Machine Learning-Assisted Cryptographic Security: A Novel ECC-ANN Framework for MQTT-Based IoT Device Communication
Abstract
1. Introduction
2. Design and Methodology
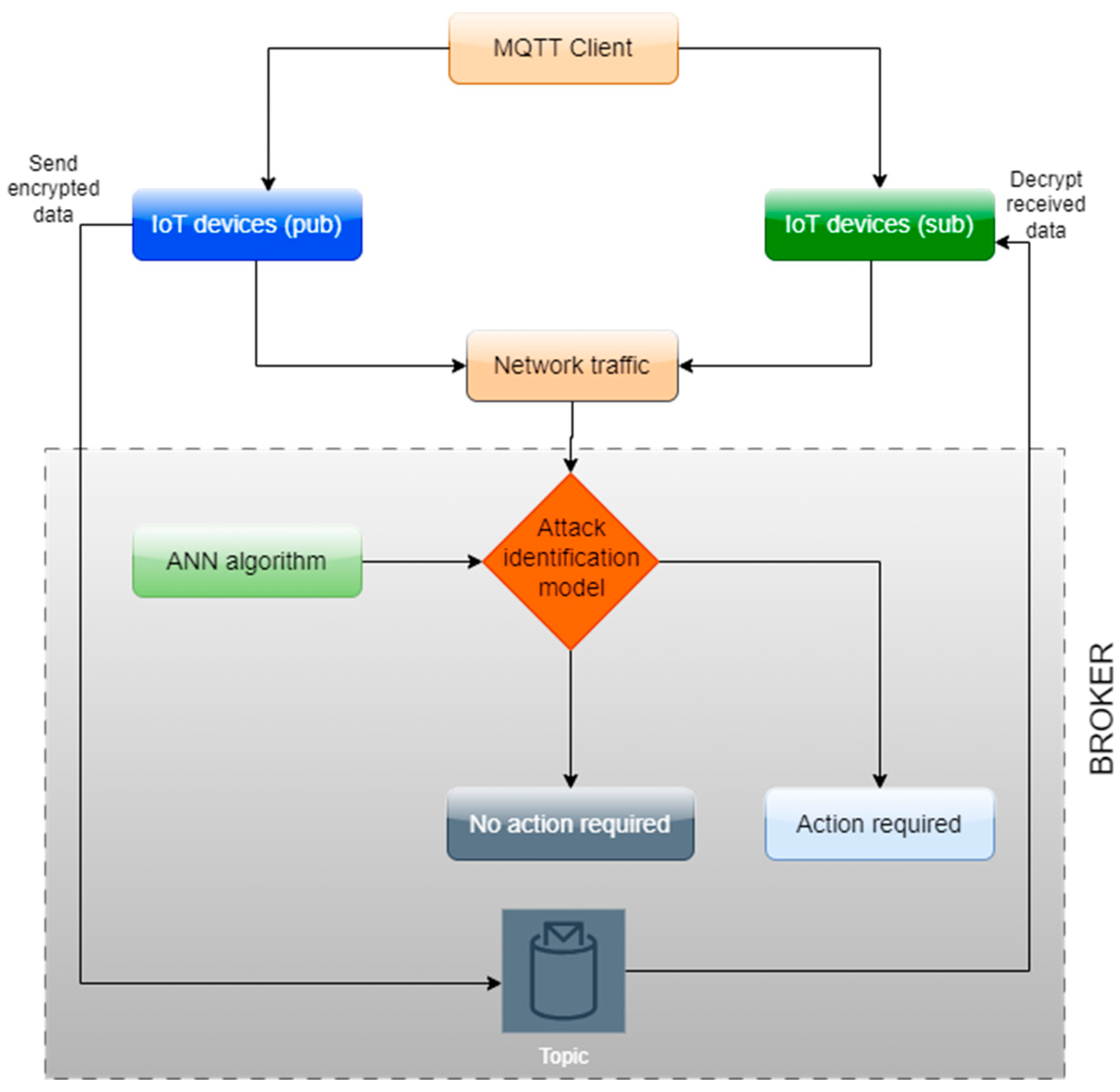
2.1. Overall System Description
2.2. Elliptic Curve and Key Exchange
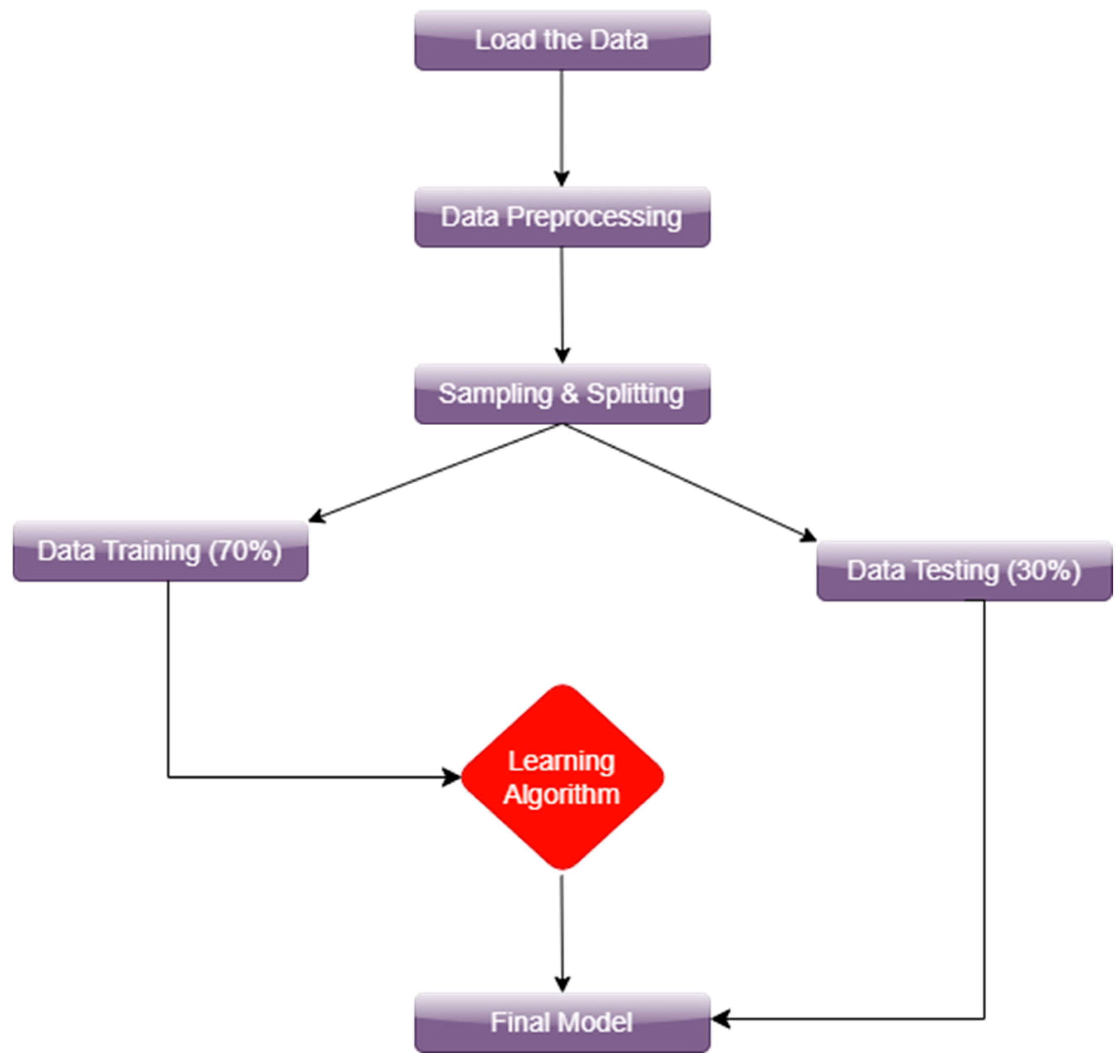
2.3. Machine Learning Algorithm
2.4. Dataset
2.5. Data Preprocessing
3. Implementation and Results
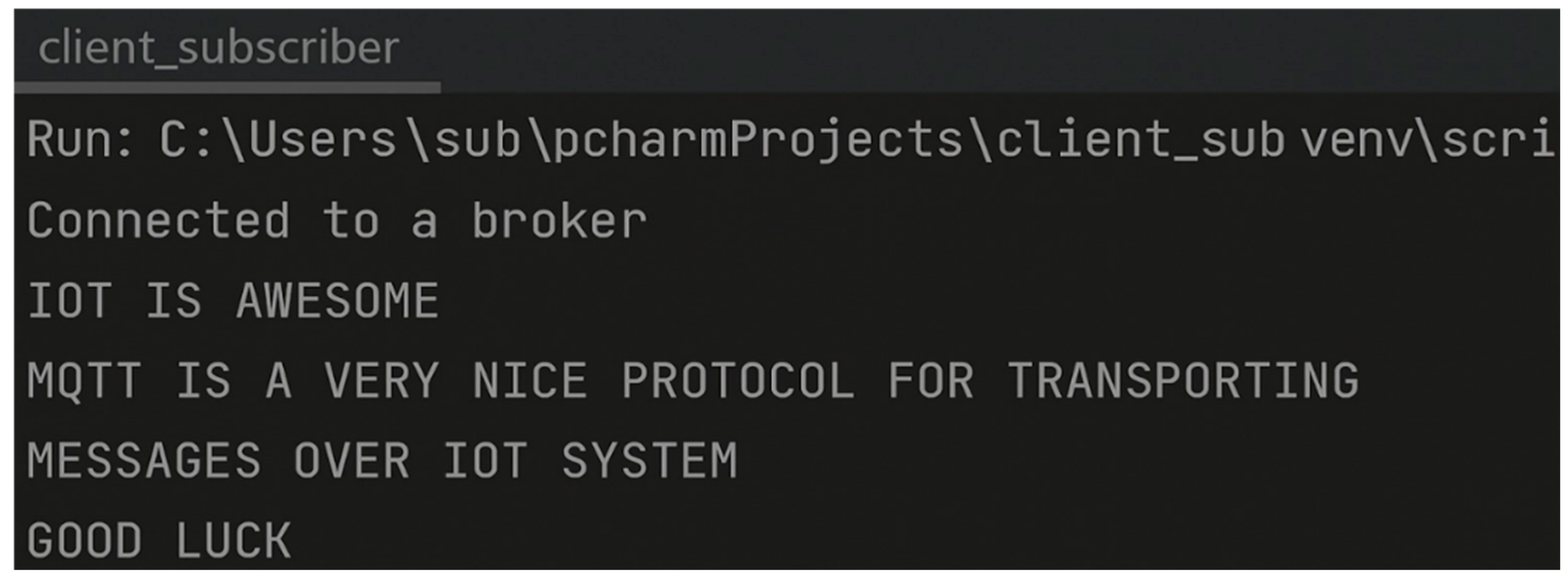
3.1. Implementation Details
- OMEN by HP Laptop
- 1 TB of Hard Disk and 512 GB of solid-state drive (SSD)
- Processor: Intel(R) Core (TM) i7-7700HQ CPU @ 2.80 GHz (8 CPUs)
- RAM: 16,384 MB
3.2. Results Discussion
4. Ann Model Evaluation
4.1. Performance Evaluation
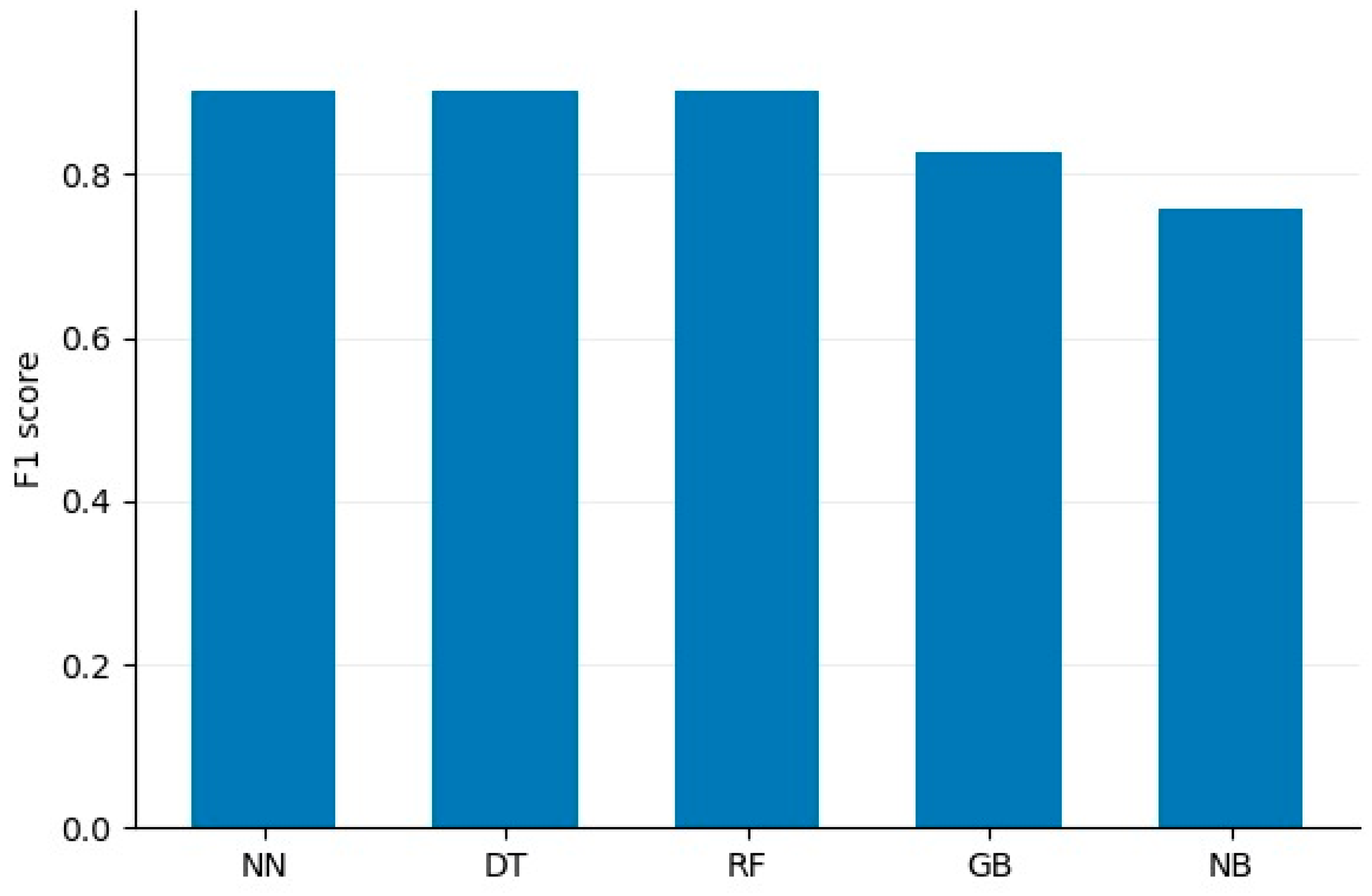
4.2. Results Comparison
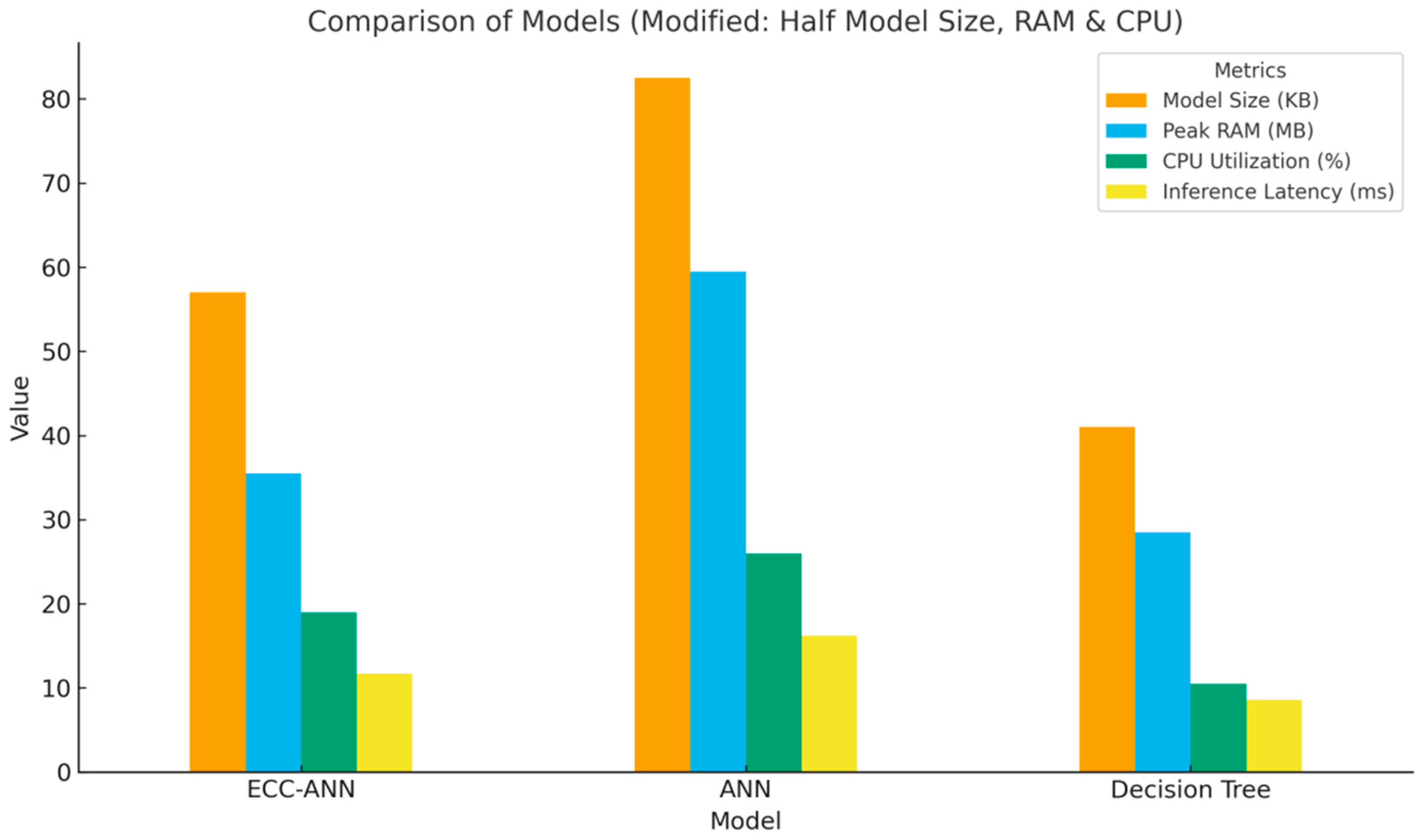
4.3. Computational and Memory Overhead Analysis
4.4. Length Key Comparison Between ECC and RSA
4.5. Novelty and Comparative Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| ANN | Artificial Neural Networks |
| CoAP | Constrained Access Protocol |
| CPU | Central Processing Unit |
| D2D | Device-to-device |
| DDS | Data Distribution Service |
| DLP | Discrete Logarithm Problem |
| DoS | Denial of Service |
| DT | Decision Tree |
| ECC | Elliptic Curve Cryptography |
| Fp | prime finite field |
| GB | Gradient Boost |
| IDE | Integrated Development Environment |
| IoD | Internet of Drones |
| IoT | Internet of Things |
| KMS | Key Management Service |
| LTS | Long Term Support |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| NV | Naïve Bayes |
| PCAP | Packet Capture |
| QoS | Quality of Service |
| RAM | Random Access Memory |
| RF | Random Forest |
| RSA | Rivest Shamir Adleman |
| SSL/TLS | Secure Sockets Layer/Transport Layer Security |
| SSD | Solid-state drive |
| UMA | User-Managed Access |
| vCPU | Virtual Central Processing Unit |
| VDP | Vulnerability Disclosure Policy |
| VMs | Virtual Machines |
References
- Ray, P.P. A Survey on Internet of Things Architectures. J. King Saud Univ.-Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef]
- Hussein, A.H. Internet of Things (IOT): Research Challenges and Future Applications. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Internet of Things: Security and Solutions Survey. Sensors 2022, 22, 7433. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 2012 10th International Conference on Frontiers of Information Technology, Islamabad, Pakistan, 17–19 December 2012; pp. 257–260. [Google Scholar]
- Andy, S.; Rahardjo, B.; Hanindhito, B. Attack Scenarios and Security Analysis of MQTT Communication Protocol in IoT System. In Proceedings of the 2017 4th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Yogyakarta, Indonesia, 19–21 September 2017; pp. 1–6. [Google Scholar]
- IoT Security Foundation. The State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2024. 2024. Available online: https://iotsecurityfoundation.org/wp-content/uploads/2024/11/The-State-of-Vulnerability-Disclosure-Usage-in-Global-Consumer-IoT-in-2024.pdf (accessed on 25 March 2025).
- Palo Alto Networks. 2020 Unit 42 IoT Threat Report. 2020. Available online: https://unit42.paloaltonetworks.com/iot-threat-report-2020/ (accessed on 25 March 2025).
- Naik, N. Choice of Effective Messaging Protocols for IoT Systems: MQTT, CoAP, AMQP and HTTP. In Proceedings of the 2017 IEEE International Systems Engineering Symposium (ISSE), Vienna, Austria, 11–13 October 2017; pp. 1–7. [Google Scholar]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A Survey on the Security of IoT Frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhry, S.A.; Alomari, O.A.; Alsharif, M.H.; Khan, M.K.; Kumar, N. Amassing the Security: An ECC-Based Authentication Scheme for Internet of Drones. IEEE Syst. J. 2021, 15, 4431–4438. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT Security: Review, Blockchain Solutions, and Open Challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Gharat, N.N.; Jolly, L. Hybrid Lightweight Cryptography Using AES and ECC for IoT Security. In Proceedings of the Cyber Security and Digital Forensics; Roy, N.R., Tanwar, S., Batra, U., Eds.; Springer Nature: Singapore, 2024; pp. 241–258. [Google Scholar]
- Aloufi, K.; Alhazmi, O. A Hybrid IoT Security Model of MQTT and UMA. Commun. Netw. 2020, 12, 155–173. [Google Scholar] [CrossRef]
- Aouedi, O.; Vu, T.-H.; Sacco, A.; Nguyen, D.C.; Piamrat, K.; Marchetto, G.; Pham, Q.-V. A Survey on Intelligent Internet of Things: Applications, Security, Privacy, and Future Directions. IEEE Commun. Surv. Tutor. 2025, 27, 1238–1292. [Google Scholar] [CrossRef]
- Szymoniak, S.; Kesar, S. Key Agreement and Authentication Protocols in the Internet of Things: A Survey. Appl. Sci. 2023, 13, 404. [Google Scholar] [CrossRef]
- Seoane, V.; Garcia-Rubio, C.; Almenares, F.; Campo, C. Performance Evaluation of CoAP and MQTT with Security Support for IoT Environments. Comput. Netw. 2021, 197, 108338. [Google Scholar] [CrossRef]
- Al-Ani, A.; Shen, W.K.; Al-Ani, A.K.; Laghari, S.A.; Elejla, O.E. Evaluating Security of MQTT Protocol in Internet of Things. In Proceedings of the 2023 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Regina, SK, Canada, 24–27 September 2023; pp. 502–509. [Google Scholar]
- Sarker, I.H. Machine Learning: Algorithms, Real-World Applications and Research Directions. SN Comput. Sci. 2021, 2, 160. [Google Scholar] [CrossRef] [PubMed]
- Mohamed, N. Artificial Intelligence and Machine Learning in Cybersecurity: A Deep Dive into State-of-the-Art Techniques and Future Paradigms. Knowl. Inf. Syst. 2025, 67, 6969–7055. [Google Scholar] [CrossRef]
- Samara, G.; Aljaidi, M.; Alazaidah, R.; Qasem, M.H.; Hassan, M.; Al-Milli, N.; Al-Batah, M.S.; Kanan, M. A Comprehensive Review of Machine Learning-Based Intrusion Detection Techniques for IoT Networks. In Artificial Intelligence, Internet of Things, and Society 5.0; Hannoon, A., Mahmood, A., Eds.; Springer Nature: Cham, Switzerland, 2023; pp. 465–473. ISBN 978-3-031-43300-9. [Google Scholar]
- Sharma, S. Classification and Regression Trees: The Use and Significance of Trees in Analytics. J. Recent Innov. Cloud Comput. Virtualiz. Web Appl. 2022, 5, 1–2021. [Google Scholar]
- Talekar, B. A Detailed Review on Decision Tree and Random Forest. Biosci. Biotechnol. Res. Commun. 2020, 13, 245–248. [Google Scholar] [CrossRef]
- Sreekumar, A.; Renuka Devi, S.M. Predicting Online Customer Purchase Using Gradient Boost Classifier. Int. J. Res. Appl. Sci. Eng. Technol. 2023, 11, 3787–3791. [Google Scholar] [CrossRef]
- Yudistira, A.S.; Nugroho, A. Prediction of the English Premier League Champion Team for the 2021/2022 Season Using the Naïve Bayes Method. J. Tek. Inform. (Jutif) 2022, 3, 1239–1243. [Google Scholar] [CrossRef]
- Yu, J.; Yang, L.; Xu, N.; Yang, J.; Huang, T.S. Slimmable Neural Networks. arXiv 2018, arXiv:1812.08928. [Google Scholar] [CrossRef]
- Pradipta, M.I.; Situmorang, Z.; Sembiring, R.W. Multilayer Perceptron Performance Analysis in Liver Disease Classification. SinkrOn 2024, 8, 426–434. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. MQTTset, a New Dataset for Machine Learning Techniques on MQTT. Sensors 2020, 20, 6578. [Google Scholar] [CrossRef]
- Mahto, D.; Yadav, D. RSA and ECC: A Comparative Analysis. Int. J. Appl. Eng. Res. 2017, 12, 9053–9061. [Google Scholar]







| Number | Hyperparameters | Settings |
|---|---|---|
| 0 | Input layer | 33 |
| 1 | Hidden layer | 3 |
| 2 | Hidden neurons | 100 (50, 30, 20) |
| 3 | Output layer | 6 |
| 4 | Batch size | 256 |
| 5 | Epochs | 50 |
| 6 | Lost function | Sparse_categorical_crossentropy |
| 7 | Activation function in the hidden layer | ReLu |
| 8 | Activation function in the output layer | Softmax |
| 9 | Learning rate | 0.001 |
| 10 | Optimizer | Adam |
| Legitimate | Dos | Bruteforce | Malformed | SlowITE | Flood | |
|---|---|---|---|---|---|---|
| legitimate | 3807 | 473 | 0 | 19 | 52 | 0 |
| Dos | 282 | 35,084 | 0 | 3650 | 60 | 1 |
| bruteforce | 2 | 4 | 89 | 89 | 0 | 0 |
| malformed | 49 | 2818 | 0 | 46,756 | 14 | 2 |
| SlowITE | 1490 | 246 | 0 | 297 | 1245 | 0 |
| flood | 0 | 1 | 0 | 0 | 0 | 2760 |
| Precision | Recall | F1-Score | Support | |
|---|---|---|---|---|
| brute force | 0.68 | 0.87 | 0.76 | 4351 |
| DoS | 0.91 | 0.90 | 0.90 | 39,077 |
| Flood | 1.00 | 0.48 | 0.65 | 184 |
| Legitimate | 0.92 | 0.94 | 0.93 | 49,639 |
| Malformed | 0.91 | 0.38 | 0.54 | 3278 |
| SlowITe | 1.00 | 1.00 | 1.00 | 2761 |
| accuracy | 0.90 | 99,290 | ||
| Macro avg | 0.90 | 0.76 | 0.80 | 99,290 |
| Weighted avg | 0.91 | 0.90 | 0.90 | 99,290 |
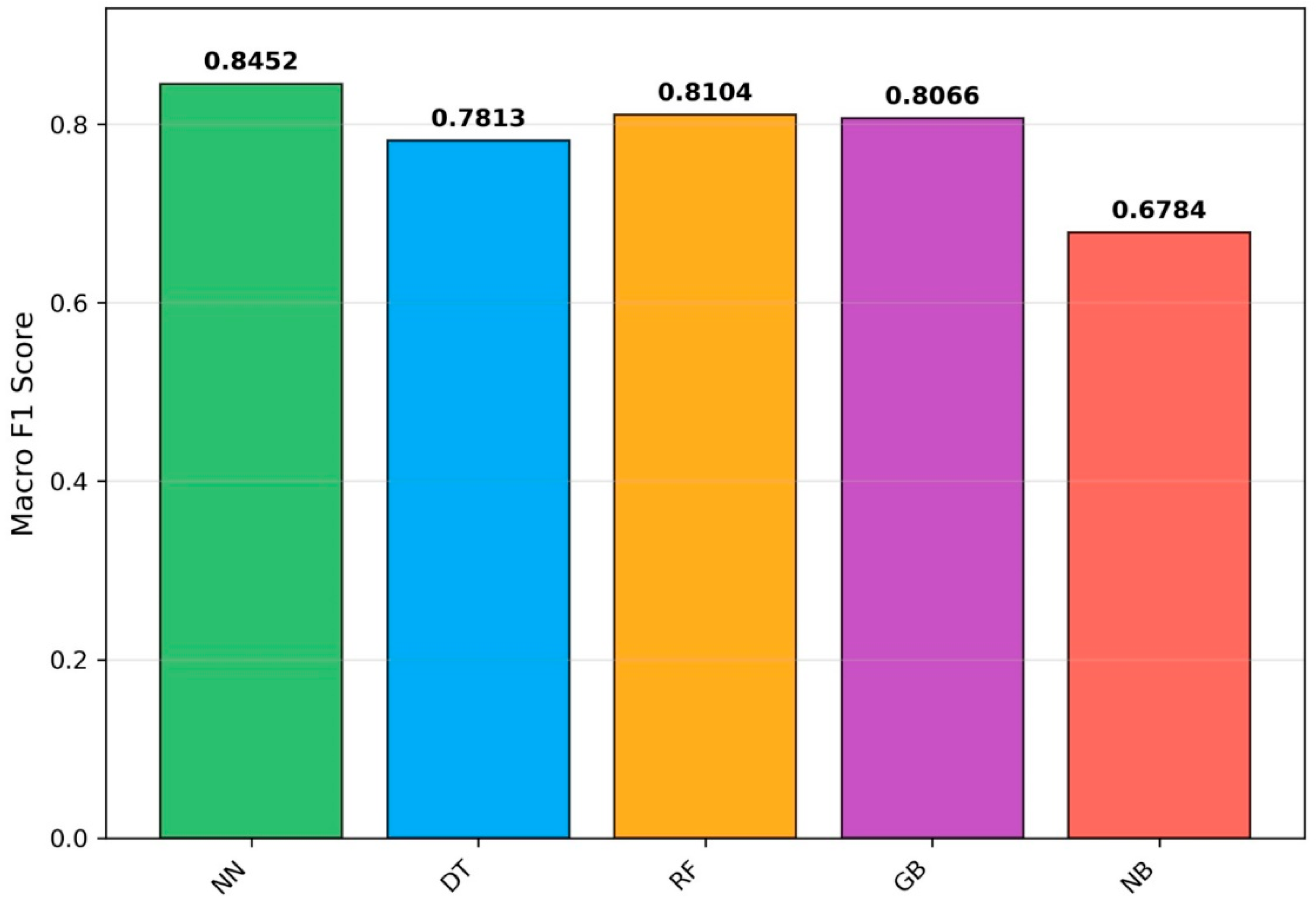
| Algorithms | Accuracy | F1 Score | Macro F1 Score |
|---|---|---|---|
| Neural Network | 0.9038271729277872 | 0.9009158054232087 | 0.8452 |
| Decision Tree | 0.9031322388961628 | 0.9009088402539802 | 0.7813 |
| Random forest | 0.9029308087420687 | 0.9009131314572056 | 0.8104 |
| Gradient Boost | 0.7931513747608017 | 0.8268049294767623 | 0.8066 |
| Naïve Bayes | 0.670863128210293 | 0.7581608917548786 | 0.6784 |
| Model | Mean Accuracy (%) | Standard Deviation | 95%CI (±) | p-Value (Paired t-Test) |
|---|---|---|---|---|
| ANN | 90.42 | 0.05 | ±0.03 | 0.012 |
| DT | 90.29 | 0.06 | ±0.04 |
| Security Level (bits) | ECC Key Length (bits) | RSA Key Length (bits) |
|---|---|---|
| 256 | 512 | 15,360 |
| 192 | 384 | 7680 |
| 128 | 256 | 3072 |
| 112 | 224 | 2048 |
| 80 | 160 | 1024 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Karimunda, K.; Ufitikirezi, J.d.D.M.; Bumbálek, R.; Zoubek, T.; Bartoš, P.; Kuneš, R.; Umurungi, S.N.; Chukwunyere, A.; Norbelt, M.; Bo, G. Machine Learning-Assisted Cryptographic Security: A Novel ECC-ANN Framework for MQTT-Based IoT Device Communication. Computation 2025, 13, 227. https://doi.org/10.3390/computation13100227
Karimunda K, Ufitikirezi JdDM, Bumbálek R, Zoubek T, Bartoš P, Kuneš R, Umurungi SN, Chukwunyere A, Norbelt M, Bo G. Machine Learning-Assisted Cryptographic Security: A Novel ECC-ANN Framework for MQTT-Based IoT Device Communication. Computation. 2025; 13(10):227. https://doi.org/10.3390/computation13100227
Chicago/Turabian StyleKarimunda, Kalimu, Jean de Dieu Marcel Ufitikirezi, Roman Bumbálek, Tomáš Zoubek, Petr Bartoš, Radim Kuneš, Sandra Nicole Umurungi, Anozie Chukwunyere, Mutagisha Norbelt, and Gao Bo. 2025. "Machine Learning-Assisted Cryptographic Security: A Novel ECC-ANN Framework for MQTT-Based IoT Device Communication" Computation 13, no. 10: 227. https://doi.org/10.3390/computation13100227
APA StyleKarimunda, K., Ufitikirezi, J. d. D. M., Bumbálek, R., Zoubek, T., Bartoš, P., Kuneš, R., Umurungi, S. N., Chukwunyere, A., Norbelt, M., & Bo, G. (2025). Machine Learning-Assisted Cryptographic Security: A Novel ECC-ANN Framework for MQTT-Based IoT Device Communication. Computation, 13(10), 227. https://doi.org/10.3390/computation13100227










