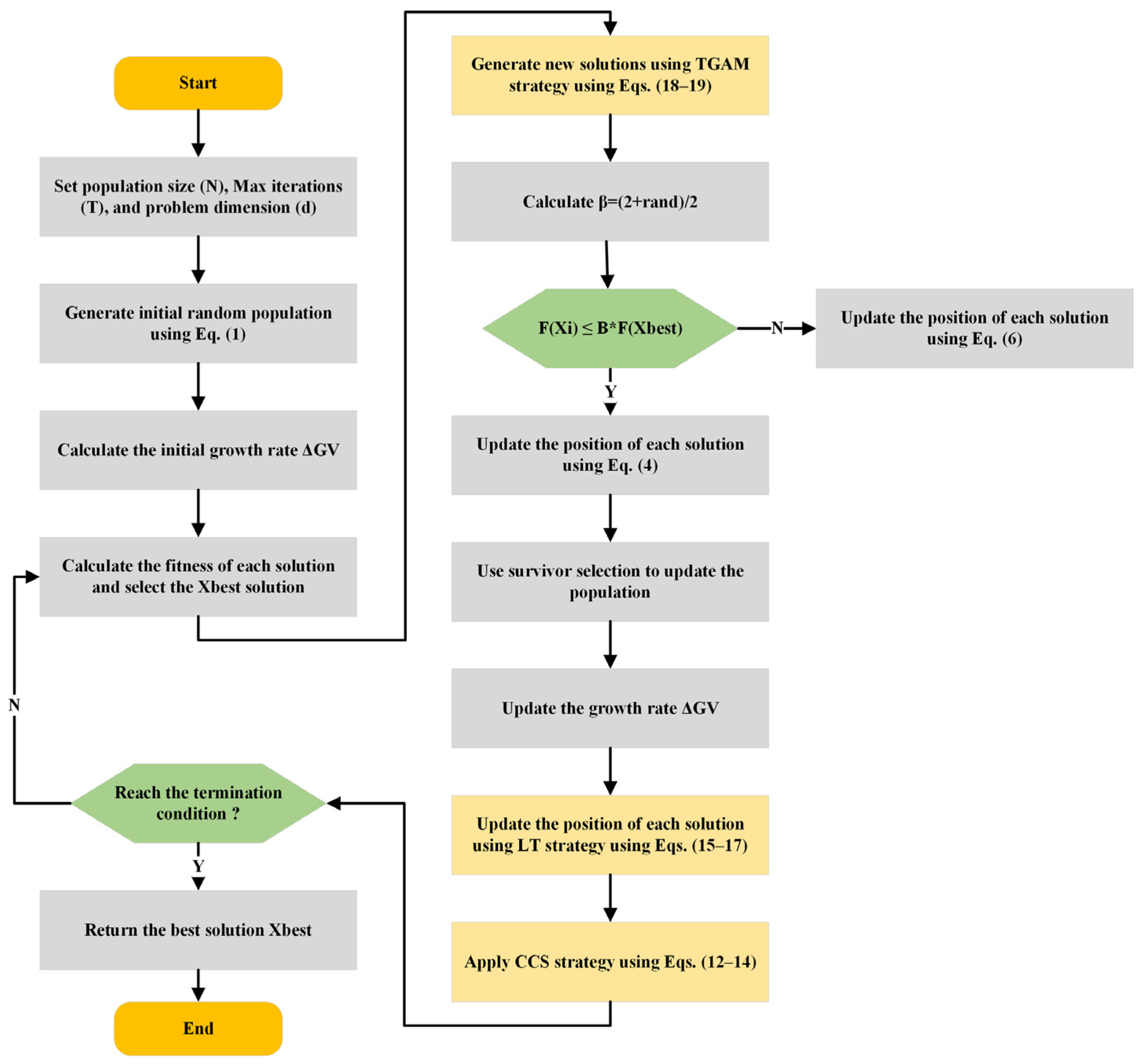
4.1. ACIVY for Global Optimization
This section gives a thorough analysis of the ACIVY algorithm by describing the experimental setup, as well as examining its performance in comparison to the other optimization techniques. The analysis consists of extensive experimentation on the CEC2017 [
60] and CEC2022 [
61] benchmark functions, modeling various real-world optimization problems. The convergence dynamics of ACIVY, as well as the distribution of performance depicted by boxplots, are also discussed in this part. Further, comparative experiments against state-of-the-art evolutionary strategies are also provided to demonstrate the efficacy of ACIVY in handling high-dimensional and complicated optimization landscapes.
4.1.1. Experimental Configuration and Settings
Two well-known benchmark sets, CEC2017 and CEC2022, were used to test ACIVY’s optimization power. CEC2017 suite comprises 29 different functions of different characteristics- unimodal (F1 and F3), multimodal (F4–F10), hybrid (F11–F20), and composite types (F21–F30). In the meantime, CEC2022 concentrates on 12 advanced functions designed to test the performance of algorithms on deceptive as well as high-dimensional problems. Each function of both suites is defined in the domain . These testbeds are designed purposefully to test the skill of an optimizer on both exploration (global search) and exploitation (local refinement).
Moreover, the experimental run was conducted with the dimensions of 50 for CEC2017 and 20 for CEC2022. All the tests were performed with a constant population size of 30 solutions, 30,000 function evaluations, and 30 repetitions were carried out independently to make the statistical analysis meaningful. All performances were conducted on a computing system composed of a 2.60 GHz Intel Core i7 10750H CPU, 32 GB RAM, and Windows 10 (64-bit), and all codes were written in MATLAB R2020b.
For benchmarking purposes, ACIVY was assessed against a wide spectrum of MAs, categorized into three main groups. The first group includes foundational methods such as AOA [
62], WOA [
31], and HHO [
30], all widely adopted for their general reliability. The second group contains more recently introduced optimizers like SWO [
63], COA [
64], CFish [
65], SHO [
66], GJO [
67], and HMO [
68], which propose recent strategies in search methodology. The third group comprises advanced and competition-winning algorithms such as eCOA [
69], CMAES [
39], GWO_CS [
70], RDWOA [
71], CSOAOA [
72], DAOA [
73], ISSA [
74], jDE [
75], and IPSO_IGSA [
76], representing state-of-the-art optimization capability. Detailed settings for each algorithm are listed in
Table 1.
The selected benchmark algorithms to compare with are based on their proven relevance and confirmed efficiency in a wide range of optimization cases. The classical methods act as a solid background, the results of which are predictable over time, and the newer models represent the rising opinions and search strategies [
77,
78]. Additionally, newer and high-scoring algorithms, particularly those that have succeeded in competition, are included to ensure that the comparison framework spans a large performance range. This multi-level choice offers the opportunity to evaluate the performance of ACIVY carefully and objectively against popular, new, and state-of-the-art metaheuristics.
4.1.2. Metrics for Evaluating Optimization Performance
In order to impartially assess the quality of work of the ACIVY algorithm among these different rivals, there are a number of statistical and descriptive measures. These are the average quality of solutions (AVG), standard deviation (SD), Friedman ranking (FR), and the Wilcoxon rank-sum significant test. All the metrics have their role in the profiling of consistency, reliability, and superiority of the optimizer.
Mean Fitness (AVG): The measure of the quality of solutions typically attained is the average fitness score over different independent runs. This measurement is useful in the evaluation of the correctness and general performance of an algorithm in repetitive usage, within the same setup. It is calculated with
where
is the number of runs and
is the fitness value obtained in the
trial.
Standard Deviation (SD): SD quantifies the extent of dispersion of the fitness values around the mean, providing information about the consistency and stability of the results produced by the algorithm. Smaller variations show that the optimizer provides consistent results when repeated many times. It can be calculated as follows:
Friedman Ranking (FR) [
79]: This non-parametric statistical test ranks algorithms based on their relative performances across multiple problem instances. A lower average rank suggests a superior performance. The final ranking is derived from averaging ranks over all tested functions. The Friedman test statistic is then evaluated using a chi-squared distribution to determine consistency in relative performance across functions.
Wilcoxon Rank-Sum Test [
80]: To establish whether performance differences between ACIVY and any competing algorithm are statistically meaningful, the Wilcoxon rank-sum test is utilized. A
-value below 0.05 denotes a significant difference. If ACIVY achieves better results, it is marked with
; if no clear difference exists, it is annotated with
; and if ACIVY underperforms, it is labeled with
.
A combination of these metrics provides an extensive basis to compare ACIVY to other algorithms and make sure that all findings regarding the optimization performance of this algorithm are statistically aligned and indicative of its practical potential.
4.1.3. Results Discussion Using CEC2022
The main goal of this part is to compare and review the functionality of the proposed ACIVY algorithm with an extensive list of well-known optimization algorithms on the CEC2022 benchmark collection. The variety of tested algorithms embodies the various algorithmic paradigms and serves as a thorough testbed to evaluate the performance of ACIVY on a wide range of optimization problems as presented in
Table 2.
On the unimodal function F1, ACIVY shows an outstanding performance, having the best rank and averaged fitness of 300.367, with an extremely low standard deviation of 0.354. Such a remarkable performance implies that ACIVY converges more precisely and reliably in single-optimum landscapes. The algorithm has spectacularly beaten all competitors, with the second-best performer (HHO) having a fitness value. Such a steep rise in performance underlines how well ACIVY’s coordinated growth and adaptive mechanisms exploit unimodal search spaces. Over the multimodal functions, ACIVY shows a continuously high performance and takes the leading position on F2, F3, and F4. On F2, ACIVY attains an average fitness of 454.503, only slightly higher than the original IVY at 461.213, indicating the improvement made with ACIVY along with preserving the strengths of the core algorithm. In the case of F3, ACIVY attains the theoretical maximum of 600.000 with a standard deviation of zero, indicating absolute convergence and superb reliability. Such a huge improvement suggests that ACIVY is more capable of traversing multimodal landscapes effectively and reliably finding global optima.
Furthermore, the hybrid functions reveal ACIVY’s robust adaptability across different problem characteristics. ACIVY secures first place on F5 and F7, second place on F6, and third place on F8, maintaining an average rank of 2 across this category. Notably, on F5, ACIVY achieves a fitness value of 1402.843, substantially outperforming the second-best GJO (1891.702). The algorithm’s performance on F6 is particularly noteworthy, where it achieves the second-best result with a significantly lower standard deviation compared to many competitors, indicating superior solution stability. In the most challenging composite function category, ACIVY demonstrates consistent excellence by securing first place on F9, F10, F11, and F12. This comprehensive dominance across all composite functions is particularly significant, as these problems combine multiple optimization challenges and represent the most complex scenarios in the benchmark suite. On F9, ACIVY achieves a near-perfect performance with a fitness value of 2480.811 and an exceptionally low standard deviation of 0.054, indicating both optimal solution quality and remarkable consistency across independent runs.
The base IVY algorithm shows decent results and ends up at a rank of 4, which confirms the base idea but also shows how much better the results can be with the additions that ACIVY provides. CFish takes the second overall spot with a solid performance across many functions, and GJO completes the top three with steady mid-range rankings. Such advanced algorithms as HHO, SHO, and HMO have different performance levels, where HHO took sixth place and provided competitive results on particular functions, such as F1. Nevertheless, the performance of all these established algorithms is not consistent with the performance of ACIVY on the wide categories of functions. Moreover, the algorithms ranked last (SWO, AOA, and COA) perform especially poorly on multimodal and composite functions, and their results have a high standard deviation, which means that the algorithms do not produce reliable solutions. This comparison underlines the superiority of ACIVY in terms of robustness and flexibility on varied optimization landscapes.
The behavior of the performance of ACIVY is distinguished not only by high-quality average fitness values but also by the low standard deviations in most functions. This combination implies that ACIVY reliably converges to high-quality solutions on multiple independent runs, an important trait in the practical use of optimization. The capability of the algorithm to sustain low variance with optimal or near-optimal fitness values shows the efficiency of adaptive mechanisms and well-balanced exploration–exploitation schemes.
Having the average rank of 1.25 over all twelve functions and obtaining the last rank of 1, ACIVY confirms itself as the most efficient algorithm in this full comparative study. The large difference in performance between ACIVY and the second-placed CFish (average rank 4.00) highlights the extensive algorithmic progress that the crisscross strategy, LT strategy, and TGAM improvements bring. These findings unreservedly show that the bio-inspired improvements incorporated in ACIVY effectively overcome the weaknesses of the original IVY algorithm, without affecting its principal advantages. The outstanding performance of the algorithm in a wide variety of categories of functions confirms its applicability to real-world optimization problems, which need robust, reliable, and high-accuracy solutions.
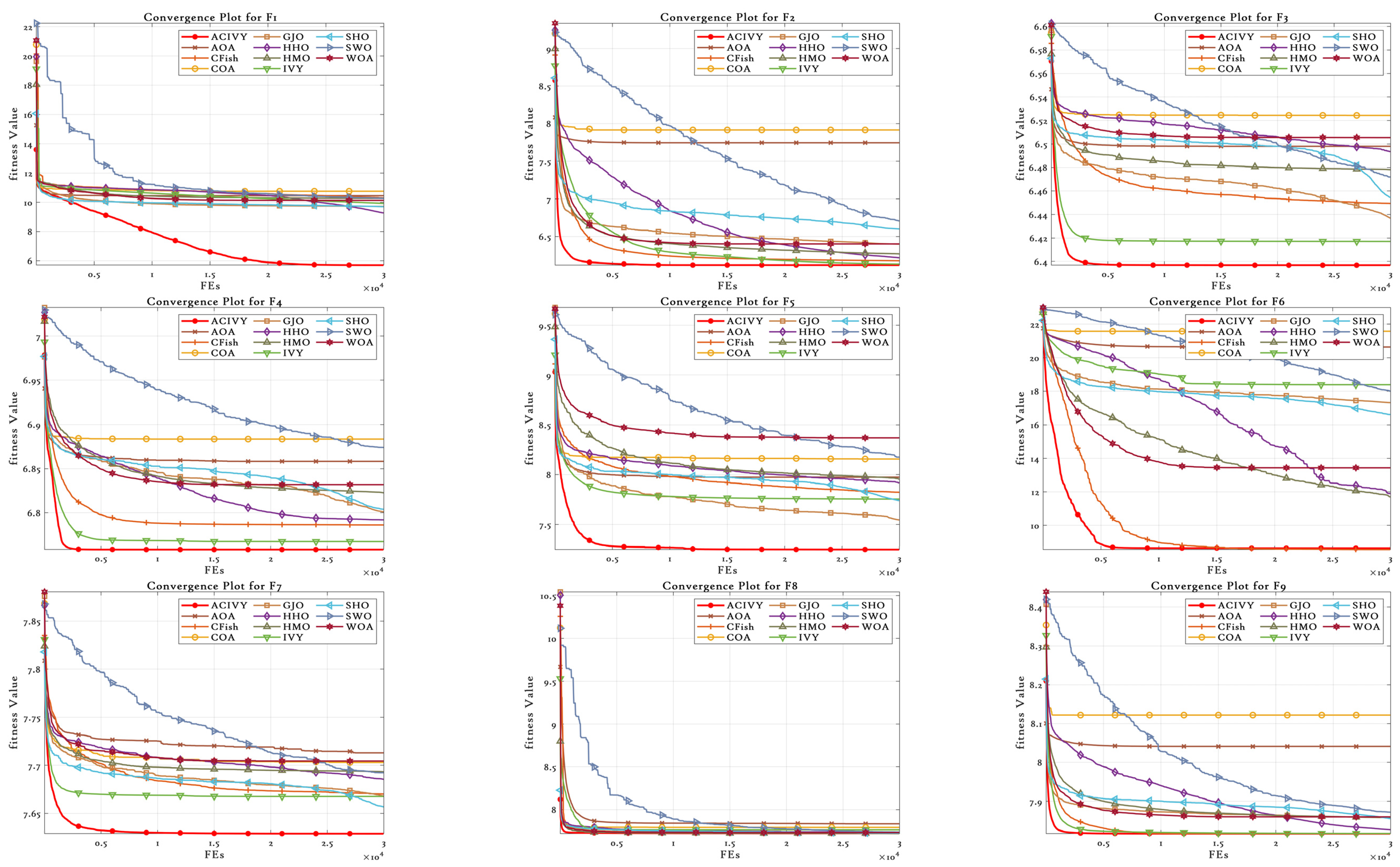
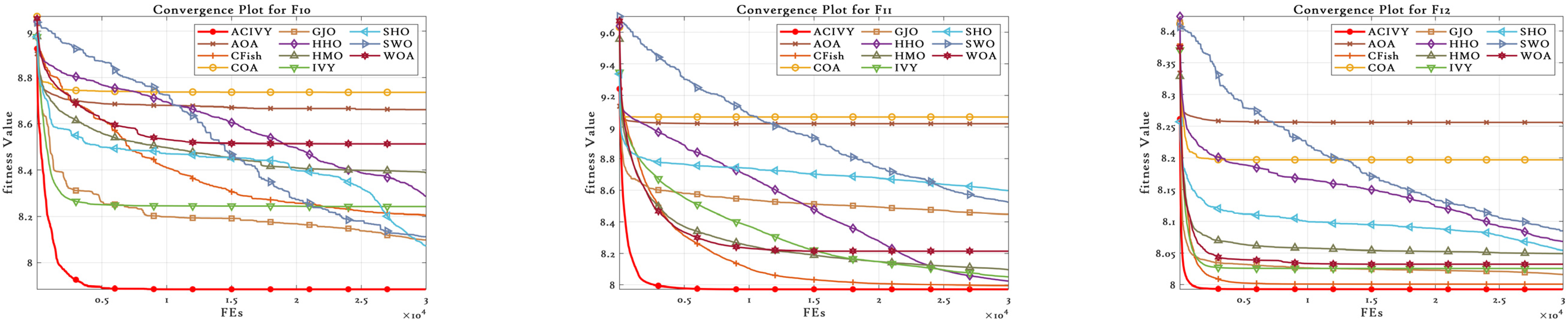
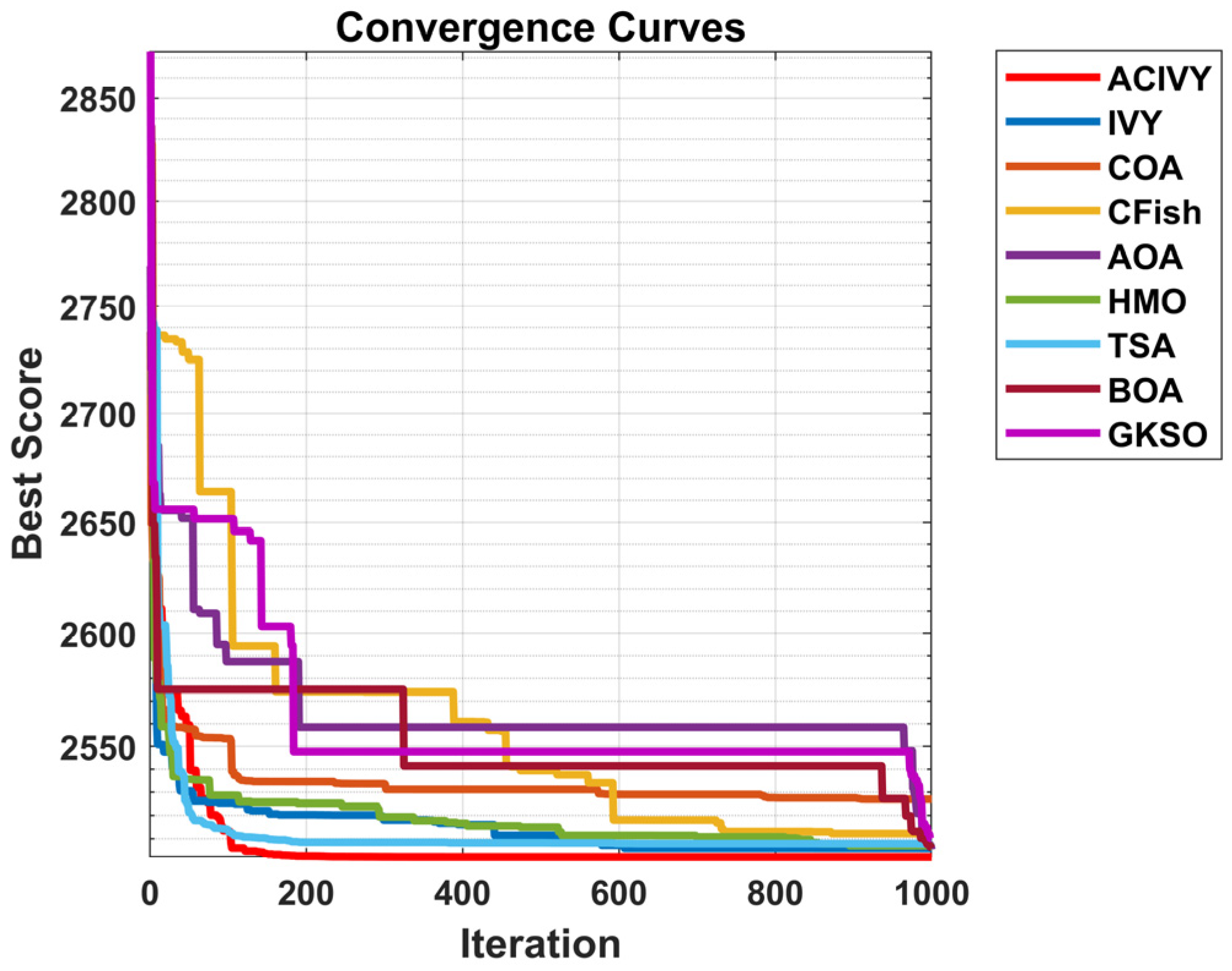
The convergence plots show the clear optimization behavior of ACIVY on the CEC2022 benchmark functions, and it exhibits better convergence properties than the competing algorithms as shown in
Figure 2. According to
Figure 2, ACIVY can be characterized by fast initial convergence and subsequent stable refinement stages and is fastest in terms of fitness values in all categories of functions. The convergence curve of the algorithm can be described as having very sharp initial drop-off curves followed by very rapid stabilization at optimal or near-optimal solutions, which implies the existence of effective exploration-to-exploitation transition mechanisms within the improved ivy-inspired strategies. In the case of unimodal and simple multimodal functions (F1–F4), ACIVY shows a remarkable convergence rate and achieves optimal solutions in the initial 5000–10,000 FEs. The convergence curves depict dramatic fitness gains during the initial iterations, where F1 and F3 converged to the theoretical optimum with little variance. Conversely, the competing algorithms either converge at non-optimal solutions or have slower rates of convergence with better final fitness values. It is noteworthy that the original IVY algorithm demonstrates decent convergence behaviors but cannot compete with ACIVY in terms of accuracy and speed, which proves the efficiency of the suggested improvements.
The hybrid functions (F5–F8) demonstrate the strong flexibility of ACIVY to a complex landscape, with identical convergence behavior when the problem complexity is increased. The algorithm shows no or minimal oscillations and no stagnation periods associated with state-of-the-art algorithms. Function F6 and F7 especially demonstrate the high performance of ACIVY, in which the algorithm quickly converges in less than 10,000 FEs, whereas other algorithms are still struggling with either slow convergence or plateau phenomena. These functions feel the impact of the LT strategy, as they allow proper escape out of local optima, which other algorithms get stuck in. In the most difficult composite functions (F9–F12), the convergence pattern of ACIVY is extremely regular and accurate, showing the fastest descent rates and being stable during the optimization process. F11 and F12 demonstrate the capability of the algorithm in finding optimal solutions in these complex multimodal landscapes, whereas ACIVY either gets stuck in local optima or exhibits unstable convergence behavior. The attribution of the TGAM strategy is especially reflected in these functions, which allow an easy transition between exploration and exploitation stages without affecting the quality of the convergence. Such a high convergence performance in all types of functions proves the efficiency of ACIVY as a strong and trustworthy optimization algorithm to handle complex real-world problems.
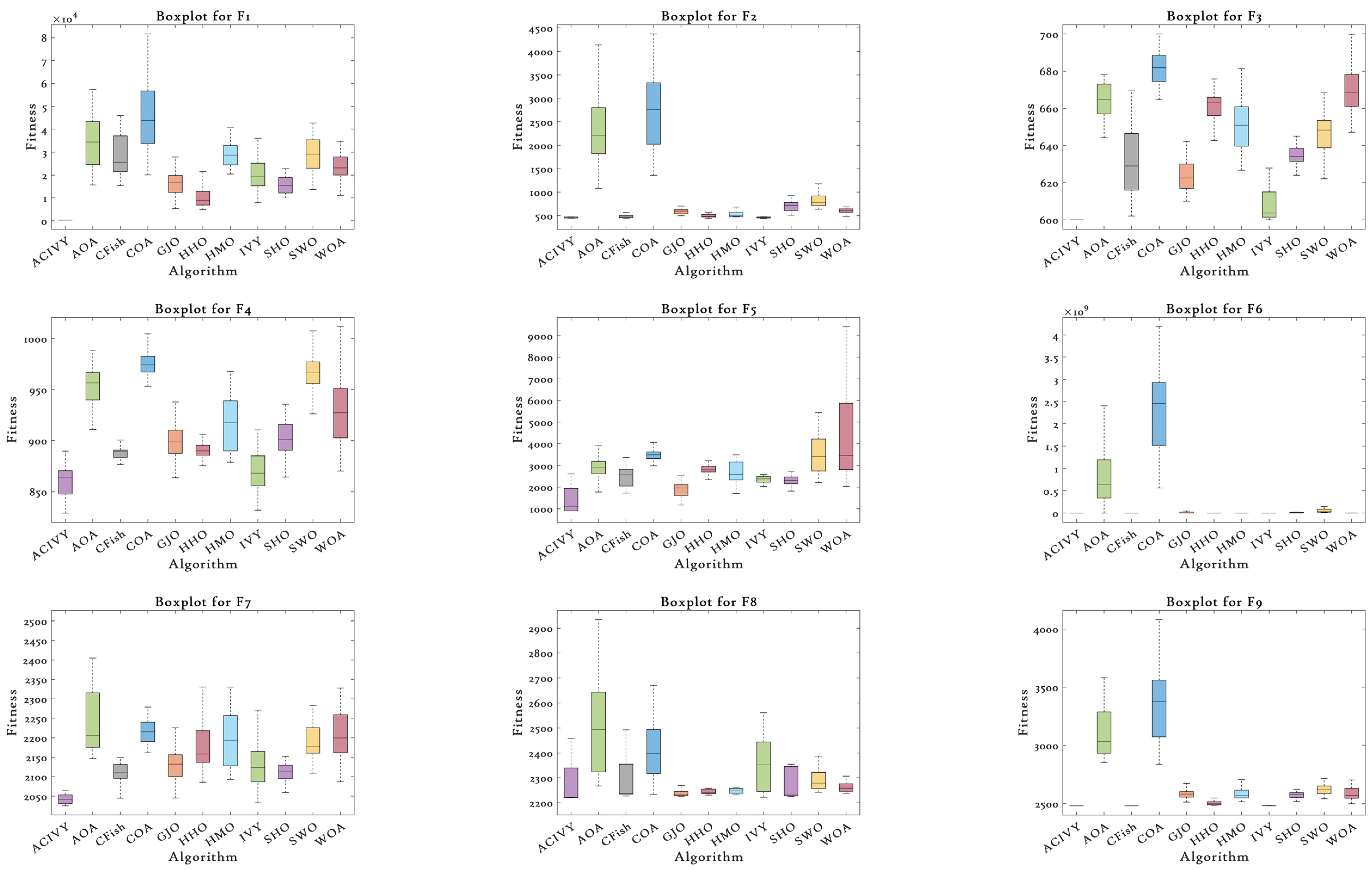
On the other hand, the boxplot analysis shown in
Figure 3 thoroughly reveals the statistical distribution nature and the reliability of the solution of ACIVY versus the rival algorithms on the CEC2022 benchmark functions. The boxplots display important performance metrics such as median fitness values, quartile ranges, the existence of outliers, and the overall consistency of solutions. ACIVY achieves statistical excellence in all aspects regarding medians, interquartile ranges, and the presence of outliers, showing the quality of the solution is optimal and the algorithm is very stable across all types of functions.
In the case of unimodal and multimodal functions (F1–F4), ACIVY shows the tightest boxplot distributions with the lowest median fitness values and minimal interquartile ranges. On F1, the boxplot of ACIVY is incredibly tight and centered around the theoretical optimum, whereas the competitors have much broader ranges and larger medians. The F3 boxplot especially shows the superiority of ACIVY, which has reached perfect convergence with zero variance, displayed as a single horizontal line at the optimal value of 600. Conversely, other algorithms, such as AOA and COA, exhibit very long whiskers and several outliers, which reflect the lack of consistency and reliability of the solution. The hybrid functions (F5–F8) illustrate the strong stability performance of ACIVY with regard to its boxplot structures that tend to be small even in multi-dimensional optimization landscapes. F6 shows that ACIVY has an outstanding performance with a very narrow distribution and low median, whereas competitors have large ranges and many outliers. The effect is especially dramatic when the compact boxplot of ACIVY is compared with the extremely wide distribution of COA spanning several orders of magnitude. F7 and F8 additionally affirm the statistical superiority of ACIVY, with low variance and ideal median rankings in comparison to the random and unreliable distributions of the rival algorithms. The composite functions (F9–F12) demonstrate the ultimate statistical excellence of ACIVY with the best median performance and superior distribution tightness. ACIVY ensures the minimum median values of all composite functions and shows an impressive consistency expressed in small boxplot ranges. This superiority is illustrated on F11, where ACIVY obtains a compact distribution with short whiskers, whereas the other algorithms, such as AOA and COA, exhibit a large population of outliers and broad quartile sticks. The statistical experiment appears to clearly indicate that ACIVY is not only capable of higher optimization performance but also offers the best degree of algorithm robustness and predictability which are critical properties of algorithms intended to be used in practice and needed to generate high-quality solutions consistently.
The testing of statistical significance is an important aspect in the optimization algorithm performance superiority proofs, as the observed performance gains can be easily attributed to random fluctuations [
81]. The analysis of MAs must be accompanied by sound statistical testing in order to determine the confidence of comparative outcomes, especially in the case of stochastic optimization algorithms, which are by nature prone to variation with multiple independent runs. In this analysis, two basic non-parametric statistical tests are used: the Friedman test to evaluate the overall ranking and the Wilcoxon rank-sum test to compare each pair of algorithms, respectively, which were explicitly invented to work with non-normal distribution data, as optimization algorithm performance data often is.
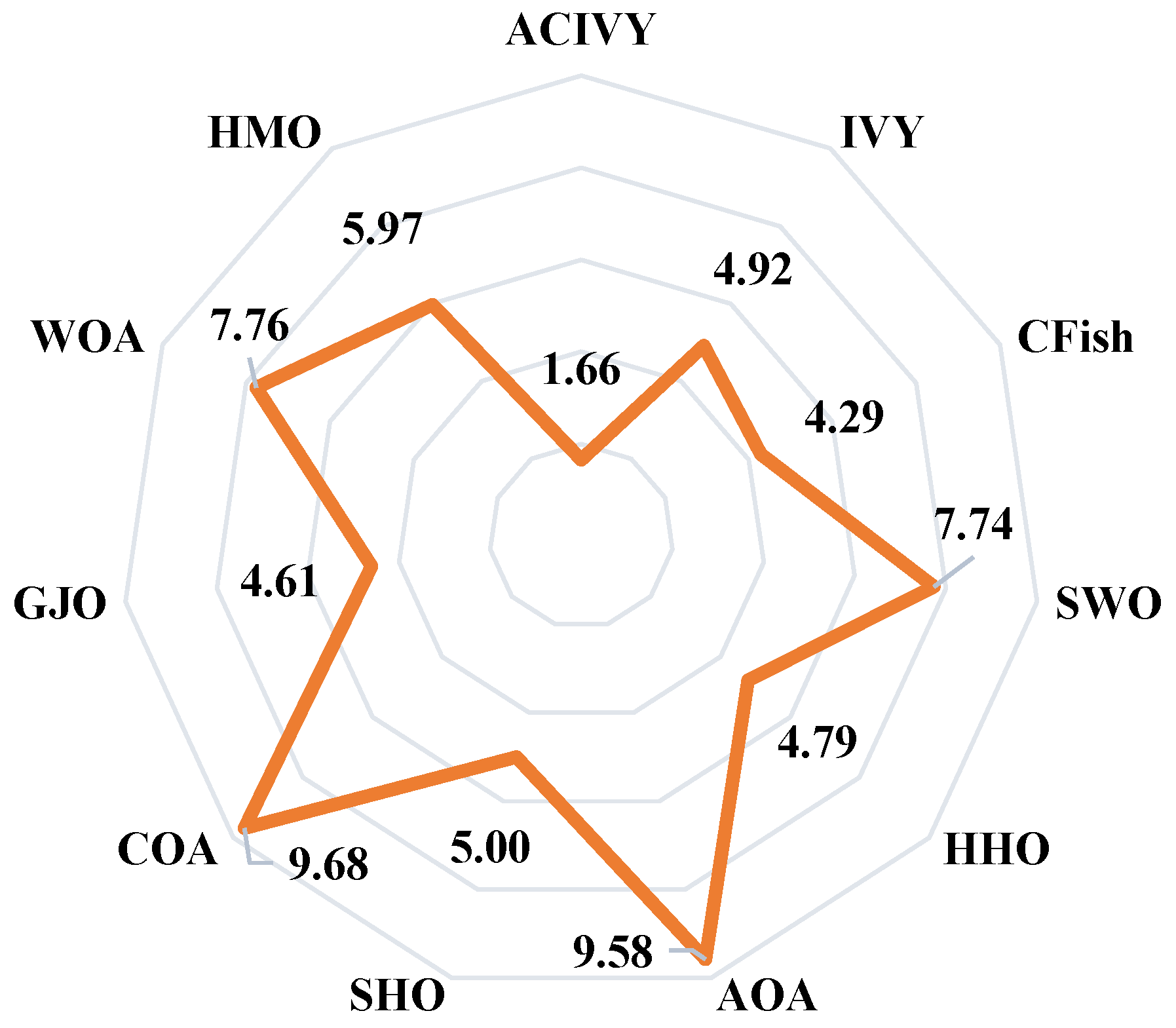
Figure 4 shows the results of the Friedman test, which gives a full ranking analysis of each of the algorithms on the entire CEC2022 benchmark suite. ACIVY attains the best average rank of 1.66 and significantly outcompetes all the competing algorithms and statistically dominates them in varying optimization landscapes. The original IVY algorithm still achieves a respectable average rank of 4.92, confirming the validity of the underlying approach but pointing to the immense gains made by ACIVY’s enhancements. The ranking order shows the existence of specific performance levels, where CFish (4.29) and GJO (4.61) comprise the second performance level and HHO (4.79) and SHO (5.00) belong to the middle-level performances. HMO (5.97), SWO (7.74), and WOA (7.76) are placed in the bottom part of the ranking, and AOA (9.58) and COA (9.68) take the last places. Such statistical ranking proves the outstanding ability of consistency in the performance of ACIVY in all categories of functions, and this shows its great flexibility in facing different kinds of optimization problems.
On the other hand,
Figure 5 shows the pairwise Wilcoxon rank-sum test results, which extensively statistically prove the superiority of ACIVY over each of the competing algorithms in a pairwise manner. The analysis shows the clear statistical overpowering of ACIVY with higher performance (
) values varying between 10 and 12 functions over all the competitors, whereas the
values are always zero in all of the pairwise comparisons. Compared to AOA, CFish, COA, GJO, HHO, HMO, SWO, and WOA, ACIVY has statistical dominance (shows a better performance on 12 functions and never performs worse on any of the 12 functions). ACIVY also performs better on 10 functions against IVY and SHO, with 2 ties (
), and once more, 0 worse performances. The
values suggest that there are some statistical ties with CFish and GJO (one function each) and SHO (two functions), but these are not losses but statistical ties, which once again underline the superiority of ACIVY across the board.
This statistical evidence gives unquestioning confirmation of the algorithmic superiority of ACIVY over the benchmark suite. The Friedman test confirms the superior position of ACIVY with the minimal average rank of 1.66, and the Wilcoxon rank-sum test proves the overall superiority of the former with its pairwise wins. Overall, the lack of values (zero inferior performances) in all algorithmic comparisons is a startling statistical feat, which means that ACIVY does not show a worse performance than any of its competitors on any of the benchmark functions. This stable trend of statistical significance, together with the large performance gaps demonstrated by the Friedman ranks, gives strong indications that the improvements found by ACIVY are not fluctuations but actual algorithmic advances. The statistical strength of these findings puts high confidence in the reliability and efficacy of ACIVY, making it a statistically proven method of handling complex optimization problems where not only is excellent performance needed, but also reliability across a wide range of problem landscapes.
4.1.4. Results Discussion with Advanced Algorithms Using CEC2017
In this section, the performance of ACIVY is compared with state-of-the-art algorithms on the CEC2017 benchmark suite of 50-dimensional problems, which, together with the earlier analysis on CEC2022, gives a thorough verification of the algorithm on various benchmark standards and problem dimensions. The comparative analysis involves ten advanced algorithms, namely, eCOA, CMAES, DAOA, CSOAOA, GWO_CS, RDWOA, jDE, ISSA, and IPSO_IGSA, which are recent advancements in evolutionary computation, swarm intelligence, and hybrid optimization techniques.
According to
Table A1, ACIVY shows a remarkable performance advantage throughout the CEC2017 benchmark set, taking the final overall first rank with an incredible average rank of 1.41, which is significantly better than all other participating advanced algorithms. The algorithm ranks first on 20 of 29 functions (win rate of 69.0%), ranks second on 7 functions, third on F17, and fourth on F10, giving a top-two result on 93.1 percent of the benchmark problems. CSOAOA turns out to be the second-best-performing with the final rank of second (average rank 3.17), and GWO_CS ranks third (average rank 3.72), and eCOA ranks fourth (average rank 3.79). The performance hierarchy shows that there are large differences between ACIVY and its nearest rivals, where DAOA is placed at the bottom (final rank 10, average rank 10.00), indicating the existence of large algorithmic advantages of ACIVY. Function category analysis reveals ACIVY’s performance patterns across diverse optimization landscapes with distinct characteristics for each problem type. For unimodal functions (F1, F3), ACIVY achieves perfect dominance with a 100% win rate (two out of two functions), demonstrating exceptional exploitation capabilities where F1 shows a fitness value of 6296.553 compared to DAOA’s 2.83 × 10
11. In multimodal functions (F4–F10), ACIVY secures first place on only two functions (F4 and F6), achieving a 28.6% win rate, but maintains a strong performance with second place on F5, F7, F8, and F9, and fourth place on F10. Despite the lower win rate, ACIVY’s fitness values remain highly competitive, with F4 showing 506.774 versus competitors ranging from 643.383 to 1.04 × 10
5. The hybrid functions category (F11–F20) showcases ACIVY’s superior adaptability with an 80% win rate (8 out of 10), securing first place on F11, F12, F13, F14, F15, F16, and F18, with second-place finishes on F19 and third place on F17. In this category, F12 particularly exemplifies ACIVY’s dominance with a fitness value of 5.89 × 10
6 versus DAOA’s 1.41 × 10
11. For composite functions (F21–F30), ACIVY demonstrates remarkable consistency with 80% superiority (8 out of 10), winning on F20, F21, F23, F24, F25, F26, F27, F28, and F29, while achieving second place on F30 and F22. The performance distribution reveals ACIVY’s exceptional strength in complex hybrid and composite functions, where its enhanced mechanisms prove most effective.
The comparative analysis reveals significant fitness value disparities between ACIVY and advanced competitors across critical benchmark functions. On function F1, while ACIVY achieves 6296.553, its closest competitor, ISSA, reaches 1.76 × 108, representing a large performance gap, with other algorithms like CMAES and DAOA performing orders of magnitude worse. Function F12 demonstrates even more dramatic differences, where ACIVY’s 5.89 × 106 substantially outperforms eCOA’s 3.83 × 108 and completely dominates DAOA’s catastrophic 1.41 × 1011. In the hybrid function F14, ACIVY maintains 1.78 × 105 while advanced algorithms like CMAES struggle with 2.14 × 107, and DAOA fails at 3.46 × 108. These substantial performance margins highlight ACIVY’s superior convergence precision and global search capabilities compared to even the most sophisticated contemporary algorithms. Furthermore, ACIVY consistently achieves lower standard deviation values, indicating superior solution reliability compared to competitors that often exhibit high variance and inconsistent performance across independent runs.
The Friedman test statistical significance of the CEC2017 benchmark shown in
Figure 6 generates the statistical dominance of ACIVY with a mean rank of 1.78, which is significantly better than all the sophisticated competitors on the 50-dimensional optimization search space. CSOAOA proves to be the most competitive algorithm with a mean rank of 3.21, slightly followed by eCOA 3.92, meaning that these algorithms are moderately competitive, irrespective of the fact that their performances differ significantly. There are the middle-tier GWO_CS (4.17) and ISSA (4.49), and the weak overall performance of such algorithms as CMAES (5.91), RDWOA (6.38), and IPSO_IGSA (7.01). The low-ranking algorithms, jDE (8.57) and DAOA (9.55), exhibit notably bad adaptation to high-dimensional optimization problems, where DAOA is ranked among the last in the majority of the functions.
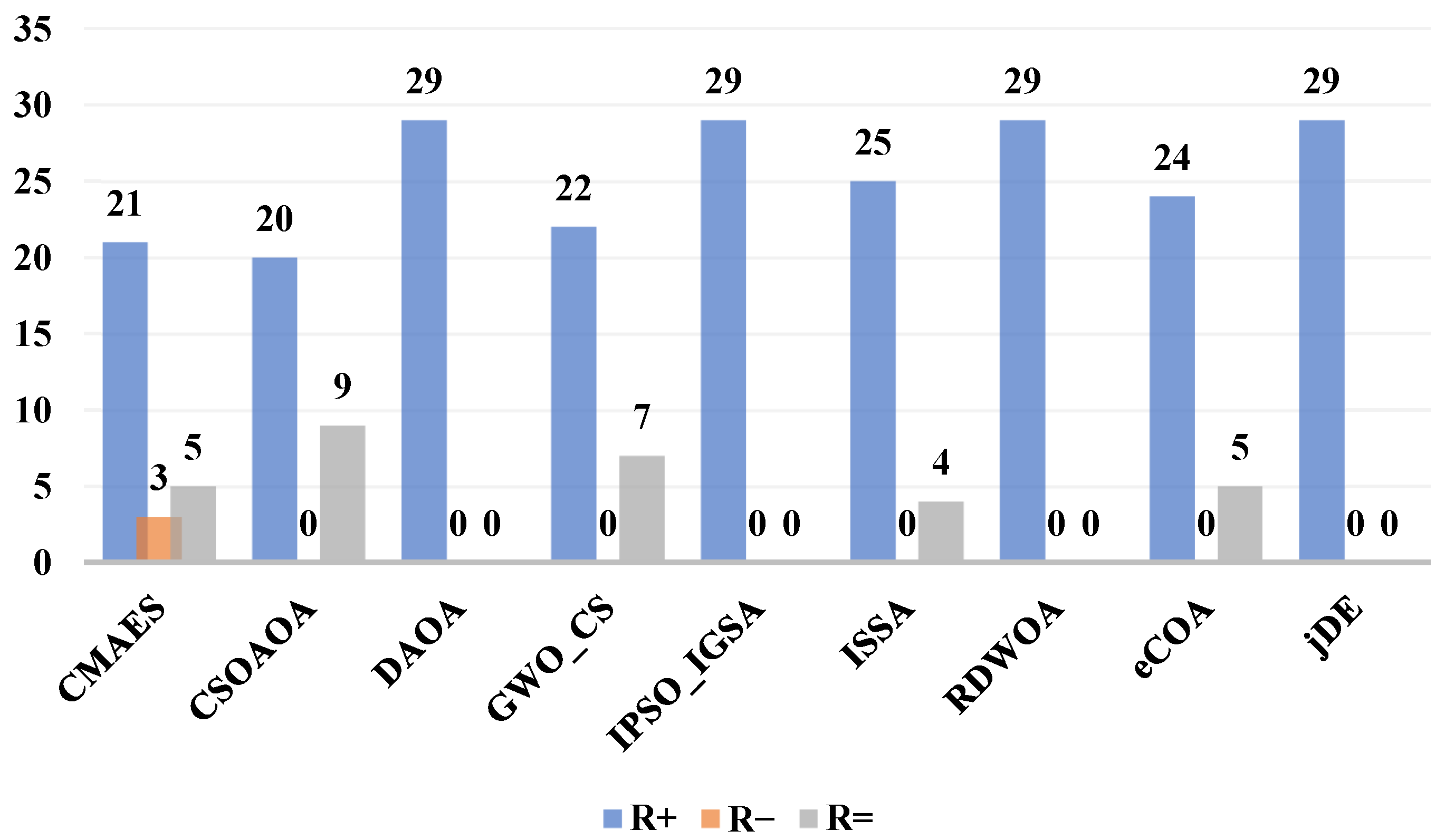
On the other hand, the Wilcoxon rank-sum test results shown in
Figure 7 provide comprehensive pairwise validation of ACIVY’s dominance, revealing overwhelming statistical superiority against all competing algorithms. ACIVY demonstrates complete dominance against CSOAOA, DAOA, GWO_CS, ISSA, RDWOA, eCOA, and jDE with R+ values of 20, 29, 22, 29, 25, 29, 24, and 29, respectively, while maintaining zero
values across all comparisons. Against CMAES, ACIVY shows superior performance on 21 functions with only 3 inferior performances and 5 ties, representing a 7:1 win-to-loss ratio. The
values indicate occasional statistical ties with CMAES (5), CSOAOA (9), GWO_CS (7), RDWOA (4), and jDE (5), but these represent performance equivalence rather than losses. The absence of
values against most algorithms demonstrates ACIVY’s remarkable consistency in outperforming advanced state-of-the-art methods across diverse optimization scenarios, establishing unequivocal statistical evidence of its algorithmic superiority in high-dimensional optimization contexts.
4.3. ACIVY for UAV Path Planning Optimization
In order to evaluate the practical relevance of the suggested ACIVY algorithm, its performance is considered in the area of unmanned aerial vehicle (UAV) navigation planning. Based on the fundamental assessments presented in
Section 4.1 and
Section 4.2, in which ACIVY demonstrated stable superiority over traditional and state-of-the-art MAs on the CEC2017 and CEC2022 benchmarks, this section applies it to the UAV path planning problem. The benchmark functions are renowned for having complicated traits such as high dimensionality, nonlinearity, and discontinuities that serve as good analogues of the problems posed by UAV trajectory design. Accordingly, the ACIVY algorithm will be tested in a simulated setting with circular areas of threats, as seen in real-life applications in defense, surveillance, and autonomous aerospace missions.
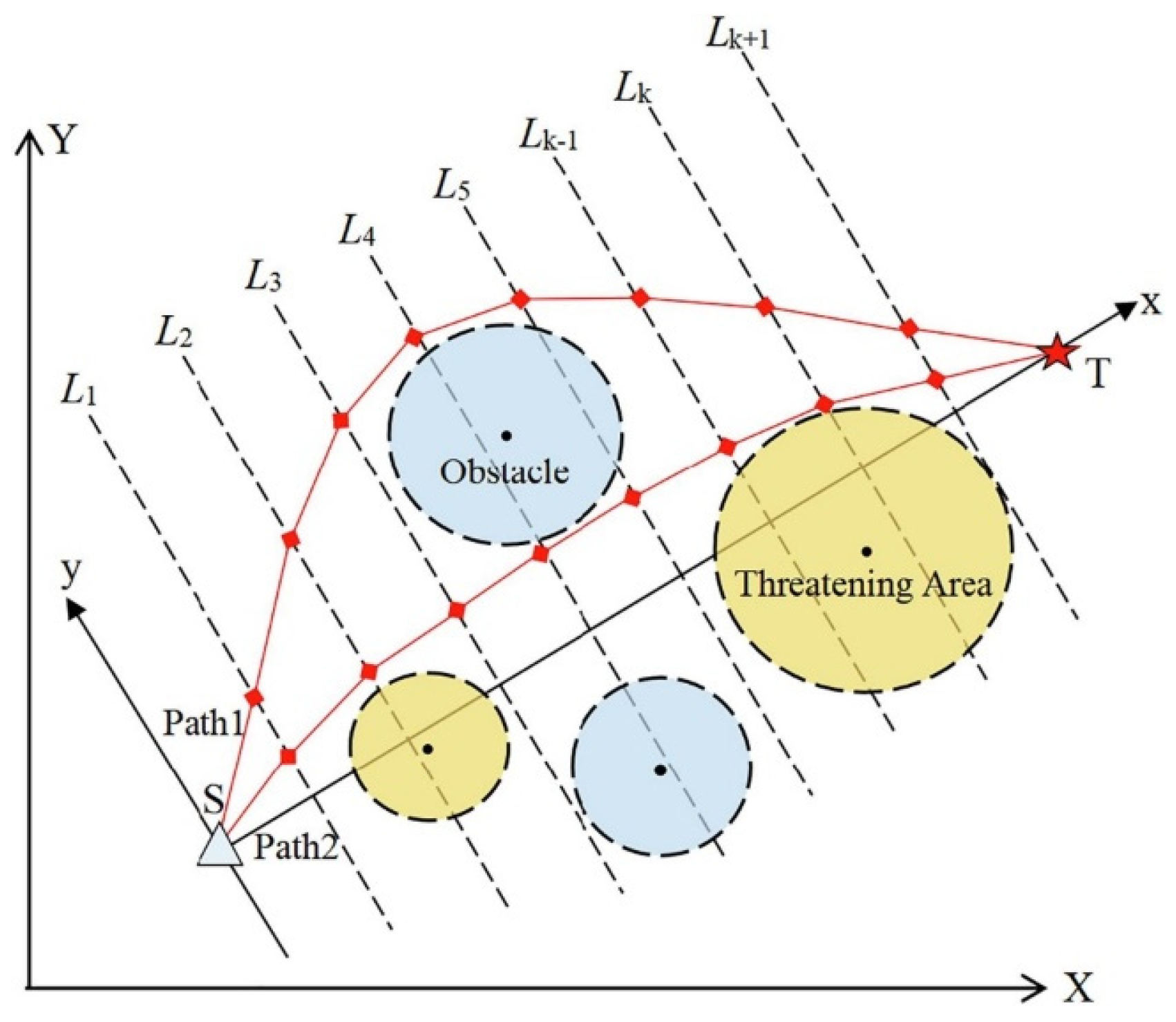
The UAV path planning problem can be formulated as follows: given a certain starting point and destination, find a trajectory that is optimal in some sense, with the constraints of operating in an environment filled with potential obstacles and operational constraints [
86]. Such risks might be in the form of terrain obstacles, enemy detection areas, or restricted airspaces. Moreover, the UAV has to observe physical limitations such as fuel capacity, dynamics, and maneuverability limits, like the turn radius and maximum climb rate. The operating environment is often idealized to a 2D or 3D grid with geometric obstacles, frequently assumed to be circles or polygons.
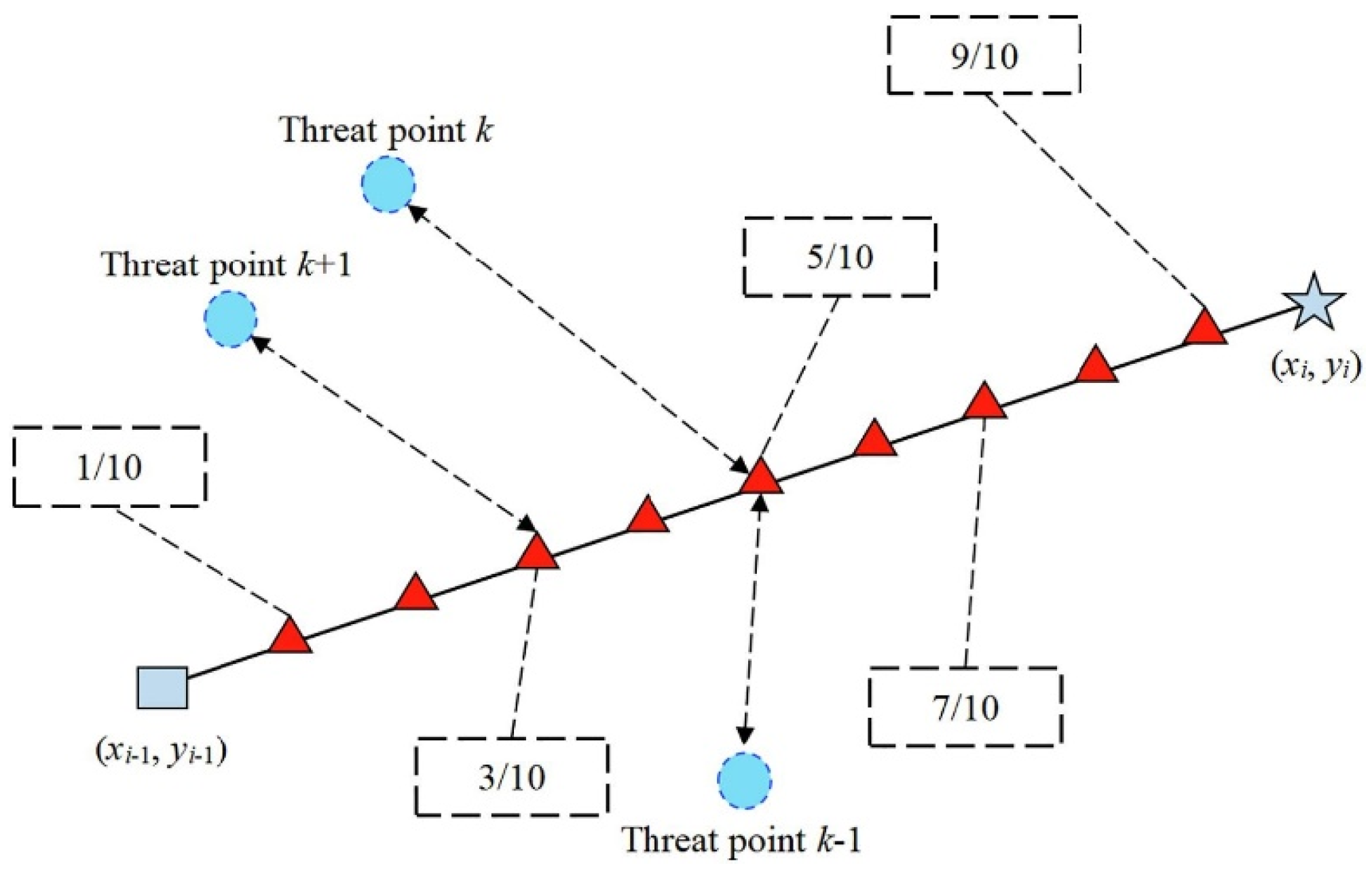
In this configuration, the object has to drive around doughnut-shaped areas, which are interpreted as regions of high risk, e.g., radar detection fields or dangerous terrain.
Figure 8 depicts that the UAV is initially at a known starting point
and has to reach the desired destination
. The direct line between
and
is split into
segments equally, which brings flexibility to the routing procedure. Also, the lines
,
,…,
,
perpendicular to the segmentation points are constructed. The lines each delineate a plane of potential discrete waypoints amongst which one optimum point may be chosen.
By connecting one point on each of these perpendicular segments in consecutive fashion, a closed and valid flight path is created that meets mission requirements and avoids any prescribed threat areas or restricted areas. Using this structure, a flexible, but constrained, optimization problem is enabled to precisely capture the nature of the operational needs of autonomous UAV systems. The complete set of navigation points is rigorously stated as
Such a discrete representation enables the ACIVY algorithm to search through a wide range of feasible paths and converge to one that achieves the minimization of exposure and fuel consumption and the feasibility of the route, considering environmental and vehicle-specific constraints. A coordinate transformation is used to ease the calculations and to match the optimization direction with the geometry of the problem. The transformation that moves the segment
into the new x-axis is
where
Here,
represents the angular deviation between the original x-axis and the segment
, allowing the trajectory generation to occur along a normalized reference frame. The fitness function used in this case is defined in terms of cost and fuel as shown in
Appendix A.
To thoroughly evaluate the proposed ACIVY algorithm in the context of UAV navigation, simulation experiments are carried out across different environmental configurations, each populated with circular threat zones. These test cases differ in threat zone density, spatial positioning, and risk magnitude, simulating a wide range of practical mission scenarios. The UAV begins its flight at position (2,2) and is required to reach the target location at (3299,3299), modeling a long-distance mission through potentially adversarial or restricted airspace.
The experimental configuration is the same in all the simulations. We limit each optimization process to 1000 iterations, and the size of the population is 30 solutions per generation. The problem space is characterized by 10 dimensions, which is equal to the number of intermediate decisions that constitute the path of the UAV. Each algorithm is run independently 30 times to make the statistical results reliable and consider the stochasticity of MA. The result of each run is stored, and such key performance indicators as the best, worst, average, and standard deviation of the final cost are calculated to compare.
The performance of ACIVY is compared to some well-known metaheuristic algorithms, which are the original Butterfly Optimization Algorithm (BOA) [
87], Crayfish Optimization Algorithm (CFish) [
65], Human Memory Optimization (HMO) [
68], Tunicate Swam Algorithm (TSA) [
88], Arithmetic Optimization Algorithm (AOA) [
62], Coati Optimization Algorithm (COA) [
64], and the original IVYA algorithm. The mentioned algorithms are well known to be successful in solving continuous and constrained optimization problems with nonlinear objective functions.
The strength and correctness of ACIVY are approved in three test cases that represent various spatial distributions of circular threat zones. The scenarios, as concluded in
Table 11, differ in the concentration of obstacles, size, and intensity, providing a wide range of assessments. These findings demonstrate that ACIVY is not only an efficient method to deal with nonlinear and high-dimensional trajectory optimization but also it is stable in various runs.
As observed in
Table 12, the results of the performance evaluation of Case 1 show that ACIVY is exceptionally competent in resolving the UAV path planning optimization problem in the first threat scenario setup. ACIVY provides the best performance in terms of all the statistical metrics because it has the best fitness value of 2502.12372, a mean fitness of 2502.32598, and the standard deviation is extremely low, 0.264660329. This extreme performance is properly several times faster than any of the competing algorithms, with the nearest rival BOA having a best fitness of 2504.41698 and a mean of 2506.60476, making the performance difference between this and the other algorithms. The advantage of the algorithm performance is even more significant in comparison to such methods as CFish (mean: 2536.58402 +/− 27.02260666) and TSA (mean: 2532.1528 +/− 16.26598301) that have a significantly higher cost and variance.
The statistical comparison shows a remarkable consistency and reliability of ACIVY in UAV mission planning, as its standard deviation is extremely low compared to all the competitors. Though such algorithms as IVY (2508.98792 +/− 2.318207734) and HMO (2510.85416 +/− 2.372573147) demonstrate a certain consistency in performance, they remain far behind in accuracy when compared to ACIVY. Such consistency is especially important in real-world UAVs where the reliability of missions and predictability of performance are top priorities, and as seen in the case of ACIVY with a relatively small gap between the best (2502.12372) and worst (2502.8327) performance values, shows the robustness of its algorithm in dynamic path planning tasks.
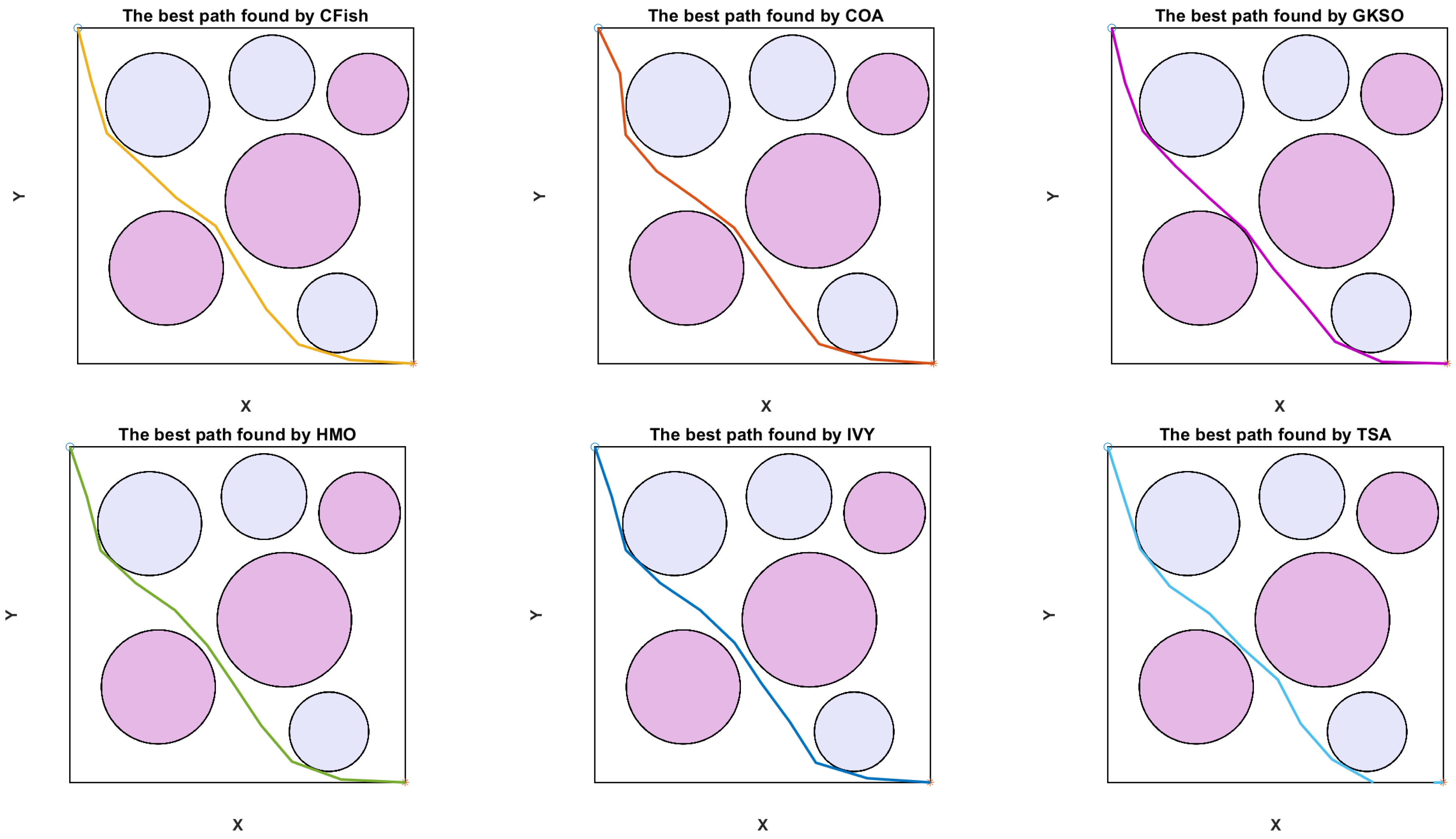
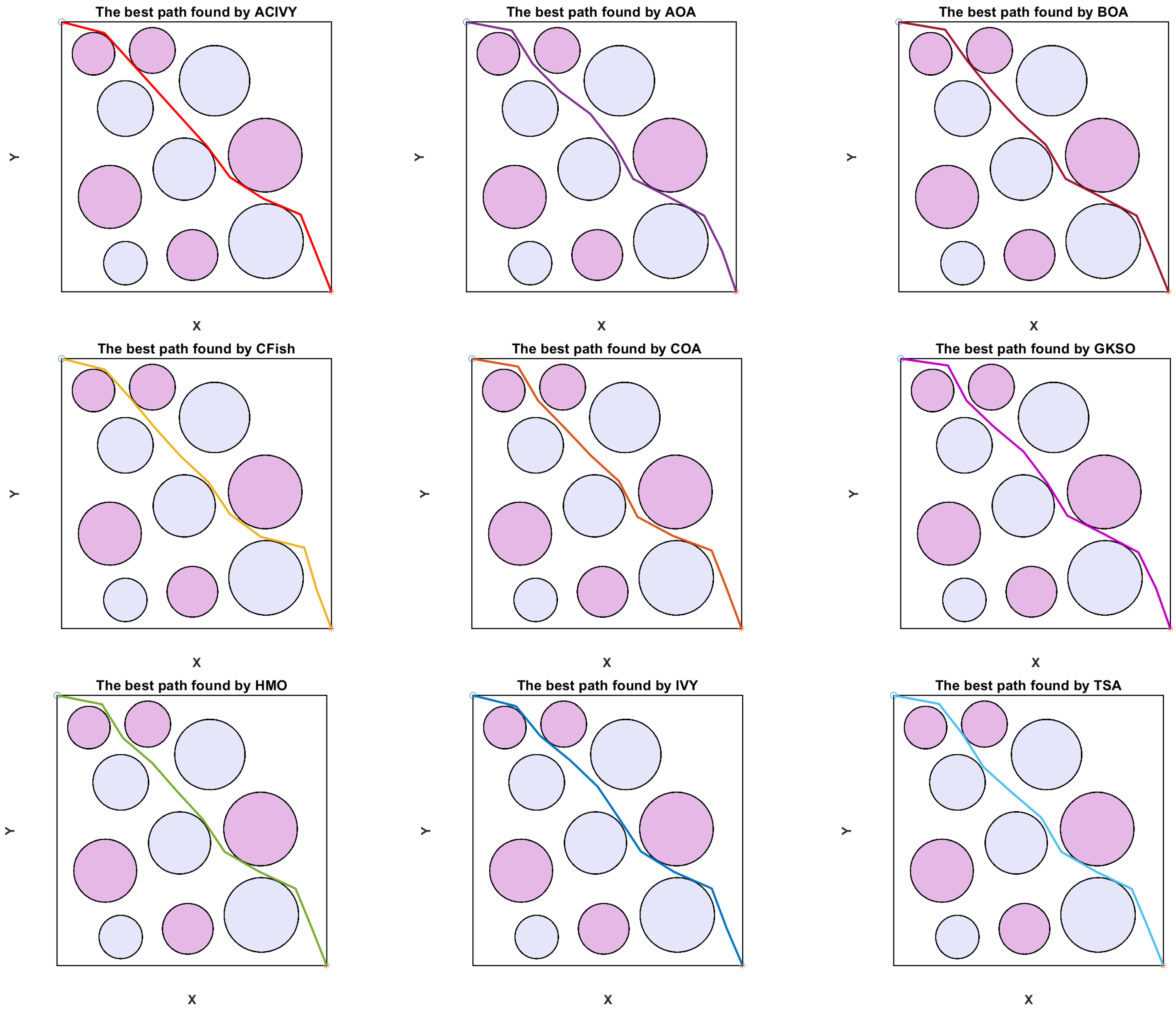
The visual optimal paths computed by each algorithm in Case 1, presented in
Figure 9, show the different high-level strategies of threat avoidance and trajectory optimization. The trajectory of ACIVY shows better spatial intelligence, as it follows the best balance between directness and safety, performing smooth curved movements to optimally go around the six circular threat areas while keeping the distance and the threat levels minimal. The trajectory covered by the algorithm has a well-chosen waypoint that results in smooth arcs around the high-risk regions, especially visible in how it avoids the large threat area in the center and the concentration of threats in the upper-right quarter. Conversely, other algorithms, such as TSA and COA, are more conservative and exhibit extreme curvature that leads to higher fuel consumption, whereas BOA and HMO tend to produce angles that are too sharp and could lead to UAV maneuverability limitations.
The comparative analysis shows a wide disparity in the quality and feasibility of paths found by the competing algorithms. The path of ACIVY shows a constant clearance margin to all threat boundaries without sacrificing the smoothness of the flight path, which implies a better constraint handling and multi-objective optimization ability. The algorithm is able to find the optimal corridor along the complex threat landscape without making unnecessary detours, and without entering dangerously close to high-intensity threat areas. Other algorithms, such as CFish and GKSO, exhibit a poor path planning performance, either by going too near the high-risk regions or by making unnecessary long diversions, which leads to an increase in the cost of the mission.
The convergence curve of Case 1, shown in
Figure 10, indicates the outstanding optimization dynamics and the excellent convergence properties of ACIVY within the UAV path planning application field. ACIVY shows the most aggressive and effective early-stage convergence behavior, falling quickly out of an initial cost of about 2900 to near-optimal costs of about 2500 in the first 100 iterations. Such a fast convergence implies that the algorithm has strong exploration abilities and effective search space exploration, which makes it quick to find and exploit good areas of the solution space. The algorithm shows consistent progress in optimization, and in the end, gives the minimum final cost compared to any other competitor. Comparatively, the GKSO and BOA algorithms exhibit slower rates of initial convergence, whereas CFish and TSA exhibit less reliable improvement trends with temporary periodical stagnation.
The convergence stability plot indicates the excellent consistency and stable optimization pattern of ACIVY during the 1000 iterations. Following the fast initial progress, ACIVY continues with a smooth and steady refinement process, which is evidence of well-balanced exploration and exploitation dynamics that avoid premature convergence, at the same time guaranteeing a constantly improving solution. The convergence curve of the algorithm has very few variations with no observable plateaus, indicating strong local optima escape mechanisms and good global search abilities. Such consistent convergence behavior is in stark contrast to other algorithms, such as COA and HMO, that show erratic convergence behavior with many plateau periods and little progress in later iterations. The enviable convergence traits of ACIVY are in direct proportion to its statistical performance indices, thus validating the role played by the increased bio-inspired strategies in the algorithm to convert the high convergence rate into a steady state of optimal solution quality in the testing UAV path planning environments.
Case 2 performance analysis presented in
Table 13 shows that ACIVY remains a clear leader in dealing with more complex threats, with the best fitness value of 2374.11064 and an incredible consistency demonstrated by the standard deviation of just 0.234912478. This constitutes a strong performance improvement over its nearest rival, BOA, which has a best fitness of 2375.47342 and a mean of 2376.87129, showing that ACIVY optimizes better in this harder threat landscape. The performance of the algorithm is further accentuated when compared to algorithms suffering significantly during the higher threat density, especially CFish (mean: 2470.77789 +/− 65.84699354) and TSA (mean: 2451.45497 +/− 32.77127957), which demonstrate extreme performance degradation and high variance in the Case 2 complex scenario.
On the other hand,
Figure 11 shows the visualization of Case 2, which indicates that ACIVY outperformed its spatial reasoning skills in the more challenging threat landscape consisting of eight distributed circular areas with different intensities. The trajectory of ACIVY is characterized by remarkable strategic analysis, showing the best path across the thick threat field, keeping an almost straight line, but carefully bypassing all high-risk sectors. The track of the algorithm illustrates highly advanced waypoint selection to develop a smooth executable path with minimal offset to the straight-line distance, efficiently balancing the two competing goals of threat avoidance and fuel optimization. It is worth noting that the ACIVY route includes going between the central large threats with safe clearance margins, demonstrating the high level of constraint processing in the complex multi-threat case.
The comparison demonstrates that the difference in the quality of paths found by the competing algorithms vastly widens in the presence of greater environmental complexity. TSA shows the most cautious case of over-curvature that significantly adds mission distance and fuel burn, and CFish displays improper planning of an unjustifiably winding track that generates numerous direction alterations. Other algorithms, such as AOA, BOA, and COA, perform moderately well on relatively straight-line paths but do not have the accuracy of the best corridor discovery exhibited by ACIVY.
The convergence pattern in
Figure 12 shows that ACIVY in Case 2 is adjusted remarkably well to higher complexity in the environment, and the optimization dynamics were faster than in Case 1. ACIVY also converges to near-optimal values of around 2380 after only 50 iterations, demonstrating that it explores the more crowded threat environment of Case 2 more efficiently. The algorithm retains its typical smooth convergence profile with no oscillations or early stagnation and ends up with the final minimum cost among all the competitors. This improved convergence rate in Case 2 indicates that the improved strategies in ACIVY are specifically suitable for the complex multi-threat environment where the traditional algorithms fail due to higher computational requirements and the complexity of the solution space.
Finally, the Case 3 performance evaluation at
Table 14 shows a much complex optimization terrain with ten threat zones, but ACIVY stays on the leadership track with the best fitness value of 2433.65864, indicating a high-quality solution even in the complex environment. Nevertheless, Case 3 demonstrates some curious performance patterns according to which the standard deviation (24.2325059) in ACIVY is higher than in the former cases, which might be interpreted as the increased complexity of the given threat constellation. Our nearest rival, COA, shows a competitive average performance of 2444.96932 with very low variance (4.0979329), whereas IVY is consistently ranked second with a best fitness of 2441.37365 and acceptable reliability (16.9353954 standard deviation). The performance of such algorithms as CFish (2478.17905 +/− 6.22824561) and AOA (2478.61011 +/− 9.35102086) is worse than in previous instances, which proves the higher level of optimization challenge provided by the dense threat configuration of Case 3.
Statistical analysis yields the peculiar challenge profile of Case 3, in which the ten-threat setting provides a more intricate optimization terrain and challenges the robustness and adaptiveness of the algorithms. Although ACIVY achieves the optimal individual solution, the higher variance implies that this specific threat configuration contains local optima issues, which sometimes impact the consistency of convergence. In this case, COA shows an excellent stability with the least standard deviation compared to other algorithms, which means that it is able to handle constraints well, even though it finds suboptimal solutions. The difference between the best (2433.65864) and mean (2444.2745) performance of ACIVY demonstrates that though the algorithm can find optimal corridors in the maze of threatening agents, convergence to the global optimum becomes more difficult in this crowded environment, which shows the implied complexity of ten-threat navigation scenarios with regards to UAV path planning problems.
Figure 13 presents the path routes for various algorithms in Case 3, which indicates the tremendous complexity caused by the ten-threat array, with ACIVY displaying highly advanced spatial navigation through the densest threat array in the experiment. The path of ACIVY demonstrates a high-level optimization of waypoints, as it found a viable corridor that demands careful maneuvering around several tightly spaced threats, especially in its lower part, where the algorithm has to thread the needle between the close group of four threats, still keeping safe clearance distances. The route exhibits a degree of tactical flexibility in that the curvature is controlled and varies dynamically according to the threat proximity, giving a smooth but dynamic route that balances the needs of directness with the safety constraints. Such an advanced navigation feature is the main difference between ACIVY and its competitors, TSA and IVY, which are characterized by less aggressive styles but with too many deviations that prolong the mission time and fuel usage.
Moreover, to address the challenge of real-world applicability and demonstrate the robustness of ACIVY in handling complex geometric configurations beyond simple circular obstacles, an additional experimental scenario was designed involving 3D path planning through an oil plant industrial environment [
89,
90]. This complex scenario represents a significant advancement from the previous circular threat zone experiments, incorporating realistic industrial structures, including pipelines, storage tanks, processing units, and multi-level platforms that UAVs commonly encounter in industrial inspection and monitoring missions. The oil plant environment presents a particularly challenging navigation landscape due to its intricate 3D geometry, varying obstacle heights, narrow corridors between equipment, and the critical safety requirements inherent in petrochemical facilities where collision avoidance is paramount.
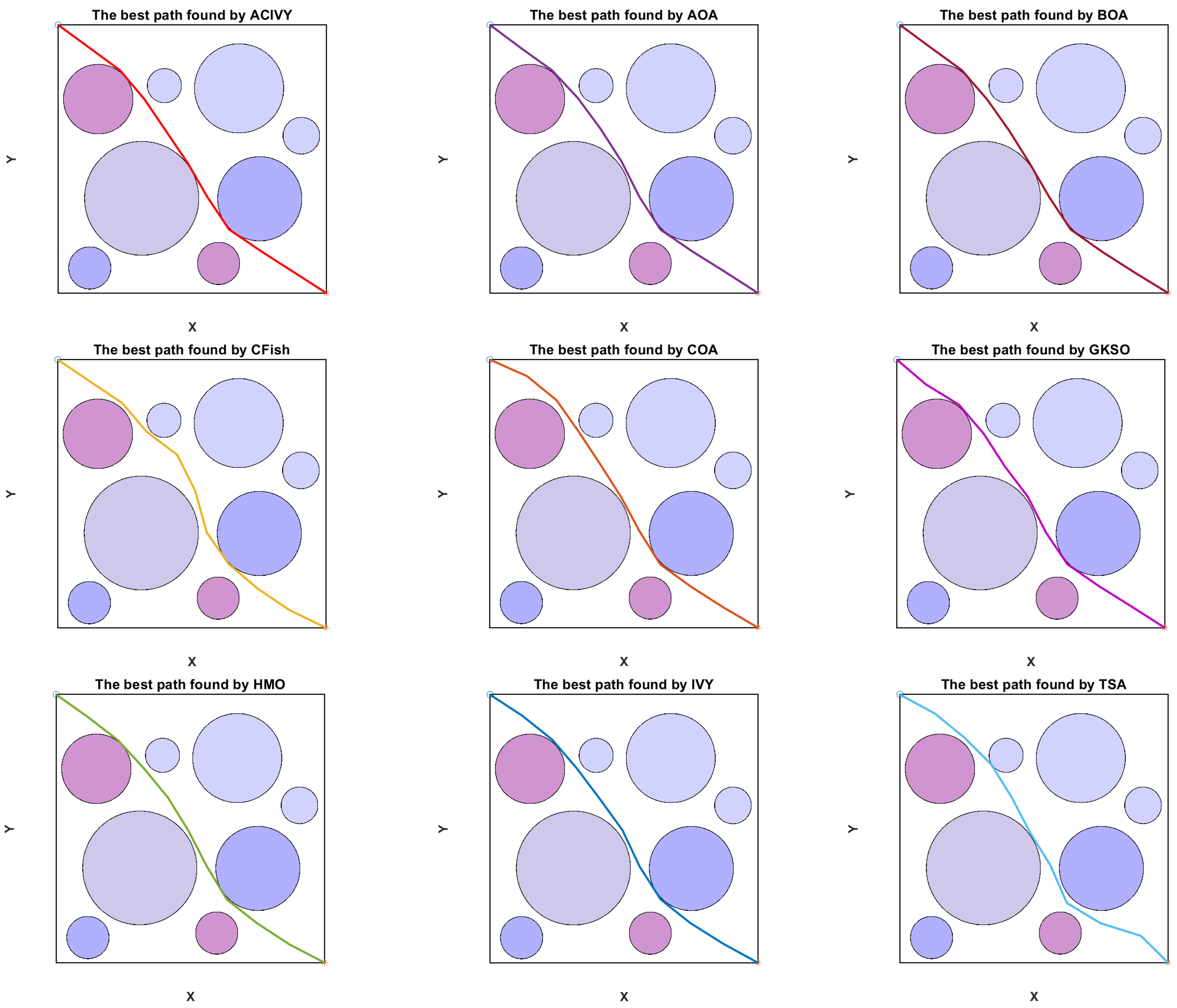
The statistical performance analysis presented in
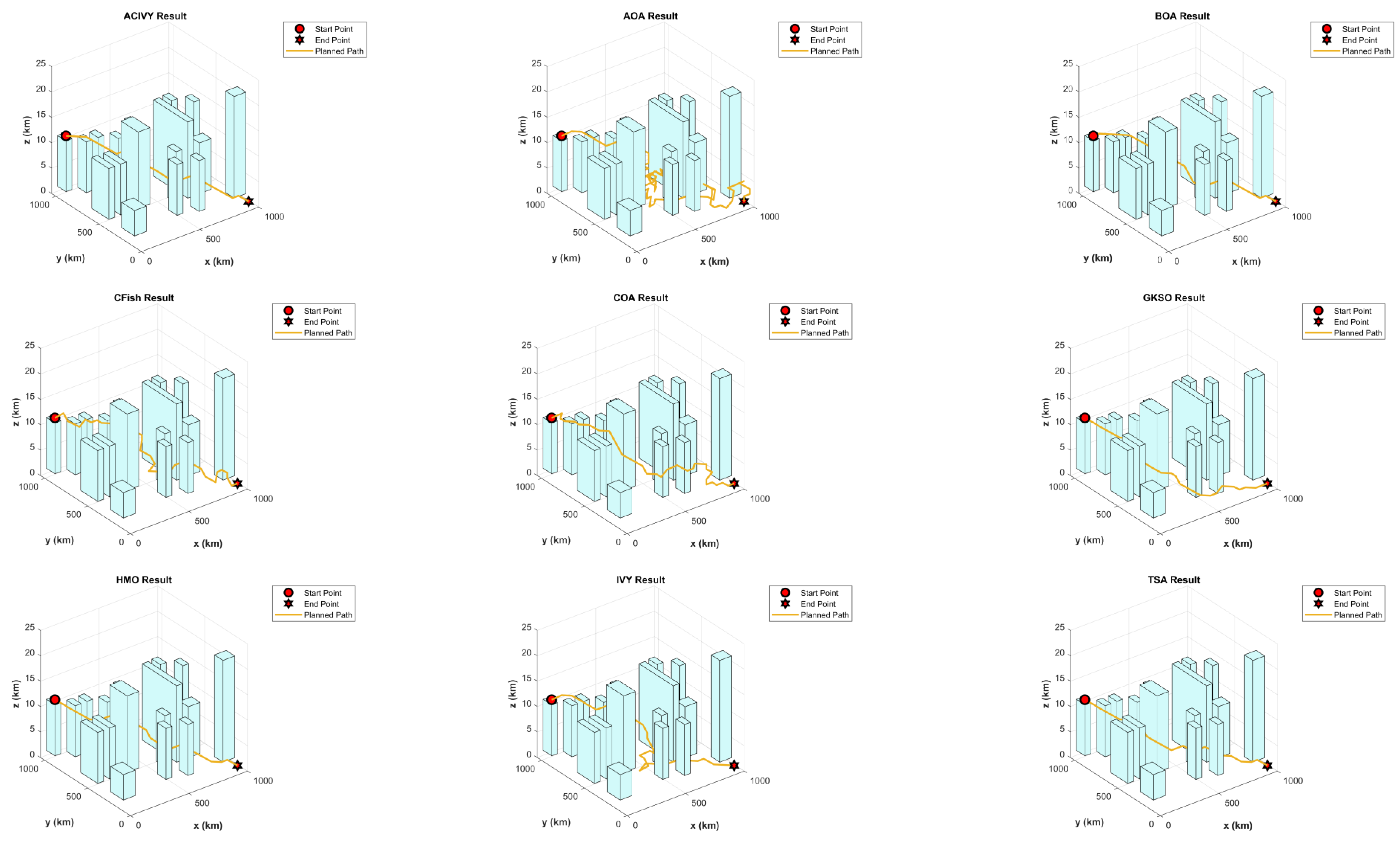
Table 15 demonstrates ACIVY’s exceptional capability in navigating this complex 3D industrial environment, achieving the best fitness value of 31.97736 with a remarkably low standard deviation of 0.11129, indicating superior consistency and reliability across multiple optimization runs. ACIVY’s performance is closely matched by BOA, which achieves an identical best fitness of 31.97736 but with higher variance (0.36918), while HMO ranks third with a competitive performance (32.07374 ± 0.25926). The algorithm significantly outperforms other competitors, with IVY showing a substantially degraded performance (44.39475 ± 4.76428) and CFish struggling considerably in this complex environment (46.96253 ± 1.43415). The visual path planning results illustrated in
Figure 14 clearly demonstrate the superior spatial reasoning capabilities of ACIVY, which successfully identifies optimal corridors through the dense industrial infrastructure while maintaining safe clearance margins from all structural components. The trajectory generated by ACIVY exhibits remarkable smoothness and directness, efficiently navigating between multi-level structures and avoiding collision with complex geometric shapes, including cylindrical tanks, rectangular processing units, and interconnected piping systems. In contrast to the smooth, efficient trajectory generated by ACIVY, competing algorithms exhibit various degrees of suboptimal behavior, including unnecessary detours, inefficient altitude changes, and potentially hazardous proximity to industrial equipment. The path visualization reveals that while some algorithms like BOA and HMO produce relatively acceptable routes, others, such as CFish and IVY generate highly irregular trajectories with excessive maneuvering that would be impractical for real UAV operations, thereby validating the enhanced optimization strategies integrated into ACIVY for handling real-world complex geometric constraints in critical industrial applications.
4.4. Results Discussion
The comprehensive experimental validation demonstrates ACIVY’s consistent superiority across diverse optimization domains. ACIVY achieved first-place rankings on both the CEC2022 (average rank 1.25) and CEC2017 (average rank 1.41) benchmark suites, delivered perfect convergence on four engineering design problems, and demonstrated an optimal UAV path planning performance across simple circular threats and complex 3D industrial environments, establishing its broad applicability and reliability.
The experimental results reveal fundamental weaknesses in competing algorithms that explain their poor performance on specific function types. Algorithms like AOA and COA exhibit severe limitations on multimodal and composite functions due to premature convergence and population diversity loss, where their search mechanisms cause early clustering around local optima, effectively reducing global exploration to local refinement. For instance, AOA’s performance on CEC2022 composite functions (F9–F12) shows fitness values worse than ACIVY, while CFish demonstrates trajectory irregularities in UAV path planning due to its temperature-based search strategy that creates oscillatory behavior preventing convergence in constrained environments. TSA suffers from swarm movement trapping in complex hybrid function landscapes, lacking sophisticated escape mechanisms when populations become confined in fitness valleys created by multi-characteristic function combinations.
ACIVY systematically addresses these limitations through its three integrated enhancement strategies, each targeting specific algorithmic weaknesses observed in competitors. The CCS strategy solves the population diversity crisis plaguing algorithms like AOA by introducing structured horizontal and vertical crossover operations that maintain genetic spread while preserving solution quality, enabling successful navigation of multimodal landscapes where competitors prematurely converge. The LT strategy provides the directional guidance deficiency observed in algorithms like TSA and CFish through its memory-based navigation system that combines historical position information with adaptive repulsion from poor regions, explaining ACIVY’s smooth UAV trajectories versus the erratic paths generated by competing methods. The TGAM strategy resolves the exploration–exploitation transition problems evident in traditional algorithms through its dynamic selection pool mechanism, ensuring gradual phase transitions that prevent both premature convergence and excessive exploration, particularly effective on hybrid and composite functions requiring balanced global–local search capabilities.
The experimental results reveal important insights regarding algorithmic scalability and robustness across different problem dimensions and characteristics. ACIVY demonstrates remarkable consistency between CEC2017 (50D) and CEC2022 (20D) performance, maintaining its top ranking across both benchmark suites despite the dimensional differences and varying function complexities. This scalability stems from the dimension-independent nature of the three enhancement strategies, which operate on relative population relationships rather than absolute dimensional coordinates. In contrast, algorithms like CMA-ES and jDE show significant performance degradation on higher-dimensional problems, indicating scalability limitations in their core mathematical frameworks.
The robustness analysis across engineering applications and UAV path planning scenarios reveals ACIVY’s exceptional constraint handling capabilities compared to competing algorithms. While traditional optimization methods often struggle with feasibility maintenance in constrained problems, ACIVY’s integrated strategies naturally preserve constraint satisfaction through their guided search mechanisms. The LT strategy’s repulsion component inherently avoids infeasible regions, while the CCS strategy’s structured recombination tends to generate feasible offspring from feasible parents. This explains ACIVY’s perfect convergence on highly constrained problems like tension–compression spring design, where competing algorithms exhibit high variance due to constraint violations and subsequent penalty applications.