Responsible Resilience in Cyber–Physical–Social Systems: A New Paradigm for Emergent Cyber Risk Modeling
Abstract
1. Introduction
- A review of recent CPS and cyber security research, highlighting the absence of social-emergent risk modeling in the literature review.
- The conceptualization of C-CPSS as a distinct category of systems requiring new resilience models that integrate cyber, physical, and social interdependencies.
- The development of the E3R modeling paradigm, which operationalizes responsible resilience through multi-method simulation and ontology design.
2. Materials and Methods
Current Research Directions with Statistical Insights
3. Recent Literature Analysis
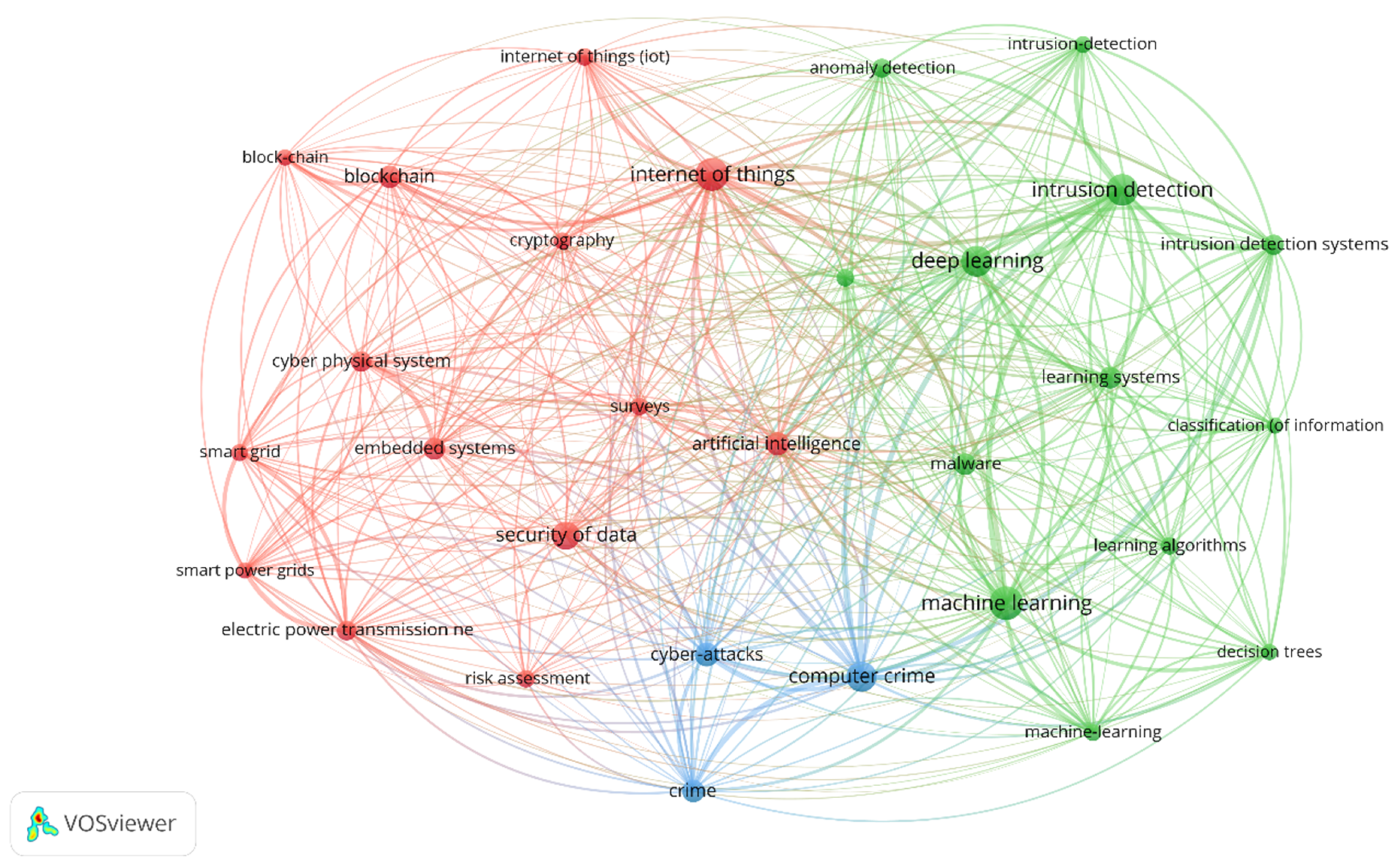
3.1. Cyber Security
3.1.1. Cybercrime
3.1.2. Data Security
3.1.3. Machine Learning for Intrusion Detection
3.1.4. Datasets and Models
3.1.5. Outliers
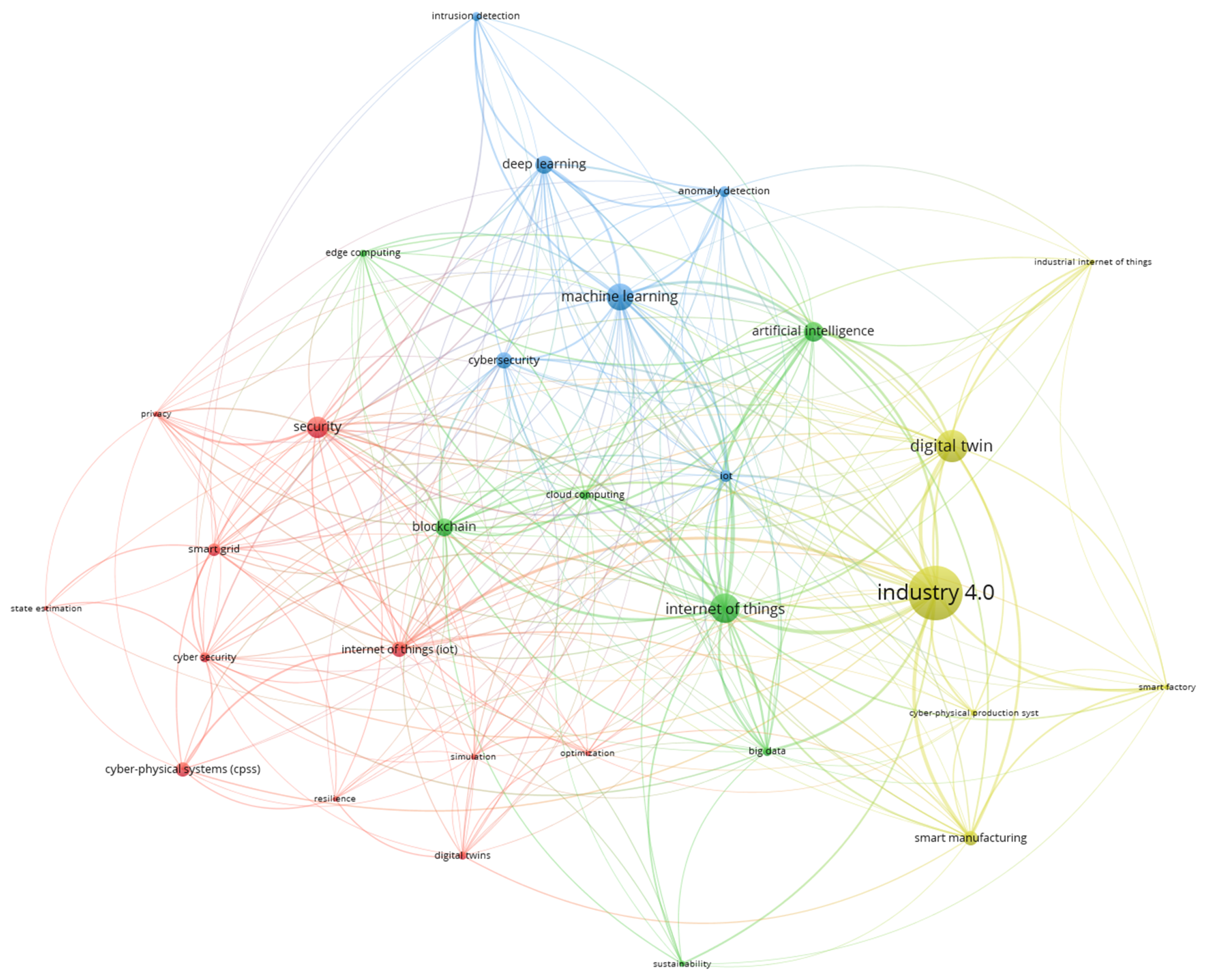
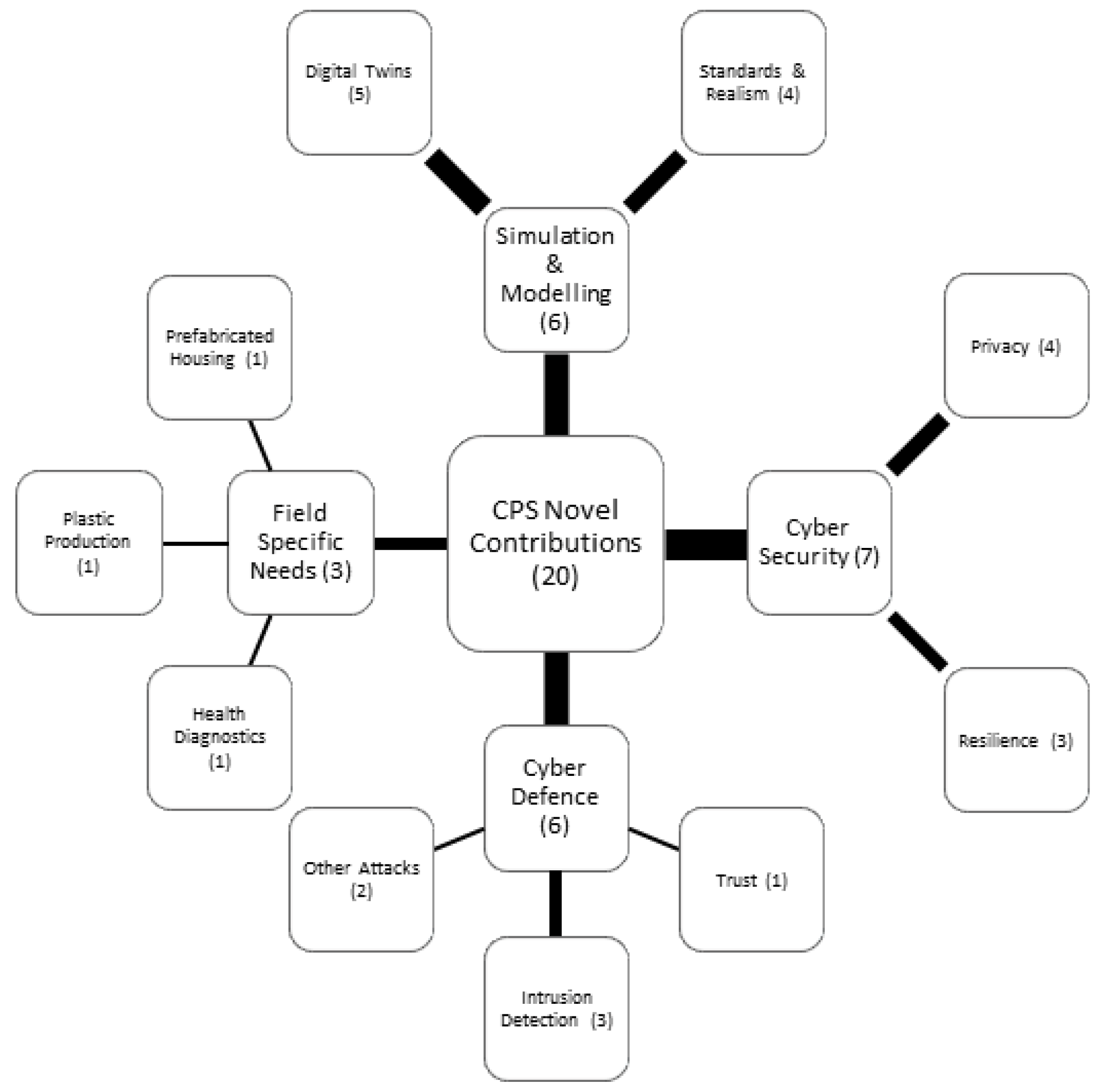
3.2. Cyber–Physical Systems
3.2.1. Simulation and Modeling
3.2.2. Cyber Security of CPS
3.2.3. Cyber Defense
3.2.4. Applications to Meet Field-Specific Niches
4. Discussions
4.1. Future Research Directions
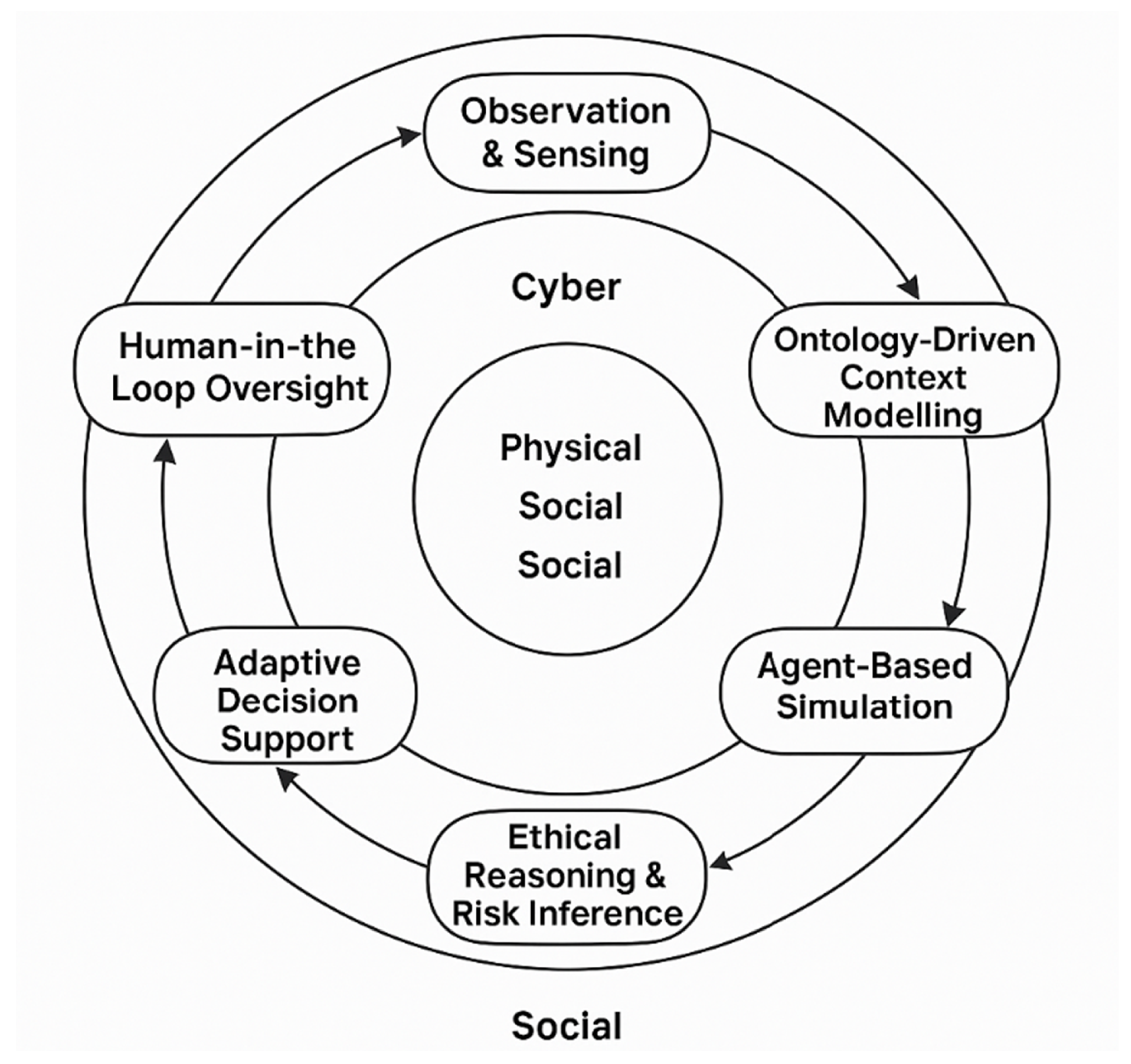
4.2. The E3R Modeling Paradigm: Towards Responsible Resilience in C-CPSS
4.3. Comparative Analysis of E3R Model
4.4. Case Studies Applying E3R
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| CPS | Cyber–Physical System |
| CPSS | Cyber–Physical–Social System |
| C-CPSS | Complex Cyber–Physical–Social System |
References
- Atheeq, C.; Sultana, R.; Sabahath, S.A.; Mohammed, M.A.K. Advancing IoT Cybersecurity: Adaptive threat identification with deep learning in Cyber-physical systems. Eng. Technol. Appl. Sci. Res. 2024, 14, 13559–13566. [Google Scholar] [CrossRef]
- Oks, S.J.; Jalowski, M.; Lechner, M.; Mirschberger, S.; Merklein, M.; Vogel-Heuser, B.; Möslein, K.M. Cyber-physical systems in the context of industry 4.0: A review, categorization and outlook. Inf. Syst. Front. 2024, 26, 1731–1772. [Google Scholar] [CrossRef]
- Qudus, L. Resilient systems: Building secure cyber-physical infrastructure for critical industries against emerging threats. Int. J. Res. Publ. Rev. 2025, 6, 3330–3346. [Google Scholar] [CrossRef]
- Kumar, S.; Bhowmik, B. Emergence, evolution, and applications of cyber-physical systems in smart society. In Proceedings of the 2024 Fourth International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), Bhilai, India, 11–12 January 2024; pp. 1–8. [Google Scholar]
- Hu, C.L.; Wang, L.; Chen, M.L.; Pei, C. A real-time interactive decision-making and control framework for complex cyber-physical-human systems. Annu. Rev. Control 2024, 57, 100938. [Google Scholar] [CrossRef]
- Bandi, A. A Taxonomy of AI techniques for security and privacy in cyber–physical systems. J. Comput. Cogn. Eng. 2024, 3, 98–111. [Google Scholar] [CrossRef]
- Calabrò, A.; Cambiaso, E.; Cheminod, M.; Bertolotti, I.C.; Durante, L.; Forestiero, A.; Lombardi, F.; Manco, G.; Marchetti, E.; Orlando, A. A Methodological Approach to Securing Cyber-Physical Systems for Critical Infrastructures. Future Internet 2024, 16, 418. [Google Scholar] [CrossRef]
- He, S.; Zhou, Y.; Yang, Y.; Liu, T.; Zhou, Y.; Li, J.; Wu, T.; Guan, X. Cascading Failure in Cyber-Physical Systems: A Review on Failure Modeling and Vulnerability Analysis. IEEE Trans. Cybern. 2024, 54, 7936–7954. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Zhu, J.; Su, C.; Zhen, X. Cascade failure modeling and resilience analysis of mine cyber physical systems under deliberate attacks. J. Saf. Sci. Resil. 2024, 5, 266–280. [Google Scholar] [CrossRef]
- Secretary of the Air Force (Ed.) Air Force Policy Directive 10-24 Mission Assurance; Department of the Air Force: Washington, DC, USA, 2019. [Google Scholar]
- Ahmad, M.A.; Baryannis, G.; Hill, R. Defining Complex Adaptive Systems: An Algorithmic Approach. Systems 2024, 12, 45. [Google Scholar] [CrossRef]
- Zimmerman, B.; Lindberg, C.; Plsek, P. A Complexity Science Primer: What Is Complexity Science and Why Should I Learn About It; Adapted From: Edgeware: Lessons From Complexity Science for Health Care Leaders; VHA Inc.: Dallas, TX, USA, 1998. [Google Scholar]
- Goldman, H.; McQuaid, R.; Picciotto, J. Cyber resilience for mission assurance. In Proceedings of the 2011 IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 15–17 November 2011; pp. 236–241. [Google Scholar]
- Hudson Jr, J.F.F. Mission Assurance in Joint All-Domain Command and Control. Air Space Power J. 2021, 35, 18–32. [Google Scholar]
- Pereira, C.; Marto, A.; Ribeiro, R.; Gonçalves, A.; Rodrigues, N.; Rabadão, C.; Costa, R.L.d.C.; Santos, L. Security and Privacy in Physical–Digital Environments: Trends and Opportunities. Future Internet 2025, 17, 83. [Google Scholar] [CrossRef]
- Phillips, S.C.; Taylor, S.; Boniface, M.; Modafferi, S.; Surridge, M. Automated knowledge-based cybersecurity risk assessment of cyber-physical systems. IEEE Access 2024, 12, 82482–82505. [Google Scholar] [CrossRef]
- Lallie, H.S.; Shepherd, L.A.; Nurse, J.R.; Erola, A.; Epiphaniou, G.; Maple, C.; Bellekens, X. Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Comput. Secur. 2021, 105, 102248. [Google Scholar] [CrossRef]
- Buil-Gil, D.; Miró-Llinares, F.; Moneva, A.; Kemp, S.; Díaz-Castaño, N. Cybercrime and shifts in opportunities during COVID-19: A preliminary analysis in the UK. Eur. Soc. 2021, 23, S47–S59. [Google Scholar] [CrossRef]
- Nguyen, G.N.; Le Viet, N.H.; Elhoseny, M.; Shankar, K.; Gupta, B.; Abd El-Latif, A.A. Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. J. Parallel Distrib. Comput. 2021, 153, 150–160. [Google Scholar] [CrossRef]
- Aslam, J.; Saleem, A.; Khan, N.T.; Kim, Y.B. Factors influencing blockchain adoption in supply chain management practices: A study based on the oil industry. J. Innov. Knowl. 2021, 6, 124–134. [Google Scholar] [CrossRef]
- Abd El-Latif, A.A.; Abd-El-Atty, B.; Mehmood, I.; Muhammad, K.; Venegas-Andraca, S.E.; Peng, J. Quantum-inspired blockchain-based cybersecurity: Securing smart edge utilities in IoT-based smart cities. Inf. Process. Manag. 2021, 58, 102549. [Google Scholar] [CrossRef]
- Alazab, M.; Alhyari, S.; Awajan, A.; Abdallah, A.B. Blockchain technology in supply chain management: An empirical study of the factors affecting user adoption/acceptance. Clust. Comput. 2021, 24, 83–101. [Google Scholar] [CrossRef]
- Latif, S.; Idrees, Z.; Ahmad, J.; Zheng, L.; Zou, Z. A blockchain-based architecture for secure and trustworthy operations in the industrial Internet of Things. J. Ind. Inf. Integr. 2021, 21, 100190. [Google Scholar] [CrossRef]
- Li, H.; Yu, K.; Liu, B.; Feng, C.; Qin, Z.; Srivastava, G. An efficient ciphertext-policy weighted attribute-based encryption for the internet of health things. IEEE J. Biomed. Health Inform. 2021, 26, 1949–1960. [Google Scholar] [CrossRef]
- Yi, J.; Dong, K.; Shen, S.; Jiang, Y.; Peng, X.; Ye, C.; Wang, Z.L. Fully fabric-based triboelectric nanogenerators as self-powered human–machine interactive keyboards. Nano-Micro Lett. 2021, 13, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Hussain, B.; Du, Q.; Sun, B.; Han, Z. Deep learning-based DDoS-attack detection for cyber–physical system over 5G network. IEEE Trans. Ind. Inform. 2020, 17, 860–870. [Google Scholar] [CrossRef]
- ur Rehman, S.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Injadat, M.; Moubayed, A.; Nassif, A.B.; Shami, A. Multi-stage optimized machine learning framework for network intrusion detection. IEEE Trans. Netw. Serv. Manag. 2020, 18, 1803–1816. [Google Scholar] [CrossRef]
- Bagui, S.; Li, K. Resampling imbalanced data for network intrusion detection datasets. J. Big Data 2021, 8, 1–41. [Google Scholar] [CrossRef]
- Gunturi, S.K.; Sarkar, D. Ensemble machine learning models for the detection of energy theft. Electr. Power Syst. Res. 2021, 192, 106904. [Google Scholar] [CrossRef]
- Hemalatha, J.; Roseline, S.A.; Geetha, S.; Kadry, S.; Damaševičius, R. An efficient densenet-based deep learning model for malware detection. Entropy 2021, 23, 344. [Google Scholar] [CrossRef] [PubMed]
- Mahbooba, B.; Timilsina, M.; Sahal, R.; Serrano, M. Explainable artificial intelligence (XAI) to enhance trust management in intrusion detection systems using decision tree model. Complexity 2021, 2021, 1–11. [Google Scholar] [CrossRef]
- Moustafa, N. A new distributed architecture for evaluating AI-based security systems at the edge: Network TON IoT datasets. Sustain. Cities Soc. 2021, 72, 102994. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Gupta, B. Ensemble machine learning approach for classification of IoT devices in smart home. Int. J. Mach. Learn. Cybern. 2021, 12, 3179–3202. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-physical energy systems security: Threat modeling, risk assessment, resources, metrics, and case studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- Zwilling, M.; Klien, G.; Lesjak, D.; Wiechetek, L.; Cetin, F.; Basim, H.N. Cyber security awareness, knowledge and behavior: A comparative study. J. Comput. Inf. Syst. 2022, 62, 82–97. [Google Scholar] [CrossRef]
- Liu, Q.; Leng, J.; Yan, D.; Zhang, D.; Wei, L.; Yu, A.; Zhao, R.; Zhang, H.; Chen, X. Digital twin-based designing of the configuration, motion, control, and optimization model of a flow-type smart manufacturing system. J. Manuf. Syst. 2021, 58, 52–64. [Google Scholar] [CrossRef]
- Leng, J.; Jiang, P.; Liu, C.; Wang, C. Contextual self-organizing of manufacturing process for mass individualization: A cyber-physical-social system approach. Enterp. Inf. Syst. 2020, 14, 1124–1149. [Google Scholar] [CrossRef]
- Yi, Y.; Yan, Y.; Liu, X.; Ni, Z.; Feng, J.; Liu, J. Digital twin-based smart assembly process design and application framework for complex products and its case study. J. Manuf. Syst. 2021, 58, 94–107. [Google Scholar] [CrossRef]
- Jiang, H.; Qin, S.; Fu, J.; Zhang, J.; Ding, G. How to model and implement connections between physical and virtual models for digital twin application. J. Manuf. Syst. 2021, 58, 36–51. [Google Scholar] [CrossRef]
- Zhuang, C.; Miao, T.; Liu, J.; Xiong, H. The connotation of digital twin, and the construction and application method of shop-floor digital twin. Robot. Comput. Integr. Manuf. 2021, 68, 102075. [Google Scholar] [CrossRef]
- Rijswijk, K.; Klerkx, L.; Bacco, M.; Bartolini, F.; Bulten, E.; Debruyne, L.; Dessein, J.; Scotti, I.; Brunori, G. Digital transformation of agriculture and rural areas: A socio-cyber-physical system framework to support responsibilisation. J. Rural Stud. 2021, 85, 79–90. [Google Scholar] [CrossRef]
- Mamta; Gupta, B.B.; Li, K.C.; Leung, V.C.M.; Psannis, K.E.; Yamaguchi, S. Blockchain-Assisted Secure Fine-Grained Searchable Encryption for a Cloud-Based Healthcare Cyber-Physical System. IEEE/CAA J. Autom. Sin. 2021, 8, 1877–1890. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. Fortified-chain: A blockchain-based framework for security and privacy-assured internet of medical things with effective access control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Alqahtani, S.; Muhammad, G.; Gupta, B.B.; Kumar, P.; Ghoneim, A. A lightweight and robust secure key establishment protocol for internet of medical things in COVID-19 patients care. IEEE Internet Things J. 2020, 8, 15694–15703. [Google Scholar] [CrossRef]
- Saeed, U.; Jan, S.U.; Lee, Y.D.; Koo, I. Fault diagnosis based on extremely randomized trees in wireless sensor networks. Reliab. Eng. Syst. Saf. 2021, 205, 107284. [Google Scholar] [CrossRef]
- Deng, C.; Wang, Y.; Wen, C.; Xu, Y.; Lin, P. Distributed resilient control for energy storage systems in cyber–physical microgrids. IEEE Trans. Ind. Inform. 2020, 17, 1331–1341. [Google Scholar] [CrossRef]
- Petrillo, A.; Pescape, A.; Santini, S. A secure adaptive control for cooperative driving of autonomous connected vehicles in the presence of heterogeneous communication delays and cyberattacks. IEEE Trans. Cybern. 2020, 51, 1134–1149. [Google Scholar] [CrossRef] [PubMed]
- Li, B.; Wu, Y.; Song, J.; Lu, R.; Li, T.; Zhao, L. DeepFed: Federated deep learning for intrusion detection in industrial cyber–physical systems. IEEE Trans. Ind. Inform. 2020, 17, 5615–5624. [Google Scholar] [CrossRef]
- Lv, Z.; Han, Y.; Singh, A.K.; Manogaran, G.; Lv, H. Trustworthiness in industrial IoT systems based on artificial intelligence. IEEE Trans. Ind. Inform. 2020, 17, 1496–1504. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.; Shimizu, S.; Ma, J.; Jin, Q. Siamese neural network based few-shot learning for anomaly detection in industrial cyber-physical systems. IEEE Trans. Ind. Inform. 2020, 17, 5790–5798. [Google Scholar] [CrossRef]
- Qi, W.; Hou, Y.; Zong, G.; Ahn, C.K. Finite-time event-triggered control for semi-Markovian switching cyber-physical systems with FDI attacks and applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 2665–2674. [Google Scholar] [CrossRef]
- Nara, E.O.B.; da Costa, M.B.; Baierle, I.C.; Schaefer, J.L.; Benitez, G.B.; do Santos, L.M.A.L.; Benitez, L.B. Expected impact of industry 4.0 technologies on sustainable development: A study in the context of Brazil’s plastic industry. Sustain. Prod. Consum. 2021, 25, 102–122. [Google Scholar] [CrossRef]
- Bonilla, S.H.; Silva, H.R.; Terra da Silva, M.; Franco Gonçalves, R.; Sacomano, J.B. Industry 4.0 and sustainability implications: A scenario-based analysis of the impacts and challenges. Sustainability 2018, 10, 3740. [Google Scholar] [CrossRef]
- Fettermann, D.C.; Cavalcante, C.G.S.; Almeida, T.D.d.; Tortorella, G.L. How does Industry 4.0 contribute to operations management? J. Ind. Prod. Eng. 2018, 35, 255–268. [Google Scholar] [CrossRef]
- Junior, J.A.G.; Busso, C.M.; Gobbo, S.C.O.; Carreão, H. Making the links among environmental protection, process safety, and industry 4.0. Process. Saf. Environ. Prot. 2018, 117, 372–382. [Google Scholar]
- Shin, S.J.; Woo, J.; Rachuri, S. Predictive analytics model for power consumption in manufacturing. Procedia CIRP 2014, 15, 153–158. [Google Scholar] [CrossRef]
- Thiede, S. Environmental sustainability of cyber physical production systems. Procedia CIRP 2018, 69, 644–649. [Google Scholar] [CrossRef]
- Li, C.Z.; Chen, Z.; Xue, F.; Kong, X.T.R.; Xiao, B.; Lai, X.; Zhao, Y. A blockchain- and IoT-based smart product-service system for the sustainability of prefabricated housing construction. J. Clean. Prod. 2021, 286, 125391. [Google Scholar] [CrossRef]
- Edwards, N.; Kiser, S.B.; Haynes, J.B. Answering the Cybersecurity Issues: Confidentiality, Integrity, and Availability. J. Strateg. Innov. Sustain. 2020, 15, 10–14. [Google Scholar]
- Nweke, L.O. Using the CIA and AAA models to explain cybersecurity activities. PM World J. 2017, 6, 1–2. [Google Scholar]
- Roelofs, R. Measuring Generalization and Overfitting in Machine Learning; University of California: Berkeley, CA, USA, 2019. [Google Scholar]
- Mersinas, K.; Sobb, T.; Sample, C.; Bakdash, J.Z.; Ormrod, D. Training Data and Rationality. In Proceedings of the ECIAIR 2019 European Conference on the Impact of Artificial Intelligence and Robotics, Oxford, UK, 31 October–1 November 2019; Academic Conferences and Publishing Limited: London, UK, 2019; p. 225. [Google Scholar]
- Huang, C.; Marshall, J.; Wang, D.; Dong, M. Towards reliable social sensing in cyber-physical-social systems. In Proceedings of the 2016 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), Chicago, IL, USA, 23–27 May 2016; pp. 1796–1802. [Google Scholar]
- Mirza, I.B. Intersecting Sensor and Social Media Information Spaces for Comprehensive Situation Awareness. Ph.D. Thesis, School of Science, Computing And Engineering Technologies, Swinburne University of Technology, Melbourne, Australia, 2024. [Google Scholar]
- Mirza, I.B.; Georgakopoulos, D.; Yavari, A. Cyber-physical-social awareness platform for comprehensive situation awareness. Sensors 2023, 23, 822. [Google Scholar] [CrossRef]
- Revathi, S.; Raja, J.; Mohanraj, M.; Malathi, K.; Mallala, B.; Vidhya, R. Challenges in Cyber Physical Social Systems and Internet of Things. In Proceedings of the 2024 5th International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 18–20 September 2024; pp. 409–413. [Google Scholar]
- Gruber, T. What is an Ontology? In Encyclopedia of Database Systems; Springer: New York, NY, USA, 2009. [Google Scholar]
- Neuhaus, F. What is an Ontology? arXiv 2018, arXiv:1810.09171. [Google Scholar]
- Brinson, A.; Robinson, A.; Rogers, M. A cyber forensics ontology: Creating a new approach to studying cyber forensics. Digit. Investig. 2006, 3, 37–43. [Google Scholar] [CrossRef]
- Kul, G.; Upadhyaya, S.J. Towards a Cyber Ontology for Insider Threats in the Financial Sector. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2015, 6, 64–85. [Google Scholar]
- Obrst, L.; Chase, P.; Markeloff, R. Developing an Ontology of the Cyber Security Domain. In Proceedings of the STIDS, Fairfax, VA, USA, 24–25 October 2012; pp. 49–56. [Google Scholar]
- Oltramari, A.; Henshel, D.S.; Cains, M.; Hoffman, B. Towards a Human Factors Ontology for Cyber Security. Stids 2015, 2015, 26–33. [Google Scholar]
- Syed, Z.; Padia, A.; Finin, T.; Mathews, L.; Joshi, A. UCO: A unified cybersecurity ontology. In Proceedings of the Workshops at the Thirtieth AAAI Conference on Artificial Intelligence, Phoenix, AZ, USA, 12–13 February 2016. [Google Scholar]
- Varvarigou, D.; Espes, D.; Bersano, G. Ontology-Based Solution for Handling Safety and Cybersecurity Interdependency in Safety-Critical Systems. In Latest Advances and New Visions of Ontology in Information Science; IntechOpen: London, UK, 2023; Book Section 3. [Google Scholar]
- An, L.; Grimm, V.; Sullivan, A.; Turner Ii, B.; Malleson, N.; Heppenstall, A.; Vincenot, C.; Robinson, D.; Ye, X.; Liu, J. Challenges, tasks, and opportunities in modeling agent-based complex systems. Ecol. Model. 2021, 457, 109685. [Google Scholar] [CrossRef]
- Bemthuis, R.; Mes, M.; Iacob, M.E.; Havinga, P. Using agent-based simulation for emergent behavior detection in cyber-physical systems. In Proceedings of the 2020 Winter Simulation Conference (WSC), Orlando, FL, USA, 14–18 December 2020; pp. 230–241. [Google Scholar]
- Kotenko, I.; Konovalov, A.; Shorov, A. Agent-based modeling and simulation of botnets and botnet defense. In Proceedings of the Conference on Cyber Conflict, Tallinn, Estonia, 29 May–1 June 2018; pp. 21–44. [Google Scholar]
- Kotenko, I.; Mankov, E. Agent-Based Modeling and Simulation of Computer Network Attacks. In Proceedings of the Fourth International Workshop on Agent-Based Simulation, Melbourne, Australia, 14 July 2003; Volume 4. [Google Scholar]
- Novak, P.; Kadera, P.; Wimmer, M. Agent-based modeling and simulation of hybrid cyber-physical systems. In Proceedings of the 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), Exeter, UK, 21–23 June 2017; pp. 1–8. [Google Scholar]
- Rafferty, L. Agent-Based Modeling Framework for Adaptive Cyber Defence of the Internet of Things. Ph.D. Thesis, University of Ontario Institute of Technology (Ontario Tech University), Oshawa, ON, Canada, 2022. [Google Scholar]
- Mata, O.; Ponce, P.; McDaniel, T.; Méndez, J.I.; Peffer, T.; Molina, A. Smart city concept based on cyber-physical social systems with hierarchical ethical agents approach. In Proceedings of the International Conference On Human-Computer Interaction, Bari, Italy, 30 August–3 September 2021; pp. 424–437. [Google Scholar]
- Ören, T. Security of Cyber-Physical-Social Systems: Impact of Simulation-Based Systems Engineering, Artificial Intelligence, Human Involvement, and Ethics. In Advances in Computing, Informatics, Networking and Cybersecurity: A Book Honoring Professor Mohammad S. Obaidat’s Significant Scientific Contributions; Springer: Berlin/Heidelberg, Germany, 2022; pp. 711–732. [Google Scholar]
- Farid, K.; Sakr, N. Few-Shot System Identification for Reinforcement Learning. In Proceedings of the 2021 6th Asia-Pacific Conference on Intelligent Robot Systems (ACIRS), Tokyo, Japan, 16–18 July 2021; pp. 1–7. [Google Scholar]
- Luo, B.; Zhang, Y.; Dubey, A.; Mukhopadhyay, A. Act as you learn: Adaptive decision-making in non-stationary markov decision processes. arXiv 2024, arXiv:2401.01841. [Google Scholar]
- Sinha, S.; Vaidya, U.; Yeung, E. On few shot learning of dynamical systems: A Koopman operator theoretic approach. arXiv 2021, arXiv:2103.04221. [Google Scholar]
- Su, Y.; Zhao, H.; Zheng, Y.; Wang, Y. Few-shot learning with multi-granularity knowledge fusion and decision-making. IEEE Trans. Big Data 2024, 10, 486–497. [Google Scholar] [CrossRef]
- Zaman, M.; Eini, R.; Zohrabi, N.; Abdelwahed, S. A Decision Support System for Cyber Physical Systems under Disruptive Events: Smart Building Application. In Proceedings of the 2022 IEEE International Smart Cities Conference (ISC2), Pafos, Cyprus, 26–29 September 2022; pp. 1–7. [Google Scholar]
- Aoki, N. The importance of the assurance that “humans are still in the decision loop” for public trust in artificial intelligence: Evidence from an online experiment. Comput. Hum. Behav. 2021, 114, 106572. [Google Scholar] [CrossRef]
- Kathiresan, G. Human-in-the-Loop Testing for LLM-Integrated Software: A Quality Engineering Framework for Trust and Safety. Authorea Prepr. 2025. [Google Scholar]
- Ghai, B.; Mueller, K. D-bias: A causality-based human-in-the-loop system for tackling algorithmic bias. IEEE Trans. Vis. Comput. Graph. 2022, 29, 473–482. [Google Scholar] [CrossRef]
- Gannon, J.D.; Hamlet, R.G.; Mills, H.D. Theory of modules. IEEE Trans. Softw. Eng. 1987, SE-13, 820–829. [Google Scholar] [CrossRef]
- Field, A. Risk Management and ISO 31000: A Pocket Guide; IT Governance Publishing: Ely, UK, 2023. [Google Scholar]
- Purdy, G. ISO 31000: 2009—setting a new standard for risk management. Risk Anal. Int. J. 2010, 30, 881–886. [Google Scholar] [CrossRef]
- Shin, J.; Son, H.; Heo, G. Development of a cyber security risk model using Bayesian networks. Reliab. Eng. Syst. Saf. 2015, 134, 208–217. [Google Scholar] [CrossRef]
- Alali, M.; Almogren, A.; Hassan, M.M.; Rassan, I.A.; Bhuiyan, M.Z.A. Improving risk assessment model of cyber security using fuzzy logic inference system. Comput. Secur. 2018, 74, 323–339. [Google Scholar] [CrossRef]
- McQueen, M.A.; Boyer, W.F.; Flynn, M.A.; Beitel, G.A. Time-to-compromise model for cyber risk reduction estimation. In Proceedings of the Quality of Protection: Security Measurements and Metrics; Springer: Idaho Falls, ID, USA, 2006; pp. 49–64. [Google Scholar]
- Palko, D.; Babenko, T.; Bigdan, A.; Kiktev, N.; Hutsol, T.; Kuboń, M.; Hnatiienko, H.; Tabor, S.; Gorbovy, O.; Borusiewicz, A. Cyber security risk modeling in distributed information systems. Appl. Sci. 2023, 13, 2393. [Google Scholar] [CrossRef]
- Mukhopadhyay, A.; Chatterjee, S.; Bagchi, K.K.; Kirs, P.J.; Shukla, G.K. Cyber risk assessment and mitigation (CRAM) framework using logit and probit models for cyber insurance. Inf. Syst. Front. 2019, 21, 997–1018. [Google Scholar] [CrossRef]
- Tam, K.; Jones, K. MaCRA: A model-based framework for maritime cyber-risk assessment. WMU J. Marit. Aff. 2019, 18, 129–163. [Google Scholar] [CrossRef]
- Akinrolabu, O.; Nurse, J.R.; Martin, A.; New, S. Cyber risk assessment in cloud provider environments: Current models and future needs. Comput. Secur. 2019, 87, 101600. [Google Scholar] [CrossRef]
- Avcı, İ.; Koca, M. Intelligent Transportation System Technologies, Challenges and Security. Appl. Sci. 2024, 14, 4646. [Google Scholar] [CrossRef]
- Lee, K.; Hong, D.; Kim, J.; Cha, D.; Choi, H.; Moon, J.; Moon, C. Road-network-based event information system in a cooperative ITS Environment. Electronics 2023, 12, 2448. [Google Scholar] [CrossRef]
- Levina, A.I.; Dubgorn, A.S.; Iliashenko, O.Y. Internet of things within the service architecture of intelligent transport systems. In Proceedings of the 2017 European Conference on Electrical Engineering and Computer Science (EECS), Bern, Switzerland, 17–19 November 2017; pp. 351–355. [Google Scholar]
| Social Dimension | Emergence | Resilience | Dynamic Adaptive Systems | Feedback Loops | Asset Mission Value | |
|---|---|---|---|---|---|---|
| E3R Model | X | X | X | X | X | X |
| ISO 31000:2018 Process Clause 6 [93,94] | - | - | X | - | X | - |
| Bayesian risk model [95] | - | - | X | - | - | - |
| Fuzzy Inference Model [96] | - | - | - | - | X | - |
| Time-To-Compromise Model [97] | - | - | - | - | X | - |
| Three-phase assessment [98] | - | - | - | - | - | X |
| CRAM Framework [99] | - | - | - | - | - | - |
| MaCRA Model [100] | - | - | X | - | - | X |
| CSCCRA model [101] | - | - | - | - | - | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sobb, T.; Moustafa, N.; Turnbull, B. Responsible Resilience in Cyber–Physical–Social Systems: A New Paradigm for Emergent Cyber Risk Modeling. Future Internet 2025, 17, 282. https://doi.org/10.3390/fi17070282
Sobb T, Moustafa N, Turnbull B. Responsible Resilience in Cyber–Physical–Social Systems: A New Paradigm for Emergent Cyber Risk Modeling. Future Internet. 2025; 17(7):282. https://doi.org/10.3390/fi17070282
Chicago/Turabian StyleSobb, Theresa, Nour Moustafa, and Benjamin Turnbull. 2025. "Responsible Resilience in Cyber–Physical–Social Systems: A New Paradigm for Emergent Cyber Risk Modeling" Future Internet 17, no. 7: 282. https://doi.org/10.3390/fi17070282
APA StyleSobb, T., Moustafa, N., & Turnbull, B. (2025). Responsible Resilience in Cyber–Physical–Social Systems: A New Paradigm for Emergent Cyber Risk Modeling. Future Internet, 17(7), 282. https://doi.org/10.3390/fi17070282







