Low-Cost Area-Efficient FPGA-Based Multi-Functional ECDSA/EdDSA
Abstract
:1. Introduction
2. Background Knowledge
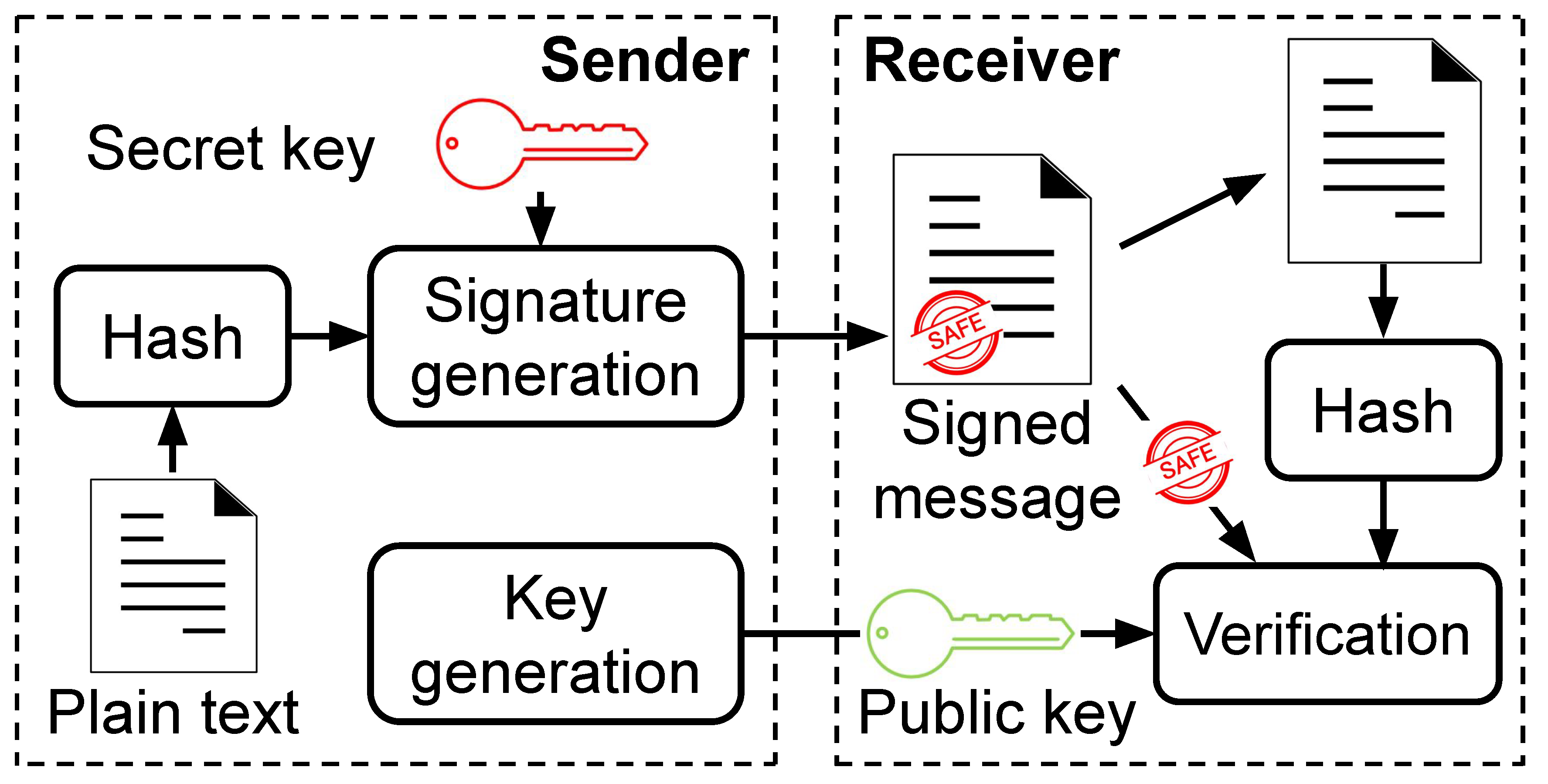
2.1. Digital Signature Algorithm
2.2. Elliptic Curve Digital Signature Algorithm—ECDSA
| Algorithm 1 Elliptic curve digital signature algorithm (ECDSA). |
| Key-generation |
| Input: Prime p, base point G |
| Output: Public key Q |
| 1: Select a random number d where |
| 2: Compute over the prime field |
| Signature generation |
| Input: Prime p, base point G, and the private key d |
| Output: Signature for the message m |
| 1: Select a random number k where |
| 2: Compute over the prime field |
| 3: Assign |
| 4: Compute |
| 5: Compute over the prime field |
| Verification |
| Input: Prime p, base point G, signature of the input message m, public key Q |
| Output: The input message m is valid or invalid |
| 1: Compute |
| 2: Compute over the prime field |
| 3: Compute over the prime field |
| 4: Compute over the prime field |
| 5: Compute over the prime field |
| 6: if where O is the point at infinity then |
| 7: State message m is invalid |
| 8: else |
| 9: Assign |
| 10: end if |
| 11: ifthen |
| 12: State message m is valid |
| 13: else |
| 14: State message m is invalid |
| 15: end if |
2.3. Edwards-Curve Digital Signature Algorithm—EdDSA
| Algorithm 2 Edwards-curve digital signature algorithm (EdDSA). |
| Key-generation |
| Input: Prime p, base point G, private key k |
| Output: Public key Q |
| 1: Compute where is 32 bytes MSB and is 32 bytes LSB. |
| 2: Assign as little-endian notation |
| 3: Compute over the prime field |
| Signature-generation |
| Input: Prime p and q, base point G, private key k, public key Q, and message m |
| Output: Signature for the message m |
| 1: Compute where is 32 bytes MSB and is 32 bytes LSB. |
| 2: Compute mod q |
| 3: Compute over the prime field |
| 4: Compute mod q |
| 5: Compute mod q |
| Verification |
| Input: Prime p and q, base point G, signature of the input message m, public key Q |
| Output: The input message m is valid or invalid |
| 1: Compute mod q |
| 2: Compute over the prime field |
| 3: Compute over the prime field |
| 4: if then |
| 5: State message m is valid |
| 6: else |
| 7: State message m is invalid |
| 8: end if |
2.4. ECDSA/EdDSA Hierarchy
3. Hardware Architecture
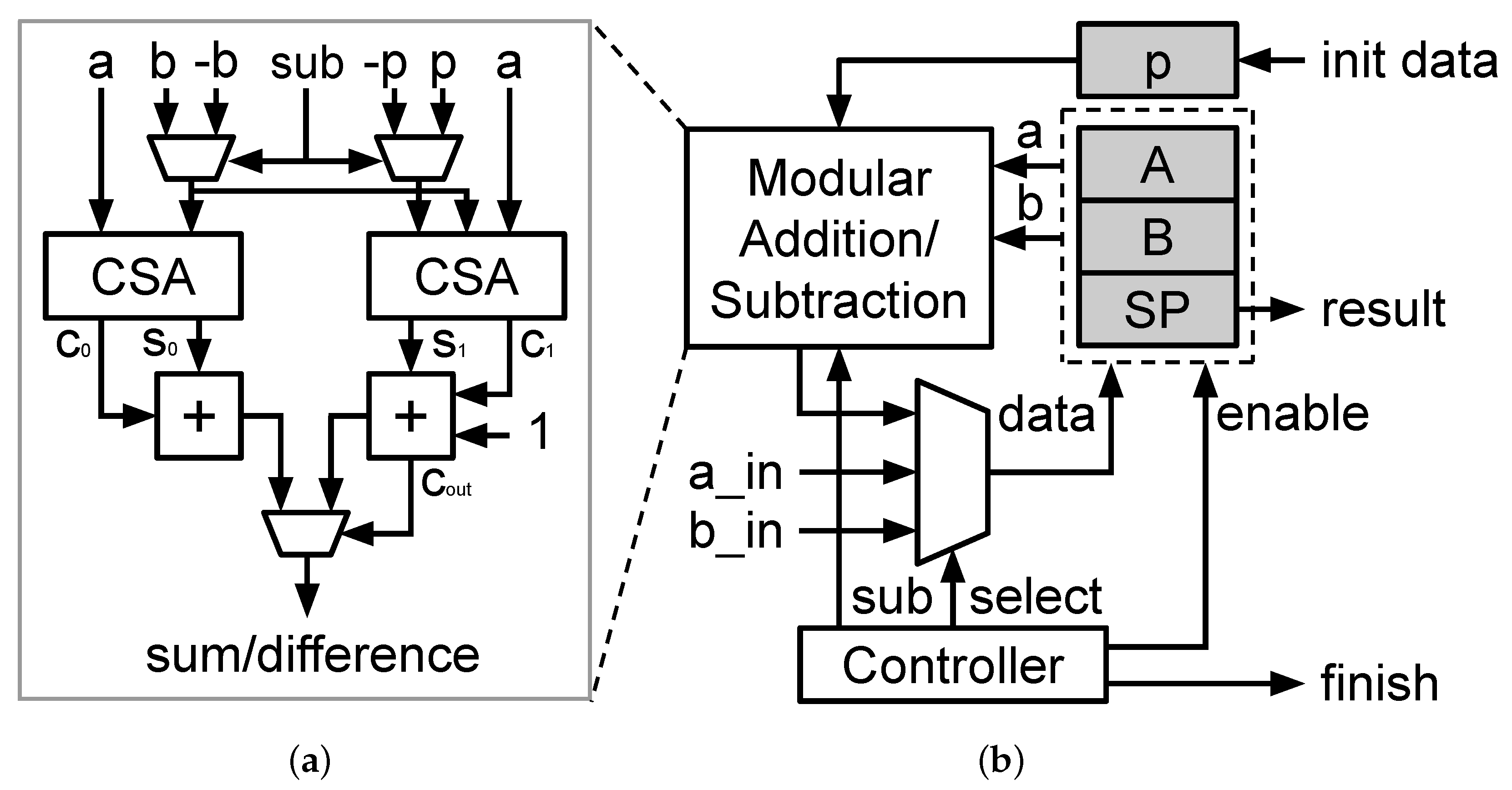
3.1. Modular Arithmetic-Logic Unit
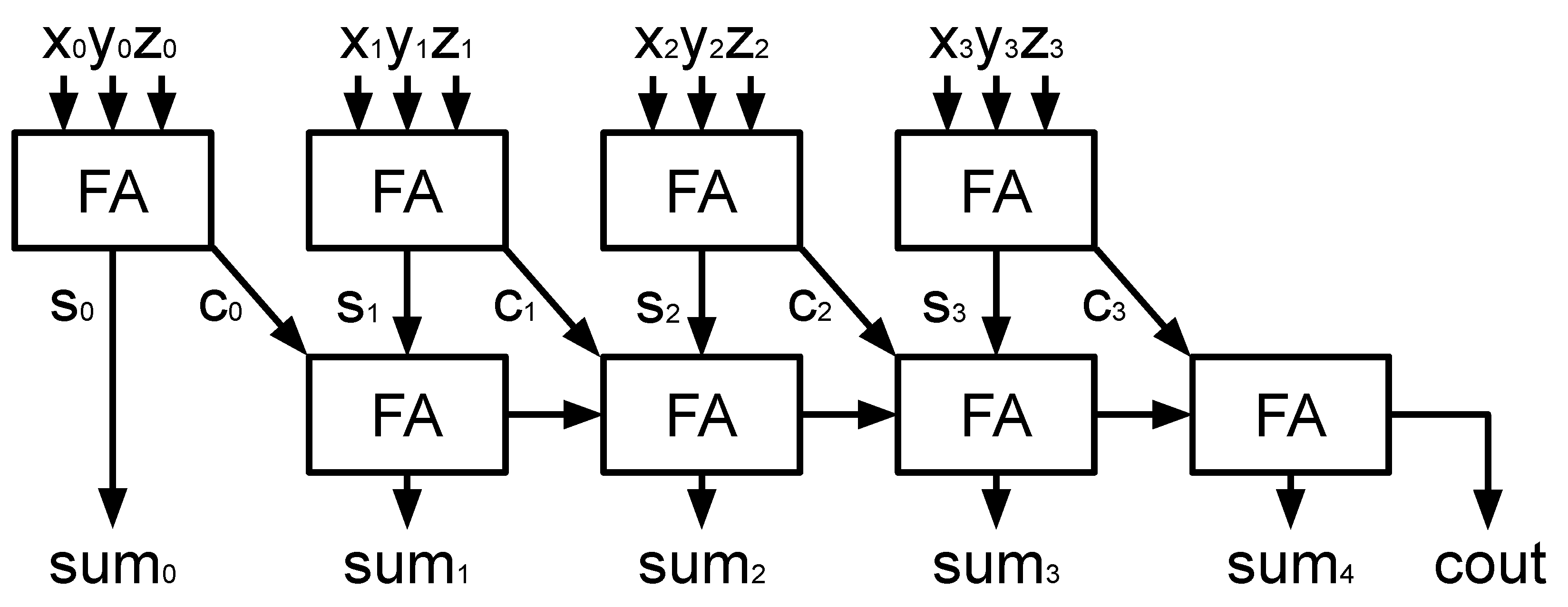
3.1.1. Modular Addition/Subtraction
3.1.2. Processing Element
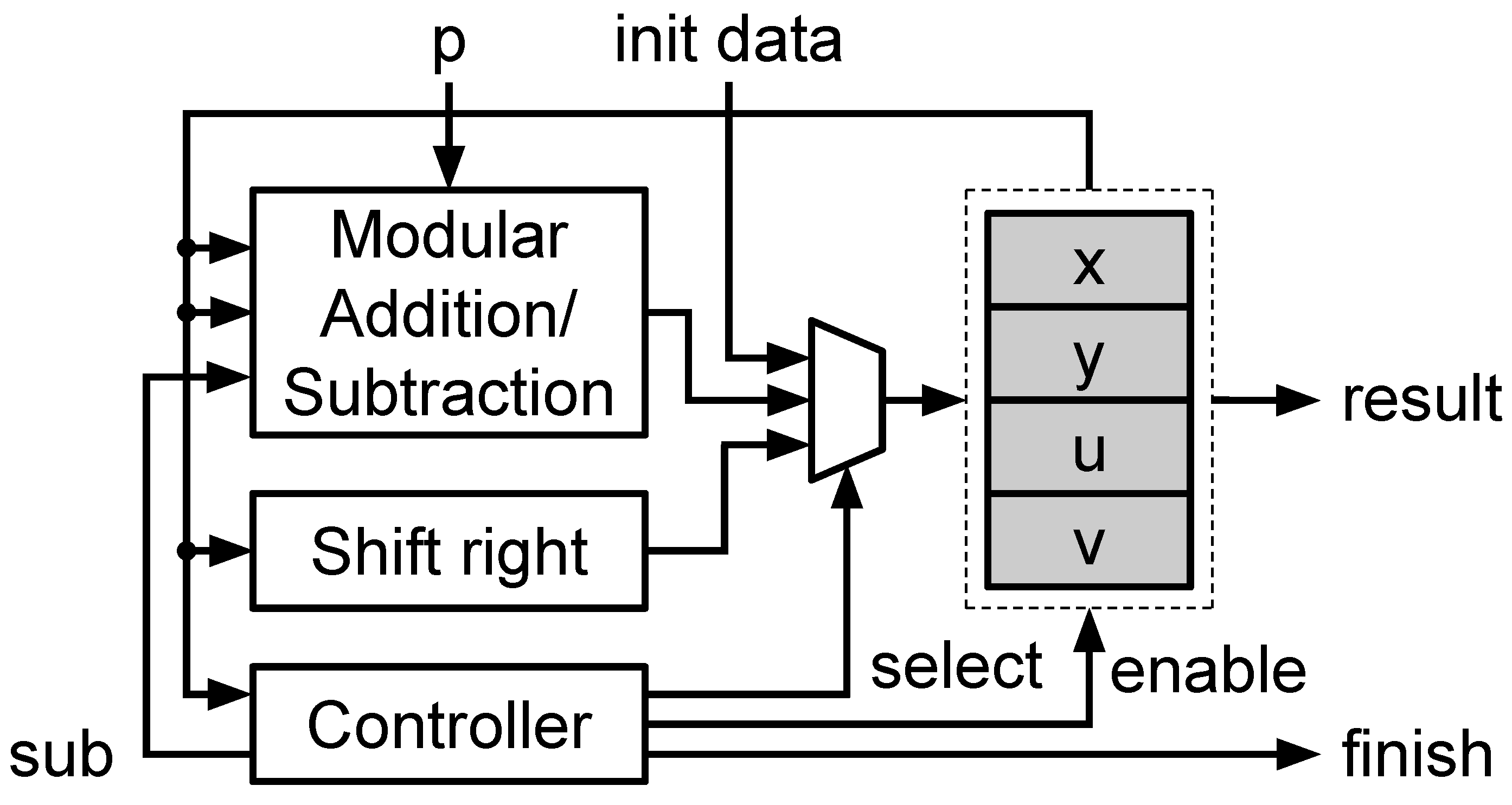
3.1.3. Modular Inversion
| Algorithm 3 Binary Euclidean algorithm (BEA). |
| Input: Prime p and |
| Output: mod p |
| 1: , , , |
| 2: while and do |
| 3: while u mod do |
| 4: |
| 5: if x mod then |
| 6: |
| 7: else |
| 8: |
| 9: end if |
| 10: end while |
| 11: while v mod do |
| 12: |
| 13: if y mod then |
| 14: |
| 15: else |
| 16: |
| 17: end if |
| 18: end while |
| 19: if then |
| 20: mod p |
| 21: mod p |
| 22: else |
| 23: mod p |
| 24: mod p |
| 25: end if |
| 26: end while |
| 27: if then |
| 28: return x |
| 29: else |
| 30: return y |
| 31: end if |
3.2. Elliptic Curve Cryptography Unit
4. Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- The Transport Layer Security (TLS) Protocol Version 1.3. Available online: https://www.rfc-editor.org/info/rfc8446 (accessed on 10 March 2022).
- IKE and IKEv2 Authentication Using the Elliptic Curve Digital Signature Algorithm (ECDSA). Available online: https://www.rfc-editor.org/info/rfc4754 (accessed on 10 March 2022).
- IT Security Techniques—Digital Signatures. Available online: https://www.iso.org/standard/76382.html (accessed on 10 March 2022).
- Digital Signature Standard (DSS). Available online: https://csrc.nist.gov/publications/detail/fips/186/2/archive/2000-01-27 (accessed on 10 March 2022).
- Public Key Cryptography for the Financial Services Industry: The Elliptic Curve Digital Signature Algorithm (ECDSA). Available online: https://standards.globalspec.com/std/1955141/ANSI%20X9.62 (accessed on 10 March 2022).
- Edwards-Curve Digital Signature Algorithm (EdDSA). Available online: https://www.rfc-editor.org/info/rfc8032 (accessed on 10 March 2022).
- Bernstein, D.; Duif, N.; Lange, T.; Schwabe, P.; Yang, B.Y. High-Speed High-Security Signatures. J. Cryp. Eng. 2011, 2, 124–142. [Google Scholar]
- Sghaier, A.; Zeghid, M.; Machhout, M. Fast hardware implementation of ECDSA signature scheme. In Proceedings of the International Symposium on Signa, Image, Video and Communications (ISIVC), Tunis, Tunisia, 21–23 November 2016; IEEE: Piscataway, NJ, USA, 2017; pp. 343–348. [Google Scholar]
- Sghaier, A.; Zeghid, M.; Massoud, C.; Mahchout, M. Design And Implementation of Low Area/Power Elliptic Curve Digital Signature Hardware Core. Electronics 2017, 6, 46. [Google Scholar] [CrossRef] [Green Version]
- Panjwani, B.; Mehta, D.C. Hardware-software co-design of elliptic curve digital signature algorithm over binary fields. In Proceedings of the International Conference on Advances in Computing, Comm. and Informatics (ICACCI), Kochi, India, 10–13 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1101–1106. [Google Scholar]
- Panjwani, B. Scalable and parameterized hardware implementation of elliptic curve digital signature algorithm over prime fields. In Proceedings of the International Conference on Advances in Computing, Comm. and Informatics (ICACCI), Udupi, India, 13–16 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 211–218. [Google Scholar]
- Bisheh-Niasar, M.; Azarderakhsh, R.; Mozaffari-Kermani, M. Cryptographic Accelerators for Digital Signature Based on Ed25519. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 1297–1305. [Google Scholar] [CrossRef]
- Salarifard, R.; Bayat-Sarmadi, S. An Efficient Low-Latency Point-Multiplication Over Curve25519. IEEE Trans. Circ. Syst. I Regul. Pap. 2019, 66, 3854–3862. [Google Scholar] [CrossRef]
- Sasdrich, P.; Güneysu, T. Implementing Curve25519 for Side-Channel–Protected Elliptic Curve Cryptography. ACM Trans. Embed. Comput. Syst. 2015, 9, 1–15. [Google Scholar] [CrossRef]
- Turan, F.; Verbauwhede, I. Compact and Flexible FPGA Implementation of Ed25519 and X25519. ACM Trans. Embed. Comput. Syst. 2019, 18, 1–21. [Google Scholar] [CrossRef]
- Asif, S.; Hossain, M.S.; Kong, Y. High-throughput multi-key elliptic curve cryptosystem based on residue number system. IET Comp. Dig. Tech. 2017, 5, 165–172. [Google Scholar] [CrossRef]
- Islam, M.M.; Hossain, M.S.; Hasan, M.K.; Shahjalal, M.; Jang, Y.M. FPGA Implementation of High-Speed Area-Efficient Processor for Elliptic Curve Point Multiplication Over Prime Field. IEEE Access 2019, 7, 178811–178826. [Google Scholar] [CrossRef]
- Kodali, R.K. Implementation of ECDSA in WSN. In Proceedings of the International Conference on Control Communication and Computing (ICCC), Thiruvananthapuram, India, 13–15 December 2013; IEEE: Piscataway, NJ, USA, 2014; pp. 310–314. [Google Scholar]
- Cheng, H.; Liu, J.; Mao, J.; Wang, M.; Chen, J.; Bian, J. A Compatible OpenFlow Platform for Enabling Security Enhancement SDN. Sec. Commun. Netw. 2018, 2018, 8392080. [Google Scholar] [CrossRef] [Green Version]
- Sunar, B. Binary Euclidean Algorithm. In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Ed.; Springer: Boston, MA, USA, 2005; pp. 31–32. [Google Scholar] [CrossRef]
- Sasdrich, P.; Güneysu, T. Efficient Elliptic-Curve Cryptography Using Curve25519 on Reconfigurable Devices. In Proceedings of the Applied Reconfigurable Computing (ARC), Vilamoura, Portugal, 14–16 April 2014; Goehringer, D., Santambrogio, M.D., Cardoso, J.M.P., Bertels, K., Eds.; Springer: Cham, Switzerland, 2014; pp. 25–36. [Google Scholar]
- Koppermann, P.; De Santis, F.; Heyszl, J.; Sigl, G. X25519 Hardware Implementation for Low-Latency Applications. In Proceedings of the Digital Syst. Design (DSD), Limassol, Cyprus, 31 August–2 September 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 99–106. [Google Scholar]




| This Work | [11] | [15] | [21] | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Support Mode | EdDSA | 25,519 | ● | ● | ● | ● | ○ | ○ | ○ | ● | ● |
| ECDSA | P-256 | ● | ● | ● | ● | ● | ○ | ○ | ○ | ○ | |
| P-384 | ○ | ○ | ● | ● | ○ | ● | ○ | ○ | ○ | ||
| P-521 | ○ | ○ | ● | ● | ○ | ○ | ● | ○ | ○ | ||
| Support Func. | Sign | ● | ● | ● | ● | ● | ● | ● | ● | ○ | |
| Verify | ● | ● | ● | ● | ● | ● | ● | ● | ○ | ||
| Keygen | ● | ● | ● | ● | ○ | ○ | ○ | ● | ● | ||
| FPGA | Virtex-6 | Virtex-7 | Virtex-6 | Virtex-7 | Virtex-6 | Virtex-6 | Virtex-6 | Artix-7 | Artix-7 | ||
| Slices | 4327 | 4276 | 8610 | 10,259 | 10,625 | 16,747 | 23,633 | 4303 | 11,277 | ||
| DSP | 0 | 0 | 0 | 0 | 136 | 196 | 280 | 16 | 220 | ||
| Slices equivalent | 4327 | 4276 | 8610 | 10,259 | 24,225 | 36,347 | 51,633 | 5903 | 33,277 | ||
| Frequency (MHz) | 116.72 | 122.05 | 72 | 112.2 | 100 | 83.3 | 71.5 | 82 | 100 | ||
| /MHz | 160 | 150 | 1030 | 938 | 5869 | 15,860 | 37,286 | 425 | 11,074 | ||
| Operations per sec. (Ops) | Ed25519 | Sign | 127 | 132 | 78 | 122 | - | - | - | 118 | - |
| Verify | 55 | 57 | 34 | 53 | - | - | - | 78 | - | ||
| Keygen | 125 | 131 | 77 | 120 | - | - | - | 90 | 21,686 | ||
| ECDSA P-256 | Sign | 108 | 113 | 67 | 104 | 787 | - | - | - | - | |
| Verify | 55 | 57 | 34 | 53 | 674 | - | - | - | - | ||
| Keygen | 109 | 113 | 67 | 104 | - | - | - | - | - | ||
| ECDSA P-384 | Sign | - | - | 30 | 47 | - | 292 | - | - | - | |
| Verify | - | - | 15 | 23 | - | 276 | - | - | - | ||
| Keygen | - | - | 30 | 47 | - | - | - | - | - | ||
| ECDSA P-521 | Sign | - | - | 16 | 25 | - | - | 109 | - | - | |
| Verify | - | - | 8 | 13 | - | - | 83 | - | - | ||
| Keygen | - | - | 16 | 26 | - | - | - | - | - | ||
| /Ops | Ed25519 | Sign | 148 | 138 | 950 | 865 | - | - | - | 295 | - |
| Verify | 341 | 318 | 2188 | 1994 | - | - | - | 447 | - | ||
| Keygen | 150 | 140 | 960 | 875 | - | - | - | 387 | 51 | ||
| ECDSA P-256 | Sign | 173 | 161 | 1109 | 1011 | 746 | - | - | - | - | |
| Verify | 342 | 320 | 2198 | 2003 | 871 | - | - | - | - | ||
| Keygen | 173 | 161 | 1107 | 1009 | - | - | - | - | - | ||
| ECDSA P-384 | Sign | - | - | 2474 | 2254 | - | 4524 | - | - | - | |
| Verify | - | - | 4936 | 4497 | - | 4790 | - | - | - | ||
| Keygen | - | - | 2471 | 2251 | - | - | - | - | - | ||
| ECDSA P-521 | Sign | - | - | 4532 | 4129 | - | - | 24,458 | - | - | |
| Verify | - | - | 9067 | 8260 | - | - | 32,120 | - | - | ||
| Keygen | - | - | 4528 | 4125 | - | - | - | - | - | ||
| This Work | [17] | [16] | [13] | [22] | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Support Curve | 25519 | ● | ● | ● | ● | ○ | ○ | ○ | ○ | ○ |
| P-256 | ● | ● | ● | ● | ● | ● | ● | ○ | ○ | |
| P-384 | ○ | ○ | ● | ● | ○ | ○ | ○ | ○ | ○ | |
| P-521 | ○ | ○ | ● | ● | ○ | ○ | ○ | ○ | ○ | |
| FPGA | Virtex-6 | Virtex-7 | Virtex-6 | Virtex-7 | Virtex-6 | Virtex-7 | Virtex-7 | Kintex-7 | Kintex-7 | |
| Slices | 3025 | 2932 | 5957 | 7172 | 9246 | 8873 | 24,200 | 3362 | 8639 | |
| DSP | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 182 | 260 | |
| Slices equivalent | 3025 | 2932 | 5957 | 7172 | 9246 | 8873 | 24,200 | 21,562 | 34,639 | |
| Frequency (MHz) | 116.72 | 149.23 | 88.82 | 138.58 | 161.1 | 177.7 | 72.9 | 87 | 115 | |
| /MHz | 78 | 58 | 400 | 371 | 531 | 443 | 8033 | 5344 | 10,434 | |
| Through- put (Kbps) | 25519 | 91 | 117 | 69 | 108 | - | - | - | 5773 | 2159 |
| P-256 | 114 | 146 | 87 | 135 | 157 | 173 | 1816 | - | - | |
| P-384 | - | - | 58 | 90 | - | - | - | - | - | |
| P-521 | - | - | 43 | 66 | - | - | - | - | - | |
| /Kbps | 25519 | 100 | 74 | 511 | 475 | - | - | - | 81 | 556 |
| P-256 | 80 | 59 | 409 | 380 | 545 | 455 | 322 | - | - | |
| P-384 | - | - | 614 | 570 | - | - | - | - | - | |
| P-521 | - | - | 833 | 774 | - | - | - | - | - | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kieu-Do-Nguyen, B.; Pham-Quoc, C.; Tran, N.-T.; Pham, C.-K.; Hoang, T.-T. Low-Cost Area-Efficient FPGA-Based Multi-Functional ECDSA/EdDSA. Cryptography 2022, 6, 25. https://doi.org/10.3390/cryptography6020025
Kieu-Do-Nguyen B, Pham-Quoc C, Tran N-T, Pham C-K, Hoang T-T. Low-Cost Area-Efficient FPGA-Based Multi-Functional ECDSA/EdDSA. Cryptography. 2022; 6(2):25. https://doi.org/10.3390/cryptography6020025
Chicago/Turabian StyleKieu-Do-Nguyen, Binh, Cuong Pham-Quoc, Ngoc-Thinh Tran, Cong-Kha Pham, and Trong-Thuc Hoang. 2022. "Low-Cost Area-Efficient FPGA-Based Multi-Functional ECDSA/EdDSA" Cryptography 6, no. 2: 25. https://doi.org/10.3390/cryptography6020025
APA StyleKieu-Do-Nguyen, B., Pham-Quoc, C., Tran, N.-T., Pham, C.-K., & Hoang, T.-T. (2022). Low-Cost Area-Efficient FPGA-Based Multi-Functional ECDSA/EdDSA. Cryptography, 6(2), 25. https://doi.org/10.3390/cryptography6020025






