Abstract
The rapid implementation of multi-cloud architectures, such as the integration of services from multiple cloud providers, gives organizations enhanced flexibility, resilience, and vendor independence. However, the multi-cloud model presents complicated security challenges due to diverse platforms, fragmented governance, and increased areas of concern. This paper presents a comprehensive literature review of the multi-cloud environment arena, focusing on the analysis of threats, vulnerabilities, cost optimization, mitigation strategies, and research trends. It covers a comprehensive range of risks, including data breaches, insider threats, API exploitation, configuration errors, and emerging multi-vector attacks, as well as the cumulative complexity of aligning policies, managing identities, and ensuring compliance across diverse providers. The review analyzes existing and proposed defence mechanisms, spanning cryptographic techniques, fuzzy-logic decision frameworks, AI and ML-driven detection systems, as well as integrated Identity and Access Management (IAM) systems. Analysis of relevant literature reveals a progression from basic foundational encryption systems toward more sophisticated, policy-driven, and collaboration-capable security frameworks. Additionally, the paper identifies significant research gaps in real-world validation, cost optimization, and unified governance models. This research departs from prior work by integrating multiple perspectives rather than limiting its scope to a single area such as security, defence, or cost optimization. It also provides new researchers with comprehensive background information on cloud architecture within a single article.
1. Introduction
The Cloud has emerged as a transformative force for entire industries, not only revolutionizing IT but also driving immense changes in sectors worldwide. It is observed that adaptation continues to accelerate, driven by growing demand for scalable and affordable infrastructure services that provide fast access to applications. The recent statistics illustrate that the cloud’s market share achieved 43% agility [1,2], as it has been mostly adopted by small to medium-sized enterprises, in particular, who have embraced cloud solutions to lower infrastructure expenditures and improve operational agility [3,4]. Financial services firms are leading the charge in adopting multi-cloud approaches as more than 90% of businesses worldwide use cloud computing in their operations [5]. In addition, 84% of organizations report that their workloads are distributed across various cloud services, and tech companies are twice as likely as other industries to have recently hired new cloud professionals [5]. Although cloud computing provides a range of services, including infrastructure, platforms, and applications, ensuring the security of sensitive big data remains a significant struggle. Industries such as healthcare, defence, and government routinely store confidential information in cloud environments, yet users often lack confidence in their providers’ protective measures [1]. Cloud environments encompass a variety of components, including networks, operating systems, memory management systems, and even databases, all of which can be targeted by different types of security attacks [1]. The conventional dependency on a single cloud provider in the cloud computing space is diminishing due to concerns related to service availability and security threats, such as potential malicious insiders.
Figure 1 highlights the evolution of cloud computing from virtualization in 1967 to modern AI, the Internet of Things (IoT), and edge computing. It highlights key developments, such as SaaS, hybrid cloud, and the shift toward intelligent and distributed systems.
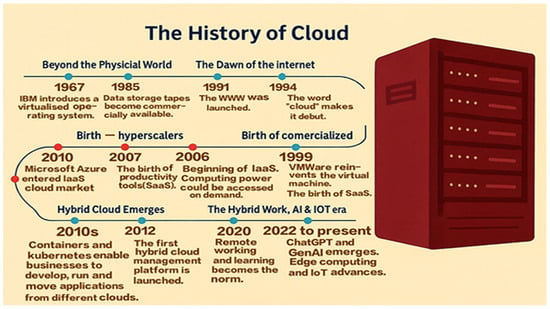
Figure 1.
Milestones in Cloud History–Key Developments from Year 1967 to Present. Reproduced from [6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23], no modifications made. © Original authors/publisher.
As a result, there is an increasing adoption of multi-cloud strategies frequently referred to as inter-cloud or cloud-of-clouds, where services are distributed across multiple cloud providers. This shift demonstrates the evolution of cloud computing from centralized, replication-focused systems to more diverse, technology-driven solutions tailored to specific contexts, and it is vulnerable to attacks [1,24,25,26]. Consequently, businesses are now at times orchestrating workflows in a sequential or parallel manner across multiple providers, leveraging the flexibility and resiliency to run their applications, which is referred to as a multi-cloud approach. A multi-cloud environment combines and interconnects two or more private or public cloud platforms to leverage their collective strengths, such as optimizing data storage capacity, improving security measures, ensuring confidentiality, facilitating efficient sharing and collaboration within disparate systems [27,28,29]. The Futurescape report issued by International Data Corporation predicted, in the context of multi-cloud adoption, that by 2020, more than 85% of large enterprises would have shifted their IT operations to a multi-cloud environment [27,30,31].
Despite the many advantages of multi-cloud, it still lacks in ensuring the security of stored data. To address this issue, many researchers have focused on multi-cloud approaches to enhance data security [1,4,32]. This paper concentrates on the major data security issues and research gaps in multi-cloud environments. It analyzes how sharing data across multiple potentially untrusted cloud providers raises risks, particularly concerning highly sensitive information such as medical records, military or government data, and credit card information. It emphasizes the methods that prevent external attackers and malicious insiders from accessing the data.
To the best of our knowledge, limited prior reviews have simultaneously examined the interconnections among core domains of multi-cloud research. This study integrates four primary perspectives, such as security, Identity and Access Management (IAM), data provenance, and SLA or cost-aware orchestration, into a unified taxonomy and analytical framework. By correlating these axes through consistent evaluative criteria and comparative discussion, the paper provides a balanced and comprehensive understanding of multi-cloud environments that extends beyond domain-specific analyses. In alignment with this aim, the primary objectives of this study are the following:
- Comprehensive literature review of multi-cloud security: Comprehensive collection and synthesis of recent research on threats, defences, and operational concerns in multi-cloud environments.
- Taxonomy of attacks and defence families: Clear classification of threat classes and countermeasure categories.
- Comparative trade-off analysis: Evaluation of security techniques in terms of cost, latency, complexity, and deployment feasibility across providers.
- Identification of critical gaps, practical research agenda, and recommendations.
The rest of the paper is organized as follows. Section 2 provides background on cloud service models, deployment types, and traces the evolution of hybrid IT and multi-cloud strategies as well as their motivating trade-offs. Section 3 analyzes the threat landscape and specific attack classes that affect multi-cloud systems. Section 4 presents a comparative study of prior works. Section 5 discusses persistent security challenges unique to multi-cloud architecture. Section 6 surveys possible solutions and frameworks, also highlights emerging technologies and enterprise-grade solutions, primarily to influence multi-cloud security. Section 7 synthesizes the most important research gaps and recommended directions for future research. Conclusions along with forthcoming research and evaluation priorities are discussed in Section 8.
2. Background
Cloud refers to a model of service delivery that enables users to access IT resources such as servers, storage, and software from a shared pool on the internet, thereby providing ubiquitous and on-demand access [33,34]. In the same way that a utility functions, it abstracts the complexities of underlying hardware and software infrastructures from end users. Most importantly, the term “cloud” gained the most user traction in 2006, which led to a surge in its popularity [35]. The term “cloud computing” refers to a specific area of interest within distributed computing, specifically the delivery and use of services provided by providers such as Google, IBM, Amazon, and others. Although often referred to as an advanced and sophisticated paradigm, cloud computing has existed for several decades [36]. The National Institute of Standards and Technology (NIST) [4] describes cloud computing as
Definition 1.
A model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Figure 2 highlights cloud computing as a virtualized, service-based model that offers scalable, real-time access to IT resources. It emphasizes mobility, data center delivery, shared infrastructure, and consumption-based billing.
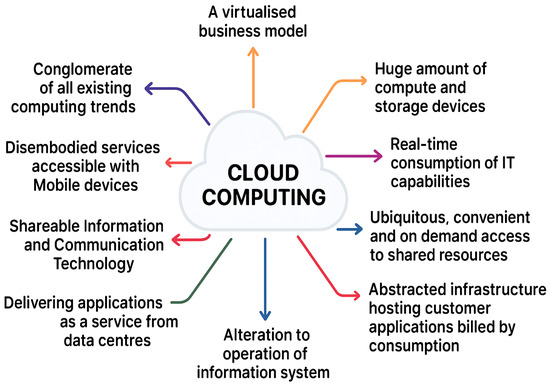
Figure 2.
Definitions of Cloud Computing. Reproduced from [37,38,39,40,41,42,43,44], no modifications made. © Original authors/publisher.
Cloud computing offers a cost-effective approach to managing modern IT applications and systems by enabling efficient resource allocation and utilizing a pay-per-use billing model [45,46,47,48,49,50]. It supports automatic scaling based on demand, minimizes initial capital expenditures through a pay-as-you-go pricing structure, and enables the rapid deployment of applications in virtualized environments [51,52,53]. In subscription-based service frameworks, the reliability and integrity of technical support are ensured through service-level agreements (SLAs) [36]. Through the use of distributed and redundant infrastructure, cloud services offer high availability, improved reliability, and robust security while also providing integrated disaster recovery and compliance with regulations. As a result, this model enables organizations, particularly small and medium enterprises, to concentrate on innovation, leverage advanced technologies such as big data analytics and machine learning, and engage in seamless global collaboration with reduced latency [54]. Thus, cloud computing has emerged as a critical component for contemporary organizations that want to achieve greater agility, operational efficiency, and sustained competitive advantage. The Cloud computing architecture comprises two primary components [36]. The front end, as the user-facing segment, encompasses the interfaces and devices that enable clients to access and interact with the system. The back end, as the infrastructural segment, consists of servers, storage devices, networking equipment, and other resources that provision and support cloud services. Together, these front-end and back-end elements form the complete cloud computing environment, with the user interface serving as the principal endpoint for user engagement.
Figure 3 illustrates the layered cloud computing model, detailing user interaction with SaaS, PaaS, and IaaS through networks and front-end interfaces. It highlights how providers manage infrastructure, APIs, and security to deliver services.
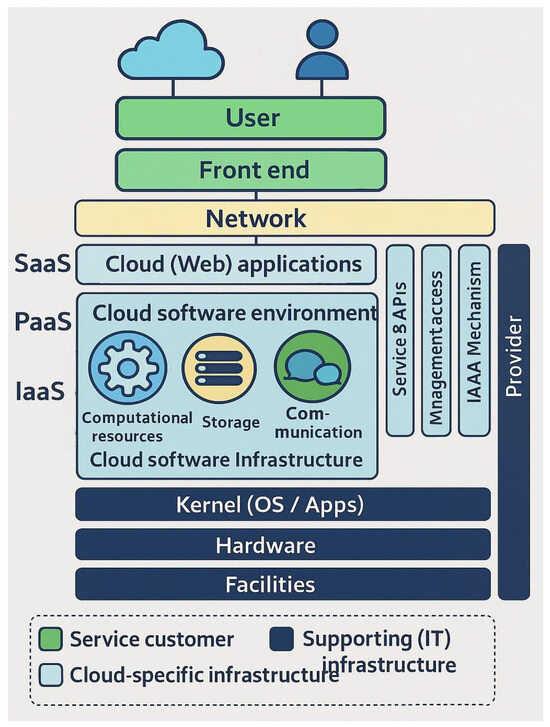
Figure 3.
Cloud Service Layers and Shared Responsibilities. Reproduced from [55], no modifications made. © Original authors/publisher.
2.1. Cloud Service Providers
Cloud computing underpins a broad spectrum of business services by providing demand-driven computing capabilities that are scalable and available on demand. Cloud service providers offer a variety of storage solutions, including object, block, and file storage—tailored to meet diverse data requirements [56]. These services are hosted in large-scale distributed data centers that span multiple geographic locations [57]. Providers strategically balance the efficient utilization of physical infrastructure with the optimization of network performance and cost-effective resource allocation. Fundamentally enabled by virtualization technologies and distributed network architectures, cloud computing empowers users to access a wide range of services without the need to own or manage physical infrastructure. This model provides scalable, cost-effective technology solutions for both enterprises and individual users [58]. Cloud computing is a service-oriented model that offers pay-per-use infrastructure, platforms, and software as services over the Internet [36,57,59]. Initially, this field emerged with Information- as well as Software services through Amazon Web Services and Salesforce.com, further branching out vertically through a middleware framework called Platform-as-a-Service [60]. This development, demonstrated by platforms such as Force.com and Google App Engine, streamlines resource consumption and facilitates cloud-based application development [60].
Cloud-based storage offerings are engineered to address a wide range of needs, for instance, object storage holds large amounts of unstructured data, block storage supports virtual machines, and file storage shares data through network-attached storage [56]. Additionally, cloud platforms enable data access and manipulation through services such as Amazon S3, Microsoft SkyDrive, and Amazon EC2, while also supporting collaborative activities and version control through tools such as Google Apps and repository services [4,61]. Beyond individual or small-scale applications, cloud computing plays an integral role in enterprise operations. For example, it supports large-scale media delivery as seen with Netflix, and extends to routine services such as email backup through Gmail and synchronization with smartphones [62,63].
Table 1 highlighted the summarization of cloud services from major providers, categorized by service model (IaaS, PaaS, SaaS) and their core functions. It highlights how different platforms support various computing needs, including storage, Customer Relationship Management(CRM), project management, and development.

Table 1.
Cloud Providers and Services provided by them [37].
Ensuring the security of customer data represents a primary obligation for cloud service providers, who must also accept accountability for any vulnerabilities that might compromise their clients’ service infrastructures [4]. By actively leveraging cloud-based networking and infrastructure platforms, users obtain rapid, location-independent access to information, extensive data storage and recovery capabilities, robust defences against unauthorized intrusion, and fine-grained, on-demand security controls [64]. Furthermore, deliberate optimization of cloud services across emerging domains such as microservices architectures, big data analytics, the IoT, and eScience holds significant promise for advancing both industrial applications and scholarly research endeavours [65,66,67].
2.2. The Evolution of Hybrid and Multi-Cloud
The cloud computing market is expanding quickly, with a valuation of USD 0.68 trillion in 2024 and is expected to reach USD 1.44 trillion by 2029. This demonstrates a solid CAGR of 16.40% in the coming years [5]. The growth of the Internet of Things fuels the expansion. The shift in data characterizes the IoT paradigm, which has transitioned from centralized locations to edge-computed locations; therefore, traditional cloud computing is less efficient than distributed computing CapEx and OpEx services, as the number of computing and storage services required is overwhelming [24]. Initially, as cloud computing companies migrated their applications and workloads onto the public cloud, they quickly realized that relying on one single cloud service provider did not provide the best scalability, cost management, or performance [36]. Across recent years, Cloud services have evolved from a single external computing service provider to a broad, context-aware, and technology-driven system, resulting in users moving from dependence on a single cloud vendor to multi-vendor cloud services. The optimization of multi-cloud approaches has been driven by concerns regarding service downtimes or failures, as well as hostile insider risks in single cloud environments, which have set the stage for inter-cloud and cloud-of-clouds concepts [4,24]. To maximize the available resources in a flexible, powerful, and efficient manner, organizations have adopted hybrid and multi-cloud strategies, which outsource both private and public cloud IT services [64,68]. Multi-cloud is a unified cloud service that enables the integration of multiple cloud services from different providers to optimize the workload hosting, data storage, security, and sharing [27,28,29]. In a single cloud environment, an attack may compromise the data confidentiality, leading to data loss, and subsequently resulting in data unavailability [69,70]. Conversely, utilizing a multi-cloud approach mitigates this risk by replicating data across multiple cloud infrastructures; if one cloud is compromised, another continues to provide the necessary data, ensuring its availability remains unaffected [4,69]. This allows companies to optimize resource utilization by leveraging the capabilities of each provider, minimizing the risks associated with vendor lock-in. Additionally, businesses can change service providers or bring on new offerings without hassle as their needs change [27,71,72,73]. In contrast to hybrid cloud strategies that combine private and public clouds to maximize resource utilization, multi-cloud approaches focus on utilizing different public cloud vendors such as Amazon Web Services, Azure, and GCP for specific business requirements [73]. Despite the difficulties faced, the institutions are still implementing hybrid and multi-cloud approaches to enhance performance and minimize risks, which stresses the need to analyze these shifts for optimizing the security of cloud ecosystems while ensuring their growth [5].
The challenges, benefits, and characteristics of the different cloud computing deployment models are highlighted in Table 2. The model is designed to help an organization define its objectives and scope systematically.

Table 2.
Overview of Cloud Deployment Strategies with Benefits and Challenges of Cloud Deployment Models [74].
There is an emerging trend in new research analyzing multi-cloud structures [4,75,76,77,78] that utilizes multiple cloud services within the same company, thereby reducing dependence on a single provider [64]. However, this shift introduces risk, now a major security challenge [79], especially in the areas of threat detection and management, and multi-clouds have become the target of complex cyber-attacks [64].
4. Comparative Study
As cloud computing has matured, both researchers and industry practitioners have increasingly adopted multi-cloud approaches, which have advanced over time. In particular, recent studies have focused on the infrastructural challenges of integrating and orchestrating resources across several clouds, where resource federation and unified management seem to be the most vibrant areas of research [27]. Security remains the most prominent barrier impeding the adoption of cloud services, while multi-cloud approaches add further complexities to protection; they also provide new opportunities to enhance control over data and services while upholding confidentiality, integrity, and availability. Implementing a multi-cloud approach enhances data confidentiality by distributing information across multiple providers, which improves confidentiality while addressing significant storage challenges, such as outages, data corruption, privacy violations, and vendor lock-in [24,139]. Different types of security measures have been formulated to address the vulnerabilities and strengthen the overall protection for data, ensuring reliable privacy during data provision and storage in a resilient manner. Table 6 provides a comparative overview of multi-cloud security research, highlighting each study’s objectives, applied mechanisms, data integrity considerations, and key limitations. All numerical performance metrics are reported exactly as stated in the original studies. Datasets and evaluation contexts vary across works. Therefore, the values are not directly comparable. The performance metrics reported across prior studies use heterogeneous datasets and evaluation protocols. Thus, the values in Table 6 are reproduced exactly as stated in the original papers and are not intended for direct numerical comparison. When a study did not provide a specific metric, this is noted as ‘Not reported in the original study’.

Table 6.
Comparative analysis of related works.
4.1. Literature Search Description and Selection
To maintain the transparency of the construction of comparative tables, we applied a structured, non-systematic search approach consistent with a comprehensive narrative literature review. Relevant studies related to multi-cloud security, IAM, provenance, and SLA or cost-aware orchestration were identified across the scholarly sources, including IEEE Xplore, ACM Digital Library, SpringerLink, Elsevier, ScienceDirect, Google Scholar, MDPI, and arXiv.
4.2. Search Scope
The search covered publications from 2009 to 2025, reflecting the period during which multi-cloud architectures, data security models, and defence mechanisms matured.
4.3. Search Keywords
“multi-cloud security”, “multi-cloud architecture”, “cross-cloud identity management”, “multi-cloud provenance”, “multi-cloud orchestration”, “cloud cost optimization”, “multi-cloud data security”.
4.4. Inclusion Basis
Studies were included if they met the following conditions:
- Addressed multi-cloud architectures.
- Examined at least one of the core domains in this review, such as security, IAM, provenance, or orchestration.
- Provided conceptual, architectural, empirical, or technical contributions relevant to multi-cloud environments.
4.5. Exclusion Basis
- Works limited to single-cloud scenarios.
- Non-technical opinion articles or introductory cloud overviews.
- Duplicated content between preprints and published versions.
With the increasing reliance on multi-cloud environments for distributed data processing and storage, securing inter-cloud interactions has become a central research focus. Foundational security techniques such as AES, RSA, and hybrid encryption mechanisms (e.g., Feistel-AES) [1,33], have been widely adopted to ensure data confidentiality and secure transmission, often paired with segmentation and indexing strategies [145,147] to minimize exposure risks. To enhance resiliency and mitigate single-point failures, secret sharing schemes such as Shamir’s algorithm [69] and Byzantine fault tolerance (BFT) [27] have been integrated into hybrid architectures to achieve secure, redundant storage across diverse clouds. Recognizing that encryption alone is insufficient, the research progressed toward incorporating dynamic and behaviour-based access control models, as demonstrated in works proposing subjective-objective trust mechanisms [148], enhanced mutual trust algorithms [144], and reputation-driven models [45,142]. These models offer real-time adaptation to user behaviour and cloud reputation, addressing gaps in static role-based models. Further sophistication was introduced through attribute-based encryption (ABE) and digital signature integration [149,151], enabling fine-grained authorization while preserving policy confidentiality. Addressing inter-cloud trust and orchestration, federated brokers and middleware layers have been designed [141,152], often leveraging zero-trust principles and service meshes for secure microservice-level interaction [140]. Parallel to this, monitoring-as-a-service solutions such as CLAMS [150] provided visibility across SaaS, PaaS, and IaaS layers, ensuring SLA enforcement and anomaly detection. In healthcare scenarios, secure visualization and anonymized data access emerged as critical, leading to privacy-preserving multi-cloud models tailored for 3D data and patient-centric workflows [143,145,151]. Blockchain-based trust enforcement [142] and access brokers further addressed the need for transparent, immutable activity logging. Despite these advancements, challenges persist, especially in areas of unified IAM, policy synchronization, and real-world adversarial resilience, as highlighted in governance-centric studies [56] and authentication-focused works [79]. These findings collectively underscore a progressive research trajectory from cryptographic foundations to intelligent, policy-aware, and interoperable multi-cloud security frameworks, essential for scalable and trustworthy digital ecosystems.
While different clouds can help organizations avoid vendor lock-in and enhance redundancy, the disparate specialized services utilized can result in a fragmented and inefficient cost structure. Consequently, optimizing costs is essential to control over provisioning, dormant resources, and erratic invoicing, all of which negatively impact ROI. Due to factors such as varying pricing strategies, inaccessibility to proprietary billing information, and constant shifts in pricing frameworks, optimizing costs in multi-cloud environments has received little attention in the scholarly literature, which is quite unfortunate considering its importance. As a result, most research focuses on issues such as security, performance, and interoperability while neglecting cost optimization, which remains a critical and underexplored domain. Table 7 presents a summary of multi-cloud cost optimization algorithms, outlining their objectives, methods, descriptions, and the limitations associated with each approach.

Table 7.
Summary of multi-cloud cost optimization algorithms and their limitations.
In recent years, the challenge of jointly optimizing cost and availability in multi-cloud environments has driven a significant evolution in scheduling and data placement methodologies. Initial research focused on centralized formulations, such as ILP-based models for workflow mapping [157,160] and service placement [165], offering optimal cost solutions under deadline and resource constraints. However, the rigidity and computational overhead of these approaches limited their applicability in dynamic, real-world clouds. This led to the adoption of lightweight heuristics, such as the dynamic storage selector in CHARM [161] and greedy schedulers balancing cost-availability trade-offs [164], which improved scalability and responsiveness. Yet, these models often failed to manage trade-offs effectively when faced with multiple conflicting objectives. To address this, researchers introduced multi-objective metaheuristics, including ACO [159], and NSGA-II [156], which generate Pareto-optimal fronts for cost and availability, often enhanced by entropy-based or adaptive selection mechanisms. Simultaneously, genetic algorithms proved effective in resource provisioning and component placement [165,168], particularly for long-running and latency-sensitive applications. As models matured, emphasis expanded to security and redundancy, with LP-based threshold models [166] and network coding techniques such as MSR and MBR [158] offering cost-resilient solutions under failure or spot instance volatility. Moreover, to scale with Internet-scale demands, research transitioned toward decentralized and predictive scheduling, where agent-based approaches [156,167] and trend-based reallocation models [164] adapted dynamically to cloud pricing and workload patterns. Collectively, these existing works depict a maturing field that has shifted from static, cost-centric optimization to adaptive, secure, and availability-aware orchestration frameworks, better aligned with the heterogeneity and volatility of real-world multi-cloud environments.
Despite their progress, recurring limitations persist. Most models assume static task execution times and provider prices, limited support for real-time reallocation or correlated failures, and overreliance on simulation-based validation. Future research must thus address these gaps through robust, real-world adaptive frameworks that can integrate predictive analytics, dynamic pricing, and reliability-aware deployment into unified, end-to-end multi-cloud orchestration solutions.
5. Security Challenges in Multi-Cloud
Organizations using multi-cloud setups often face unique security risks due to the fragmented nature of cloud platforms [4,56]. Each provider comes with its own tools, policies, and architectures, which makes it harder to maintain consistent security rules across the entire environment [56,169]. Without unified governance, sensitive data may be classified differently or left unprotected during transfers [169]. Key management becomes risky when encryption keys are handled differently across providers, as a single forgotten key can lead to full compromise [170]. Visibility is another concern, since monitoring is not centralized, threats in one cloud may remain undetected [143,171]. Also, IAM complexity increases, with orphaned accounts and inconsistent roles becoming a serious threat [4,56]. Shared responsibility is often misunderstood, leading to gaps where no one enforces cross-cloud API protection [96]. Compliance becomes a nightmare as audit logs get scattered and laws vary between data centers [169,170]. This inconsistency can allow attackers to pivot laterally between clouds using exposed APIs or weak access paths [96,171]. All these factors prove that security consistency and unified control are essential in multi-cloud environments [143]. Table 8 summarizes major cloud security challenges, detailing their causes and practical effects, and demonstrates how misconfigurations, fragmented controls, and limited visibility can compromise cloud security and resilience.

Table 8.
Common Security Challenges in Multi-Cloud Environments.
In conclusion, the identified challenges reveal that policies failing to address the challenges of fragmentation, inconsistency of IAM, and complexity of key management are not only isolated obstacles but also interconnected challenges that increase exposure to risk across providers. While most studies emphasize the issues of misconfiguration and visibility gaps, fewer studies address the compounded issues of cross-cloud compliance and governance misalignment. This synthesis suggests that to achieve consistent security across multi-cloud ecosystems, there must be a convergence of both technical and organizational controls, particularly unified policy frameworks and comprehensive observability solutions that reach across provider boundaries.
6. Solutions and Frameworks for Securing Multi-Cloud
Navigating security challenges across multiple cloud platforms is inherently difficult; considerable progress has been made in developing robust mitigation strategies. Cryptographic techniques such as secret sharing and homomorphic encryption are often used to protect sensitive data, even when it’s stored or shared across multiple providers [96,170]. These methods ensure that the data stays secure even if part of the system is compromised. Another technique is Machine learning, which is helping security systems become more responsive. It can detect unusual patterns or risky behaviours by analyzing large volumes of cloud activity [56,171]. In some systems, AI is also used to make access decisions or alert teams without human input, which saves time and reduces errors [171]. In cases where the data is unclear or incomplete, fuzzy logic is useful. It provides systems with a way to reason through uncertainty, a common occurrence when different clouds handle information in other ways [171]. Another key tool is Identity and Access Management (IAM). When IAM is centralized, it helps apply the same access policies across clouds, which lowers the chance of mistakes or forgotten user accounts [4,56]. Some research also recommends using tools such as policy-as-code, automated infrastructure setups, and orchestration frameworks to maintain security controls uniform across all platforms [143,170]. These combined solutions provide organizations with better awareness and control, making their overall system more secure. Although no approach is perfect on its own, combining these methods creates a more flexible, stronger, and forward-thinking security strategy for modern cloud environments [96,143,170].
6.1. Cryptographic Techniques for Multi-Cloud Security
Cryptographic techniques are methods used to secure data and communication by transforming plain information into an unreadable form known as ciphertext. These encrypted forms can only be decrypted by authorized parties [69,172]. These techniques are indispensable for upholding the core principles of information security: confidentiality, integrity, and authenticity [172,173]. In multi-cloud environments where data flows across different providers and is stored in varied, often externally managed locations, cryptography becomes important. It safeguards information as it moves or resides across platforms, ensuring protection against unauthorized access, tampering and data leaks [1,69,174]. For example, encrypting data before it exits an organization ensures that cloud providers only handle encrypted forms, reducing the chances of internal abuse or breaches [1]. Overall, modern multi-cloud security heavily relies on cryptography to ensure secure access, data confidentiality, and cross-cloud compliance, allowing organizations to use cloud flexibility without exposing sensitive assets [1,172,174]. Table 9 summarizes cryptographic techniques used in multi-cloud environments, explaining their working principles and highlighting their primary security and performance advantages.

Table 9.
Cryptographic Techniques in Multi-Cloud Environments.
After analyzing various cryptographic approaches, it seems that hybrid encryption, along with secret sharing models, achieves an optimal balance between computational efficiency and confidentiality across distribution. On the contrary, homomorphic and attribute-based encryption approaches offer an improved level of privacy, albeit at a significantly higher computational expense. Blockchain-assisted encryption provides new opportunities for integrating auditability; however, challenges persist regarding scalability. Overall, most recent research in cryptography focused on multi-clouds is transitioning from static encryption to adaptive encryption, utilizing policy-based approaches that embed key management systems and trust enforcement in orchestration layers.
6.2. AI Techniques for Multi-Cloud Security
Artificial Intelligence (AI) techniques have become a cornerstone in strengthening multi-cloud security due to their ability to detect and respond to complex cyber threats in real time. Traditional rule-based systems fail to handle dynamic, large-scale environments, but AI bridges this gap by offering adaptive, intelligent defence mechanisms [176]. Machine learning models such as Random Forest and Gradient Boosting can classify threats effectively. In contrast, deep learning architectures such as LSTM can detect abnormal behaviours by analyzing time-series patterns across diverse cloud infrastructures [177]. Moreover, the integration of reinforcement learning allows cloud systems to update security policies autonomously based on evolving risks, reducing both false positives and mitigation time [177]. Federated learning is another powerful approach that supports privacy-preserving detection without transferring raw logs across cloud platforms, which is vital for regulatory compliance in sensitive sectors such as finance and healthcare [178,179]. To further enhance detection precision, techniques such as Graph Neural Networks help identify multi-step attacks by modelling cloud interactions as structured graphs [178]. In addition, self-supervised learning proves useful when labelled datasets are scarce, allowing AI models to learn directly from unstructured logs [178]. Importantly, zero-trust AI frameworks powered by behaviour analytics and reinforcement learning now enable dynamic access control and micro-segmentation, effectively containing lateral movement and insider threats [178,180]. All these methods work in synergy to provide scalable, cloud-agnostic, and proactive security strategies. Without AI, maintaining uniform protection across heterogeneous cloud platforms such as AWS, Azure, and GCP would remain a fragmented and reactive process [179]. Hence, AI not only empowers real-time threat detection but also ensures that multi-cloud environments remain resilient, intelligent, and future-ready [176,177]. Table 10 presents various AI techniques applied in multi-cloud security, highlighting their purposes and primary advantages in enhancing threat detection, anomaly detection, policy adaptation, and incident response.

Table 10.
AI Techniques In Multi-Cloud Security.
AI-based techniques analyses indicate that deep and reinforcement learning models are proficient at identifying and automating responses to dynamic threats. However, their reliance on considerable, high-quality datasets constrains their generalization across heterogeneous clouds. Although federated and graph-based learning approaches address some problems related to data sharing and contextualization, challenges such as explainability and real-time adaptability remain unsolved. The latest advancements in hybrid AI frameworks that integrate predictive analytics with zero-trust micro-segmentation to achieve intelligent, continuous protection across distributed cloud environments.
6.3. ML Techniques for Multi-Cloud Security
Machine learning in multi-cloud security typically involves using algorithms which learn patterns from the vast data across multiple cloud platforms to automatically detect and respond to security issues [181,182]. This strategy is highly significant because traditional rule-based and manual security solutions struggle to deal with the size and complexity of multi-cloud settings [181,183,184]. Conventional tools often fail against new cyberattacks in these distributed cloud setups, which is making AI-driven anomaly detection and analysis increasingly important [121,181]. By applying machine learning, organizations can analyze large volumes of cloud logs and user behaviours to spot unusual patterns or threats in real-time and then predict potential system failures or breaches before they can happen [121,181,185]. They are also able to modify resource allocations or security restrictions [181,182] quickly. This means security teams get proactive warning of suspicious activities and automated assistance in neutralizing risks [121,181]. In summary, machine learning adds an intelligent, adaptive layer of defence that enhances the reliability and safety of multi-cloud [121,181,182,184]. Table 11 outlines key machine learning techniques in multi-cloud security, explaining their applications and highlighting their primary advantages in threat detection, classification, adaptability, and privacy preservation.

Table 11.
Machine Learning Techniques in Multi-Cloud Security.
The analysis indicates that machine learning techniques have undeniably strong capabilities for detecting anomalies and intrusions. However, they still contend with issues such as a lack of available labels, data imbalance, and dynamically changing attack patterns. In terms of precision, deep architectures such as CNN and LSTM outperform classical approaches, whereas federated models preserve data privacy across providers. Future research should focus on analyzing adaptive self-learning ML pipelines that autonomously retrain when an environment drifts while ensuring confidentiality and minimal latency.
6.4. Fuzzy-Logic Techniques for Multi-Cloud Security
Fuzzy logic has emerged as a powerful tool in multi-cloud security due to its ability to handle uncertainty, ambiguity and imprecision in decision-making. Since cloud environments involve constant changes in trust, risk and resource demands, fuzzy systems help in making smarter decisions. For example, it enables accurate fault detection and automatic task migration using performance metrics such as throughput and response time [186]. It also improves energy efficiency and secure job scheduling by weighing multiple factors such as job size, memory and required security levels [187]. In terms of trust, fuzzy logic combines subjective feedback and objective SLA data to assess service provider reliability more effectively [188]. Moreover, risk analysis becomes more realistic when threats, vulnerabilities, and asset values are treated as fuzzy variables instead of fixed numbers [189]. Recent works show that fuzzy logic adapts well to load balancing, QoS control, and security prediction across various cloud services [190,191]. In provisioning, fuzzy rules optimize resource scaling and reduce SLA violations by reacting to real-time workload fluctuations [192]. It is also powerful in detecting over-privileged access by evaluating user behaviour and permission strength fuzzily [193], and in building adaptive intrusion detection systems with lower false alarm rates [194]. Finally, fuzzy models help quantify layered security risks in MFA and container orchestration, which is crucial for modern multi-cloud setups [195]. All these show that fuzzy logic not only simplifies decision-making but also adds a layer of intelligent control to complex, distributed cloud systems. Table 12 summarizes various fuzzy logic techniques applied in multi-cloud security, highlighting their explanations and primary advantages in enhancing fault tolerance, trust, risk management, scheduling, and intrusion detection.

Table 12.
Fuzzy Logic Techniques In Multi-Cloud Security.
The analysis of fuzzy-logic frameworks demonstrates distinctive proficiency in managing uncertainty, evaluating trust, and performing multi-criteria decision-making in the context of variable workloads. Fuzzy systems offer interpretability and robustness in diverse contexts, extended beyond just having rule-based models. This becomes particularly effective when combined with artificial intelligence or machine learning for hybrid reasoning. Nevertheless, the extent of their accuracy and scalability remains limited to the manual tuning of rule sets. The integration of fuzzy inference, reinforcement learning, and policy-as-code frameworks could provide multi-cloud environments with adaptive security controllers tailored to their complexity.
6.5. IAM Approach for Multi-Cloud Security
Identity and Access Management (IAM) is one of the foundational pillars of multi-cloud security, ensuring that only authorized users and services can access sensitive data and resources, regardless of the cloud platform in use. As identity becomes the new perimeter, IAM approaches such as Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Multi-Factor Authentication (MFA) provide flexible yet strict access controls tailored to different user roles and conditions [196]. Moreover, techniques such as federated identity using OAuth, OpenID Connect, and SAML allow users to move securely across platforms without credential duplication [197,198]. This is particularly important for avoiding identity silos and ensuring seamless user experience in distributed architectures [199]. In recent years, the shift toward Zero Trust Architecture has redefined IAM by enforcing continuous verification and behaviour-based access decisions, making trust a dynamic, context-aware variable rather than a static rule [200,201]. To strengthen this, AI-driven systems have been integrated into IAM models to detect anomalies, automate policy enforcement, and dynamically assess identity risks [196,201]. In addition, microservice environments benefit from fine-grained access policies enforced through tools such as Open Policy Agent (OPA), allowing real-time, decentralized control [198]. Altogether, IAM not only safeguards against external threats such as credential theft or API abuse, but also reduces insider risks by applying least-privilege principles and monitoring user behaviour across cloud ecosystems [79,200]. Thus, in a world where cloud boundaries blur and attack surfaces grow, IAM serves as both the gatekeeper and the auditor of trust. Table 13 presents different IAM techniques with their details and key benefits, showing how they enhance security, access management, and compliance in multi-cloud environments.

Table 13.
IAM Techniques, Explanation, Primary Advantage.
The analysis shows that IAM solutions continue to be fragmented, and also remain lacking in automated role synchronization and consolidated credential lifecycle management across providers. Centralized identity federations may improve visibility but also introduce single points of failure in policy. Architectures of emerging zero-trust IAM systems, along with decentralized identity protocols based on blockchain, show potential for establishing trust boundaries across multiple clouds. The combination of these with compliance-orchestrated governance layers represents a practical pathway for unified governance.
6.6. Emerging Technologies
Multi-cloud security is becoming increasingly secure with new technologies that solve real and growing problems. To begin with, Zero Trust Architecture plays a crucial role by ensuring that no user or device is automatically trusted. Instead, every access request is strictly verified using multi-factor authentication and continuous monitoring [202,203,204]. Additionally, Federated Learning helps train AI models across different cloud nodes without moving sensitive data, which protects privacy and reduces the risk of central data breaches [204,205]. Blockchain also contributes by securing cloud transactions through tamper-proof records and distributed consensus, allowing better transparency in multi-cloud operations [204]. In the case of intrusion detection, Swarm Technologies such as OBL-RIO improve the selection of network features using bio-inspired optimization, which leads to better accuracy and fewer false alerts [133,206,207,208]. In the meantime, the shift towards 6G technologies provides ultra-fast and intelligent support for distributed trust models, helping cloud and edge nodes coordinate securely in real-time [205]. In addition, to enhance decision-making transparency in cloud-based security systems, Explainable AI methods are being adopted, enabling analysts to understand threat classifications and reduce false positives [209]. In multi-cloud environments, Natural Language Processing (NLP) is also increasingly leveraged to enable secure, privacy-aware training of language models for analyzing textual threat intelligence and detecting social engineering attacks [210]. Table 14 highlights emerging technologies that enhance multi-cloud security, describing their mechanisms and emphasizing key benefits such as stronger identity control, improved privacy, secure logging, better intrusion detection, and advanced threat response.

Table 14.
Emerging Technologies Enhancing Multi-Cloud Security.
The analyses indicate that progress in blockchain technology, alongside quantum-resistant cryptography and AI-driven orchestration, reflects a transformative movement toward autonomous and trustless verifiable environments of the multi-cloud. The synthesis suggests a greater utilization of interoperable testbeds for validating these innovations with real-world workloads. Future steps in progress may focus on balancing technological advancements with governance, prioritizing that resilience, cost efficiency, and regulatory compliance evolve together with next-generation distributed cloud architectures.
6.7. Enterprise-Grade Solutions
While academic proposals have introduced a wide range of cryptographic, AI, fuzzy-logic, and IAM-based defences, real-world deployment increasingly depends on enterprise-grade solutions. Modern enterprise environments are increasingly dependent on integrated security management platforms that extend beyond traditional academic or experimental models. These consist of Cloud-Native Application Protection Platforms (CNAPP), Cloud Workload Protection Platforms (CWPP), and Cloud Security Posture Management (CSPM). These solutions serve as frameworks that integrate compliance supervision, workload defence, and protection at runtime over dispersed cloud infrastructures. CSPM helps automate the enforcement of compliance and detects configuration drift while also aligning with the research efforts on governance-aware cloud orchestration [211,212]. By integrating vulnerability management with behavioural monitoring, CWPP ensures host- and container-level security, paralleling academic proposals for context-aware anomaly detection(Non-peer-reviewed source [213]). CNAPP provides unified visibility and adaptive response pipelines, which extend these capabilities and effectively implement multi-layered defence architectures(Non-peer-reviewed source [212,214]).
From this analysis, it indicates that academic approaches mainly focus on conceptual innovations such as federated intelligence sharing, adaptive cryptography, and explainable AI, while enterprise tools concentrate on operational scalability and automation. The combination of both perspectives reveals a convergence whereby theoretical frameworks guide the advancement of business systems, while the real-world applications feed back on and polish the theoretical constructs. This integration demonstrates the increasing convergence of research with the practical aspects of securing contemporary multi-cloud environments.
Table 15 presents a summary of these enterprise solutions concerning their primary functions, advantages, and significance in relation to a multi-cloud environment.

Table 15.
Enterprise Security Solutions in Multi-Cloud Environments.
7. Research Gap
While multi-cloud security has evolved considerably, critical gaps remain. These areas that are frequently ignored weaken the robustness and effectiveness of current methods. Addressing these issues is essential for guiding future research efforts aimed at strengthening the security of multi-cloud environments.
7.1. Heavy Reliance on Simulation Without Real-World Cloud Validation
A critical shortcoming in the current state of research is the reliance on simulation environments such as CloudSim and iFogSim for the validation of multi-cloud architectures. This reliance on simulation environments deeply undermines the real-world relevance of the proposed models. Such simulators abstract away crucial infrastructure behaviours. For example, these include virtual machine boot delays, API rate limiting, network jitter, the likelihood of an availability zone outage, and the expenses for specific regions. Additionally, they are unable to accommodate service-specific details, which leads to an unrealistic representation of system behaviour. Consequently, insights gained from simulation environments often are incapable of leading to production systems that are deployable, resilient, or efficient. This gap can be addressed by shifting the research focus toward reproducible benchmarking environments using Infrastructure-as-Code (IaC) tools, such as Terraform or Pulumi, to provision actual resources across providers. Multi-cloud service meshes such as Istio and Consul provide routing, observability, and failover, while service orchestration can be managed through Kubernetes Federation (KubeFed). Continuous performance measurement, SLA tracking, and auditing of associated costs will be enabled by Integration with monitoring stacks such as Prometheus and Grafana. Importantly, experiments must include live billing analysis, compliance verification, and API compatibility validation. This transition from hypothetical concepts to practical operations is crucial for achieving resilient, scalable, and production-grade multi-cloud research.
7.2. Fragmented Security Controls and Absence of Federated Trust Models
In multi-cloud deployments, the failure to establish a cohesive, cross-platform, and flexible security architecture remains one of the most difficult obstacles to secure operational security. Most existing models were built under the assumption of a homogeneous trust model. Such environments do not exist in real-world federated environments involving third-party services, hybrid clouds, and decentralized edge nodes. Access control definitions remain static as they rely on older RBAC models or ABAC models, which are too simplistic to capture real-time context such as user location and behavioural deviations. Additionally, the absence of established trust negotiation protocols results in the continued fragmentation and insecurity of identity federation and cross-provider data sharing. To address these limitations, future research should shift towards implementing decentralized trust architectures based on blockchain-based identities and distributed reputation systems to validate and score identities. Smart contracts can enforce data governance and auditability policies, guaranteeing both regulatory compliance and interoperability simultaneously. Coupling this with zero-trust identity fabrics will ensure adaptive, policy-consistent access in even the most dynamic environments. Moreover, adopting context-aware ABAC engines backed by policy-as-code frameworks, such as OPA, would enable dynamic enforcement of security policies based on time, geography, access frequency, and other risk dimensions. Most importantly, these mechanisms also need to be enhanced with compliance-aware filters to ensure that decisions on data placement, access, and replication decisions align with cross-border privacy laws and are synchronized with jurisdictional requirements. The outcome is a unified, resilient, and legally compliant security layer for multi-cloud environments.
7.3. Lack of Real-Time, Cross-Cloud Threat Intelligence and Response
The new attack surface that expands as a result of modern multi-cloud architectures is characterized by distributed control planes and heterogeneous security capabilities of various cloud providers. Despite these persistent challenges, the majority of existing threat-detection systems remain siloed, depending on offline-trained, provider-specific, non-collaborative, and machine learning models, as well as rule-based algorithms. Such systems do not possess the architectural ability to combine asynchronous and distributed within-space threat indicators, such as unusual login attempts in one cloud and concurrent lateral movement in another. Furthermore, existing approaches overlook the continuous nature of attack evolution, leaving them unable to defend against polymorphic and zero-day attacks that adapt faster than signature updates. However, a consolidated behavioural intelligence layer that can aggregate, normalize, and analyze activity patterns across clouds does not exist. This leads to an environment where subtle behavioural deviations, such as anomalous API call patterns or unauthorized lateral movements, go undetected because each cloud sees only a partial picture. This matters especially for detecting stealthy threats, insider attacks, or fraud that span federated services. The consequence is reduced visibility, delayed detection, and a fragmented response posture. To respond appropriately, an improved federated threat detection framework must be architected, which includes real-time ingestions of telemetry from various clouds, cross-border intelligence sharing through standard protocols and online model updating through federated learning techniques. In addition to employing graph neural networks (GNNs) to represent and reason about the interrelated behaviours of the user and entity, these approaches can provide context-aware, precise anomaly detection. When combined with a zero-trust access architecture, such systems would dynamically enforce fine-grained security decisions at runtime, transforming cloud security from static, perimeter-based defence to adaptive, scalable risk mitigation.
7.4. Cost Optimization Strategies Ignore Dynamic Constraints and SLA Penalties
Despite the existence of numerous models to reduce the cost of infrastructure in multi-cloud architectures, they remain fundamentally inadequate in modelling the full complexity of operational environments. Due to the heterogeneous billing structures, dynamic pricing, and hidden operational costs imposed by different cloud providers, the cost modelling of multi-cloud environments remains fragmented and disjointed. Many orchestration strategies optimize for either performance, such as minimizing latency or cost, such as query minimization, but these strategies rarely consider a combination of many real-world constraints. Existing approaches often optimize for static cost parameters such as hourly VM rates or compute unit pricing, while ignoring a multitude of dynamic and context-sensitive variables, including spot price volatility, IOPS-based storage pricing, and SLA penalties for underperformance. Moreover, the optimization logic within several frameworks is not designed to handle non-linear trade-offs between conflicting objectives, such as minimizing cost while ensuring high availability and low latency. Most approaches also overlook workload heterogeneity and do not model user-specific preferences or data compliance constraints. To overcome this, frameworks focused on cost optimization need to transform into multi-objective, SLA-aware optimization engines that can dynamically allocate resources through deep reinforcement learning, multi-objective evolutionary algorithms, or even Bayesian optimization. Such models would need to have the capability to process real-time pricing data and predict SLA breaches and penalties, and QoS preferences. In addition, integrating carbon-intensity APIs and data locality-aware schedulers will enable workload placement based on monetary expense, energy consumption and compliance risk. This shift facilitates resource orchestration that is SLA-compliant, cost-efficient, and sustainable across dynamic multi-cloud environments.
7.5. Lack of Explainability and NLP-Driven Automation in Multi-Cloud Threat Detection and Intelligence Integration
In the evolving landscape of multi-cloud security, two critical research gaps have been identified that compromise the efficiency, transparency, and flexibility of the systems for intelligent threat detection. The initial gap concerns the absence of Explainable Artificial Intelligence (XAI) in deep learning-based threat detection models, especially those using Convolutional Neural Networks (CNNs) and Long Short-Term Memory (LSTM) networks. While these models are successful at anomaly detection and attack classification, they tend to operate as non-transparent systems, providing minimal explanation of their decision-making processes. The absence of transparency creates significant challenges in mission-critical environments where security analysts must justify and audit automated security actions such as access denial, account isolation, or resource suspension. Moreover, a lack of explanation of model outputs impairs the retraining and validation of processes as the threat landscape evolves. Although SHAP, LIME, and attention-weighted visualization techniques offer potential solutions, their integration in the operational pipelines remains insufficient. The second gap concerns the underutilization of Natural Language Processing (NLP) in real-time threat intelligence integration within Security Information and Event Management (SIEM) and Security Operations Center (SOC) platforms. Even with the increasing volume of unstructured threat data, such as advisories, vulnerability reports, and analyst-authored alerts, manual triage remains the standard, resulting in lagging responses and heightened analyst burnout. NLP-based real-time enrichment using domain-specific large language models (LLMs) and intelligent co-pilots can significantly enhance contextual analytical understanding and decision-making capabilities by transforming unstructured feeds into actionable insights. Bridging these two gaps through the integration of interpretable AI and NLP-enhanced automation is essential for establishing transparent, efficient, and adaptable multi-cloud security infrastructures.
7.6. Lack of Robust Data Provenance and Lineage Across Multi-Cloud Environments
In the analyzed literature on data security and trust, a major shortcoming is the absence of dependable data lineage tracing throughout multiple providers. As organizations spread their processing and storage across numerous cloud services, data undergoes transformation, duplication, and movement, often lacking an identifiable, secure log of its origins, subsequent usage, and any alterations that were made. This creates severe compliance, integrity, and forensic risks, particularly when sensitive datasets such as financial records and health data are involved, as well as when service boundaries are crossed. Existing logging mechanisms, such as those offered by CSPs such as AWS CloudTrail, are limited in integration and have restrictive scopes. An effective data provenance framework should integrate timestamped hashes, cryptographic commitments, and immutable logs to achieve comprehensive traceability. Leveraging blockchain or distributed ledger technology (DLT) can ensure that data flow events are both transparent and tamper-proof. Research should focus on ensuring that provenance protocols are cloud-native, scalable, object-store, stream-processor, and container-runtime-friendly, all while achieving low-latency and high-throughput performance. Provenance should additionally be semantically enriched by connecting access logs to business policies, user actions, and system status. This would result in raw data trails being transformed into auditable records, which would be compliant with regulations.
8. Conclusions
In this paper, we present a comprehensive literature review that integrates different areas of research on multi-cloud environments, security threats, defence mechanisms, cost, SLA-aware orchestration, provenance, and privacy, which have been studied individually. Moreover, multi-clouds increase both operational trade-offs and technical complexity. As illustrated in the literature review, some defences which improve confidentiality or integrity exacerbate both latency and cost. Cost-cutting measures increase the attack surface. Additionally, provider diversity makes consistent policy enforcement and forensic analysis more difficult. Identifying these inter-dependencies is critical for formulating effective, actionable solutions for real-world multi-cloud deployments. Our survey also highlights several distinct trends and potential techniques, such as federated and privacy-preserving learning techniques used for cross-cloud anomaly detection, application of graph neural networks for service behavioural correlation across services, use of zero-trust architectures, service meshes for mitigating lateral movements, and stronger data provenance through cryptographic approaches. However, in all these areas, we found that much of the work remains in the experimental phase, often confined to simulations, and few studies evaluate solutions under realistic, adversarial conditions or at production scale. We also emphasize critical gaps that require the most focus. Cross-provider policy synchronization and unified IAM semantics are still unresolved issues. There is also a lack of comprehensive, federated SIEM and threat-intelligence sharing systems. XAI is underexplored, as is the case with the explainability of AI-driven detectors. There is insufficient development on end-to-end, multi-cloud cryptographic and verifiable provenances. Finally, there is a lack of combined optimization of cost, compliance, availability, and sustainability demands for SLA-aware and regulation-informed orchestration strategies.
Based on the review, we recommend that the research community focus on the following:
- Federated, privacy-preserving detection layers with threat sharing standardization
- XAI validation for ML models applied to security issues
- Cross-cloud provenance systems combining cryptographic commitments with immutable logging
- Multi-objective cost, compliance, availability and environmental impact optimization in orchestration.
Importantly, these efforts should be validated on publicly available benchmarks and real-world testbeds, using adversarial evaluations and longitudinal studies to measure operational robustness and operational costs. Another significant contribution of this study lies in its multi-directional scope. In contrast to prior research, which typically focuses on a single dimension, such as security threats, defence mechanisms, or cost optimization, this work deliberately integrates multiple perspectives. This approach enables researchers to investigate interrelated trade-offs and comprehend implications on a broader system level. In conclusion, securing the distributed skies of multi-cloud environments will require integrated technical, operational, and policy solutions. Through the integration of existing insights, highlighting recurring challenges, and proposing a well-defined research direction, this study aims to support the development of transparent, resilient, and practically applicable multi-cloud security frameworks that are appropriate for real-world adoption.
Author Contributions
Conceptualization: L.H.B., T.S.K. and F.A.; Methodology: L.H.B., T.S.K. and F.A.; Software, L.H.B. and T.S.K.; validation: T.S.K. and F.A.; Formal analysis: L.H.B., T.S.K. and F.A.; Investigation: T.S.K. and F.A.; Resources: L.H.B. and T.S.K.; Data curation: L.H.B. and T.S.K.; Writing—original draft preparation: L.H.B. and T.S.K.; Writing—review and editing: F.A., M.S.I. and M.T.I.; visualization: T.S.K., F.A., M.S.I. and M.T.I.; Supervision: T.S.K. and F.A.; Project administration: T.S.K., F.A. and M.S.I.; Funding acquisition: M.S.I. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Universiti Telekom Sdn. Bhd., Research Management, Multimedia University, Persiaran Multimedia, 63100 Cyberjaya, Selangor, Malaysia.
Data Availability Statement
Acknowledgments
The authors acknowledge the American International University Bangladesh (AIUB) and Universiti Telekom Sdn. Bhd., Multimedia University, 63100, Cyberjaya, Malaysia, for their support in this study, including facilities and encouragement.
Conflicts of Interest
The authors declare no conflicts of interest. The funder had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
| Abbreviation | Full Form |
| RBFNN | Radial Basis Function Neural Network |
| CNN | Convolutional Neural Network |
| LSTM | Long Short-Term Memory |
| CNN-LSTM | Convolutional Neural Network Long Short-Term Memory |
| DNN | Deep Neural Networks |
| MLP-BP | Multi-Layer Perceptron Backpropagation |
| MLP-PSO | Multi-Layer Perceptron Particle Swarm Optimization |
| MFE-ELM | Multi-Feature Extraction Extreme Learning Machine |
| I-GN | Integer-Grading Normalization |
| OBL-RIO | Opposition-Based Learning Rat Inspired Optimizer |
| 2D-ACNN | 2D-Array Convolutional Neural Network |
| IoT | Internet of Things |
| CAPEX | Capital Expenditure |
| OPEX | Operational Expenditure |
| SIEM | Security Information and Event Management |
References
- Viswanath, G.; Krishna, P.V. Hybrid encryption framework for securing big data storage in multi-cloud environment. Evol. Intell. 2021, 14, 691–698. [Google Scholar] [CrossRef]
- Canalys. Cloud Market Share Q4 2018 and Full Year 2018. 2018. Available online: https://www.canalys.com/newsroom/cloud-market-share-q4-2018-and-full-year-2018 (accessed on 11 January 2019).
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11. [Google Scholar] [CrossRef]
- AlZain, M.A.; Pardede, E.; Soh, B.; Thom, J.A. Cloud Computing Security: From Single to Multi-Clouds. In Proceedings of the 45th Hawaii International Conference on System Sciences (HICSS), Maui, HI, USA, 4–7 January 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 5490–5499. [Google Scholar] [CrossRef]
- Ahmed, W. Trends and Challenges in Securing Cloud Computing Environments: An Overview of Current Techniques. Prem. J. Comput. Sci. 2024, 1, 100004. [Google Scholar] [CrossRef]
- Creasy, R.J. The Origin of the VM/370 Time-Sharing System. IBM J. Res. Dev. 1981, 25, 483–490. [Google Scholar] [CrossRef]
- Dee, R. Magnetic Tape for Data Storage: An Enduring Technology. Proc. IEEE 2008, 96, 1775–1785. [Google Scholar] [CrossRef]
- Berners-Lee, T.; Cailliau, R.; Groff, J.F.; Pollermann, B. World-Wide Web: The Information Universe. Internet Res. 2010, 20, 461–471. [Google Scholar] [CrossRef]
- Hertzfeld, A. Bill and Andy’s Excellent Adventure II. Wired Magazine. 1994. Available online: https://www.wired.com/1994/04/general-magic/ (accessed on 28 June 2025).
- Khajeh-Hosseini, A.; Sommerville, I.; Sriram, I. Research Challenges for Enterprise Cloud Computing. arXiv 2010, arXiv:1001.3257. [Google Scholar] [CrossRef]
- Choudhary, V. Software as a Service: Implications for Investment in Software Development. In Proceedings of the 40th Annual Hawaii International Conference on System Sciences (HICSS), Waikoloa, HI, USA, 3–6 January 2007; p. 209. [Google Scholar] [CrossRef]
- Khajeh-Hosseini, A.; Sommerville, I.; Sriram, I. Research Agenda in Cloud Technologies. arXiv 2010, arXiv:1001.3259. [Google Scholar] [CrossRef]
- Bugnion, E.; Devine, S.; Rosenblum, M.; Sugerman, J.; Wang, E.Y. Bringing Virtualization to the x86 Architecture with the Original VMware Workstation. ACM Trans. Comput. Syst. 2012, 30, 12:1–12:51. [Google Scholar] [CrossRef]
- Matana, T. Origin & History of ASP, SaaS, PaaS and Cloud Computing. Int. J. Sci. Res. Manag. 2024, 12, 1571–1607. [Google Scholar] [CrossRef]
- Randal, A. The Ideal Versus the Real: Revisiting the History of Virtual Machines and Containers. arXiv 2019, arXiv:1904.12226. [Google Scholar] [CrossRef]
- Buyya, R.; Calheiros, R.N.; Li, X. Autonomic Cloud Computing: Open Challenges and Architectural Elements. arXiv 2012, arXiv:1209.3356. [Google Scholar] [CrossRef]
- Yang, L.; Jaffe, S.; Holtz, D.; Suri, S.; Sinha, S.; Weston, J.; Joyce, C.; Shah, N.; Sherman, K.; Lee, C.J.; et al. How Work From Home Affects Collaboration: A Large-Scale Study of Information Workers in a Natural Experiment During COVID-19. arXiv 2020, arXiv:2007.15584. [Google Scholar] [CrossRef]
- López Flores, N.G.; Islind, A.S.; Óskarsdóttir, M. Effects of the COVID-19 Pandemic on Learning and Teaching: A Case Study from Higher Education. arXiv 2021, arXiv:2105.01432. [Google Scholar] [CrossRef]
- Cao, Y.; Li, S.; Liu, Y.; Yan, Z.; Dai, Y.; Yu, P.S.; Sun, L. A Comprehensive Survey of AI-Generated Content (AIGC): A History of Generative AI from GAN to ChatGPT. arXiv 2023, arXiv:2303.04226. [Google Scholar] [CrossRef]
- Mohamadi, S.; Mujtaba, G.; Le, N.; Doretto, G.; Adjeroh, D.A. ChatGPT in the Age of Generative AI and Large Language Models: A Concise Survey. arXiv 2023, arXiv:2307.04251. [Google Scholar] [CrossRef]
- Pérez-Martínez, J.; Díaz, J.; Berrocal, J.; López-Viana, R.; González-Prieto, A. Edge computing. Computing 2022, 104, 2711–2747. [Google Scholar] [CrossRef]
- Hasan, B.T.; Idrees, A.K. Edge Computing for IoT. arXiv 2024, arXiv:2402.13056. [Google Scholar] [CrossRef]
- Tuli, S.; Mirhakimi, F.; Pallewatta, S.; Casale, G.; Javadi, B.; Yan, F.; Buyya, R.; Jennings, N.R. AI-Augmented Edge and Fog Computing: Trends and Challenges. arXiv 2022, arXiv:2208.00761. [Google Scholar] [CrossRef]
- Alonso, J.; Orue-Echevarria, L.; Casola, V.; Torre, A.I.; Huarte, M.; Osaba, E.; Lobo, J.L. Understanding the challenges and novel architectural models of multi-cloud native applications—A systematic literature review. J. Cloud Comput. 2023, 12, 6. [Google Scholar] [CrossRef]
- Atieh, A.T. The next generation cloud technologies: A review on distributed cloud, fog and edge computing and their opportunities and challenges. Res. Berg Rev. Sci. Technol. 2021, 1, 1–15. [Google Scholar]
- Somani, U.; Kanika, L.; Manish, M. Implementing digital signature with RSA encryption algorithm to enhance the data security of cloud in cloud computing. In Proceedings of the First International Conference on Parallel, Distributed and Grid Computing (PDGC ’10), Solan, India, 28–30 October 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 211–216. [Google Scholar] [CrossRef]
- Pachala, S.; Rupa, C.; Sumalatha, L. An improved security and privacy management system for data in multi-cloud environments using a hybrid approach. Evol. Intell. 2021, 14, 1117–1133. [Google Scholar] [CrossRef]
- Nandhini, M.; Madhavi, S. Provisioning of data security for file transformation on multi-cloud storage. Bonfring Int. J. Softw. Eng. Soft Comput. 2019, 9, 15–16. [Google Scholar]
- Miyachi, C. What is “Cloud”? It is time to update the NIST definition? IEEE Cloud Comput. 2018, 5, 6–11. [Google Scholar] [CrossRef]
- Talbi, J.; Haqiq, A. A cloud broker architecture for cloud service selection based on multi-criteria decision making and rough set theory. Int. J. Comput. Aided Eng. Technol. 2020, 13, 448–464. [Google Scholar] [CrossRef]
- Software Development Company USA. Simform. 2020. Available online: http://www.simform.com/ (accessed on 28 June 2025).
- Fu, Z.; Sun, X.; Liu, Q.; Zhou, L.; Shu, J. Achieving Efficient Cloud Search Services: Multi-Keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing. IEICE Trans. Commun. 2015, 98, 190–200. [Google Scholar] [CrossRef]
- Junghanns, P.; Fabian, B.; Ermakova, T. Engineering of secure multi-cloud storage. Comput. Ind. 2016, 83, 108–120. [Google Scholar] [CrossRef]
- Agrawal, D.; Das, S.; Abbadi, A.E. Big data and cloud computing: Current state and future opportunities. In Proceedings of the 14th International Conference on Extending Database Technology (EDBT/ICDT ’11), Uppsala, Sweden, 21–24 March 2011; pp. 530–533. [Google Scholar] [CrossRef]
- Zardari, M.; Low, T.; Zakaria, M. Hybrid Multi-cloud Data Security (HMCDS) Model and Data Classification. In Proceedings of the 2013 International Conference on Advanced Computer Science Applications and Technologies (ACSAT ’13), Kuching, Malaysia, 23–24 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 166–171. [Google Scholar] [CrossRef]
- Gundu, S.R.; Panem, C.A.; Thimmapuram, A. Hybrid IT and Multi Cloud an Emerging Trend and Improved Performance in Cloud Computing. SN Comput. Sci. 2020, 1, 256. [Google Scholar] [CrossRef]
- Bello, S.A.; Oyedele, L.O.; Akinade, O.O.; Bilal, M.; Delgado, J.M.D.; Akanbi, L.A.; Ajayi, A.O.; Owolabi, H.A. Cloud computing in construction industry: Use cases, benefits and challenges. Autom. Constr. 2021, 122, 103441. [Google Scholar] [CrossRef]
- Goscinski, A.; Brock, M. Toward dynamic and attribute based publication, discovery and selection for cloud computing. Future Gener. Comput. Syst. 2010, 26, 947–970. [Google Scholar] [CrossRef]
- Pallis, G. Cloud computing: The new frontier of internet computing. IEEE Internet Comput. 2010, 14, 70–73. [Google Scholar] [CrossRef]
- Misra, S.C.; Mondal, A. Identification of a company’s suitability for the adoption of cloud computing and modelling its corresponding return on investment. Math. Comput. Model. 2011, 53, 504–521. [Google Scholar] [CrossRef]
- Armbrust, M.; Stoica, I.; Zaharia, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef]
- Sharif, A.M. It’s written in the cloud: The hype and promise of cloud computing. J. Enterp. Inf. Manag. 2010, 23, 131–134. [Google Scholar] [CrossRef]
- Voorsluys, W.; Broberg, J.; Venugopal, S.; Buyya, R. Cost of virtual machine live migration in clouds: A performance evaluation. In Proceedings of the 1st International Conference on Cloud Computing, Beijing, China, 1–4 December 2009; pp. 245–265. [Google Scholar] [CrossRef]
- Sultan, N. Cloud computing for education: A new dawn? Int. J. Inf. Manag. 2010, 30, 109–116. [Google Scholar] [CrossRef]
- Banyal, R.K.; Jain, V.K.; Jain, P. Dynamic Trust Based Access Control Framework for Securing Multi-Cloud Environment. In Proceedings of the 2014 International Conference on Information and Communication Technology for Competitive Strategies (ICTCS ’14), Udaipur Rajasthan, India, 14–16 November 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Takabi, D.; Joshi, J.; Ahn, G.J. SecureCloud: Towards a Comprehensive Security Framework for Cloud Computing Environments. In Proceedings of the International Computer Software and Applications Conference (COMPSACW ’10), Seoul, Republic of Korea, 19–23 July 2010; pp. 393–398. [Google Scholar] [CrossRef]
- Alliance, C.S. Security Guidance for Critical Areas of Focus in Cloud Computing V3.0. Technical Report. 2011. Available online: https://www.researchgate.net/publication/356433278_Security_guidance_for_critical_areas_of_focus_in_cloud_computing_v30; also available: https://cloudsecurityalliance.org/artifacts/security-guidance-for-critical-areas-of-focus-in-cloud-computing-v3# (accessed on 20 November 2025).
- Abbadi, I.M. A framework for establishing trust in Cloud provenance. Int. J. Inf. Secur. 2013, 12, 111–128. [Google Scholar] [CrossRef]
- Sekar, J. Multi-cloud Strategies for Distributed AI Workflows and Application. J. Emerg. Technol. Innov. Res. 2023, 10, 600–610. [Google Scholar]
- NIST. The NIST Definition of Cloud Computing; Special Publication 800-145; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011. [Google Scholar]
- Buyya, R.; Yeo, C.S.; Venugopal, S.; Broberg, J.; Brandic, I. Cloud computing and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th utility. Future Gener. Comput. Syst. 2009, 25, 599–616. [Google Scholar] [CrossRef]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.H.; Konwinski, A.; Lee, G.; Patterson, D.A.; Rabkin, A.; Stoica, I.; et al. Above the Clouds: A Berkeley View of Cloud Computing; Technical Report UCB/EECS-2009-28; University of California: Berkeley, CA, USA, 2009. [Google Scholar]
- Marston, S.; Li, Z.; Bandyopadhyay, S.; Zhang, J.; Ghalsasi, A. Cloud computing—The business perspective. Decis. Support Syst. 2011, 51, 176–189. [Google Scholar] [CrossRef]
- Adabala, S.K. The Role of Cloud Computing in Driving Business Innovation. Int. J. Innov. Res. Creat. Technol. 2020, 6, 1–19. [Google Scholar]
- Zawoad, S.; Hasan, R. Cloud Forensics: A Meta-Study of Challenges, Approaches, and Open Problems. arXiv 2013, arXiv:1302.6312. [Google Scholar] [CrossRef]
- Yeboah-Ofori, A.; Jafar, A.; Abisogun, T.; Hilton, I.; Oseni, W.; Musa, A. Data Security and Governance in Multi-Cloud Computing Environment. In Proceedings of the 11th International Conference on Future Internet of Things and Cloud (FiCloud ’24), Vienna, Austria, 19–21 August 2024; pp. 215–222. [Google Scholar] [CrossRef]
- Mishra, S.K.; Mishra, S.; Alsayat, A.; Jhanjhi, N.Z.; Humayun, M.; Sahoo, K.S.; Luhach, A.K. Energy-Aware Task Allocation for Multi-Cloud Networks. IEEE Access 2020, 8, 178825–178834. [Google Scholar] [CrossRef]
- Mavrogeorgi, N.; Gogouvitis, S.; Voulodimos, A.; Kiriazis, D.; Varvarigou, T.; Shulman-Peleg, A.; Kolodner, E.K. Dynamic Rule-Based SLA Management in Clouds. In Proceedings of the 2013 IEEE Sixth International Conference on Cloud Computing (CLOUD ’13), Santa Clara, CA, USA, 28 June–3 July 2013; pp. 964–965. [Google Scholar] [CrossRef]
- Lin, X.; Wang, Y.; Xie, Q.; Pedram, M. Task Scheduling with Dynamic Voltage and Frequency Scaling for Energy Minimization in the Mobile Cloud Computing Environment. IEEE Trans. Serv. Comput. 2014, 8, 175–186. [Google Scholar] [CrossRef]
- Ferrer, A.J.; Pérez, D.G.; González, R.S. Multi-cloud Platform-as-a-service Model, Functionalities and Approaches. Procedia Comput. Sci. 2016, 97, 63–72. [Google Scholar] [CrossRef]
- Cachin, C.; Keidar, I.; Shraer, A. Trusting the cloud. SIGACT News 2009, 40, 81–86. [Google Scholar] [CrossRef]
- Alyas, T.; Alissa, K.; Alqahtani, M.; Faiz, T.; Alsaif, S.A.; Tabassum, N.; Naqvi, H.H. Multi-Cloud Integration Security Framework Using Honeypots. Mob. Inf. Syst. 2022, 2022, 2600712. [Google Scholar] [CrossRef]
- Gonzalez, A.E.; Arzuaga, E. HerdMonitor: Monitoring Live Migrating Containers in Cloud Environments. In Proceedings of the 2020 IEEE International Conference on Big Data (BigData ’20), Atlanta, GA, USA, 10–13 December 2020; pp. 2180–2189. [Google Scholar]
- James, W. AI-Powered Threat Detection in Hybrid and Multi-Cloud Environments: Overcoming Security Challenges. 2023. Available online: https://www.researchgate.net/publication/384935856_AI-Powered_Threat_Detection_in_Hybrid_and_Multi-Cloud_Environments_Overcoming_Security_Challenges (accessed on 20 November 2025).
- Heilig, L.; Lalla-Ruiz, E.; Voß, S. Modeling and solving cloud service purchasing in multi-cloud environments. Expert Syst. Appl. 2020, 147, 113165. [Google Scholar] [CrossRef]
- Hoffa, C.; Mehta, G.; Freeman, T.; Deelman, E.; Keahey, K.; Berriman, B.; Good, J. On the use of cloud computing for scientific workflows. In Proceedings of the Fourth IEEE International Conference on eScience (eScience ’08), Indianapolis, IN, USA, 7–12 December 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 640–645. [Google Scholar]
- Tuli, S.; Mahmud, R.; Tuli, S.; Buyya, R. Towards Secure Fog Computing: A Survey on Trust Management, Privacy, Authentication, Threats and Access Control. Electronics 2021, 10, 1171. [Google Scholar] [CrossRef]
- Guan, S.; De Grande, R.E.; Boukerche, A. A Multi-Layered Scheme for Distributed Simulations on the Cloud Environment. IEEE Trans. Cloud Comput. 2019, 7, 5–18. [Google Scholar] [CrossRef]
- Muhil, M.; Krishna, U.H.; Kumar, R.K.; Anita, E.A.M. Securing Multi-cloud Using Secret Sharing Algorithm. Procedia Comput. Sci. 2015, 50, 421–426. [Google Scholar] [CrossRef][Green Version]
- Zhou, L.; Zygmunt, H. Securing Ad Hoc Networks. IEEE Netw. 1999, 13, 24–30. [Google Scholar] [CrossRef]
- Kritikos, K.; Zeginis, C.; Iranzo, J.; Gonzalez, R.S.; Seybold, D.; Griesinger, F.; Domaschka, J. Multi-cloud provisioning of business processes. J. Cloud Comput. 2019, 8, 18. [Google Scholar] [CrossRef]
- Journal of Cloud Computing. 2020. Available online: https://journalofcloudcomputing.springeropen.com/ (accessed on 28 June 2025).
- Pochu, S.; Nersu, S.; Kathram, S. Multi-Cloud DevOps Strategies: A Framework for Agility and Cost Optimization. J. Artif. Intell. Gen. Sci. 2024, 7, 104–119. [Google Scholar] [CrossRef]
- Seth, D.; Nerella, H.; Najana, M.; Tabbassum, A. Navigating the Multi-Cloud Maze: Benefits, Challenges, and Future Trends. Int. J. Glob. Innov. Solut. (IJGIS) 2024. [Google Scholar] [CrossRef]
- Abu-Libdeh, H.; Princehouse, L.; Weatherspoon, H. RACS: A case for cloud storage diversity. In Proceedings of the 1st ACM Symposium on Cloud Computing (SoCC ’10), Indianapolis, IN, USA, 10–11 June 2010; pp. 229–240. [Google Scholar] [CrossRef]
- Bessani, A.; Correia, M.; Quaresma, B.; André, F.; Sousa, P. DepSky: Dependable and Secure Storage in a Cloud-of-Clouds. ACM Trans. Storage 2013, 9, 1–33. [Google Scholar] [CrossRef]
- Bowers, K.D.; Juels, A.; Oprea, A. HAIL: A high-availability and integrity layer for cloud storage. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS ’09), Chicago, IL, USA, 9–13 November 2009; pp. 187–198. [Google Scholar] [CrossRef]
- Cachin, C.; Haas, R.; Vukolic, M. Dependable Storage in the Intercloud. Tech. Report 3783, IBM Research. 2010. Available online: https://www.researchgate.net/publication/288925333_Dependable_storage_in_the_Intercloud/citation/download (accessed on 16 July 2025).
- Megouache, L.; Zitouni, A.; Djoudi, M. Ensuring User Authentication and Data Integrity in Multi-Cloud Environment. Hum.-Centric Comput. Inf. Sci. 2020, 10, 15. [Google Scholar] [CrossRef]
- Reece, M.; Lander, T.E.; Stoffolano, M.; Sampson, A.; Dykstra, J.; Mittal, S.; Rastogi, N. Systemic Risk and Vulnerability Analysis of Multi-cloud Environments. arXiv 2023, arXiv:2306.01862. [Google Scholar] [CrossRef]
- Afolaranmi, S.O.; Ferrer, B.R.; Martinez Lastra, J.L. A Framework for Evaluating Security in Multi-Cloud Environments. In Proceedings of the 44th Annual Conference of the IEEE Industrial Electronics Society (IECON ’18), Washington, DC, USA, 21–23 October 2018; pp. 3059–3066. [Google Scholar] [CrossRef]
- Lander, T.E., Jr. Multi-Cloud Architecture Attacks Through Application Programming Interfaces. Master’s Thesis, Mississippi State University, Starkville, MS, USA, 2024. [Google Scholar]
- Sun, P.J. Privacy Protection and Data Security in Cloud Computing: A Survey, Challenges, and Solutions. IEEE Access 2019, 7, 147420–147452. [Google Scholar] [CrossRef]
- Gupta, L.; Salman, T.; Ghubaish, A.; Unal, D.; Al-Ali, A.K.; Jain, R. Cybersecurity of multi-cloud healthcare systems: A hierarchical deep learning approach. Appl. Soft Comput. 2022, 118, 108439. [Google Scholar] [CrossRef]
- Salman, T.; Bhamare, D.; Erbad, A.; Jain, R.; Samaka, M. Machine Learning for Anomaly Detection and Categorization in Multi-Cloud Environments. In Proceedings of the 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud ’17), New York, NY, USA, 26–28 June 2017; pp. 97–103. [Google Scholar] [CrossRef]
- Hayajneh, T.; Mohd, B.; Itradat, A. Performance and Information Security Evaluation with Firewalls. Int. J. Secur. Its Appl. 2013, 7, 335–372. [Google Scholar] [CrossRef]
- Binu, C.T.; Mohan Kumar, S. A Review on Security Issues in Multi Cloud Computing and Prevention by Security Measures. Int. J. Sci. Res. Publ. 2023, 13, 248–254. [Google Scholar] [CrossRef]
- Reece, M.; Rastogi, N.; Lander, T.; Dykstra, J.; Mittal, S.; Sampson, A. Defending Multi-Cloud Applications Against Man-in-the-Middle Attacks. In Proceedings of the 29th ACM Symposium on Access Control Models and Technologies (SACMAT 2024), San Antonio, TX, USA, 15–17 May 2024; pp. 47–52. [Google Scholar] [CrossRef]
- Awodele, O.; Ogu, E.; Kuyoro, S.; Umezuruike, C. On the Evolution of Virtualization and Cloud Computing: A Review. J. Comput. Sci. Appl. 2014, 2, 40–43. [Google Scholar] [CrossRef][Green Version]
- Kilari, N.; Sridaran, R. A Survey on Security Threats for Cloud Computing. Int. J. Eng. Res. Technol. (IJERT) 2021, 1. [Google Scholar]
- Torkura, K.A.; Sukmana, M.I.H.; Cheng, F.; Meinel, C. Continuous auditing and threat detection in multi-cloud infrastructure. Comput. Secur. 2021, 102, 102124. [Google Scholar] [CrossRef]
- Cloud Security Alliance (CSA). Top Threats to Cloud Computing: The Egregious 11; Technical Report; Cloud Security Alliance: Seattle, WA, USA, 2019. [Google Scholar]
- Trend Micro. Data on 123 Million US Households Exposed Due to Misconfigured AWS S3 Bucket. 2017. Available online: https://www.trendmicro.com/vinfo/au/security/news/virtualization-and-cloud/data-on-123-million-us-households-exposed-due-to-misconfigured-aws-s3-bucket (accessed on 16 July 2025).
- UpGuard. Data Leaks, Cyber Risk, and eStar. 2017. Available online: https://www.upguard.com/breaches/cloud-leak-alteryx (accessed on 20 November 2025).
- Kincaid, J. Google Privacy Blunder Shares Your Docs Without Permission. 2009. Available online: http://techcrunch.com/2009/03/07/huge-google-privacy-blunder-shares-your-docs-without-permission/ (accessed on 16 July 2025).
- Jensen, M.; Schwenk, J.; Gruschka, N.; Iacono, L.L. Security Prospects through Cloud Computing by Adopting Multiple Clouds. In Proceedings of the IEEE 4th International Conference on Cloud Computing (CLOUD), Washington, DC, USA, 4–9 July 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 565–572. [Google Scholar] [CrossRef]
- Ristenpart, T.; Tromer, E.; Shacham, H.; Savage, S. Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS ’09), Chicago, IL, USA, 9–13 November 2009; pp. 199–212. [Google Scholar] [CrossRef]
- Gruschka, N.; Iacono, L.L. Vulnerable Cloud: SOAP Message Security Validation Revisited. In Proceedings of the 2009 IEEE International Conference on Web Services (ICWS ’09), Los Angeles, CA, USA, 6–10 July 2009; pp. 625–631. [Google Scholar] [CrossRef]
- McIntosh, M.; Austel, P. XML Signature Element Wrapping Attacks and Countermeasures. In Proceedings of the 2005 Workshop on Secure Web Services (SWS ’05), Fairfax, VA, USA, 11 November 2005; pp. 20–27. [Google Scholar] [CrossRef]
- Ponemon, I. Cost of a Data Breach Report; Benchmark Research Sponsored by IBM Security Independently Conducted by Ponemon Institute LLC; 2019. Available online: https://insights.integrity360.com/hubfs/2019-cost-of-a-data-breach-report-04_03025203USEN.pdf (accessed on 20 November 2025).
- Mohammad, N. Enhancing Security and Privacy in Multi-Cloud Environments: A Comprehensive Study on Encryption Techniques and Access Control Mechanisms. Int. J. Comput. Eng. Technol. 2021, 12, 51–63. [Google Scholar]
- Caprolu, M.; Raponi, S.; Oligeri, G.; Di Pietro, R. Cryptomining Makes Noise: A Machine Learning Approach for Cryptojacking Detection. arXiv 2020, arXiv:1910.09272. [Google Scholar] [CrossRef]
- Jayasinghe, K.; Guhanathan, P. A Survey of Attack Instances of Cryptojacking Targeting Cloud Infrastructure. In Proceedings of the 2020 2nd International Conference on Cloud Computing and Internet of Things (CCIOT 2020), Singapore, 22–24 February 2020; pp. 100–107. [Google Scholar] [CrossRef]
- Tekiner, E.; Acar, A.; Uluagac, A.S.; Kirda, E.; Selcuk, A.A. SoK: Cryptojacking Malware. arXiv 2021, arXiv:2103.03851. [Google Scholar] [CrossRef]
- Somani, G.; Gaur, M.S.; Sanghi, D.; Conti, M.; Buyya, R. DDoS Attacks in Cloud Computing: Issues, Taxonomy and Future Directions. Comput. Commun. 2017, 107, 30–48. [Google Scholar] [CrossRef]
- Dorsett, M.; Mann, S.; Chowdhury, J.; Mahmood, A. A Comprehensive Review of Denial of Wallet Attacks in Serverless Architectures. arXiv 2025, arXiv:2508.19284. [Google Scholar] [CrossRef]
- Karami, M.; Gupta, L.; Shakarian, P.; Shakarian, J. Attribution of Economic Denial of Sustainability Attacks in Public Clouds. EAI Endorsed Trans. Secur. Saf. 2018, 4, e2. [Google Scholar] [CrossRef][Green Version]
- Saeed, S.; Zainal, A.B.; Ghaleb, F.A.; Al-rimy, B.A.S. Enhancing Public Cloud Resilience: An Analytical Review of Detection and Mitigation Strategies Against Economic Denial of Sustainability Attacks. Discov. Internet Things 2025, 5, 79. [Google Scholar] [CrossRef]
- Somasundaram, A. Economic Denial of Sustainability (EDoS) Attack on Cloud—A Survey. ICTACT J. Commun. Technol. 2016, 7, 1402–1407. [Google Scholar] [CrossRef]
- Aldhyani, T.H.H.; Alkahtani, H. Artificial Intelligence Algorithm-Based Economic Denial of Sustainability Attack Detection Systems: Cloud Computing Environments. Sensors 2022, 22, 4685. [Google Scholar] [CrossRef]
- Frieß, J.; Gattermayer, T.; Gelernter, N.; Schulmann, H.; Waidner, M. Cloudy with a Chance of Cyberattacks: Dangling Resources Abuse on Cloud Platforms. arXiv 2024, arXiv:2403.19368. [Google Scholar] [CrossRef]
- Pansy. 80+ Cloud Security Statistics to Know for 2024. 2024. Available online: https://sprinto.com/blog/cloud-security-statistics/ (accessed on 16 July 2025).
- IBM. Cost of a Data Breach 2024. 2024. Available online: https://www.ibm.com/reports/data-breach (accessed on 20 November 2025).
- Alouffi, B.; Hasnain, M.; Alharbi, A.; Alosaimi, W.; Alyami, H.; Ayaz, M. A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies. IEEE Access 2021, 9, 57792–57807. [Google Scholar] [CrossRef]
- Jaeger, P.; Lin, J.; Grimes, J. Cloud Computing and Information Policy: Computing in a Policy Cloud? J. Inf. Technol. Politics 2008, 5, 269–283. [Google Scholar] [CrossRef]
- Sasubilli, M.K.; Venkateswarlu, R. Cloud Computing Security Challenges, Threats and Vulnerabilities. In Proceedings of the 6th International Conference on Inventive Computation Technologies (ICICT ’21), Coimbatore, India, 20–22 January 2021; pp. 476–480. [Google Scholar] [CrossRef]
- Tankard, C. What the GDPR Means for Businesses. Netw. Secur. 2016, 2016, 5–8. [Google Scholar] [CrossRef]
- European Union. General Data Protection Regulation (GDPR). 2020. Available online: https://eur-lex.europa.eu/eli/reg/2016/679/oj (accessed on 20 November 2025).
- Cloud Security Alliance (CSA). State of Cloud Report; Cloud Security Alliance: Seattle, WA, USA, 2018; Available online: https://cloudsecurityalliance.org/artifacts/state-of-cloud-report (accessed on 20 November 2025).
- NetDiligence. Cyber Claims Study 2020 Report. 2020. Available online: https://netdiligence.com/cyber-claims-study-2020-report/ (accessed on 20 November 2025).
- Ali, T.E.; Zoltan, A.D. Hierarchical Deep Learning for Robust Cybersecurity in Multi-Cloud Healthcare Infrastructures. Eng. Technol. Appl. Sci. Res. 2025, 15, 20358–20366. [Google Scholar] [CrossRef]
- Choi, S.J.; Johnson, M.E. Do Hospital Data Breaches Reduce Patient Care Quality? arXiv 2019. [Google Scholar] [CrossRef]
- Marelli, M. The SolarWinds Hack: Lessons for International Humanitarian Organizations. Int. Rev. Red Cross 2022, 104, 1267–1284. [Google Scholar] [CrossRef]
- Jones, J.; Smith, B.; Micheal, O.; Barnes, M.; Adebayo, H. Revolutionizing Cybersecurity with AI-Driven SIEM: Optimizing Threat Detection in Multi-Cloud Environments. 2025; unpublished manuscript. [Google Scholar]
- Velavan, A.S.; Sureshkumar, C. Double Fuzzy Clustering-Driven Context Neural Network for Intrusion Detection in Cloud Computing. Wirel. Netw. 2025, 31, 2513–2524. [Google Scholar] [CrossRef]
- Masoodi, H.J.K.A.L. Evaluating the Effectiveness of Machine Learning-Based Intrusion Detection in Multi-Cloud Environments. Babylon. J. Internet Things 2024, 2024, 94–105. [Google Scholar] [CrossRef]
- Mitropoulou, K.; Kokkinos, P.; Soumplis, P.; Varvarigos, E. Anomaly Detection in Cloud Computing using Knowledge Graph Embedding and Machine Learning Mechanisms. J. Grid Comput. 2024, 22, 6. [Google Scholar] [CrossRef]
- Fatani, A.; Dahou, A.; Abd Elaziz, M.; Al-qaness, M.A.A.; Lu, S.; Alfadhli, S.A.; Alresheedi, S.S. Enhancing Intrusion Detection Systems for IoT and Cloud Environments Using a Growth Optimizer Algorithm and Conventional Neural Networks. Sensors 2023, 23, 4430. [Google Scholar] [CrossRef]
- Alzughaibi, S.; El Khediri, S. A Cloud Intrusion Detection Systems Based on DNN Using Backpropagation and PSO on the CSE-CIC-IDS2018 Dataset. Appl. Sci. 2023, 13, 2276. [Google Scholar] [CrossRef]
- Attou, H.; Mohy-eddine, M.; Guezzaz, A.; Benkirane, S.; Azrour, M.; Alabdultif, A.; Almusallam, N. Towards an Intelligent Intrusion Detection System to Detect Malicious Activities in Cloud Computing. Appl. Sci. 2023, 13, 9588. [Google Scholar] [CrossRef]
- Bingu, R.; Jothilakshmi, S. Design of Intrusion Detection System using Ensemble Learning Technique in Cloud Computing Environment. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2023, 14, 751–764. [Google Scholar] [CrossRef]
- Lin, H.; Xue, Q.; Feng, J.; Bai, D. Internet of things intrusion detection model and algorithm based on cloud computing and multi-feature extraction extreme learning machine. Digit. Commun. Netw. 2023, 9, 111–124. [Google Scholar] [CrossRef]
- Nizamudeen, S. Intelligent intrusion detection framework for multi-clouds–IoT environment using swarm-based deep learning classifier. J. Cloud Comput. 2023, 12, 134. [Google Scholar] [CrossRef]
- Shahzad, F.; Mannan, A.; Javed, A.; Almadhor, A.S.; Baker, T.; Al-Jumeily OBE, D. Cloud-based multiclass anomaly detection and categorization using ensemble learning. J. Cloud Comput. 2022, 11, 74. [Google Scholar] [CrossRef]
- Samunnisa, K.; Kumar, G.S.V.; Madhavi, K. Intrusion detection system in distributed cloud computing: Hybrid clustering and classification methods. Meas. Sens. 2023, 25, 100612. [Google Scholar] [CrossRef]
- Abusitta, A.; Bellaiche, M.; Dagenais, M.; Halabi, T. A Deep Learning Approach for Proactive Multi-Cloud Cooperative Intrusion Detection System. Future Gener. Comput. Syst. 2019, 98, 308–318. [Google Scholar] [CrossRef]
- Achar, S. Cloud Computing Security for Multi-Cloud Service Providers: Controls and Techniques in Our Modern Threat Landscape. Int. J. Comput. Syst. Eng. 2022, 16, 379–384. [Google Scholar] [CrossRef]
- Deepa, T.; Kiran Mayee, M. Cloud Computing: Security and Privacy Issues. Int. J. Trend Res. Dev. (IJTRD) 2017. Available online: http://www.ijtrd.com/papers/IJTRD13397.pdf (accessed on 14 October 2025).
- Razaque, A.; Nadimpalli, S.S.V.; Vommina, S.; Atukuri, D.K.; Reddy, D.N.; Anne, P.; Vegi, D.; Malllapu, V.S. Secure Data Sharing in Multi-Clouds. In Proceedings of the 2016 International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016; pp. 1909–1913. [Google Scholar] [CrossRef]
- Rodigari, S.; O’Shea, D.; McCarthy, P.; McCarry, M.; McSweeney, S. Performance Analysis of Zero-Trust Multi-Cloud. In Proceedings of the 14th IEEE International Conference on Cloud Computing (CLOUD ’21), Chicago, IL, USA, 5–10 September 2021; pp. 730–732. [Google Scholar] [CrossRef]
- Dickinson, M.; Debroy, S.; Calyam, P.; Valluripally, S.; Zhang, Y.; Antequera, R.B.; Joshi, T.; White, T.; Xu, D. Multi-Cloud Performance and Security Driven Federated Workflow Management. IEEE Trans. Cloud Comput. 2021, 9, 240–257. [Google Scholar] [CrossRef]
- Kurdi, H.; Alsalamah, S.; Alatawi, A.; Alfaraj, S.; Altoaimy, L.; Ahmed, S.H. HealthyBroker: A Trustworthy Blockchain-Based Multi-Cloud Broker for Patient-Centered eHealth Services. Electronics 2019, 8, 602. [Google Scholar] [CrossRef]
- Alaluna, M.; Vial, E.; Neves, N.; Ramos, F.M.V. Secure Multi-Cloud Network Virtualization. Comput. Netw. 2019, 161, 168–185. [Google Scholar] [CrossRef]
- Shirvani, M.H. Web Service Composition in Multi-Cloud Environment: A Bi-Objective Genetic Optimization Algorithm. In Proceedings of the 2018 Innovations in Intelligent Systems and Applications (INISTA ’18), Thessaloniki, Greece, 3–5 July 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Subramanian, K.; John, F.L. Enhanced Security for Data Sharing in Multi Cloud Storage (SDSMC). Int. J. Adv. Comput. Sci. Appl. 2017, 8, 176–185. [Google Scholar] [CrossRef][Green Version]
- Sarojini, G.; Vijayakumar, V.A.; Selvamani, K. Trusted and Reputed Services Using Enhanced Mutual Trusted and Reputed Access Control Algorithm in Cloud. Procedia Comput. Sci. 2016, 92, 506–512. [Google Scholar] [CrossRef]
- Sulochana, M.; Dubey, O. Preserving Data Confidentiality Using Multi-cloud Architecture. Procedia Comput. Sci. 2015, 50, 357–362. [Google Scholar] [CrossRef][Green Version]
- Fan, W.; Perros, H. A Novel Trust Management Framework for Multi-Cloud Environments Based on Trust Service Providers. Knowl.-Based Syst. 2014, 70, 392–406. [Google Scholar] [CrossRef]
- Kumar, N.S.; Lakshmi, G.V.R.; Balamurugan, B. Enhanced Attribute Based Encryption for Cloud Computing. Procedia Comput. Sci. 2015, 46, 689–696. [Google Scholar] [CrossRef][Green Version]
- Alhamazani, K.; Ranjan, R.; Mitra, K.; Jayaraman, P.P.; Huang, Z.; Wang, L.; Rabhi, F. CLAMS: Cross-layer Multi-cloud Application Monitoring-as-a-Service Framework. In Proceedings of the 2014 IEEE International Conference on Services Computing (SCC ’14), Anchorage, AK, USA, 27 June–2 July 2014; pp. 283–290. [Google Scholar] [CrossRef]
- Giweli, N.; Shahrestani, S.; Cheung, H. Enhancing Data Privacy and Access Anonymity in Cloud Computing. Commun. IBIMA 2013, 2013, 1–10. [Google Scholar] [CrossRef][Green Version]
- Dou, W.; Zhang, X.; Liu, J.; Chen, J. HireSome-II: Towards Privacy-Aware Cross-Cloud Service Composition for Big Data Applications. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 455–466. [Google Scholar] [CrossRef]
- Tabalvandani, M.A.N.; Shirvani, M.H.; Motameni, H. Reliability-aware web service composition with cost minimization perspective: A multi-objective particle swarm optimization model in multi-cloud scenarios. Soft Comput. 2024, 28, 5173–5196. [Google Scholar] [CrossRef]
- Tang, X. Reliability-Aware Cost-Efficient Scientific Workflows Scheduling Strategy on Multi-Cloud Systems. IEEE Trans. Cloud Comput. 2022, 10, 2909–2919. [Google Scholar] [CrossRef]
- Wojtowicz, D.T.; Yin, S.; Morvan, F.; Hameurlain, A. Cost-Effective Dynamic Optimisation for Multi-Cloud Queries. In Proceedings of the 2021 IEEE 14th International Conference on Cloud Computing (CLOUD), Chicago, IL, USA, 5–10 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 387–397. [Google Scholar] [CrossRef]
- Wang, P.; Zhao, C.; Liu, W.; Chen, Z.; Zhang, Z. Optimizing Data Placement for Cost Effective and High Available Multi-Cloud Storage. Comput. Inform. 2020, 39, 51–82. [Google Scholar] [CrossRef]
- Gao, T.; Wu, C.Q.; Hou, A.; Wang, Y.; Li, R.; Xu, M. Minimizing Financial Cost of Scientific Workflows under Deadline Constraints in Multi-Cloud Environments. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing (SAC ’19), Limassol, Cyprus, 8–12 April 2019; pp. 114–121. [Google Scholar] [CrossRef]
- Peralta, G.; Garrido, P.; Bilbao, J.; Agüero, R.; Crespo, P.M. On the Combination of Multi-Cloud and Network Coding for Cost-Efficient Storage in Industrial Applications. Sensors 2019, 19, 1673. [Google Scholar] [CrossRef] [PubMed]
- Wang, P.; Zhao, C.; Zhang, Z. An Ant Colony Algorithm-Based Approach for Cost-Effective Data Hosting with High Availability in Multi-Cloud Environments. In Proceedings of the 2018 IEEE 15th International Conference on Networking, Sensing and Control (ICNSC), Zhuhai, China, 27–29 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Mohammadi, S.; Pedram, H.; PourKarimi, L. Integer Linear Programming-based Cost Optimization for Scheduling Scientific Workflows in Multi-cloud Environments. J. Supercomput. 2018, 74, 4717–4745. [Google Scholar] [CrossRef]
- Zhang, Q.; Li, S.; Li, Z.; Xing, Y.; Yang, Z.; Dai, Y. CHARM: A Cost-Efficient Multi-Cloud Data Hosting Scheme with High Availability. IEEE Trans. Cloud Comput. 2015, 3, 372–386. [Google Scholar] [CrossRef]
- Imai, S.; Patterson, S.; Varela, C.A. Cost-Efficient High-Performance Internet-Scale Data Analytics over Multi-Cloud Environments. In Proceedings of the 2015 15th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGrid), Shenzhen, China, 4–7 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 793–796. [Google Scholar] [CrossRef]
- Lucas-Simarro, J.L.; Moreno-Vozmediano, R.; Montero, R.S.; Llorente, I.M. Cost optimization of virtual infrastructures in dynamic multi-cloud scenarios. Concurr. Comput. Pract. Exper. 2015, 27, 2260–2277. [Google Scholar] [CrossRef]
- Bellur, U.; Malani, A.; Narendra, N.C. Cost Optimization in Multi-site Multi-cloud Environments with Multiple Pricing Schemes. In Proceedings of the 2014 IEEE 7th International Conference on Cloud Computing (CLOUD), Anchorage, AK, USA, 27 June–2 July 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 689–696. [Google Scholar] [CrossRef]
- Legillon, F.; Melab, N.; Renard, D.; Talbi, E.G. Cost Minimization of Service Deployment in a Multi-Cloud Environment. In Proceedings of the 2013 IEEE Congress on Evolutionary Computation (CEC), Cancun, Mexico, 20–23 June 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 2580–2587. [Google Scholar] [CrossRef]
- Singh, Y.; Kandah, F.; Zhang, W. A Secured Cost-Effective Multi-Cloud Storage in Cloud Computing. In Proceedings of the 2011 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Shanghai, China, 10–15 April 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 619–624. [Google Scholar] [CrossRef]
- Simarro, J.L.L.; Moreno-Vozmediano, R.; Montero, R.S.; Llorente, I.M. Dynamic Placement of Virtual Machines for Cost Optimization in Multi-Cloud Environments. In Proceedings of the 2011 International Conference on High Performance Computing & Simulation (HPCSim), Istanbul, Turkey, 4–8 July 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 1–7. [Google Scholar] [CrossRef]
- Frincu, M.E.; Craciun, C. Multi-objective Meta-heuristics for Scheduling Applications with High Availability Requirements and Cost Constraints in Multi-Cloud Environments. In Proceedings of the 2011 Fourth IEEE International Conference on Utility and Cloud Computing (UCC), Melbourne, VIC, Australia, 5–8 December 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 267–274. [Google Scholar] [CrossRef]
- Gholami, A.; Laure, E. Data Security and Privacy Protection Issues in Cloud Computing: A Survey. Int. J. Big Data Intell. (IJBDI) 2017, 4, 81–87. [Google Scholar]
- Casola, V.; Benedictis, A.D.; Rak, M.; Villano, U. Security-by-design in multi-cloud applications: An optimization approach. Inf. Sci. 2018, 462, 220–234. [Google Scholar] [CrossRef]
- Paul, A.L. Security Challenges and Solutions in Multi-Cloud Environments. 2024. Available online: https://www.researchgate.net/publication/381074289_Security_Challenges_and_Solutions_in_Multi-Cloud_Environments (accessed on 27 July 2025).
- Saini, G.; Kaur, N. A Survey of Various Encryption Techniques in Multi Cloud to Reduce Information Leakage. Int. J. Intell. Syst. Appl. Eng. (IJISAE) 2024, 12, 3262–3273. [Google Scholar]
- Tchernykh, A.; Babenko, M.; Kuchukov, V.; Miranda-López, V.; Rivera-Rodriguez, R.; Avetisyan, A.; Radchenko, G. Data Reliability and Redundancy Optimization of a Secure Multi-Cloud Storage Under Uncertainty of Errors and Falsifications. In Proceedings of the International Conference on Computational Science (ICCS), Amsterdam, The Netherlands, 3–5 June 2020. [Google Scholar] [CrossRef]
- Gadde, S.; Amutharaj, J.; Usha, S. A Hybrid Cryptography Technique for Cloud Data Security. Int. J. Eng. Trends Technol. (IJETT) 2022, 70, 258–267. [Google Scholar] [CrossRef]
- Thangavel, P.; Mary, P.S.A.; RameshKannan, M.; Deiwakumari, K. Enhancing Data Security in Multi-Cloud Settings with Homomorphic Encryption: Concepts, Uses, And Obstacles. Educ. Adm. Theory Pract. 2024, 30, 7347–7353. [Google Scholar]
- Shaffi, S.M.; Vengathattil, S.; Sidhick, J.N.; Vijayan, R. AI-Driven Security in Cloud Computing: Enhancing Threat Detection, Automated Response, and Cyber Resilience. J. Cybersecur. Artif. Intell. 2024, 6, 44–56. [Google Scholar] [CrossRef]
- Rasel, F.M.; Peter, B. AI-Driven Frameworks for Enhancing Cybersecurity in Multi-Cloud Environments. Int. J. Adv. Eng. Technol. Innov. 2025, 1, 24–32. [Google Scholar]
- Talati, D.V. Enhancing Multi-Cloud Security with Quantum-Resilient AI for Anomaly Detection. World J. Adv. Res. Rev. 2022, 13, 629–638. [Google Scholar] [CrossRef]
- Nagaraj, B.K. Challenges and Solutions for Integrating AI with Multi-Cloud Architectures. Int. J. Multidiscip. Innov. Res. Methodol. (IJMIRM) 2022, 1, 15–23. [Google Scholar]
- Miryala, N.K. Effective Multi Cloud Security Using AI Technologies. Int. J. Comput. Trends Technol. (IJCTT) 2024, 72, 143–149. [Google Scholar] [CrossRef]
- Nassif, A.B.; Talib, M.A.; Nasir, Q.; Albadani, H.; Dakalbab, F.M. Machine Learning for Cloud Security: A Systematic Review. IEEE Access 2021, 9, 20717–20735. [Google Scholar] [CrossRef]
- Qayyum, A.; Qadir, J.; Al-Fuqaha, A.; Imran, M.A.; Krichen, M. Securing Machine Learning in the Cloud: A Systematic Review of Cloud Machine Learning Security. Front. Big Data 2020, 3, 587139. [Google Scholar] [CrossRef]
- Butt, U.A.; Afzal, S.; Asif, H.; Khalil, I.; Halim, Z. A Review of Machine Learning Algorithms for Cloud Computing Security. Electronics 2020, 9, 1379. [Google Scholar] [CrossRef]
- Mamidi, S.R. Securing Multi-Cloud Architectures: A Machine Learning Perspective. J. Artif. Intell. Gen. Sci. (JAIGS) 2024, 2, 233–247. [Google Scholar] [CrossRef]
- Ahmed, Q.O. Machine Learning for Intrusion Detection in Cloud Environments: A Comparative Study. J. Artif. Intell. Gen. Sci. (JAIGS) 2024, 6, 551–561. [Google Scholar] [CrossRef]
- Hagshenas, N.; Mojarad, M.; Arfaeinia, H. A Fuzzy Approach to Fault Tolerant in Cloud using the Checkpoint Migration Technique. Int. J. Adv. Res. Comput. Sci. 2017, 8, 230–236. [Google Scholar] [CrossRef]
- Swamy, S.R.; Mandapati, S. A Fuzzy Energy and Security Aware Scheduling in Cloud. Int. J. Comput. Sci. Eng. 2018, 6, 168–173. [Google Scholar]
- Soleymani, M.; Abapour, N.; Taghizadeh, E.; Siadat, S.; Karkehabadi, R. Fuzzy Rule-Based Trust Management Model for the Security of Cloud Computing. Math. Probl. Eng. 2021, 2021, 1–15. [Google Scholar] [CrossRef]
- Sharmila, L.; Sakthi, U. Cloud Security Risk Analysis Method based on Fuzzy Logic. Int. J. Recent Technol. Eng. (IJRTE) 2019, 8, 6152–6156. [Google Scholar] [CrossRef]
- Tariq, M.I.; Tayyaba, S.; Mian, N.A.; Sarfraz, M.S.; Hussain, A.; Imran, M.; Pricop, E.; Cangea, O.; Paraschiv, N. An Analysis of the Application of Fuzzy Logic in Cloud Computing. J. Intell. Fuzzy Syst. 2021, 41, 3629–3640. [Google Scholar] [CrossRef]
- Chopra, P.; Bedi, R.P.S. Applications of Fuzzy Logic in Cloud Computing: A Review. Int. J. Sci. Res. Eng. Technol. (IJSRET) 2017, 6, 868–873. [Google Scholar]
- Mateen, M.; Nasrullah, N.; Hayat, S.; Tehreem, T.; Akbar, M.A. A Self-Adaptive Resource Provisioning Approach using Fuzzy Logic for Cloud-Based Applications. Int. J. Comput. Digit. Syst. 2020, 9, 341–348. [Google Scholar] [CrossRef]
- Parkinson, S.; Khana, S. Identifying High-Risk Over-Entitlement in Access Control Policies Using Fuzzy Logic. Cybersecurity 2022, 5, 6. [Google Scholar] [CrossRef]
- Alqahtani, S. Cloud Intrusion Detection Systems: Fuzzy Logic and Classifications. Ph.D. Dissertation, University of Nottingham, Nottingham, UK, 2021. [Google Scholar]
- Hersyah, M.H.; Hossain, M.D.; Taenaka, Y.; Kadobayashi, Y. Fuzzyfortify: A Multi-Attribute Risk Assessment for Multi-Factor Authentication and Cloud Container Orchestration. Front. Comput. Sci. 2025, 7, 1557918. [Google Scholar] [CrossRef]
- Ike, J.E.; Kessie, J.D.; Okaro, H.E.; Ezeife, E.; Onibokun, T. Identity and Access Management in Cloud Storage: A Comprehensive Guide. Int. J. Multidiscip. Res. Growth Eval. 2025, 6, 245–252. [Google Scholar] [CrossRef]
- Cuzzocrea, A.; Belmerabet, I. Towards Privacy-Preserving Multi-Cloud Identity Management Using SOLID. In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT), Dijon, France, 8–10 July 2024; pp. 649–654. [Google Scholar] [CrossRef]
- Barker, N.; Hughes, O.; Warren, R.; James, A. Identity and Access Management (IAM) for Microservices in Multi-Cloud. 2024. Available online: https://www.researchgate.net/publication/392163648 (accessed on 20 November 2025).
- Khambam, S.K.R.; Kaluvakuri, V.P.K. Multi-Cloud IAM Strategies for Fleet Management: Ensuring Data Security Across Platforms. J. Adv. Res. Cloud Comput. 2023, 7, 36–48. [Google Scholar] [CrossRef]
- Sivaraman, H. Zero Trust Identity and Access Management (IAM) in Multi-Cloud Environments. ESP J. Eng. Technol. Adv. 2023, 3, 135–139. [Google Scholar] [CrossRef]
- Akuthota, A.K. Securing Multi-Cloud Environments with SAP BTP, AI, and IAM: A Comprehensive Approach. Int. J. Sci. Technol. (IJSAT) 2025, 16, 14–28. [Google Scholar] [CrossRef]
- Peter, H. Emerging Threats and Best Practices in Cloud Security: Protecting Data in Multi-Cloud Environments. University of Belgrade. 2024. Available online: https://www.researchgate.net/publication/392195015_Emerging_Threats_and_Best_Practices_in_Cloud_Security_Protecting_Data_in_Multi-Cloud_Environments (accessed on 20 November 2025).
- Aditya, W.F.P.; Sukmaaji, A. Exploring Opportunities and Challenges in Multi-Cloud and Hybrid Cloud Implementation: A Focus on Security and Data Management. Inf. Technol. Int. J. 2024, 2, 64–69. [Google Scholar] [CrossRef]
- Karthick, R. A Comprehensive Survey on AI-Enabled Cloud Security, DevSecOps, and Scalable Digital Infrastructure. Preprints 2025. [Google Scholar] [CrossRef]
- Blika, A.; Palmos, S.; Doukas, G.; Lamprou, V.; Pelekis, S.; Kontoulis, M.; Ntanos, C.; Askounis, D. Federated Learning for Enhanced Cybersecurity and Trustworthiness in 5G and 6G Networks: A Comprehensive Survey. IEEE Open J. Commun. Soc. 2024, 5, 2456–2487. [Google Scholar] [CrossRef]
- Brezočnik, L.; Fister, I.; Podgorelec, V. Swarm Intelligence Algorithms for Feature Selection. Appl. Sci. 2018, 8, 1521. [Google Scholar] [CrossRef]
- Varzaneh, Z.A.; Hosseini, S. An Improved Equilibrium Optimization Algorithm for Feature Selection Problem in Network Intrusion Detection. Sci. Rep. 2024, 14, 18696. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Usman, A.A.; Sukat, F.D.; Abdulrahman, M. A novel hybrid autoencoder and modified particle swarm optimization feature selection for intrusion detection in the Internet of Things network. Front. Comput. Sci. 2023, 5, 997159. [Google Scholar] [CrossRef]
- Zhang, Z.; Hamadi, H.A.; Damiani, E.; Yeun, C.Y.; Taher, F. Explainable Artificial Intelligence Applications in Cyber Security: State-of-the-Art in Research. Procedia Comput. Sci. 2023, 224, 858–865. [Google Scholar] [CrossRef]
- Tunde, O. Multi-Cloud Collaborative Training for Large-Scale Language Models: Techniques, Challenges, and Privacy Considerations. Int. J. Multidiscip. Res. Growth Eval. 2025, 6, 517–522. [Google Scholar] [CrossRef]
- Jimmy, F.N.U. Cloud Security Posture Management: Tools and Techniques. J. Knowl. Learn. Sci. Technol. 2023, 2, 622. [Google Scholar] [CrossRef]
- Palo Alto Networks. Prisma Cloud: Comprehensive CSPM and CNAPP Platform. 2024. Available online: https://www.paloaltonetworks.com/prisma/cloud (accessed on 6 November 2025).
- Microsoft Corporation. Microsoft Defender for Cloud Documentation. Microsoft Learn. 2025. Available online: https://learn.microsoft.com/en-us/azure/defender-for-cloud/ (accessed on 20 November 2025).
- Petty, C. 2025 Gartner CNAPP Market Guide: Runtime Visibility is No Longer Optional. Sysdig Blog. 2025. Available online: https://www.sysdig.com/blog/2025-gartner-cnapp-market-guide/ (accessed on 20 November 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).