In this section, we discuss how we developed a strong and undetectable watermarking method to make it more difficult to steal digital images. The suggested method uses advanced math and signal processing to make it very hard to attack in many ways. The method uses DWT, SVD, and Schur matrix factorization in an integrated manner. These methods work together to make sure the watermark stays hidden and that people cannot change the image. The next steps describe how to embed and remove watermarks in a systematic way to protect proof of ownership of digital images. The proposed watermarking method consists of three steps: embedding, extraction, and evaluation.
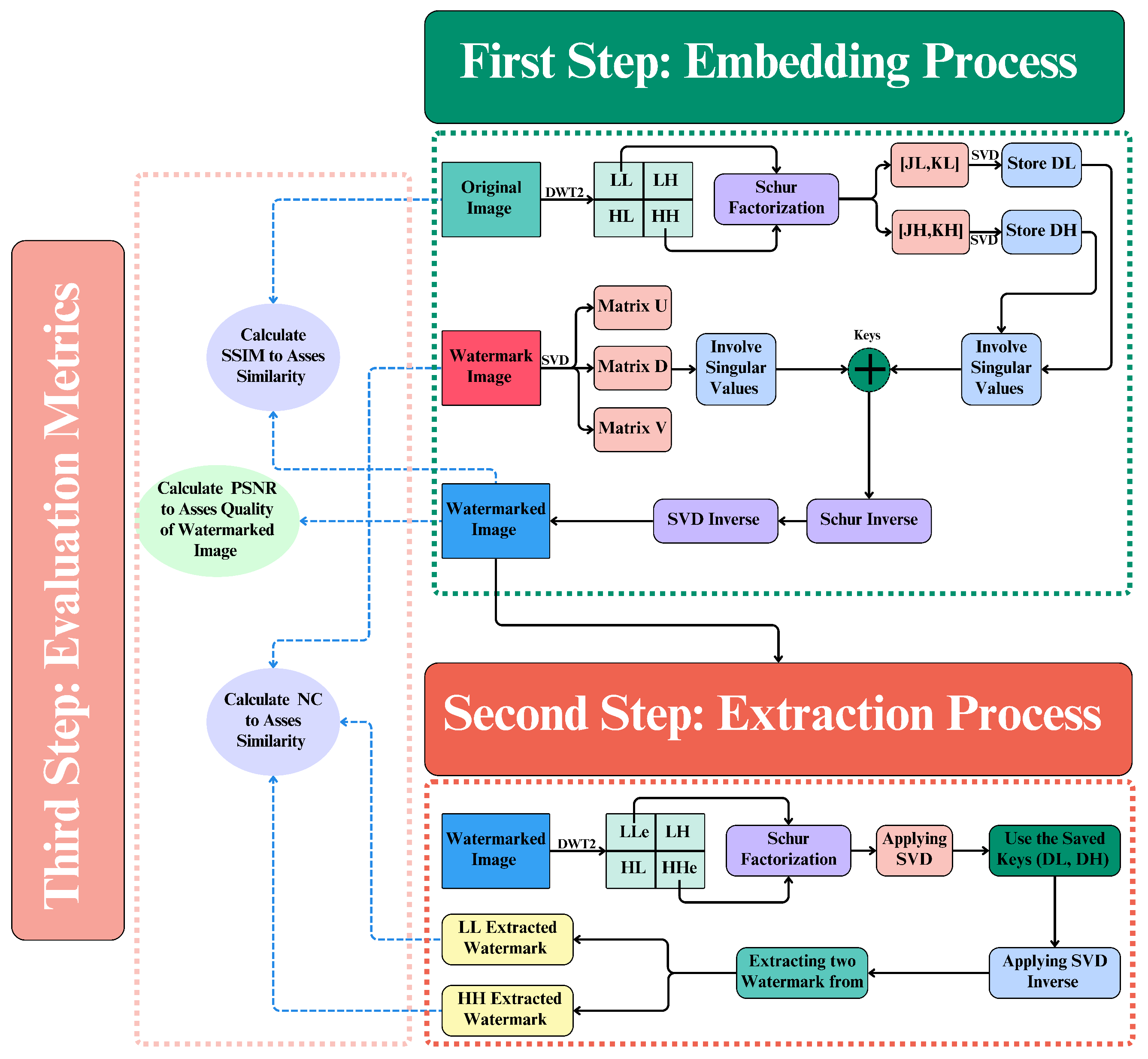
Figure 2 shows the whole process. The first step in embedding is to use a two-level DWT on the original image. This creates four sub-bands: LL, LH, HL, and HH. After that, Schur factorization and SVD are used to put the watermark’s information into the image’s sub-bands. The inverse process reconstructs the image with the watermark. In the extraction phase, the watermarked image goes through DWT, Schur factorization, and SVD in a manner similar to the first phase. It uses stored keys to correctly recover the embedded watermark. We use evaluation metrics like the Peak Signal-to-Noise Ratio (PSNR), the Structural Similarity Index (SSIM), and the NC to validate the method works.
4.1. Watermark Embedding Schema
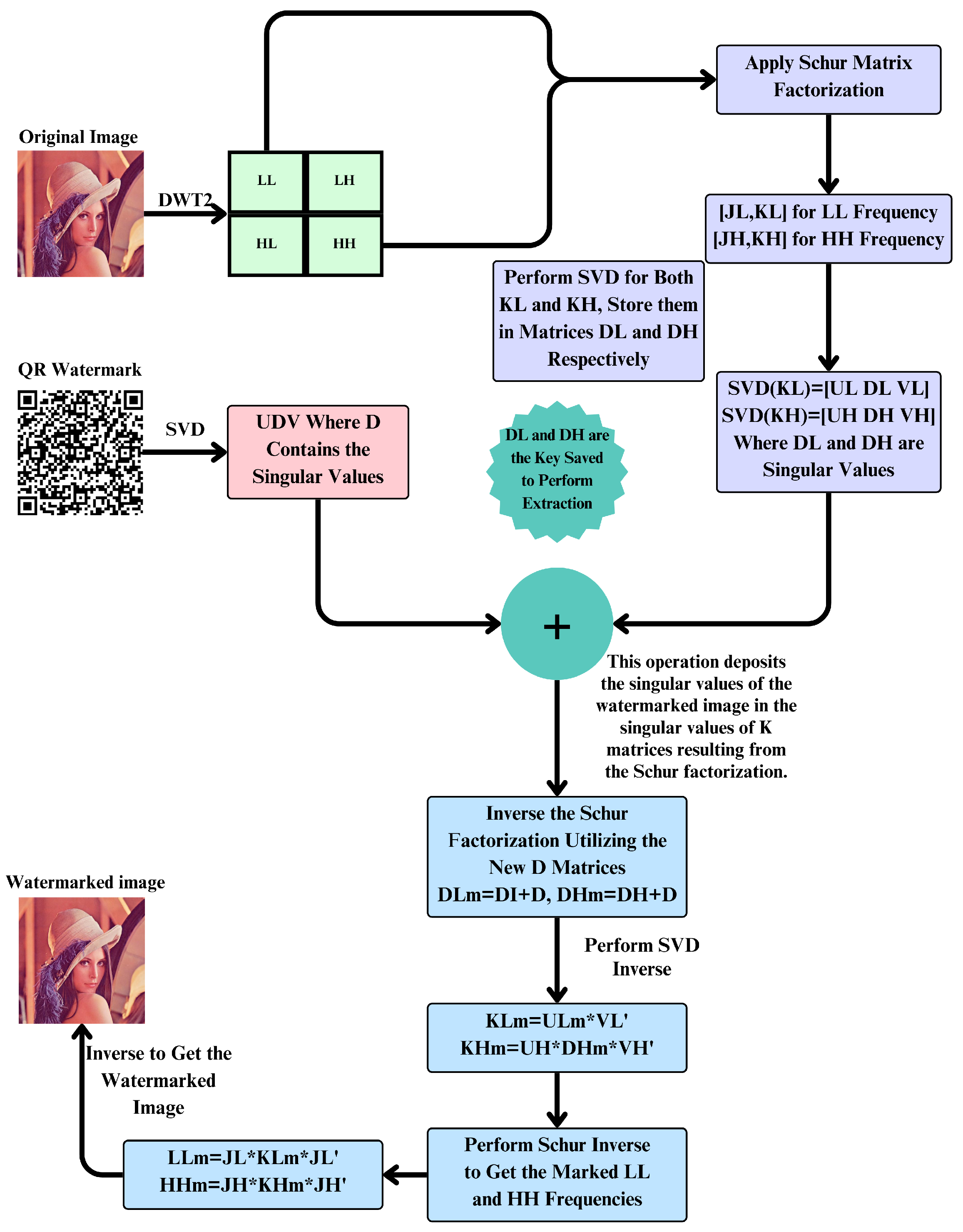
The watermark embedding process ensures that the watermark is imperceptible yet resilient against various attacks. This comprehensive process involves several advanced techniques including DWT, Schur matrix factorization, and SVD.
Figure 3 presents our watermark embedding scheme in detail.
The first step in the watermark embedding scheme is to use a two-level DWT on the original image. This breaks the picture up into four sub-bands: LL, LH, HL, and HH. DWT gives you a multi-resolution image representation, which makes it easy to work with different frequency components. It captures both big and small details, which makes it easy to add a strong watermark. DWT helps hide the watermark in a way that people cannot see it by focusing on different frequency bands. It also keeps the quality of the image overall. The LL sub-band keeps the most important parts of the image, while the LH, HL, and HH sub-bands capture smaller details. This makes them perfect for adding watermarks that cannot be seen.
In the second step, the Schur matrix factorization is carried out on the LL and HH frequency sub-bands and yields matrices for the LL band and for the HH band. Schur factorization reduces operations on a matrix by factoring it into an orthogonal matrix and an upper triangular matrix. This provides an easier way of handling the matrix characteristics for manipulations and analyses. Using Schur matrix factorization in digital watermarking is of huge benefit as it efficiently processes big matrices while the visual quality of the image is not compromised. This factorization can help to maintain the structure of the image during watermark embedding with minimal distortion while maintaining good robustness.
In the third step, SVD is used on both the
and
matrices to break them down into their singular values and the matrices that go with them. When you apply SVD to the watermark image, you obtain matrices U, D, and V. D has the watermark’s unique values. SVD is a strong way to break down a matrix into its most basic parts, capturing the most important parts of the image and the watermark. By changing the singular values, the embedded watermark can withstand different types of image processing attacks, making sure that the watermark embedding is strong and not noticeable, as shown in Equations (
16) and (
17).
In the fourth step, the singular values of the watermark matrix
D are then embedded into the singular-value matrices
and
obtained from the Schur factorization by modifying
and
with the watermark singular values scaled by a factor (
). The new matrices are denoted as
and
. Embedding singular values ensures that the watermark is integrated into the image’s core components, making it less likely to be removed or altered by common image processing operations. This method enhances the robustness and imperceptibility of the watermark, as represented in Equations (
18) and (
19).
The fifth step consists of applying inverse SVD to the transformed
and
to recover the watermarked matrices
and
. The inverse SVD operation reconstructs the watermarked matrices, thereby integrating the watermark into the image. This ensures the watermark remains invisible and robust without degrading the quality or integrity of the image. The inverse SVD operation must be performed to properly embed the watermark without introducing any artifacts or distortions in the image, as shown in Equations (
20) and (
21).
The sixth step applies an inverse Schur factorization to
and
in order to extract the initialized
and
frequencies. Taking the inverse of the Schur factorization guarantees that the adjustments made during watermark embedding are correctly captured in the output image. This operation preserves the structural regularities already inherent in the image while embedding watermarks that are resilient to a host of attacks. It is important to achieve the following reconstruction through the inverse Schur factorization, as shown in Equations (
22) and (
23):
The inverse DWT is applied to combine the modified , LH, HL, and sub-bands to reconstruct the watermarked image. The inverse DWT process reassembles the image from its frequency components, ensuring that the watermark is integrated into the final image. This step guarantees that the watermark is imperceptible to the human eye while providing robust protection against various image processing operations. The inverse DWT process ensures that the watermark remains embedded within the image’s core components, maintaining the image quality and the watermark’s robustness. By following these steps, the proposed watermark embedding scheme achieves a balance between imperceptibility and robustness, ensuring that the watermark remains hidden while providing strong protection against unauthorized use and tampering. Algorithm 1 illustrates the utilized embedding approach in detail.
We have chosen the values of
and
: a model-based rationale and protocol. Let
W denote the QR watermark with
, and let
represent the Schur triangular factor extracted from the DWT sub-bands (
or
), where
. The embedding process modifies the singular values of
K as
using additive SVD-domain modulation; then, it reconstructs the watermarked sub-band via
. This formulation balances imperceptibility and robustness through the scalar
, controlling watermark energy in each sub-band. To empirically determine optimal values, we evaluated multiple
settings over the range
(Figures 6 and 7). Results revealed a stable trade-off region around
and
, which preserved high imperceptibility (PSNR
dB, SSIM
) and robustness (NC
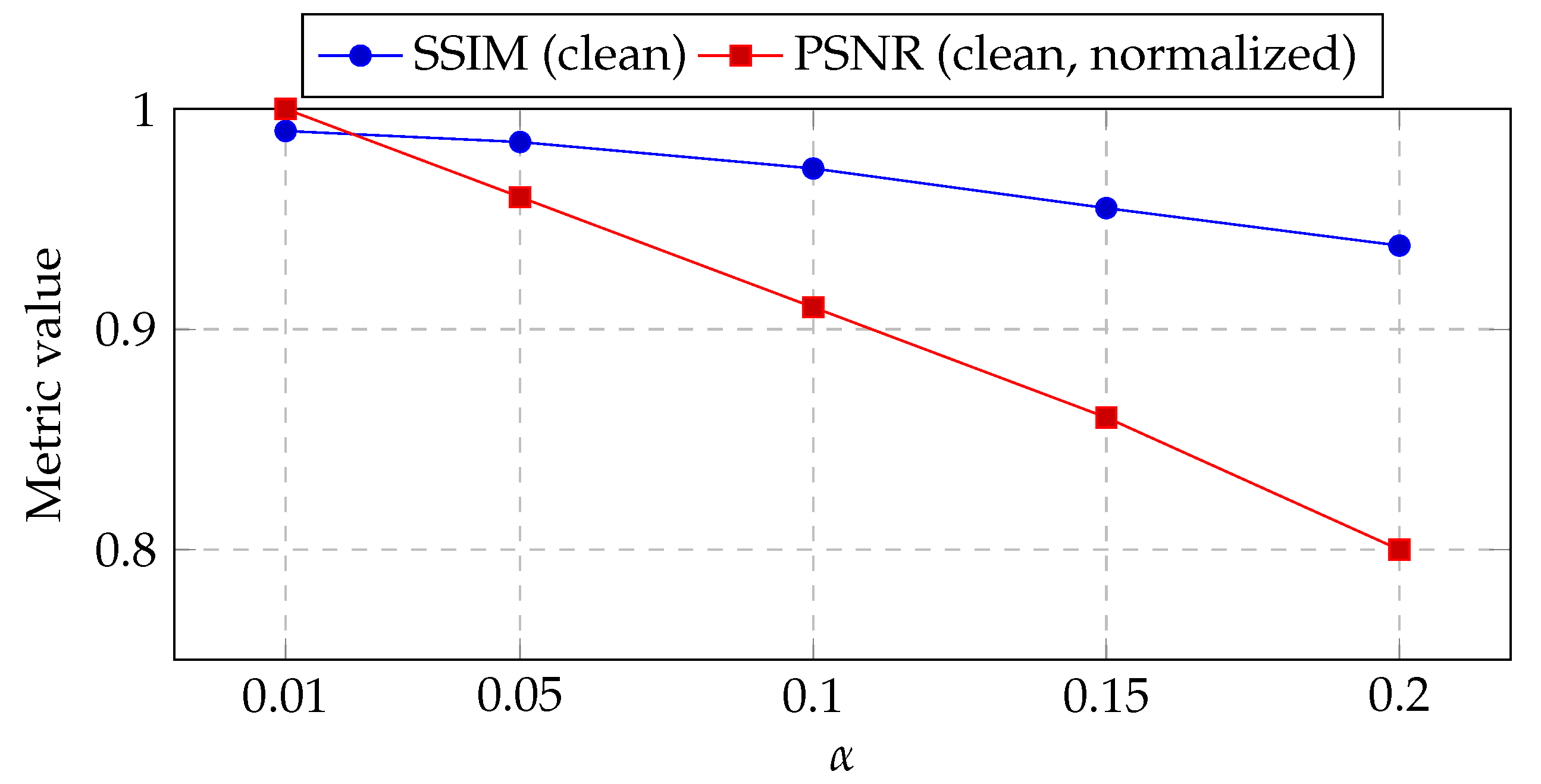
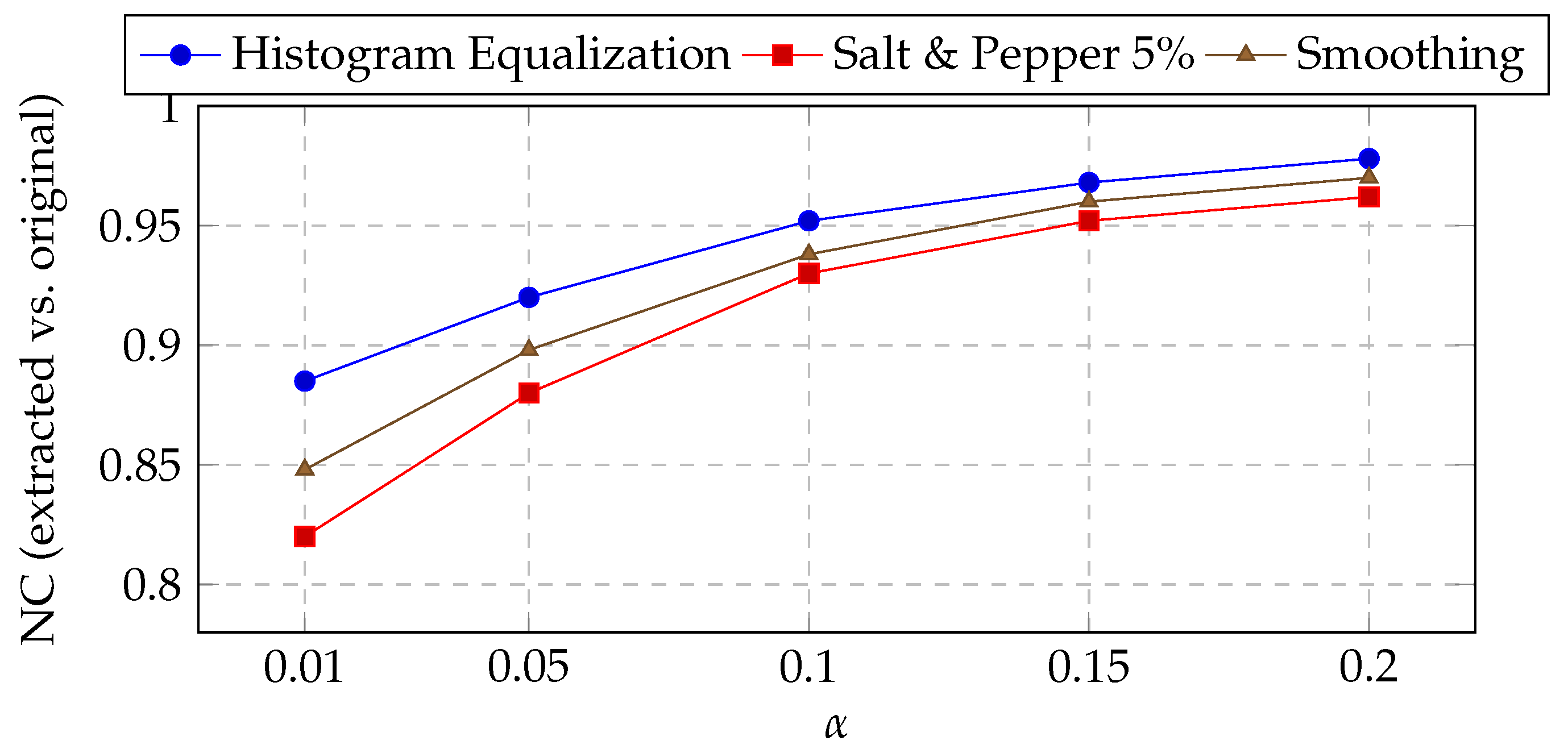
) across attacks. Schur decomposition was specifically integrated to enhance numerical stability, enable triangular sparsity-aware factorization, and improve energy compaction over high-frequency DWT sub-bands, thereby strengthening the resilience of the embedded watermark against geometric distortions.
and reconstructing
(cf. Algorithm 1). The induced perturbation is
so by unitary invariance of spectral/Frobenius norms,
Therefore, (i)
imperceptibility degrades at most linearly with
in the sub-band domain; after inverse Schur/DWT, the per-pixel MSE is bounded by a constant times
(energy preservation of unitary maps), which explains the observed monotone drop of PSNR/SSIM as
increases (
Section 4.3). (ii)
Robustness improves with
because extraction (Algorithm 2) uses
; the watermark SNR scales as
, while common attacks add approximately
-independent perturbations to
K, yielding the empirical NC lift vs.
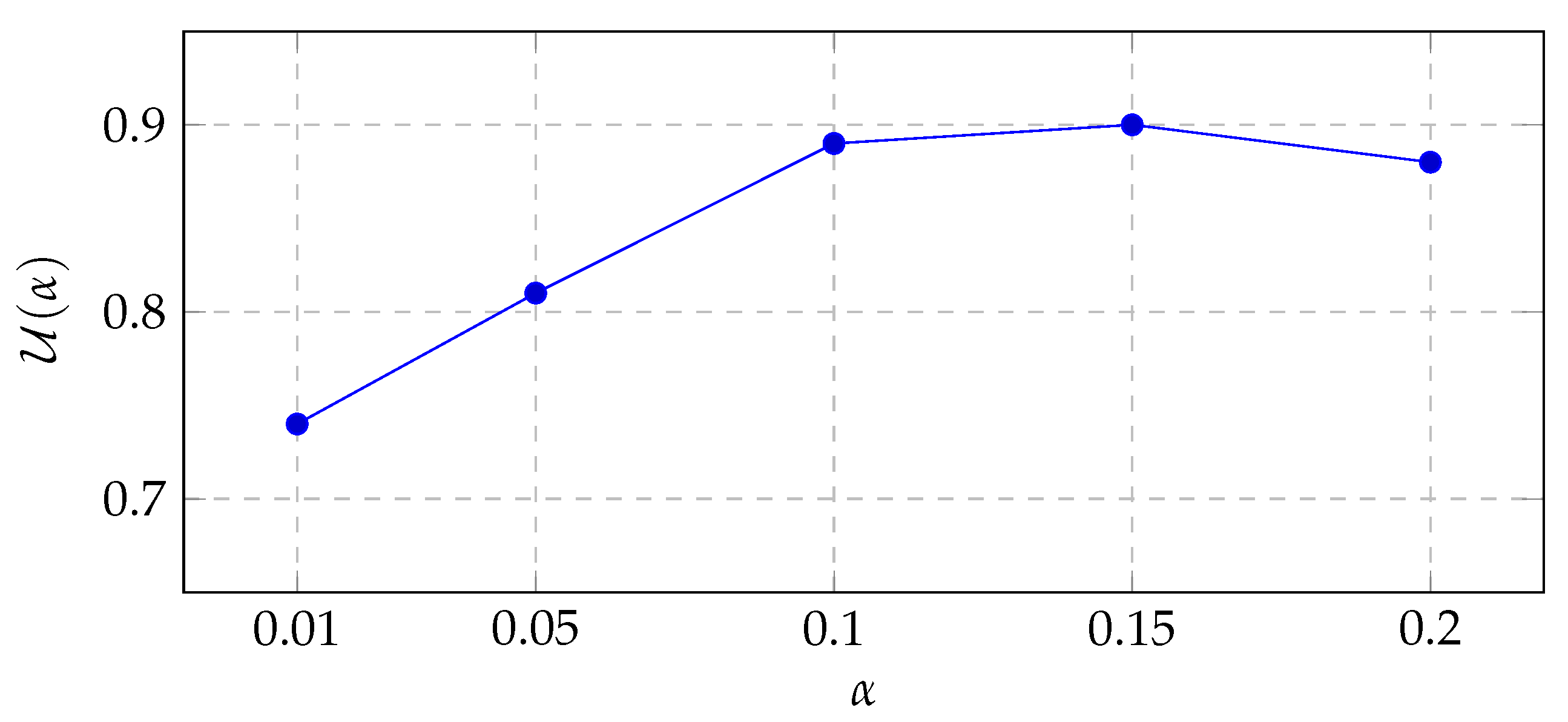
. We therefore sweep
and select
by maximizing a composite utility
(
Section 4.3), trading off PSNR/SSIM (imperceptibility) against NC (robustness). In our experiments, a high-fidelity setting
is used for the per-image tables to showcase invisibility (PSNR
–
dB; SSIM
), while the
balanced setting
attains
mean NC
on representative attacks with PSNR still
dB (
Section 4.3).
| Algorithm 1 Embedding Watermark Schema Using DWT, Schur Factorization and SVD |
Require: Cover image (original image), watermark image, alpha factor for embedding and Ensure: Watermarked image Step 1: Apply DWT to the cover image
- 1:
Decompose the cover image using Discrete Wavelet Transform (DWT) to obtain four sub-bands: LL, LH, HL, and HH.
- 2:
for each sub-band in {LL, HH} do - 3:
if sub-band is LL then - 4:
- 5:
else - 6:
- 7:
for each K in {, } do - 8:
if K is then - 9:
- 10:
else - 11:
- 12:
Decompose the watermark image using SVD: - 13:
= SVD(watermark_image)
- 14:
for each D in {, } do - 15:
if D is then - 16:
- 17:
else - 18:
- 19:
for each K in {, } do - 20:
if K is then - 21:
- 22:
else - 23:
- 24:
for each pair in {(), ()} do - 25:
if J is and K is then - 26:
- 27:
else - 28:
- 29:
Combine the modified , LH, HL, and sub-bands using the inverse DWT to obtain the final watermarked image.
|
We chose a Schur in addition to DWT+SVD given a real matrix
A (a DWT sub-band); the real Schur factorization
(orthogonal
J, quasi-upper-triangular
K) is a unitary similarity transform that preserves
and
. We embed in
K and remap via
J:
with
defined above. This offers three advantages: (1)
Energy-preserving control: Because
J is orthogonal, the image-domain perturbation norm equals that in the Schur domain, enabling the precise control of injected energy (hence PSNR/SSIM) through
. (2)
Structured perturbations with predictable spectra: Operating on the triangular
K allows low-rank, diagonally dominated updates; by Mirsky/Weyl inequalities, singular/eigen-spectra vary at most by
, which bounds distortions and explains stable extraction. (3)
Numerical stability and perceptual behavior: The Schur transform is backward stable; concentrating embedding in
K (rather than directly in spatial or raw DWT coefficients) reduces ringing/aliasing when mapped back via
J, especially in
, while
provides photometric stability. Empirically, this hybrid (DWT+Schur+SVD) yields higher NC at comparable PSNR than DWT+SVD alone under histogram equalization, smoothing, and heavy cropping.
Motivation for Embedding Watermarks Separately into the LL and HH Subbands
Let denote a two-level orthonormal DWT of an RGB image (applied per luminance or per channel). Each level yields four sub-bands: LL (approximation), LH (horizontal detail), HL (vertical detail), and HH (diagonal detail). We embed watermarks separately in LL and HH with strengths to exploit complementary properties. Natural images have approximate spectra, so the LL band concentrates most energy with high signal-to-quantization ratios and exhibits stable behavior under mild photometric and geometric operations (illumination shifts, histogram equalization, small rescalings). Injecting a controlled perturbation into LL via our Schur+SVD mechanism is mapped back by orthogonal transforms, preserving Frobenius energy and maintaining imperceptibility for moderate , which in turn yields reliable extraction under global operations and compression-like effects. Conversely, HH resides in high spatial frequencies where local-contrast masking is strong; small structured changes are less visible in textured/edge-dense regions. Embedding in HH with a smaller leverages this masking while remaining sensitive to tampering that alters fine structures (such as sharpening, resampling, inpainting, local smoothing), thereby improving resilience and manipulation traceability when combined with the LL path.
The directional bands LH and HL are less suitable carriers. Their anisotropy makes them unstable under small rotations and sub-pixel resampling, which redistribute energy between LH and HL and weaken any band-specific payload. Linear smoothing/denoising suppresses LH/HL more strongly than LL and often less predictably than HH, reducing the payload SNR; direction-specific artifacts (such as motion blur along a dominant axis) further degrade one band disproportionately, complicating thresholding and reducing cross-dataset consistency. Empirically, these factors produce less predictable NC across attacks for the same visual budget. Selecting LL+HH therefore balances robustness (LL) with fine-detail responsiveness (HH) while keeping distortion low and control simple through two strengths
rather than four. Our sensitivity analysis in
Section 5.1 shows that moderate
preserves PSNR
dB and maintains high NC under representative attacks, supporting this design choice.
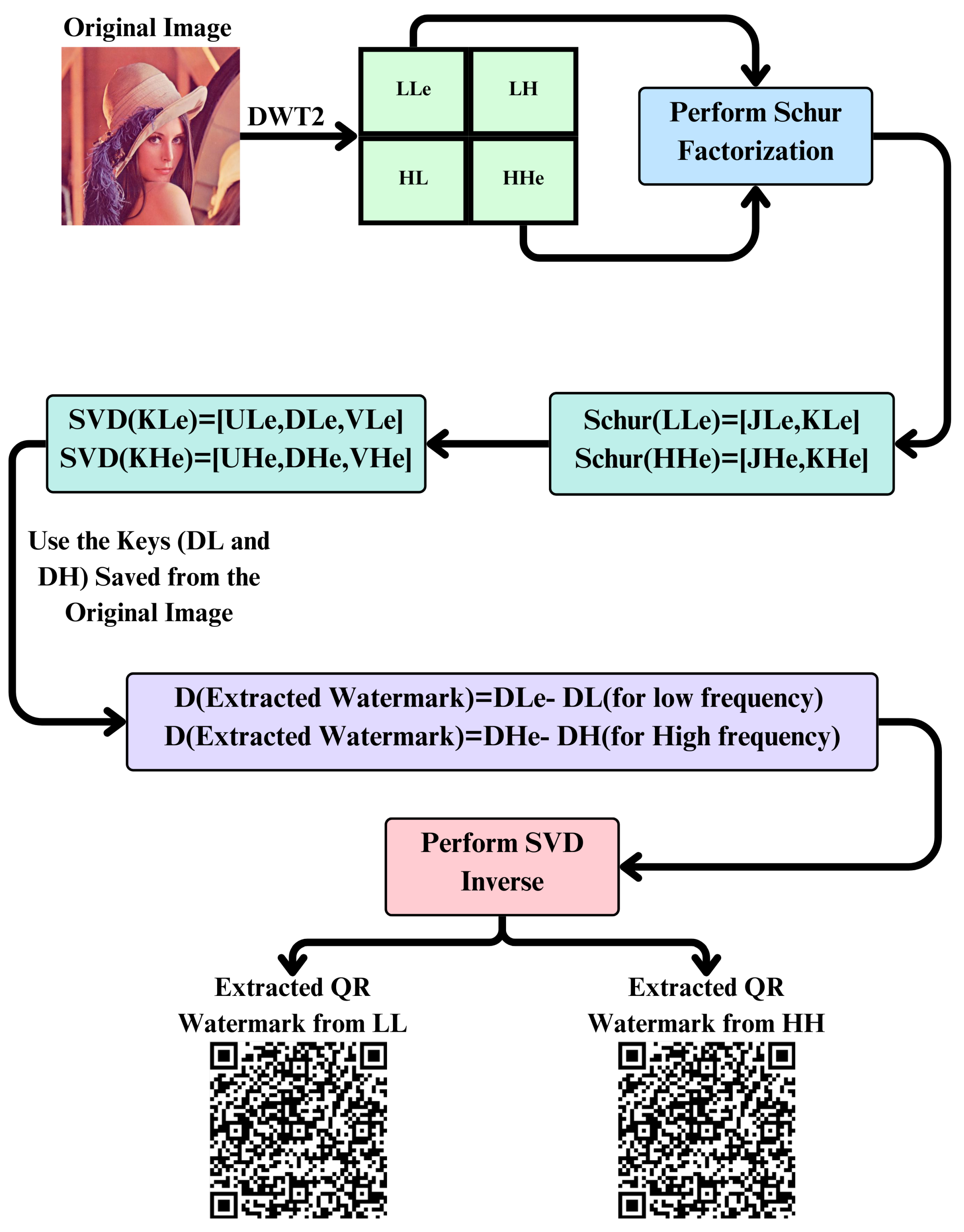
4.2. Watermark Extraction
The watermark extraction processes are designed to accurately retrieve the embedded watermark from the watermarked image. This process leverages several advanced techniques, including DWT, Schur matrix factorization, and SVD.
Figure 4 presents our watermark extraction scheme in detail.
The first step in the watermark extraction process is to use a two-level DWT on the watermarked image. This breaks the image down into four sub-bands: LLe (low–low), LHe (low–high), HLe (high–low), and HHe (high–high). DWT gives the image a multi-resolution representation, which makes it easy to work with different frequency components. This step is very important because it prepares the image for more processing by separating different frequency bands.
In the second step, we perform the Schur matrix factorization for the matrices in the LLe and HHe frequency sub-bands to obtain for the LLe frequency and for the HHe frequency. Schur factorization decomposes a matrix into an orthogonal matrix and an upper triangular matrix. This is important for preserving the structural features of the image and for isolating the necessary components required for watermark extraction.
In the third step, SVD is applied to both
and
matrices, decomposing them into their singular values and corresponding matrices. This step is represented by Equations (
24) and (
25).
In the fourth step, the watermark is taken out of the watermarked image using the singular values that were saved during the embedding process (
and
). To obtain the singular values of the extracted watermark, you subtract the singular values of the original image from the singular values of the watermarked image. This step makes sure that the watermark is retrieved correctly without changing the main parts of the image. These Equations (
26) and (
27) show this step.
The inverse SVD is then applied in the fifth step on the extracted singular values to recover the watermark. This process ensures that the embedded watermark is recovered faithfully and remains perceptually strong. The inverse SVD operation is very important to ensure that the watermark is retrieved accurately and without any visible artifacts or distortions. The recovered watermark is restored by the inverse SVD. This process guarantees that the watermark is correctly recovered and can be used for verification, etc. It is clear from the above description that after applying these procedures, when extracting the watermark from the watermarked image according to a proposed watermark extraction scheme, the watermark can be accurately and robustly extracted in its entirety while ensuring that neither the quality of the image nor the quality of the watermark is degraded. Algorithm 2 shows the used extraction method in detail.