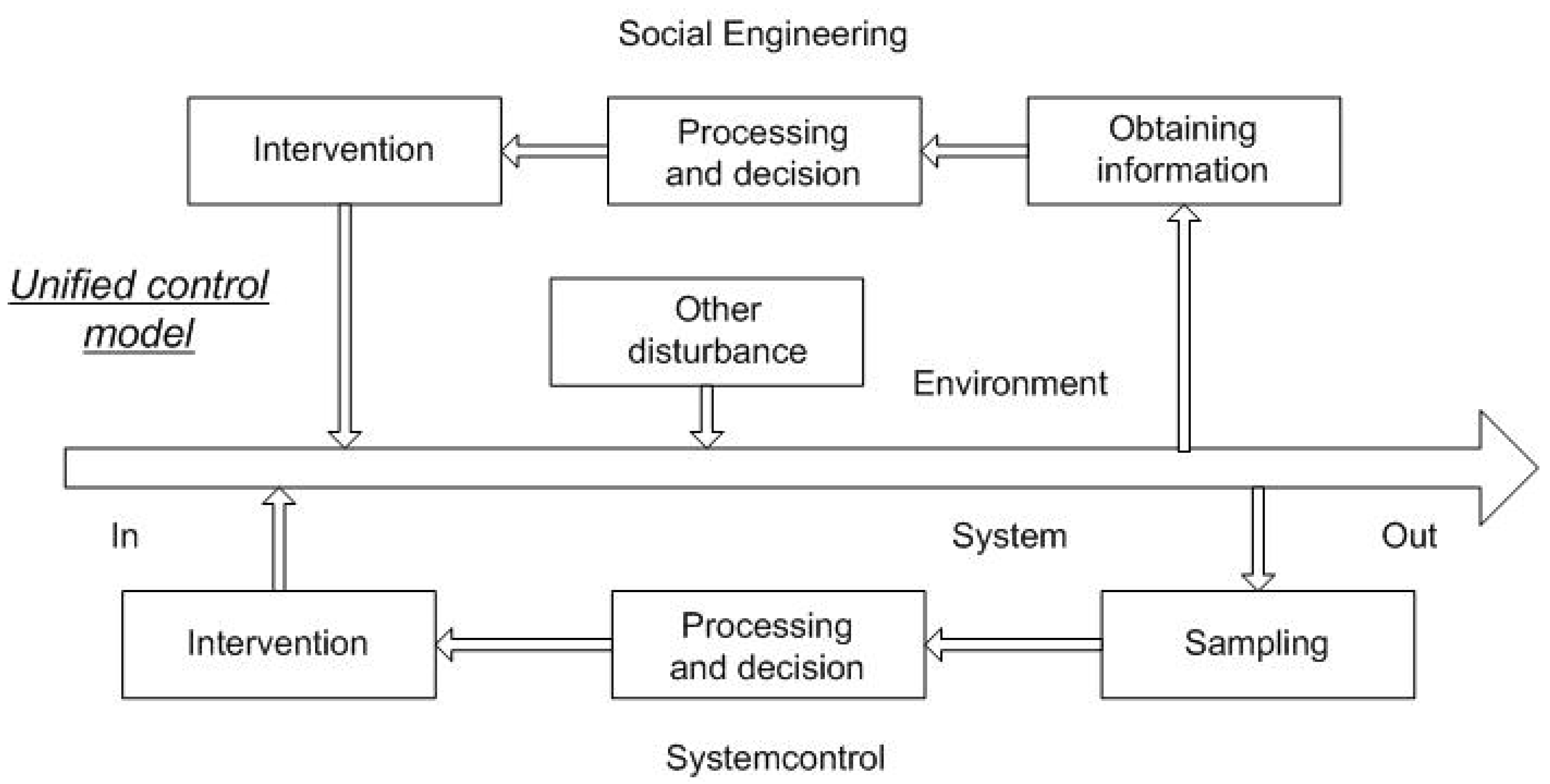
- As social engineering can be understood as a manifestation of regulation, it can be incorporated into the model of the cybernetic loop, which results in a unified process model;
- Based on the unified process model, a cybernetic definition of social engineering can be given.
4. Discussion
4.1. Cybernetic Loop
4.2. Social Engineering
- Techniques for obtaining information: impersonation, shoulder surfing, dumpster diving, piggybacking, tailgating, scam, phishing, baiting, and OSINT (Open-source intelligence);
- As the method of data processing and decision making is completely independent of the implementation of the system, the same central technologies can be used to control system and social engineering. However, in the case of the use of distributed technologies, there is a high probability that the hidden state will disappear. Thus, manual correlation search technologies, data warehousing solutions, the use of artificial intelligence, and central decision systems can also be mentioned here;
- Intervention techniques: asking for help, providing help, taking advantage of reciprocity, impersonation, piggybacking, tailgating, scam, phishing, DNS-based (Domain Name System based) attacks, whaling-type attacks, and baiting.
4.3. The Paralell
4.4. Model and Definition
5. Conclusions
Conflicts of Interest
References
- Albini, A.; Rajnai, Z. Modeling general energy balance of systems. Procedia Manuf. 2019, 32, 374–379. [Google Scholar] [CrossRef]
- Kasac, J.; Stefancic, H.; Stepanic, J. Comparison of social and physical free energies on a toy model. Phys. Rev. E 2004, 70, 016117. [Google Scholar] [CrossRef] [PubMed]
- Kiss, M.; Breda, G.; Muha, L. Information security aspects of Industry 4.0. Procedia Manuf. 2019, 32, 848–855. [Google Scholar] [CrossRef]
- Tokody, D. Digitising the European industry—Holonic systems approach. Procedia Manuf. 2018, 22, 1015–1022. [Google Scholar] [CrossRef]
- Kiss, M.; Muha, L. The Cybersecurity Capability Aspects of Smart Government and Industry 4.0 Programmes. Interdiscip. Descr. Complex Syst. 2018, 16, 313–319. [Google Scholar] [CrossRef]
- Tokody, D.; Schuszter, G.; Papp, J. Study of How to Implement an Intelligent Railway System in Hungary. In Proceedings of the IEEE 13th International Symposium on Intelligent Systems and Informatics (SISY 2015), Subotica, Serbia, 17–19 September 2015. [Google Scholar]
- Szabó, Z. The effects of globalization and cyber security on smart cities. Interdiscip. Descr. Complex Syst. 2019, 17, 503–510. [Google Scholar] [CrossRef]
- Pető, R. Security of Smart City. Interdiscip. Descr. Complex Syst. 2019, 17, 13–19. [Google Scholar] [CrossRef]
- Albini, A.; Rajnai, Z. General Architecture of Cloud. Procedia Manuf. 2018, 22, 485–490. [Google Scholar] [CrossRef]
- Albini, A.; Tokody, D.; Rajnai, Z. Theoretical Study of Cloud Technologies. Interdiscip. Descr. Complex Syst. 2019, 17, 511–519. [Google Scholar] [CrossRef]
- Mester, G. Obstacle Avoidance and Velocity Control of Mobile Robots. In Proceedings of the 6th International Symposium on Intelligent Systems and Informatics (SISY 2008), Subotica, Serbia, 26–27 September 2008. [Google Scholar]
- Mester, G.; Rodic, A. Sensor-Based Intelligent Mobile Robot Navigation in Unknown Environments. Int. J. Electr. Comput. Eng. Syst. 2010, 2, 1–8. [Google Scholar]
- Kovács, Z. Cloud Security in Terms of the Law Enforcement Agencies. Hadmérnök 2012, 7, 144–156. [Google Scholar]
- Rodic, A.; Jovanovic, M.; Popic, S.; Mester, G. Scalable Experimental Platform for Research, Development and Testing of Networked Robotic Systems in Informationally Structured Environments. In Proceedings of the 2011 IEEE Workshop on Robotic Intelligence in Informationally Structured Space, Paris, France, 11–15 April 2011. [Google Scholar]
- Mester, G. Rankings Scientists, Journals and Countries Using h-index. Interdiscip. Descr. Complex Syst. 2016, 14, 1–9. [Google Scholar] [CrossRef]
- Dobrilovic, D.; Odadzic, B. Virtualization Technology as a Tool for Teaching Computer Networks. Int. J. Educ. Pedagog. Sci. 2008, 13, 41–45. [Google Scholar]
- Mester, G. Academic Ranking of World Universities 2009/2010. IPSI J. Trans. Internet Res. 2011, 7, 44–47. [Google Scholar]
- Szabó, A.; Szucs, E.; Berek, T. Illustrating Training Opportunities Related to Manpower Facility Protection through the Example of Máv Co. Interdiscip. Descr. Complex Syst. 2018, 16, 320–326. [Google Scholar] [CrossRef]
- Mester, G.; Pletl, S.; Nemes, A.; Mester, T. Structure Optimization of Fuzzy Control Systems by Multi-Population Genetic Algorithm. In Proceedings of the 6th European Congress on Intelligent Techniques and Soft Computing (EUFIT ’98), Aachen, Germany, 7–10 September 1998; pp. 450–456. [Google Scholar]
- Mester, G.; Rodic, A. Simulation of Quad-rotor Flight Dynamics for the Analysis of Control, Spatial Navigation and Obstacle Avoidance. In Proceedings of the 3rd International Workshop on Advanced Computational Intelligence and Intelligent Informatics (IWACIII 2013), Shanghai, China, 18–21 October 2013; pp. 1–4. [Google Scholar]
- Albini, A.; Mester, G.; Iantovics, B.L. Unified Aspect Search Algorithm. Interdiscip. Descr. Complex Syst. 2019, 17, 20–25. [Google Scholar] [CrossRef]
- Zamfirescu, C.B.; Duta, L.; Iantovics, L.B. The Cognitive Complexity in Modelling the Group Decision Process. Brain Broad Res. Artif. Intell. Neurosci. 2010, 1, 69–79. [Google Scholar]
- Mester, G.; Pletl, S.; Pajor, G.; Basic, D. Adaptive Control of Rigid-Link Flexible-Joint Robots. In Proceedings of the 3rd International Workshop of Advanced Motion Control, Berkeley, CA, USA, 20–23 March 1994; pp. 593–602. [Google Scholar]
- Albininé Budavári, E.; Rajnai, Z. The Role of Additional Information in Obtaining information. Interdiscip. Descr. Complex Syst. 2019, 3-A, 438–443. [Google Scholar] [CrossRef]
- Hell, P.M.; Varga, P.J. Drone systems for factory security and surveillance. Interdiscip. Descr. Complex Syst. 2019, 17, 458–467. [Google Scholar] [CrossRef]
- Shatnawi, M.M. Applying Information Security Risk Management Standards Process for Automated Vehicles. Bánki Rep. 2019, 2, 70–74. [Google Scholar]
- Tokody, D.; Flammini, F. Smart Systems for the Protection of Individuals. Key Eng. Mater. 2017, 755, 190–197. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Budavári, E.A.; Rajnai, Z. Social Engineering—The Hidden Control. Proceedings 2020, 63, 60. https://doi.org/10.3390/proceedings2020063060
Budavári EA, Rajnai Z. Social Engineering—The Hidden Control. Proceedings. 2020; 63(1):60. https://doi.org/10.3390/proceedings2020063060
Chicago/Turabian StyleBudavári, Edina Albininé, and Zoltán Rajnai. 2020. "Social Engineering—The Hidden Control" Proceedings 63, no. 1: 60. https://doi.org/10.3390/proceedings2020063060
APA StyleBudavári, E. A., & Rajnai, Z. (2020). Social Engineering—The Hidden Control. Proceedings, 63(1), 60. https://doi.org/10.3390/proceedings2020063060




