1. Introduction
Fuzzy graph networks merge fuzzy set theory and graph theory and offer a mechanism to model imprecision, vagueness, and uncertainty in systems and relations. Fuzzy graph networks increasingly find application in cryptography because they can deal with ambiguity and allow flexible solutions for security issues. Fuzzy graph networks are graphs whose nodes and edges possess fuzzy attributes that define uncertain or imprecise relationships between entities. A fuzzy graph is represented by = (, υ, ω), where υ is a mapping from into [0, 1], a membership function representing the extent of participation of a vertex, and ω is a mapping from × into [0, 1], a relation showing the extent of the relationship (edge weight) between two vertices.
If every vertex in the graph is either in the subset or adjacent to at least one vertex in the subset, the subset is known as a dominating set in graph theory. A dominating set in a graph that has the further requirement that just one vertex in the dominating set dominates every vertex in the graph is called an efficient dominating set, often referred to as a perfect dominating set. This ensures that domination is not redundant and is therefore an “efficient” solution. Vertex set is a subset of of = (, υ, ω) and is a dominating set if, for each vertex in − , the following condition is met: (i) υ() > 0 and the vertex is in , or (ii) is adjacent to vertex in , with ω() > 0. The edge () connects to in and contains a positive membership value. A fuzzy graph network ( is a graph network if it satisfies ω() min( for every () in . A fuzzy graph network is said to be a strong fuzzy graph network ( if ω() min( for every () in
To define the notion of uncertainty in practical situations, Zadeh presented a mathematical theory in 1965 [
1]. This was the start of fuzzy graph theory and research on certain kinds of connected graph theoretical structures. Research by Bondy and U.S.R. Murthy delved into graph theory and its diverse applications [
2]. Ore [
3] studied dominance in graph structures. Haynes et al. [
4] initiated research on paired domination. Biggs [
5] and Kulli [
6] contributed prominently to the theoretical part of domination in graphs. Kulli and Janakiram [
7] worked on split domination, whereas Kulli and Patwari [
8] worked on graph domination in general. Cockayne and Hedetniemi [
9] first proposed the independent domination numbers in graphs. Meenakshi and Baskar Babujee [
10] extended the idea of paired equitable domination. Kwon et al. [
11] were involved in classifying efficiently dominant sets of circular graphs with a degree of 5. Somasundram A and Somasundram S studied domination and total domination in fuzzy graphs [
12]. Nagoorkani and chandrasekaran [
13] studied domination in fuzzy graphs. Atanassov [
14] laid the basis for intuitionistic fuzzy graphs (IFGs) and intuitionistic fuzzy relations. Enrico Enriquez [
15] researched domination in fuzzy directed graphs, while Atanassov worked on intuitionistic fuzzy graphs and their relational structures. Karunambigai et al. later examined a certain subtype of IFGs, as characterized by Shannon and Atanassov [
16].
Pius et al. [
17] proposed a cryptographic method to encrypt sensitive information to solve data privacy in fuzzy graph theory. Wang et al. [
18] gave a more concise derivation for matrix extension by extending the extended visual Cryptography Scheme to encrypt several color pictures with significant shares. Also, the authors proposed new applications for these tagged structures and cryptography to optimize the graph features, particularly in networks that require high efficiency and interconnectedness. The paper presented a mathematical framework and outlined its applications in network security. The work was subsequently followed up by Meenakshi et al. [
19] and later generalized to hypergraphs [
20]. Wu et al. [
21] suggested a security model based on hypergraph structures to model and handle security mechanisms over multiple layers in optical networks. Finally, in [
22,
23,
24,
25,
26], the authors discussed various types and applications of fuzzy graphs.
Motivation and Novelty
Although many studies have considered fuzzy-logic-based cryptographic systems, most of them consider fuzzy authentication, threshold schemes, or standard fuzzy set uses without incorporating essential structural graph theoretic features. Fuzzy and intuitionistic fuzzy graphs have been considered for modeling uncertainty in networks in previous research, and RSA is a well-established encryption technique. The integration of fuzzy domination principles with traditional cryptographic methods is still unexplored. The innovation of this research is the integration of efficient domination in fuzzy graph networks with RSA cryptosystem, a layered encryption mechanism that increases security through mathematical complexity and structural optimization. In contrast to traditional hybrid cryptosystems, which tend to merge fuzzy logic concepts with encryption schemes, our approach embeds data within fuzzy graph structures that are controlled by effective dominating sets, minimizing redundancy and maximizing control in secure communication. In addition, the employment of triangular fuzzy membership functions and strong fuzzy graph networks in the cryptographic process introduces a new paradigm for handling uncertainty and vagueness in encryption methods. This integrated framework not only enhances encryption but also confers a structural advantage in secure key distribution and decryption, hence presenting a marked improvement over earlier methods.
For the sake of clarity, a list of all symbols and notations employed in this paper is given in
Table 1.
Section 2 describes how a fuzzy graph network can be constructed using an efficient dominating set, RSA algorithm, and triangular fuzzy membership function.
Section 3,
Section 4 and
Section 5 present the encryption and decryption algorithms of the designed cryptosystem.
Section 6 presents the cryptosystem through an example that explains how to obtain the cipher graph and plaintext of the secret data.
Section 7 provides a comparative study of various cryptographic methods against the proposed one.
Section 8,
Section 9 and
Section 10 present the flowchart of the proposed cryptosystem and possible vector attacks and
Section 11 presents the conclusion.
2. Proposed Cryptosystem
The proposed system consists of (i) the numerical plaintext, (ii) cipher graph, (iii) encryption algorithm, (iv) decryption algorithm and (v) key.
- (i)
Numerical plaintext: This is the original, readable, and unencrypted data or message. It is what is fed into an encryption procedure, which scrambles it to make it unreadable in the form of a cipher graph to secure its confidentiality. In this cryptosystem, the numerical plaintext is the non-negative composite number.
- (ii)
Cipher graph: This is the encrypted, non-readable data resulting from plaintext having an encryption algorithm applied to it. It is meant to safeguard the original information against unauthorized parties, so its confidentiality can be guaranteed during storage or transmission. In this study, the cipher graph is a fuzzy graph network, and it is denoted by .
- (iii)
Encryption algorithm: This is a mathematical operation to convert plaintext (readable data) into a cipher graph (unreadable data) in order to maintain its confidentiality and security. This algorithm, along with a cryptographic key, specifies how the conversion is performed. In this cryptosystem, the encryption algorithm is constructed based on RSA, efficient domination and the triangular fuzzy membership function.
- (iv)
Decryption algorithm: This is an algorithmic process applied to decrypt data that have been encrypted back to their original readable form. It is the inverse of encryption and needs the proper cryptographic key in order to execute the conversion.
- (v)
Key: This is a piece of information, often a string of characters, used in conjunction with an encryption or decryption algorithm to secure and unlock data. Keys are a fundamental component of cryptographic systems, determining how data are encrypted or decrypted. The keys used in this methodology are (i) finding efficient dominating nodes in the cipher graph represented as (key 1), (ii) finding the range of triangular fuzzy triplets (key 2) and (iii) RSA private key . The decryption process is performed by applying these keys to access the numerical plaintext.
3. Construction of
Step 1: Let the numerical plain text
be
where
k and
r are positive integers.
Step 2: Using , the first sub network is constructed. By using the RSA algorithm, find the encrypted message that says , which corresponds to . Convert into a triangular fuzzy number and let it be . Let .
Step 3: Let the nodes of
(
Figure 1) be
such that the distance between
and
, where
. Regarding the node membership value (
the
values of
are given by
, respectively. The edge membership values
are
and
min (
, respectively.
Step 4: Using , the second sub network is constructed. By using the RSA algorithm, find the encrypted message that says , which corresponds to . Let the nodes of be such that the distance between and is equal to 1, where . The of are , respectively. The of = min ( = min (, …, and = min (, respectively.
Step 5: Continuing this until the last step, construct rth sub network . Using , rth sub network is constructed. By using the RSA algorithm, find the encrypted message and let it be , which corresponds to . Let the nodes of be such that the distance between and = 1, where The of are , respectively. The = min ( = min ( = min (, …, and = min (, respectively. The of the rest of the constructed edges is established according to the definition of
Step 6: Let be the nodes of the efficient dominating set, which has that are Construct network using as follows. The node set of is where The number of nodes present in is r + + + + … + The minimum number of edges required for is calculated as follows.
Step 7: Define for only one where . The minimum number of edges required for is = .
Step 8: The maximum number of edges required for is = (r + + + + … + where }.
4. Encryption Procedure
Input: where .
Output: Cipher graph .
Step 1: Let the numerical plaintext be where k and ir are positive integers.
Partition the as , , , …, and Using , the first sub network is constructed.
Step 2: For , choose , (where l < i) and all are prime numbers (if preferred, choose the number , where and it may be one digit or two digits or something else).
For , choose , (where l < i) and all are prime numbers (if preferred, choose the number , where and it may be one digit or two digits or something else). Proceeding to choose , (where l < i) and all are prime numbers (if preferred, choose the number , where and it may be one digit or two digits or something else).
Step 3: Let , such that . Let . By using the RSA algorithm, find suitable and such that , which is congruent to 1 mod . Compute the encrypted message , which corresponds to . Let , such that . Let . By using the RSA algorithm, find suitable and such that mod (.
Compute the encrypted message , which corresponds to . Continue this until the last value is calculated.
Let , such that . Let . By using the RSA algorithm, find suitable and such that mod (. Compute the encrypted message
Step 4: Using triangular fuzzy membership functions, convert
into a triangular fuzzy number, say
. Then, the fuzzy number
is as follows:
Let Using triangular fuzzy membership functions, convert into a triangular fuzzy number, say . Let . Continuing this until the last value is calculated, using triangular fuzzy membership functions, convert into a triangular fuzzy number, say . Let .
Step 5: Fuzzy graph sub network construction : Let the nodes of be such that distance between and where . The of are given by , respectively. The = min( = min ( min ( and the of and is a minimum of , where
Fuzzy graph sub network construction : Let the nodes of be such that the distance between and where The of are , respectively. The of and is a minimum of (, the of and is a minimum of ( , where
Fuzzy graph sub network construction : Let the nodes of be such that the distance between and = 1, where The of are , respectively. The of and are a minimum of (,), where The s of the rest of the constructed edges follow the definition of The nodes are the centers of , …. They are members of the efficient dominating set of the
End
5. Decryption Procedure
Input: Cipher graph .
Output: .
Begin
Step 1: Determine the of , whose are denoted by .
Step 2: Let the membership values of triangular fuzzy number of , , be , , , and its triplet parameters are given as , , respectively.
Step 3: Let the triangular fuzzy number of be and its range be , meaning and likewise, find . Continue this for whose triangular triplets are and its range is , meaning and likewise, find . Similarly, find the values of from ,, respectively.
Step 4: By using the RSA algorithm, obtain while decrypting using (mod . Obtain while decrypting using (mod and continue this until the last value is obtained, and obtain while decrypting using (mod .
Step 5: Concatenate the values , which gives the .
6. Illustration
Step 1: Let the numerical plaintext be 11,985,920/21,450,625/245,394/149,528,879/77,343.
Divide the into components ,.
Let 11,985,920, 21,450,625, 245,394, 149,528,879, and 77,343.
Step 2: Using
, the first sub network
is constructed. An illustration of
is given in
Figure 2. Let the nodes of
be
such that the distance between
and
, where
.
Let = (, υ, ω) be a graph. Subset is an efficient dominating set if , |{| where denotes the neighboring vertices of . The of are given by respectively. The of min of min (,…, and min (, respectively.
Step 3: Using , the second sub network is constructed. Let the nodes of the be such that the distance between and , where The of are , respectively. The of = min of = of = , …, and of = , respectively.
Step 4: Similarly, construct . Using , the fifth sub network is constructed. Let the nodes of be such that the distance between and , where The of are , respectively. The of = of = min of = min , …, and = , respectively.
Step 5: The of the rest of the constructed edges follows the definition of Let be the nodes of the efficient dominating set, which have that are . Construct the network using as follows. The node set of is where The number of nodes present in is + + + + + . The minimum number of edges required for is calculated as follows.
Define for only one where
The minimum number of edges required for is = .
Step 6: The maximum number of edges required for is = ( + + + + + where , , , , and , .
- (i)
Encryption Algorithm
Input: Numerical plaintext
, which are all positive integers.
Output: Cipher graph
Begin
Step 1: Let the numerical plaintext be 11,985,920/21,450,625/245,394/149,528,879/77,343. Divide the into components , respectively, where 11,985,920, 21,450,625, 245,394, 149,528,879, and 77,343.
Step 2: Consider 11,985,920. is encrypted using the RSA algorithm. Let us consider the prime numbers 53,(it may be two digits or three digits). = 21,985,937, such that
Step 3: Let the function
Step 4: Find suitable and such that , which is congruent to 1 mod , and find the encrypted message that says (mod , which corresponds to . Find a suitable , where such that gcd(=. Let
Step 5: Find such that mod ( = 8,606,465. Now, let the cipher integer mod 7,517,755.
Step 6: Convert into a triangular fuzzy number, say , and let its range be , meaning and likewise, find . For the value, choose any number between and then the fuzzy number.
Step 7: Let the triangular fuzzy number of
be
and its range be
, meaning
and likewise, find
. Let
. Convert the cipher integer to TFNs
. For the
value, choose any number between
. Then, the fuzzy number
is as follows:
Here, the cipher graph 7,517,755 is given as where 7,517,755 and and its range is .
Let
Step 8: Now,
is split into six parts and assigned as a membership value for the vertices of the network, as in
Table 2.
.
Step 9: Let the nodes of
be
such that the distance between
and
is equal to 1, where
. The
of
are given by
, respectively. The
of
= min (
= min (
of
min (
, …, and
= min (
, respectively, as in
Table 3.
Step 10: Similarly, construct from 21,450,625, 245,394, 149,528,879, and 77,343, respectively.
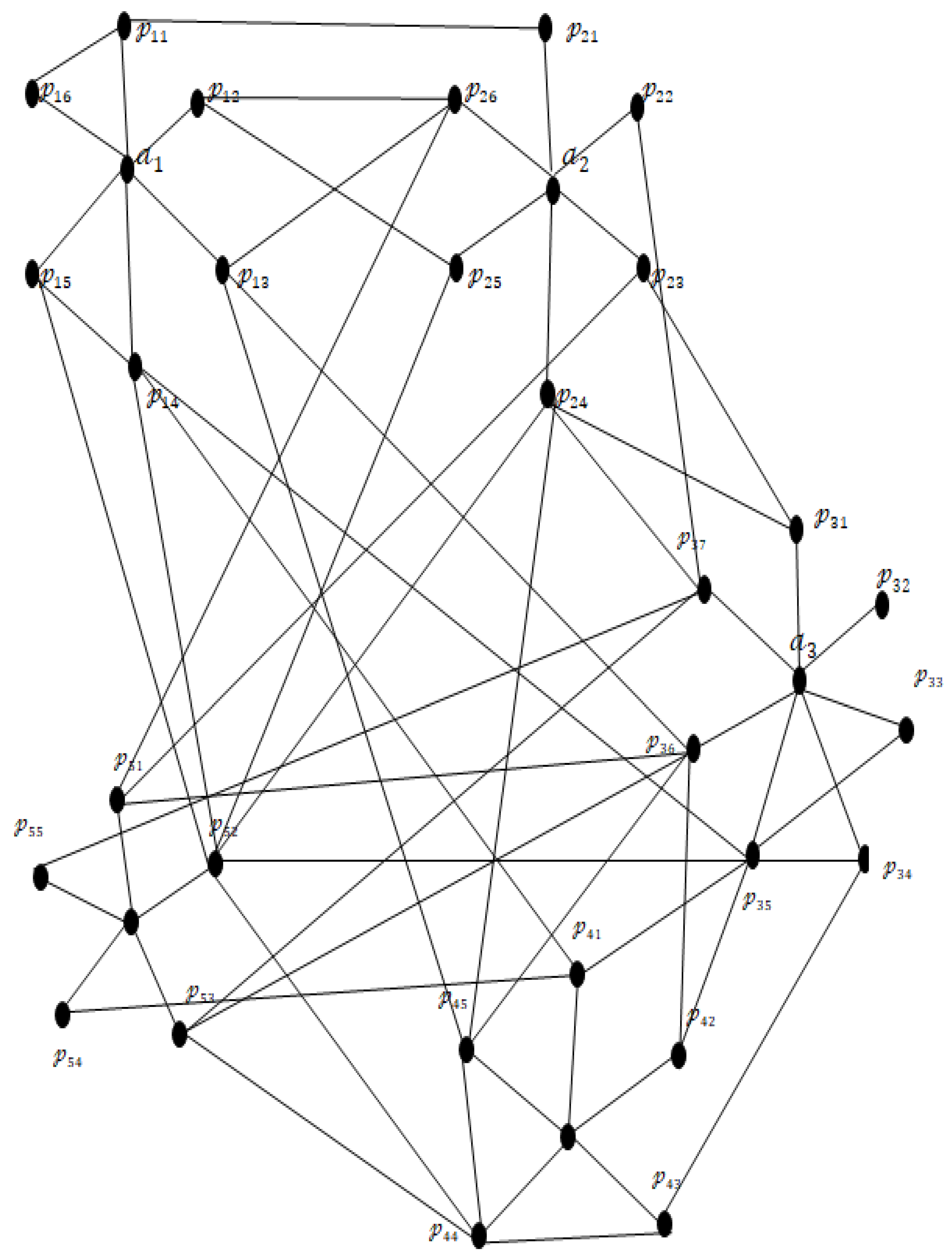
Step 11: Now, the networks
are connected using edges from set
network
(
Figure 3), where
for only one
The
of the above constructed edges follows from the definition of
Let
be the nodes of the
, which have
s
Step 12: The network is expanded by adding additional edges, as in
Figure 4, while adhering to the given constraints, resulting in a moderately connected structure as in
Table 4.
Step 13: The maximum number of edges required for is = ( + + + + + )C2 − { where , , , , and , .
This is shown in
Figure 5.
End.
- (ii)
Decryption Algorithm
Input: Cipher graph .
Output: .
Begin
Step 1: Determine the of . whose are denoted by
Step 2: Let the membership values of the triangular fuzzy number of , be , ,, and its triplet parameters are given as , , respectively.
Step 3: Let the triangular fuzzy number of
be
and its range be
, meaning
and likewise, find
.
Similarly, find the values of from ,, respectively.
Step 4: By using the RSA algorithm, obtain
while decrypting
using
(mod
.
Likewise, obtain while decrypting using (mod and continue this until the last value is obtained, and obtain while decrypting using (mod .
Step 5: Concatenate values
to obtain the
.
7. Comparative Study
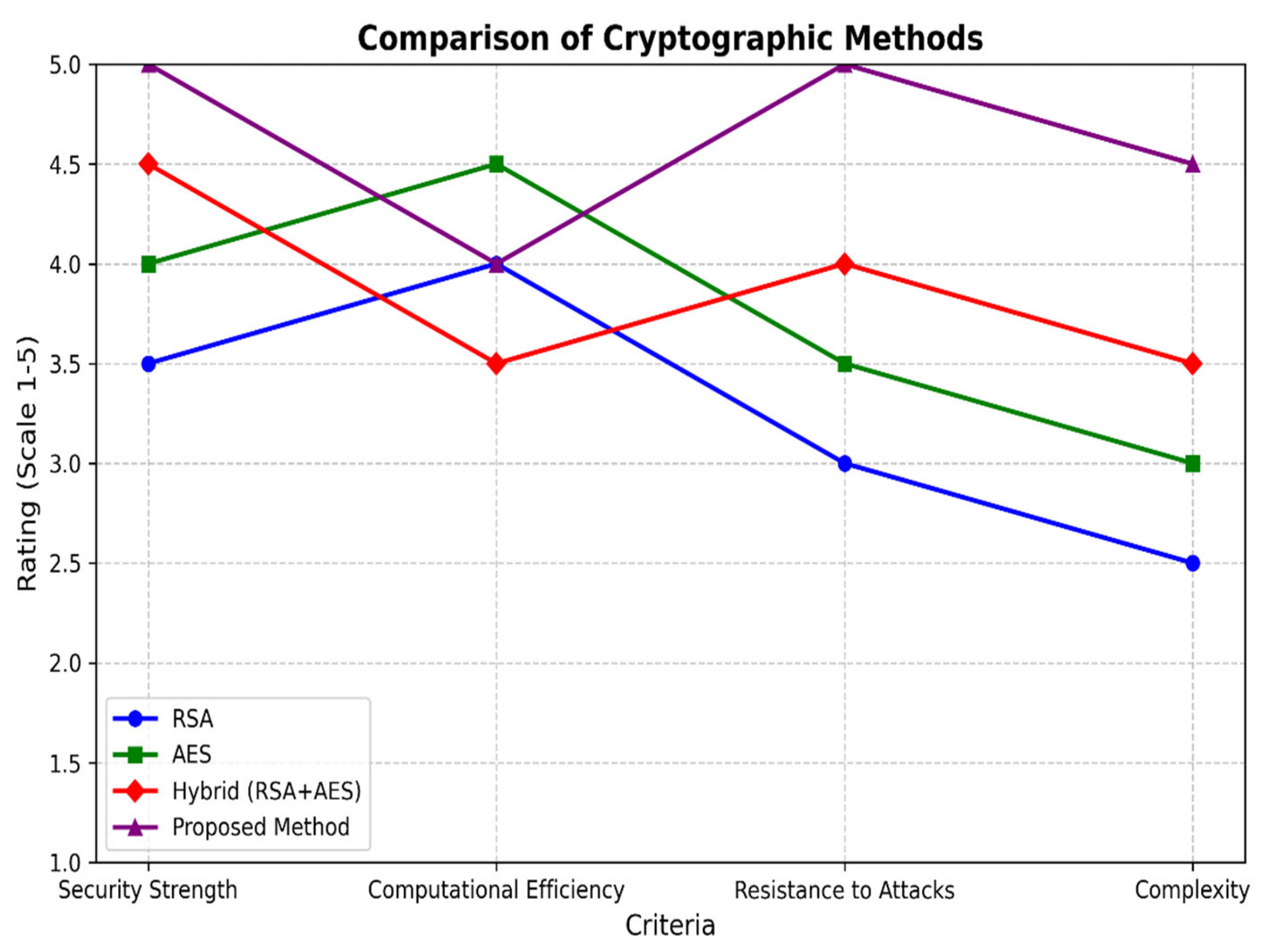
Cryptographic encryption methods are essential to protect data from unauthorized access. Conventional techniques like RSA and AES have been extensively employed, while hybrid techniques use more than one encryption method for better security. This research compares the available methods with the new encryption method proposed in this research, using the RSA algorithm, fuzzy logic, and graph-based transformations to offer a highly secure and efficient cryptographic system. The encryption techniques are assessed on the basis of the following four crucial criteria’s namely security strength, computational efficiency, resistance to attacks and complexity. The comparative assessment, as represented in the graph (
Figure 6) and
Table 5, reflects the following:
- ⮚
RSA Encryption: Though popular, RSA has less security and resistance to attacks but it is computationally intensive.
- ⮚
AES Encryption: It offers greater security and efficiency than RSA and is thus best for rapid encryption but vulnerable to quantum attacks.
- ⮚
Hybrid (RSA + AES): It provides a well-balanced trade-off between efficiency and security, improving resistance against attacks.
- ⮚
Proposed Method: It outperforms all other current methods, with better security and attack resistance without compromising computational efficiency. Fuzzy logic combined with graph-based encryption provides a greater level of complexity, and therefore, decryption is very difficult for an unauthorized user.
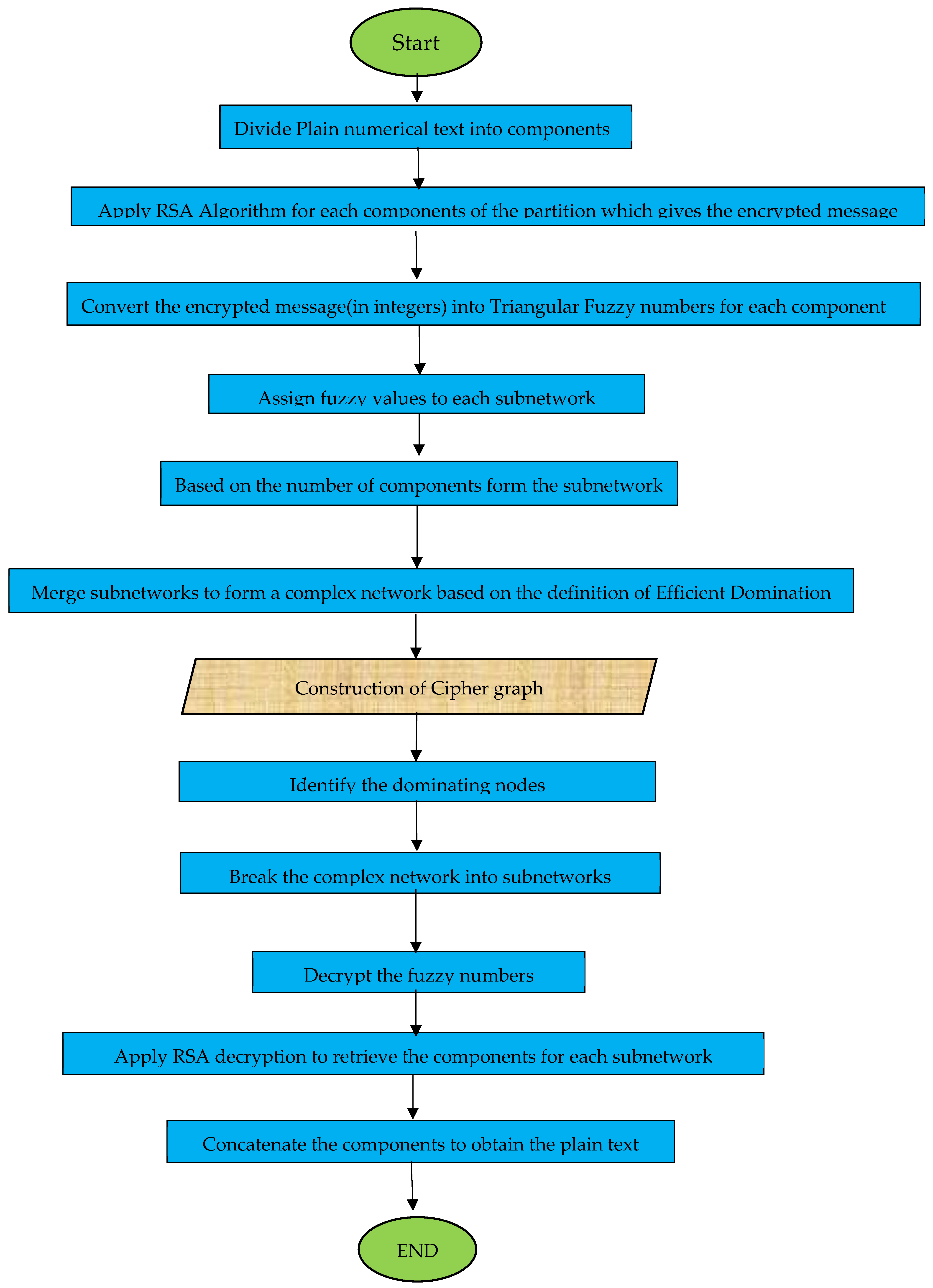
8. Flowchart
This workplan outlines a multi layer encryption process where a very large numerical plaintext is encrypted in structured steps and then converted into a complex fuzzy graph network. A flowchart is essential to visualize each stage from plaintext to ciphertext and finally back to plaintext in decryption. The flowchart is given in
Figure 7.
9. Applications in Secure Cloud Storage and Access Control
Cloud computing has emerged as the core infrastructure for the storage of data and delivery of services, but the open and distributed nature of cloud computing poses great challenges to security-sensitive information. Classical security systems tend to bank on static access control and binary authentication, which can be inadequate to manage the dynamic and contextual nature of user access in today’s cloud computing environment. The fuzzy graph-based model proposed here overcomes these shortcomings by combining RSA encryption, effective domination in graph theory, and fuzzy logic to create an adaptive and robust security system.
How the Working Model Operates in a Cloud Scenario:
- (i)
RSA for Data Privacy and Authentication: The entire sensitive information kept in the cloud is encrypted with the help of RSA, so even if storage is hacked, the data cannot be read without the private key. RSA also facilitates secure key exchange and digital signatures, enabling both cloud service providers and users to authenticate each other.
- (ii)
Efficient Domination for Fine-Tuned Access Control Structures: The cloud infrastructure can be modeled as a graph in which the nodes are either users, devices, or access points and the edges are communication or control relationships. Using efficient domination, the system is able to determine a minimum subset of key control points (dominating nodes) that are capable of monitoring and controlling access across the network. This minimizes redundancy, decreases overhead, and provides efficient monitoring and policy enforcement.
- (iii)
Fuzzy Logic for Context-Aware Access Decisions: In contrast to static access control systems, the fuzzy logic module presents triangular fuzzy membership functions to analyze contextual variables such as the following: access time (e.g., working hours vs. non-working hours), geography (e.g., familiar vs. unfamiliar IPs), user activity (e.g., frequent vs. suspicious usage) and device trust level (e.g., personal vs. public device).
Given these fuzzy inputs, the system allocates access permissions on a graded basis (e.g., full access, reduced access, or denial), enhancing flexibility without sacrificing security.
Advantages of the Model in Cloud Environments
- (i)
Dynamic Access Control: Access decisions are taken dynamically according to contextual information, enhancing responsiveness to threats or anomalies.
- (ii)
Resource Optimization: Efficient domination decreases the workload by minimizing the nodes that need to actively control access and security enforcement.
- (iii)
Greater Resilience: The hybrid model incorporates additional layers of security—cryptographic strength provided by RSA, structural optimization by graph theory, and flexibility by fuzzy logic.
- (iv)
Improved User Experience: Legitimate users stand less chance of denial of access because of strict rules since the fuzzy system checks intent and context more astutely.
This model demonstrates that the suggested fuzzy graph network model provides a big improvement over standard access control and encryption methods used in cloud computing. It can provide both secure protection of information and intelligent management of access and is particularly best suited for conditions where flexibility, scalability, and real-time decisions are needed.
10. Possible Attack Vectors of the Proposed Model
Although the model proposed here is an innovative blend of RSA, efficient domination, and fuzzy logic used to improve security, it is important to keep in mind possible attack surfaces that could threaten system integrity. The detection of these vulnerabilities aids in making the model more resilient and consistent with typical threat models used in cryptography.
Chosen-Cipher Text Attack: An attacker presents a decryption oracle with random cipher texts to obtain respective plaintexts, potentially exposing patterns or secret keys.
Graph Theoretic Structural Attacks: Efficient domination determines key nodes in a graph. If the attacker can determine and take out these dominating nodes, they can potentially achieve higher-level access or interfere with communication channels.
Fuzzy Inference Manipulation: Attackers can take advantage of the fuzzy logic layer by providing specially designed input values to control decision outputs (e.g., gain unauthorized access via marginal input conditions).
11. Conclusions
This research provides a solid mathematical framework for the protection of communication systems by combining fuzzy graph networks, efficient domination, and RSA. The suggested model increases security using the intractability of the prime factorization in RSA and improving resource consumption with efficient domination within fuzzy graphs. Through the addition of triangular fuzzy membership functions, the system provides an extra level of complexity to unauthorized decryption, rendering it very difficult. Hence, this approach guarantees a very secure and computation-friendly cryptographic form, reinforcing the confidentiality and integrity of data within contemporary networks of communication.
Key Takeaways
The model merges RSA, fuzzy logic, and graph theory for better security.
It incorporates efficient domination in fuzzy graphs for additional structural complexity.
It scales well with key size and sub-network design.
It is most appropriate for high-security data transmissions.
It is no longer quantum-resistant, but additional layers provide added protection.
It is flexible for future expansion with post-quantum methods.