Generation of Affine-Shifted S-Boxes with Constant Confusion Coefficient Variance and Application in the Partitioning of the S-Box Space
Abstract
1. Introduction
- Our generation method directly and quickly computes the S-boxes that have the same CCV as the initial S-box. There is no need for an extra computation to check the entire affine-shifted class. The level of resistance to side channel attacks that we provide is only in its theoretical form. However, because the property ensures minimal security in the first phase of the S-box design, then that level of practical applicability is embedded.
- Our proposal of partitioning the space of S-boxes in mega-classes (focused on the CCV property, instead of in the Hamming weight), is practical and applicable to heuristic methods and combinatorial optimization, to speed up the search, in the same manner as was carried out for Hamming weight classes [20,22]. Before this work, moving from an S-box solution to another S-box solution with the same CCV value was only possible if the move was inside the same Hamming weight class. In this work, we provide a new way of keeping the CCV value constant, with the addition of also keeping the NL value constant. In other words, having the mathematical definition of the CCV partition of the S-box space is not enough for a cipher designer to quickly obtain S-boxes with the same NL and CCV; the designer needs a generation method like ours.
- The previous points, (1) and (2), expose the technical novelty of our research.
- Our invariance statement is supported by several experiments. We consider this a theoretical result by itself that provides a new insight about the intersection between affine-shifted classes and the Hamming weight classes. Moreover, we provide another proposition where we outline a strong and novel theoretical result, also related with the intersection: we prove the existence of different Hamming weight classes in the affine-shifted set.
- Our contribution lies not in computational efficiency or generality but in structure and interpretation of the CCV landscape within this tractable class. We define the notion of CCV mega-classes, observe their empirical separation across Hamming weight classes, and propose that this structure can be used to guide or constrain S-box search algorithms. We acknowledge that this work may be considered exploratory and structural rather than a breakthrough in cryptographic design. In other words, we believe that identifying invariant metrics within subsets of S-boxes is a useful building block for future heuristic or evolutionary design strategies.
- Detailed experiments on 3-bit S-boxes were presented to analyze the joint and marginal probabilities of NL and CCV. We calculated those probabilities after generating and evaluating all the S-boxes from the entire S-box space; we did not follow any abstract or a pure math approach. In this particular case, the size of the space is computable and there are only two values for the NL property and there values for the CCV property, which helped us to obtain the insights. However, for bigger spaces like, for example, the 8-bit S-boxes, we think the combinatorial space is not computable with a personal computer, and the range of values for NL is big, but it is much bigger for CCV. The scope of our research ended in the simplest case.
1.1. Related Works
1.2. Basic Notions
2. Results: Generation of S-Boxes with the Same NL and CCV Values as an Arbitrary Initial S-Box
2.1. Balanced Case
2.2. Unbalanced Case
2.3. Cases Comparison
2.4. Invariance of the Confusion Coefficient Variance Under Affine-Shifted S-Boxes, and a Generation Method
- Preserves the number of pairs: ;
- Ensures that no pair is repeated;
- Covers all possible key pair combinations.
| Algorithm 1 Generation method. |
|
- Fix an S-box space of (, bits) or (, bits).
- Generation of tens of thousands of initial random S-boxes.
- For each initial random S-box, apply the generation method Algorithm 1 and obtain the resulting subset of affine-shifted S-boxes.
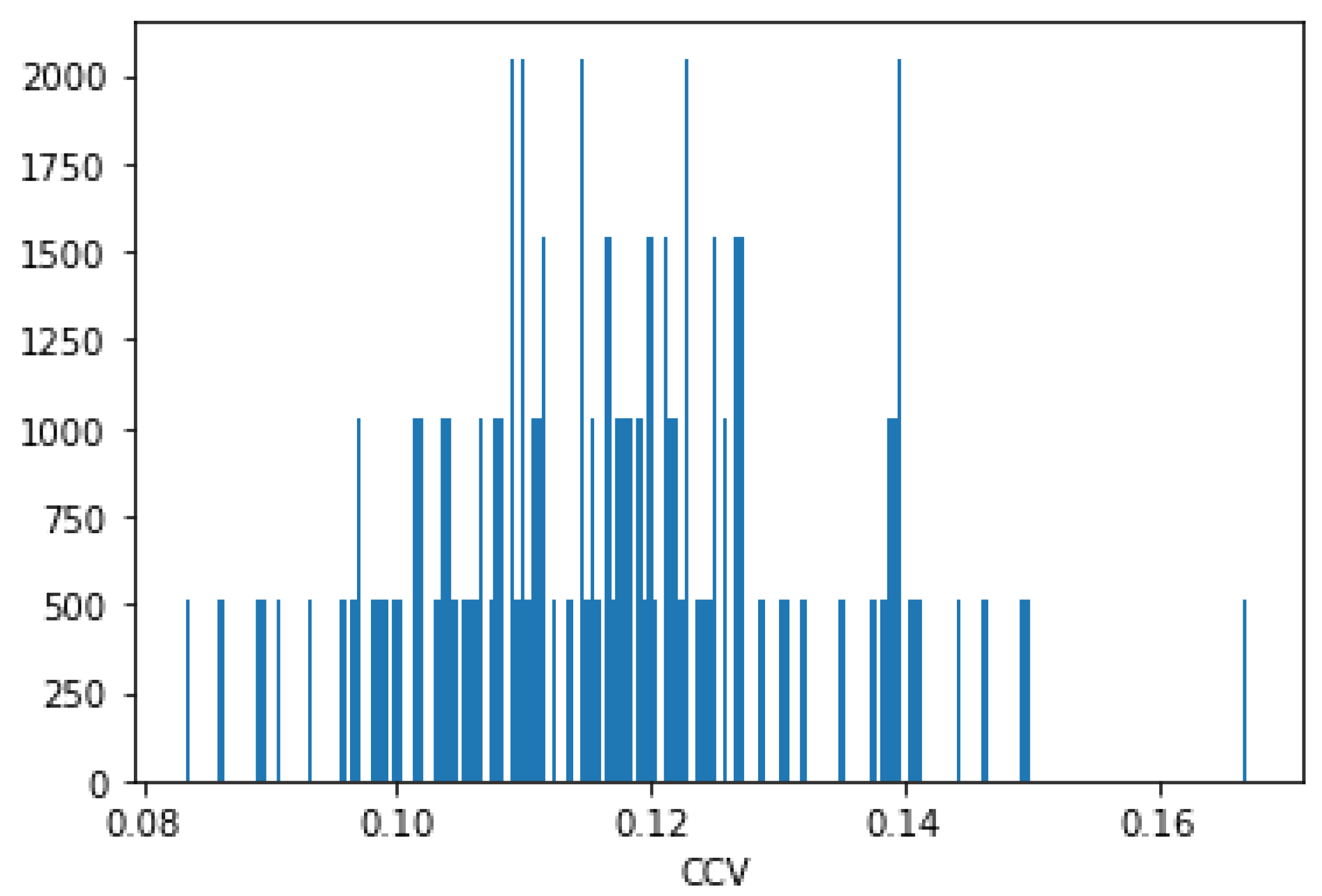
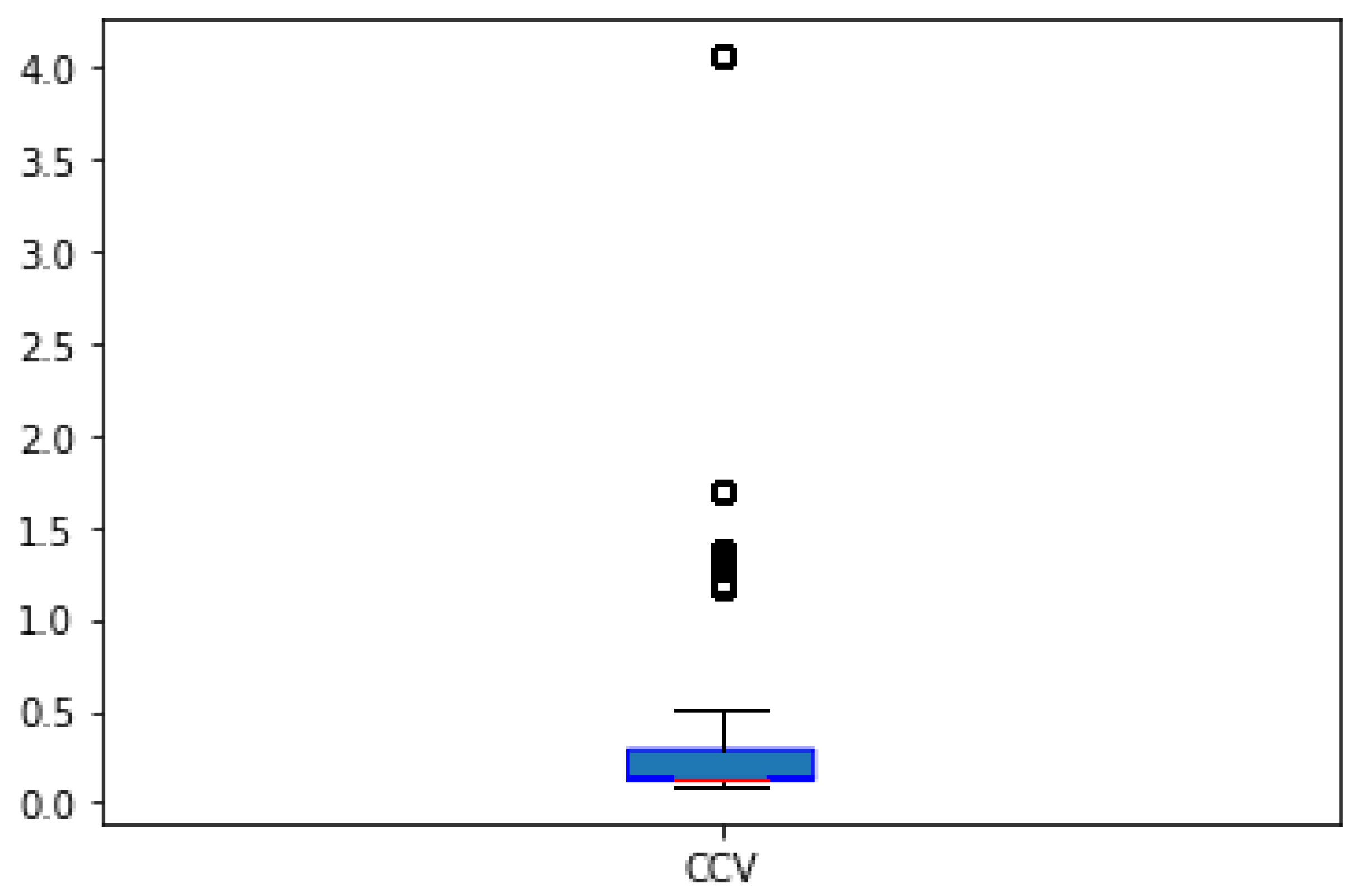
- Calculate the CCV of all the S-boxes that belong to the resulting subset.
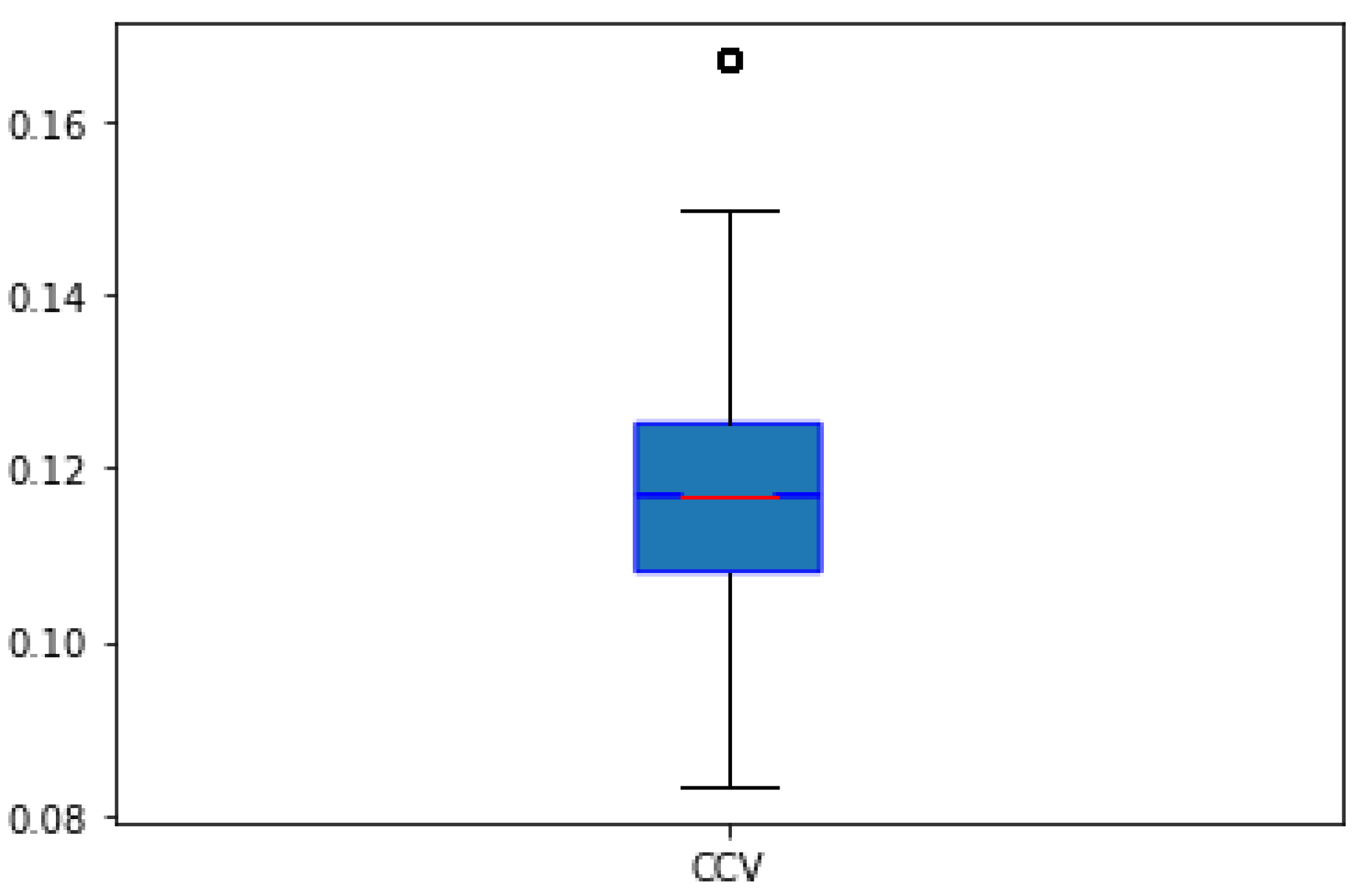
- Check if the CCV value stays constant and equal to the CCV of the initial S-box.
2.5. Generated S-Box Example
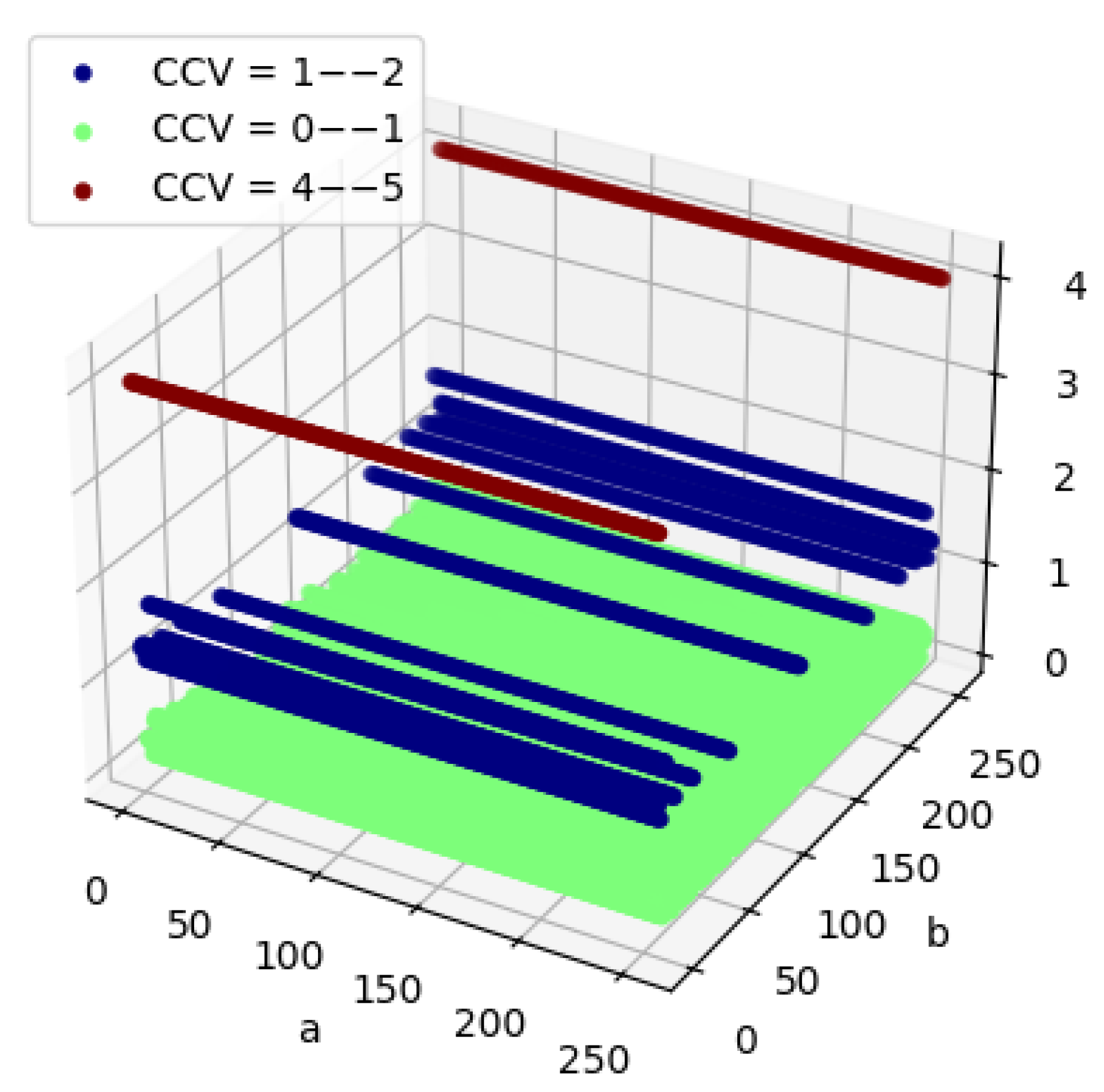
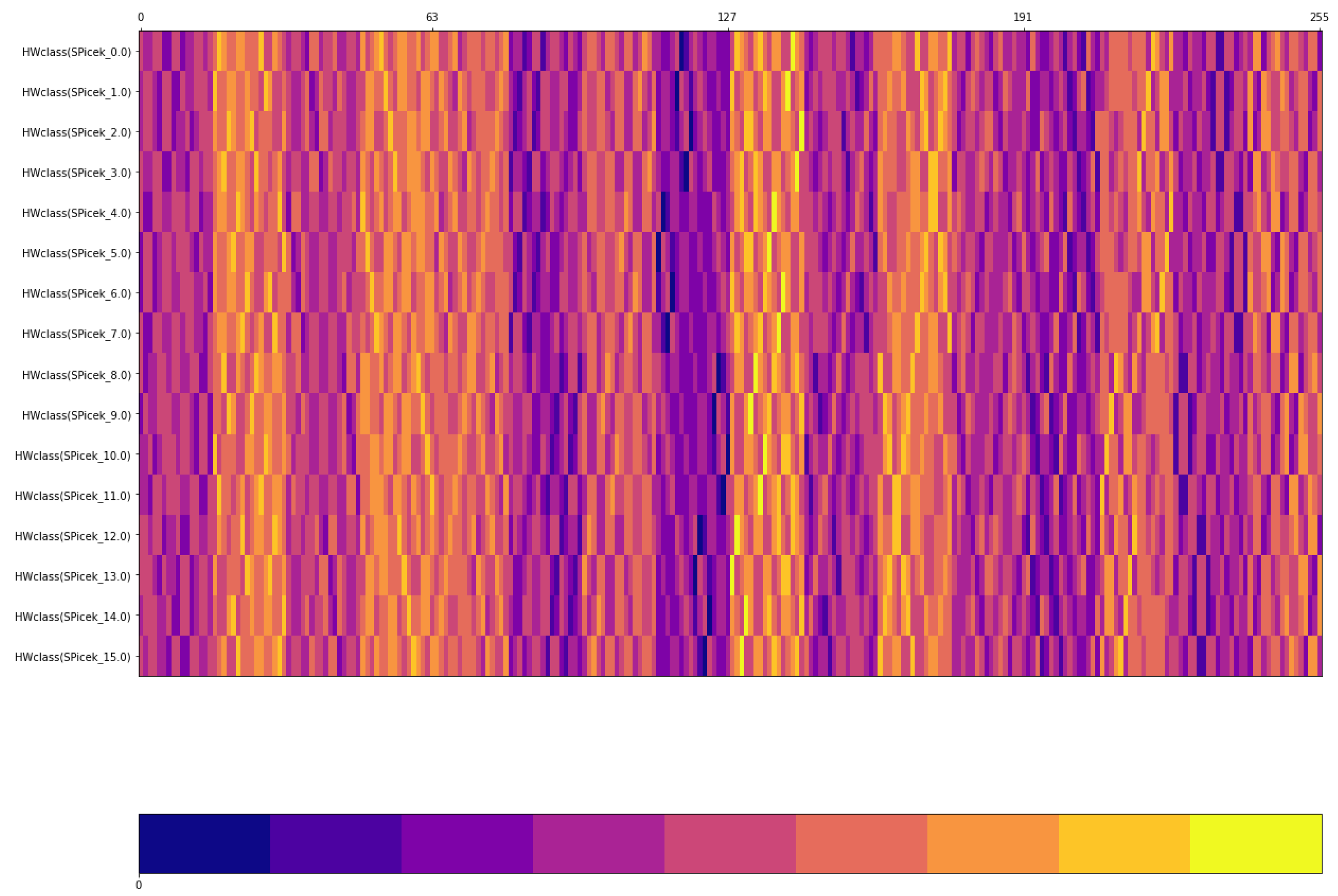
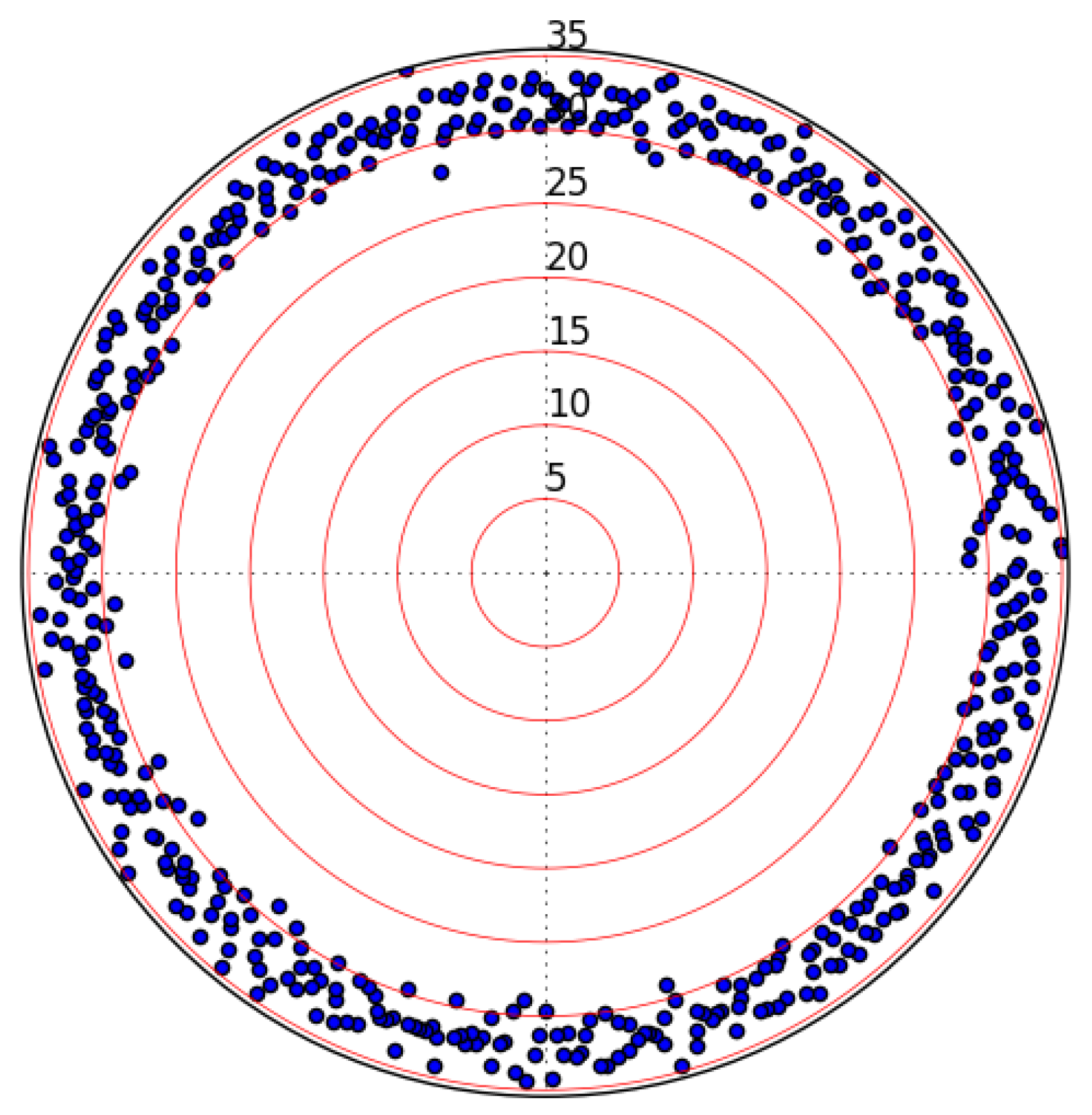
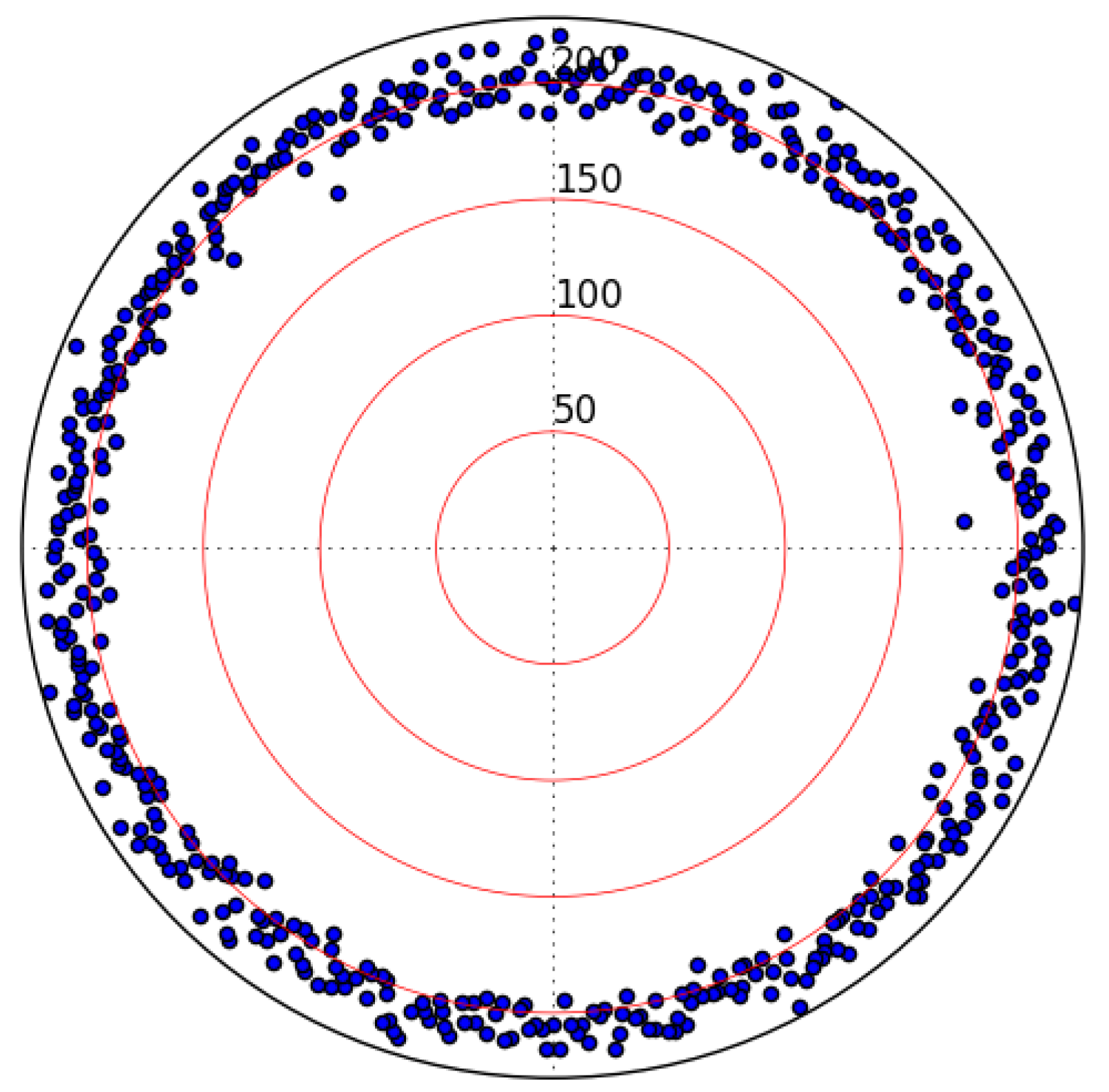
2.6. Hamming Weight Class Membership via Distance Analysis
2.7. Proof of Different Hamming Weight Classes for Affine-Shifted S-Boxes
2.8. Comparison of Strategies for Optimize NL and CCV
- For NL values and as for CCV values, most probabilities are the lowest they can be, and , which are not desirable in cryptographic terms.
- The lowest probable value, , is reserved for the higher values of NL and CCV simultaneously, which corresponds to good cryptographic properties.
- The conditional probability for the maximum NL given the maximum CCV, , is greater than the conditional probability for maximum CCV given the maximum NL, .
3. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Van Tilborg, H.C.; Jajodia, S. Encyclopedia of Cryptography and Security; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Naseer, M.; Tariq, S.; Riaz, N.; Ahmed, N.; Hussain, M. S-box Security Analysis of NIST Lightweight Cryptography Candidates: A Critical Empirical Study. arXiv 2024, arXiv:2404.06094. [Google Scholar]
- Al-Dweik, A.Y.; Hussain, I.; Saleh, M.; Mustafa, M. A novel method to generate key-dependent s-boxes with identical algebraic properties. J. Inf. Secur. Appl. 2022, 64, 103065. [Google Scholar] [CrossRef]
- Thakor, V.A.; Razzaque, M.A.; Darji, A.D.; Patel, A.R. A novel 5-bit S-box design for lightweight cryptography algorithms. J. Inf. Secur. Appl. 2023, 73, 103444. [Google Scholar] [CrossRef]
- Cerini, S.Y. Empirical Evaluation of the Resilience of Novel s-Box Implementations Against Power Side-Channel Attacks. Ph.D. Thesis, Politecnico di Torino, Turin, Italy, 2021. [Google Scholar]
- Carlet, C.; Ding, C. Nonlinearities of S-boxes. Finite Fields Their Appl. 2007, 13, 121–135. [Google Scholar] [CrossRef]
- Picek, S.; Papagiannopoulos, K.; Ege, B.; Batina, L.; Jakobovic, D. Confused by Confusion: Systematic Evaluation of DPA Resistance of Various S-boxes. In Progress in Cryptology—INDOCRYPT 2014, Proceedings of the 15th International Conference on Cryptology, New Delhi, India, 14–17 December 2014, Proceedings; Meier, W., Mukhopadhyay, D., Eds.; Springer: Cham, Switzerland, 2014; pp. 374–390. [Google Scholar] [CrossRef]
- Nyberg, K. Differentially uniform mappings for cryptography. In Advances in Cryptology—EUROCRYPT ’93, Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Lofthus, Norway, 23–27 May 1993 Proceedings; Helleseth, T., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; pp. 55–64. [Google Scholar] [CrossRef]
- Picek, S. Applications of Evolutionary Computation to Cryptology. Doctoral Dissertation, University of Zagreb, Zagreb, Croatia, 2015. [Google Scholar]
- Picek, S.; Jakobovic, D. Evolutionary computation and machine learning in cryptology. In Proceedings of the Genetic and Evolutionary Computation Conference Companion, Lille, France, 10–14 July 2021; GECCO ’21. pp. 1089–1118. [Google Scholar] [CrossRef]
- Mariot, L.; Jakobovic, D.; Bäck, T.; Hernandez-Castro, J. Artificial Intelligence for the Design of Symmetric Cryptographic Primitives. In Security and Artificial Intelligence: A Crossdisciplinary Approach; Springer International Publishing: Cham, Switzerland, 2022; pp. 3–24. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Poluyanenko, N.; Frontoni, E.; Arnesano, M.; Smirnov, O. Evolutionary Approach to S-box Generation: Optimizing Nonlinear Substitutions in Symmetric Ciphers. arXiv 2024, arXiv:2407.03510. [Google Scholar]
- de la Cruz Jiménez, R.A. On some methods for constructing almost optimal S-Boxes and their resilience against side-channel attacks. IACR. 2018. Available online: https://eprint.iacr.org/2018/618.pdf (accessed on 8 June 2025).
- Carlet, C.; Djurasevic, M.; Jakobovic, D.; Mariot, L.; Picek, S. Evolving constructions for balanced, highly nonlinear boolean functions. In Proceedings of the Genetic and Evolutionary Computation Conference, Boston, MA, USA, 9–13 July 2022; GECCO ’22. pp. 1147–1155. [Google Scholar] [CrossRef]
- Mariot, L.; Picek, S.; Jakobovic, D.; Djurasevic, M.; Leporati, A. Evolutionary Construction of Perfectly Balanced Boolean Functions. In Proceedings of the 2022 IEEE Congress on Evolutionary Computation (CEC), Padua, Italy, 18–23 July 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Kim, G.; Kim, H.; Heo, Y.; Jeon, Y.; Kim, J. Generating cryptographic s-boxes using the reinforcement learning. IEEE Access 2021, 9, 83092–83104. [Google Scholar] [CrossRef]
- Díaz, I.M. Búsqueda Local de S-Cajas con Alta Varianza del Coeficiente de Confusión. Master’s Thesis, Universidad de la Habana Havana, La Habana, Cuba, 2019. [Google Scholar]
- Martínez-Díaz, I.; Legón-Pérez, C.M.; Rojas, O.; Sosa-Gómez, G.; Oliva, D. Local Search Trajectories over S-box space. J. Inf. Secur. Appl. 2022, 69, 103272. [Google Scholar] [CrossRef]
- Leander, G.; Poschmann, A. On the Classification of 4 Bit S-Boxes. In Arithmetic of Finite Fields, Proceedings of the First International Workshop, WAIFI 2007, Madrid, Spain, 21–22 June 2007, Proceedings; Springer: Berlin/Heidelberg, Germany, 2007; pp. 159–176. [Google Scholar] [CrossRef]
- Legón-Pérez, C.M.; Sánchez-Muiña, R.; Miyares-Moreno, D.; Bardaji-López, Y.; Martínez-Díaz, I.; Rojas, O.; Sosa-Gómez, G. Search-Space Reduction for S-Boxes Resilient to Power Attacks. Appl. Sci. 2021, 11, 4815. [Google Scholar] [CrossRef]
- Baioletti, M.; Milani, A.; Santucci, V. An algebraic approach for the search space of permutations with repetition. In Evolutionary Computation in Combinatorial Optimization, Proceedings of the 20th European Conference, EvoCOP 2020, Held as Part of EvoStar 2020, Seville, Spain, 15–17 April 2020, Proceedings; Springer: Berlin/Heidelberg, Germany, 2020; pp. 18–34. [Google Scholar]
- Legón-Pérez, C.M.; Menéndez-Verdecía, J.A.; Martínez-Díaz, I.; Sosa-Gómez, G.; Rojas, O.; Veloz-Remache, G.d.R. Probabilistic Evaluation of the Exploration–Exploitation Balance during the Search, Using the Swap Operator, for Nonlinear Bijective S-Boxes, Resistant to Power Attacks. Information 2021, 12, 509. [Google Scholar] [CrossRef]
- Prouff, E. DPA attacks and S-boxes. In Fast Software Encryption, Proceedings of the 12th International Workshop, FSE 2005, Paris, France, 21–23 February 2005, Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2005; pp. 424–441. [Google Scholar]
- Chakraborty, K.; Sarkar, S.; Maitra, S.; Mazumdar, B.; Mukhopadhyay, D.; Prouff, E. Redefining the transparency order. Des. Codes Cryptogr. 2017, 82, 95–115. [Google Scholar] [CrossRef]
- Li, H.; Zhou, Y.; Ming, J.; Yang, G.; Jin, C. The Notion of Transparency Order, Revisited. Comput. J. 2020, 63, 1915–1938. [Google Scholar] [CrossRef]
- Khalid, I.; Hassan, Z.; Rasheed, H. The Effect of Affine and Extended Affine Equivalence Class Against Various Cryptographic Profile. In Proceedings of the 2024 21st International Bhurban Conference On Applied Sciences And Technology (IBCAST), Murree, Pakistan, 20–23 August 2024; pp. 576–583. [Google Scholar]
- Wang, Y.; Zhang, Z.; Zhang, L.Y.; Feng, J.; Gao, J.; Lei, P. A genetic algorithm for constructing bijective substitution boxes with high nonlinearity. Inf. Sci. 2020, 523, 152–166. [Google Scholar] [CrossRef]
- Kneževi´c, K. Combinatorial optimization in cryptography. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017; IEEE: New York, NY, USA, 2017; pp. 1324–1330. [Google Scholar] [CrossRef]
- Fei, Y.; Luo, Q.; Ding, A.A. A statistical model for DPA with novel algorithmic confusion analysis. In Cryptographic Hardware and Embedded Systems—CHES 2012, Proceedings of the 14th International Workshop, Leuven, Belgium, 9–12 September 2012, Proceedings; Lecture Notes in Computer Science Series (Including Subseries Lect. Notes Artif. Intell. Lect. Notes Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2012; Volume 7428, pp. 233–250. [Google Scholar] [CrossRef]
- Kim, J.; Picek, S.; Heuser, A.; Bhasin, S.; Hanjalic, A. Still Making Noise: Improving Deep Learning-based Side-channel Analysis. IEEE Design Test 2024, 42, 20–27. [Google Scholar] [CrossRef]



| Size of Bits | Size of the Subset |
|---|---|
| 4 | 30 |
| 8 | 510 |
| CCV = 0.27551 | CCV = 0.489796 | CCV = 1.13265 | Total | |
|---|---|---|---|---|
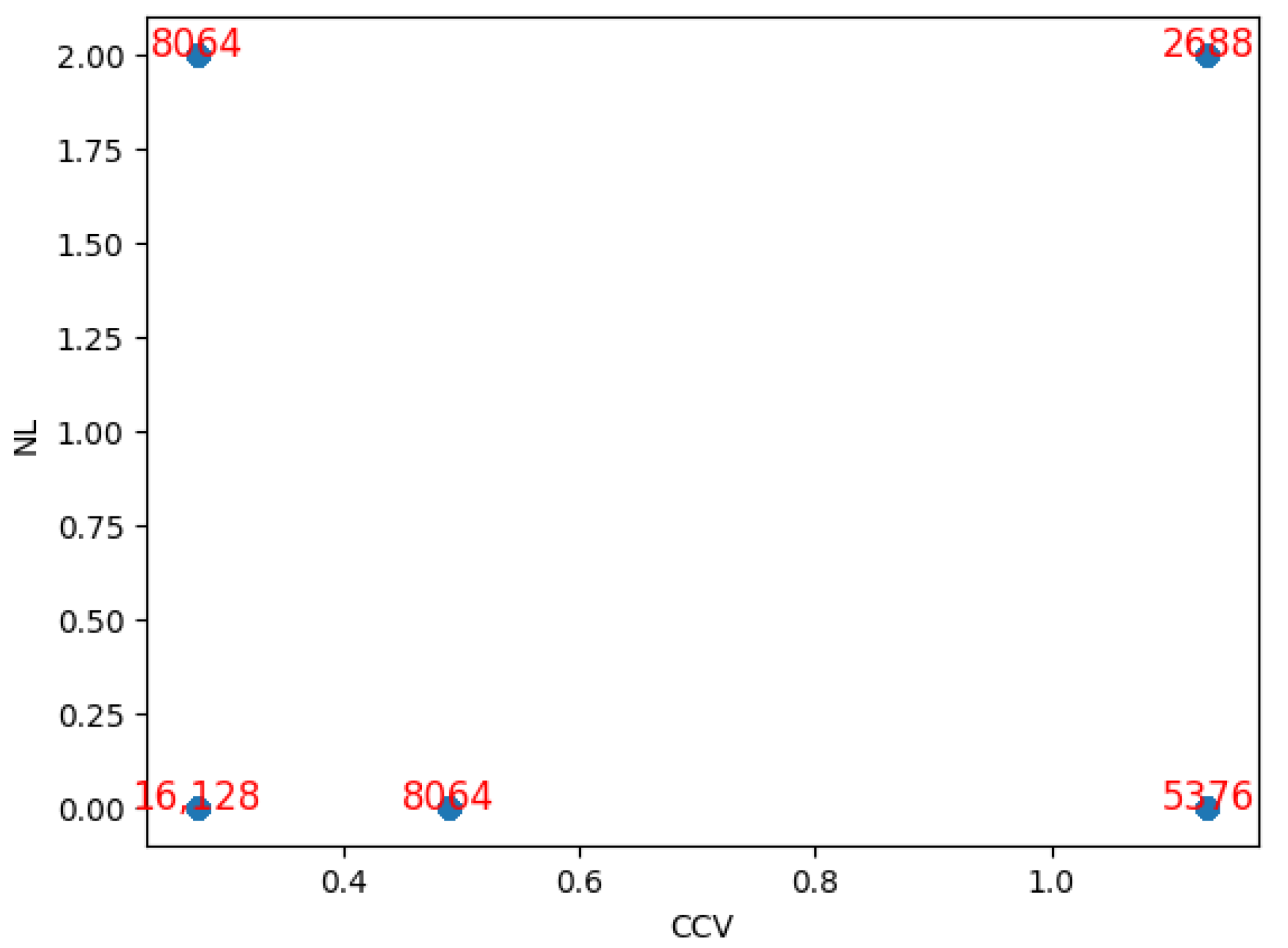
| NL = 2 | 8064 | 0 | 2688 | = 10,752 |
| NL = 0 | 16,128 | 8064 | 5376 | = 29,568 |
| Total | = 24,192 | = 8064 | 40,320 |
| CCV | 0.27551 | 0.489796 | 1.13265 | Total |
|---|---|---|---|---|
| 24,192 | 8064 | 8064 | 40,320 Number of S-boxes in | |
| 672 | 224 | 224 | 1120 Number of HW classes in |
| CCV = 0.27551 | CCV = 0.489796 | CCV = 1.13265 | Total | |
|---|---|---|---|---|
| NL = 2 | ||||
| NL = 0 | ||||
| Total |
| Total of S-boxes | 1,000,000 | 100,000 |
| P(NL = max , CCV = max) | 0.0001 | 0 |
| P(NL = max) | 0.0886 | 0.0017 |
| P(CCV = max) | 0.0010 | |
| P(NL = max|CCV = max) | 0.0998 | 0 |
| P(CCV = max|NL = max) | 0.0012 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Martínez-Díaz, I.; Legón-Pérez, C.M.; Sosa-Gómez, G. Generation of Affine-Shifted S-Boxes with Constant Confusion Coefficient Variance and Application in the Partitioning of the S-Box Space. Cryptography 2025, 9, 45. https://doi.org/10.3390/cryptography9020045
Martínez-Díaz I, Legón-Pérez CM, Sosa-Gómez G. Generation of Affine-Shifted S-Boxes with Constant Confusion Coefficient Variance and Application in the Partitioning of the S-Box Space. Cryptography. 2025; 9(2):45. https://doi.org/10.3390/cryptography9020045
Chicago/Turabian StyleMartínez-Díaz, Ismel, Carlos Miguel Legón-Pérez, and Guillermo Sosa-Gómez. 2025. "Generation of Affine-Shifted S-Boxes with Constant Confusion Coefficient Variance and Application in the Partitioning of the S-Box Space" Cryptography 9, no. 2: 45. https://doi.org/10.3390/cryptography9020045
APA StyleMartínez-Díaz, I., Legón-Pérez, C. M., & Sosa-Gómez, G. (2025). Generation of Affine-Shifted S-Boxes with Constant Confusion Coefficient Variance and Application in the Partitioning of the S-Box Space. Cryptography, 9(2), 45. https://doi.org/10.3390/cryptography9020045







