SAVE: Securing Avatars in Virtual Healthcare Through Environmental Fingerprinting for Elder Safety Monitoring †
Abstract
1. Introduction
- Authentication Framework: We introduce SAVE, a comprehensive framework for securing avatars in virtual healthcare environments using environmental fingerprinting based on ENF signals.
- Implementation in Elder Care: We demonstrate the practical application of SAVE in a lightweight Metaverse-based nursing home designed to monitor elderly people living alone, showcasing its relevance to critical healthcare applications.
- Security Evaluation: We evaluate SAVE against multiple attack scenarios, including unauthorized device access, device ID spoofing, and replay attacks, providing empirical evidence of its effectiveness in detecting Deepfake attempts.
- Usability Considerations: We address the unique requirements of elder care applications, ensuring that security enhancements do not introduce additional complexity for elderly users or healthcare providers.
2. Background and Related Works
2.1. Metaverse Security and Authentication
2.2. ENF Signals in Security Applications
- Ubiquitous in environments with electrical infrastructure;
- Difficult to predict or artificially replicate;
- Temporally unique, creating time-specific signatures;
- Regionally consistent across connected power grids.
2.3. Digital Twins in Healthcare
2.4. Elder Care Monitoring Systems
2.5. Research Gap
- Behavioral Biometrics: These systems monitor patterns like keystroke dynamics, mouse movements, gait, or touchscreen interactions. While effective for detecting user anomalies, these data streams are increasingly susceptible to generative AI models that can mimic legitimate user behavior.
- Physiological Biometrics: This approach uses signals from wearable devices, such as electrocardiography (ECG) or photoplethysmography (PPG), to create a continuous and unique physiological signature. This is a strong method, but it is vulnerable to sophisticated attacks that can synthesize or replay biometric data, as noted in recent security analyses. It also places the burden on the user to consistently wear a specific monitoring device.
- Context-Aware Authentication: These methods use environmental cues like GPS location, IP address, or connected Wi-Fi networks to verify the user’s context. However, these digital context markers are often easy to spoof (e.g., via VPNs or GPS spoofing tools) and fail to validate the integrity of the physical environment at a granular level.
- Authenticating the Environment, Not the User: By using ENF signals, SAVE verifies that the data originates from the correct physical location at the correct time. This is a critical distinction, as an attacker who has compromised a device’s keys and can even synthesize a user’s biometrics cannot remotely forge the real-time ENF signal of the patient’s home.
- Ensuring Passivity and Usability: The system operates in the background without requiring any action from the elderly user, making it uniquely suited for elder care applications where ease of use is essential.
- Providing Inherent Replay Attack Resistance: Because the ENF signal is time-variant, data packets from a previous session, even if legitimately captured, will have an ENF fingerprint that does not match the server’s real-time reference signal, rendering replay attacks ineffective.
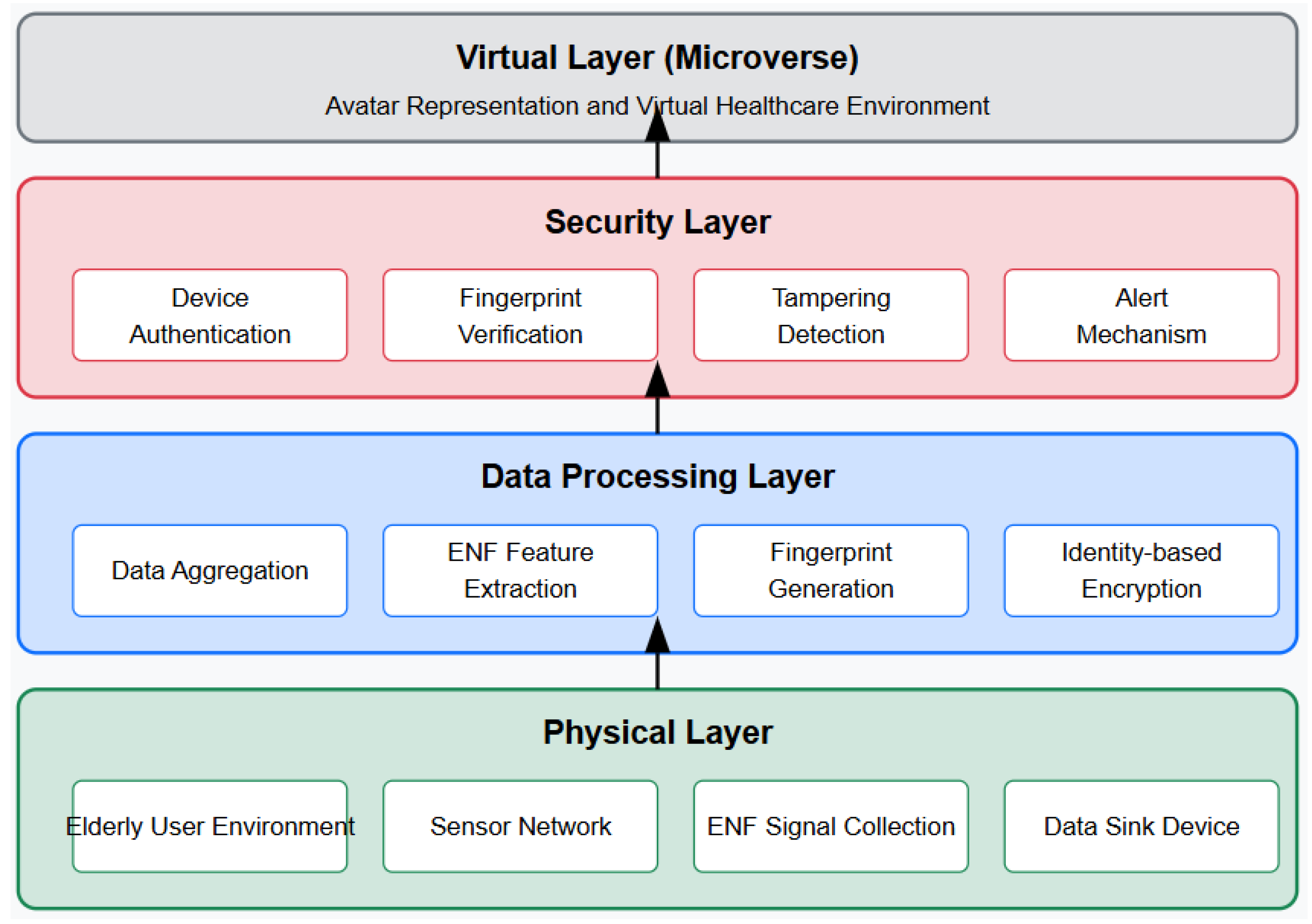
3. SAVE: System Design and Architecture
3.1. System Overview
3.2. ENF-Based Environmental Fingerprinting
3.3. Secure Authentication Framework
3.3.1. Elliptic Curve Cryptography (ECC)
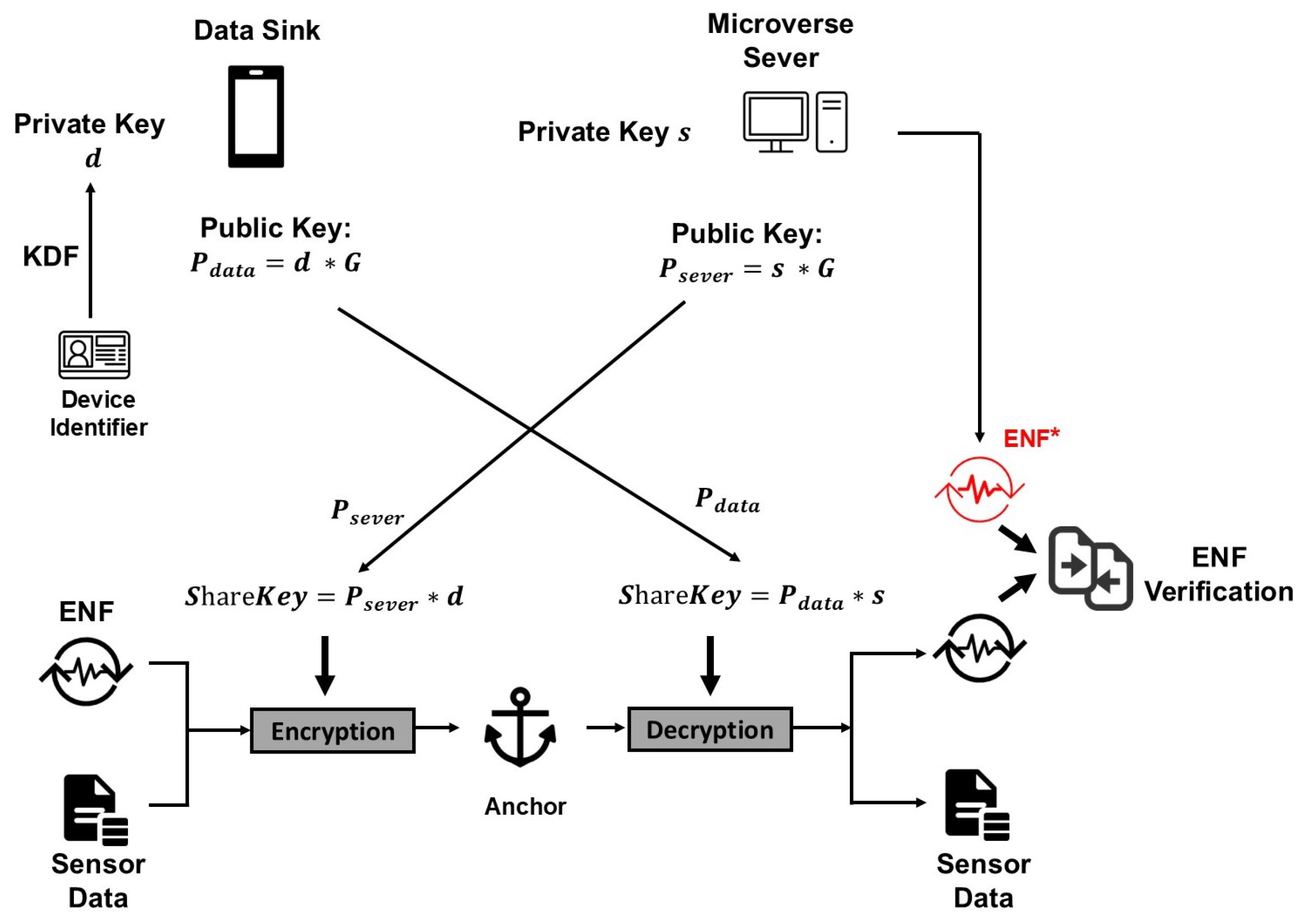
3.3.2. ECDH-Based Key Exchange Scheme
- The data sink generates the private key d based on the device identifier using the Key Derivation Function (KDF) and computes its public key: .
- The server generates a random private key s and computes its public key: .
- The data sink and the server exchange their public keys.
- The data sink computes the shared key: .
- The server computes the shared key: .
- Both parties now possess the same shared secret key for symmetric encryption and decryption.
3.4. Threat Model and Security Properties
3.4.1. Threat Model
- Intercept and Analyze Traffic: Eavesdrop on all communication between the data sink devices () and the Microverse Server (S).
- Modify, Replay, and Inject Messages: Arbitrarily alter, drop, delay, or replay previously captured messages. The adversary can also inject newly created messages into the network. This capability is assessed by our evaluation of replay attacks.
- Compromise Edge Devices: In the most severe case, the adversary may compromise a data sink device to gain access to its cryptographic keys, including its unique identifier and the derived private key . Our framework is designed to detect attacks even under this condition.
- Generate Deepfake Data: The adversary can use sophisticated AI techniques to generate synthetic sensor data () that appears legitimate, such as faking a normal heart rate to hide a medical emergency.
3.4.2. Cryptographic Properties for Long-Term Robustness
- Confidentiality: The privacy of sensitive patient data during transmission is ensured by symmetric encryption (e.g., AES). The ECDH protocol establishes a unique session key for each communication, meaning an adversary who intercepts the ciphertext cannot access the underlying health data without compromising the session key.
- Authenticity and Integrity: SAVE ensures authenticity at two levels:
- Device Authenticity: The use of an ECDH key exchange, where the device’s private key is derived from its unique ID, cryptographically authenticates the source of the data. Only the legitimate device can compute the correct shared secret to create a valid ciphertext that the server can decrypt.
- Spatio-Temporal Authenticity: This is the core innovation of SAVE. The ENF fingerprint serves as a physical-world anchor, verifying that the data was generated not only by the correct device but also at the correct physical location and time. This property is critical for defeating deepfake and replay attacks, as forged data will lack the correct, time-synchronized ENF signature.
- Forward Secrecy: The protocol is designed to provide forward secrecy. By having the server generate a random, ephemeral private key s for each session, the compromise of a device’s long-term private key at some point in the future will not compromise the confidentiality of past communications. Each session is protected by a unique shared key that cannot be re-derived from the long-term keys alone.
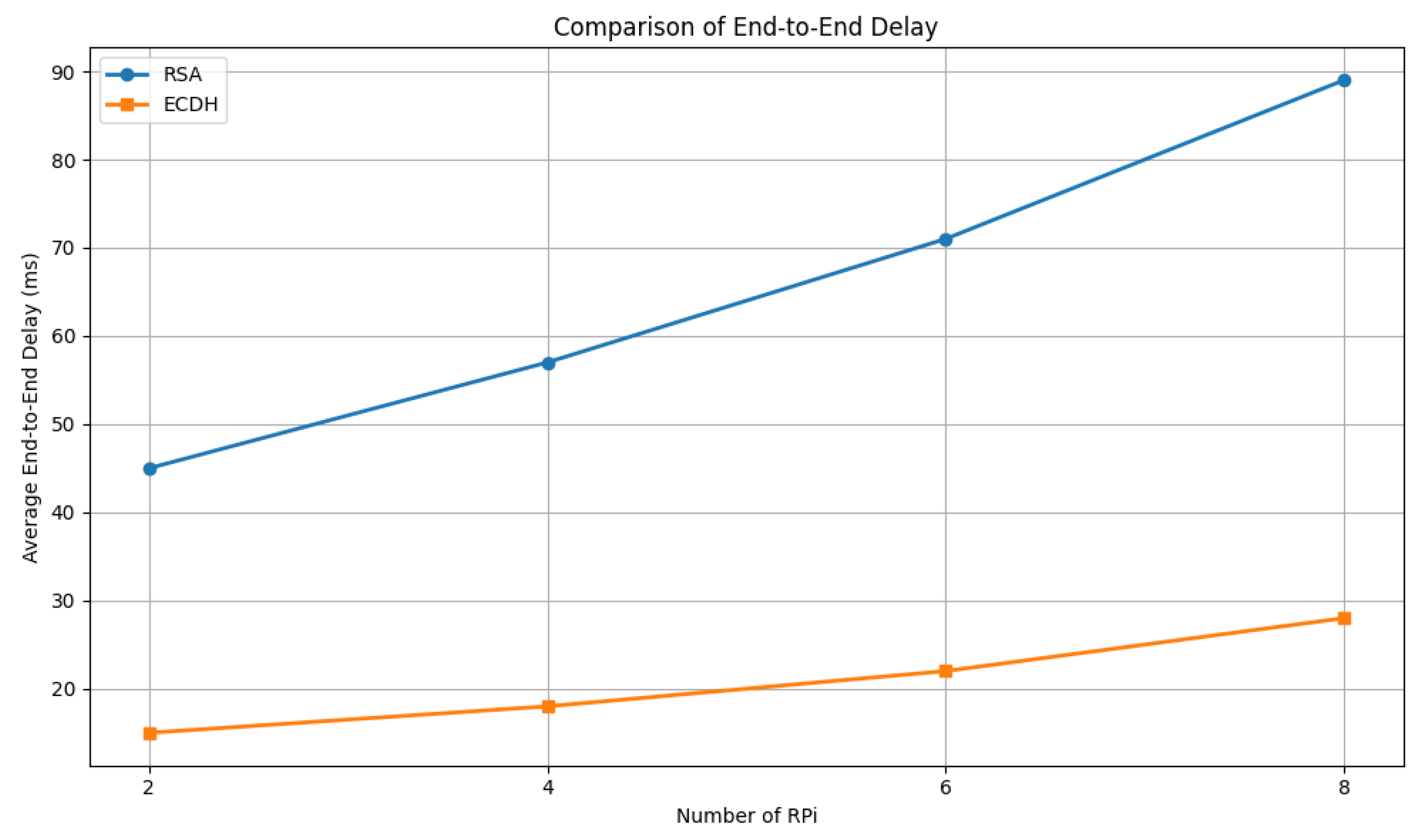
- Efficiency and Scalability: Long-term robustness also depends on practical feasibility. ECC was chosen specifically for its high security with much smaller key sizes and lower computational overhead compared to alternatives like RSA. This efficiency is critical for deployment on resource-constrained IoT devices used in healthcare. Our scalability evaluation confirms that the system maintains low end-to-end delay even as the number of devices increases, ensuring its long-term viability in expanding healthcare networks.
3.5. Formal System Model
3.5.1. System Entities and Components
- A set of Data Sink Devices , where each is an edge device (e.g., Raspberry ) deployed in the elderly user’s environment. Each device is assigned a unique identifier .
- A central Microverse Server S, responsible for receiving data, performing verification, and updating the virtual environment.
- An Adversary , who may attempt to compromise the system by intercepting, modifying, or forging data packets.
3.5.2. Cryptographic and Environmental Primitives
- Elliptic Curve Cryptography (ECC) Parameters: A public set of domain parameters for ECC, , defining the finite field , the curve equation , a base point G of prime order n, and a cofactor h. All point operations are performed in the additive group of points on this curve.
- Key Generation and Exchange:
- Key Derivation Function (KDF): A function that maps a device identifier to a private key .
- Elliptic Curve Diffie-Hellman (ECDH): A protocol to establish a shared secret between a device and the server S.
- Symmetric Encryption Scheme: A pair of algorithms where
- : An encryption algorithm that takes a shared key and a message M to produce a ciphertext C.
- : A decryption algorithm that takes a shared key and a ciphertext C to produce the original message M.
- Environmental Signal Processing:
- ENF Signal: We denote the Electric Network Frequency signal captured over a time window by a device as .
- Fingerprint Generation Function (): A function that extracts a unique feature vector, or fingerprint, , from the raw ENF signal. This function encapsulates techniques such as the Short-time Fourier Transform (STFT).
- Correlation Function (Corr): A function that computes the similarity (e.g., Pearson correlation coefficient) between the fingerprint from device and the reference fingerprint from server S.
3.5.3. Framework Phases
- Phase 1: System Initialization and Key Generation
- The Microverse Server S publishes the global ECC parameters .
- Each device generates its long-term private key from its unique identifier:
- Each device computes its corresponding public key :The pair constitutes the device’s key pair. The public key is securely registered with the server S.
- The server S generates its own long-term private and public keys, , where .
- Phase 2: Data Aggregation and Environmental Fingerprinting (at Device )
- Collects Sensor Data: Acquires raw sensor data from its attached sensors (e.g., camera, thermometer).
- Captures ENF Signal: Records the local ENF signal over a predefined time window.
- Generates ENF Fingerprint: Computes the environmental fingerprint :
- Constructs Data Packet: Assembles a message packet containing the sensor data, the ENF fingerprint, a timestamp, and its identifier:where denotes concatenation.
- Phase 3: Secure Data Transmission (ECDH-based Encryption)
- To transmit securely, and S establish a session-specific shared secret key using the ECDH protocol.
- Device computes:
- Server S computes:
- Device encrypts the message packet using the shared key:
- transmits the ciphertext to the server S.
- Phase 4: Server-Side Verification and Authentication
- Decryption: It computes the same shared key and decrypts the ciphertext to recover the message packet:This yields the components . The server first validates that matches the claimed sender identity.
- Reference Fingerprint Generation: Concurrently, the server captures its own local ENF signal for the corresponding timestamp and generates a reference fingerprint:
- Environmental Authentication: The server computes the correlation between the received fingerprint and its reference fingerprint:
- Decision Logic: A verification function determines the authenticity of the data based on a predefined correlation threshold :
- State Update:
- If , the data is deemed authentic. The server uses it to update the corresponding avatar’s state in the Microverse.
- If , the data is flagged as suspicious. The server discards the data and triggers an alert mechanism as described in Section 4.3. This outcome indicates a potential deepfake, replay, or man-in-the-middle attack.
4. Implementation in Virtual Elder Care
4.1. Microverse-Based Nursing Home Environment
4.2. Sensor Deployment
4.2.1. Hardware Configuration
- Motion Sensors: Passive Infrared (PIR) and ultrasonic motion sensors are installed at key locations (e.g., near beds, doors, and bathrooms) to detect movement patterns, presence, and activity levels. These are essential for behavioral profiling and fall detection.
- Smart Cameras: Depth and RGB (red, green, and blue) cameras with embedded AI capabilities are deployed to perform real-time skeletal tracking, posture analysis, and anomaly detection. Cameras are installed at high vantage points to maximize coverage while preserving privacy through body-skeleton abstraction.
- Thermometers: Non-contact infrared thermometers continuously measure ambient and body surface temperature. These sensors are placed in living quarters and integrated with bedside systems to monitor possible signs of fever or thermal stress.
- Humidity Sensors: Capacitive humidity sensors are used to assess the level of moisture in the environment, ensuring that the conditions of the room remain within the medically recommended comfort thresholds for respiratory health.
4.2.2. Data Collection Parameters
- Motion Sensors: Sampled at 1–2 Hz, sufficient for capturing discrete activity events without excessive data redundancy.
- Smart Cameras: Operate at 15–30 frames per second (fps), allowing smooth and accurate skeletal modeling and behavior inference.
- Thermometers: Sampled every 0.1 s to capture gradual temperature fluctuations while saving energy.
- Humidity Sensors: Sampled every 1–2 min, as the environmental humidity changes slowly over time.
4.3. Security Integration
5. Experimental Evaluation
5.1. Experimental Setup
5.2. Attack Scenarios
- An attacker tries to feed fake data but has no information about the device ID (private keys) nor the elliptic curve;
- An attacker obtained all information about encryption/decryption and intercepts the channel with deepfake data, but is unaware of or does not have sufficient/correct information about the current ENF signals;
- An attacker obtained all information about encryption/decryption from both agents and tampered with the user’s behavior description data using intercepted data packets from earlier communication.
5.3. Data Profile and Validation
5.4. Analysis of Results
5.4.1. Attack Detection Effectiveness
5.4.2. Scalability Evaluation
- Encryption Time: The time required to perform encryption of the plain text sensor data on the RPi5;
- Transmission Time: The time taken to transmit the encrypted message over the MQTT protocol from the RPi5 to the server;
- Decryption Time: The time required to decipher the message received on the server.
6. Discussions
6.1. Key Findings and Insights
6.2. Limitations
6.3. Ethical and Regulatory Concerns
6.4. Future Work
- Sensing and Sampling: Sense temperature and humidity with cheap digital sensors (e.g., DHT22) and sample them continuously at a low rate (e.g., 0.1–1 Hz). This rate is fast enough to capture the slow-moving dynamics of HVAC cycles and background thermal changes without adding too much data overhead.
- Feature Extraction: From raw time-series data, extract discriminative features in 5–15 min sliding windows. High current order three features, such as short-time mean, variance, and spectral energy, were used to provide a consistent, but distinguishing model of the local environmental state at any time.
- Authentication and Fusion: The extracted temperature and humidity feature vectors are compared with trusted baselines, specific to the location. This analog could be performed using techniques such as Pearson correlation or dynamic time warping (DTW) to adjust for small temporal differences. The decision to authenticate was made based on whether a similarity score exceeded a pre-set threshold. In a fusion strategy, an intuitive policy would enforce the validation of the primary ENF fingerprint and the second microclimate fingerprint (logic AND) to accept an authentication request, making the plot of an attacker to spoof multiple, independent environmental signals at the same time much more challenging.
6.5. Theoretical and Practical Implications
6.5.1. Theoretical Implications
6.5.2. Practical Implications
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Correction Statement
Abbreviations
| AES | Advanced Encryption Standard |
| AI | Artificial Intelligence |
| DHKE | Diffie–Hellman Key Exchange |
| DIHM | Distributed Intelligent Health Monitoring |
| DSA | Digital Signature Algorithm |
| DT | Digital Twin |
| DTW | Dynamic Time Warping |
| ECC | Elliptic Curve Cryptography |
| ECDH | Elliptic Curve Diffie–Hellman |
| ECDLP | Elliptic Curve Discrete Logarithm Problem |
| ENF | Electric Network Frequency |
| FNR | False Negative Rate |
| FPR | False Positive Rate |
| FPS | Frames per Second |
| GUI | Graphic User Interface |
| HAR | Human Activity Recognition |
| HVAC | Heating, Ventilation, and Air Conditioning |
| IBE | Identity-based Encryption |
| IoMT | Internet of Medical Things |
| IoT | Internet of Things |
| KDF | Key Derivation Function |
| LAN | Local Area Network |
| LSTM | Long Short Term Memory |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| PIR | Passive Infrared |
| PoENF | Proof of ENF |
| PRNG | Pseudorandom Number Generator |
| PUF | Physical Unclonable Functions |
| RGB | red, green, and blue |
| RPi | Raspberry Pi |
| RSA | Rivest–Shamir–Adleman |
| STFT | Short-time Fourier Transform |
| TPM | Trusted Platform Modules |
| UE5 | Unreal Engine 5 |
| UMG | Unreal Motion Graphics |
References
- Bibri, S.E. The social shaping of the metaverse as an alternative to the imaginaries of data-driven smart Cities: A study in science, technology, and society. Smart Cities 2022, 5, 832–874. [Google Scholar] [CrossRef]
- Musamih, A.; Yaqoob, I.; Salah, K.; Jayaraman, R.; Al-Hammadi, Y.; Omar, M.; Ellahham, S. Metaverse in healthcare: Applications, challenges, and future directions. IEEE Consum. Electron. Mag. 2022, 12, 33–46. [Google Scholar] [CrossRef]
- Wang, H.; Ning, H.; Lin, Y.; Wang, W.; Dhelim, S.; Farha, F.; Ding, J.; Daneshmand, M. A survey on the metaverse: The state-of-the-art, technologies, applications, and challenges. IEEE Internet Things J. 2023, 10, 14671–14688. [Google Scholar] [CrossRef]
- Gu, D.; Andreev, K.; Dupre, M.E. Major trends in population growth around the world. China CDC Wkly. 2021, 3, 604. [Google Scholar] [CrossRef]
- Navaneetham, K.; Arunachalam, D. Global population aging, 1950–2050. In Handbook of Aging, Health and Public Policy: Perspectives from Asia; Springer: Berlin/Heidelberg, Germany, 2023; pp. 1–18. [Google Scholar]
- Melgar, M. Use of respiratory syncytial virus vaccines in older adults: Recommendations of the Advisory Committee on Immunization Practices—United States, 2023. MMWR. Morb. Mortal. Wkly. Rep. 2023, 72, 793–801. [Google Scholar] [CrossRef]
- US Census Bureau. The Older Population in the United States: 2023. Available online: https://www.census.gov/library/publications/2020/demo/p25-1145.html (accessed on 17 July 2024).
- Awasthi, M.; Raghuvanshi, C.; Dudhagara, C.; Awasthi, A. Exploring virtual smart healthcare trends using digital twins. In Digital Twins for Smart Cities and Villages; Elsevier: Amsterdam, The Netherlands, 2025; pp. 377–406. [Google Scholar]
- Boschert, S.; Rosen, R. Digital twin—The simulation aspect. In Mechatronic Futures: Challenges and Solutions for Mechatronic Systems and Their Designers; Springer: Cham, Switzerland, 2016; pp. 59–74. [Google Scholar]
- Sun, T.; He, X.; Li, Z. Digital twin in healthcare: Recent updates and challenges. Digit. Health 2023, 9, 20552076221149651. [Google Scholar] [CrossRef]
- Wickramasinghe, N.; Ulapane, N.; Andargoli, A.; Ossai, C.; Shuakat, N.; Nguyen, T.; Zelcer, J. Digital twins to enable better precision and personalized dementia care. JAMIA Open 2022, 5, ooac072. [Google Scholar] [CrossRef]
- Hsu, C.C.; Tsai, M.Y.; Yu, C.M. Securing Healthcare Data Integrity: Deepfake Detection Using Autonomous AI Approaches. IEEE J. Biomed. Health Inform. 2025. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Xing, R.; Liu, D.; Luan, T.H.; Shen, X. A survey on metaverse: Fundamentals, security, and privacy. IEEE Commun. Surv. Tutor. 2022, 25, 319–352. [Google Scholar] [CrossRef]
- Wang, J.; Makowski, S.; Cieślik, A.; Lv, H.; Lv, Z. Fake news in virtual community, virtual society, and metaverse: A survey. IEEE Trans. Comput. Soc. Syst. 2023, 11, 4828–4842. [Google Scholar] [CrossRef]
- Gupta, B.B.; Gaurav, A.; Arya, V. Fuzzy logic and biometric-based lightweight cryptographic authentication for metaverse security. Appl. Soft Comput. 2024, 164, 111973. [Google Scholar] [CrossRef]
- Thakur, G.; Kumar, P.; Chen, C.M.; Vasilakos, A.V.; Anchna; Prajapat, S. A robust privacy-preserving ecc-based three-factor authentication scheme for metaverse environment. Comput. Commun. 2023, 211, 271–285. [Google Scholar] [CrossRef]
- Ruiu, P.; Nitti, M.; Pilloni, V.; Cadoni, M.; Grosso, E.; Fadda, M. Metaverse & Human Digital Twin: Digital Identity, Biometrics, and Privacy in the Future Virtual Worlds. Multimodal Technol. Interact. 2024, 8, 48. [Google Scholar] [CrossRef]
- Yang, K.; Zhang, Z.; Youliang, T.; Ma, J. A secure authentication framework to guarantee the traceability of avatars in metaverse. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3817–3832. [Google Scholar] [CrossRef]
- Qu, Q.; Chen, Y. ANCHOR: Authenticating avatars and virtual objects via anchors in the real world. In Proceedings of the Disruptive Technologies in Information Sciences IX, Orlando, FL, USA, 13–17 April 2025; pp. 237–253. [Google Scholar]
- Grigoras, C. Applications of ENF criterion in forensic audio, video, computer and telecommunication analysis. Forensic Sci. Int. 2007, 167, 136–145. [Google Scholar] [CrossRef]
- Ngharamike, E.; Ang, L.M.; Seng, K.P.; Wang, M. ENF based digital multimedia forensics: Survey, application, challenges and future work. IEEE Access 2023, 11, 101241–101272. [Google Scholar] [CrossRef]
- Nagothu, D.; Xu, R.; Chen, Y.; Blasch, E.; Aved, A. Defakepro: Decentralized deepfake attacks detection using enf authentication. IT Prof. 2022, 24, 46–52. [Google Scholar] [CrossRef]
- Hua, G.; Bi, G.; Thing, V.L. On practical issues of electric network frequency based audio forensics. IEEE Access 2017, 5, 20640–20651. [Google Scholar] [CrossRef]
- Liu, Y.; You, S.; Yao, W.; Cui, Y.; Wu, L.; Zhou, D.; Zhao, J.; Liu, H.; Liu, Y. A distribution level wide area monitoring system for the electric power grid–FNET/GridEye. IEEE Access 2017, 5, 2329–2338. [Google Scholar] [CrossRef]
- Cheng, R.; Wu, N.; Chen, S.; Han, B. Will metaverse be nextg internet? vision, hype, and reality. IEEE Netw. 2022, 36, 197–204. [Google Scholar] [CrossRef]
- Qu, Q.; Hatami, M.; Xu, R.; Nagothu, D.; Chen, Y.; Li, X.; Blasch, E.; Ardiles-Cruz, E.; Chen, G. The microverse: A task-oriented edge-scale metaverse. Future Internet 2024, 16, 60. [Google Scholar] [CrossRef]
- Chakshu, N.K.; Carson, J.; Sazonov, I.; Nithiarasu, P. A semi-active human digital twin model for detecting severity of carotid stenoses from head vibration—A coupled computational mechanics and computer vision method. Int. J. Numer. Methods Biomed. Eng. 2019, 35, e3180. [Google Scholar] [CrossRef] [PubMed]
- Hatami, M.; Qu, Q.; Chen, Y.; Kholidy, H.; Blasch, E.; Ardiles-Cruz, E. A survey of the real-time metaverse: Challenges and opportunities. Future Internet 2024, 16, 379. [Google Scholar] [CrossRef]
- He, S.; Zhang, Y.; Zhu, R.; Tian, W. Electric signature detection and analysis for power equipment failure monitoring in smart grid. IEEE Trans. Ind. Inform. 2020, 17, 3739–3750. [Google Scholar] [CrossRef]
- Suzuki, T.; Takao, H.; Rapaka, S.; Fujimura, S.; Ioan Nita, C.; Uchiyama, Y.; Ohno, H.; Otani, K.; Dahmani, C.; Mihalef, V.; et al. Rupture risk of small unruptured intracranial aneurysms in Japanese adults. Stroke 2020, 51, 641–643. [Google Scholar] [CrossRef]
- Barabási, A.L.; Gulbahce, N.; Loscalzo, J. Network medicine: A network-based approach to human disease. Nat. Rev. Genet. 2011, 12, 56–68. [Google Scholar] [CrossRef]
- Sun, H.; Chen, Y. Real-time elderly monitoring for senior safety by lightweight human action recognition. In Proceedings of the 2022 IEEE 16th International Symposium on Medical Information and Communication Technology (ISMICT), Lincoln, NE, USA, 2–4 May 2022; pp. 1–6. [Google Scholar]
- National Academies of Sciences and Medicine and Medicine Division; Committee on Health Care Utilization and Adults with Disabilities. Health-Care Utilization as a Proxy in Disability Determination; National Academies Press: Washington, DC, USA, 2018. [Google Scholar]
- Al-Naji, F.H.; Zagrouba, R. A survey on continuous authentication methods in Internet of Things environment. Comput. Commun. 2020, 163, 109–133. [Google Scholar] [CrossRef]
- Baig, A.F.; Eskeland, S. Security, privacy, and usability in continuous authentication: A survey. Sensors 2021, 21, 5967. [Google Scholar] [CrossRef]
- Dahia, G.; Jesus, L.; Pamplona Segundo, M. Continuous authentication using biometrics: An advanced review. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2020, 10, e1365. [Google Scholar] [CrossRef]
- Nagothu, D.; Xu, R.; Chen, Y.; Blasch, E.; Ardiles-Cruz, E. Application of Electrical Network Frequency as an Entropy Generator in Distributed Systems. In Proceedings of the NAECON 2023—IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 28–31 August 2023; pp. 233–238. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology: Proceedings of CRYPTO ’84; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Hammi, B.; Fayad, A.; Khatoun, R.; Zeadally, S.; Begriche, Y. A lightweight ECC-based authentication scheme for Internet of Things (IoT). IEEE Syst. J. 2020, 14, 3440–3450. [Google Scholar] [CrossRef]
- Subashini, A.; Raju, P.K. Hybrid AES model with elliptic curve and ID based key generation for IOT in telemedicine. Meas. Sensors 2023, 28, 100824. [Google Scholar] [CrossRef]
- Hajj-Ahmad, A.; Garg, R.; Wu, M. Instantaneous frequency estimation and localization for ENF signals. In Proceedings of the 2012 Asia Pacific Signal and Information Processing Association Annual Summit and Conference, Hollywood, CA, USA, 3–6 December 2012; pp. 1–10. [Google Scholar]
- Menezes, A. Evaluation of security level of cryptography: The elliptic curve discrete logarithm problem (ECDLP). Univ. Waterloo 2001, 14, 1–24. [Google Scholar]
- Haakegaard, R.; Lang, J. The Elliptic Curve Diffie-Hellman (ecdh). 2015. Available online: https://koclab.cs.ucsb.edu/teaching/ecc/project/2015Projects/Haakegaard+Lang.pdf (accessed on 10 December 2024).
- Angel, N.A.; Ravindran, D.; Vincent, P.D.R.; Srinivasan, K.; Hu, Y.C. Recent advances in evolving computing paradigms: Cloud, edge, and fog technologies. Sensors 2021, 22, 196. [Google Scholar] [CrossRef] [PubMed]
- El-Wajeh, Y.A.; Hatton, P.V.; Lee, N.J. Unreal Engine 5 and immersive surgical training: Translating advances in gaming technology into extended-reality surgical simulation training programmes. Br. J. Surg. 2022, 109, 470–471. [Google Scholar] [CrossRef]
- Li, C.; Niu, D.; Jiang, B.; Zuo, X.; Yang, J. Meta-har: Federated representation learning for human activity recognition. In Proceedings of the Web Conference 2021, Ljubljana, Slovenia, 19–23 April 2021; pp. 912–922. [Google Scholar]
- Sun, Z.; Ke, Q.; Rahmani, H.; Bennamoun, M.; Wang, G.; Liu, J. Human action recognition from various data modalities: A review. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 45, 3200–3225. [Google Scholar] [CrossRef]
- Soni, D.; Makwana, A. A survey on mqtt: A protocol of internet of things (iot). In Proceedings of the International Conference on Telecommunication, Power Analysis and Computing Techniques (ICTPACT-2017), Chennai, India, 6–8 April 2017; Volume 20. [Google Scholar]
- Wen, D.; Zhou, Y.; Li, X.; Shi, Y.; Huang, K.; Letaief, K.B. A survey on integrated sensing, communication, and computation. IEEE Commun. Surv. Tutor. 2024. [Google Scholar] [CrossRef]
- Morehouse, K.N.; Kurdi, B.; Nosek, B.A. Responsible data sharing: Identifying and remedying possible re-identification of human participants. Am. Psychol. 2025, 80. [Google Scholar] [CrossRef]





| Paradigm | Core Principle | User Intrusiveness | Resilience to Deepfake Data | Primary Application |
|---|---|---|---|---|
| Behavioral Biometrics | User’s unique interaction patterns | Low | Low to Medium: Patterns can be learned and synthesized by AI. | Desktop/Mobile Security |
| Physiological Biometrics | User’s unique biological signals | Medium (Requires wearable) | Medium: Signals can be synthesized or captured in replay attacks. | High-Security Access, Healthcare |
| Context-Aware Systems | Digital context (GPS, IP, Wi-Fi) | Low | Low: Digital context is easily spoofed. | Mobile Security, Fraud Detection |
| SAVE (Environmental) | Ambient physical phenomena (ENF) | Very Low (Passive) | High: Real-time physical signals are difficult to predict or forge remotely. | Virtual Twins, Metaverse Integrity |
| Device | Laptop | RPi 5(s) | Smart Watch |
|---|---|---|---|
| CPU | Intel Core i5-11400 | 2.4 GHz | 2.0 GHz |
| Memory | 16 GB DDR3 | 8 GB | 1 GB |
| Sensors | MAX30101 | MLX90632 | Webcam |
| Function | PPG | Temp | Image |
| Sample rate | 25 Hz | 10 Hz | 30 Hz |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qu, Q.; Chen, Y.; Blasch, E. SAVE: Securing Avatars in Virtual Healthcare Through Environmental Fingerprinting for Elder Safety Monitoring. Future Internet 2025, 17, 419. https://doi.org/10.3390/fi17090419
Qu Q, Chen Y, Blasch E. SAVE: Securing Avatars in Virtual Healthcare Through Environmental Fingerprinting for Elder Safety Monitoring. Future Internet. 2025; 17(9):419. https://doi.org/10.3390/fi17090419
Chicago/Turabian StyleQu, Qian, Yu Chen, and Erik Blasch. 2025. "SAVE: Securing Avatars in Virtual Healthcare Through Environmental Fingerprinting for Elder Safety Monitoring" Future Internet 17, no. 9: 419. https://doi.org/10.3390/fi17090419
APA StyleQu, Q., Chen, Y., & Blasch, E. (2025). SAVE: Securing Avatars in Virtual Healthcare Through Environmental Fingerprinting for Elder Safety Monitoring. Future Internet, 17(9), 419. https://doi.org/10.3390/fi17090419








