Abstract
This paper deals with an autonomous cognitive network management architecture which aims at achieving inter-network (horizontal) and inter-layer (vertical) cross-optimization. The proposed architecture is based on the so-called Cognitive Managers transparently embedded in properly selected network nodes. The core of each Cognitive Manager are the so-called thinking modules, which are in charge of taking consistent and coordinated decisions according to a fully cognitive approach. The thinking modules potentially avail of information coming from both the transport and the service/content layers of all networks and, based on all this inter-layer and inter-network information, take consistent and coordinated decisions impacting the different layers, aiming at the overall inter-layer, inter-network optimization.
1. Introduction
In the framework of the most advanced telecommunication systems and projects the following kinds of horizontal interoperations are being pursued: service/content interoperation and transport interoperation (this last including physical interoperation, MAC interoperation and network interoperation):
- (A)
- The service/content interoperation allows the users to benefit, in a fully context-aware fashion, of heterogeneous services/contents provided by heterogeneous service/content providers. The target is to allow users (i) to discover the services/contents, even provided by heterogeneous service/content providers, which are appropriate for them in the present context, (ii) to aggregate the services/contents in order to create personalized services/contents meeting their expectations, (iii) to distribute the aggregated services/contents to properly selected people. Several research projects have defined SoA-based service and content convergence layers able to assure such interoperations. For instance, the FP6 Daidalos I and II IP projects [1] as for the service interoperation and the FP7 P2P-Next IP project [2] as for the content interoperation, have developed (i) advanced ontologies allowing a formal description of services/contents and (ii) basing on such ontological service/content descriptions, the procedures for context aware discovery, composition, re-composition and distribution of services/contents.
- (B)
- The transport interoperation allows to assure interoperation among heterogeneous access networks (in the following, also referred to as "underlying networks" or "underlying technologies”, or "networks"). The transport interoperation includes at least the physical interoperation (layer 1), the MAC interoperation (layer 2) and the network interoperation (layer 3). The target of these interoperations is to satisfy the requirements of users equipped with multi-mode terminals, in terms of Quality of Service (QoS), security and mobility, when roaming across heterogeneous underlying networks. Several research projects [3] have defined, at various layers (ranging from physical to network layer), transport convergence layers able to assure such interoperations. For instance, the FP7 IP OMEGA project [4] is implementing a " convergence layer" which, based on the monitoring of some appropriate parameters of the heterogeneous wireless underlying networks, takes appropriate control provisions aiming at achieving a flexible and efficient selection of the underlying networks which should support the connections (in particular, a connection can be supported even by more than one underlying network), as well as an optimized real-time routing of the packets among the selected (possibly heterogeneous) underlying networks (load balancing).
Although several research projects have already achieved valuable results in the framework of horizontal interoperation and optimization, at content, service, network, MAC, and physical levels, in general they have dealt with them in a separate, uncoordinated fashion: this particularly applies to service/content interoperations versus transport interoperations. No research project has still attempted to draw an unifying and coordinated perspective of all the horizontal interoperations; in other words, no research project has still attempted to add a vertical interoperation and optimization to the horizontal interoperations.
In this respect, this paper outlines an innovative architecture which achieves the collapsing of the service/content and transport convergence layers. According to such vision, this collapsing will be implemented through the design and development of a fully cognitive, technology-independent, distributed middleware embedded in some appropriate network entities (hereinafter simply referred to as Cognitive Middleware) which, based on the information collected by all the layers of the cooperating terminal, network and service providing elements, takes consistent and coordinated decisions impacting on all layers of all networks, according to a fully cognitive approach. In other words, the Cognitive Middleware becomes somehow the "embedded mind" of the network of networks.
In the author's view this approach, by extending the cognitive radio one [5] focused just on the physical layer, to all the layers of the protocol stack, could be a fundamental evolution step in the Future Internet direction [6]: on the one hand, in a short/medium term view, the new approach can support existing standards by gradually demanding to the Cognitive Middleware all horizontal and vertical interoperation control tasks already yielding fundamental advantages in terms of efficiency and flexibility. On the other hand, in a long term view (Future Internet perspective), the proposed approach could lead to the introduction of a new standard where all control functions relevant to all layers are demanded to such fully Cognitive Middleware, whilst other layers become just slaves of this layer, thus aiming at a complete inter-layer, inter-network optimization [7].
2. Proposed layering structure
The proposed architecture relies on a layering architecture as the one reported in Figure 1. This layering architecture example highlights the fact that the Cognitive Middleware is a middleware lying between the service/content layers and the transport layers; in the example reported in the figure these last are represented by the technology-independent IP layer and by the technology-dependent layers (1, 2 and 3) belonging to four different underlying access networks indicated, for convenience, with the letters A,..., D.
The figure also highlights that a key novelty is that the Cognitive Middleware takes information from both transport and service/content layers; such information can concern transport related performance parameters such as Bit Error Rates (BERs), transfer delays, supported traffic bit rates for each service class and each underlying network, as well as service/content related information such as the type of carried contents/services and the related characteristics. Then, based on proper (technology independent) elaborations of all this information, the Cognitive Middleware provides valuable outputs to both transport and service/content layers. Note that, according to the proposed vision, the traditional stack layering, becomes, as far as control is concerned, a sort of star layering with the Cognitive Middleware being the centre of the star.
In other words, the proposed approach aims at moving all "thinking" tasks related to all layers in a single transparent, flexible and efficient layer, namely the Cognitive Middleware layer. The advantages of this approach will be outlined in Section 4.
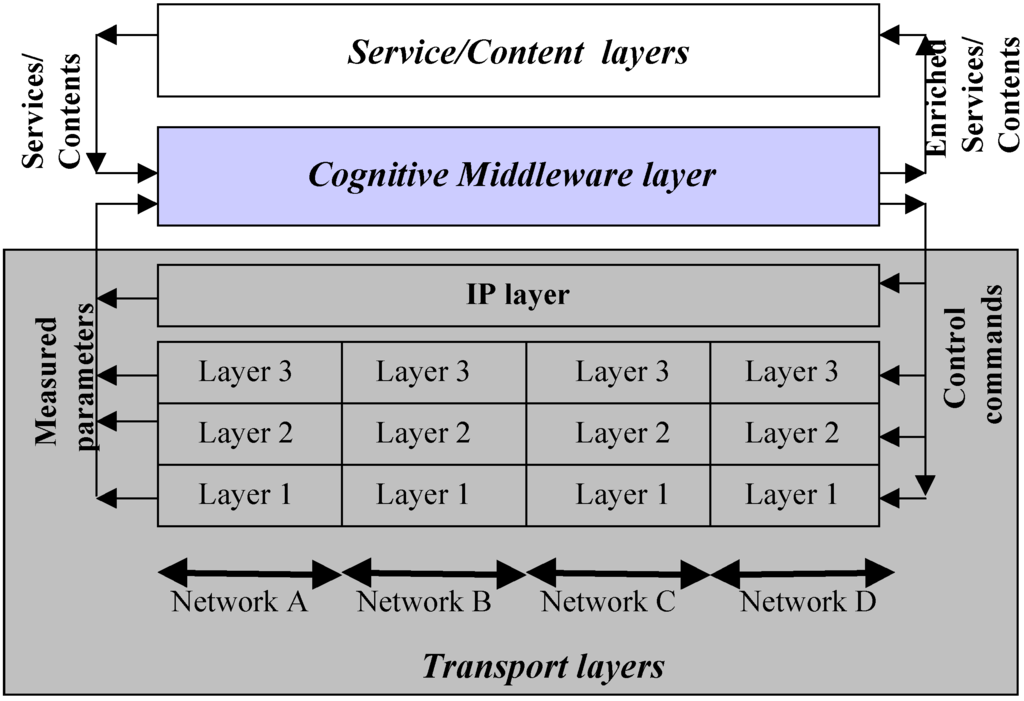
Figure 1.
Proposed layering architecture.
A fundamental Cognitive Middleware property is its transparency; this means that its insertion does not entail the modification of any of the Underlying Networks, IP, service/content/middleware layer procedures. Such transparency will be achieved thanks to the appropriate combination of non-invasive sensing and actuation techniques. In this respect, at least in a first exploitation phase, Cognitive Middleware control functionalities will be put into operation whenever they will be necessary either in order to assure interoperation, or to enhance unsatisfactory performance, whilst already existing control functionalities of the underlying access networks will be used in all other cases.
The flexibility of the Cognitive Middleware layer can be reached thanks to the extensive use of ontological models allowing the "translation" of heterogeneous data and parameters (belonging to heterogeneous networks) in homogeneous metadata which are properly handled (discovered, aggregated, elaborated, provided) in a context-aware fashion. This approach favors the decoupling from the specificity, on the one hand, of the lower layers (namely the underlying network transport layers) and, on the other hand, of the higher layers (namely the middleware/service/content layers). In addition, the middleware nature and the modular organization of the Cognitive Middleware makes system evolution possible via a Software Defined Radio (SDR) approach, i.e., the Cognitive Middleware can be upgraded via SDR-like techniques, without the need of modifying any piece of hardware.
The efficiency of the Cognitive Middleware layer mainly derives from the concentration of the thinking functionalities related to all the layers in a single layer. Therefore, in theory, a given thinking module can reason on the grounds of the complete vision of the overall information (measurements, data, services, contents) coming from all layers of all networks; in practice, to reduce the amount of data exchanged over the network, a subset of the overall potential information, dynamically selected according to the actual context, will be actually visible to the Cognitive Middleware, namely the one which is considered most valuable for the Cognitive Middleware algorithms. Nevertheless, when a sufficient statistics is selected as subset, the Cognitive Middleware can reason on the basis of on a much more complete (from both the inter-layer and inter-network points of view) information than traditional single layer, single network approaches. In addition, the technology/content/service independence of the Cognitive Middleware favors the adoption of advanced multi-objective algorithms, jointly addressing problems traditionally dealt with in a separate, uncoordinated fashions.
Therefore, the above-mentioned issues are expected to yield remarkable advantages both to the transport layers, in terms of improved QoS, security and mobility performance, and to the service/content layers in terms of enriched and more satisfactory services and contents.
3. Proposed Cognitive Middleware architecture
The Cognitive Middleware defined in the previous section is a distributed framework which will be realized through the implementation of appropriate Cognitive Middleware-based Agents (in the following referred to as Cognitive Managers) which will be transparently embedded in appropriate network entities (Mobile Terminals, Base Stations, Backhaul Network entities, Core Network entities).
Figure 2 outlines the high-level architecture of a generic Cognitive Manager, showing its interfacing with (i) the lower Transport layers (ii) the higher Service/Content layers and (iii) the other peer Cognitive Managers.
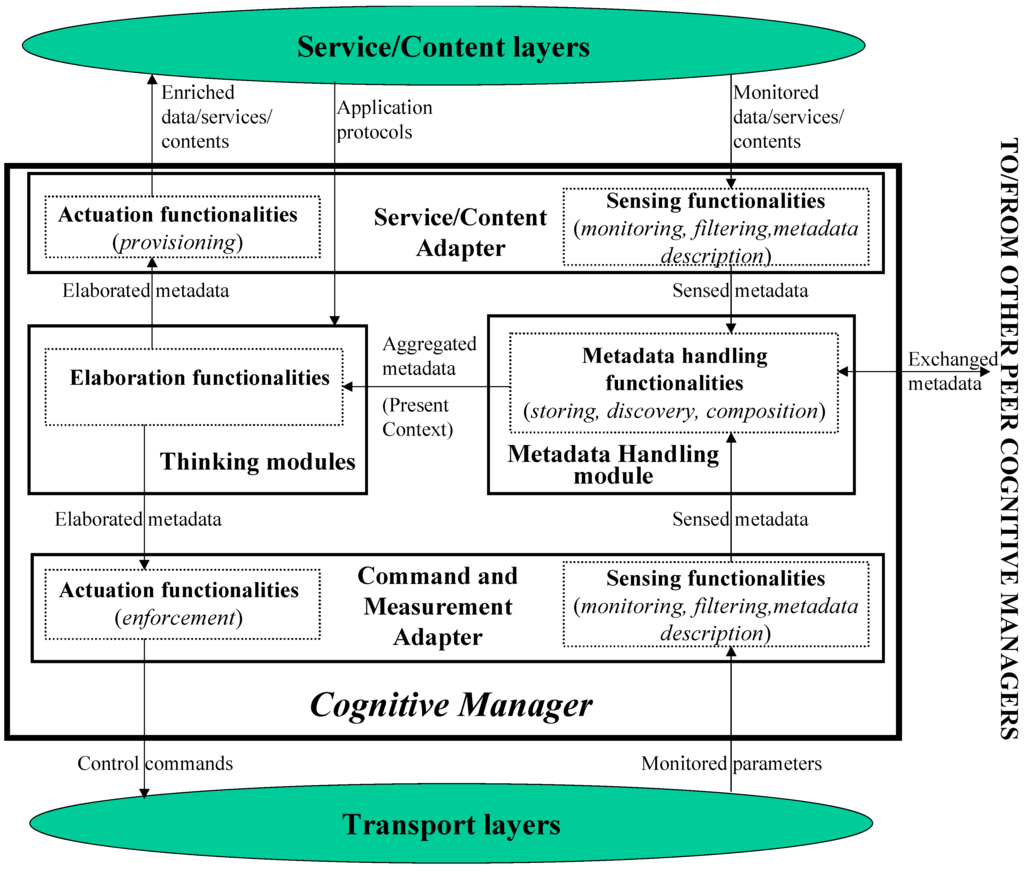
Figure 2.
Cognitive Manager architecture.
Figure 2 highlights that a Cognitive Manager will encompass four fundamental high-level functionalities, namely the Sensing, Metadata Handling, Elaboration and Actuation functionalities. The Sensing and Actuation functionalities are embedded in the "Adapters", namely the equipment which interface the Cognitive Module with the Transport Layers (Command and Measurement Adapter) and with the Service/Content layer (Service/Content Adapter); these adapters (and the corresponding sensing and actuation functionalities) must be tailored to the specific technologies of the underlying networks (i.e., to the specific transport layers) and to the specific interfaced service/content layers.
The Metadata Handling functionalities are embedded in the so-called Metadata Handling module, whilst the Elaboration functionalities are distributed among a set of Thinking modules. The Metadata Handling and the Elaboration functionalities (and in particular, the Thinking modules which are the core of the proposed architecture) are technology-independent and service/content-independent.
The roles of the above-mentioned functionalities are the following:
- Sensing functionalities: they are in charge of:
- (i)
- the monitoring and preliminary filtering of both data/services/contents coming from service/content layer (Sensing functionalities embedded in the Service/Content Adapter) and of transport layers parameters (Sensing functionalities embedded in the Command and Measurement Adapter); this monitoring has to take place according to non-invasive (transparent) techniques (e.g., "sniffing" and/or "probing packets" approaches) which do not interfere with the underlying network procedures),
- (ii)
- the formal description of the above-mentioned heterogeneous parameters/data/services/ contents in homogeneous metadata according to proper ontology based languages (such as OWL – Web Ontology Language) [8];
- Metadata Handling functionalities: they are in charge of the storing, discovery and composition of the metadata coming from the sensing functionalities and/or from metadata exchanged among peer Cognitive Managers, in order to dynamically derive the aggregated metadata which can serve as inputs for the thinking modules; these aggregated metadata form the so-called Present Context; it is worth stressing that such Present Context has an highly dynamic nature;
- Elaboration functionalities: they are embedded in a set of Thinking modules which are the core of the Cognitive Manager. These modules, following the various application protocols, having as key inputs the aggregated metadata forming the Present Context, produce elaborated metadata aiming at (i) controlling the transport layers, (ii) providing enriched data/services/contents to the service/content layers (iii) controlling the sensing, metadata handling and actuation functionalities, (iv) further detailing and enriching the Present Context (the issues (iii) and (iv), for clarity reasons, are not represented in Figure 2).Due to their paramount importance, these Thinking modules are detailed in section 4;
- Actuation functionalities: they are in charge of:
- (i)
- actuation of the thinking modules control decisions in the underlying networks (Enforcement functionalities embedded in the Command and Measurement Adapter; see Figure 2); the decision enforcement has to take place according to non-invasive (transparent) techniques (e.g. "cheating" approaches) which put in operation the control commands without interfering with the underlying network procedures,
- (ii)
- provisioning to the appropriate users of the enriched data/contents/services produced by the thinking modules (Provisioning functionalities embedded in the Service/Content Adapter; see Figure 2).
A so-called Supervisor and Data/Access Security Module (not shown for clarity reason in Figure 2) is embedded in each Cognitive Manager supervising the whole Cognitive Manager and, at the same time, assuring the security of the Cognitive Manager itself (in particular, to prevent the access to undesired users). The key role of this module will be to dynamically decide, on an application basis, (i) if the application in question has the necessary authorizations to access the Cognitive Manager, (ii) consistently with the application protocols, the Cognitive Manager functionalities which have to be activated to handle the application in question, as well as their proper activation/deactivation timing, (iii) the most appropriate configuration of the thinking modules which have to deal with the application in question, including, for instance, the dynamic selection of the most suitable algorithms, as well as the identification of the aggregated metadata which have to form the "present context" to be used as input for such thinking modules. In addition, this module will jointly address all issues aiming at assuring a secure data exchange. In particular, the security related features embedded in this module will include: end-to-end encryption, Authentication, Authorization and Accounting (AAA) at user and device level, and Service Security, Intrusion Detection and Denial of Service detection and countermeasures. Finally, for each application, the set of peer Supervisor and Data/Access Security Modules relevant to the Cognitive Managers involved in the handling of the application in question are responsible for assuring the satisfaction of the application requirements.
The selection of the most appropriate network entities in which the Cognitive Managers have to be inserted, as well as the actual design of the Cognitive Manager elaboration functionalities have to be performed case by case. In particular, a given network operator can manage several Cognitive Managers and organize them according to its own requirements in terms of business models, ethical, security, regulatory issues, etc. Nevertheless, thanks to its huge flexibility, the Cognitive Manager architecture could be the same in any network (such architecture will be just conceived according to the concepts just explained).
In this respect, note that the software implementing the various Cognitive Manager functionalities can be simply upgraded by means of software upgrades.
Also note that each thinking module can be dynamically disabled or enabled depending on whether or not the underlying/overlying networks perform the corresponding task in a satisfactory way.
4. Advantages entailed by the proposed Approach and Architecture
The proposed approach and architecture have the following key advantages which are hereinafter outlined in a qualitative way:
5. Thinking modules
The thinking modules are the core of the Cognitive Middleware: they include control functionalities related to all layers of the protocol stack. As already mentioned, the thinking modules control functionalities aim at assuring optimized vertical interoperation among layers and horizontal interoperation among networks. It is important to note that the overall network optimization carried by the thinking modules of various network nodes is done by using proper multi-object optimization methodologies using the most advanced concepts available in the literature and even developing ad hoc optimization theories.
The thinking modules will be designed as a modular set of functional, independent components that can be activated in real-time according to the requirements from the applications which have to be supported and to dynamically changing network management needs.
Modularity of the thinking modules is essential to improve the scalability of the proposed concept. In fact, the modular organization assures the possibility to add/upgrade/delete these modules via remote software updates that can be executed using SDR-like techniques, as well as to tailor the Elaboration functionalities to the actual need of the considered network. So, in a near future perspective, even low power devices, such as sensors or embedded devices, will be able to run the essential thinking modules. Thus, in the proposed vision, even the Internet of Things should be based on the Cognitive Middleware approach.
Thinking module modularity is also assured by the mutual independence of the algorithms running in the various modules. Nevertheless, the thinking modules will strictly cooperate one another and are expected to take consistent decisions. Simultaneous independence and cooperation of thinking modules can be achieved as the global knowledge of the network is conveyed through the Cognitive Middleware, but the input to a given module, namely the so-called Present Context, is formulated with respect to its functionalities. This allows to design simpler agents, while keeping their efficiency high, as such components are indirectly aware of both the present state of the network and the way of operating of the other modules, which allows them to take weighted optimization decisions.
Efficiency enhancement achieved by means of the thinking modules derives from the fact that the input to a given thinking module, namely the so-called Present Context, includes information potentially coming from all layers of all networks, as well as from the other network Cognitive Managers. As already outlined above, extensive use of ontology based languages (e.g. OWL, CoRaL) and utility-based optimizers is performed in order to manage the metadata which form the Present Context. In addition, the technology independence of the input information allows the use of abstract closed-loop methods for performing the network optimization (e.g., control-based methodologies such as gaming theory, predictive control, optimization, adaptive tracking, etc.).
The thinking modules could be classified according to the main layer of the protocol stack they impact on (apart for the Overall network optimization Module which impact on all the others):
In the following of this section, without claiming to be exhaustive, meaningful thinking modules examples are provided (note that the fundamental Supervisor and Data/Access Security Module has already been discussed in Section 3).
5.1. Physical thinking modules
Adaptive modulation and coding enable robust and spectrally-efficient transmission over time-varying channels. Basing on radio channel measurements, provided by the physical layers, properly combined with information related to the upper layers (in particular, the kind of services/contents to be carried), the innovative algorithms embedded in this module has to jointly select the most proper frequency band, as well as dynamically adapt the modulation, coding, transmission power and data rate (some of these tasks will be performed in strict cooperation with the MAC-Physical cross-layer module), aiming at increasing the supported throughput and, at the same time, at enhancing the Link Availability (i.e. at meeting the desired user QoS and security requirements).
Moreover, this module cooperates with the Access Selection module (see below), for the dynamic selection of the most appropriate access network; for this task, it needs, as input, aggregated metadata which consider the radio channels of all the candidate heterogeneous access networks.
5.2. MAC and Traffic Control Module
Scheduling, congestion control and dynamic capacity allocation can be fully integrated in a unique algorithm [9] which, basing on the feedback information received from the metadata describing the queue status and the present bit rate supported by the underlying networks, jointly decides (i) the capacity-to-terminals assignments, (ii) the packets to be admitted/dropped/downgraded, (iii) the packet priorities. The closed-loop approach and the joint consideration of procedures which are usually dealt with in a separate and uncoordinated fashion are expected to enhance system robustness and efficiency. Note that efficiency enhancement is possible thanks to the adoption of abstract control-based methodologies such as optimal control turned to the maximization of proper performance indexes, or adaptive tracking of ideal balance; the adoption of these advanced and innovative techniques is possible just in virtue of the technology-independence of the Cognitive Middleware approach.
In addition, the MAC and Traffic Control module has to focus, among others, on cross-layer MAC-PHY and MAC-TCP/IP optimizations.
5.3. Network Control and Access Selection Module
The Network Control and Access Selection Module is in charge of jointly dynamically deciding:
- (1)
- at each application set-up attempt, the most appropriate QoS, mobility and security requirements to meet the target user expectations (including the target user Quality of Experience, the cost the user is ready to pay, etc.) (intelligent requirement identification);
- (2)
- the most appropriate available access network(s) (if any) able to support the application satisfying its requirements identified in issue (1), as well as the most appropriate supporting flows (intelligent access and flow selection);
- (3)
- during the connection lifetime, the (dynamically varying) most proper access network(s) and relevant flows which has/have to support the connection, thus triggering possible traffic/quality/content/service driven vertical handovers (inter-network mobility);
- (4)
- the most appropriate virtual paths which have to support the in progress flows in the selected access network(s) (load balancing).
The proposed approach will make possible to jointly perform the four above-mentioned tasks which, in current implementations and works in the literature, are generally dealt with in separate, uncoordinated fashion by different procedures (namely, inter-domain selection/reselection, connection admission control, routing/load balancing).
The algorithms embedded in this thinking module, basing on a knowledge of the present underlying access network status which could include the present performance of the various virtual paths, as well as of the type of contents/services to be carried (clearly, the information actually available depends to the deployed sensing functionalities), jointly decide, in a dynamic way, the connections-to-access-network assignments, the connections-to-flows assignments and the flows-to-virtual-paths assignments, also deciding the possible triggering of vertical handovers. It is fundamental stressing that these decisions have be taken by using proper multi-object optimization methodologies using the most advanced concepts available in the literature and even developing ad hoc optimization theories.
5.4. Service and Content Management modules
The Service and Content Management modules play the following two fundamental roles:
- (α)
- Enriched Data/Services/Contents provision consisting in (i) deciding the services and contents to be monitored and filtered, (ii) deciding their possible aggregations, (iii) enriching the aggregated information through appropriate elaboration, (iv) deciding the most appropriate destinations the enriched data/services/contents have to be provided to;
- (β)
- Context management consisting in (i) dynamically monitoring, filtering and discovering from the surrounding environment parameters related to services/contents (e.g. the requirements and the characteristics of the services/contents, the nature of the supported contents), networks (e.g. current underlying network availability, current queue length, current delays, current BER, presently available services/contents and related characteristics) and users (e.g. user profile, user requirements, current user location, current user battery status, user screen resolution, current user connection speed, distance of the user from a destination), and (ii) properly aggregating them, also in the light of the output of other thinking modules, to form the so called Present Context (so, such a context includes service, content, network and user contexts) which is the key multi-layer, multi-network input for all the thinking modules. Note that the fully cognitive nature of the proposed approach just lies in the fact that the various thinking modules can avail of such context.
More in detail, taking into account the above-mentioned issues, the following Service and Content Management thinking modules can be considered:
5.4.1. Monitoring, filtering, storing, discovering and composition module
This module on the basis of the application protocols (inputs from the Service/Content layers), as well as of the Present Context, is in charge of jointly performing the following fundamental and strictly related tasks:
- -
- dynamically managing the advertisement information about the potentially available metadata: these last are the network/user/service/content data/parameters which could be monitored by means of the sensing functionalities. As a matter of fact, the potentially available metadata need to be advertised and indexed in order to be recovered whenever they are needed. Note that the advertisement information has to be properly exchanged among Cognitive Managers so that any Cognitive Manger can be aware of (i) which metadata are potentially available in the various networks, (ii) which Cognitive Managers handle the potentially available metadata, (iii) how and at which conditions it is possible to actually avail of such metadata;
- -
- dynamically deciding which metadata (among the potentially available ones, which have been advertised as mentioned in the previous issue) have to be discovered and the relevant filtering and storing criteria; then, this module has to accordingly control the discovery, filtering and storing functionalities (included in the Metadata Handling block represented in Figure 2), which are in charge of actually discovering, filtering and, possibly, storing the above-mentioned metadata. The best algorithms which the discovery and filtering functionalities have to put into operation, are dynamically selected by the Supervisor module;
- -
- dynamically deciding the criteria for the aggregation of the discovered metadata in order to generate the aggregated metadata which form the Present Context which, as already explained, is the multi-layer, multi-network information serving as key input for all thinking modules. These criteria are put into operation by the composition functionalities included in the Metadata Handling block represented in Figure 2 which generates the Present Context.
5.4.2. Enriched Services/Contents module
This module consists of a set of routines; each of these routines is specialized on a given application and is in charge of enriching, through proper context-driven elaborations, the services/contents to be provided to the users.
For instance, following a specific user query, the associated routine can be in charge of ranking the aggregated metadata relevant to the query in question, according to the relevance to the user profile, the actual context and learning from the user behaviour; then, the module can decide to provide to the users just the N aggregated metadata with the highest ranking with N being selected taking into account the present available bandwidth resources.
Therefore, the outputs of this module are application/user-specific elaborated metadata which are forwarded to the provisioning functionalities. These last are in charge of actually providing the elaborated metadata to the end user device(s), by using a collection of provisioning paradigms, architectural solutions and protocols (OSGi, UPnP, Web services, etc.) to dynamically setup the device, install, configure and make it properly run the required services and contents.
6. Conclusions
This paper proposes a novel solution for horizontal and vertical interoperation in order to achieve the full coordinated cooperation of the various layers of heterogeneous networks, aiming at interlayer and inter-network optimization.
The proposed architecture is based on Cognitive Modules which can be transparently embedded in selected network entities. These Cognitive Modules have a modular organization which is claimed to be flexible and scalable, thus allowing a smooth migration.
The thinking modules, which are the core of the Cognitive Managers, can potentially benefit from information coming from all layers of all networks and can take consistent and coordinated context-aware decisions impacting on all layers. Clearly, which thinking modules have to be activated, which input information has to be provided to the thinking module, the algorithms the thinking modules will be based on, have all to be carefully selected case by case; nevertheless, the proposed architecture has an inherent formidable point of strength in the concentration of all thinking tasks in a single technology/service/content independent layer, opening the way, in a natural fashion, to inter-network, inter-layer optimizations.
Acknowledgements
This paper is based on the work performed by the author in the framework of the FP7 COMETS project proposal. The authors wish to thank all the COMETS partners and, in particular Claudio Becchetti (Selex-Com), Petri Mahonen (University of Aachen), Giuliano Salcito (Radiolabs), Marco Castrucci and Antonio Pietrabissa (University of Roma "Sapienza"), for their important suggestions.
References
- Designing Advanced Interfaces for the Delivery and Administration of Location independent Optimised personal Services II. European Union FP6 IST DAIDALOS II Project, November 2003-December 2008. www.ist-daidalos.org (accessed on December 2008).
- Next Generation Peer-to-Peer Content Delivery Platform. European Union FP7 ICT P2P-Next Project, January 2008-December 2011. www.p2p-next.org (accessed on December 2009).
- Becchetti, L.; Delli Priscoli, F.; Mahonen, P.; Muñoz, L.; Inzerilli, T. Enhancing IP Service Provision over Heterogeneous Wireless Networks: a Path Towards 4G. IEEE Commun. Mag. 2001, 39, 74–81. [Google Scholar] [CrossRef]
- Home Gigabit Access. European Union FP7 ICT OMEGA Project, January 2008-December 2010. www.ict-omega.eu (accessed on December 2009).
- Mitola, J. Cognitive radio: making software radio more personal. IEEE Pers. Commun. 1999, 6, 48–52. [Google Scholar] [CrossRef]
- Shenker, S. Fundamental design issues for the future Internet. IEEE J. Sel. Areas Commun. 1995, 13, 1176–1188. [Google Scholar] [CrossRef]
- Shakkottai, S.; Rappaport, T.; Karlsson, P. Cross-layer design for wireless networks. IEEE Commun. Mag. 2003, 41, 74–80. [Google Scholar] [CrossRef]
- Nirenburg, S.; Raskin, V. Ontological semantics. MIT Press: Boston, MA, USA, 2004. [Google Scholar]
- Delli Priscoli, F. A Control Based Solution for Integrated Dynamic Capacity Assignment, Congestion Control and Scheduling in Wireless Networks. Eur. J. Control 2010, in press. [Google Scholar]
© 2010 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/3.0/).