Fuzzy Signature from Computational Diffie–Hellman Assumption in the Standard Model
Abstract
1. Introduction
1.1. Digital Signature and Fuzzy Signature
1.2. Our Contributions
- –
- First, we redefine the notion of fuzzy signature and propose a new security model, which we call -existential unforgeability under chosen-message attack (), for fuzzy signatures. Compared with previous work [18], this new definition eliminates the requirement for the signing algorithm to take a verification key as input, thereby reducing the burden on users to maintain the verification key. Furthermore, our new security model is stronger than the one proposed by Matsuda et al. [12], because our security model allows the adversary to determine the differences between different biometric samples.
- –
- We formally define the error-recoverable property of the secure sketch and show that the syndrome-based secure sketch possesses the error recoverable property. We redefine the homomorphic property and define the key-shift* security of the signature scheme. In our key-shift* security model, the adversary can modify not only the signing key , but also the verification key . We also prove that the Waters signature scheme is homomorphic and key-shift* secure.
- –
- We present a generic construction of a fuzzy signature scheme, built upon three core primitives: a homomorphic secure sketch () with error recovery, a homomorphic average-case strong extractor (), and a homomorphic signature scheme () satisfying key-shift security.
- –
- Instantiating these primitives yields a fuzzy signature scheme that achieves security under the Computational Diffie–Hellman (CDH) assumption in the standard model over bilinear groups, and, notably, does not require the verification key as input to the signing algorithm.
1.3. Our Approach
2. Preliminaries
2.1. Metric Spaces
- (i)
- if, and only if, ;
- (ii)
- (symmetry);
- (iii)
- (triangle inequality).
2.2. Min-Entropy and Statistical Distance
2.3. Computational Diffie–Hellman (CDH) Assumption
2.4. Secure Sketch and Average-Case Strong Extractor
- –
- on input , outputs a sketch .
- –
- on input and a sketch , outputs a recovered value .
- –
- When , then .
- –
- For any distribution W over , if , .
2.5. Signature Scheme
- : On input the security parameter λ, outputs public parameters .
- : On input , generates a key pair consisting of a verification key and a signing key .
- : On input , , and a message , outputs a signature σ.
- : On input , , m, and σ, outputs a bit indicating whether the signature is valid (1) or invalid (0).
- 1.
- The challenger runs , generates , initializes an empty query set , and sends and to the adversary .
- 2.
- Throughout the experiment, may adaptively query a signing oracle:
- submits a message to .
- computes , adds to , and returns to .
- 3.
- Finally, outputs a forgery . The experiment outputs 1 if, and only if,Otherwise, it outputs 0.
- 1.
- For all , the signing key space constitutes an abelian group .
- 2.
- For all , there exists a deterministic and efficient algorithm such thatwhere , .
- 3.
- Suppose the random space of the signing algorithm is . For all , and , there exists a deterministic and efficient algorithm such thatwhere , .
- 1.
- The first difference lies in the inputs required by the algorithm . In our definition, takes as input and generates a valid signature of m under the signing key . However, in [8], the algorithm additionally requires as part of its input.
- 2.
- The second difference is that in our definition with the same random number r, while in [8], the distribution of and is required to be identical.
- 3.
- The third difference is that our definition omits the requirement that for all and all pairs satisfying , it holds that .
- 1.
- The challenger runs , generates , initializes an empty query set , and sends and to the adversary .
- 2.
- Throughout the experiment, may adaptively query a signing oracle with pairs , where and is a key shift:
- submits to .
- computes the signature , adds to , and returns to .
- 3.
- Finally, outputs a forgery and a final shift . The experiment outputs 1 if, and only if,Otherwise, it outputs 0.
- Upon receiving the public parameters and verification key from its EUF-CMA challenger, forwards to .
- For each j-th signing query made by , proceeds as follows:
- queries its signing oracle on and receives a signature .
- computes using the homomorphic signing algorithm, and returns to .
- In the final phase, when outputs a forgery and a shift , computesand submits to its challenger. then outputs whatever its challenger returns.
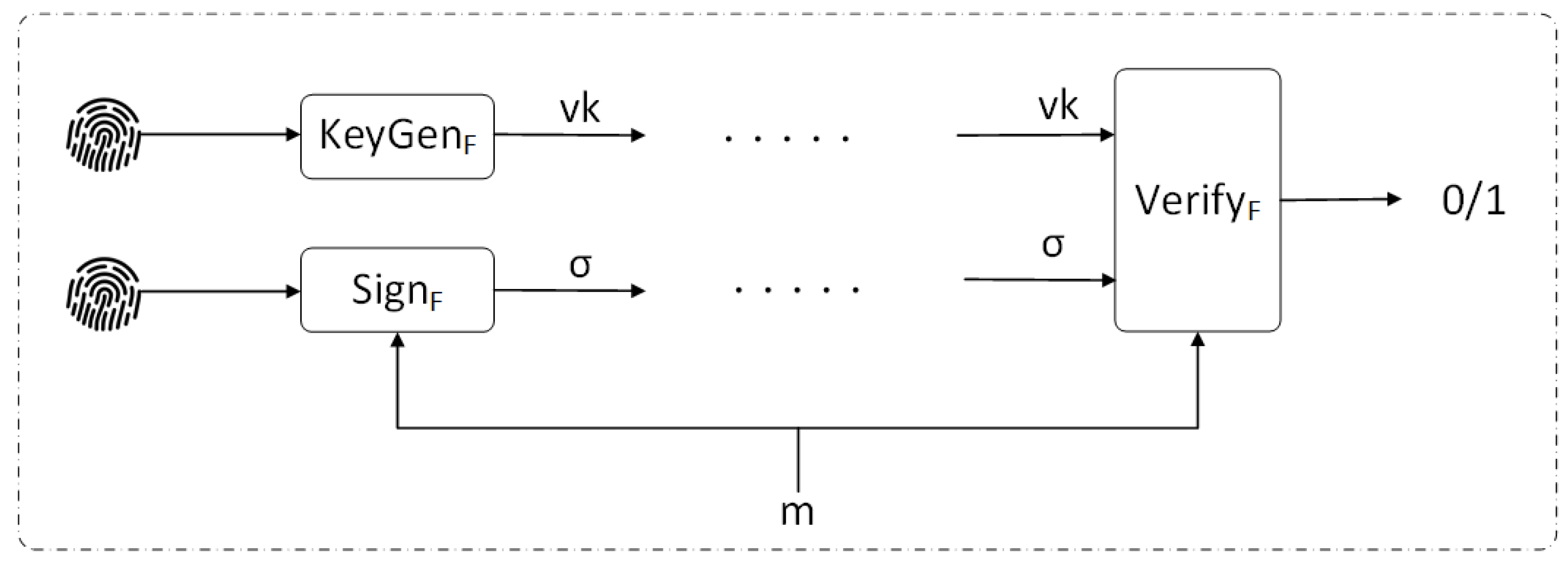
3. Fuzzy Signature
- . Upon input of the security parameter , this algorithm outputs public parameters .
- . Given the public parameters and a fuzzy signing key (e.g., a biometric template), this algorithm generates a verification key .
- . To sign a message , the signer uses a (possibly different) fuzzy key close to the original , along with , to produce a signature .
- , where . This algorithm checks the validity of the signature on message m under the verification key and public parameters , returning 1 if valid and 0 otherwise.
- 1.
- The challenger runs ; samples a signing key , where W is a distribution over with ; computes ; and initializes an empty query set . Next, it returns and to .
- 2.
- Over the course of the experiment, is allowed to adaptively make signing oracle queries in the following form:
- sends a message and a shift to .
- If , returns ⊥ (invalid shift). Else, invokes , adds to the query set , and returns to .
- 3.
- In the final phase, outputs a forgery . The experiment returns 1 if ; otherwise, it returns 0.
- If the original bit is 1, it remains unchanged.
- If the original bit is 0, it is flipped to 1.
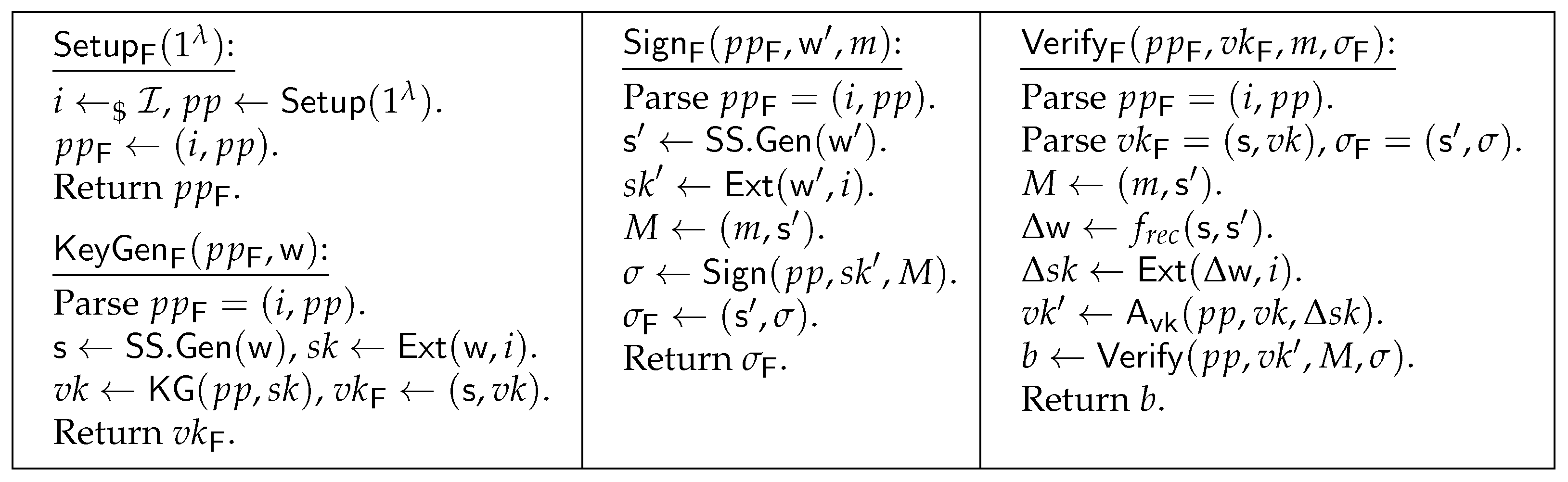
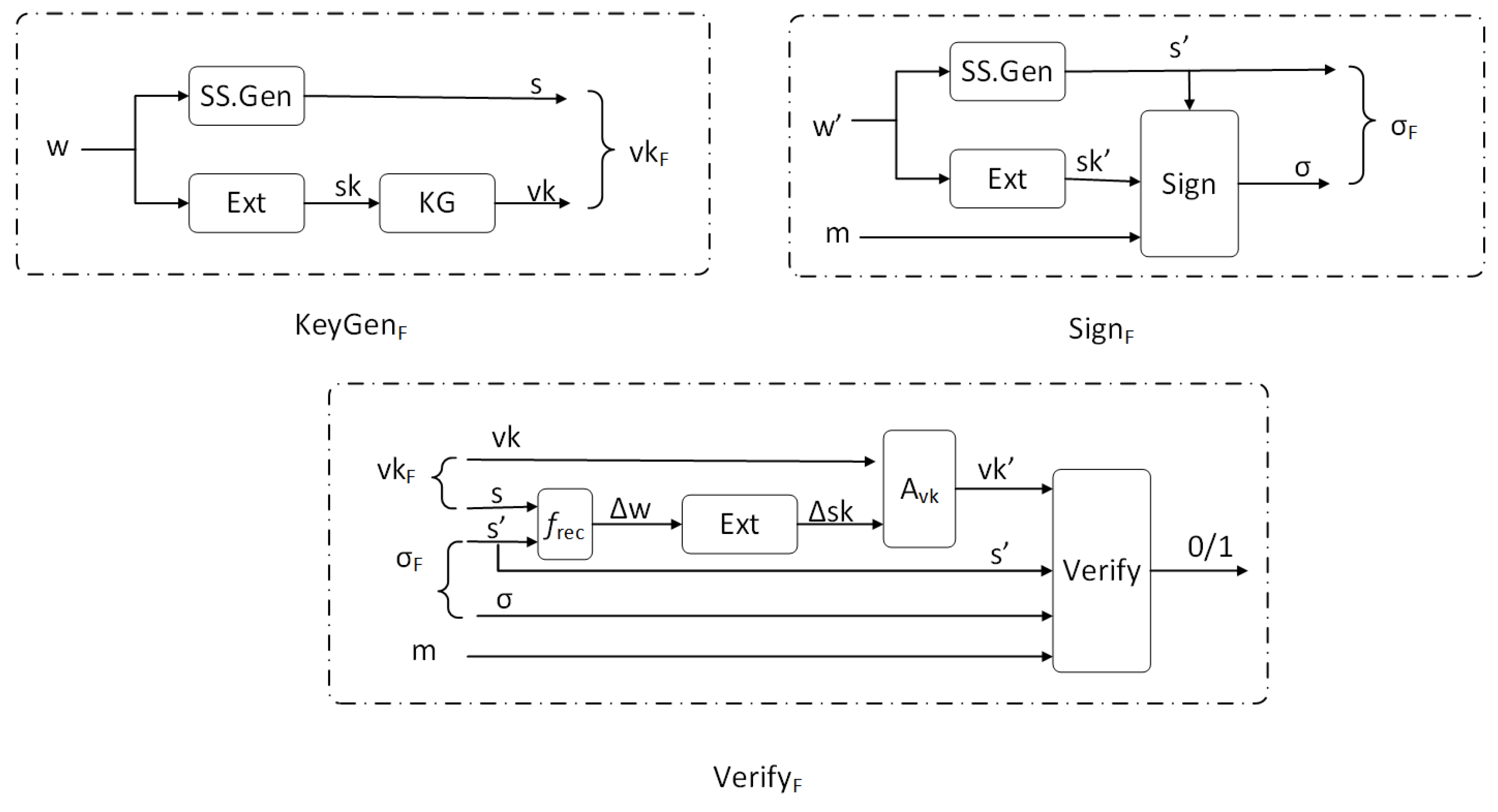
4. Construction of Fuzzy Signature
4.1. Construction
- A homomorphic -secure sketch with a sketching space that satisfies the error-recoverable property.
- A key-shift* secure and homomorphic with a secret key space and a message space .
- A homomorphic average-case -strong extractor with seed space .
4.2. Correctness
4.3. Security
- Challenger samples , invokes , sets , then samples , computes , , , and sets . Next, it initializes the query set , which denotes the set of queries selected by . Afterwards, returns to .
- The adversary may adaptively make signing queries.
- submits a message and a shift to .
- If , returns ⊥. Else, parses , invokes and , then sets , invokes , sets , adds to the set , and returns to .
- Finally, submits a forgery . parses , , , then sets , and computes , and . If , the experiment outputs 1; else, it outputs 0.Obviously,
- The adversary may adaptively make signing queries.
- submits a message and a shift to .
- If , returns ⊥. Else, parses , invokes and , then sets , invokes , sets , adds to the set , and returns to .
- Challenger samples , invokes , sets , then samples , computes , randomly chooses , computes , and sets . Next, it initializes the query set , which denotes the set of queries selected by . Afterwards, returns to .
- invokes , sets , then sets , computes , and sets . Next, it initializes the query set , which denotes the set of queries selected by . Afterwards, returns to .
- may adaptively interact with the signing oracle in the following manner.
- submits a message and a shift to .
- If , returns ⊥. Else, parses , invokes and , then sets , invokes , sets , adds to the set , and returns to .
- In the finalization phase, outputs a forgery . parses , , , then sets , and computes , , and . If , returns 1; else, returns 0.
- Upon receiving from its key-shift* challenger, samples , , then calculates , sets , and returns to adversary .
- When makes a signing query on , responds to ’s query in the following manner:
- If , returns ⊥. Else, computes and , sets , and sends to its key-shift* challenger.
- Upon receiving from its key-shift* challenger, sets and returns to .
- In the finalization phase, outputs a forgery to . parses , sets , computes and , submits and a shift to its challenger, and returns what its challenger returns.
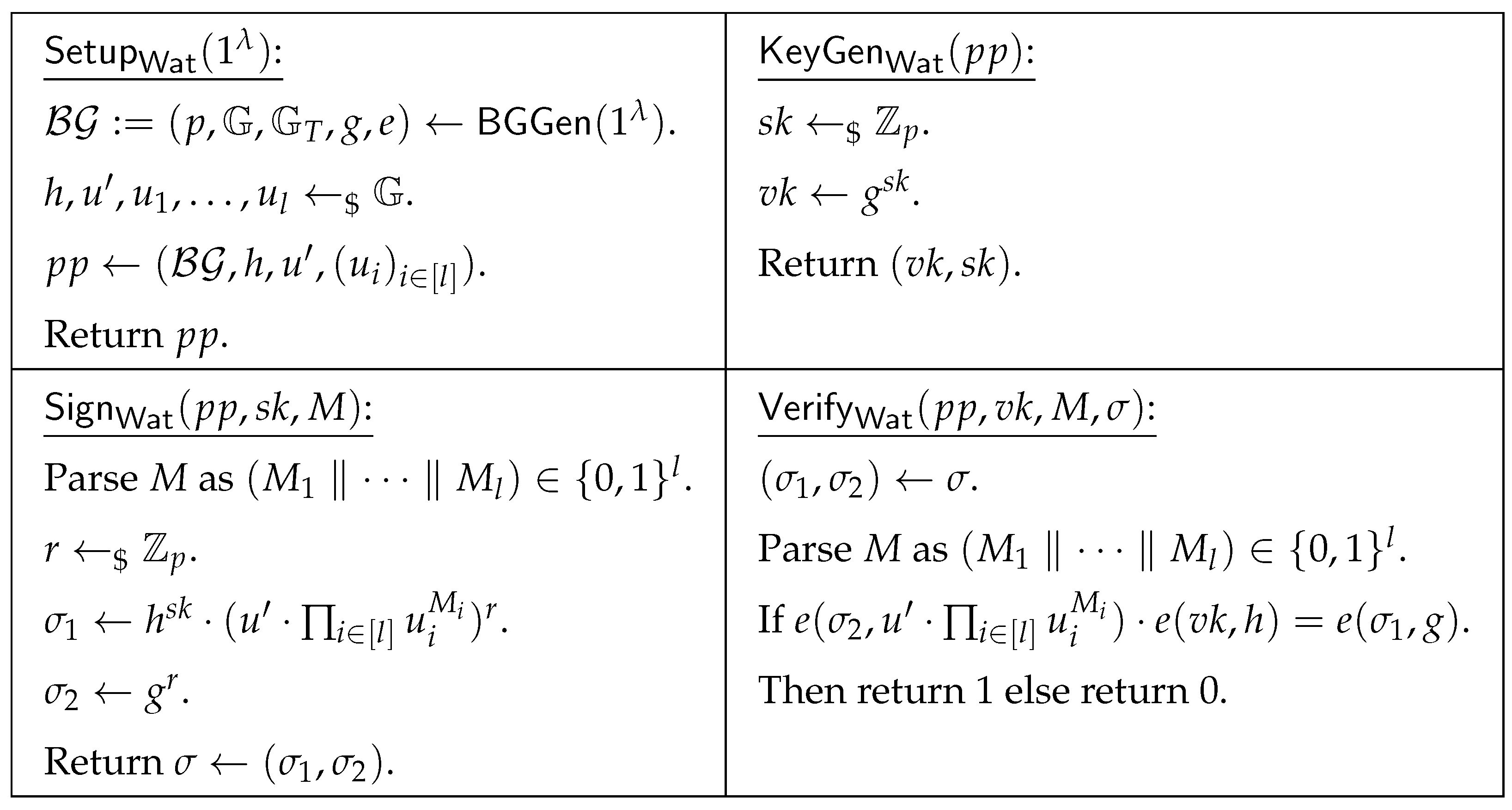
5. Instantiation
- Note that The signing key space , equipped with addition modulo p, constitutes an abelian group.
- Note that , so there exsits a deterministic and efficient algorithm , such that
- Given a message M and a fixed random number , the signature of M under signing key with random number r isThe signature of M under signing key with the same random number r isNote thatandSo there exisits a deterministic and efficient algorithm , such thatThe lemma follows. □
6. Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Syndrome-Based Secure Sketch
- Secure Sketch (SS):
- Reconstruction (Rec):
Appendix B. RKA Security
- 1.
- The challenger runs , computes , then initializes , which denotes the set of queries selected by . Afterwards, returns and to .
- 2.
- Over the course of the experiment, is allowed to adaptively make signing oracle queries in the following form:
- sends a message and a funcition to the challenger .
- computes , adds to the query set , and replies to with .
- 3.
- In the final phase, outputs a candidate forgery in the form of a message–signature pair . The experiment returns 1 if ; otherwise, it returns 0.
Appendix C. Bilinear Groups
- p is a prime number;
- and are cyclic groups of order p;
- g is a generator of ;
- is a bilinear map computable in time polynomial in , satisfying the following:
- –
- Bilinearity: For all and , we have
- –
- Non-degeneracy: For all generators g of , is not the identity in .
References
- Kaur, R.; Kaur, A. Digital signature. In Proceedings of the 2012 International Conference on Computing Sciences, Phagwara, India, 14–15 September 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 295–301. [Google Scholar] [CrossRef]
- Yin, H.L.; Fu, Y.; Li, C.L.; Weng, C.X.; Li, B.H.; Gu, J.; Lu, Y.S.; Huang, S.; Chen, Z.B. Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 2023, 10, nwac228. [Google Scholar] [CrossRef] [PubMed]
- Alzubi, J.A. Blockchain-based Lamport Merkle digital signature: Authentication tool in IoT healthcare. Comput. Commun. 2021, 170, 200–208. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Li, G.; Li, X. Improvement of robust smart-card-based password authentication scheme. Int. J. Commun. Syst. 2015, 28, 383–393. [Google Scholar] [CrossRef]
- Lu, H.K. Network smart card review and analysis. Comput. Netw. 2007, 51, 2234–2248. [Google Scholar] [CrossRef]
- Wala’a, M.A.; Abusaimeh, H. Modified USB Security Token for User Authentication. Comput. Inf. Sci. 2015, 8, 51–63. [Google Scholar] [CrossRef][Green Version]
- Jiang, L.; Li, X.; Cheng, L.; Guo, D. Identity authentication scheme of cloud storage for user anonymity via USB token. In Proceedings of the 2013 International Conference on Anti-Counterfeiting, Security and Identification (ASID), Shanghai, China, 25–27 October 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Takahashi, K.; Matsuda, T.; Murakami, T.; Hanaoka, G.; Nishigaki, M. A signature scheme with a fuzzy private key. In Applied Cryptography and Network Security, Proceedings of the International Conference on Applied Cryptography and Network Security, New York, NY, USA, 2–5 June 2015; Malkin, T., Kolesnikov, V., Lewko, A., Polychronakis, M., Eds.; LNCS; Springer: Cham, Switzerland, 2015; Volume 9092, pp. 105–126. [Google Scholar] [CrossRef]
- Tan, J.; Bauer, L.; Bonneau, J.; Cranor, L.F.; Thomas, J.; Ur, B. Can Unicorns Help Users Compare Crypto Key Fingerprints? In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems, CHI’17, Denver, CO, USA, 6–11 May 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 3787–3798. [Google Scholar] [CrossRef]
- Yoon, S.; Jain, A.K. Longitudinal study of fingerprint recognition. Proc. Natl. Acad. Sci. USA 2015, 112, 8555–8560. [Google Scholar] [CrossRef]
- Omolara, A.E.; Jantan, A.; Abiodun, O.I.; Arshad, H.; Mohamed, N.A. Fingereye: Improvising security and optimizing ATM transaction time based on iris-scan authentication. Int. J. Electr. Comput. Eng. 2019, 9, 1879–1886. [Google Scholar] [CrossRef]
- Matsuda, T.; Takahashi, K.; Murakami, T.; Hanaoka, G. Fuzzy signatures: Relaxing requirements and a new construction. In Applied Cryptography and Network Security, Proceedings of the International Conference on Applied Cryptography and Network Security, Guildford, UK, 19–22 June 2016; Manulis, M., Sadeghi, A.R., Schneider, S., Eds.; LNCS; Springer: Cham, Switzerland, 2016; Volume 9696, pp. 97–116. [Google Scholar] [CrossRef]
- Schnorr, C.P. Efficient identification and signatures for smart cards. In Advances in Cryptology—CRYPTO’ 89 Proceedings, Proceedings of the 9th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 1989; Brassard, G., Ed.; LNCS; Springer: Cham, Switzerland, 1990; Volume 435, pp. 239–252. [Google Scholar] [CrossRef]
- Katsumata, S.; Matsuda, T.; Nakamura, W.; Ohara, K.; Takahashi, K. Revisiting fuzzy signatures: Towards a more risk-free cryptographic authentication system based on biometrics. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, CCS ’21, Virtual, 15–19 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 2046–2065. [Google Scholar] [CrossRef]
- Peikert, C. A decade of lattice cryptography. Found. Trends® Theor. Comput. Sci. 2016, 10, 283–424. [Google Scholar] [CrossRef]
- Odlyzko, A. Discrete logarithms in finite fields and their cryptographic significance. In Advances in Cryptology, Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques, Paris, France, 9–11 April 1984; Beth, T., Cot, N., Ingemarsson, I., Eds.; LNCS; Springer: Cham, Switzerland, 1984; Volume 209, pp. 224–314. [Google Scholar] [CrossRef]
- Koblitz, N.; Menezes, A.J. The random oracle model: A twenty-year retrospective. Des. Codes Cryptogr. 2015, 77, 587–610. [Google Scholar] [CrossRef]
- Song, J.; Wen, Y. A generic construction of fuzzy signature. In Information Security and Cryptology, Proceedings of the International Conference on Information Security and Cryptology, Virtual,12–14 August 2021; Yu, Y., Yung, M., Eds.; LNCS; Springer: Cham, Switzerland, 2021; Volume 13007, pp. 23–41. [Google Scholar] [CrossRef]
- Bein, B. Entropy. Best Pract. Res. Clin. Anaesthesiol. 2006, 20, 101–109. [Google Scholar] [CrossRef] [PubMed]
- Dodis, Y.; Reyzin, L.; Smith, A.D. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Cachin, C., Camenisch, J., Eds.; LNCS; Springer: Cham, Switzerland, 2004; Volume 3027, pp. 523–540. [Google Scholar] [CrossRef]
- Joux, A.; Nguyen, K. Separating decision Diffie–Hellman from computational Diffie–Hellman in cryptographic groups. J. Cryptol. 2003, 16, 239–247. [Google Scholar] [CrossRef]
- Tian, Y.; Li, Y.; Deng, R.; Sengupta, B.; Yang, G. Lattice-based remote user authentication from reusable fuzzy signature. J. Comput. Secur. 2021, 29, 273–298. [Google Scholar] [CrossRef]
- Apon, D.; Cho, C.; Eldefrawy, K.; Katz, J. Efficient, reusable fuzzy extractors from LWE. In Cyber Security Cryptography and Machine Learning, Proceedings of the first International Conference, CSCML 2017, Beer-Sheva, Israel, 29–30 June 2017; Dolev, S., Lodha, S., Eds.; LNCS; Springer: Cham, Switzerland, 2017; Volume 10332, pp. 1–18. [Google Scholar] [CrossRef]
- Wen, Y.; Liu, S. Reusable fuzzy extractor from LWE. In Information Security and Privacy, Proceedings of the ACISP 2018, Wollongong, NSW, Australia, 11–13 July 2018; Susilo, W., Yang, G., Eds.; LNCS; Springer: Cham, Switzerland, 2018; Volume 10946, pp. 13–27. [Google Scholar] [CrossRef]
- Zhou, Y.; Liu, S.; Han, S. Robustly Reusable Fuzzy Extractor from Isogeny. Theor. Comput. Sci. 2024, 1008, 114677. [Google Scholar] [CrossRef]
- Lyubashevsky, V. Lattice signatures without trapdoors. In Advances in Cryptology—EUROCRYPT 2012, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Cham, Switzerland, 2012; Volume 7237, pp. 738–755. [Google Scholar] [CrossRef]
- Zheng, M.; Liu, Z.; Mambo, M. A Provably Secure Lattice-Based Fuzzy Signature Scheme Using Linear Sketch. IEEE Access 2023, 11, 62510–62521. [Google Scholar] [CrossRef]
- Wang, S.; Zhu, Y.; Ma, D.; Feng, R. Lattice-based key exchange on small integer solution problem. Sci. China Inf. Sci. 2014, 57, 1–12. [Google Scholar] [CrossRef]
- Wen, Y.; Liu, S. Robustly reusable fuzzy extractor from standard assumptions. In Advances in Cryptology—ASIACRYPT 2018, Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, QLD, Australia, 2–6 December 2018; Peyrin, T., Galbraith, S., Eds.; LNCS; Springer: Cham, Switzerland, 2018; Volume 11274, pp. 459–489. [Google Scholar] [CrossRef]
- Shoup, V. A Computational Introduction to Number Theory and Algebra; Cambridge University Press: Cambridge, UK, 2006. [Google Scholar]
- Bellare, M.; Cash, D.; Miller, R. Cryptography Secure against Related-Key Attacks and Tampering. In Advances in Cryptology—ASIACRYPT 2011, Proceedings of the 17th International Conference on the Theory and Application of Cryptology and Information Security, Seoul, Republic of Korea, 4–8 December 2011; Lee, D.H., Wang, X., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2011; Volume 7073, pp. 486–503. [Google Scholar] [CrossRef]
- Waters, B. Efficient identity-based encryption without random oracles. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Cham, Switzerland, 2005; Volume 3494, pp. 114–127. [Google Scholar] [CrossRef]
- Hofheinz, D.; Jager, T.; Knapp, E. Waters Signatures with Optimal Security Reduction. In Public Key Cryptography—PKC 2012, Proceedings of the 15th International Conference on Practice and Theory in Public Key Cryptography, Darmstadt, Germany,21–23 May 2012; Fischlin, M., Buchmann, J., Manulis, M., Eds.; Springer: Cham, Switzerland, 2012; Volume 7293, pp. 66–83. [Google Scholar] [CrossRef]

| Method | Correlation | Assumption | Standard Model | ||
|---|---|---|---|---|---|
| TMMHN15 [8] | Linear Sketch | Independent | ✓ | CDH | ✓ |
| MTMH16 [12] | Linear Sketch | Independent | ✓ | DL | ✗ |
| KK21 [14] | Linear Sketch | Independent | ✓ | DL | ✗ |
| ZLM23 [27] | Linear Sketch | Independent | ✓ | SIS | ✗ |
| SW21 [18] | Fuzzy Extractor | Arbitrary | ✗ | CDH | ✓ |
| TLDSY21 [22] | Fuzzy Extractor | Adversary-Selected | ✓ | LWE, SIS | ✗ |
| Our Scheme | Secure Sketch | Adversary-Selected | ✓ | CDH | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, Y.; Jin, T.; Li, W. Fuzzy Signature from Computational Diffie–Hellman Assumption in the Standard Model. Axioms 2025, 14, 613. https://doi.org/10.3390/axioms14080613
Wen Y, Jin T, Li W. Fuzzy Signature from Computational Diffie–Hellman Assumption in the Standard Model. Axioms. 2025; 14(8):613. https://doi.org/10.3390/axioms14080613
Chicago/Turabian StyleWen, Yunhua, Tianlong Jin, and Wei Li. 2025. "Fuzzy Signature from Computational Diffie–Hellman Assumption in the Standard Model" Axioms 14, no. 8: 613. https://doi.org/10.3390/axioms14080613
APA StyleWen, Y., Jin, T., & Li, W. (2025). Fuzzy Signature from Computational Diffie–Hellman Assumption in the Standard Model. Axioms, 14(8), 613. https://doi.org/10.3390/axioms14080613






