Abstract
In increasingly competitive digital markets, software firms must strategically balance cybersecurity investments and pricing decisions to attract consumers while safeguarding their platforms. This study develops a game-theoretic model in which two competing firms choose among three cybersecurity strategies—no action, bug bounty programs, and in-house protection—before setting prices. We demonstrate that cybersecurity efforts and pricing are interdependent: investment choices significantly alter market outcomes by influencing consumer trust and competitive dynamics. Our analysis reveals that a bug bounty program is preferable when consumer sensitivity to security and the probability of ethical vulnerability disclosures are high, while in-house protection becomes optimal when firms must rebuild credibility from a weaker competitive position. Furthermore, initial service quality gaps between firms critically shape both investment intensity and pricing behavior. By jointly endogenizing security efforts and prices, this study offers new insights into strategic cybersecurity management and provides practical guidance for software firms seeking to integrate security initiatives with competitive pricing strategies.
1. Introduction
In today’s digital world, software service providers face constant pressure to deliver both secure and affordable platforms. As cyber threats become more frequent and sophisticated, software firms need to think carefully about how much to invest in security and how to balance that with competitive pricing. Making the right choices here is tricky—spending too much on security can hurt profits, but spending too little can lead to vulnerabilities, data breaches, and loss of consumer trust [1,2]. One solution that is grown in popularity is the Bug Bounty Programs (BBPs). These programs invite ethical hackers and security researchers to report software vulnerabilities in exchange for financial rewards. The basic idea is simple: the more eyes on the code, the more likely it is that flaws will be caught—an idea often summed up by Linus’s Law: “Given enough eyeballs, all bugs are shallow” [3]. BBPs are relatively inexpensive compared to maintaining large internal security teams and allow companies to tap into a global network of expertise [4].
Although bug bounty programs (BBPs) were first introduced in the 1990s, their adoption has expanded significantly in recent years. Major technology firms such as Google and Microsoft have institutionalized these programs as part of their long-term security strategies [5,6]. Other prominent software companies—including Meta, Apple, and Intel—have also launched large-scale BBPs to leverage external expertise. For example, Meta has paid over $16 million in rewards since launching its program in 2011, with individual bounties reaching up to $50,000 for critical vulnerabilities [7]. Apple offers payouts as high as $1 million for zero-click kernel code execution exploits discovered in iOS [8], while Intel’s program has led to more than 200 publicly disclosed vulnerabilities addressed through coordinated disclosure [9]. These examples underscore the scale and financial commitment leading firms are making to crowd-sourced vulnerability discovery. In addition, public-sector organizations have recognized their value; for instance, the U.S. Department of Defense launched the “Hack the Pentagon” initiative to engage ethical hackers in identifying system vulnerabilities, demonstrating how BBPs can be applied to enhance national cybersecurity readiness [10]. Empirical studies have shown that BBPs are not only effective but also economical. For instance, running a typical BBP costs around $85,000 a year, which is often far less than hiring full-time security staff [11]. They also help build a stronger relationship between companies and the cybersecurity community, promoting transparency and trust [12]. While existing research has explored BBPs, most studies examine them in isolation or emphasize technical implementation. However, the strategic implications of BBPs—particularly their influence on firms’ pricing behavior and security investments in competitive markets—remain underexplored. Little attention has been given to how BBPs compare to traditional approaches such as in-house protection when firms compete for market share. Furthermore, prior models often assume that firms operate independently, neglecting the interdependencies introduced by market competition and consumer trust [13,14].
To fill this gap, our study builds a game-theoretic model that looks at how two competing software firms choose between three cybersecurity strategies: (i) No-action (Strategy N): Firms take no additional security measures and only compete on pricing; (ii) Bug bounty program (Strategy B): Firms invest in external security incentives by allocating a bug bounty budget and setting prices accordingly; and (iii) In-house protection (Strategy I): Firms rely on internal security teams, investing directly in security effort prior to pricing. Table 1 illustrates additional real-world examples of how software firms respond to cybersecurity threats using diverse strategic approaches. Following the selection of a cybersecurity strategy, each firm determines its pricing, taking into account consumers’ sensitivity to both security and cost. The model captures firms’ strategic behavior under varying cost structures, market asymmetries, and degrees of consumer trust, offering insights into the complex interplay between cybersecurity investment and price competition. This analytical framework enables us to explore several pressing questions in the context of cybersecurity-driven market competition. Specifically, we aim to answer: (i) When is a BBP the better choice over traditional protection? (ii) How do these choices affect pricing strategies and market outcomes? (iii) Can a firm actually benefit from doing nothing if its competitor over-invests? (iv) What factors—like vulnerability discovery rates or reward levels—tip the balance?

Table 1.
Practical examples of managing piracy strategy of digital firms.
Our analysis yields several novel findings to the extant literature. First, we show that cybersecurity investments and pricing strategies must be jointly determined rather than treated separately, as cybersecurity actions significantly alter competitive market outcomes. Second, we reveal that the superiority of a bug bounty program versus in-house protection depends critically on consumer trust sensitivity and vulnerability disclosure dynamics, offering new insights into the strategic use of external security initiatives. Third, we identify how market asymmetries, such as initial service quality gaps between firms, influence not only pricing but also the preferred mode of cybersecurity investment. The study contributions are threefold: (i) We bring BBPs and in-house protection into the same model and show how they interact with pricing in a competitive market. (ii) By analyzing all three strategies, we highlight when each is optimal and how external incentives can outperform traditional investments. (iii) The results provide practical guidance for software firms designing BBPs—what to spend, when to spend it, and how to use pricing as part of the strategy.
The remainder of this paper is structured as follows: Section 2 reviews relevant literature on software pricing strategies, cybersecurity investments, and bug bounty programs. Section 3 presents the theoretical framework and game-theoretic model. Section 4 discusses equilibrium outcomes and their implications. Section 5 provides numerical simulations and sensitivity analyses. Finally, Section 6 concludes with key findings, limitations, and directions for future research. By delving into the strategic considerations of BBPs within competitive markets, this study aims to enhance understanding of how external security incentives can be effectively leveraged to achieve a balance between robust cybersecurity and market competitiveness.
2. Literature Review
Our work is situated within three major areas of existing literature. First, we contribute to research on software pricing strategy by examining how competitive pricing behaviors are shaped when cybersecurity investments are incorporated into firms’ strategic decisions. Second, we add to the cybersecurity management literature by showing how firms’ security efforts—whether through in-house protection or external bug bounty programs—interact with pricing and competitive positioning. Finally, we extend the emerging body of work on bug bounty programs by integrating vulnerability disclosure incentives directly into firms’ strategic competition models, offering a new perspective on how cybersecurity initiatives affect both consumer trust and market outcomes.
2.1. Software Pricing Strategy
Pricing strategies have been widely studied in software markets, particularly in contexts involving technological differentiation, licensing models, and platform competition. Feng et al. [20] analyzed the optimal market entry strategies of competing software-as-a-service (SaaS) vendors based on quality development decisions. Their study found that when the initial quality gap between products is significant, the new entrant benefits most from a low-quality, low-price strategy. Guo and Ma [21] examined the pricing strategies of a perpetual software vendor competing with a SaaS provider. They found that when SaaS improves rapidly, existing users remain with perpetual software due to high switching costs. The incumbent initially sets low prices to deter SaaS entry but later shifts to market segmentation, where both firms adopt high pricing strategies. Zhang [22] explored the competition between incumbent and entrant SaaS firms, focusing on existing and new consumers. The study found that when the entrant’s application has low quality, the incumbent retains all existing users. Additionally, Zhang et al. [23] investigated the first-mover advantage, highlighting its role in creating a lock-in effect. This advantage decreases consumer competition in the later stage, allowing the competitor to increase prices for retained customers. Sun et al. [24] modeled how enterprise software firms choose between on-premise, SaaS, or dual-version release strategies when competing with cloud providers. They found that cloud rental costs and value differentiation directly influence firms’ optimal pricing—with on-premise products priced higher when cloud services are costly. In contrast, when cloud rental is cheap, firms reduce prices and may offer both versions to segment the market effectively. Tang et al. [25] studied how two competing software platforms choose between envelopment (building their own hardware) and connection (partnering with hardware firms) as expansion strategies. They found that mutual envelopment leads to higher hardware quality and demand, but also results in lower software prices due to intensified competition. Although envelopment yields better product outcomes, mutual connection can be more profitable from a system-wide pricing and coordination perspective. While existing research has provided valuable insights into software pricing strategies under various competitive and technological conditions, most studies treat cybersecurity concerns as exogenous to pricing decisions. In contrast, our study integrates cybersecurity investment directly into the pricing framework, allowing firms to jointly determine price and security effort in a competitive environment. This approach captures the strategic role of trust-building through protection mechanisms and how such actions affect both demand and the firm’s exposure to cyber risks. By endogenizing cyber risk management alongside pricing, our model provides a more holistic view of strategic decision-making in software markets—an area that remains underexplored in the current literature.
2.2. Cybersecurity Management
The second stream of literature focuses on cybersecurity management in software and digital service firms, particularly how organizations design, invest in, and implement strategies to mitigate cyber threats. Fielder et al. [13] explored optimal cybersecurity investment strategies by comparing game-theoretic, combinatorial optimization, and hybrid approaches. Their framework modeled interactions between defenders and attackers as a two-player control game and integrated a knapsack-based optimization tool. The hybrid approach effectively balanced cost and security outcomes, and the resulting decision support tool aligned with UK government recommendations for SME cybersecurity. Lee et al. [26] analyzed how mandatory cybersecurity standards influence firms’ investment behavior. Their findings suggested that compliance-driven strategies may lead firms to underinvest in actual security if their primary motivation is to avoid liability rather than reduce vulnerability, highlighting the misalignment between regulatory compliance and effective risk mitigation. Focusing on outsourcing, Feng et al. [27] examined firms’ decisions to engage managed security service providers (MSSPs), taking into account the risks of information leakage. Their results showed that partial outsourcing becomes preferable under high leakage risk, whereas in-house protection is optimal when attack risks are low. Additionally, in competitive markets, peer firms tend to adopt similar security strategies, suggesting strategic conformity. Li et al. [28] provided empirical evidence on how IT strategies—specifically digitalization and IT outsourcing—interact with security investments to influence breach incidence. They found that security investments are more effective for less digitalized firms, while in highly digitalized firms, these investments may inadvertently increase breach risks. Moreover, technical controls were shown to reduce external breaches, whereas identity management systems decreased internal breaches but could increase external exposure. Addressing agency concerns in outsourcing, Wu et al. [29] investigated the double moral hazard problem in MSSP contracts, where both parties exert hidden effort. Their study showed that monitoring contracts are only effective when monitoring costs are low, while liability-based contracts outperform under high attack risks, high system interdependence, long contract durations, or shared responsibility for security outcomes. Lastly, Aljaradat et al. [30] used a game-theoretic model to study how cybersecurity threats influence digital payment adoption. They demonstrated that rising cyber threats discourage user adoption, underscoring the need for firms to maintain strong security to sustain user trust and market growth in digital financial services. In contrast, our study develops a strategic competition model in which firms simultaneously determine cybersecurity investment and pricing strategies, accounting for both expected cyberattack losses and consumer trust-driven demand. By situating the analysis in a duopolistic market, our model reveals how security efforts are shaped not only by internal cost structures and breach risks, but also by competitive dynamics and demand sensitivity—factors that are largely absent in existing cybersecurity management literature.
2.3. Bug Bounty Programs
The final stream of literature relevant to our work centers on bug bounty programs (BBPs)—market-based mechanisms that incentivize ethical hackers to identify and disclose software vulnerabilities. Zhao et al. [12] developed economic models to evaluate policy design for bug bounty platforms. They found that validation rewards can improve report quality and that better researcher-task allocation reduces duplication. The study also emphasizes the importance of clear regulations to support ethical hacking and responsible disclosure. Maillart et al. [31] empirically examined the strategic interactions among bug bounty managers, researchers, and platforms, focusing on engagement incentives and bug discovery patterns. They found that each researcher can discover only a limited number of bugs, validating the theory that diverse skills enhance security. Bug bounty programs benefit from large researcher participation, but new programs draw engagement away from older ones. Building on this perspective, Subramanian and Malladi [32] developed a theory of bug bounty programs (BBPs) using incentive compatibility and mechanism design frameworks and empirically analyzes BBPs’ market creation function using data from two BBP types. They discovered that BBPs effectively source software vulnerabilities, but disclosure rates and hacker participation increase only marginally with higher rewards. Akgul et al. [33] conducted interviews with 20 bug bounty hunters to examine their motivations and challenges. They found that while monetary rewards and learning opportunities drive participation, hunters often face unclear scopes, poor communication, and inconsistent reward processes. More recently, Feng et al. [14] examined the optimal timing for launching BBPs under perpetual vs. subscription licensing models. They found that simultaneous launch or no launch is optimal for perpetual licensing, while delayed launch may be best for subscription models if failure costs are low and user trust is valuable. Zhang et al. [34] developed a game-theoretical model to analyze the cost-effectiveness of bug bounty programs (BBPs). Their study revealed that higher researcher productivity or increased legal protections do not always lead to higher bounties or lower total costs. The optimal design of BBPs depends on factors such as organizational patching capabilities, vulnerability complexity, and researcher. While existing literature on bug bounty programs (BBPs) has contributed significantly to understanding their policy design, participant behavior, and operational timing, most prior studies adopt either empirical or theoretical approaches that treat vulnerability discovery and disclosure as exogenous outcomes. Our study integrates bug bounty investment decisions into a duopoly framework where firms compete not only on price but also on perceived security. This approach allows us to endogenize both consumer demand and cyberattack risk, thereby capturing how firms strategically manage user trust and economic losses through BBP design under market competition—an angle largely unaddressed in the existing literature.
In Table 2, we summarize the relevant literature to highlight the contribution of this study. To the best of our knowledge, no analytical models have jointly examined cybersecurity investment decisions and pricing strategies in a competitive software market. Existing research has typically treated cybersecurity efforts as exogenous or focused on isolated aspects such as outsourcing, regulatory compliance, or vulnerability disclosure. In contrast, our study considers three integrated strategic options available to competing software firms: (i) the no-action strategy, (ii) the in-house protection strategy, and (iii) the bug bounty program strategy. By endogenizing both cybersecurity effort levels and pricing decisions, and by capturing how these choices affect consumer demand and competitive dynamics, we provide new insights into the interplay between security management, trust-building, and market outcomes—dimensions that have been largely overlooked in prior research.

Table 2.
A brief summary of the relevant studies.
3. The Model
3.1. Model Setup
In a competitive market, two software firms—a superior firm (Firm 1) and an inferior firm (Firm 2)—offer software services. Each firm sets a price, denoted by , where indicates the firm and represents the cybersecurity strategy. Firms must choose one of three security investment strategies: no action (Strategy N), in-house protection (Strategy I), or a bug bounty program (Strategy B). If a firm selects the bug bounty program, it must determine its bug bounty investment level . Alternatively, if it opts for in-house protection, it must decide on the in-house protection effort . To enhance security, firms allocate effort to the bug bounty program, incurring a cost of , where is the cost coefficient. Similarly, firms investing in in-house protection allocate effort and incur a cost of , where is the corresponding cost coefficient. Note that, to maintain analytical tractability and to reflect the superior firm’s market leadership, we assume a sequential structure in which Firm 1 selects its cybersecurity strategy and price first. Firm 2 then observes Firm 1’s choices before determining its own security investment and pricing decisions. This assumption follows established approaches in sequential competition modeling [22,35].
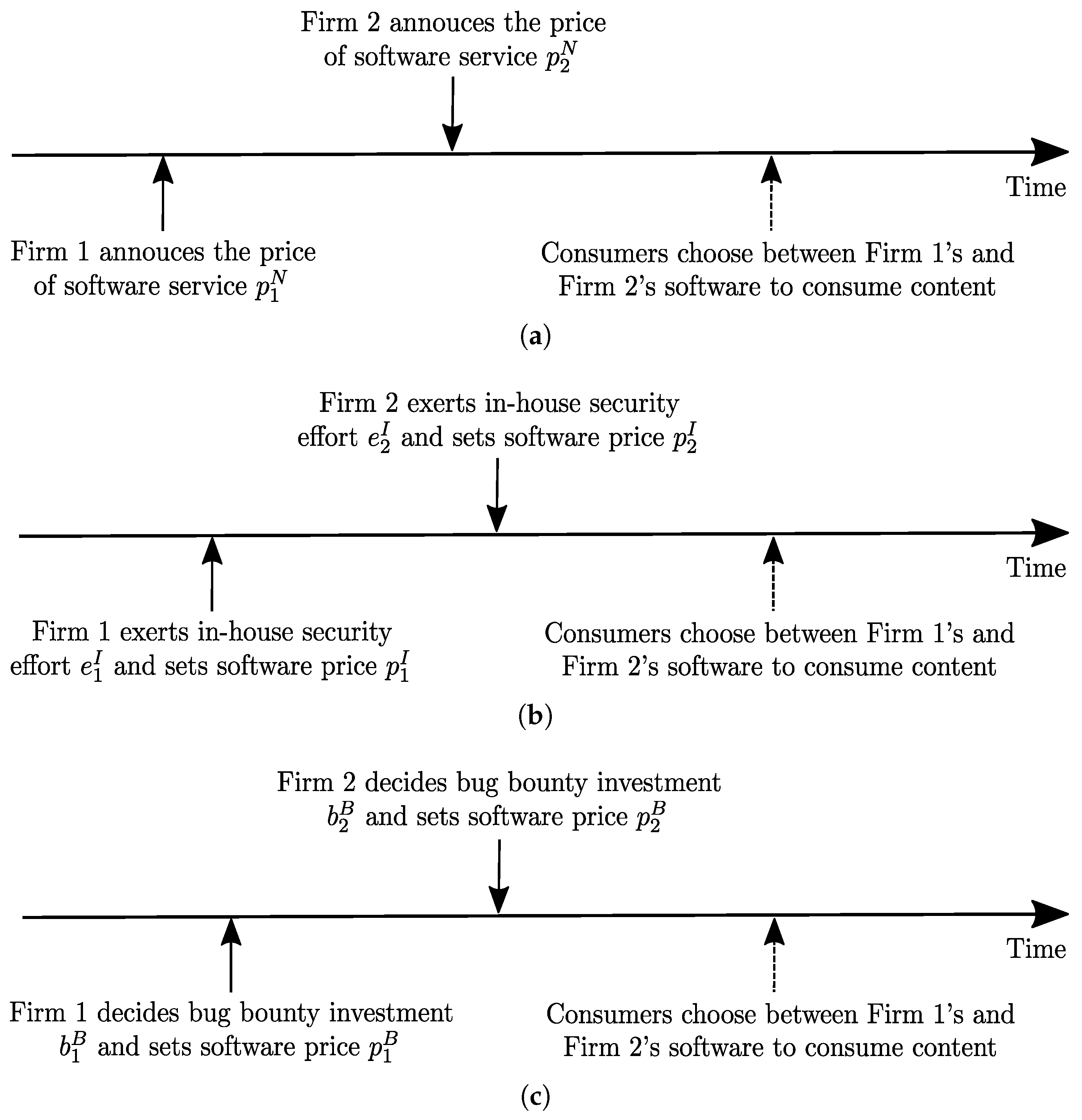
Building on this framework, the sequence of events under the three strategies is illustrated in Figure 1. In Strategy N, the firms engage solely in pricing decisions. Firm 1 first announces its software service price . After observing this, Firm 2 sets its own price . Once both firms have determined their prices, consumers compare the offerings and choose between Firm 1’s and Firm 2’s software services. In Strategy I, the firms incorporate in-house security measures prior to pricing. Firm 1 initiates the process by exerting in-house security effort and setting its price . Firm 2 subsequently decides on its in-house security effort and sets its price . With both security investments and prices established, consumers assess the alternatives and select the software service that best meets their preferences. Lastly, In Strategy B, the firms adopt a bug bounty strategy, emphasizing external security contributions. Firm 1 begins by selecting its bug bounty investment and setting its software price . Firm 2 then follows by choosing its bug bounty investment and setting its price . Consumers then evaluate the available options and make their purchasing decisions. Table 3 summarizes the notation used in this paper.
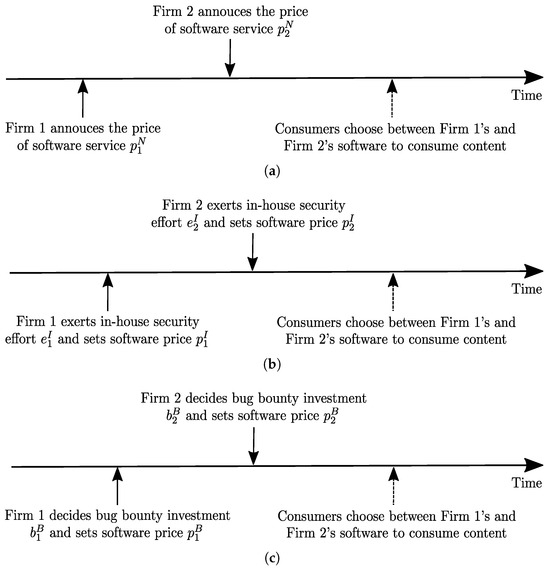
Figure 1.
Sequence of events. (a) No-action strategy (Scenario N). (b) In-house deterrence strategy (Scenario I). (c) Bug bounty strategy (Scenario B).

Table 3.
Notation used in this paper.
3.2. Consumer Choices and Demands
We follow the approach of Chiang et al. [36] and McWilliams [37] in modeling consumer demand for the superior and inferior firms’ software services. Consumers evaluate the utility of purchasing either the superior’s or inferior’s service, considering price, brand preference, and cybersecurity investments (i.e., either bug bounty programs or in-house deterrence investment). We assume that consumer preferences are heterogeneous, and each consumer’s valuation of the superior firm’s software is denoted as their willingness to pay (WTP) , which is uniformly distributed in the interval . In addition, consumers prefer the superior firm’s brand over the inferior firm’s brand (e.g., [36,38,39,40]). Thus, WTP for the inferior firm’s product is a discounted fraction of , denoted as , where represents the discount factor applied to the inferior firm’s service valuation.
Given the central role of cybersecurity investments in shaping consumer valuation, it is crucial to clarify how these investments become visible to consumers. Consumers typically gauge a firm’s cybersecurity efforts through multiple observable signals. Certifications such as ISO 27001 or SOC 2 are prominently displayed by firms, serving as explicit indicators of robust security management practices [41]. For example, Dropbox prominently features its ISO 27001 certification and independent audit reports on its security page to demonstrate commitment to data protection and transparency, thus shaping consumer perceptions positively [42]. Firms also use targeted marketing communications and explicit privacy disclosures to highlight cybersecurity measures, further enhancing trust and perceived value. In addition, consumers rely on direct experiences, online user reviews, and media coverage that detail security incidents or successful incident management strategies. Lastly, third-party audits and independent security ratings significantly influence consumer trust by providing credible validation of firms’ cybersecurity claims [43].
Under no-action case (Strategy N), consumers recognize this vulnerability and factor it into their purchasing decisions. We denote to present the potential loss of cyberattack from using Firm i’s service. A consumer’s utility from adopting the superior firm’s service is given by , while the utility from purchasing the inferior firm’s service is expressed as . The consumer with a utility (i.e., requiring ) is indifferent to buying from the superior firm and making a purchase at all. Similarly, if (i.e., requiring ), is indifferent buying from the inferior firm. The consumer with a valuation of , where is indfferent between the two services, while when the valuation is greater than this consumers prefer the superior firm’s service. If , then , and consumers in the interval prefer the inferior firm’s service, while those in prefer the superior firm’s service. If , then , and no consumers purchase from the inferior firm.
Under the in-house protection case (Strategy I), both firms invest in internal security measures. The security benefit for each firm is represented by , where denotes the firm’s in-house security investment, and captures the average benefit users derive from in-house security. The consumer utility functions are given by for the superior firm, and for the inferior firm.
Under bug bounty program case (Strategy B), firms rely on external researchers to identify and report vulnerabilities. This approach enhances security and strengthens consumer trust. The impact of the bug bounty program is modeled by , where represents the firm’s investment in the program, and captures consumer sensitivity to security improvements resulting from such initiatives. Accordingly, the consumer utility functions are given by: , and . These utility functions under the three strategies, along with the conditions for coexistence and demand, are summarized in Lemma 1.
Lemma 1.
For , two-competing brands can co-exist if and only if , the market is segmented by the firms’ services, and the demands for the superior and inferior software services are
- (i)
- and ,
- (ii)
- and ,
- (iii)
- and , respectively.
As shown in Lemma 1, when , both brands have demand, where j is the index for strategy and . All proofs are provided in the Appendix A.
4. Equilibrium Decisions
4.1. No-Action Case (Strategy N)
We now consider the baseline scenario, Strategy N, in which both firms take no action to mitigate cybersecurity risks. The firms aim to decide the optimal prices to maximize thier profits, given by
In Equation (1), Firm i earns revenue from its software service, where c is the development cost per user. The term captures the firm’s profit, and the total revenue is . Notably, due to the characteristics of information products, we assume that product development costs are sunk, and the marginal cost of reproducing an add-on is zero [44,45]. This assumption holds throughout the paper. The following proposition presents the equilibrium prices under no-action strategy, as presented in Proposition 1.
Proposition 1.
Under Strategy N, the equilibrium prices are
Proposition 1 characterizes the firms’ equilibrium pricing decisions under the no-action strategy. We find that the price sets by the superior firm () decreases with its own potential cyberattack loss , i.e., . This result reflects the fact that as the reputational or risk-related cost increases, the superior firm is pressured to lower its price to remain attractive to consumers. Moreover, the same price increases with the potential loss associated with the inferior firm , i.e., , because greater perceived risk from the competitor allows the superior firm to charge more while remaining the safer option.
For the inferior firm, the price increases with the superior firm’s cyberattack risk, i.e., , as consumers become more tolerant of the inferior firm’s offering when the superior firm’s reputation is weakened. Lastly, decreases with its own cyber risk , i.e., , due to reduced willingness to pay for a less secure service. These dynamics highlight that even when firms do not actively invest in security, perceived risk differences still shape pricing power. A dominant software provider facing rising reputational threats may need to lower prices preemptively to avoid customer attrition, while a smaller competitor can maintain or even increase prices if the rival’s vulnerabilities become more salient. This suggests that in markets where consumers are highly sensitive to relative security perceptions, managers should monitor competitors’ incident histories closely, as these external events can significantly influence optimal pricing strategies.
4.2. In-House Protection Case (Strategy I)
Under Strategy I, firms invest in in-house security measures to proactively protect their software against potential vulnerabilities. Each firm strategically determines both its in-house protection effort and subscription price with the objective of maximizing its expected profit.
In Equation (4), the firm’s profit consists of two components: (i) revenue from software subscriptions , and (ii) the cost of in-house security investment , where is the cost-efficiency of in-house security spending of Firm i. Through backward induction, we can solve the firms’ equilibrium decisions under Scenario I as shown in Proposition 2.
Proposition 2.
Under Strategy I, the equilibrium in-house protection investments are
The equilibrium prices are
Proposition 2 provides the equilibrium expressions for in-house protection efforts and prices under Strategy I, where firms actively invest in internal security to mitigate cyber risks. A key distinction from the no-action scenario lies in how cyberattack risks ( and ) influence firm decisions. Under Strategy N, these risks affect consumer utility directly, resulting in pricing adjustments based solely on perceived vulnerability. In contrast, under Strategy I, firms respond to heightened risk by increasing their internal protection efforts , which not only enhances perceived trust but also offsets some of the negative utility effects, thereby moderating the impact on consumer demand.
The comparative statics reveal that both and respond asymmetrically to changes in cyber risk parameters. Specifically, an increase in Firm 1’s or Firm 2’s cyberattack loss ( or ) leads to a decrease in —that is, and . This reflects Firm 1’s strategic need to absorb more cost to remain competitive in the presence of heightened risk, even after increasing its protection effort.
In contrast, Firm 2’s price responds differently. While decreases as increases—i.e., , suggesting indirect effects of rival competition—the price increases with its own cyberattack loss, . This occurs because the inferior firm, facing higher risk, must invest more in protection and can partially pass these costs onto consumers, especially when its perceived value improves through internal security enhancement. These insights suggest that leading firms may prefer to absorb higher security costs to defend their reputation and competitive position, while smaller competitors could use visible security investments to justify modest price increases and build consumer trust. In practice, this means managers should coordinate security spending and pricing decisions rather than treating them independently.
4.3. Bug Bounty Program (Strategy B)
In this strategy, Firm i invests in a bug bounty program to mitigate security risks by incentivizing ethical hackers to report vulnerabilities. The firms determine their optimal bug bounty investment and subscription price to maximize their profits as follows:
In Equation (9), the firm’s profit comprises four components: (i) revenue from software subscriptions ; (ii) Expected loss from vulnerabilities being exploited . Here represents the potential loss when an exploit occurs, and is the probability that a hacker ethically reports a discovered vulnerability. This probability increases with higher bug bounty investment , thereby reducing the risk of exploitation; and (iii) the cost of investment in the bug bounty program, captured by , where is the cost coefficient corresponding to the firm’s security investment effort. We can solve the firm’s equilibrium decisions under Scenario B as shown in Proposition 3.
Proposition 3.
Under Strategy B, the equilibrium invesments for bug bounty program are
The equilibrium prices are
Proposition 3 shows a similar results with Proposition 2. Specifically, as cyberattack risk increases, the superior firm reduces its price, i.e., and , while the inferior firm lowers its price in response to the competitor’s vulnerability (), but raises it when its own risk increases (). These results reflect the dual pressures faced by firms adopting bug bounty programs. On one hand, higher cyber risk necessitates greater investment in security incentives to encourage vulnerability disclosure. On the other hand, the firms must maintain competitive pricing to retain customer trust, especially when the market is sensitive to perceived security. The superior firm, in particular, absorbs more of the security cost internally to preserve its advantage, leading to lower prices under increased threat.
For the inferior firm, a rise in its own cyber risk prompts a more aggressive investment in the bug bounty program to compensate for its weaker position. This justifies a moderate price increase to recover some of the expenditure, as consumers may value the enhanced protection and be willing to pay a premium. These results have important implications for software firms considering the use of bug bounty programs. For example, a smaller SaaS provider with limited brand recognition may find that signaling improved security through visible bounty payouts allows it to charge higher subscription fees, offsetting the cost of incentivizing ethical hackers [12]. In contrast, an established platform provider may be compelled to lower prices in response to rising cyber threats to protect its market share, even if it is already investing heavily in security incentives. More broadly, the findings suggest that firms should not treat security expenditures and pricing independently. Instead, managers need to coordinate these decisions carefully to balance reputational considerations, cost recovery, and competitive dynamics.
5. Analysis of the Strategies
In this section, we analyze how each strategy affects the firms’ decisions and profitability by comparing the equilibrium outcomes across the three strategies. For clarity, the thresholds are provided in the Appendix A. Moreover, to illustrate the equilibrium properties of the model, we conduct numerical simulations using hypothetical parameter values that are not drawn from any specific enterprise data but are broadly consistent with ranges reported in prior literature (e.g., [25,27,34,35]). Specifically, the baseline parameter settings for the simulations are as follows: , , , , , , , , , , , , and .
5.1. Impact on the Firm Pricing Behavior
Now, we compare the equilibrium prices under the three strategies and attempt to determine the effects of the firm’s action to handle cybersecurity for their pricing behaviors, as shown in Proposition 4.
Proposition 4.
Comparative analysis of the firm’s equilibrium prices.
- (i)
- When the discount factor applied to the inferior firm’s service valuation is low, the superior firm sets the highest price under the bug bounty strategy, i.e., . However, when θ becomes sufficiently large, the superior firm sets the highest price under the no-action strategy, i.e., .
- (ii)
- Regardless of the value of θ, the inferior firm always sets the most expensive price under in-house security strategy, i.e., .
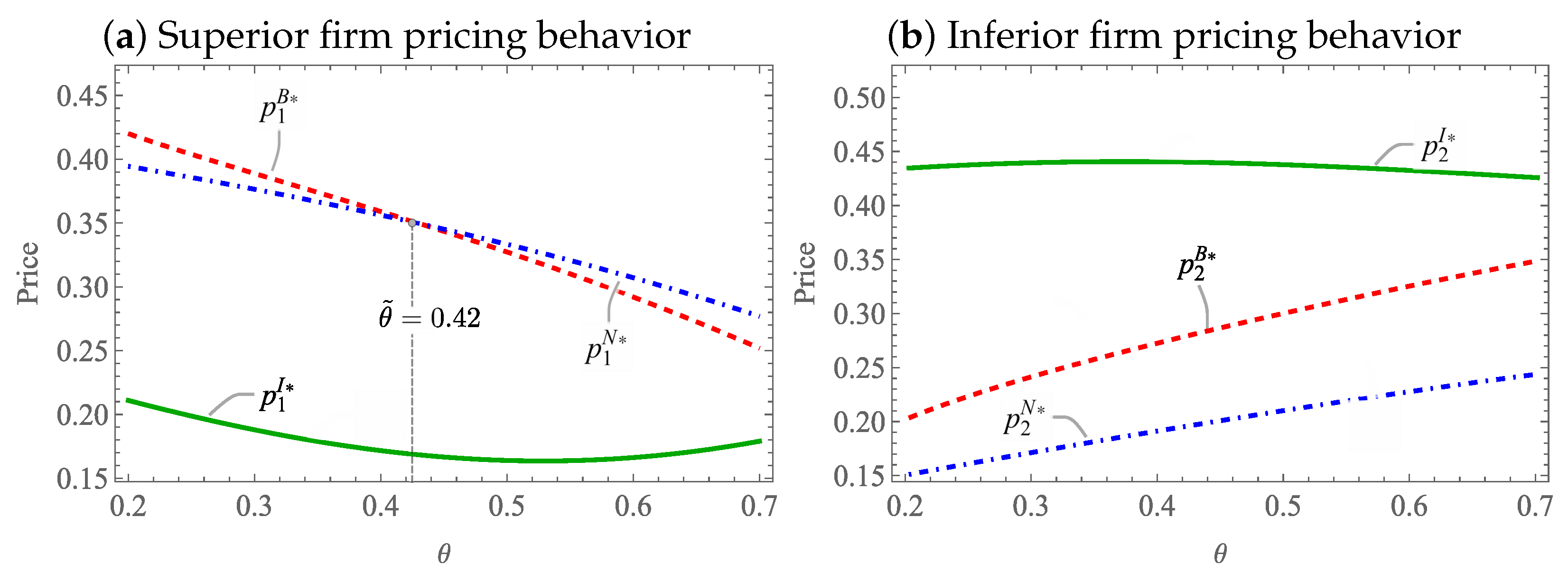
Proposition 4 (i) shows that when the discount factor applied to the inferior firm’s service valuation is low, consumers perceive the inferior firm’s service as substantially less valuable, which strengthens the superior firm’s competitive position. In this environment, the superior firm benefits most from adopting the bug bounty strategy, as enhanced security measures significantly differentiate its service, allowing it to command the highest price. Thus, the pricing order follows . However, as increases, the perceived gap between the two firms narrows, making consumers less sensitive to security differences. Consequently, as illustrated in Figure 2a, the superior firm’s advantage from bug bounty investment diminishes, and it becomes optimal to set the highest price under the no-action strategy instead, reversing the price order to .

Figure 2.
Pricing behaviors of superior and inferior firms.
Interestingly, for the superior firm, the in-house protection strategy consistently results in the lowest equilibrium prices among all strategies. This is because in-house security investment imposes direct and quadratic costs on the firm, increasing operational expenses without proportionately expanding consumer demand. Although improved security enhances consumer utility, the marginal benefit from in-house protection is limited compared to external bug bounty programs, where disclosures can be incentivized more cost-effectively. Consequently, the superior firm must lower its prices under Strategy I to remain competitive and attract consumers, absorbing part of the investment cost instead of fully passing it onto customers.
In contrast, Proposition 4 (ii) and Figure 2b reveals that the inferior firm consistently sets the highest price under the in-house security strategy. This pricing behavior is primarily driven by the structure of the firm’s cost function. Internal protection efforts entail direct and increasing (quadratic) costs, which must be partially recovered through higher pricing. Since Strategy I does not benefit from external efficiency gains (as in the bug bounty case), the inferior firm must rely more heavily on price to offset its security expenditures. Moreover, the in-house strategy improves the firm’s perceived trustworthiness, which allows it to sustain a higher price without completely losing market demand. However, the primary reason for the elevated price lies in the need to internalize the cost of protection. This differs from strategies like bug bounty or no-action, where either the cost burden is lower or security investments are not undertaken at all. Therefore, the in-house strategy leads to the highest price for the inferior firm not because of competitive strength.
5.2. Impact on the Firm Cybersecurity Investment
We now compare the equilibrium investments between in-house security and bug bounty strategies, as illustrated in Proposition 5.
Proposition 5.
Comparative analysis of the firm’s equilibrium investments.
- (i)
- Regardless of the development cost of the software service c, the superior firm always exerts greater security effort under the bug bounty strategy, i.e., .
- (ii)
- No matter how high the development cost c is, the inferior firm always exerts greater security effort under the in-house security strategy, i.e., .
Proposition 5 reveals that for the superior firm, the bug bounty strategy consistently induces a higher level of security effort compared to in-house protection, irrespective of the development cost c. This outcome stems from the superior firm’s advantage in leveraging external expertise: by incentivizing independent researchers through bug bounty programs, the firm can achieve broader vulnerability coverage at a lower marginal cost, thereby justifying greater overall investment.
Conversely, the inferior firm exhibits the opposite behavior. Regardless of c becomes, the inferior firm always exerts greater security effort under the in-house security strategy compared to the bug bounty strategy. This tendency reflects the inferior firm’s strategic caution: without strong market dominance, relying heavily on external actors (as in bug bounty programs) may not be as cost-effective or reliable. Hence, the inferior firm prefers investing more internally to maintain control over its security outcomes, even though it incurs direct operational costs.
5.3. Impact on the Firm Preferences Toward the Strategies
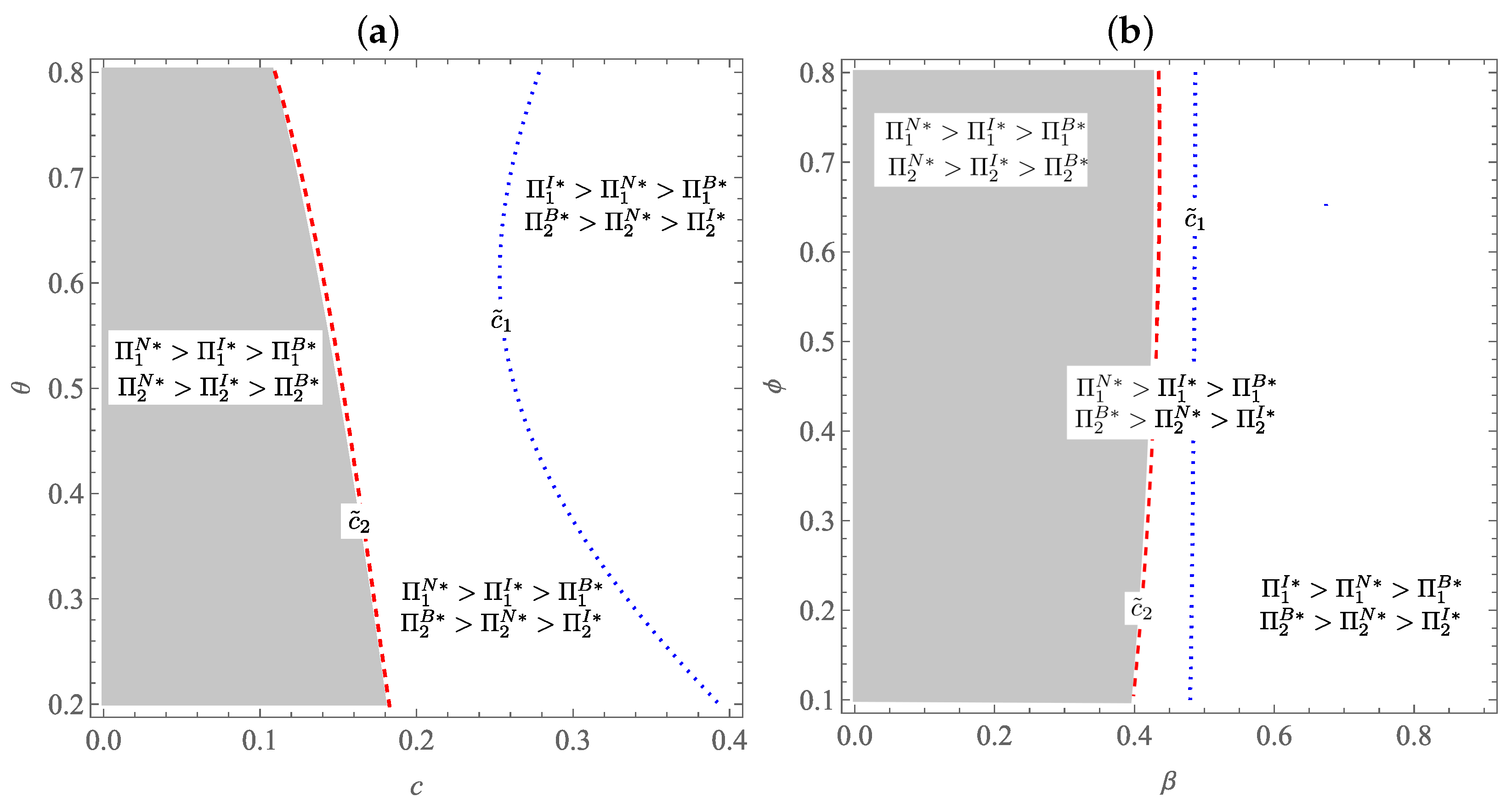
We compare the firms’ preferences under the three strategies, as shown in Proposition 6 and Figure 3.

Figure 3.
The parametric effects on the firms’ preferences and their equilibrium choices. (a) Firms’ preferences w.r.t. and c. (b) Firms’ preferences w.r.t. and .
Proposition 6.
Firms’ strategic preferences toward the software security strategies.
- (i)
- For the superior firm, when the development cost of the software service is low, the no-action strategy yields the highest profit, i.e., . However, when c is high, the in-house cybersecurity strategy becomes more profitable, i.e., .
- (ii)
- For the inferior firm, when c is low, the no-action strategy yields the highest profit, i.e., . However, when c is significant, the bug bounty strategy becomes more profitable, i.e., .
Proposition 6 (i) shows that when the development cost c is low, the marginal gain from enhanced security is relatively limited given the superior firm’s already dominant market position. In this situation, adopting a no-action strategy is optimal, as it allows the firm to avoid unnecessary operational expenses while relying on its existing reputation and customer loyalty. However, as the development cost rises ()—often reflecting increasing system complexity—the potential risks associated with security breaches also grow, due to a larger attack surface and higher likelihood of vulnerabilities [46]. Investing in in-house cybersecurity becomes more attractive because it enables the firm to exert greater control over security outcomes, protecting its market leadership and minimizing long-term reputational risks.
Similarly, in Proposition 6 (ii), we find when , the inferior firm, like its stronger counterpart, benefits most from a no-action strategy by keeping operational costs to a minimum. Yet, as development costs escalate (), the firm’s weaker market position makes heavy internal investment economically unviable. Unlike the superior firm, the inferior firm cannot easily leverage brand strength to offset increased costs. Consequently, instead of pursuing costly in-house solutions, the inferior firm turns to bug bounty programs as a more cost-effective alternative. These programs allow the firm to tap into external expertise while maintaining financial flexibility. This shift reflects the inferior firm’s pragmatic need to manage limited resources and stay competitive under tighter budget constraints.
Based on Proposition 6, we compare the firms’ preference strategies, as outlined in Corollary 1.
Corollary 1.
Comparative analysis of the firms’ preference software security strategies.
- (i)
- When and .
- (ii)
- When .
- (iii)
- When and .
Corollary 1 shows that when and , the development cost is low, such that neither firm perceives strong incentives to invest in additional security, so both continue to rely on the no-action strategy to minimize expenses. When the cost rises past the threshold but remain below , the inferior firm, with less established brand strength, finds that maintaining no-action becomes riskier and less competitive. As a result, it adopts a bug bounty strategy to improve perceived security in a cost-effective way. The superior firm, however, continues to rely on its established reputation and does not yet see sufficient value in switching from no-action. Finally, when the cost exceeds both thresholds ( and ), the environment becomes more complex and the potential impact of security breaches grows. The superior firm adopts in-house protection to exert tighter control over security risks and reinforce its market position. The inferior firm continues to rely on bug bounty programs as a more flexible and affordable way to strengthen security without incurring the higher fixed costs associated with in-house solutions.
We further discuss the parametric effects on the firm’s equilibrium choices in Corollary 2.
Corollary 2.
Parametric effects on the thresholds are as follows:
- (i)
- , , and .
- (ii)
- , and .
Corollary 2 (i) and Figure 3 demonstrates that the threshold , which determines the superior firm’s preferred strategy, decreases as the discount factor increases. This implies that when consumers perceive the inferior firm’s service as more comparable (i.e., higher ), the superior firm loses pricing power and is less inclined to bear the cost of external security investment. On the other hand, the threshold increases with the ethical disclosure probability , as a higher likelihood of bug reports enhances the effectiveness of bug bounty programs. Interestingly, remains unchanged across different levels of consumer sensitivity , as seen in the vertical demarcation in Figure 3c, indicating that the superior firm’s strategic choice is robust to variations in how consumers value security improvements.
Corollary 2 (ii) and Figure 3 shows that the inferior firm’s threshold is more responsive to all three parameters. As the discount factor increases, declines, suggesting that when consumers perceive the inferior product as relatively better, the firm becomes more willing to invest in bug bounty programs. Moreover, the threshold rises with both the probability of ethical disclosure and consumer sensitivity to security improvements . This pattern highlights the inferior firm’s greater dependence on trust-building mechanisms to compensate for its initial disadvantage in perceived service quality. In addition, the sensitivity analysis shows that a higher likelihood of ethical vulnerability disclosure and stronger consumer responsiveness to security enhancements encourage greater investment in external security measures, particularly for the inferior firm. This result is consistent with [34], who found that vulnerability disclosure dynamics critically shape firms’ willingness to engage in bug bounty programs.
6. Discussion and Conclusions
6.1. Discussion
This study integrates cybersecurity investment decisions into a competitive software pricing framework, highlighting how firms strategically manage in-house protection, bug bounty programs, and pricing to balance security risks, cost efficiency, and consumer trust. Our findings contribute to several streams of research, including cybersecurity investment behavior (e.g., [13,27]), pricing competition under digital service settings (e.g., [20,21]), and the design of market-based vulnerability disclosure mechanisms (e.g., [12,32]). First, the analysis shows that firms’ pricing behavior is strongly driven by consumer perception of service differentiation. When consumers perceive the inferior firm’s service as significantly less valuable, the superior firm benefits from adopting a bug bounty strategy, which enhances consumer trust through credible security efforts and allows it to command higher prices. This is consistent with prior research emphasizing that visible security improvements can serve as a competitive advantage in digital service markets [28]. However, as the discount factor increases and the perceived gap between services narrows, the superior firm’s advantage from security investments diminishes. Consequently, the superior firm shifts to relying on a no-action strategy, setting higher prices based solely on intrinsic service value rather than security enhancements. Second, our results reveal asymmetries between the superior and inferior firms regarding the role of in-house protection. The in-house strategy consistently leads the superior firm to set the lowest prices, as internal security investments impose significant cost burdens with only modest marginal increases in consumer utility. This finding aligns with [29], who observed that when security investment yields diminishing consumer gains, firms must absorb more costs through lower pricing. In contrast, the inferior firm leverages in-house protection to enhance its credibility, charging the highest prices across strategies. This behavior reflects the strategic use of security investments as a differentiation tool when starting from a disadvantaged position. Third, the intensity and nature of cybersecurity investments differ significantly across strategies and firms. The superior firm tends to invest more heavily in external bug bounty programs, taking advantage of cost-effective vulnerability disclosure through incentivized ethical hacking. This supports [12]’s findings that externally sourced security improvements can efficiently enhance software quality. Conversely, the inferior firm favors larger in-house investments, prioritizing control over security processes to directly shape consumer perceptions of reliability and trustworthiness. Finally, the strategic preference between no-action, in-house protection, and bug bounty strategies varies with the level of software development costs. When development costs are low, both firms avoid security investments to minimize expenditure. As costs rise, the superior firm increasingly shifts toward in-house protection to safeguard its brand and user base, whereas the inferior firm relies on bug bounty programs to maintain flexibility and control costs. These results are consistent with [14], who emphasized that firms facing higher failure risks must align security investment strategies with cost structures and competitive positioning.
6.2. Managerial Implications
This study provides several actionable insights for managers of software firms considering how to allocate cybersecurity investments in competitive environments. First, balancing security and pricing. Firms should recognize that security expenditures and pricing decisions are interdependent. Investing in cybersecurity is not only a technical measure but also a strategic lever to shape market perceptions and defend market share. Second, responding to increasing development costs. As software development costs rise and systems become more complex, firms must reevaluate their security strategy. Leading firms may find it necessary to invest more heavily in in-house protection to reduce risk and protect their reputation, while smaller competitors can maintain flexibility through cost-effective bug bounty programs. Third, monitoring competitive dynamics. Because perceived cyber risk can change rapidly in response to competitor actions or public disclosures, managers should monitor the security environment closely and be prepared to adjust pricing and investment levels dynamically.
Overall, these findings emphasize that cybersecurity strategy should be tailored to a firm’s relative market position, consumer trust dynamics, and cost structure, rather than treated as a standalone operational decision.
6.3. Conclusions
This study offers new insights into how cybersecurity and pricing decisions are intertwined in competitive software markets. Unlike previous models that treat cybersecurity risks as exogenous or examine security investment in isolation (e.g., [27,34]), our framework endogenizes security choices and explicitly links them to pricing strategies in a competitive duopoly setting. This integration is one of the key contributions of the paper, as it shows how firms’ cybersecurity decisions dynamically interact with consumer trust and competitive positioning.
The main innovations of this study are threefold. First, we develop a unified game-theoretic model comparing three distinct cybersecurity strategies—no action, in-house protection, and bug bounty programs—within the same analytical framework. Prior research typically investigates either internal security investments (e.g., [27]) or bug bounty programs separately (e.g., [12,34]) but does not analyze their comparative impacts under direct market competition. Second, our model incorporates asymmetric firm positions, allowing us to capture how superior and inferior firms adopt different security strategies depending on their brand strength and cost structures, extending the work on asymmetric competition (e.g., [35]). Third, we demonstrate that cybersecurity investments are not merely operational costs but strategic tools that directly shape market outcomes, such as equilibrium pricing and the allocation of demand across firms.
The results show that cybersecurity investment is not a stand-alone technical decision but a key component of strategic market positioning. Superior firms leverage external programs to differentiate when quality gaps are large, while inferior firms rely on in-house protection to rebuild credibility. Pricing strategies are directly affected by cybersecurity investments, with in-house protection exerting downward pressure on prices for leading firms and upward pressure for challengers. Future research could extend this work by considering dynamic multi-period competition, where firms adjust security and pricing decisions over time in response to emerging threats and observed competitor strategies. Moreover, incorporating consumer heterogeneity in security awareness or trust sensitivity, as well as regulatory impacts such as mandatory disclosure requirements, would offer valuable extensions to further enrich the strategic cybersecurity literature.
Funding
This research is partially suppoted by the National Science and Technology Council, Taiwan, under NSC 113-222-E-167-005.
Data Availability Statement
There is no data availability to be shown.
Conflicts of Interest
The author declares that they have no known financial conflicts of interest or personal relationships that could have influenced the work presented in this paper.
Appendix A
Proof of Proposition 1.
Under Strategy N, the uniqueness of for can be assured because . Then, solving for , we obtain the inferior firm’s best response decision :
Next, we take in Equation (A1) and into . The uniqueness of for can be assured because . Thus, solving the first-order condition of gives the unique equilibrium :
By substitute into the firm’s best-response decision in Equation (A1), we obtain the equilibrium price :
The parametric effects can be verified based on the following derivation.
Thus, Proposition 1 is proved. □
Proof of Proposition 2.
The Hessian matrix of the firm’s profit with respect to and is
Thus, the Hessian matrix is negative definite, indicating that is jointly concave in and . Then, simultaneously solving for , , we obtain the inferior firm’s best response decisions as follows:
Next, we take and in Equation (A4) and into . The uniqueness of and for and , respectively can be assured because and . Thus, solving the first-order condition of and gives the unique equilibriums and :
By substitute and into the firms’ best-response decision in Equation (A4), we obtain the equilibrium results of the interior firm as follows:
The parametric effects can be verified based on the following derivation.
The proof of Proposition 2 is completed. □
Proof of Proposition 3.
Regarding the proof of the equilibrium results under Strategy B, we follows the same steps as the proof of Proposition 2 and is therefore omitted here. The parametric effects can be verified through the following derivations.
The proof of Proposition 3 is completed. □
Proof of Proposition 4.
The comparative analysis of the firm’s optimal prices among the three strategies is as follows:
(i) Regarding the discrepancies between Firm 1’s equilibrium prices, we have
- The discrepancy between and is
- The discrepancy between and is
- The discrepancy between and isDue towe can obtain a threshold by solving , given byThus, , if and only if (iff) .
(ii) Regarding the discrepancies between Firm 2’s equilibrium prices, we have
- The discrepancy between and is
- The discrepancy between and is
- The discrepancy between and isThus, always holds.
Therefore, iff , iff , and . The proof is completed. □
Proof of Proposition 5.
The comparative analysis of the firm’s optimal efforts between Strategy I and Strategy B are as follows:
- The discrepancy between and is
- The discrepancy between and is
Therefore, and . The proof is completed. □
Proof of Proposition 6.
The comparative analysis results for Firm 1’s equilibrium profits among the three strategies are as follows:
(a) The discrepancy between and is as follows:
(b) The discrepancy between and is as follows:
(c) The discrepancy between and is as follows:
Because
we can obtain a threshold by solving , given by
Hence, iff , .
The comparative analysis results for Firm 2’s equilibrium profits among the three strategies are as follows:
(a) The discrepancy between and is as follows:
(b) The discrepancy between and is as follows:
Because
we can obtain a threshold by solving , given by
Thus, iff , .
We can conclude that iff , ; iff , ; iff , ; and iff , . The proof is completed. □
Proof of Corollary 1.
Since the results follow directly from Proposition 6, we omit the proof here. □
Proof of Corollary 2.
The parametric effects can be verified through the following derivations.
The proof is completed. □
References
- Anderson, R.; Moore, T. The economics of information security. Science 2006, 5799, 610. [Google Scholar] [CrossRef] [PubMed]
- Gordon, L.A.; Loeb, M.P.; Zhou, L. Investing in cybersecurity: Insights from the gordon-loeb model. J. Inf. Secur. 2016, 2, 49. [Google Scholar] [CrossRef]
- Raymond, E.S. The Cathedral & the Bazaar: Musings on Linux and Open Source by an Accidental Revolutionary, 1st ed.; O’Reilly Media: Sebastopol, CA, USA, 2001. [Google Scholar]
- Ruohonen, J.; Hyrynsalmi, S.; Leppänen, V. A mixed methods probe into the direct disclosure of software vulnerabilities. Comput. Hum. Behav. 2020, 103, 161. [Google Scholar] [CrossRef]
- Daryna, A. Google Bug Bounty Program Paid a Record $12 Million Last Year. The Record. 2023. Available online: https://therecord.media/google-bug-bounty-program-2022-12-million (accessed on 26 June 2025).
- Aanchal, G. Celebrating Ten Years of the Microsoft Bug Bounty Program and More Than $60M Awarded. Microsoft. 2023. Available online: https://msrc.microsoft.com/blog/2023/11/celebrating-ten-years-of-the-microsoft-bug-bounty-program-and-more-than-60m-awarded/ (accessed on 27 June 2025).
- Neta, O. Looking Back at Our Bug Bounty Program in 2022. Meta. 2022. Available online: https://about.fb.com/news/2022/12/metas-bug-bounty-program-2022/ (accessed on 27 June 2025).
- Davey, W. Apple Confirms iPhone Hacking Reward of $1.5 Million. Forbes. 2019. Available online: https://www.forbes.com/sites/daveywinder/2019/12/20/apple-confirms-iphone-hacking-reward-of-15-million/ (accessed on 27 June 2025).
- Robert, L. Intel: More Than 90% of Our Vulnerabilities Found via Research. Darkreading. 2021. Available online: https://www.darkreading.com/vulnerabilities-threats/intel-more-than-90-of-our-vulnerabilities-found-via-research (accessed on 27 June 2025).
- Chatfield, A.T.; Reddick, C.G. Crowdsourced cybersecurity innovation: The case of the pentagon’s vulnerability reward program. Inf. Polity 2018, 2, 177. [Google Scholar] [CrossRef]
- Walshe, T.; Simpson, A. An empirical study of bug bounty programs. In Proceedings of the 2020 IEEE 2nd International Workshop on Intelligent Bug Fixing (IBF), London, ON, Canada, 18 February 2020; p. 45. [Google Scholar]
- Zhao, M.; Laszka, A.; Grossklags, J. Devising effective policies for bug-bounty platforms and security vulnerability discovery. J. Inf. Policy 2017, 7, 372. [Google Scholar] [CrossRef]
- Fielder, A.; Panaousis, E.; Malacaria, P.; Hankin, C.; Smeraldi, F. Decision support approaches for cyber security investment. Decis. Support Syst. 2016, 86, 13. [Google Scholar] [CrossRef]
- Feng, N.; Zhou, T.; Feng, H.; Li, M. Optimal launch timing of bug bounty programs for software products under different licensing models. J. Assoc. Inf. Syst. 2024, 2, 239. [Google Scholar] [CrossRef]
- Trello. Operations and Security. Atlassian. 2025. Available online: https://trello.com/legal/security (accessed on 18 February 2025).
- Michael, C.; Sri, T. Introducing Google Cloud’s New Vulnerability Reward Program. Google Clound. 2024. Available online: https://cloud.google.com/blog/products/identity-security/google-cloud-launches-new-vulnerability-rewards-program (accessed on 18 February 2025).
- Dropbox. Bug Bounty Program. Dropbox.Tach. 2025. Available online: https://dropbox.tech/tag-results.bug-bounty-program (accessed on 18 February 2025).
- Lexi, C. The Biggest Security Risks to Your Salesforce Org. Varonis. 2023. Available online: https://www.varonis.com/blog/security-risks-to-your-salesforce-org (accessed on 18 February 2025).
- Chen, W.; Zou, Y. Why zoom is not doomed yet: Privacy and security crisis response in the COVID-19 pandemic. Am. Behav. Sci. 2023, 00027642231155367. [Google Scholar] [CrossRef]
- Feng, H.; Jiang, Z.; Liu, D. Quality, pricing, and release time. MIS Q. 2018, 1, 333. [Google Scholar] [CrossRef]
- Guo, Z.; Ma, D. A model of competition between perpetual software and software as a service. MIS Q. 2018, 1, 101. [Google Scholar] [CrossRef]
- Zhang, Z. Competitive pricing strategies for software and saas products. Inf. Manag. 2020, 8, 103367. [Google Scholar] [CrossRef]
- Zhang, Z.; Nan, G.; Li, M.; Tan, Y. Competitive entry of information goods under quality uncertainty. Manag. Sci. 2022, 4, 2869. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, Z.-J.; Deveci, M.; Chen, Z.-S. Optimal releasing strategy of enterprise software firms facing the competition from cloud providers. Expert Syst. Appl. 2024, 236, 121264. [Google Scholar] [CrossRef]
- Tang, H.; Ai, X.; He, H.; Guo, S. Business expansion strategy of two competing software platforms: Envelopment vs. connection. Electron. Commer. Res. 2024, 4, 2239. [Google Scholar] [CrossRef]
- Lee, C.H.; Geng, X.; Raghunathan, S. Mandatory standards and organizational information security. Inf. Syst. Res. 2016, 1, 70. [Google Scholar] [CrossRef]
- Feng, N.; Chen, Y.; Feng, H.; Li, D.; Li, M. To outsource or not: The impact of information leakage risk on information security strategy. Inf. Manag. 2020, 5, 103215. [Google Scholar] [CrossRef]
- Li, H.; Yoo, S.; Kettinger, W.J. The roles of it strategies and security investments in reducing organizational security breaches. J. Manag. Inf. 2021, 1, 222. [Google Scholar] [CrossRef]
- Wu, Y.; Tayi, G.K.; Feng, G.; Fung, R.Y. Managing information security outsourcing in a dynamic cooperation environment. J. Assoc. Inf. Syst. 2021, 3, 2. [Google Scholar] [CrossRef]
- Aljaradat, A.; Sarkar, G.; Shukla, S.K. Modelling cybersecurity impacts on digital payment adoption: A game theoretic approach. J. Econ. Criminol. 2024, 5, 100089. [Google Scholar] [CrossRef]
- Maillart, T.; Zhao, M.; Grossklags, J.; Chuang, J. Given enough eyeballs, all bugs are shallow? revisiting eric raymond with bug bounty programs. J. Cybersecur. 2017, 2, 81. [Google Scholar] [CrossRef]
- Subramanian, H.C.; Malladi, S. Bug bounty marketplaces and enabling responsible vulnerability disclosure: An empirical analysis. J. Database Manag. 2021, 1, 38. [Google Scholar] [CrossRef]
- Akgul, O.; Eghtesad, T.; Elazari, A.; Gnawali, O.; Grossklags, J.; Mazurek, M.L.; Votipka, D.; Laszka, A. Bug {Hunters’} perspectives on the challenges and benefits of the bug bounty ecosystem. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; p. 2275. [Google Scholar]
- Zhang, L.; Demirezen, E.M.; Kumar, S. How to make my bug bounty cost-effective? A game-theoretical model. Inf. Syst. Res. 2024, 36, 1031–1053. [Google Scholar] [CrossRef]
- Wu, C.H.; Chamnisampan, N.; Sin, L. Freemium vs. Deterrence: Optimizing revenue in the face of piracy competition. J. Bus. Res. 2025, 194, 115354. [Google Scholar] [CrossRef]
- Chiang, W.-y.K.; Chhajed, D.; Hess, J.D. Direct marketing, indirect profits: A strategic analysis of dual-channel supply-chain design. Manag. Sci. 2003, 1, 1. [Google Scholar] [CrossRef]
- McWilliams, B. Money-back guarantees: Helping the low-quality retailer. Manag. Sci. 2012, 8, 1521. [Google Scholar] [CrossRef]
- Chamnisampan, N.; Wu, C.-H. Frenemies: Exploring interfirm credit between an incumbent and a capital-constrained startup. Int. Trans. Oper. Res. 2024. [Google Scholar] [CrossRef]
- Zhu, F.; Iansiti, M. Entry into platform-based markets. Strateg. Manag. 2012, 1, 88. [Google Scholar] [CrossRef]
- Pepall, L.M.; Richards, D.J. The simple economics of brand stretching. J. Bus. 2002, 3, 535. [Google Scholar] [CrossRef]
- Emily, B. SOC 2 vs. ISO 27001: What’s the Difference and Which Standard Do You Need? Secureframe. 2024. Available online: https://secureframe.com/blog/soc-2-vs-iso-27001 (accessed on 1 July 2025).
- Dropbox. ISO Certification. Dropbox. 2025. Available online: https://www.dropbox.com/business/trust/compliance/certifications-compliance (accessed on 27 June 2025).
- Raymond, C. How to Leverage Cybersecurity Audits to Enhance Customer Confidence Decrypt Compliance. Vocal. 2025. Available online: https://vocal.media/01/how-to-leverage-cybersecurity-audits-to-enhance-customer-confidence-decrypt-compliance (accessed on 27 June 2025).
- Shulman, J.D.; Geng, X. Add-on pricing by asymmetric firms. Manag. Sci. 2013, 4, 899. [Google Scholar] [CrossRef]
- Wu, D.; Nan, G.; Li, M. Optimal software upgrade strategy: Should we sell products or premium services in the presence of piracy? Electron. Commer. Res. Appl. 2018, 28, 219. [Google Scholar] [CrossRef]
- Walden, J.; Stuckman, J.; Scandariato, R. Predicting vulnerable components: Software metrics vs text mining. In Proceedings of the 2014 IEEE 25th International Symposium on Software Reliability Engineering, Naples, Italy, 3–6 November 2014; p. 23. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).