Securing Blockchain Systems: A Layer-Oriented Survey of Threats, Vulnerability Taxonomy, and Detection Methods
Abstract
1. Introduction
- RQ1: How can blockchain security threats be categorized and analyzed based on the specific layer of the blockchain system they target?
- RQ2: What are the common attack vectors and their potential impact on different blockchain layers? What countermeasures can be implemented to mitigate these threats?
- RQ3: What are the prominent categories of research on blockchain vulnerability detection, and how can they be systematically classified based on their methodologies and focal problems?
- RQ4: What are the strengths and weaknesses of each vulnerability detection category, and how can this comparative analysis inform the selection of appropriate tools and techniques?
2. Blockchain: An Overview
2.1. Key Components of Blockchain
2.1.1. Node
2.1.2. Immutable Records (Transactions)
2.1.3. Distributed Ledger
2.1.4. Smart Contract
2.1.5. Consensus Algorithm
2.2. How Blockchain Works
2.2.1. Request Transaction
2.2.2. Validate Transaction
2.2.3. Verify Transaction
2.2.4. Append Block and Complete
3. Security Threats
3.1. Methodology for Attack Classification
- Article Selection: We searched for papers using terms such as “blockchain attacks”, “security taxonomy”, and “vulnerabilities in distributed ledgers”. Studies were included if they (i) focused on blockchain-based systems, and (ii) presented or discussed a classification of security threats or attack types.
- Relevance Screening: Titles and abstracts were reviewed to filter out papers that were either not technical, not related to blockchain, or purely focused on cryptographic primitives. This helped ensure focus on architectural and systemic security threats.
- Classification Analysis: For each selected study, we examined how attacks were categorized (e.g., by type, impact, architecture layer). This comparative analysis informed the design of our own five-layer taxonomy, which maps attacks to the data, network, consensus, contract, and application layers of blockchain systems.
3.2. Reviewed Security Literatures
3.3. Layer-Based Attack Classification
4. Security Attacks
4.1. Data Layer
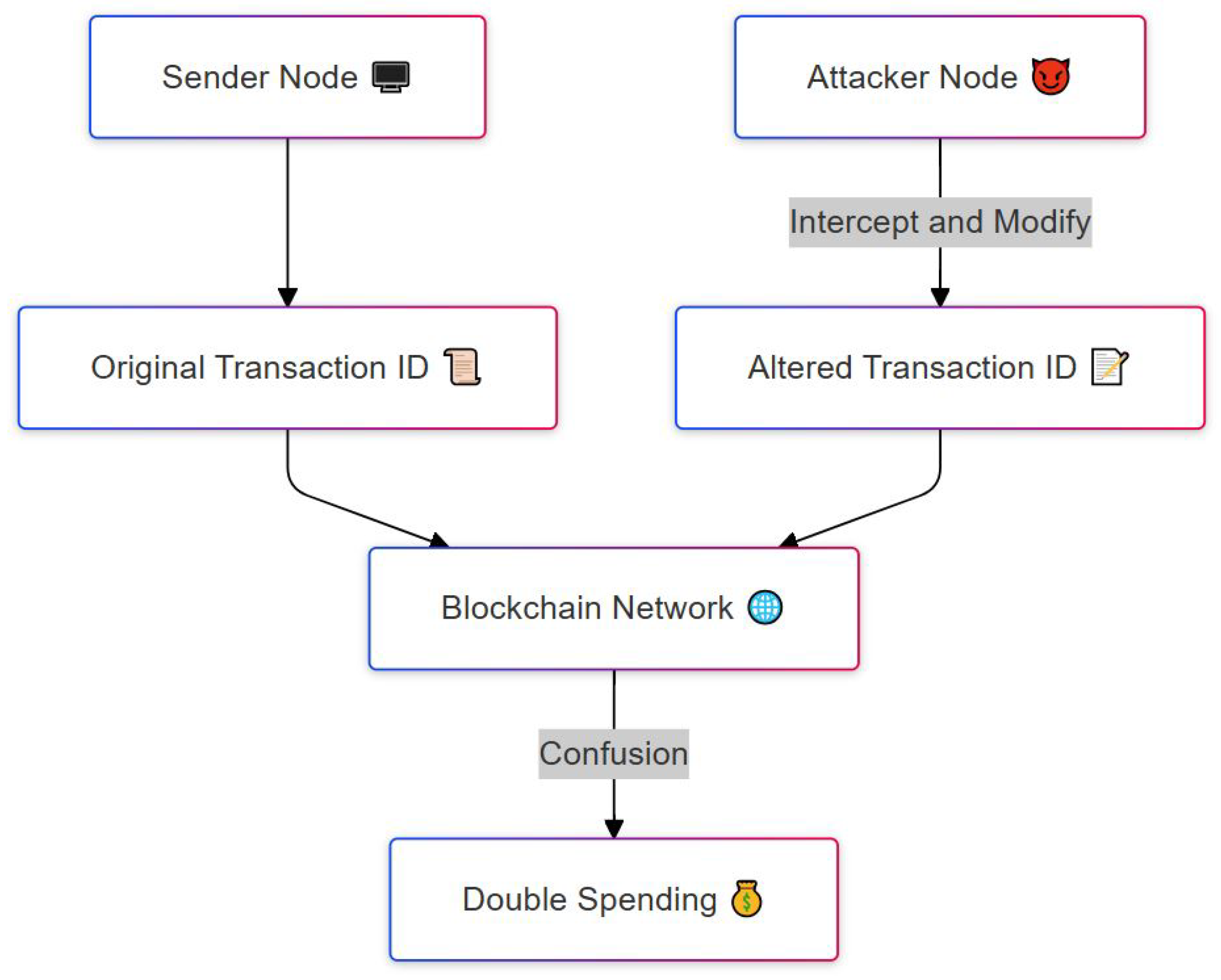
4.1.1. Transaction Malleability Attack
4.1.2. Quantum Attack
4.2. Network Layer
4.2.1. Sybil Attack
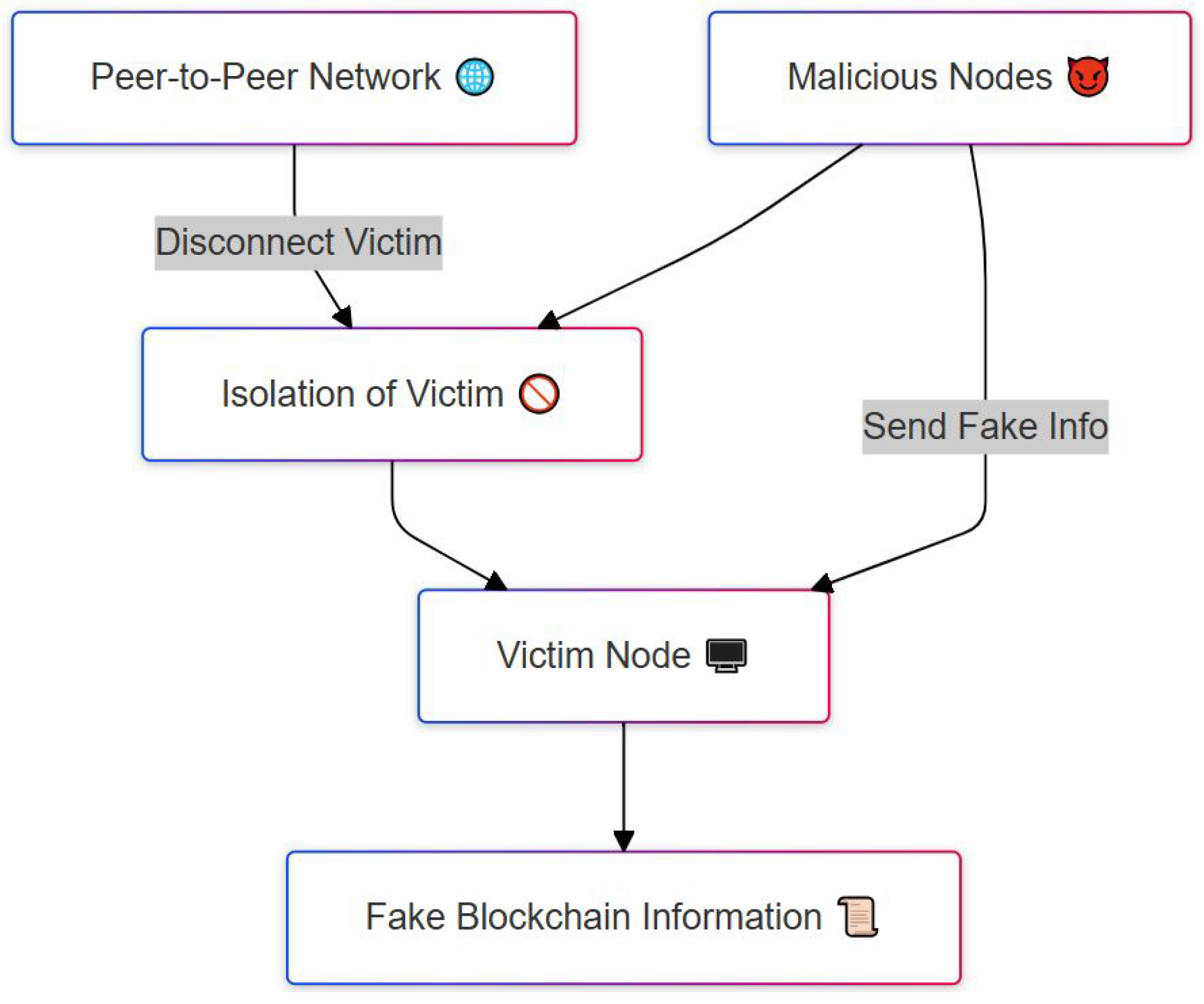
4.2.2. Eclipse Attack
4.2.3. DDoS Attack
4.2.4. BGP Hijacking Attack
4.2.5. Routing Attack
4.2.6. DNS Attack
4.3. Consensus and Incentive Layer
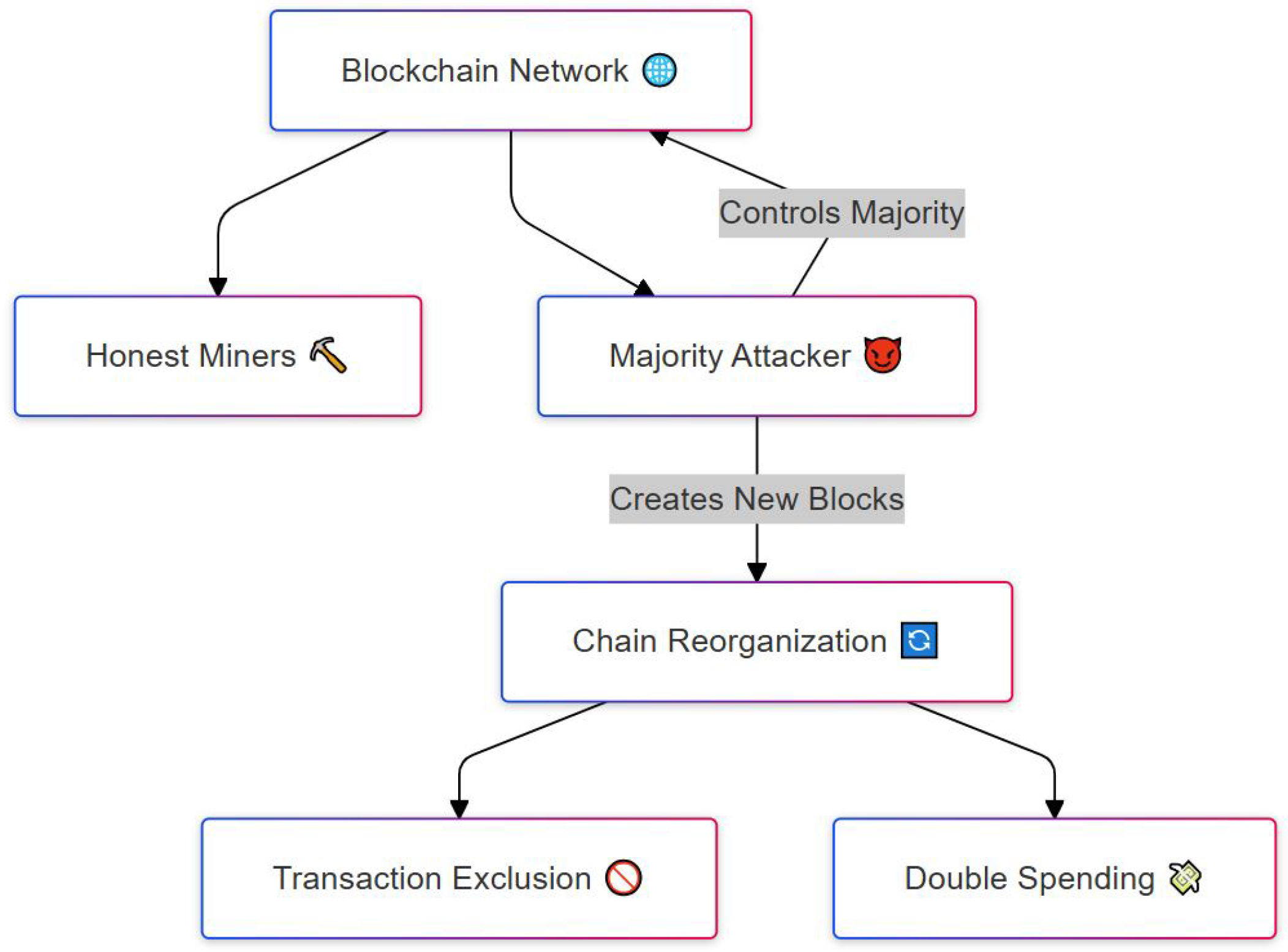
4.3.1. 51% Majority Attacks
4.3.2. Replay Attacks
4.3.3. Race Attack
4.3.4. Finney Attack
4.3.5. Time Jacking
4.3.6. Vector 76 Attack
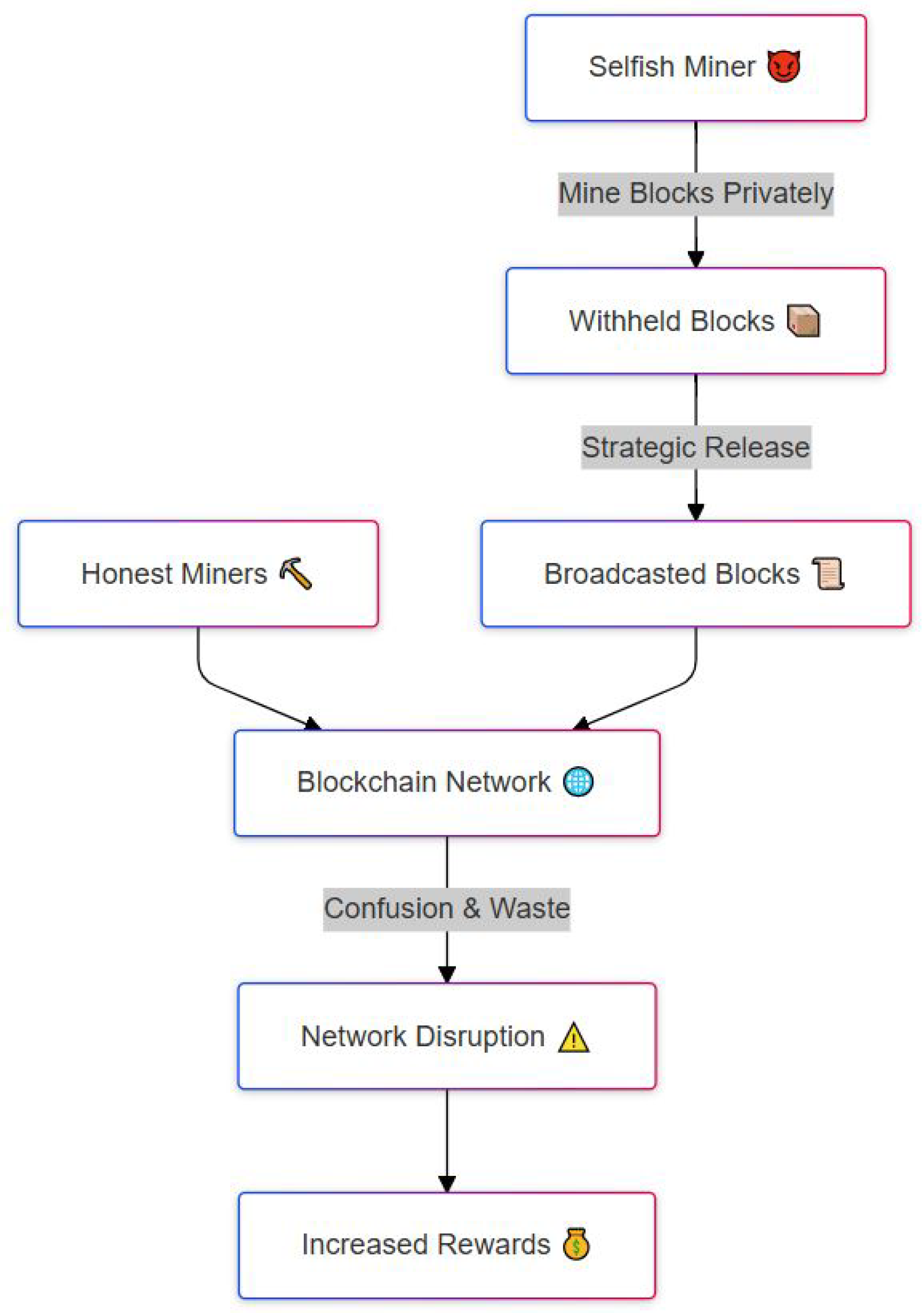
4.3.7. Selfish Mining
4.3.8. Block-Withholding Attack (BWH)
4.3.9. Bribery Attack
4.4. Contract Layer
4.4.1. Re-Entrancy Attack
4.4.2. Overflow Attacks
4.4.3. Short Address Attacks
4.4.4. Balance Attack
4.5. Application Layer
4.5.1. Cryptojacking
4.5.2. Attacks on Cold Wallets
4.5.3. Attacks on Hot Wallets
4.5.4. Dictionary Attack
4.5.5. Malware Attack
5. Vulnerability Detection
5.1. A Systematic Taxonomy of Vulnerability Detection
KeyAspects of the Taxonomy
5.2. Detailed Comparative Analysis on Vulnerability Detection Methods
5.2.1. Machine Learning and Deep Learning Approaches
Issues in the Existing Approaches
5.2.2. Static and Program Analysis-Based Methods
Issues in the Existing Approaches
5.2.3. Fuzzing and Cross-Contract Methods
Issues in the Existing Approaches
5.2.4. Vulnerability Repair and Fraud Detection
5.2.5. Datasets and Evaluation-Based Methods
5.2.6. Comprehensive Surveys and Domain-Specific Enhancements
5.2.7. Key Insights from the Vulnerability Detection Taxonomy
- Hybrid Approaches Enhance Security: No single approach—whether based on machine learning, static analysis, or fuzzing—can fully cover the vast and evolving threat landscape in blockchain environments. Hybrid strategies, such as combining symbolic execution with deep neural networks [57] or using static analysis to identify suspicious points before applying fuzzing, are emerging as best practices. The integration of multiple methods—including formal verification for critical invariants, deep learning for dynamic anomaly detection, and fuzzing for real-world scenario testing—provides a more robust defense against malicious actors.
- Adaptability and Machine Learning: Machine learning provides the flexibility and adaptability necessary for real-time anomaly detection and novel vulnerability identification, complementing traditional security measures. Its capability for advanced pattern recognition makes it highly effective against evolving threats.
- Persistent Challenges Require Attention: Several challenges persist, demanding ongoing research and community collaboration: (1) Scalability and Efficiency: Techniques must effectively handle large-scale contracts and cross-chain interactions without incurring excessive overhead. (2) Data Quality and Benchmarking: High-quality, standardized datasets and consensus-driven benchmarks are critical for developing and evaluating reliable security tools. (3) Interpretability and Transparency: Tools must provide clear, understandable explanations suitable for end-users, auditors, and regulatory compliance. (4) Future-Proofing Against Evolving Threats: Solutions must continually evolve to counter emerging threats, including quantum-based vulnerabilities and sophisticated MEV exploits.
- Community-Driven Collaboration is Essential: Successfully addressing blockchain vulnerabilities demands collaboration across disciplines such as software engineering, cryptography, artificial intelligence, and other specialized fields. A multidisciplinary approach is essential to keep blockchain systems innovative and secure.
6. ML and the Security of Blockchain
6.1. Anomaly Detection and Intrusion Prevention
6.2. Smart Contract Security
6.3. Consensus Mechanism Enhancement
6.4. Sybil Attack Mitigation
6.5. Quantum Attack Resistance
6.6. Network Traffic Analysis
6.7. Blockchain Forensics
6.8. BlockGPT Framework
6.9. Adversarial Use of ML in Blockchain Security
6.10. Broader Perspectives on ML in Blockchain Security
7. Discussion and Future Directions
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- IBM. What Is Blockchain Security? Available online: https://www.ibm.com/topics/blockchain-security (accessed on 27 January 2024).
- Baldwin, C. Bitcoin Worth 72 Million Stolen from Bitfinex Exchange in Hong Kong. 2016. Available online: https://www.reuters.com/article/us-bitfinex-hacked-hongkong-idUSKCN10E0KP (accessed on 15 March 2024).
- Popper, N. A Hacking of More than 50 Million Dashes Hopes in the World of Virtual Currency. 2016. Available online: https://www.nytimes.com/2016/06/18/business/dealbook/hacker-may-have-removed-more-than-50-million-from-experimental-cybercurrency-project.html (accessed on 13 February 2024).
- Zhao, W. Crypto Exchange Bithumb Hacked for 13 Million in Suspected Insider Job. 2019. Available online: https://www.coindesk.com/markets/2019/03/30/crypto-exchange-bithumb-hacked-for-13-million-in-suspected-insider-job (accessed on 10 April 2025).
- Mollajafari, S.; Bechkoum, K. Blockchain technology and related security risks: Towards a seven-layer perspective and taxonomy. Sustainability 2023, 15, 13401. [Google Scholar] [CrossRef]
- Dwivedi, K.; Agrawal, A.; Bhatia, A.; Tiwari, K. A novel classification of attacks on blockchain layers: Vulnerabilities, attacks, mitigations, and research directions. arXiv 2024, arXiv:2404.18090. [Google Scholar]
- Gurjar, A.; Chandavarkar, B. Smart Contract Vulnerabilities and Detection Methods: A Survey. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, 24–28 June 2024; IEEE: New York, NJ, USA, 2024; pp. 1–7. [Google Scholar]
- Hejazi, N.; Lashkari, A.H. A comprehensive survey of smart contracts vulnerability detection tools: Techniques and methodologies. J. Netw. Comput. Appl. 2025, 237, 104142. [Google Scholar] [CrossRef]
- Chu, H.; Zhang, P.; Dong, H.; Xiao, Y.; Ji, S.; Li, W. A survey on smart contract vulnerabilities: Data sources, detection and repair. Inf. Softw. Technol. 2023, 159, 107221. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Goyal, S.; Kumar, M.; Singh, T.P. An AI-Enabled Blockchain Algorithm: A Novel Approach to Counteract Blockchain Network Security Attacks. EAI Endorsed Trans. Internet Things 2024, 10, 1–9. [Google Scholar] [CrossRef]
- Magalhães, J. Current Vulnerabilities and Risks of Blockchain: A Systematic Literature Review. In Digital Technologies and Transformation in Business, Industry and Organizations; Springer: Cham, Switzerland, 2025; pp. 159–175. [Google Scholar]
- Verma, P.; Bharot, N.; Breslin, J.G.; O’Shea, D.; Vidyarthi, A.; Gupta, D. Zero-day guardian: A dual model enabled federated learning framework for handling zero-day attacks in 5G enabled IIoT. IEEE Trans. Consum. Electron. 2023, 70, 3856–3866. [Google Scholar] [CrossRef]
- Hallaji, E.; Razavi-Far, R.; Saif, M.; Wang, B.; Yang, Q. Decentralized federated learning: A survey on security and privacy. IEEE Trans. Big Data 2024, 10, 194–213. [Google Scholar] [CrossRef]
- Huan, N.T.Y.; Zukarnain, Z.A. A Survey on Addressing IoT Security Issues by Embedding Blockchain Technology Solutions: Review, Attacks, Current Trends, and Applications. IEEE Access 2024, 12, 69765–69782. [Google Scholar] [CrossRef]
- Li, D.; Han, D.; Weng, T.H.; Zheng, Z.; Li, H.; Liu, H.; Castiglione, A.; Li, K.C. Blockchain for federated learning toward secure distributed machine learning systems: A systemic survey. Soft Comput. 2022, 26, 4423–4440. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Liu, P.; Xu, X.; Wang, W. Threats, attacks and defenses to federated learning: Issues, taxonomy and perspectives. Cybersecurity 2022, 5, 4. [Google Scholar] [CrossRef]
- Lee, J.H. Systematic Approach to Analyzing Security and Vulnerabilities of Blockchain Systems. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2019. [Google Scholar]
- Zamani, E.; He, Y.; Phillips, M. On the security risks of the blockchain. J. Comput. Inf. Syst. 2020, 60, 495–506. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Zarrin, J.; Wen Phang, H.; Babu Saheer, L.; Zarrin, B. Blockchain for decentralization of internet: Prospects, trends, and challenges. Clust. Comput. 2021, 24, 2841–2866. [Google Scholar] [CrossRef]
- Manu, M.; Musthafa, N.; Balamurugan, B.; Chauhan, R. Blockchain components and concept. In Blockchain Technology and Applications; Auerbach Publications: Boca Raton, FL, USA, 2020; pp. 21–50. [Google Scholar]
- Patel, V.; Khatiwala, F.; Shah, K.; Choksi, Y. A review on blockchain technology: Components, issues and challenges. In Proceedings of the ICDSMLA 2019: Proceedings of the 1st International Conference on Data Science, Machine Learning and Applications, Hyderabad, India, 26–28 July 2019; Springer: Berlin/Heidelberg, Germany, 2020; pp. 1257–1262. [Google Scholar]
- Puthal, D.; Malik, N.; Mohanty, S.P.; Kougianos, E.; Das, G. Everything you wanted to know about the blockchain: Its promise, components, processes, and problems. IEEE Consum. Electron. Mag. 2018, 7, 6–14. [Google Scholar] [CrossRef]
- IBM. What Is Blockchain Technology? 2022. Available online: https://www.ibm.com/topics/what-is-blockchain (accessed on 10 September 2024).
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. (CSUR) 2019, 52, 1–34. [Google Scholar] [CrossRef]
- Bhushan, B.; Sinha, P.; Sagayam, K.M.; Andrew, J. Untangling blockchain technology: A survey on state of the art, security threats, privacy services, applications and future research directions. Comput. Electr. Eng. 2021, 90, 106897. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- Mosakheil, J.H. Security Threats Classification in Blockchains. Master’s Thesis, Herberger School of Business, St. Cloud, MN, USA, 2018. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of blockchain from security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17. [Google Scholar] [CrossRef]
- Anita, N.; Vijayalakshmi, M. Blockchain security attack: A brief survey. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Putz, B.; Pernul, G. Detecting blockchain security threats. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; IEEE: New York, NJ, USA, 2020; pp. 313–320. [Google Scholar]
- Gao, R.; Zhang, Q.; Chen, Y.; Ma, J. A Taxonomy of Consensus Attacks in Blockchain. Future Gener. Comput. Syst. 2022, 128, 325–338. [Google Scholar] [CrossRef]
- Cheng, J.; Xie, L.; Tang, X.; Xiong, N.; Liu, B. A survey of security threats and defense on Blockchain. Multimed. Tools Appl. 2021, 80, 30623–30652. [Google Scholar] [CrossRef]
- Toapanta, T.S.M.; Del Pozo, D.R.; Izurieta, R.R.; Guamán, J.A.; Orizaga, J.A.; Arellano, R.M.; Hifóng, M.M.B. Blockchain-based Security Model to Mitigate the Risks of a Database for a Public Organization. J. Internet Serv. Inf. Secur. (JISIS) 2024, 14, 78–98. [Google Scholar] [CrossRef]
- Parino, F.; Beiro, M.; Gauvin, L. Analysis of the Bitcoin blockchain: Socio-economic factors behind the adoption. EPJ Data Sci. 2018, 7, 38. [Google Scholar] [CrossRef]
- Popov, S. The Tangle; White Paper; IOTA: Berlin, Germany, 2018. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the EuroSys, Porto, Portugal, 23–26 April 2018. [Google Scholar]
- Buterin, V. Ethereum 2.0 Phase 0—Beacon Chain. 2020. Available online: https://ethereum.org/en/upgrades/beacon-chain/ (accessed on 10 August 2024).
- Kwon, J.; Buchman, E. Cosmos: A Network of Distributed Ledgers. Cosm. Whitepaper 2019, 1–32. [Google Scholar]
- Wen, Y.; Lu, F.; Liu, Y.; Huang, X. Attacks and countermeasures on blockchains: A survey from layering perspective. Comput. Netw. 2021, 191, 107978. [Google Scholar] [CrossRef]
- Kearney, J.J.; Perez-Delgado, C.A. Vulnerability of blockchain technologies to quantum attacks. Array 2021, 10, 100065. [Google Scholar] [CrossRef]
- Allende, M.; León, D.L.; Cerón, S.; Pareja, A.; Pacheco, E.; Leal, A.; Da Silva, M.; Pardo, A.; Jones, D.; Worrall, D.J.; et al. Quantum-resistance in blockchain networks. Sci. Rep. 2023, 13, 5664. [Google Scholar] [CrossRef]
- Hasanova, H.; Baek, U.J.; Shin, M.G.; Cho, K.; Kim, M.S. A survey on blockchain cybersecurity vulnerabilities and possible countermeasures. Int. J. Netw. Manag. 2019, 29, e2060. [Google Scholar] [CrossRef]
- Cooper, E.; Weese, E.; Fortson, A.; Lo, D.; Shi, Y. Cyber Security in Blockchain. In Proceedings of the 2023 IEEE Conference on Dependable and Secure Computing (DSC), Tampa, FL, USA, 7–9 November 2023; IEEE: New York, NJ, USA, 2023; pp. 1–11. [Google Scholar]
- Wang, H.; Wang, Y.; Cao, Z.; Li, Z.; Xiong, G. An overview of blockchain security analysis. In Proceedings of the Cyber Security: 15th International Annual Conference, CNCERT 2018, Beijing, China, 14–16 August 2018; Revised Selected Papers 15. Springer: Singapore, 2019; pp. 55–72. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Georgia, W. Arithmetic Underflow and Overflow Vulnerabilities in Smart Contracts. 2023. Available online: https://101blockchains.com/underflow-and-overflow-vulnerabilities-in-smart-contracts/ (accessed on 22 April 2024).
- Guggenberger, T.; Schlatt, V.; Schmid, J.; Urbach, N. A Structured Overview of Attacks on Blockchain Systems. In Proceedings of the PACIS, Dubai, United Arab Emirates, 12–14 July 2021; p. 100. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the Principles of Security and Trust: 6th International Conference, POST 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2017, Uppsala, Sweden, 22–29 April 2017; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Chen, Y.; Sun, Z.; Gong, Z.; Hao, D. Improving Smart Contract Security with Contrastive Learning-based Vulnerability Detection. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–11. [Google Scholar]
- Luo, F.; Luo, R.; Chen, T.; Qiao, A.; He, Z.; Song, S.; Jiang, Y.; Li, S. Scvhunter: Smart contract vulnerability detection based on heterogeneous graph attention network. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–13. [Google Scholar]
- Zhen, Z.; Zhao, X.; Zhang, J.; Wang, Y.; Chen, H. DA-GNN: A smart contract vulnerability detection method based on Dual Attention Graph Neural Network. Comput. Netw. 2024, 242, 110238. [Google Scholar] [CrossRef]
- Sun, Y.; Gu, L. Attention-based machine learning model for smart contract vulnerability detection. J. Phys. Conf. Ser. 2021, 1820, 012004. [Google Scholar] [CrossRef]
- Lutz, O.; Chen, H.; Fereidooni, H.; Sendner, C.; Dmitrienko, A.; Sadeghi, A.R.; Koushanfar, F. Escort: Ethereum smart contracts vulnerability detection using deep neural network and transfer learning. arXiv 2021, arXiv:2103.12607. [Google Scholar]
- Colin, L.S.H.; Mohan, P.M.; Pan, J.; Keong, P.L.K. An Integrated Smart Contract Vulnerability Detection Tool Using Multi-layer Perceptron on Real-time Solidity Smart Contracts. IEEE Access 2024, 12, 23549–23567. [Google Scholar] [CrossRef]
- Jain, V.K.; Tripathi, M. An integrated deep learning model for Ethereum smart contract vulnerability detection. Int. J. Inf. Secur. 2024, 23, 557–575. [Google Scholar] [CrossRef]
- Zhou, Q.; Zheng, K.; Zhang, K.; Hou, L.; Wang, X. Vulnerability analysis of smart contract for blockchain-based IoT applications: A machine learning approach. IEEE Internet Things J. 2022, 9, 24695–24707. [Google Scholar] [CrossRef]
- Narayana, K.L.; Sathiyamurthy, K. Automation and smart materials in detecting smart contracts vulnerabilities in Blockchain using deep learning. Mater. Today Proc. 2023, 81, 653–659. [Google Scholar] [CrossRef]
- Rabieinejad, E.; Yazdinejad, A.; Parizi, R.M. A deep learning model for threat hunting in ethereum blockchain. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; IEEE: New York, NJ, USA, 2021; pp. 1185–1190. [Google Scholar]
- Ismail, S.; Nouman, M.; Dawoud, D.W.; Reza, H. Towards a lightweight security framework using blockchain and machine learning. Blockchain Res. Appl. 2024, 5, 100174. [Google Scholar] [CrossRef]
- Bresil, M.; Prasad, P.; Sayeed, M.S.; Bukar, U.A. Deep Learning-based Vulnerability Detection Solutions in Smart Contracts: A Comparative and Meta-Analysis of Existing Approaches. IEEE Access 2025, 13, 28894–28919. [Google Scholar] [CrossRef]
- Chen, J.; Wang, W.; Liu, B.; Cai, S.; Towey, D.; Wang, S. Hybrid semantics-based vulnerability detection incorporating a Temporal Convolutional Network and Self-attention Mechanism. Inf. Softw. Technol. 2024, 171, 107453. [Google Scholar] [CrossRef]
- Crisostomo, J.; Bacao, F.; Lobo, V. Machine learning methods for detecting smart contracts vulnerabilities within Ethereum blockchain—A review. Expert Syst. Appl. 2025, 268, 126353. [Google Scholar] [CrossRef]
- Duy, P.T.; Khoa, N.H.; Quyen, N.H.; Trinh, L.C.; Kien, V.T.; Hoang, T.M.; Pham, V.H. Vulnsense: Efficient vulnerability detection in ethereum smart contracts by multimodal learning with graph neural network and language model. Int. J. Inf. Secur. 2025, 24, 48. [Google Scholar] [CrossRef]
- Mohammed, H.A.; Husien, I.M. A Deep Transfer Learning Framework for Robust IoT Attack Detection: A Review. Informatica 2024, 48, 55–64. [Google Scholar] [CrossRef]
- Korba, A.A.; Boualouache, A.; Ghamri-Doudane, Y. Zero-X: A Blockchain-Enabled Open-Set Federated Learning Framework for Zero-Day Attack Detection in IoV. IEEE Trans. Veh. Technol. 2024, 73, 12399–12414. [Google Scholar] [CrossRef]
- Mbaya, E.B.; Adetiba, E.; Badejo, J.A.; Wejin, J.S.; Oshin, O.; Isife, O.; Thakur, S.C.; Moyo, S.; Adebiyi, E.F. SecFedIDM-V1: A secure federated intrusion detection model with blockchain and deep bidirectional long short-term memory network. IEEE Access 2023, 11, 116011–116025. [Google Scholar] [CrossRef]
- Chen, H.; Zhao, X.; Wang, Y.; Zhen, Z. SafeCheck: Detecting smart contract vulnerabilities based on static program analysis methods. Secur. Priv. 2024, 7, e393. [Google Scholar] [CrossRef]
- Sun, Y.; Wu, D.; Xue, Y.; Liu, H.; Wang, H.; Xu, Z.; Xie, X.; Liu, Y. Gptscan: Detecting logic vulnerabilities in smart contracts by combining gpt with program analysis. In Proceedings of the IEEE/ACM 46th International Conference on Software Engineering, Lisbon, Portugal, 14–20 April 2024; pp. 1–13. [Google Scholar]
- Pise, R.G.; Patil, S. Pioneering automated vulnerability detection for smart contracts in blockchain using KEVM: Guardian ADRGAN. Int. J. Inf. Secur. 2024, 23, 1805–1819. [Google Scholar] [CrossRef]
- Singh, A.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R.; Dehghantanha, A. Blockchain smart contracts formalization: Approaches and challenges to address vulnerabilities. Comput. Secur. 2020, 88, 101654. [Google Scholar] [CrossRef]
- Chinen, Y.; Yanai, N.; Cruz, J.P.; Okamura, S. RA: Hunting for re-entrancy attacks in ethereum smart contracts via static analysis. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Virtual, 2–6 November 2020; IEEE: New York, NJ, USA, 2020; pp. 327–336. [Google Scholar]
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Krichen, M.; Lahami, M.; Al-Haija, Q.A. Formal methods for the verification of smart contracts: A review. In Proceedings of the 2022 15th International Conference on Security of Information and Networks (SIN), Sousse, Tunisia, 11–13 November 2022; IEEE: New York, NJ, USA, 2022; pp. 01–08. [Google Scholar]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic review of security vulnerabilities in ethereum blockchain smart contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Li, Z.; Lu, S.; Zhang, R.; Xue, R.; Ma, W.; Liang, R.; Zhao, Z.; Gao, S. SmartFast: An accurate and robust formal analysis tool for Ethereum smart contracts. Empir. Softw. Eng. 2022, 27, 197. [Google Scholar] [CrossRef]
- Cao, X.; Zhang, J.; Wu, X.; Liu, B. A survey on security in consensus and smart contracts. Peer-to-Peer Netw. Appl. 2022, 15, 1008–1028. [Google Scholar] [CrossRef]
- Li, B.; Pan, Z.; Hu, T. EvoFuzzer: An Evolutionary Fuzzer for Detecting Reentrancy Vulnerability in Smart Contracts. IEEE Trans. Netw. Sci. Eng. 2024, 11, 5790–5802. [Google Scholar] [CrossRef]
- Praitheeshan, P.; Pan, L.; Yu, J.; Liu, J.; Doss, R. Security analysis methods on ethereum smart contract vulnerabilities: A survey. arXiv 2019, arXiv:1908.08605. [Google Scholar]
- Feng, Z.; Feng, Y.; He, H.; Zhang, W.; Zhang, Y. A bytecode-based integrated detection and repair method for reentrancy vulnerabilities in smart contracts. IET Blockchain 2024, 4, 235–251. [Google Scholar] [CrossRef]
- Gao, C.; Yang, W.; Ye, J.; Xue, Y.; Sun, J. sGuard+: Machine learning guided rule-based automated vulnerability repair on smart contracts. ACM Trans. Softw. Eng. Methodol. 2024, 33, 1–55. [Google Scholar] [CrossRef]
- Senanayake, J.; Kalutarage, H.; Petrovski, A.; Piras, L.; Al-Kadri, M.O. Defendroid: Real-time Android code vulnerability detection via blockchain federated neural network with XAI. J. Inf. Secur. Appl. 2024, 82, 103741. [Google Scholar] [CrossRef]
- Priya, J.C.; Rudzki, K.; Nguyen, X.H.; Nguyen, H.P.; Chotechuang, N.; Pham, N.D.K. Blockchain-Enabled Transfer Learning for Vulnerability Detection and Mitigation in Maritime Logistics. Pol. Marit. Res. 2024, 31, 135–145. [Google Scholar] [CrossRef]
- He, N.; Wang, H.; Wu, L.; Luo, X.; Guo, Y.; Chen, X. A survey on eosio systems security: Vulnerability, attack, and mitigation. Front. Comput. Sci. 2025, 19, 196806. [Google Scholar] [CrossRef]
- Yang, H.; Gu, X.; Chen, X.; Zheng, L.; Cui, Z. CrossFuz: Cross-contract fuzzing for smart contract vulnerability detection. Sci. Comput. Program. 2024, 234, 103076. [Google Scholar] [CrossRef]
- Shou, C.; Liu, J.; Lu, D.; Sen, K. LLM4Fuzz: Guided fuzzing of smart contracts with large language models. arXiv 2024, arXiv:2401.11108. [Google Scholar]
- Zheng, Z.; Su, J.; Chen, J.; Lo, D.; Zhong, Z.; Ye, M. DAppSCAN: Building large-scale datasets for smart contract weaknesses in dapp projects. IEEE Trans. Softw. Eng. 2024, 50, 1360–1373. [Google Scholar] [CrossRef]
- Cai, J.; Li, B.; Zhang, T.; Zhang, J.; Sun, X. Fine-grained smart contract vulnerability detection by heterogeneous code feature learning and automated dataset construction. J. Syst. Softw. 2024, 209, 111919. [Google Scholar] [CrossRef]
- Victor, F.; Lüders, B.K. Measuring ethereum-based erc20 token networks. In Proceedings of the Financial Cryptography and Data Security: 23rd International Conference, FC 2019, Frigate Bay, Saint Kitts and Nevis, 18–22 February 2019; Revised Selected Papers 23. Springer: Berlin/Heidelberg, Germany, 2019; pp. 113–129. [Google Scholar]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Li, B.; Pan, Z.; Hu, T. Redefender: Detecting reentrancy vulnerabilities in smart contracts automatically. IEEE Trans. Reliab. 2022, 71, 984–999. [Google Scholar] [CrossRef]
- Wu, G.; Wang, H.; Lai, X.; Wang, M.; He, D.; Chan, S. A comprehensive survey of smart contract security: State of the art and research directions. J. Netw. Comput. Appl. 2024, 226, 103882. [Google Scholar] [CrossRef]
- He, D.; Wu, R.; Li, X.; Chan, S.; Guizani, M. Detection of vulnerabilities of blockchain smart contracts. IEEE Internet Things J. 2023, 10, 12178–12185. [Google Scholar] [CrossRef]
- Yao, Y.; Duan, J.; Xu, K.; Cai, Y.; Sun, Z.; Zhang, Y. A survey on large language model (llm) security and privacy: The good, the bad, and the ugly. High-Confid. Comput. 2024, 4, 100211. [Google Scholar] [CrossRef]
- Homoliak, I.; Venugopalan, S.; Hum, Q.; Szalachowski, P. A security reference architecture for blockchains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Seoul, Republic of Korea, 14–17 May 2019; IEEE: New York, NY, USA, 2019; pp. 390–397. [Google Scholar]
- He, Z.; Li, Z.; Yang, S.; Qiao, A.; Zhang, X.; Luo, X.; Chen, T. Large language models for blockchain security: A systematic literature review. arXiv 2024, arXiv:2403.14280. [Google Scholar]
- Venkatesan, K.; Rahayu, S.B. Blockchain security enhancement: An approach towards hybrid consensus algorithms and machine learning techniques. Sci. Rep. 2024, 14, 1149. [Google Scholar] [CrossRef]
- Ali, S.; Li, Q.; Yousafzai, A. Blockchain and federated learning-based intrusion detection approaches for edge-enabled industrial IoT networks: A survey. Ad Hoc Netw. 2024, 152, 103320. [Google Scholar] [CrossRef]
- Taher, S.S.; Ameen, S.Y.; Ahmed, J.A. Advanced Fraud Detection in Blockchain Transactions: An Ensemble Learning and Explainable AI Approach. Eng. Technol. Appl. Sci. Res. 2024, 14, 12822–12830. [Google Scholar] [CrossRef]
- Kim, S.K. Automotive vulnerability analysis for deep learning blockchain consensus algorithm. Electronics 2021, 11, 119. [Google Scholar] [CrossRef]
- Ibba, G.; Baralla, G.; Destefanis, G. Large Language Models for Synthetic Dataset Generation: A Case Study on Ethereum Smart Contract DoS Vulnerabilities. In Proceedings of the IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER) 2025, Montréal, QC, Canada, 4–7 March 2025. [Google Scholar]
- Li, Z.; Zou, D.; Xu, S.; Ou, X.; Jin, H.; Wang, S.; Deng, Z.; Zhong, Y. Vuldeepecker: A deep learning-based system for vulnerability detection. arXiv 2018, arXiv:1801.01681. [Google Scholar]
- Kong, L.; Luo, S.; Pan, L.; Wu, Z.; Li, X. A multi-type vulnerability detection framework with parallel perspective fusion and hierarchical feature enhancement. Comput. Secur. 2024, 140, 103787. [Google Scholar] [CrossRef]
- SWC Registry. Smart Contract Weakness Classification and Test Cases. Available online: https://swcregistry.io/ (accessed on 5 May 2022).
- Hasan, M.; Rahman, M.S.; Janicke, H.; Sarker, I.H. Detecting anomalies in blockchain transactions using machine learning classifiers and explainability analysis. Blockchain Res. Appl. 2024, 5, 100207. [Google Scholar] [CrossRef]
- Mounnan, O.; Manad, O.; Boubchir, L.; El Mouatasim, A.; Daachi, B. A review on deep anomaly detection in blockchain. Blockchain Res. Appl. 2024, 5, 100227. [Google Scholar] [CrossRef]
- Mishra, S. Blockchain and machine learning-based hybrid IDS to protect smart networks and preserve privacy. Electronics 2023, 12, 3524. [Google Scholar] [CrossRef]
- He, F.; Li, F.; Liang, P. Enhancing smart contract security: Leveraging pre-trained language models for advanced vulnerability detection. IET Blockchain 2024, 4, 543–554. [Google Scholar] [CrossRef]
- Radanliev, P. Artificial intelligence and quantum cryptography. J. Anal. Sci. Technol. 2024, 15, 4. [Google Scholar] [CrossRef]
- Gai, Y.; Zhou, L.; Qin, K.; Song, D.; Gervais, A. Blockchain large language models. arXiv 2023, arXiv:2304.12749. [Google Scholar]
- Brew, B. Can Artificial Intelligence Hack Blockchain Technology? 2023. Available online: https://medium.com/@blockchaindevelopment121/can-artificial-intelligence-hack-blockchain-technology-e26ac4f17c3 (accessed on 9 February 2024).
- Knight, O. Ethereum Bot Gets Attacked for 20M as Validator Strikes Back. 2023. Available online: https://www.coindesk.com/business/2023/04/03/ethereum-mev-bot-gets-attacked-for-20m-as-validator-strikes-back/ (accessed on 12 April 2024).
- Coghlan, J. This AI Chatbot Is Either an Exploiter’s Dream or Their Nightmare. 2022. Available online: https://cointelegraph.com/news/this-ai-chatbot-is-either-an-exploiter-s-dream-or-their-nightmare (accessed on 19 August 2024).
- Kayikci, S.; Khoshgoftaar, T.M. Blockchain meets machine learning: A survey. J. Big Data 2024, 11, 9. [Google Scholar] [CrossRef]
- Palaiokrassas, G.; Bouraga, S.; Tassiulas, L. Machine Learning on Blockchain Data: A Systematic Mapping Study. arXiv 2024, arXiv:2403.17081. [Google Scholar]
- Azad, P.; Akcora, C.G.; Khan, A. Machine Learning for Blockchain Data Analysis: Progress and Opportunities. arXiv 2024, arXiv:2404.18251. [Google Scholar] [CrossRef]


| Study | Taxonomy Type | Categories | Key Features/Limitations |
|---|---|---|---|
| Bhushan et al. (2021) [27] | Threat-based | 4 | General classification of threats; lacks architecture-specific alignment. |
| Saad et al. (2019) [28] | Surface-based | 3 | Abstract attack surfaces; does not directly align with blockchain system layers. |
| Mosakheil (2018) [29] | Impact-based | 5 | Categorizes by severity and consequences; limited structural insight. |
| Dasgupta et al. (2019) [31] | Functional-based | 8 | Detailed, but mixes threat types and system components. |
| Anita et al. (2019) [32] | Type-based | 7 | Catalog of known attacks; lacks architectural grouping. |
| Lee (2019) [18] | System-component | 6 | Focuses on blockchain node internals; limited generalizability. |
| Mollajafari & Bechkoum (2023) [5] | Layer-based | 7 | Strong emphasis on smart contract centralization risks; contract layer focus. |
| Gao et al. (2022) [34] | Consensus-attack | 6 | Comprehensive categorization of consensus-specific threats; does not cover full system layers. |
| Cheng et al. (2021) [35] | Threat-centric layered | 5 | Maps attacks to technical stack; lacks emphasis on adaptability across architectures. |
| Our Work | Layer-based | 5 | Scalable, architecture-aligned mapping of attacks to blockchain layers; supports DAG, BFT, sharded, hybrid chains. |
| Attack Name | Layer | Impact | Counter Measure |
|---|---|---|---|
| Transaction Malleability | Data | Network reliability and Integrity. | Hashing of the transactions, Time commitment scheme. |
| Quantum | Data | Cryptographic algorithm. | Quantum resistant key Scheme. |
| Race | Network | Double spending, System integrity. | Enforcing multiple transaction confirmation. |
| Finney | Network | Double spending, Integrity, Trust and reliability. | Increased the required number of Block confirmations for transactions. |
| Replay | Network | Transaction duplication, Double spending, Network congestion. | Transaction sequencing techniques, Digital signatures. |
| Eclipse | Network | Network partitioning, Isolation, Forking and reorganization. | Detection through monitoring, Introducing peer discovery protocols. |
| DDoS | Network | Service disruption, unavailability, Network congestion, and performance degradation. | Traffic filtering, Rate limiting, IP blacklisting. |
| BGP Hijacking | Network | Routing manipulation, Network isolation, Dropped transactions. | BGP monitoring, Relay network. |
| Routing | Network | Network partitioning, Delay in transactions. | Audit, Verification, Cryptography. |
| DNS | Network | Service disruption and unavailability, Phishing, and Information leakage. | Improved authentication Scheme, Monitoring DNS traffic. |
| 51% | Consensus | Double spending, Network disruption. | Diversify mining pool, Increased hash rate, improved consensus algorithms. |
| Time-jacking | Consensus | Consensus disruption, Undermined integrity, Trust, and Reliability. | Enhanced timestamp validation. |
| Sybil | Network | Identity, Integrity, Consensus, Double spending. | Robust identity verification such as PoW, PoS. |
| Vector 76 | Consensus | Double spending, Loss of trust | Multiple confirmation, Improved consensus. |
| Selfish Mining | Consensus | Mining pool, Double spending, and centralization. | Fork resolution scheme, Rational mining scheme. |
| Block Withholding | Consensus | Disruption of consensus, Centralization, Reduced transaction speed. | Zeroblock algorithm, Pool incentives. |
| Bribery | Consensus | Integrity, Reduced confidence, Trust Pool. | Improved consensus such as PoS and strong incentives. |
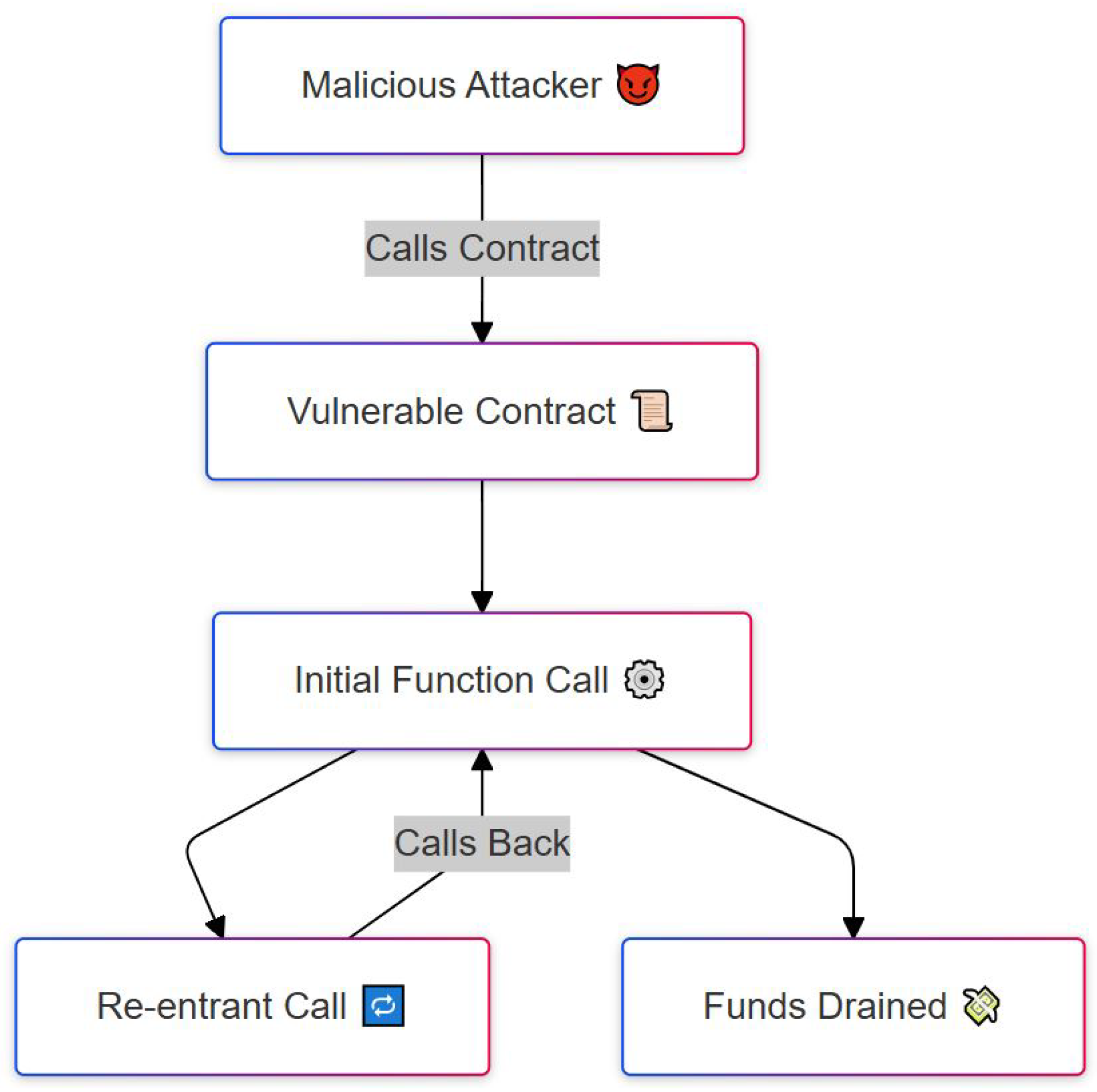
| Re-entrancy | Contract | Wallet theft, Disruption of application. | Security Audits, Secure coding practices, Checks-effects-interactions (CEI) pattern. |
| Integer Overflow | Contract | Unintended token transfer, DoS, Smart contract failure. | Careful smart contract design, Symbolic execution for detection. |
| Short Address | Contract | Validation error | Automatic sanitization techniques. |
| Balance | Contract | Double Spending, Reduced Network Efficiency. | Fast block confirmation, Monitoring. |
| Cryptojacking | Application | Performance degradation, Increased operational cost. | Detection software, Network monitoring. |
| Cold wallet | Application | Loss of funds. | Careful Smart Contract design, Multifactor authentication. |
| Hot wallet | Application | Loss of funds and trust. | Regular software upgrade, Multifactor authentication. |
| Dictionary | Application | Private key compromise, Unauthorized access and control. | Strong password, Hardware wallet. |
| Malware | Application | Private key compromise, Network integrity. | Usage of antimalware or detection software. |
| Architecture | Applies | Adjustments | Remarks |
|---|---|---|---|
| Chain-based (Bitcoin, Ethereum) | Yes | No | Fully compatible with all five layers. |
| DAG-based (IOTA [38], Hedera) | Yes | Minor | Non-linear consensus, but threats map to Network & Consensus layers. |
| Hybrid (Hyperledger Fabric [39]) | Yes | Yes | No token layer; chaincode maps to Contract. Rename Consensus & Incentive. |
| Sharded (Ethereum 2.0 [40]) | Yes | Yes | Cross-shard comm. affects Network/Consensus layers. |
| BFT-based (Cosmos, Tendermint [41]) | Yes | Minor | Consensus layer must model validator-specific attacks. |
| Categories | References | Strengths | Weaknesses |
|---|---|---|---|
| Deep Learning and Machine Learning | [52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69] |
|
|
| Static and Program Analysis | [70,71,72,73,74,75,76,77,78,79,80,81,82] |
|
|
| Vulnerability Repair and Fraud Detection | [79,82,83,84,85,86] |
|
|
| Fuzzing and Cross-Contract Analysis | [66,80,87,88] |
|
|
| Datasets and Evaluations | [65,73,78,89,90,91,92,93,94] |
|
|
| Comprehensive Surveys and Reviews | [63,65,68,73,77,79,81,93,95,96,97,98,99] |
|
|
| Domain-Specific Enhancements | [63,64,69,79,93,99,100,101,102,103,104] |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Islam, M.J.; Islam, S.; Hossain, M.; Noor, S.; Islam, S.M.R. Securing Blockchain Systems: A Layer-Oriented Survey of Threats, Vulnerability Taxonomy, and Detection Methods. Future Internet 2025, 17, 205. https://doi.org/10.3390/fi17050205
Islam MJ, Islam S, Hossain M, Noor S, Islam SMR. Securing Blockchain Systems: A Layer-Oriented Survey of Threats, Vulnerability Taxonomy, and Detection Methods. Future Internet. 2025; 17(5):205. https://doi.org/10.3390/fi17050205
Chicago/Turabian StyleIslam, Mohammad Jaminur, Saminur Islam, Mahmud Hossain, Shahid Noor, and S. M. Riazul Islam. 2025. "Securing Blockchain Systems: A Layer-Oriented Survey of Threats, Vulnerability Taxonomy, and Detection Methods" Future Internet 17, no. 5: 205. https://doi.org/10.3390/fi17050205
APA StyleIslam, M. J., Islam, S., Hossain, M., Noor, S., & Islam, S. M. R. (2025). Securing Blockchain Systems: A Layer-Oriented Survey of Threats, Vulnerability Taxonomy, and Detection Methods. Future Internet, 17(5), 205. https://doi.org/10.3390/fi17050205










