Transforming Smart Healthcare Systems with AI-Driven Edge Computing for Distributed IoMT Networks
Abstract
1. Introduction
- i.
- How can the proposed system ensure data privacy and integrity with AI-enabled techniques without affecting network resources?
- ii.
- What methods can healthcare applications explore to decrease congestion and provide a responsive system by optimizing resources through efficient communication and network scalability?
- iii.
- What kind of potential threats can be addressed by healthcare applications using an AI model to reduce unauthorized access and vulnerabilities to cyber attacks?
- i.
- Design and implementation of smart healthcare solution using AI-powered security for ensuring privacy of health records while affecting its integrity in a distributed environment.
- ii.
- Edge computing is integrated for real-time processing and increases the scalability of the IoMT network while reducing congestion among health devices, and improves the responsiveness of the system in critical conditions.
- iii.
- AI-based models are explored to ensure network availability and provide a lightweight communication paradigm for coping with network disruptions in the presence of cyber threats affecting healthcare services.
2. Literature Review
3. Materials and Methods
3.1. System Architecture for Distributed IoMT Networks
3.2. AI-Enabled Secure Edge System for Distributed Decision Making
- is the classifier output (normal or anomalous).
- is the feature vector, which includes:
- –
- packet size () and transmission rate ();
- –
- response time () and data flow patterns ();
- –
- and other network characteristics.
- is the weight associated with each feature , and b is the bias term.
| Algorithm 1: Anomaly detection using SVM for IoMT traffic. |
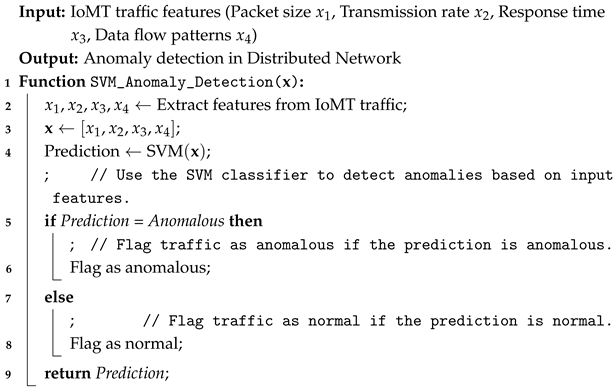 |
3.3. Integrating Edge Computing for Scalable IoMT System
- is the error function measuring the performance of the edge node in processing the data.
- is the predicted output for the input feature , and is the actual value.
| Algorithm 2: Edge computing for task offloading and error minimization. |
 |
- is the time of detection for the i-th attack.
- is the time the i-th attack starts.
- is the time when the system identifies the attack.
- is the time when the attack begins.
- is the time when the system returns to normal operation after mitigation.
- is the time when the attack is first detected.
- is the number of detected attack events.
- is the detection time for the attack.
- is the mitigation time for the attack.
- is the system’s total operational time, including both normal and attack-response phases.
| Algorithm 3: Cyber resilience evaluation for distributed IoMT system. |
 |
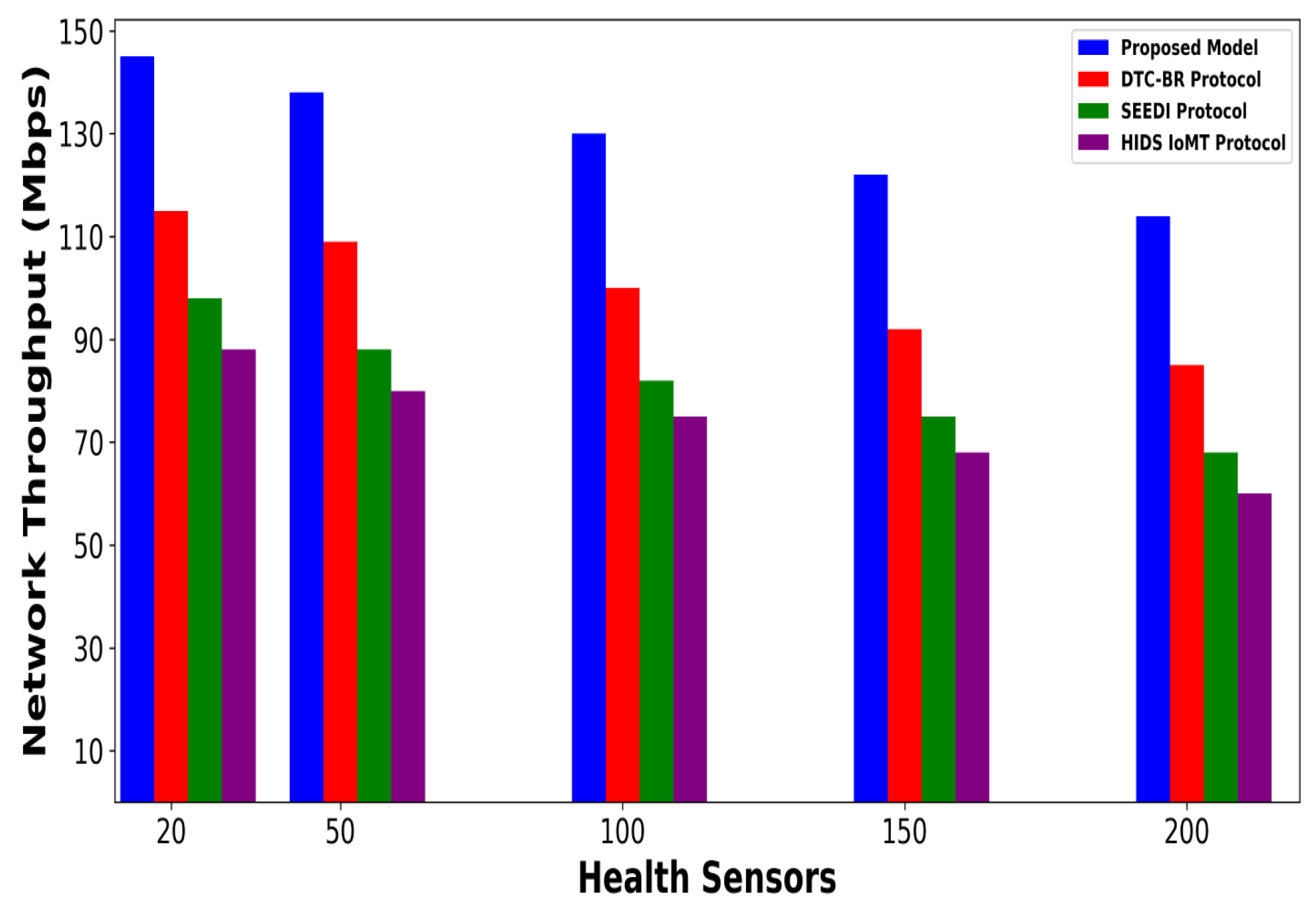
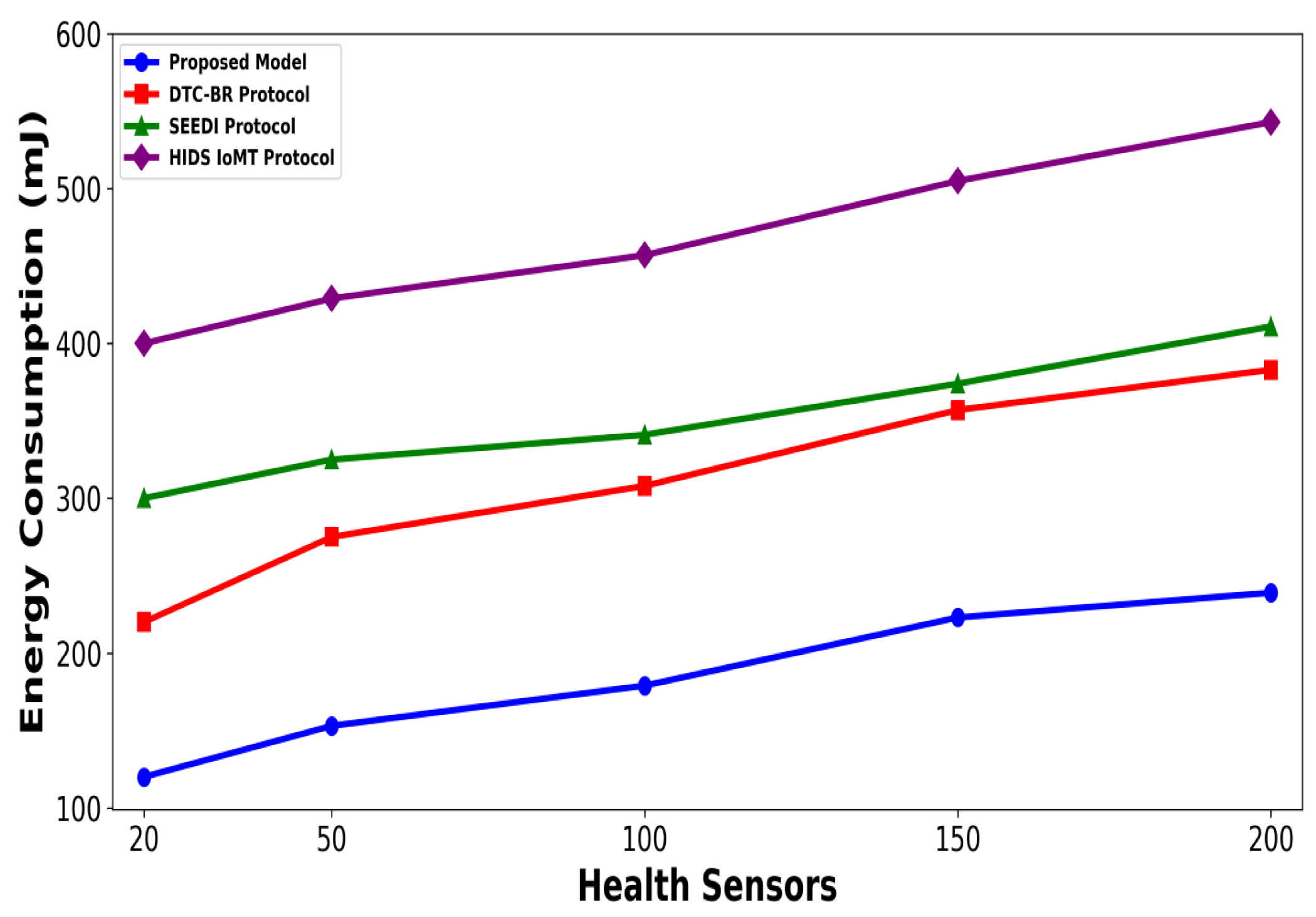
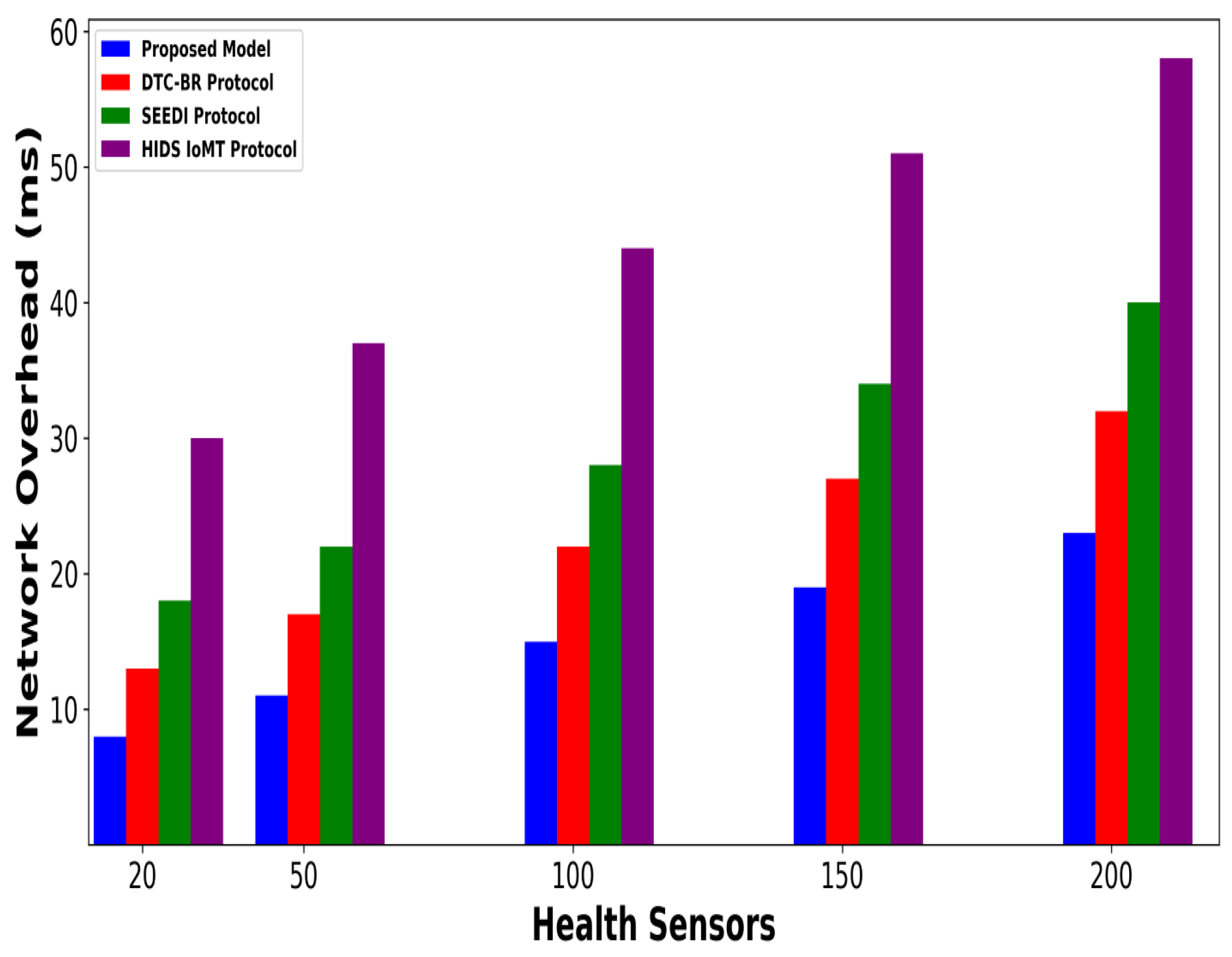
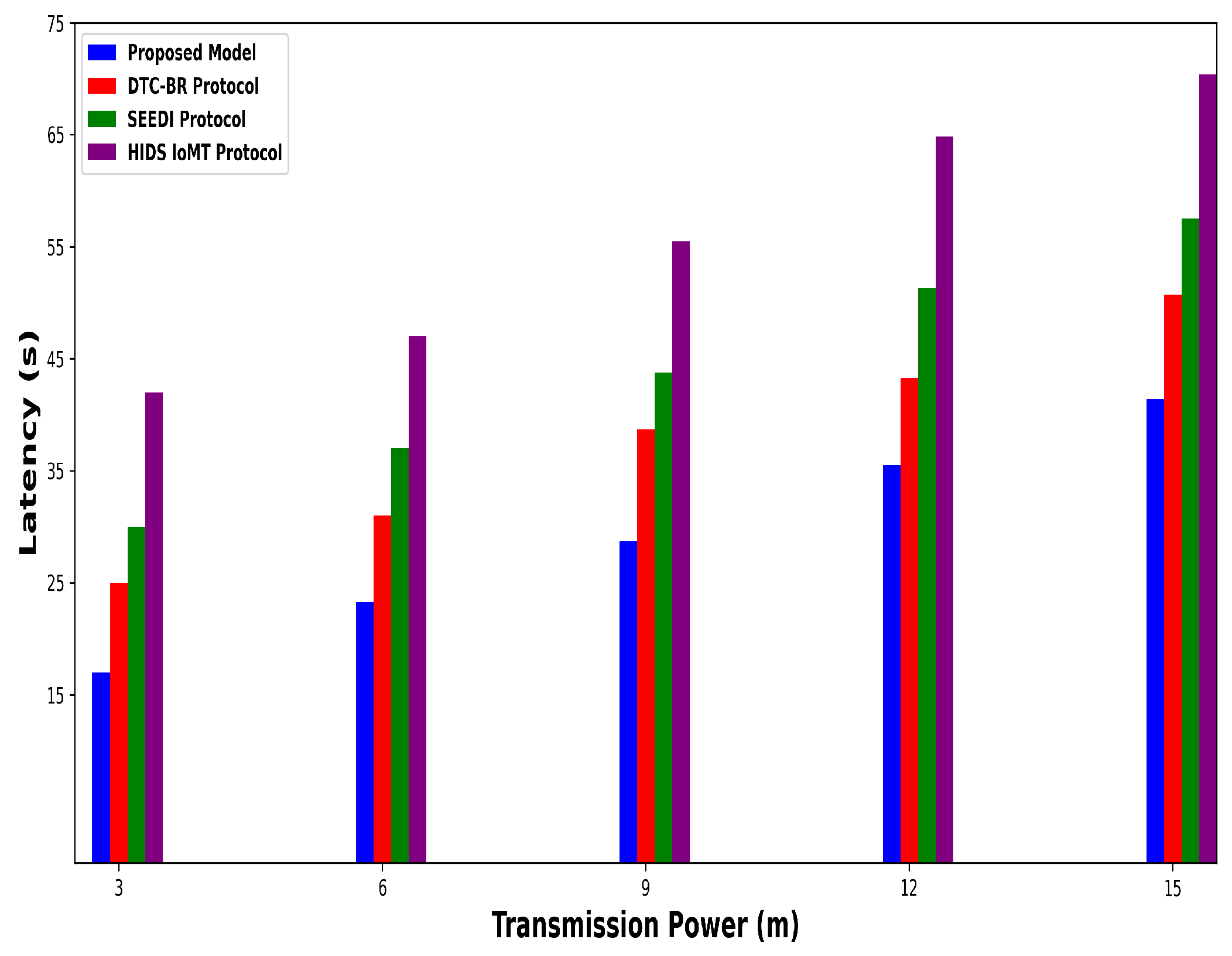
4. Simulation Configuration
Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ficili, I.; Giacobbe, M.; Tricomi, G.; Puliafito, A. From sensors to data intelligence: Leveraging IoT, cloud, and edge com-puting with AI. Sensors 2025, 25, 1763. [Google Scholar] [CrossRef] [PubMed]
- Uddin, R.; Koo, I. Real-time remote patient monitoring: A review of biosensors integrated with multi-hop IoT systems via cloud connectivity. Appl. Sci. 2024, 14, 1876. [Google Scholar] [CrossRef]
- Mathkor, D.M.; Mathkor, N.; Bassfar, Z.; Bantun, F.; Slama, P.; Ahmad, F.; Haque, S. Multirole of the internet of medical things (IoMT) in biomedical systems for managing smart healthcare systems: An overview of current and future innova-tive trends. J. Infect. Public Health 2024, 17, 559–572. [Google Scholar] [CrossRef]
- Bolat-Akça, B.; Bozkaya-Aras, E. Digital twin-assisted intelligent anomaly detection system for Internet of Things. Ad Hoc Netw. 2024, 158, 103484. [Google Scholar] [CrossRef]
- Chen, Z.; Sivaparthipan, C.B.; Muthu, B. IoT based smart and intelligent smart city energy optimization. Sustain. Energy Technol. Assess. 2022, 49, 101724. [Google Scholar]
- Sharma, M.; Tomar, A.; Hazra, A. Edge computing for industry 5.0: Fundamental, applications, and research challenges. IEEE Internet Things J. 2024, 11, 19070–19093. [Google Scholar] [CrossRef]
- Varriale, V.; Cammarano, A.; Michelino, F.; Caputo, M. Critical analysis of the impact of artificial intelligence integration with cutting-edge technologies for production systems. J. Intell. Manuf. 2025, 36, 61–93. [Google Scholar] [CrossRef]
- Alamri, M.; Haseeb, K.; Humayun, M.; Alshammeri, M.; Alwakid, G.N.; Ramzan, N. Edge-Driven Disability Detection and Outcome Measurement in IoMT Healthcare for Assistive Technology. Bioengineering 2025, 12, 1013. [Google Scholar] [CrossRef]
- Poyyamozhi, M.; Murugesan, B.; Rajamanickam, N.; Shorfuzzaman, M.; Aboelmagd, Y. IoT—A promising solution to energy management in smart buildings: A systematic review, applications, barriers, and future scope. Buildings 2024, 14, 3446. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.N.; Wang, H.; Xiong, Z.; Guo, S. A survey of intelligent network slicing management for industrial IoT: Integrated approaches for smart transportation, smart energy, and smart factory. IEEE Commun. Surv. Tutor. 2022, 24, 1175–1211. [Google Scholar] [CrossRef]
- Alshammeri, M.; Humayun, M.; Haseeb, K.; Alwakid, G.N. AI-Driven Sentiment-Enhanced Secure IoT Communication Model Using Resilience Behavior Analysis. Comput. Mater. Contin. 2025, 84, 433. [Google Scholar] [CrossRef]
- Al-Jumaili, A.H.A.; Muniyandi, R.C.; Hasan, M.K.; Paw, J.K.S.; Singh, M.J. Big data analytics using cloud computing based frameworks for power management systems: Status, constraints, and future recommendations. Sensors 2023, 23, 2952. [Google Scholar] [CrossRef]
- Cai, H.; Xu, B.; Jiang, L.; Vasilakos, A.V. IoT-based big data storage systems in cloud computing: Perspectives and chal-lenges. IEEE Internet Things J. 2016, 4, 75–87. [Google Scholar] [CrossRef]
- Hashem, I.A.T.; Yaqoob, I.; Anuar, N.B.; Mokhtar, S.; Gani, A.; Khan, S.U. The rise of “big data” on cloud computing: Re-view and open research issues. Inf. Syst. 2015, 47, 98–115. [Google Scholar] [CrossRef]
- Virmani, N.; Singh, R.K.; Agarwal, V.; Aktas, E. Artificial intelligence applications for responsive healthcare supply chains: A decision-making framework. IEEE Trans. Eng. Manag. 2024, 71, 8591–8605. [Google Scholar] [CrossRef]
- Gala, D.; Behl, H.; Shah, M.; Makaryus, A.N. The role of artificial intelligence in improving patient outcomes and future of healthcare delivery in cardiology: A narrative review of the literature. Healthcare 2024, 12, 481. [Google Scholar] [CrossRef]
- Mahmmod, B.M.; Naser, M.A.; Al-Sudani, A.H.S.; Alsabah, M.; Mohammed, H.J.; Alaskar, H.; Almarshad, F.; Hussain, A.; Abdulhussain, S.H. Patient monitoring system based on internet of things: A review and related challenges with open research issues. IEEE Access 2024, 12, 132444–132479. [Google Scholar] [CrossRef]
- Olawade, D.B.; David-Olawade, A.C.; Wada, O.Z.; Asaolu, A.J.; Adereni, T.; Ling, J. Artificial intelligence in healthcare delivery: Prospects and pitfalls. J. Med. Surg. Public Health 2024, 3, 100108. [Google Scholar] [CrossRef]
- Boisrond, K.; Tardif, P.M.; Jaafar, F. Ensuring the integrity, confidentiality, and availability of IoT data in Industry 5.0: A Systematic Mapping Study. IEEE Access 2024, 12, 107017–107045. [Google Scholar] [CrossRef]
- Khan, A.Y.; Latif, R.; Latif, S.; Tahir, S.; Batool, G.; Saba, T. Malicious insider attack detection in IoTs using data analytics. IEEE Access 2019, 8, 11743–11753. [Google Scholar] [CrossRef]
- Alketbi, K.S.; Mehmood, A. A Comprehensive Survey of Explainable Artificial Intelligence Techniques for Malicious In-sider Threat Detection. IEEE Access 2025, 13, 121772–121798. [Google Scholar] [CrossRef]
- Shafiq, M.; Choi, J.G.; Cheikhrouhou, O.; Hamam, H. Advances in IoMT for healthcare systems. Sensors 2023, 24, 10. [Google Scholar] [CrossRef]
- Pradyumna, G.R.; Hegde, R.B.; Bommegowda, K.B.; Jan, T.; Naik, G.R. Empowering healthcare with IoMT: Evolution, machine learning integration, security, and interoperability challenges. IEEE Access 2024, 12, 20603–20623. [Google Scholar] [CrossRef]
- Ibrahim, M.; Al-Wadi, A.; Elhafiz, R. Security analysis for smart healthcare systems. Sensors 2024, 24, 3375. [Google Scholar] [CrossRef] [PubMed]
- Awotunde, J.B.; Imoize, A.L.; Jimoh, R.G.; Adeniyi, E.A.; Abdulraheem, M.; Oladipo, I.D.; Falola, P.B. AIoMT enabling real-time monitoring of healthcare systems: Security and privacy considerations. In Handbook of Security and Privacy of AI-Enabled Healthcare Systems and Internet of Medical Things; CRC Press: Boca Raton, FL, USA, 2023; pp. 97–133. [Google Scholar]
- Rajavel, R.; Ravichandran, S.K.; Harimoorthy, K.; Nagappan, P.; Gobichettipalayam, K.R. IoT-based smart healthcare video surveillance system using edge computing. J. Ambient Intell. Humaniz. Comput. 2022, 13, 3195–3207. [Google Scholar] [CrossRef]
- Alshuhail, A.; Alshahrani, A.; Mahgoub, H.; Ghaleb, M.; Darem, A.A.; Aljehane, N.O.; Alotaibi, M.; Alzahrani, F. Ma-chine edge-aware IoT framework for real-time health monitoring: Sensor fusion and AI-driven emergency response in decentralized networks. Alex. Eng. J. 2025, 129, 1349–1361. [Google Scholar] [CrossRef]
- Al-Sadoon, M.E.; Jedidi, A.; Al-Raweshidy, H. Dual-tier cluster-based routing in mobile wireless sensor network for IoT application. IEEE Access 2023, 11, 4079–4094. [Google Scholar] [CrossRef]
- Arpitha, T.; Chouhan, D.; Shreyas, J. A hybrid optimization approach to enhance source location privacy for iot healthcare. IEEE Access 2024, 12, 132801–132816. [Google Scholar] [CrossRef]
- Karunkuzhali, D.; Meenakshi, B.; Lingam, K. A QoS-aware routing approach for Internet of Things-enabled wireless sensor networks in smart cities. Multimed. Tools Appl. 2025, 84, 17951–17977. [Google Scholar] [CrossRef]
- Sharma, S.; Mishra, V.M.; Tripathi, M.M.; Verma, S.; Kaur, S. SEEDI: Sink-Mobility-Based Energy-Efficient Data Dissemi-nation in the Internet of Medical Things. IEEE Sens. J. 2024, 24, 35367–35373. [Google Scholar] [CrossRef]
- Berguiga, A.; Harchay, A.; Massaoudi, A. HIDS-IoMT: A deep Learning-Based intelligent intrusion detection system for the internet of medical things. IEEE Access 2025, 13, 32863–32882. [Google Scholar] [CrossRef]
- Gupta, S.; Chithaluru, P.; Stephan, T.; Nafisa, S.; Kumar, S. HSPBCI: A robust framework for secure healthcare data management in blockchain-based IoT systems. Multimed. Tools Appl. 2025, 84, 27695–27719. [Google Scholar] [CrossRef]






| Existing Approaches | Contributions | Limitations |
|---|---|---|
| DTC-BR Protocol [28] | Enhances MWSN performance using dual-tier clustering and virtual network zones. The protocol divides the network into two zones: the main connectivity zone (MCZ) and the candidate cluster zone (CCZ), thereby improving energy efficiency and scalability. | May not be effective in highly dynamic environments with frequent topology changes. |
| FFAO [29] | Integrates multi-objective optimization criteria to strengthen the network stability and reliability. It improved the routing process while selecting the optimal path for transmitting IoT data. | May face additional challenges such as overheads, and network delay in coping with resource optimization. |
| QoS-aware Routing Strategy [30] | Proposes a software architecture for data collection and communication in IoT-enabled smart applications, utilizing Chaotic Bird Swarm Optimization (CBSO) for cluster formation and Improved Differential Search (IDS) to assess node reliability. | High computational complexity during the data collection phase may result in increased overhead for real-time applications. |
| SEEDI Protocol [31] | Presents a sink-mobility-based energy-efficient data dissemination protocol for IoMT, designed to address the hot-spot problem in static WBANs. It deploys energy-powered nodes at the periphery to collect patient data and uses the Remora Optimization Algorithm (ROA) to select cluster heads. | Faces challenges in highly dynamic environments with fluctuating traffic patterns, which may hinder real-time data transmission. |
| HIDS-IoMT Protocol [32] | Introduces a hybrid deep learning-based intrusion detection system (HIDS-IoMT) combining CNN for feature extraction and LSTM for sequence prediction, implemented on a Raspberry Pi with fog computing for decentralized processing. | High computational demands of deep learning models may result in slow performance on resource-constrained devices in real-time deployments. |
| HSPBCI framework [33] | Improves the security level for healthcare system with blockchain network and effective key management for authorized data access. | Limited in network scalability and enhanced data latency while processing high amount of health records. |
| Parameter | Value/Description |
|---|---|
| Simulation area | |
| Simulation duration | 3000 s |
| Number of executions | 50 independent runs |
| Round interval | 25 s |
| Sensor nodes | 20, 50, 100, 150, 200 |
| Edge nodes | 15 |
| Sink nodes | 3 |
| Malicious nodes | 5–15 |
| Mobility model | Random waypoint |
| Packet size | 128–1024 bytes |
| Transmission power | 3–15 m |
| Initial energy | 5000 mJ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almufareh, M.F.; Humayun, M.; Haseeb, K. Transforming Smart Healthcare Systems with AI-Driven Edge Computing for Distributed IoMT Networks. Bioengineering 2025, 12, 1232. https://doi.org/10.3390/bioengineering12111232
Almufareh MF, Humayun M, Haseeb K. Transforming Smart Healthcare Systems with AI-Driven Edge Computing for Distributed IoMT Networks. Bioengineering. 2025; 12(11):1232. https://doi.org/10.3390/bioengineering12111232
Chicago/Turabian StyleAlmufareh, Maram Fahaad, Mamoona Humayun, and Khalid Haseeb. 2025. "Transforming Smart Healthcare Systems with AI-Driven Edge Computing for Distributed IoMT Networks" Bioengineering 12, no. 11: 1232. https://doi.org/10.3390/bioengineering12111232
APA StyleAlmufareh, M. F., Humayun, M., & Haseeb, K. (2025). Transforming Smart Healthcare Systems with AI-Driven Edge Computing for Distributed IoMT Networks. Bioengineering, 12(11), 1232. https://doi.org/10.3390/bioengineering12111232







