Abstract
We investigate the Maker–Breaker subgraph game played on the edge set of the complete graph , where , and Maker’s objective is to construct a member of a prescribed family of graphs H, while Breaker aims to prevent this. In our study, Breaker moves first, and H is taken to be either the family of connected spanning subgraphs or the family of spanning subgraphs with minimum-degree at least . For the minimum-degree-k game, we determine the asymptotically optimal threshold bias across a wide range of values for a. For the connectivity game, we resolve an open problem posed by Hefetz et al. (2012) by identifying the exact leading term in the asymptotic behavior of the threshold bias when .
1. Introduction
Positional game theory studies two-player games of perfect information, typically played on discrete structures, ranging from popular leisure games such as Tic-Tac-Toe and Hex to abstract games played on graphs and hypergraphs. Over the past 40 years, such games have been extensively studied (Beck, 2008; Glazik & Srivastav, 2022; Hancock, 2019; Hefetz et al., 2014; Krivelevich, 2011; Liebenau & Nenadov, 2022; Mikalacki & Stojaković, 2017).
In particular, games such as the connectivity and minimum-degree-k games can model adversarial scenarios in emergency infrastructure deployment. For instance, consider a situation where Maker represents a government agency tasked with establishing a communication network between critical locations (e.g., hospitals, shelters, or command centers) after a natural disaster. In the setting, Maker secures a communication links per round, while Breaker permanently blocks b links due to natural obstacles, logistical failures, or conflicting operations. Once an edge is either claimed by Maker or blocked by Breaker, it cannot be used again. These games capture the strategic allocation of non-shareable resources under pressure and reveal threshold phenomena that determine the minimum advantage Maker must have to ensure global properties such as full connectivity or fault tolerance, even in the face of persistent disruption.
Let be a family of subsets of a finite set X. In the biased Maker–Breaker game played on the hypergraph , two players, called Maker and Breaker, alternately claim a and b—previously unclaimed elements of X, respectively. The set X is called board, and the elements of are the winning sets. Maker wins the game if they occupy a winning set; otherwise, Breaker wins.
The threshold bias for the game is defined as follows: given a Maker–Breaker game and , let be the unique positive integer such that Maker has a winning strategy for all , whereas Breaker has a winning strategy for all . Such an integer must exist, as Maker–Breaker games are known to be bias-monotone.
Determining the asymptotic threshold bias in Maker–Breaker subgraph games remains a significant challenge, especially for targets that contain cycles—a problem first raised in the foundational work of (Chvátal & Erdős, 1978). One such game is the triangle game, where the board is the edge set of the complete graph , and Maker’s goal is to occupy all three edges of a triangle. A notable advancement in this direction was recently made by (Glazik & Srivastav, 2022), who substantially reduced the gap between known upper and lower bounds in the triangle game.
In this paper, we study two variants of the Maker–Breaker game: the minimum-degree-k game and the connectivity game. Both are played on the complete graph with n vertices, where the board is the edge set of . The winning sets for Maker consist, respectively, of all spanning subgraphs with the minimum-degree at least k, and all connected spanning subgraphs.
1.1. Previous Work
The biased connectivity game was introduced by (Chvátal & Erdős, 1978). Maker wins the connectivity game if he is able to occupy the edges of a spanning tree, thus winning. The authors proved that if , then Breaker wins the game, and if , then Maker has a winning strategy to occupy a spanning tree. The problem of determining the exact leading constant for the threshold bias of the connectivity game was one of the famous open problems in Maker–Breaker games until it was resolved in a paper by (Gebauer & Szabó, 2009).
An earlier improvement came in a paper by (Beck, 1982), who showed that Maker wins the connectivity game for . Later, (Gebauer & Szabó, 2009) established the asymptotically optimal threshold bias for this game, showing that Maker has a winning strategy if .
They further demonstrated that Maker can occupy not only a spanning tree but even an induced subgraph with minimum-degree in the minimum-degree-k game, provided that
The techniques developed in their proofs have since been used in several works on Hamiltonicity, connectivity, and strong connectivity of graphs, digraphs, and randomly perturbed graphs (see, e.g., (Clemens et al., 2021; Frieze & Pegden, 2021; Hefetz et al., 2012; Krivelevich, 2011)).
Hefetz et al. (2012) considered the general connectivity game, where both a and b may be greater than 1. For , where is a constant, they proved that the threshold bias lies between
For , they showed that the threshold bias lies between
In both cases, the lower and upper bounds do not match in their leading terms.
In this paper, we resolve this problem by proving that Breaker has a winning strategy whenever
for any , where .
1.2. Our Results
Unless stated otherwise, Breaker is assumed to move first in all games considered in this paper.
1.2.1. The Maker–Breaker Minimum-Degree-k Game
We show that in the Maker–Breaker minimum-degree-k game, for
Maker has a winning strategy if
thus involving the parameter a directly in the threshold bias. Moreover, for
Maker wins whenever
Both results extend the work of (Gebauer & Szabó, 2009) to a wide range of values for a.
A new analytical technique is introduced for the Maker strategy, where a vertex is considered dangerous if its degree in the Maker’s graph is less than . While (Gebauer & Szabó, 2009) define the average danger of a multiset of vertices for Maker and Breaker based solely on the number of distinct elements, our approach accounts for the fact that a vertex can become dangerous multiple times during the game. Consequently, we compute the average by considering both the distinct vertices and their repetitions. This refinement allows for a more accurate representation of the game’s dynamics with respect to Maker’s strategy.
Moreover, the technique of computing the average value of a multiset used by (Gebauer & Szabó, 2009) introduces complications when comparing the averages of two multisets. In this paper, we propose an alternative approach that allows us to derive a generalized form of Theorem 1.2 from (Gebauer & Szabó, 2009), without needing to distinguish whether the multisets are identical.
At this point, the question is whether there exists a strategy for Breaker such that he wins if in the case where and , or if when and . Establishing these bounds would determine the asymptotically optimal threshold bias. We are able to prove both of these statements.
Furthermore, for the connectivity game, our result for in the case implies that Breaker wins if , improving upon the weaker bound stated in (Hefetz et al., 2012).
Our proof relies on the BoxMaker game technique introduced by (Chvátal & Erdős, 1978), in which Breaker plays the role of BoxMaker. This technique was employed by (Gebauer & Szabó, 2009) to devise a winning strategy for Breaker in the minimum-degree Maker–Breaker game. Later, Hefetz et al. (2012) adapted the same approach to demonstrate Breaker’s win in the Connectivity Maker–Breaker game.
In our approach, we begin by constructing an instance of the BoxMaker game using a clique in the complete graph . The size of this clique plays a crucial role in determining the threshold bias: the larger the clique, the more difficult it becomes for Maker to prevent Breaker from isolating vertices.
In the earlier work of Hefetz et al. (2012), for , the clique size was set to
In contrast, our analysis allows for a smaller clique size, namely,
1.2.2. The Maker–Breaker Connectivity Game
Hefetz et al. (2012) showed that if for some , then the threshold bias satisfies
and if for some , then
They posed as an open problem the task of narrowing the gap between the lower and upper bounds on .
Our result for the minimum-degree-k game, with for some , , and , immediately implies a win for Breaker in the connectivity game.
Remark 1.
When not necessary, we omit the ceiling and floor signs.
2. Minimum-Degree- Game
Recall that Breaker moves first.
2.1. Winning Strategy for Maker
We introduce the notion of danger for each vertex, from the perspectives of both Maker and Breaker, and present a strategy designed to minimize the risk of losing the game for Maker.
Definition 1.
Maker’s Strategy. At each round , Maker makes a sequential moves. In the jth step of the ith round (for ), he proceeds as follows:Let and denote the subgraphs of G formed by the edges claimed by Maker and Breaker, respectively. For each vertex , let and denote its degree in and , respectively.
- A vertex v is said to be dangerous if .
- The danger of v is defined by
- A vertex is called saturated if all its incident edges have been claimed, i.e.,
- Selects a vertex of maximum danger (i.e., one that maximizes over all );
- Claims an arbitrary free edge incident to .
This greedy strategy ensures that Maker continually reinforces the most vulnerable vertices, with the aim of eventually achieving degree at least k for every vertex in .
To analyze Maker’s minimum-degree strategy, we introduce the concept of average danger.
Consider the sth round of the game, for some integer , and let be a particular dangerous vertex at this stage. For each , denote by and the ith move of Maker and Breaker, respectively.
According to Maker’s strategy, the vertices were those of maximum danger immediately before the corresponding step j in Maker’s ith move.
For each , let
denote the multiset of vertices among
that are dangerous immediately before Maker’s th move. We define .
Note that the same vertex may appear multiple times in the above multiset, reflecting the fact that a given vertex can remain dangerous over several rounds.
Definition 2 (Average Danger).
We define the average danger of a multiset as follows:
- (i)
- is the average danger of the vertices in the multiset from Maker’s perspective, immediately before Maker begins his moves in round .
- (ii)
- is the average danger of the vertices in the multiset from Breaker’s perspective, immediately before round .
Note that round begins with Breaker’s move. Therefore, the values of and generally differ.
In the following two lemmas, we establish lower and upper bounds on the average danger. Maker plays according to the strategy defined in Section 2.1. To illustrate the definitions, we focus on rounds and (Figure 1):
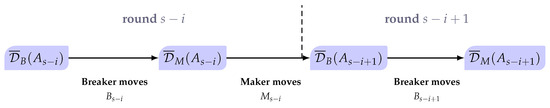
Figure 1.
Schematic representation of the evolution of the average danger during two consecutive rounds.
Proposition 1.
For every , the following inequalities hold:
Proof.
The first inequality is immediate since during Breaker’s moves the Maker degree of each vertex in remains unchanged, implying that the danger
for , can only increase.
For the second inequality, let
and fix an arbitrary vertex . Since u is dangerous just before Maker’s move, , its danger value
can only decrease during Maker’s move (because Maker’s actions increase or leave it unchanged).
Moreover, by the strategy, Maker selects the vertices — those with the highest danger values among all vertices in —one after the other in move . Consequently, the minimum danger among these chosen vertices (evaluated immediately before ) is at least as large as the danger of any vertex in .
After Maker’s move , the set of dangerous vertices is updated to ; however, since Maker’s moves do not increase danger, the maximum danger among the vertices in (measured immediately before Breaker’s move ) is no greater than the minimum danger among from before .
It follows that
which is the desired inequality. □
Definition 3.
Let be the function such that denotes the number of edges Breaker has claimed during the first rounds of the game, where both endpoints lie in the multiset .
Lemma 1.
Let , and let p be the number of edges claimed by Breaker during his move in round , with both endpoints . Then:
Proof.
Before his th move, Breaker has claimed exactly edges with both endpoints in . Thus, during round , he claims an additional p edges with both endpoints in , so that by the end of the round, the total is .
Recall that the multiset consists of the a vertices selected in round together with the vertices in ; that is,
where ⊎ denotes the multiset union.
There can be at most edges connecting pairs of vertices within . Moreover, each of the a vertices in this set can be incident with at most vertices from , contributing at most additional edges.
Hence, the total number of edges with both endpoints in after round is at most
Rearranging the terms yields
which is the desired inequality. □
Lemma 2.
For every integer i such that , the following inequalities hold:
- (i)
- (ii)
Proof.
- (i)
- The first inequality follows immediately from Proposition 1. During round , Breaker claims b edges, causing the total Breaker-degree of vertices in to increase by at most . Since is a linear function of these danger values, this implies
- (ii)
- Let , with p defined in Lemma 1. During Breaker’s move in round , the sumincreases by at most . Consequently, increases by at most . Applying Lemma 1, we derive:This completes the proof.
□
Corollary 1.
For every integer i with , the following holds:
Proof.
By Proposition 1, we have
Applying Lemma 2 then establishes the stated inequality in Corollary 1, and the proof follows. □
Claim 1.
We recall the following well-known inequalities involving the harmonic numbers
- For all ,
- For all integers with ,
Proof.
We use the fact that the function is positive and decreasing on .
- (a)
- Upper BoundLower Bound
- (b)
- We have
□
Lemma 3.
The following inequality holds:
Proof.
Before round one starts, neither Breaker nor Maker has claimed any edge; hence
We proceed as follows:
where in the last inequality we used . Rearranging yields
as claimed. □
Lemma 4.
Let . The following inequalities hold:
- (i)
- If , then
- (ii)
- If , then
Proof.
- (i)
- We start by observing that , since no edges have been chosen before round one. Then:where in the last inequality we used . Rearranging givesas required.
- (ii)
- First, recall that . Then, using Corollary 1 repeatedly, we obtain:Since and the function is decreasing on , we conclude thatThis completes the proof.
□
Theorem 1.
Suppose Maker follows his strategy described in Section 2.1. Then, the following assertions hold:
- (i)
- For every , there exists an integer such that, for all , Maker can construct a spanning subgraph of with minimum-degree at least , provided that:
- (ii)
- For every , there exists an integer such that, for all , Maker can construct a spanning subgraph of with minimum-degree at least k, given that:
Proof.
Assume for a moment that Maker loses the game, say in round s. Then, there exists a vertex with . Before round s, Breaker has claimed at least edges incident to , so we have at that moment. Since , it follows that . By definition of , we obtain:
Maker’s strategy prescribes easing a dangerous vertices in every round. Before round s, he has claimed exactly edges. We now show that .
Let be the multiset of dangerous vertices up to round . Each vertex in A can be eased at most k times, because is still a dangerous vertex with degree less than in Maker’s graph. Therefore, all the edges claimed by Maker until round are incident to vertices in A and each such vertex has Maker-degree at most . Since each vertex of can appear at most k times in the multiset A, we conclude that
- (i)
- Let and . By assumption, and . We distinguish between two cases.Case 1: .By Lemma 4, we have:Using and , we obtain:This leads to:Thus,But since , we obtain:which leads to a contradiction for sufficiently large n.Case 2: .From Lemma 4, we have:Using , we obtain:This yields the inequality:Isolating b gives:Since , it follows that:which clearly leads to a contradiction for sufficiently large n.
- (ii)
- Set , and assume thatBy Lemma 3, we have:Using the estimate , it follows that:This yields the inequality:Since , we derive:which yields a contradiction when n is large enough.
□
Theorem 2.
Let . Suppose that one of the following holds:
- (i)
- , , and ;
- (ii)
- , , and .
Then, following the strategy described in Theorem 1, Maker can, in at most rounds, construct a graph of minimum-degree at least k such that the Breaker-degree of any vertex v with Maker-degree less than k is at most .
Proof.
Maker follows the strategy described in Section 2.1. Suppose Breaker wins in round s, meaning that immediately after there is a vertex with and . Then,
Since this condition only affects Maker’s strategy, the conclusions of Lemmas 3 and 4 remain valid. Hence, we can proceed exactly as in the proof of Theorem 1, except that the definition of is adjusted to satisfy .
- (i)
- Let and . By assumption,We distinguish two cases.Case 1: . Arguing as in the proof of Theorem 1, Case 1 in part (i), we obtainSince and , it follows thatHence,Since and , the above inequality cannot hold for sufficiently large n.Case 2:. As before, we getand isolating b impliesFor sufficiently large n, this yields a contradiction with
- (ii)
- Set , and assume thatIn the same way as in the proof of Theorem 1 (ii), we have:Since , it follows that:This yields the inequality:For large n, this contradicts the assumption , since .
□
2.2. A Winning Strategy for Breaker
In this section, we present a strategy that enables Breaker to win the minimum-degree-k game.
For previous results on this topic, we refer the reader to the works of Hefetz et al. (2012), and of (Chvátal & Erdős, 1978), which have already been discussed in the introduction.
The Box Game
The Box game is played on k pairwise disjoint sets of possibly different sizes, with total size . These sets are often referred to as boxes, and their elements as balls.
Two players, called BoxMaker and BoxBreaker, alternately claim a and b elements, respectively. BoxMaker wins if he manages to claim all the balls in at least one box, while BoxBreaker aims to prevent this.
This setting can also be described as a game played on a hypergraph , where and . Let .
The family consists of pairwise disjoint sets whose total size is t. The board of the Box game is said to form a canonical hypergraph of type if the size difference between any two boxes satisfies for all . We denote this game by .
The Box Game was introduced in 1978 by (Chvátal & Erdős, 1978) for the special case of one-sided bias, that is, arbitrary a but .
For the general Box Game, (Hamidoune & Las Vergnas, 1987) provided necessary and sufficient conditions under which BoxMaker can win when BoxBreaker starts the game. Later, in 2012, Hefetz et al. (2012) established a sufficient condition for BoxMaker’s win in the case where BoxMaker moves first.
A typical winning strategy for BoxMaker is as follows: whenever Breaker claims a ball in a specific box, that box is considered lost for Maker. In the remaining boxes, Maker selects balls in such a way as to maintain a balancing condition, namely for all boxes . Maker continues in this manner until he reaches a box that contains fewer than a unclaimed balls.
We will use a sufficient condition for BoxMaker’s win in the game as proved by Hefetz et al. (2012).
Given positive integers a and b, define the function f as follows:
Lemma 5
(Lemma 6 in (Hefetz et al., 2012)). Let and k be positive integers satisfying and . Then,
Lemma 6
(Lemma 7 in (Hefetz et al., 2012)). If , then BoxMaker has a winning strategy for .
Here is our strategy for Breaker:
Let
Breaker wins if and only if he manages to ensure that
for some vertex .
He proceeds in two phases:
Step 1: Breaker builds a clique C of size at least h such that no vertex in C is incident to any edge claimed by Maker. That is, Maker does not touch any vertex of C during this step.
Step 2: Breaker selects a vertex , and claims free edges incident to v that are not in the clique C. As a result, the degree of v in Maker’s graph is strictly less than k, and therefore Maker cannot win.
Let denote the number of vertices in the clique C.
Breaker’s Strategy
First Step: Clique Construction
Set .
For each , Breaker constructs a clique , as large as possible, satisfying the following conditions:
- (a)
- is a clique in Breaker’s graph such that for every vertex just before Breaker’s ith turn. That is, no edge claimed by Maker is incident to any vertex in .
- (b)
- .
After constructing , Maker claims a edges.
The construction process terminates once a clique C of size at least h has been built.
Second Step: Playing the Box Game
Let C be the clique constructed in the first step, so that and for all . Immediately after the construction of C, Maker may touch at most a vertices in C. Let be the set of such vertices.
- (c)
- Let be a subset of size .
- (d)
- For each vertex , let denote the set of edges incident to v that are neither claimed by Maker nor part of the clique C.
- (e)
- Define the hypergraph , where and . This hypergraph models an instance of the BoxMaker–Breaker game, where the nodes are edges of .
- (f)
- Breaker plays as BoxMaker in the auxiliary box game , and makes the first move.
Lemma 7.
If Breaker, playing as BoxMaker, wins the box game
then he also wins the minimum-degree-k game.
Proof.
Let v be the vertex whose box is fully claimed by Breaker in the auxiliary box game. By definition of , at least free edges incident to v and lying outside the clique C are now owned by Breaker.
Inside the clique C of size h Breaker already controls all edges incident to v. Hence the total number of Breaker edges incident to v is
Consequently, Maker can be incident to at most edges at v. Thus, the degree of v in Maker’s graph is strictly less than k, and Breaker wins the minimum-degree-k game. □
We now show that, by following the strategy described above, Breaker can win the minimum-degree-k game.
The proof will also verify that each step of the strategy, from (a) to (f), can be correctly and effectively implemented. This includes the construction of increasingly large cliques disjoint from Maker’s graph, the maintenance of the degree condition during the game, and the successful reduction of the problem to an instance of the Box game where Breaker, acting as BoxMaker, is guaranteed to win.
Theorem 3.
For every , there exists such that for all , Breaker wins the minimum-degree-k game whenever
Proof.
The first step consists of at most h moves, where
and begins with . Suppose Breaker has already constructed cliques , with . After Breaker’s i-th move, Maker has claimed at most a edges incident with vertices in .
Claim 2.
There exist at least vertices that belong neither to the clique nor to Maker’s graph.
Proof of Claim 2.
At this stage of the game, the clique constructed by Breaker () contains at most vertices. Additionally, Maker’s graph involves at most vertices (since in each of the previous rounds, Maker claims at most a edges, each of which is incident to two vertices). Hence, the total number of vertices occupied (those belonging to and those claimed by Maker) is at most
Since and , for sufficiently large n, we have
Thus, at least vertices remain available, belonging neither to the clique nor to Maker’s graph, and Claim 1 is proven. □
Breaker uses Claim 1 iteratively to enlarge the cliques until he obtains a clique C with . At that point he switches to the auxiliary box game described in steps (c)–(f). By Lemma 7, a win for Breaker in this box game implies a win in the minimum-degree-k game.
To justify that Breaker can always extend the current clique, note first that implies Hence
Moreover,
With we therefore have, for sufficiently large n,
Consequently, in Breaker’s -st turn he can
1. claim all edges of the clique on the fresh vertices ;
2. claim at most additional edges between and .
Let X be the set of nodes of and let be the clique constructed on .
Breaker may claim the remaining edges arbitrarily. Maker, in contrast, can claim at most a edges incident to vertices in during his i-th turn. Consequently, there is at least one vertex, say w, with Maker-degree 0. Vertex w can then be used to construct a new clique satisfying and maintaining for all vertices .
In the second step, Breaker begins with a clique of size at least h, with for all . Maker can select edges incident to at most a vertices from C. Let be a subset of vertices with cardinality a, containing exactly these selected vertices. Breaker’s goal is then to claim at least edges incident to a particular vertex .
As a result,
so Maker cannot achieve minimum-degree k. Breaker thus wins the minimum-degree-k game.
We define the set , and clearly, . For each vertex , the number of edges incident to v not claimed by Maker and not included in C is . Let denote a subset of these edges with cardinality for each vertex . We construct the BoxMaker–Breaker hypergraph as with vertex set and edge set . Breaker begins playing first as BoxMaker in the auxiliary Box Game .
By Lemma 7, if BoxMaker has a winning strategy for , then Breaker wins the minimum-degree-k game on .
To establish that BoxMaker indeed has a winning strategy for , it suffices, according to Lemma 6, to demonstrate:
Given , we note that and for sufficiently large n. Applying Lemma 5, we have:
Recall that the harmonic numbers satisfy the following inequality (Chen, 2010).
Therefore, we obtain:
Hence, it remains to verify that:
Dividing by , then multiplying by a, gives:
leading finally to the condition:
Since this lower bound on b is asymptotically equivalent to , and given that , the above inequality indeed holds for sufficiently large n. □
We note a straightforward bound on b that guarantees Breaker’s win.
Remark 2.
If , then Breaker can win the minimum-degree-k game by claiming edges incident to a vertex v on his first turn, preventing Maker from reaching degree k at v.
We now determine the asymptotic optimal generalized threshold bias for this game, a direct consequence of Theorem 1, Theorem 3, and Remark 2:
Theorem 4.
- (i)
- If and , the asymptotic optimal threshold bias is .
- (ii)
- If and , the asymptotic optimal threshold bias is n.
Applying Theorem 4 with immediately yields the following result for the connectivity game:
Theorem 5.
- (i)
- If , the asymptotic optimal generalized threshold bias for the connectivity game is .
- (ii)
- If , the asymptotic optimal generalized threshold bias for the connectivity game is n.
As mentioned in the introduction, this resolves the open problem posed by Hefetz et al. (2012).
3. Conclusions and Open Problems
In this paper, we investigate the Maker–Breaker minimum-degree-k game and establish new upper and lower bounds on the threshold bias, thereby extending the foundational results of (Gebauer & Szabó, 2009). A key objective of our work is to identify and analyze cases where the threshold bias can be determined precisely in the asymptotic sense. Notably, we resolve an open problem posed by Hefetz et al. (2012) concerning the connectivity game, by determining its exact asymptotic threshold bias.
However, many cases remain in which the threshold bias is not yet fully characterized. For example, based on the proof of Theorem 1 and the result of Theorem 3, when , , , and , the threshold bias satisfies
This leaves a gap between the lower and upper bounds that still requires refinement. We believe that narrowing this gap would be of significant interest and would warrant further investigation.
Author Contributions
Conceptualization, M.E.O.; Methodology, A.F.; Formal analysis, A.F. and M.E.O.; Supervision, A.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received financial support by DFG-OA-Fonds der CAU.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflict of interest.
Nomenclature
Summary of main notations used in the paper:
| Symbol | Description |
| Complete graph on n vertices | |
| Bias parameters in the Maker–Breaker game | |
| Threshold bias function for fixed Maker power a | |
| Smallest integer that is greater than or equal to x. |
References
- Beck, J. (1982). Remarks on positional games. Acta Mathematica Academiae Scientiarum Hungarica, 40(1–2), 65–71. [Google Scholar] [CrossRef]
- Beck, J. (2008). Combinatorial games: Tic-Tac-Toe theory (Vol. 114). Cambridge University Press. [Google Scholar]
- Chen, C.-P. (2010). Inequalities for the Euler–Mascheroni constant. Applied Mathematics Letters, 23(2), 161–164. [Google Scholar] [CrossRef]
- Chvátal, V., & Erdős, P. (1978). Biased positional games. In Annals of discrete mathematics (Vol. 2, pp. 221–229). Elsevier. [Google Scholar]
- Clemens, D., Hamann, F., Mogge, Y., & Parczyk, O. (2021). Maker-Breaker games on randomly perturbed graphs. SIAM Journal on Discrete Mathematics, 35(4), 2723–2748. [Google Scholar] [CrossRef]
- Frieze, A., & Pegden, W. (2021). Maker-Breaker on digraphs. Journal of Graph Theory, 98(4), 653–661. [Google Scholar] [CrossRef]
- Gebauer, H., & Szabó, T. (2009). Asymptotic random graph intuition for the biased connectivity game. Random Structures & Algorithms, 35(4), 431–443. [Google Scholar] [CrossRef]
- Glazik, C., & Srivastav, A. (2022). A new bound for the Maker–Breaker triangle game. European Journal of Combinatorics, 104, 103536. [Google Scholar] [CrossRef]
- Hamidoune, Y. O., & Las Vergnas, M. (1987). A solution to the box game. Discrete Mathematics, 65(2), 157–171. [Google Scholar] [CrossRef]
- Hancock, R. (2019). The Maker–Breaker Rado game on a random set of integers. SIAM Journal on Discrete Mathematics, 33(1), 68–94. [Google Scholar] [CrossRef]
- Hefetz, D., Krivelevich, M., Stojaković, M., & Szabó, T. (2014). Positional games. Springer. [Google Scholar]
- Hefetz, D., Mikalacki, M., & Stojaković, M. (2012). Doubly biased Maker-Breaker connectivity game. Electronic Journal of Combinatorics, 19(1), P61. [Google Scholar] [CrossRef] [PubMed]
- Krivelevich, M. (2011). The critical bias for the Hamiltonicity game is (1 + o(1))n/ ln n. Journal of the American Mathematical Society, 24(1), 125–131. [Google Scholar] [CrossRef]
- Liebenau, A., & Nenadov, R. (2022). The threshold bias of the clique-factor game. Journal of Combinatorial Theory, Series B, 152, 221–247. [Google Scholar] [CrossRef]
- Mikalacki, M., & Stojaković, M. (2017). Winning fast in biased Maker-Breaker games. Electronic Notes in Discrete Mathematics, 61, 863–868. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).