On Quantum Chosen-Ciphertext Attacks and Learning with Errors †
Abstract
1. Introduction
1.1. Background
1.2. Our Contributions
1.2.1. The Model
1.2.2. A Quantum-Query Attack on
1.2.3. Important Caveats
1.2.4. Related Work
1.3. Technical Summary of Results
1.3.1. Security Model and Basic Definitions
- 1.
- a key and a uniformly random bit are generated; gets access to oracles and , and outputs ;
- 2.
- receives and gets access to an oracle for only, and outputs a bit ; wins if .
- 1.
- a key is generated; gets access to oracles , and outputs circuits ;
- 2.
- Sample ; receives , , and access to an oracle for only, and outputs a string s; wins if .
1.3.2. Secure Constructions
1.3.3. Key Recovery Against LWE
1.3.4. Quantum Algorithm for Linear Rounding Functions
1.3.5. One Quantum Query Against
1.4. Organization
2. Preliminaries
2.1. Basic Notation and Conventions
2.2. Basic Number Theory Notation
2.3. Quantum-Secure Pseudorandomness
2.4. Quantum Random Access Codes
- Alice gets and encodes it as a d-dimensional quantum state .
- Bob receives from Alice, and some index , and is asked to recover the i-th bit of x, by performing some measurement on .
- They win if Bob’s output agrees with and lose otherwise.
2.5. Quantum Fourier Transform
3. The QCCA1 Security Model
3.1. Quantum Oracles
3.2. Ciphertext Indistinguishability
- 1.
- Setup: a key and a bit are generated;
- 2.
- Pre-challenge: gets access to oracles and , and outputs ;
- 3.
- Challenge: gets and access to only, and outputs a bit ;
- 4.
- Resolution: wins if .
3.3. Semantic Security
- 1.
- Setup:a key is generated;
- 2.
- Pre-challenge: gets access to oracles and , and outputs a challenge template ;
- 3.
- Challenge: a plaintext is generated; receives and gets access to an oracle for only; if , also receives ; outputs a string s;
- 4.
- Resolution: wins if .
4. Secure Constructions
4.1. Scheme
- 1.
- : output a key ;
- 2.
- : to encrypt a message , choose a random string and output ;
- 3.
- : to decrypt a ciphertext , output ;
- Game 0:
- This is the game , which we briefly review for convenience (see also Figure 1). In the pre-challenge phase, gets access to oracles and , and outputs a message while keeping a private state for the challenge phase. In the challenge phase, a random bit is sampled, and is run on input and a challenge ciphertextHere, where and x are sampled uniformly at random. In the challenge phase, only has access to and must output a bit . wins if , so we call the outcome of the game.
- Game 1:
- This is the same game as Game 0, except we replace with a uniformly random function .
- Run , answering encryption queries using classical calls to g in place of , and answering decryption queries using quantum oracle calls to g:
- Simulate the challenge phase by sampling and encrypting the challenge using g in place of ; run and simulate encryption queries as before;
- When outputs , output .
- gets lucky in one of his at most many queries to and happens to sample the challenge pair ;
- Or, the adversary is somehow able to use what he learned while he had access to , and thus F, to learn , meaning that the -sized quantum memory sends to , that can depend on queries to F, but which cannot depend on , allows to learn .
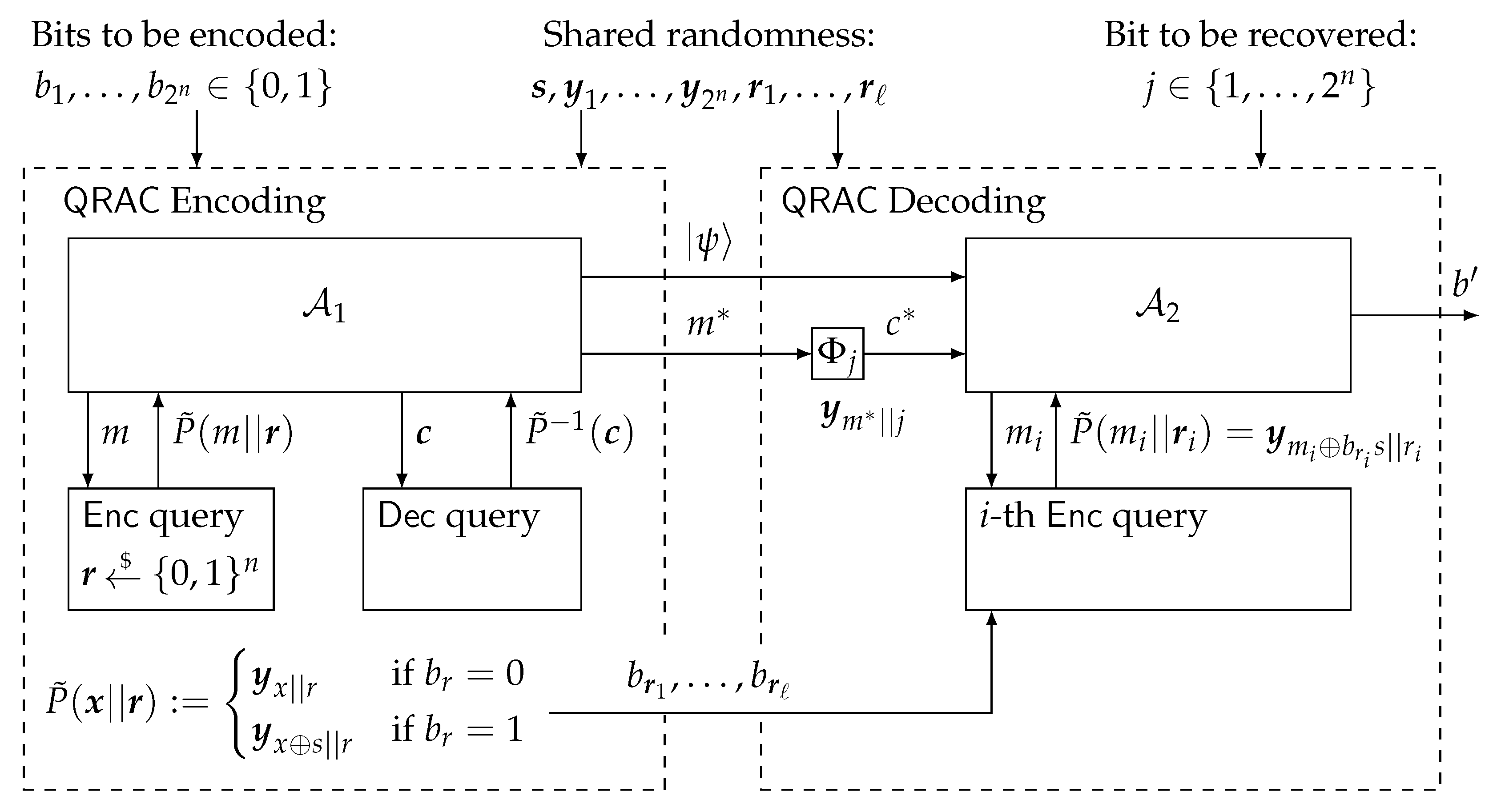
- Encoding.
- Let be the string to be encoded. Let be given by the first bits of the shared randomness, and let be the next bits. Define a function as follows. For , we will slightly abuse notation by letting r denote the corresponding integer value between 1 and . Define . Run , answering encryption and decryption queries using in place of F. Let and be the outputs of (see Figure 1). Output .
- Decoding.
- Let be the index of the bit to be decoded (so given as above, the goal is to recover ). Decoding will make use of the values given by the shared randomness. Upon receiving a query , run with inputs and . On ’s i-th encryption oracle call, use randomness , so that if the input to the oracle is , the state returned is (note that is given as part of ). Return the bit output by .
4.2. Scheme
- 1.
- : output ;
- 2.
- : to encrypt , choose and output ;
- 3.
- : to decrypt , output the first n bits of .
- Game 0:
- in the pre-challenge phase, gets access to oracles and . in the challenge phase, outputs m and its private data ; a random bit is sampled, and is run on input and a challenge ciphertextwhere and x is sampled uniformly at random. In the challenge phase, has oracle access to only and outputs a bit . The outcome of the game is simply the bit .
- Game 1:
- This is the same game as Game 0, except we now replace with a perfectly random permutation .
- Run , answering encryption queries using oracle calls to in place of , where for a given input and via randomness r,Answer decryption queries using quantum oracle calls to , a function that first computes but then (analogous to the construction) discards the last n bits of the pre-image corresponding to the randomness, i.e.
- Simulate the challenge phase by sampling and encrypting using a randomness together with a classical call to in place of ; run and simulate encryption queries as before.
- When outputs , output .
- Encoding.
- Let be the string to be encoded and let the shared randomness be given by a random string together with a random permutation and a set of random strings . Using , we define a new random permutation by letting ( remains a permutation since ). Now run by answering encryption and decryption queries using in place of (for decryption, use and discard the last n bits). Let and be the outputs of . Then, output .
- Decoding.
- Let be the index of the bit to be decoded; so given as above, we will recover by making use of the shared randomness defined above. Upon receiving a query , run with inputs and . Return the bit output by .
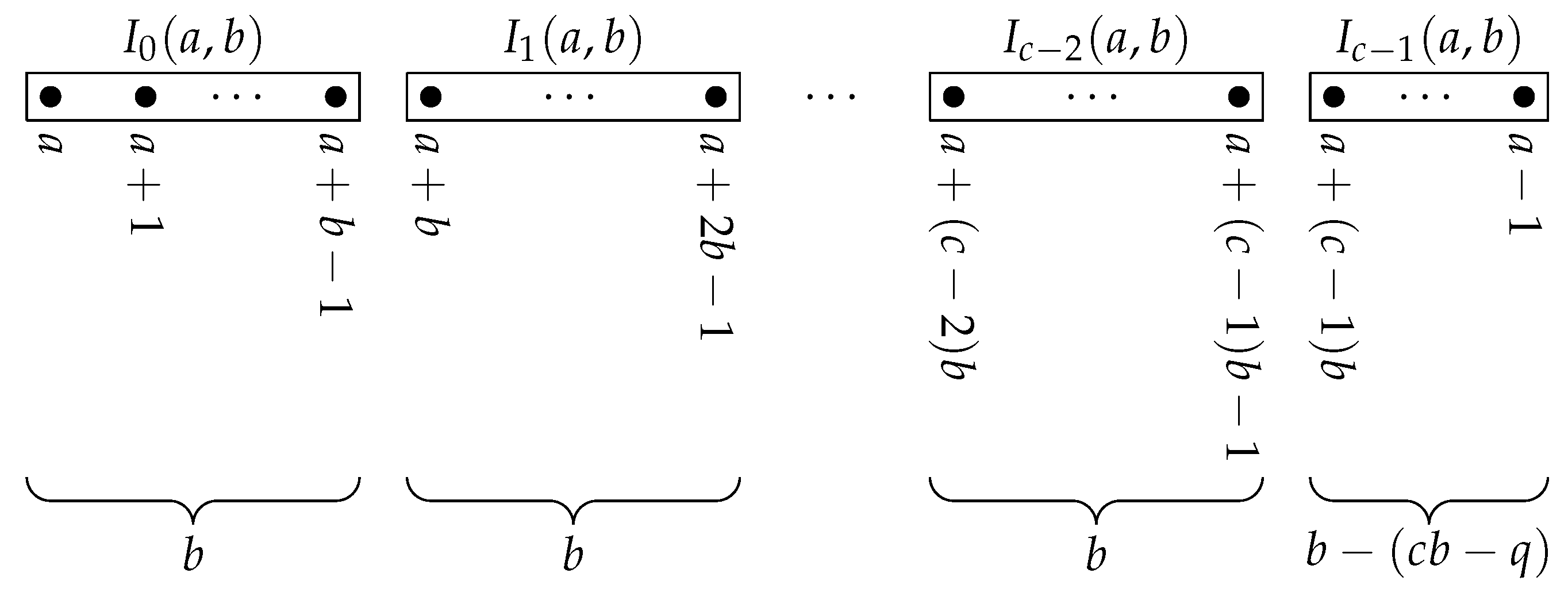
5. Quantum Algorithm for Linear Rounding Functions
| Algorithm 1: Bernstein–Vazirani for linear rounding functions |
| Parameters: n, q, , . |
|
|
6. Key Recovery Against LWE
6.1. Key Recovery via One Decryption Query in Symmetric-Key LWE
- 1.
- : output ;
- 2.
- : to encrypt , sample , and output ;
- 3.
- : to decrypt , output 0 if , else output 1.
6.2. Key Recovery via One Decryption Query in Public-Key LWE
6.2.1. Regev’s Public-Key Scheme
- 1.
- : output a secret key and a public key , where , , and all arithmetic is done modulo
- 2.
- : to encrypt , pick a random with Hamming weight roughly and output , where denotes the transpose of .
- 3.
- : to decrypt , output 0 if , else output 1.
6.2.2. Frodo Public-Key Scheme
- 1.
- : generate a matrix and matrices ; compute ; output the key-pair with public key and secret key .
- 2.
- : to encrypt (encoded as a matrix with each entry having 0 s in all but the B most significant bits) with public key , sample error matrices and ; compute and ; output the ciphertext .
- 3.
- : to decrypt with secret-key , compute . For each , output the first B bits of .
6.3. Key Recovery via One Decryption Query in Public-Key Ring-LWE
- 1.
- : sample and ; output and .
- 2.
- : to encrypt , sample and output a ciphertext pair , where and .
- 3.
- : to decrypt , compute ; output 0 if the constant term of the polynomial is closer to 0 than , else output 1.
6.4. Key Recovery via a Randomness-Access Query
| Algorithm 2: Bernstein–Vazirani for randomness-accessible encryption |
| input: Quantum randomness-access oracle for |
| output: with probability |
|
| Algorithm 3: Bernstein–Vazirani for (single-error) randomness-accessible encryption |
|
|
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Bound for Quantum Random Access Codes
- Alice receives an N-bit string x and encodes it as a quantum state .
- Bob receives from Alice and is asked to recover the i-th bit of x, for some , by measuring the state.
- They win if Bob’s output agrees with and lose otherwise.
- a shared random variable ,
- for each , a d-dimensional quantum state encoding x,
- for each , an observable for recovering the i-th bit.
Appendix A.2. Equivalence of QCCA Models
References
- Chen, L.; Jordan, S.; Liu, Y.K.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. Report on Post-Quantum Cryptography; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016. [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; IEEE: Piscataway, NJ, USA, 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM 2005, 56, 34:1–34:40. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology (NIST). Post-Quantum Cryptography; NIST: Gaithersburg, MD, USA, 2017.
- Kuwakado, H.; Morii, M. Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 2682–2685. [Google Scholar] [CrossRef]
- Kuwakado, H.; Morii, M. Security on the quantum-type Even-Mansour cipher. In Proceedings of the 2012 International Symposium on Information Theory and its Applications, Honolulu, HI, USA, 28–31 October 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 312–316. [Google Scholar]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Breaking symmetric cryptosystems using quantum period finding. In Advances in Cryptology—CRYPTO 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 207–237. [Google Scholar] [CrossRef]
- Santoli, T.; Schaffner, C. Using Simon’s algorithm to attack symmetric-key cryptographic primitives. In Quantum Information & Computation; Rinton Press: Paramus, NJ, USA, 2017; pp. 65–78. [Google Scholar] [CrossRef]
- Simon, D.R. On the power of quantum computation. SIAM J. Comput. 1997, 26, 1474–1483. [Google Scholar] [CrossRef]
- Gagliardoni, T.; Hülsing, A.; Schaffner, C. Semantic security and indistinguishability in the quantum world. In Advances in Cryptology—CRYPTO 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 60–89. [Google Scholar] [CrossRef]
- Bleichenbacher, D. Chosen ciphertext attacks against protocols based on the RSA encryption standard PKCS #1. In Advances in Cryptology—CRYPTO ’98; Krawczyk, H., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; pp. 1–12. [Google Scholar] [CrossRef]
- Boneh, D.; Zhandry, M. Secure signatures and chosen ciphertext security in a quantum computing world. In Advances in Cryptology—CRYPTO 2013; Canetti, R., Garay, J.A., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 361–379. [Google Scholar] [CrossRef]
- Boneh, D.; Zhandry, M. Quantum-secure message authentication codes. In Advances in Cryptology—EUROCRYPT 2013; Johansson, T., Nguyen, P.Q., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 592–608. [Google Scholar] [CrossRef]
- Broadbent, A.; Jeffery, S. Quantum homomorphic encryption for circuits of low T-gate complexity. In Advances in Cryptology—CRYPTO 2015; Gennaro, R., Robshaw, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 609–629. [Google Scholar] [CrossRef]
- Zhandry, M. How to construct quantum random functions. In Proceedings of the 2012 IEEE 53rd Annual Symposium on Foundations of Computer Science, New Brunswick, NJ, USA, 20–23 October 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 679–687. [Google Scholar] [CrossRef]
- Zhandry, M. A note on quantum-secure PRPs. arXiv 2016, arXiv:1611.05564. [Google Scholar]
- Bernstein, E.; Vazirani, U. Quantum complexity theory. SIAM J. Comput. 1997, 26, 1411–1473. [Google Scholar] [CrossRef]
- Alkim, E.; Bos, J.W.; Ducas, L.; Longa, P.; Mironov, I.; Naehrig, M.; Nikolaenko, V.; Peikert, C.; Raghunathan, A.; Stebila, D.; et al. FrodoKEM—Learning With Errors Key Encapsulation; Submission to the NIST Post-Quantum Cryptography standardization project; Round 2. Revised July 2, 2019. unpublished work.
- Lindner, R.; Peikert, C. Better key sizes (and attacks) for LWE-based encryption. In Topics in Cryptology—CT-RSA 2011; Kiayias, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 319–339. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. A toolkit for ring-LWE cryptography. In Advances in Cryptology—EUROCRYPT 2013; Johansson, T., Nguyen, P.Q., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 35–54. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. J. ACM 2013, 60, 43:1–43:35. [Google Scholar] [CrossRef]
- Grilo, A.B.; Kerenidis, I.; Zijlstra, T. Learning with errors is easy with quantum samples. arXiv 2017, arXiv:1702.08255. [Google Scholar] [CrossRef]
- Fujisaki, E.; Okamoto, T. Secure integration of asymmetric and symmetric encryption schemes. In Advances in Cryptography—CRYPTO 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 537–554. [Google Scholar]
- Goldreich, O.; Levin, L.A. A hard-core predicate for all one-way functions. In Proceedings of the Twenty-first Annual ACM Symposium on Theory of Computing (STOC ’89), Seattle, WA, USA, 14–17 May 1989; ACM: New York, NY, USA, 1989; pp. 25–32. [Google Scholar] [CrossRef]
- Goldreich, O.; Goldwasser, S.; Micali, S. How to construct random functions. J. ACM 1986, 33, 792–807. [Google Scholar] [CrossRef]
- Nayak, A. Optimal lower bounds for quantum automata and random access codes. In Proceedings of the 40th Annual Symposium on Foundations of Computer Science, New York City, NY, USA, 17–19 October 1999; pp. 369–376. [Google Scholar] [CrossRef]
- Ambainis, A.; Leung, D.; Mancinska, L.; Ozols, M. Quantum random access codes with shared randomness. arXiv 2008, arXiv:0810.2937. [Google Scholar]
- Kitaev, A.Y. Quantum measurements and the abelian stabilizer problem. arXiv 1995, arXiv:quant-ph/9511026. [Google Scholar]
- Hales, L.; Hallgren, S. An improved quantum Fourier transform algorithm and applications. In Proceedings of the 41st Annual Symposium on Foundations of Computer Science, Redondo Beach, CA, USA, 12–14 November 2000; pp. 515–525. [Google Scholar] [CrossRef]
- Goldreich, O. Foundations of Cryptography: Volume 2, Basic Applications; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 2nd ed.; The MIT Press: Cambridge, MA, USA, 2001. [Google Scholar]
- Alkim, E.; Ducas, L.; Pöppelmann, T.; Schwabe, P. Post-quantum key exchange—A new hope. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; USENIX Association: Austin, TX, USA, 2016; pp. 327–343. [Google Scholar]
- Bshouty, N.H.; Jackson, J.C. Learning DNF over the uniform distribution using a quantum example oracle. SIAM J. Comput. 1998, 28, 1136–1153. [Google Scholar] [CrossRef]
- Tomczak-Jaegermann, N. The moduli of smoothness and convexity and the Rademacher averages of the trace classes Sp (1≤p<∞). Stud. Math. 1974, 50, 163–182. [Google Scholar]
- Humphries, P. Reference for Euler Totient Function Identity? Mathematics Stack Exchange. Available online: https://math.stackexchange.com/q/2889027 (accessed on 8 May 2012).


© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alagic, G.; Jeffery, S.; Ozols, M.; Poremba, A. On Quantum Chosen-Ciphertext Attacks and Learning with Errors. Cryptography 2020, 4, 10. https://doi.org/10.3390/cryptography4010010
Alagic G, Jeffery S, Ozols M, Poremba A. On Quantum Chosen-Ciphertext Attacks and Learning with Errors. Cryptography. 2020; 4(1):10. https://doi.org/10.3390/cryptography4010010
Chicago/Turabian StyleAlagic, Gorjan, Stacey Jeffery, Maris Ozols, and Alexander Poremba. 2020. "On Quantum Chosen-Ciphertext Attacks and Learning with Errors" Cryptography 4, no. 1: 10. https://doi.org/10.3390/cryptography4010010
APA StyleAlagic, G., Jeffery, S., Ozols, M., & Poremba, A. (2020). On Quantum Chosen-Ciphertext Attacks and Learning with Errors. Cryptography, 4(1), 10. https://doi.org/10.3390/cryptography4010010



