VBQ-Net: A Novel Vectorization-Based Boost Quantized Network Model for Maximizing the Security Level of IoT System to Prevent Intrusions
Abstract
:1. Introduction
1.1. Major Contributions
- ○
- In this work, an intelligent and novel security framework, named Vectorization-Based Boost Quantized Network (VBQ-Net), is developed for securing IoT systems;
- ○
- To select essential attributes from the featured data, a Vector Space Bag of Words (VSBW) methodology is implemented, which minimizes the dimensionality of features;
- ○
- Also, a new Boosted Variance Quantization Neural Network (BVQNN)-based classification algorithm is used with the weighted feature matrix to classify the type of intrusion from the given data;
- ○
- During classification, a Multi-Hunting Reptile Search Optimization (MH-RSO) algorithm is used to optimally compute the probability value for making proper decisions while predicting intrusions;
- ○
- The most popular recent datasets, such as IoTID-20, IoT-23, and CIDDS-001, are used in this study for validating and assessing the performance of the suggested framework.
1.2. Paper Organization
2. Literature Review
3. Materials and Methods
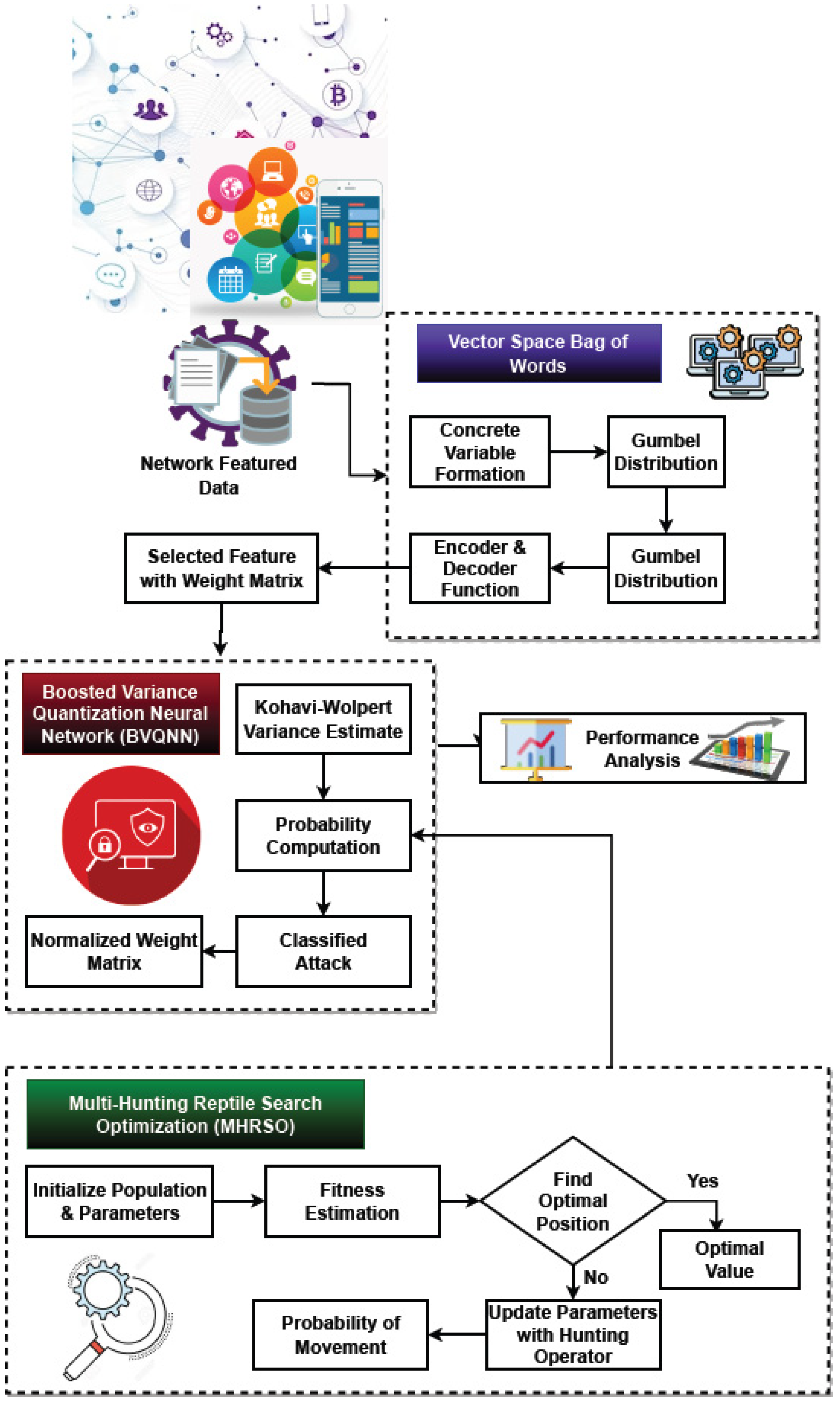
Proposed Framework
- ○
- Network-featured data collection;
- ○
- Feature selection using the Vector Space Bag of Words (VSBW);
- ○
- Intrusion identification using a Boosted Variance Quantization Neural Network (BVQNN);
- ○
- Probability estimation using Multi-Hunting Reptile Search Optimization (MH-RSO);
- ○
- Performance evaluation.
- A
- Vector Space Bag-of-Words (VSBW) for Feature Selection: The VSBW technique is used to select the most necessary and pertinent features for identifying and categorizing the type of intrusion from the IoT networks after the input dataset has been collected. Overall steps of VSBW are described in Algorithm 1. The dataset properties typically have a significant impact on intrusion detection performance, since they aid in the analysis of attack characteristics. Some optimization strategies were used in the earlier works for feature selection and dimensionality reduction. These methods struggle with the main issues of long search times, low efficiency, and intricate mathematical modeling. Therefore, the proposed study seeks to employ a straightforward as well as cutting-edge methodology for feature selection. In the proposed VSNW model, the following operations are performed to choose the relevant features:
- (a)
- Concrete variable formation;
- (b)
- Gumbel distribution;
- (c)
- Encoding and decoding operations;
- (d)
- Weight matrix formation.
| Algorithm 1: Vector Space Bag-of-Words |
| Input: Features data Output: Selected feature
|
- B.
- Boosted Variance Quantization Neural Network (BVQNN) Classification: The intrusion prediction and classification are carried out using the BVQNN technique, following the selection of features using the weight matrix. Earlier studies have used a variety of machine learning and deep learning methods to create successful intrusion detection systems for protecting IoT networks. The steps of BVQNN algorithm are described in Algorithm 2. However, the main issues with the current models include longer processing times, excessive overfitting, and increasing computing complexity. Determining the type of intrusion from the provided dataset using an innovative and efficient classification algorithm known as BVQNN is the goal of the presented work. This algorithm incorporates the procedures of adaptive boost classification and quantization neural network mechanisms for accurate prediction and classification. The most popular technique is often adaptive boosting, which enables the developer to continue integrating weak learners, whose precision is merely modest until an expected minimum training error is attained. It is “adaptive” since it does not necessitate prior understanding of the veracity of these assumptions. On the contrary, it evaluates the precision of a base hypothesis after each iteration and adapts its parameters. According to a weighted training dataset, it repeatedly generates base hypotheses. In accordance with how well component hypotheses perform in classification, the weights are adaptively adjusted.
| Algorithm 2: Boosted Variance Quantization Neural Network |
| Input: Training data , test data , associated distribution weight ; Output: Classified attack ; Procedure: Step 1: Initialize the training data and weight value as shown in Equations (8) and (9); Step 2: // total number of iterations Train the classifier with the weighted sample {} based on the hypothesis ; Step 3: Estimate the Kohavi–Wolpert variance at the time of training by using Equation (10); Step 4: Label probability computation with the weighted label value as shown in Equation (11); Step 5: Update the weight value according to the probability of input sample and weight vector by using Equation (12); Step 6: Normalize the weight value as shown in Equation (13); end for; Step 7: Produce the final classified output as indicated in Equation (14). |
- C.
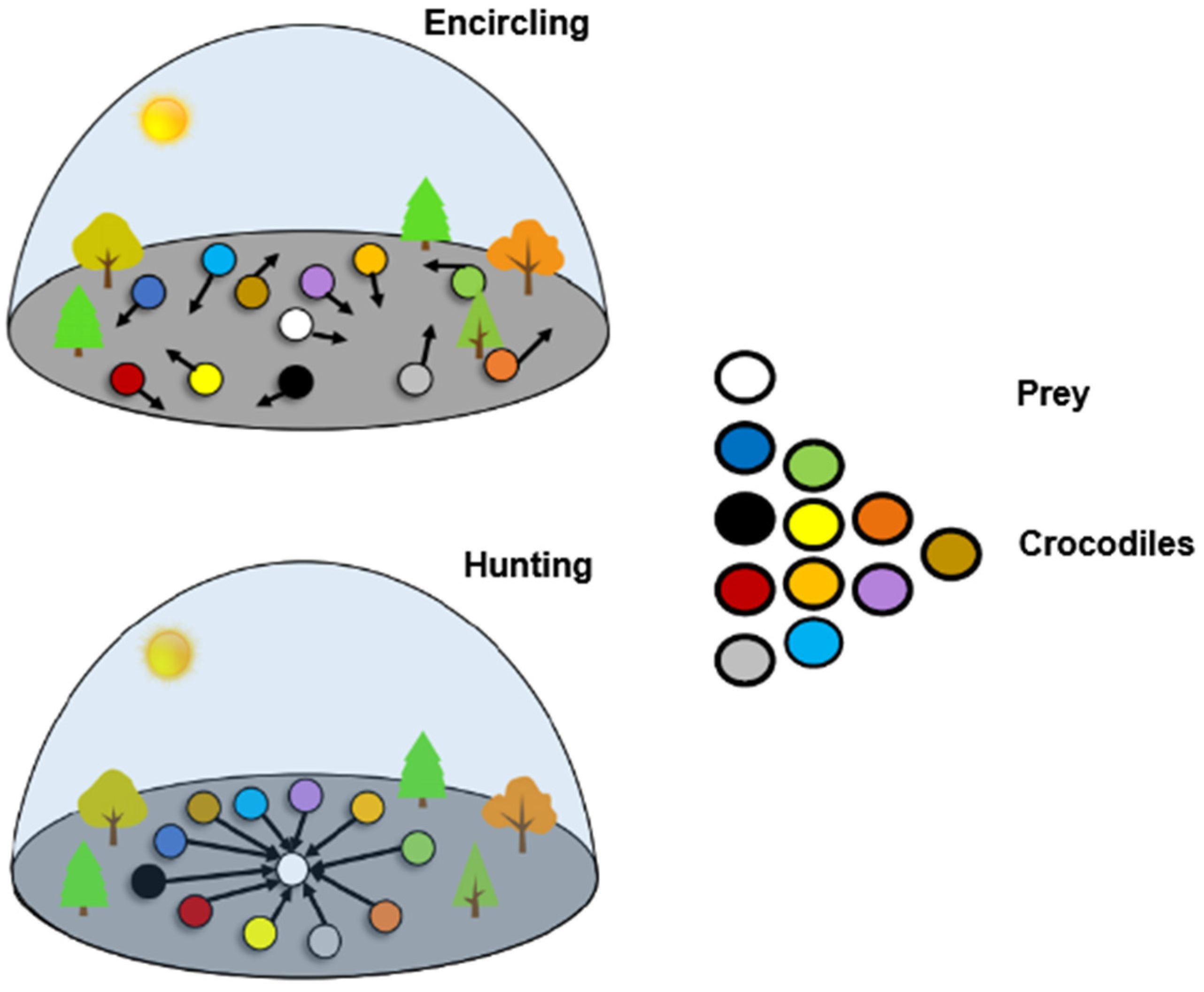
- Multi-Hunting Reptile Search Optimization Algorithm (MH-RSO): The MH-RSO algorithm is utilized in this study to forecast intrusions and classify them accurately by computing the classifier’s probability value in the best possible way. Numerous optimization strategies are employed in the current studies to solve several complex problems in an appropriate manner. In the proposed study, a unique MH-RSO technique is employed to categorize the intrusions in the dataset while computing the best probability weight value. Its main advantages over conventional optimization algorithms include accelerated convergence, high efficiency, and an optimal solution with few iterations. The search for the ideal value is known as optimization, where a minimal problem is typically created by transforming the optimization problem. The boundary’s lowest value, which further fulfills the constraint conditions, is the ideal global value. The reptile search algorithm models how crocodiles’ approach and pursue prey. The algorithm is broken down into four stages: exploration, which includes fast crawling and belly jogging, and exploitation, which includes collaborative and cooperative hunting. Crocodiles are going to approach their prey after spotting them during the early and final phases of the hunt. Even if MH-RSO possesses some fractional optimization capabilities, it will be difficult for MH-RSO to converge on the middle and late phases of a complicated issue if MH-RSO cannot identify a rough location of the best solution in its initial and intermediate stages. The hunting behavior of MH-RSO is illustrated in Figure 2 and described in Algorithm 3.
- Parameter initialization;
- Encircling;
- High walking;
- Belly walking;
- Hunting.
| Algorithm 3: Multi-Hunting Reptile Search algorithm (MH-RSA) |
| Input: feature matrix ; Output: Optimal value ; Procedure: Step 1: Initialization parameters: Candidate solution ; Dimension of each solution ; Total iteration ; Control the search accuracy ; Control the sensitive parameter to search capability ; Step 2: Initialize population ; Step 3: Calculate each individual’s fitness value of the population as shown in Equation (21); Step 4: Find the optimal position with lower bound and upper bound values as defined in Equation (22); Step 5: The searching parameter is updated by using Equation (23); Step 6: By using formulas from Equations (24) and (25), the parameters , , and R are updated for hunting operation; Step 7: Step 8: End for; End for; Step 9: ; Step 10: End while; Step 11: Return the best solution; |
4. Results
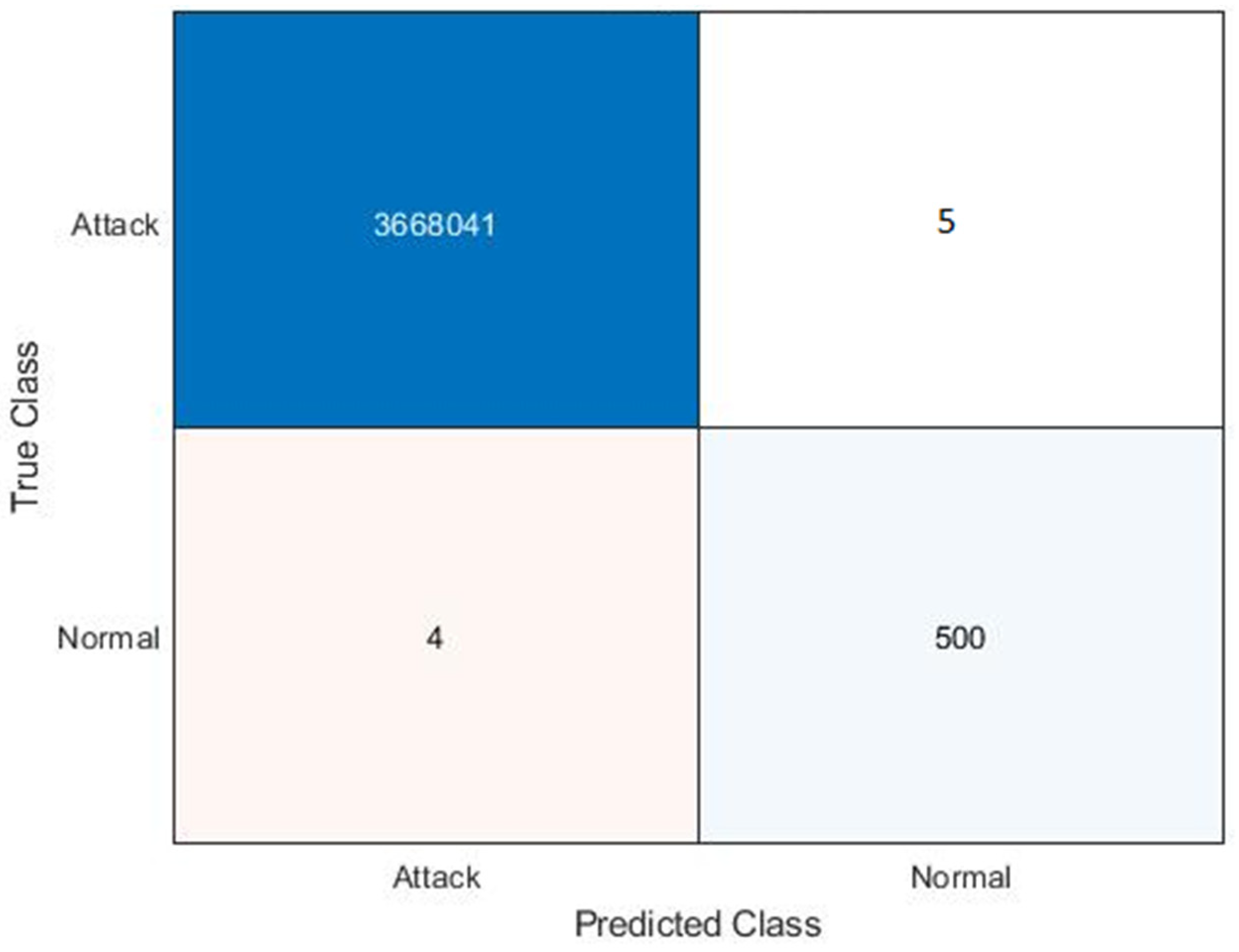
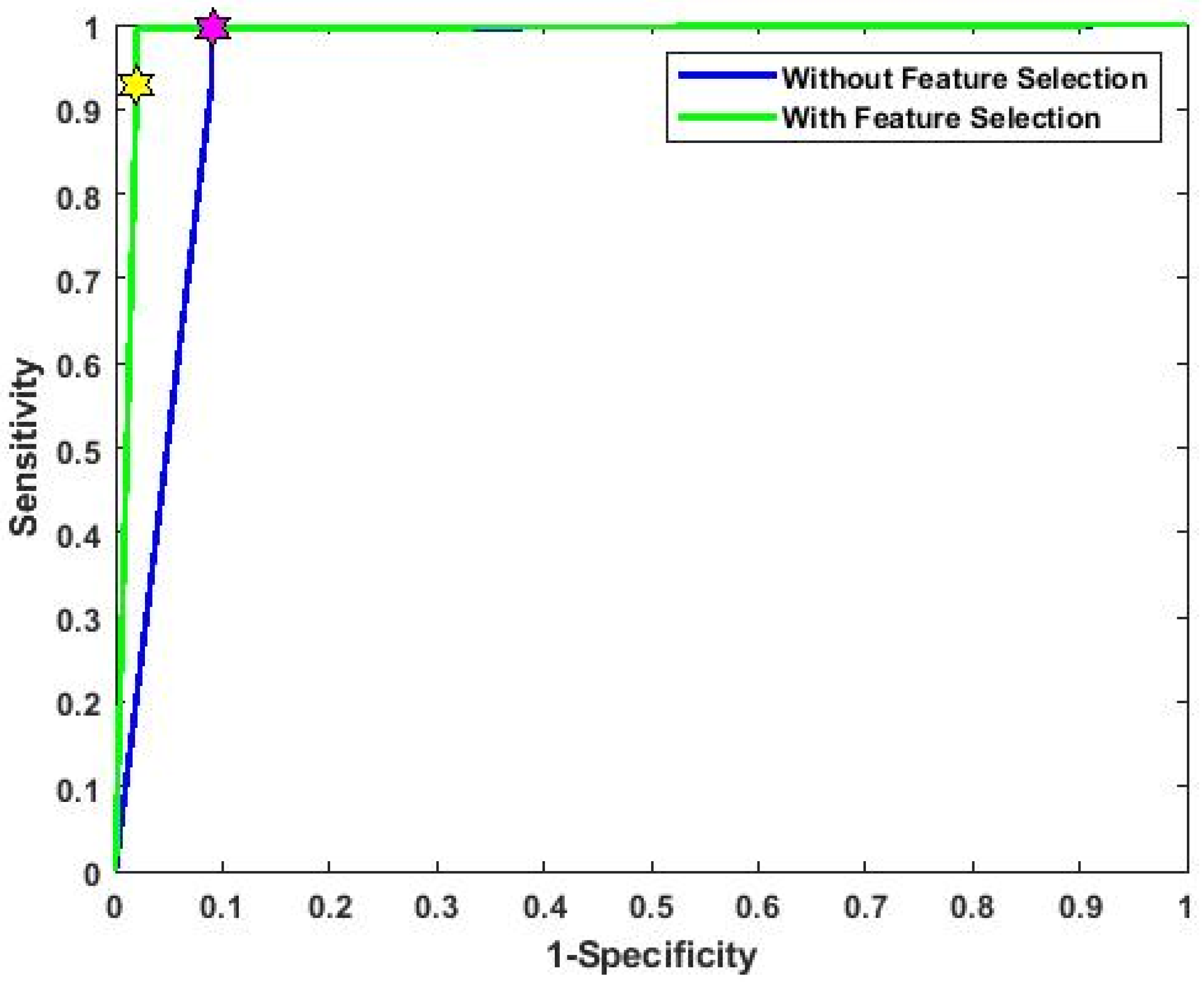
4.1. Statistical Analysis
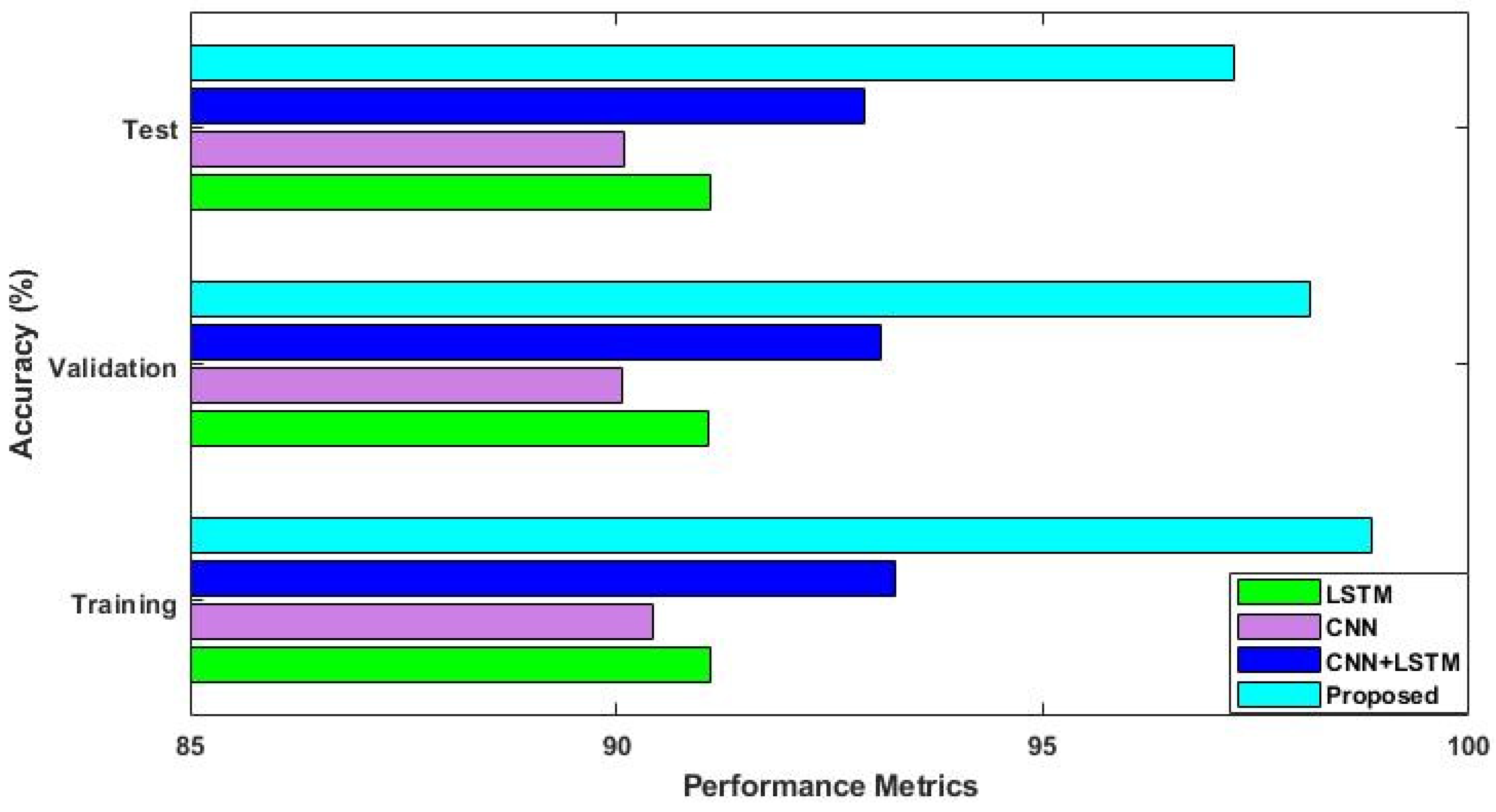
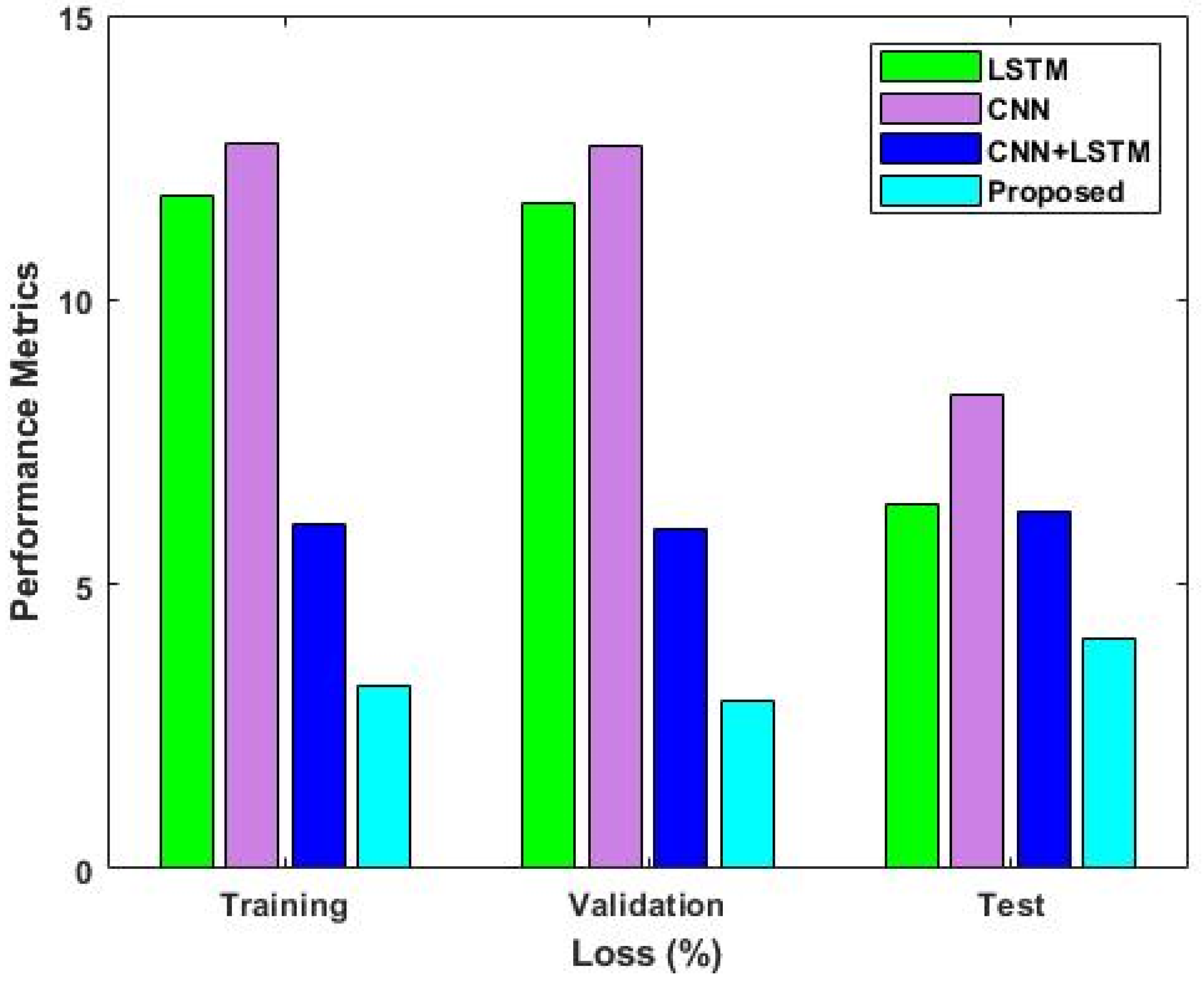
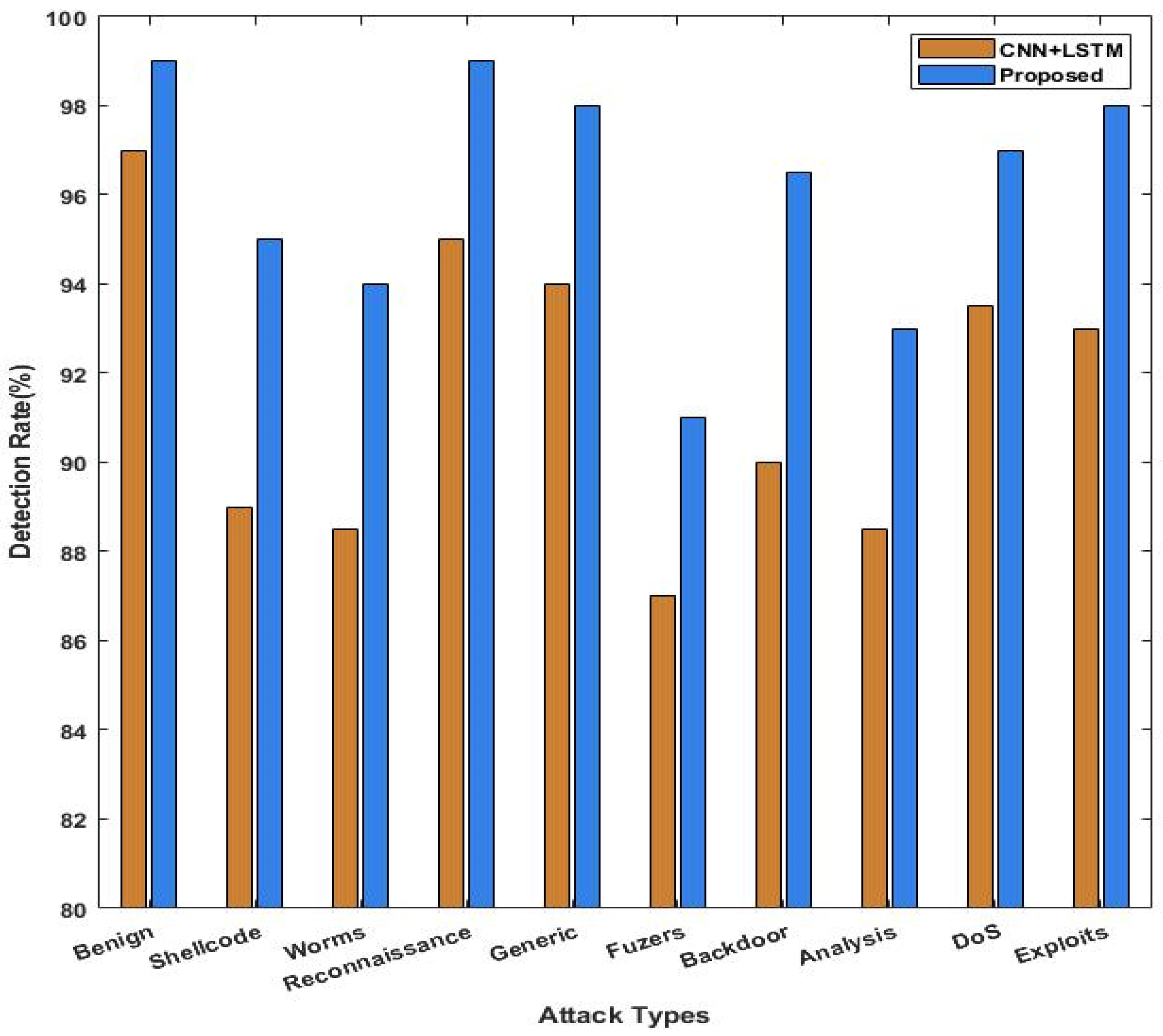
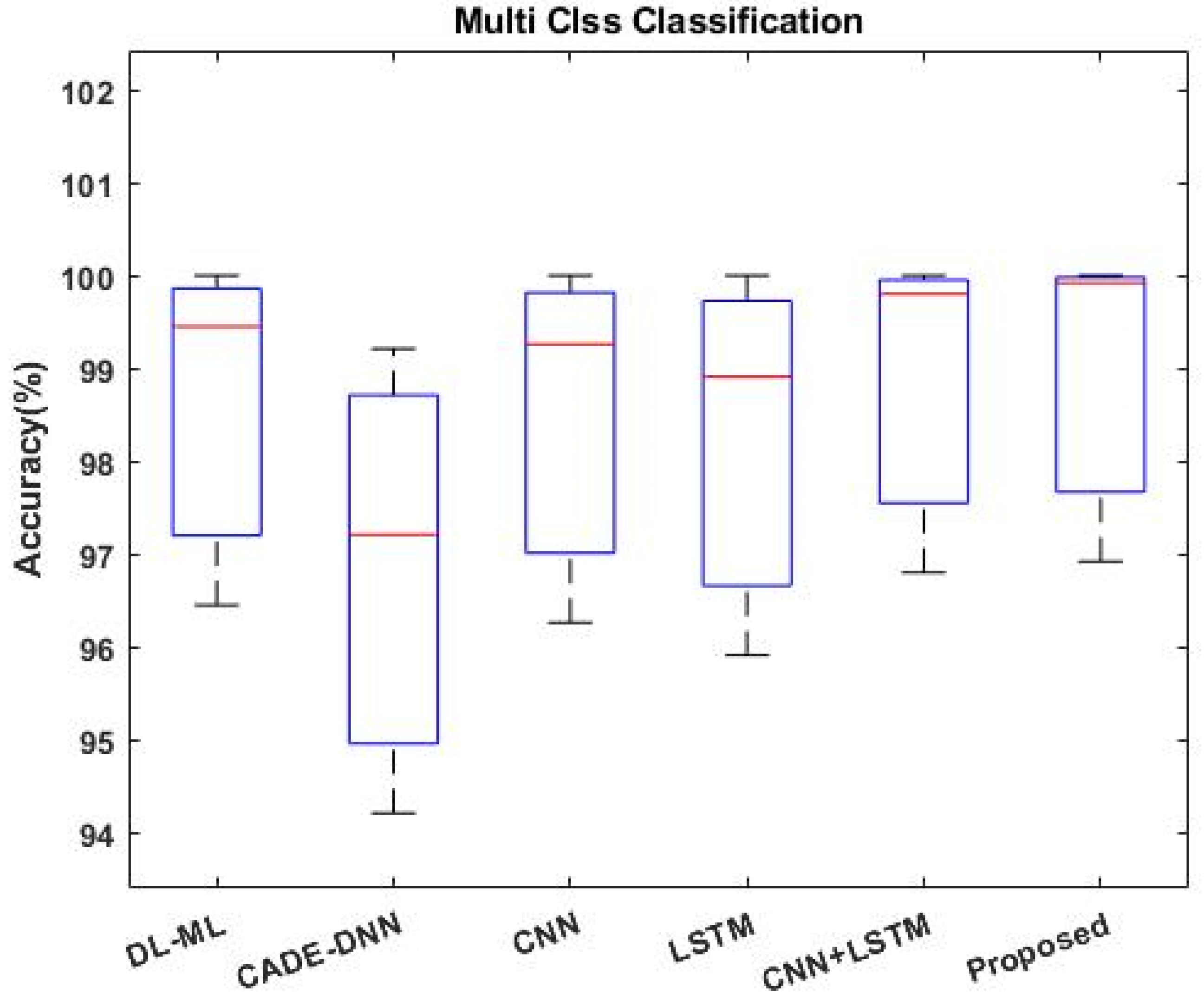
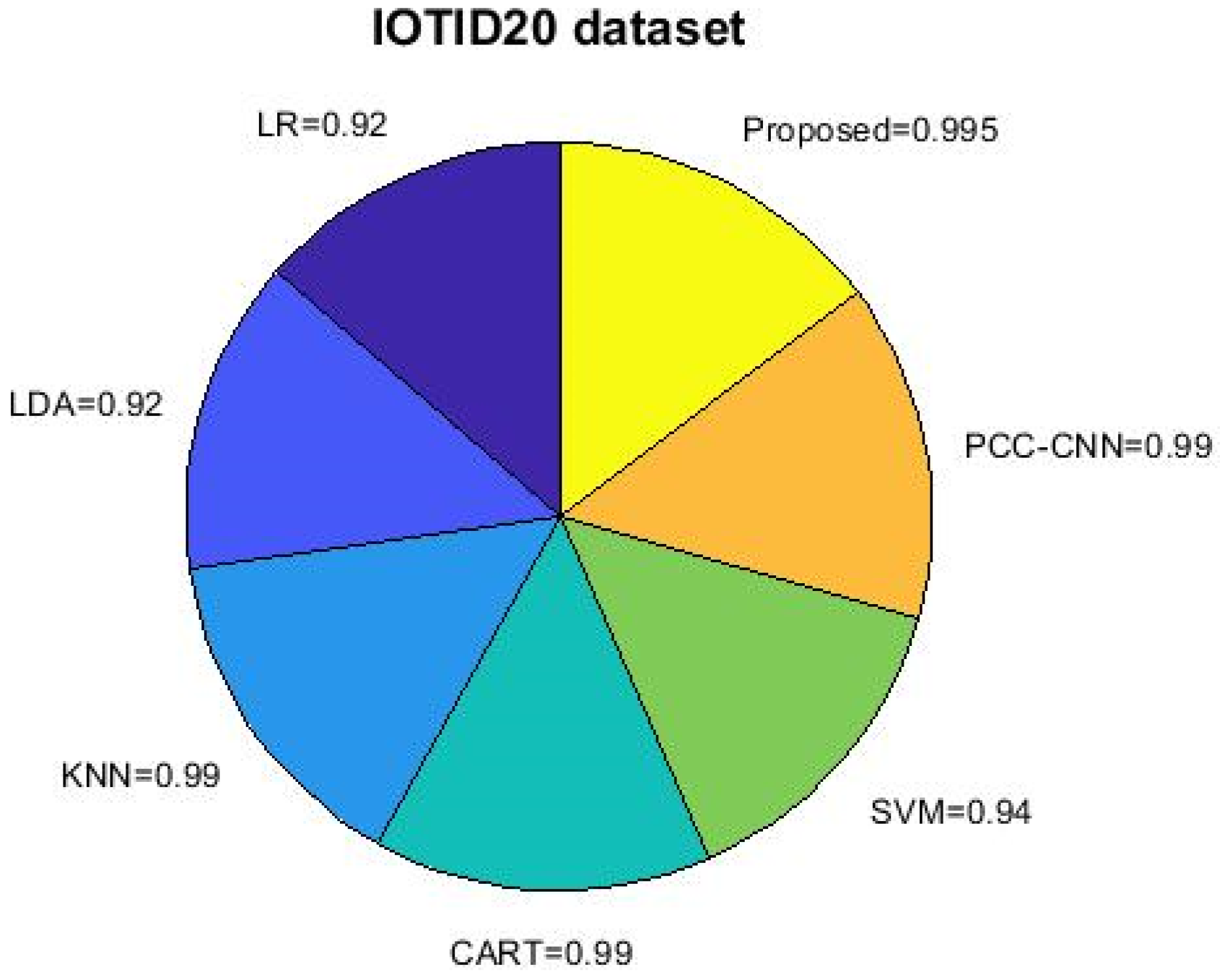
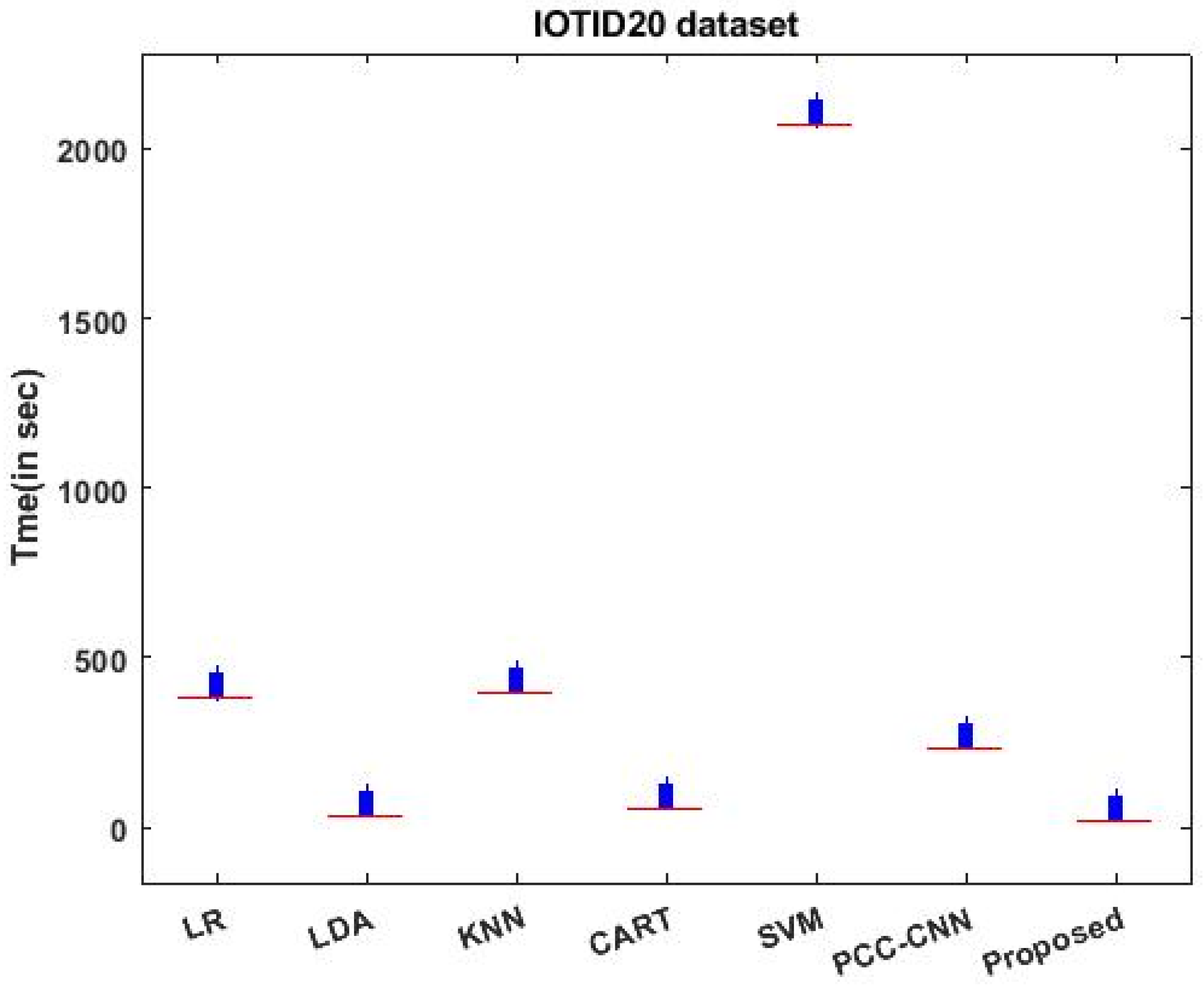
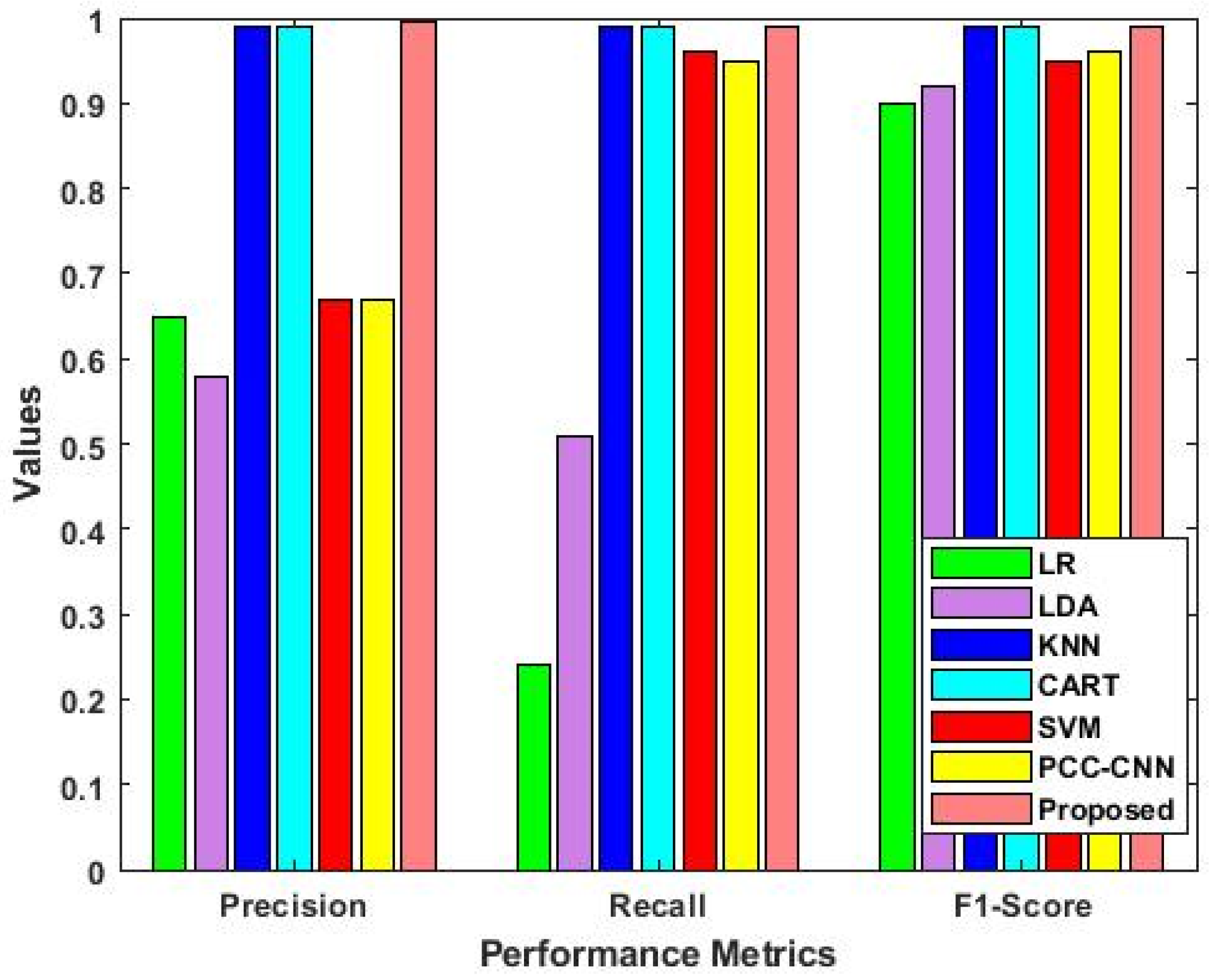
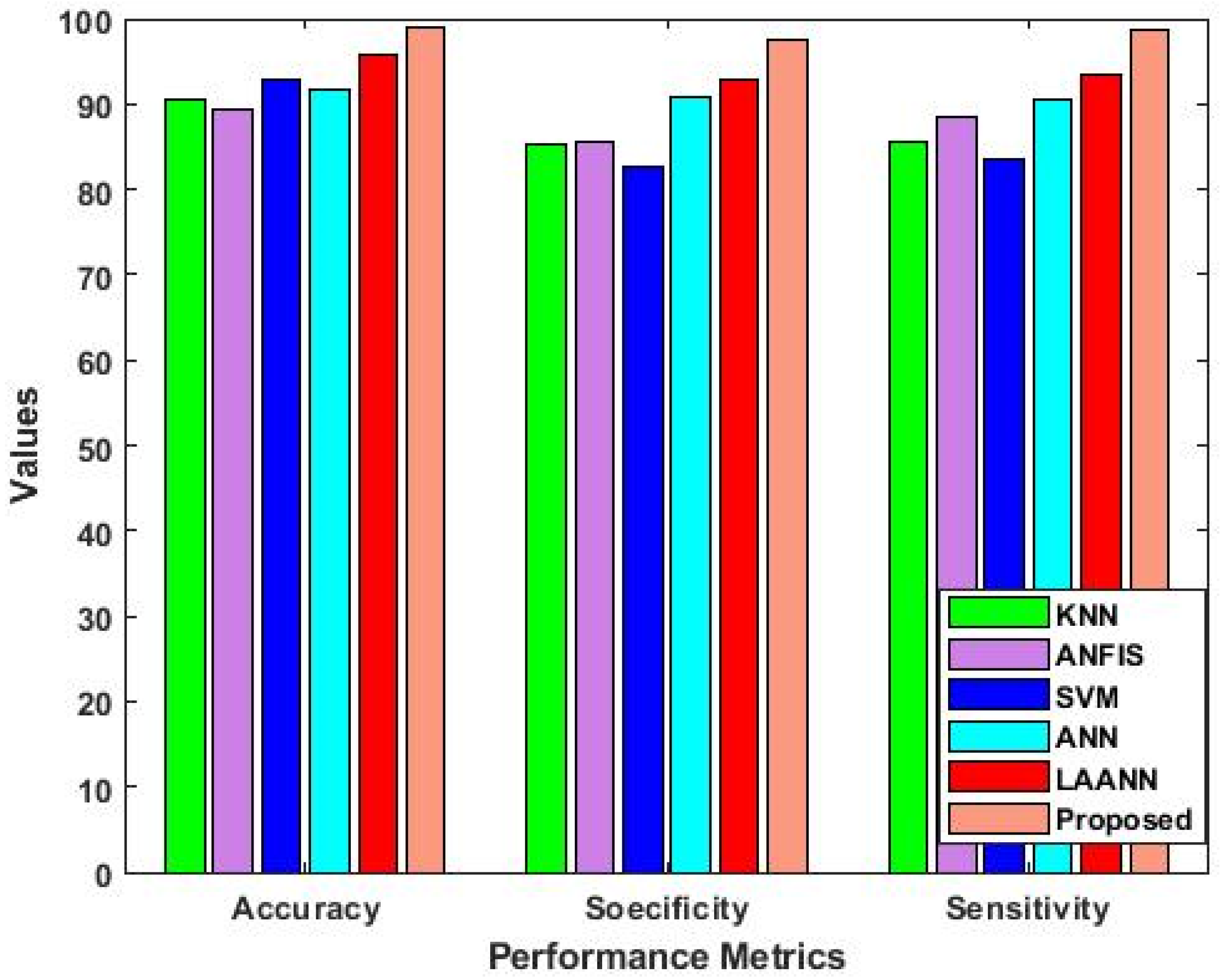
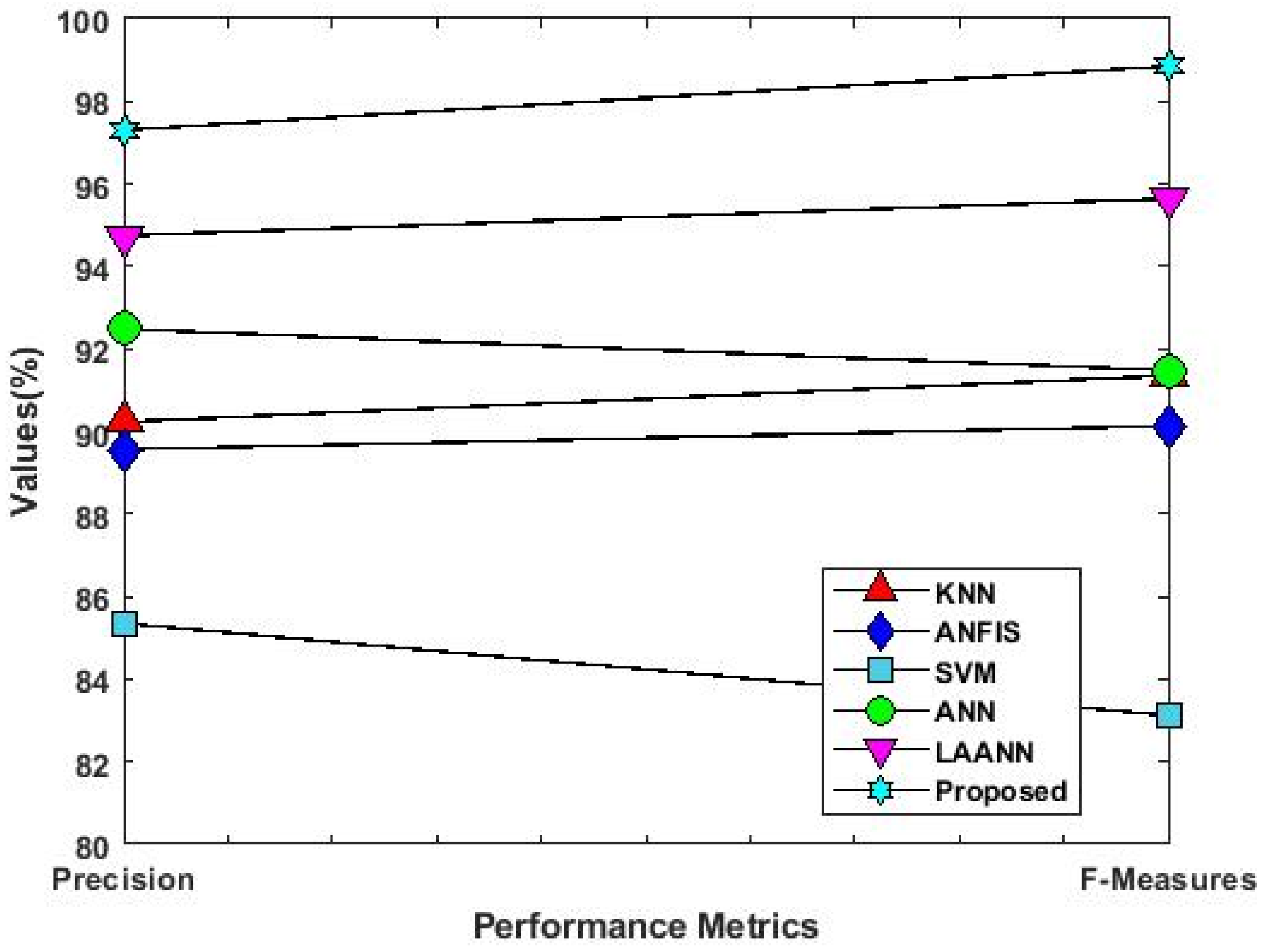
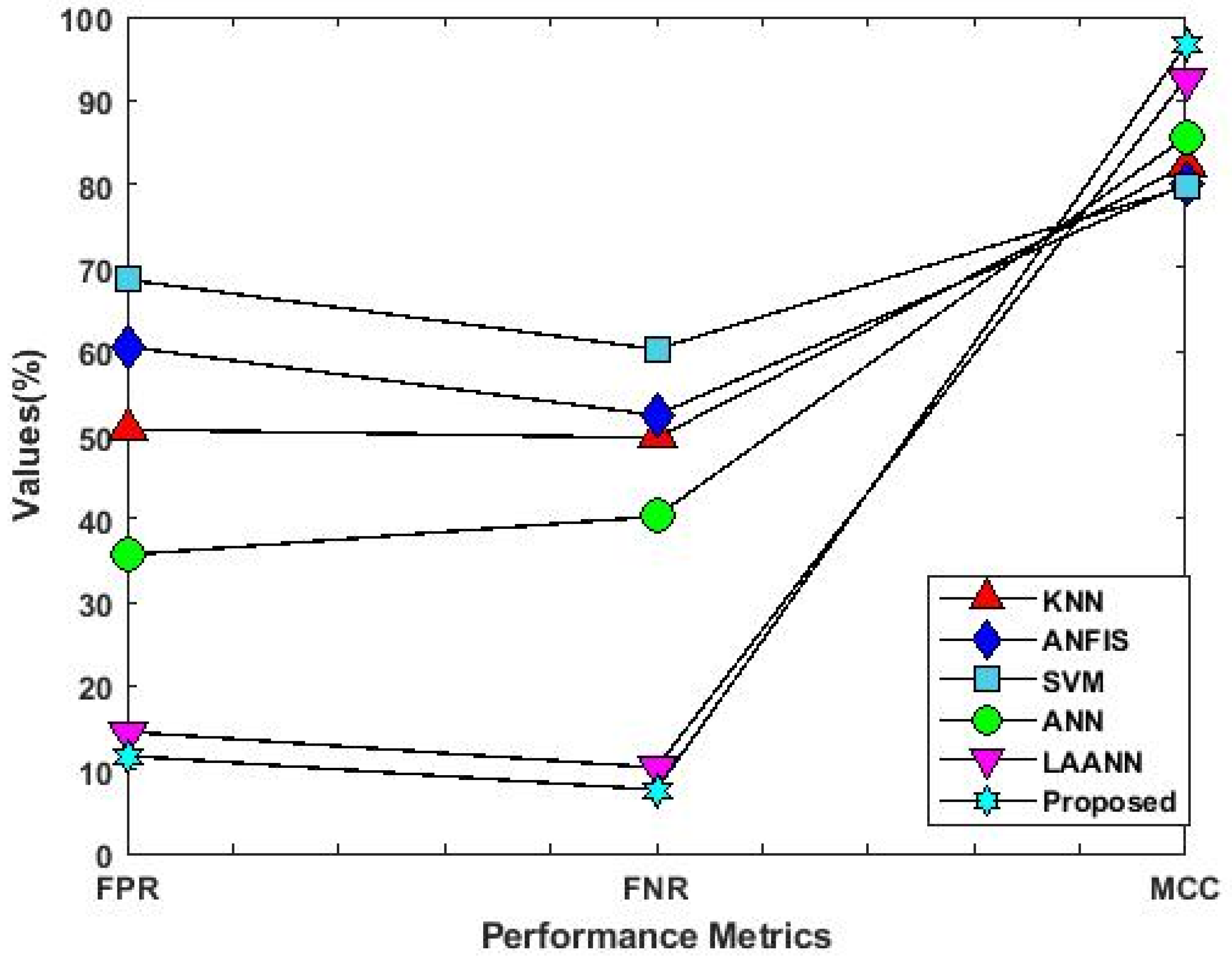
4.2. Results Analysis
5. Discussions
Significance of Proposed System
- VBQ-Net leverages the power of the Vector Space Bag of Words (VSBW) methodology to effectively reduce the dimensionality of features extracted from IoT data. This process allows the model to focus on key characteristics, improving its ability to detect intrusions accurately and efficiently;
- The novel Boosted Variance Quantization Neural Networks (BVQNN) classification technique employed in VBQ-Net enhances the accuracy of intrusion identification. By using a weighted feature matrix, the model can prioritize relevant features and classify different types of intrusions with higher precision;
- With the quantization technique integrated into the architecture, VBQ-Net optimizes computational complexity and memory requirements. This leads to reduced latency and processing time, making it suitable for real-time intrusion detection in resource-constrained IoT environments;
- The incorporation of the Multi-Hunting Reptile Search Optimization (MH-RSO) algorithm enables VBQ-Net to calculate probability values during intrusion categorization. This approach helps the model make more informed decisions, improving its ability to anticipate and respond to intrusions effectively;
- VBQ-Net is designed to work with a variety of datasets, including well-known and up-to-date ones such as IoTID-20, IoT-23, and CIDDS-001. Its adaptability makes it applicable to different IoT deployment scenarios, enhancing its generalizability;
- As an innovative security architecture, VBQ-Net strikes a balance between accuracy and efficiency. The quantization of network parameters reduces memory overhead and computational complexity, making it suitable for IoT devices with limited resources;
- By combining multiple advanced techniques, VBQ-Net provides a comprehensive security solution for protecting IoT networks. It addresses the primary shortcomings of current IoT security frameworks, such as inadequate intrusion detection and substantial latency, making it a promising defense mechanism against cyberattacks;
- The validation of VBQ-Net on popular and current IoT datasets demonstrates its effectiveness in real-world scenarios. Its performance in detecting intrusions and safeguarding IoT networks showcases its practical applicability in the field of IoT security.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Moustafa, N.; Koroniotis, N.; Keshk, M.; Zomaya, A.Y.; Tari, Z. Explainable Intrusion Detection for Cyber Defences in the Internet of Things: Opportunities and Solutions. IEEE Commun. Surv. Tutor. 2023, 1. [Google Scholar] [CrossRef]
- Tekin, N.; Acar, A.; Aris, A.; Uluagac, A.S.; Gungor, V.C. Energy consumption of on-device machine learning models for IoT intrusion detection. Internet Things 2023, 21, 100670. [Google Scholar] [CrossRef]
- Wu, J.; Dai, H.; Wang, Y.; Ye, K.; Xu, C. Heterogeneous Domain Adaptation for IoT Intrusion Detection: A Geometric Graph Alignment Approach. IEEE Internet Things J. 2023, 10, 10764–10777. [Google Scholar] [CrossRef]
- Musleh, D.; Alotaibi, M.; Alhaidari, F.; Rahman, A.; Mohammad, R.M. Intrusion Detection System Using Feature Extraction with Machine Learning Algorithms in IoT. J. Sens. Actuator Netw. 2023, 12, 29. [Google Scholar] [CrossRef]
- Chaganti, R.; Suliman, W.; Ravi, V.; Dua, A. Deep Learning Approach for SDN-Enabled Intrusion Detection System in IoT Networks. Information 2023, 14, 41. [Google Scholar] [CrossRef]
- Basati, A.; Faghih, M.M. APAE: An IoT intrusion detection system using asymmetric parallel auto-encoder. Neural Comput. Appl. 2023, 35, 4813–4833. [Google Scholar] [CrossRef]
- Abu Alghanam, O.; Almobaideen, W.; Saadeh, M.; Adwan, O. An improved PIO feature selection algorithm for IoT network intrusion detection system based on ensemble learning. Expert Syst. Appl. 2023, 213, 118745. [Google Scholar] [CrossRef]
- Namatherdhala, B.; Mazher, N.; Sriram, G.K. Artificial Intelligence trends in IoT Intrusion Detection System: A Systematic Mapping Review. Int. Res. J. Mod. Eng. Technol. Sci. 2022, 4, 59–69. [Google Scholar]
- Dina, A.S.; Siddique, A.; Manivannan, D. A deep learning approach for intrusion detection in Internet of Things using focal loss function. Internet Things 2023, 22, 100699. [Google Scholar] [CrossRef]
- Kumar, S.V.N.S.; Selvi, M.; Kannan, A. A Comprehensive Survey on Machine Learning-Based Intrusion Detection Systems for Secure Communication in Internet of Things. Comput. Intell. Neurosci. 2023, 2023, 8981988. [Google Scholar]
- Elnakib, O.; Shaaban, E.; Mahmoud, M.; Emara, K. EIDM: Deep learning model for IoT intrusion detection systems. J. Supercomput. 2023, 79, 13241–13261. [Google Scholar] [CrossRef]
- Arisdakessian, S.; Wahab, O.A.; Mourad, A.; Otrok, H.; Guizani, M. A survey on IoT intrusion detection: Federated learning, game theory, social psychology, and explainable AI as future directions. IEEE Internet Things J. 2022, 10, 4059–4092. [Google Scholar] [CrossRef]
- Mohamed, D.; Ismael, O. Enhancement of an IoT hybrid intrusion detection system based on fog-to-cloud computing. J. Cloud Comput. 2023, 12, 41. [Google Scholar] [CrossRef]
- Mohy-Eddine, M.; Guezzaz, A.; Benkirane, S.; Azrour, M. An efficient network intrusion detection model for IoT security using K-NN classifier and feature selection. Multimed. Tools Appl. 2023, 82, 23615–23633. [Google Scholar] [CrossRef]
- Kably, S.; Benbarrad, T.; Alaoui, N.; Arioua, M. Multi-Zone-Wise Blockchain Based Intrusion Detection and Prevention System for IoT Environment. Comput. Mater. Contin. 2023, 74, 253–278. [Google Scholar] [CrossRef]
- Sanju, P. Enhancing intrusion detection in IoT systems: A hybrid metaheuristics-deep learning approach with ensemble of recurrent neural networks. J. Eng. Res. 2023, 100122. [Google Scholar] [CrossRef]
- Shah, H.; Shah, D.; Jadav, N.K.; Gupta, R.; Tanwar, S.; Alfarraj, O.; Tolba, A.; Raboaca, M.S.; Marina, V. Deep Learning-Based Malicious Smart Contract and Intrusion Detection System for IoT Environment. Mathematics 2023, 11, 418. [Google Scholar] [CrossRef]
- Alweshah, M.; Hammouri, A.; Alkhalaileh, S.; Alzubi, O. Intrusion detection for the internet of things (IoT) based on the emperor penguin colony optimization algorithm. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 6349–6366. [Google Scholar] [CrossRef]
- Fadele, A.A.; Othman, M.; Hashem, I.A.T.; Yaqoob, I.; Imran, M.; Shoaib, M. A novel countermeasure technique for reactive jamming attack in internet of things. Multimed. Tools Appl. 2019, 78, 29899–29920. [Google Scholar] [CrossRef]
- Jia, Y.; Zhong, F.; Alrawais, A.; Gong, B.; Cheng, X. FlowGuard: An Intelligent Edge Defense Mechanism Against IoT DDoS Attacks. IEEE Internet Things J. 2020, 7, 9552–9562. [Google Scholar] [CrossRef]
- Vu, L.; Nguyen, Q.U.; Nguyen, D.N.; Hoang, D.T.; Dutkiewicz, E. Deep Transfer Learning for IoT Attack Detection. IEEE Access 2020, 8, 107335–107344. [Google Scholar] [CrossRef]
- Al-Othman, Z.; Alkasassbeh, M.; Baddar, S.A.-H. A state-of-the-art review on IoT botnet attack detection. arXiv 2020, arXiv:2010.13852. [Google Scholar]
- Hekmati, A.; Grippo, E.; Krishnamachari, B. Neural Networks for DDoS Attack Detection using an Enhanced Urban IoT Dataset. In Proceedings of the 2022 International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 25–28 July 2022; pp. 1–8. [Google Scholar]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. A Novel Ensemble of Hybrid Intrusion Detection System for Detecting Internet of Things Attacks. Electronics 2019, 8, 1210. [Google Scholar] [CrossRef]
- Qiu, H.; Dong, T.; Zhang, T.; Lu, J.; Memmi, G.; Qiu, M. Adversarial Attacks Against Network Intrusion Detection in IoT Systems. IEEE Internet Things J. 2020, 8, 10327–10335. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion detection systems in the Internet of things: A comprehensive investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks. Future Internet 2020, 12, 44. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. Performance Analysis of Intrusion Detection Systems Using a Feature Selection Method on the UNSW-NB15 Dataset. J. Big Data 2020, 7, 105. [Google Scholar] [CrossRef]
- Alshamkhany, M.; Alshamkhany, W.; Mansour, M.; Khan, M.; Dhou, S.; Aloul, F. Botnet attack detection using machine learning. In Proceedings of the 2020 14th International Conference on Innovations in Information Technology (IIT), Al Ain, United Arab Emirates, 17–18 November 2020; pp. 203–208. [Google Scholar]
- Alani, M.M.; Miri, A. Towards an Explainable Universal Feature Set for IoT Intrusion Detection. Sensors 2022, 22, 5690. [Google Scholar] [CrossRef] [PubMed]
- Hussein, A.Y.; Sadiq, A.T. Meerkat Clan-Based Feature Selection in Random Forest Algorithm for IoT Intrusion Detection. Iraqi J. Comput. Commun. Control Syst. Eng. 2022, 22, 15–24. [Google Scholar]
- Daoud, M.; Dahmani, Y.; Bendaoud, M.; Ouared, A.; Ahmed, H. Convolutional neural network-based high-precision and speed detection system on CIDDS-001. Data Knowl. Eng. 2023, 144, 102130. [Google Scholar] [CrossRef]
- Altunay, H.C.; Albayrak, Z. A hybrid CNN+ LSTMbased intrusion detection system for industrial IoT networks. Eng. Sci. Technol. Int. J. 2023, 38, 101322. [Google Scholar]
- Jeyaselvi, M.; Dhanaraj, R.K.; Sathya, M.; Memon, F.H.; Krishnasamy, L.; Dev, K.; Ziyue, W.; Qureshi, N.M.F. A highly secured intrusion detection system for IoT using EXPSO-STFA feature selection for LAANN to detect attacks. Clust. Comput. 2023, 26, 559–574. [Google Scholar] [CrossRef]
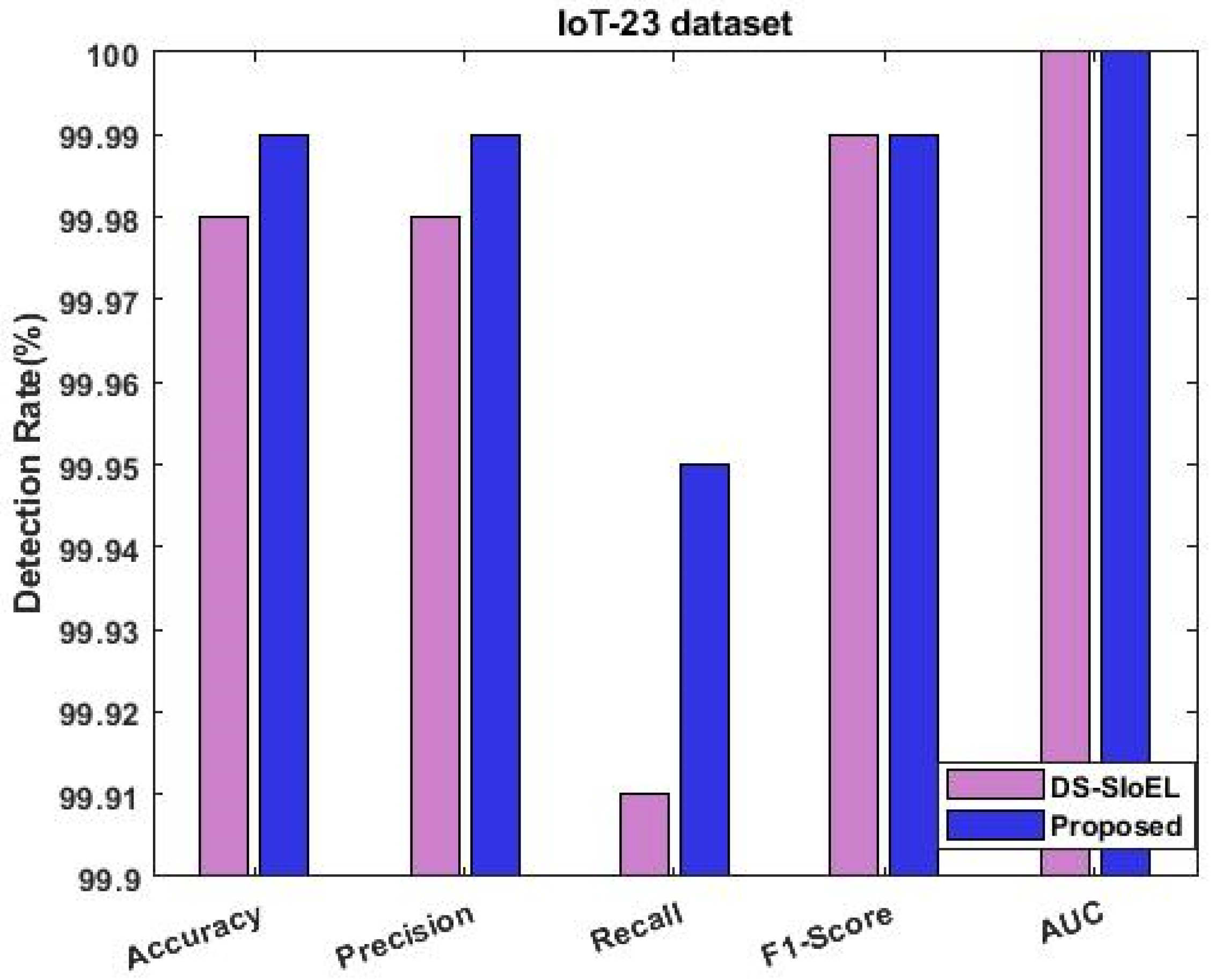
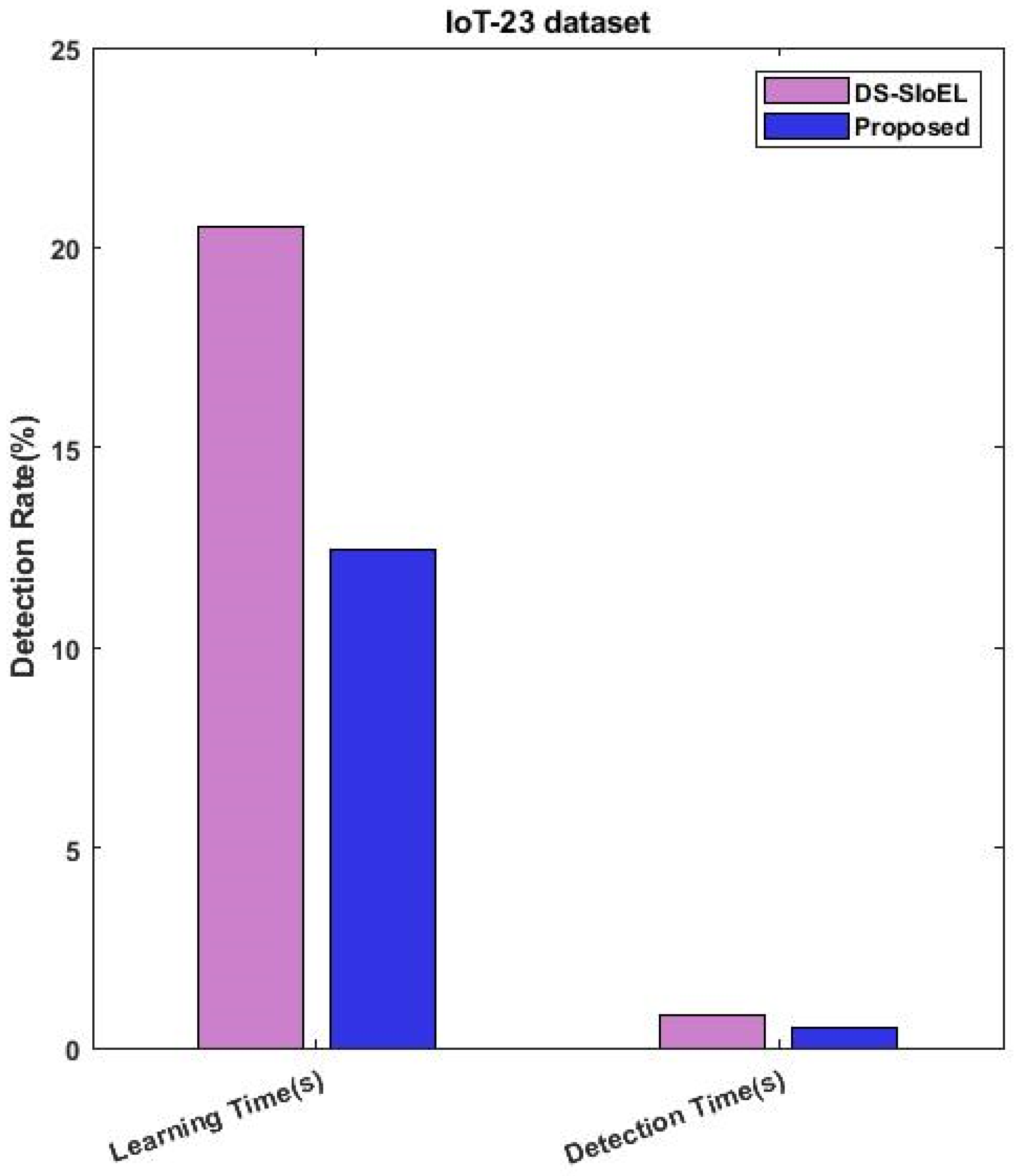
- Hazman, C.; Guezzaz, A.; Benkirane, S.; Azrour, M. lIDS-SIoEL: Intrusion detection framework for IoT-based smart environments security using ensemble learning. Clust. Comput. 2022, 1–15. [Google Scholar] [CrossRef]
- Gopalakrishnan, S.; Hemanand, D.; Arun, P.R.; Rajesh, A.; Deepika, K.; Chitra, T. Cluster Based Malicious Node Detection System for Mobile Ad-Hoc Network Using ANFIS Classifier. J. Appl. Secur. Res. 2023, 18, 402–420. [Google Scholar]
| Cited | Methodology | Limitations |
|---|---|---|
| Fadele et al. [19] | Implemented a countermeasure technique based on the consistency algorithm to detect jamming attacks in IoT. They focused on reliable and secure packet transmission. | Lack of information on the actual effectiveness in real IoT environments. |
| Jia et al. [20] | Introduced FlowGuard, a defense mechanism for protecting IoT networks from DDoS attacks. They aimed to detect different types of DDoS attacks in the network. | May not cover all possible DDoS attack variations. |
| Vu et al. [21] | Deployed a deep transfer learning technique using auto-encoders to spot attacks in IoT networks. However, the suggested model was time-consuming for detection. | The suggested model’s time-consuming nature affects detection efficacy. |
| AI-Othman et al. [22]: | Investigated state-of-the-art methodologies for detecting and classifying botnet attacks in the IoT. They highlighted the importance of accuracy as the primary performance metric for classification models. | Limited exploration of hybrid or signature-based detection methods. |
| Hekmati et al. [23]: | Compared four classification techniques (MLP, CNN, auto-encoder, LSTM) to improve IoT network security, with LSTM outperforming others. | Evaluation limited to specific classifiers, may not generalize to other datasets. |
| Khraisat et al. [24]: | Implemented an ensemble classification approach to detect intrusions in IoT networks, aiming for increased accuracy and a low false alarm rate. | May not provide insights into the performance of individual intrusion detection methods within the ensemble. |
| Qiu et al. [25]: | Introduced a Kitsune-based intrusion detection system using deep learning to categorize benign and malignant traffic in IoT networks. | Performance evaluation metrics used may not cover all aspects of attack detection. |
| Hajiheidari et al. [26]: | Presented a comprehensive analysis of different attack detection methodologies used in IoT systems. | Lack of quantitative results on the effectiveness of reviewed attack detection methodologies. |
| Ferrag et al. [27]: | Developed a rule-based decision tree classification mechanism to reduce false acceptance rate and improve detection rate for IoT networks. | Evaluation might not be performed on a diverse set of IoT attack scenarios. |
| Kasongo et al. [28]: | Designed a machine learning algorithm for detecting intrusions using the UNSW-NB 15 dataset. They compared various ML algorithms (SVM, DT, ANN, KNN, LR) and used PCA for dimensionality reduction. | Performance comparison limited to specific ML algorithms and dataset (UNSW-NB 15). |
| Proposed | Developed VBQ-Net, a security framework for IoT systems that uses VSBW to select essential data attributes and BVQNN for classification. MH-RSO algorithm optimizes probability values. Validated the framework using popular datasets like IoTID-20, IoT-23, and CIDDS-001. | It is necessary to keep VBQ-Net updated and improved to stay protected from new intrusion methods. |
| Machine Learning Method | Description | Advantages | Limitations |
|---|---|---|---|
| Consistency Algorithm | Detects jamming attacks in IoT networks. | Simple implementation. | May have limitations in handling more complex attack types. |
| Deep Transfer Learning | Utilizes auto-encoders for attack identification. | Can learn complex patterns in data. | Time-consuming for detection in some cases. |
| Hybrid IDS | Combines signature-based and behavioral detection. | Effective at detecting both known and unknown attacks. | Complexity in designing and integrating different methods. |
| Kitsune-based IDS | Categorizes benign and malignant traffic in IoT networks. | Effective in handling temporal statistics of data packets. | Performance may vary depending on the dataset and features. |
| Support Vector Machine | Divides data into distinct classes for intrusion detection. | Performs well in high-dimensional source fields. | Choosing the appropriate kernel function can be challenging. |
| Logistic Regression | Used for binary classification tasks. | Simple and interpretable. | Limited performance for complex multi-class problems. |
| K-Nearest Neighbors | Classifies data based on its proximity to neighbors. | Simple and easy to implement. | Computationally intensive for large datasets. |
| Principal Component Analysis (PCA) | Reduces dimensionality of the dataset. | Helps streamline the classification process. | Information loss due to dimensionality reduction. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Perumal, G.; Subburayalu, G.; Abbas, Q.; Naqi, S.M.; Qureshi, I. VBQ-Net: A Novel Vectorization-Based Boost Quantized Network Model for Maximizing the Security Level of IoT System to Prevent Intrusions. Systems 2023, 11, 436. https://doi.org/10.3390/systems11080436
Perumal G, Subburayalu G, Abbas Q, Naqi SM, Qureshi I. VBQ-Net: A Novel Vectorization-Based Boost Quantized Network Model for Maximizing the Security Level of IoT System to Prevent Intrusions. Systems. 2023; 11(8):436. https://doi.org/10.3390/systems11080436
Chicago/Turabian StylePerumal, Ganeshkumar, Gopalakrishnan Subburayalu, Qaisar Abbas, Syed Muhammad Naqi, and Imran Qureshi. 2023. "VBQ-Net: A Novel Vectorization-Based Boost Quantized Network Model for Maximizing the Security Level of IoT System to Prevent Intrusions" Systems 11, no. 8: 436. https://doi.org/10.3390/systems11080436
APA StylePerumal, G., Subburayalu, G., Abbas, Q., Naqi, S. M., & Qureshi, I. (2023). VBQ-Net: A Novel Vectorization-Based Boost Quantized Network Model for Maximizing the Security Level of IoT System to Prevent Intrusions. Systems, 11(8), 436. https://doi.org/10.3390/systems11080436










