Abstract
Opportunistic networks, an evolution of mobile Ad Hoc networks (MANETs), offer decentralized communication without relying on preinstalled infrastructure, enabling nodes to route packets through different mobile nodes dynamically. However, due to the absence of complete paths and rapidly changing connectivity, routing in opportunistic networks presents unique challenges. This paper proposes a novel probabilistic routing model for opportunistic networks, leveraging nodes’ meeting probabilities to route packets towards their destinations. Thismodel dynamically builds routes based on the likelihood of encountering the destination node, considering factors such as the last meeting time and acknowledgment tables to manage network overload. Additionally, an efficient message detection scheme is introduced to alleviate high overhead by selectively deleting messages from buffers during congestion. Furthermore, the proposed model incorporates cross-layer optimization techniques, integrating optimization strategies across multiple protocol layers to maximize energy efficiency, adaptability, and message delivery reliability. Through extensive simulations, the effectiveness of the proposed model is demonstrated, showing improved message delivery probability while maintaining reasonable overhead and latency. This research contributes to the advancement of opportunistic networks, particularly in enhancing connectivity and efficiency for Internet of Things (IoT) applications deployed in challenging environments.
1. Introduction
Opportunistic networks represent a paradigm shift in communication, offering decentralized and resilient connectivity in scenarios where traditional infrastructure-based networks may be impractical or unavailable [1]. These networks, born from the evolution of mobile ad hoc networks (MANETs), enable communication between nodes without relying on pre-established infrastructure, allowing packets to be routed dynamically through various mobile nodes in the network. However, the inherently sporadic and unpredictable nature of opportunistic networks poses significant challenges for routing and message delivery. In opportunistic networks, the absence of complete end-to-end paths between source and destination nodes requires routing protocols to adapt dynamically to changing network conditions. Traditional routing approaches designed for internet routing are ill-suited for such environments, necessitating the development of novel routing models tailored to the unique characteristics of opportunistic networks. Additionally, the resource-constrained nature of mobile devices in these networks imposes constraints on energy consumption, requiring energy-efficient routing strategies to prolong network lifespan [1,2].
This paper proposes a novel cross-layer probabilistic routing model for opportunistic networks, designed to address the challenges of dynamic routing and energy efficiency. The proposed model leverages nodes’ meeting probabilities to route packets towards their destinations, dynamically adjusting routes based on encounter history and network conditions. Furthermore, the model incorporates techniques integrating strategies across multiple protocol layers to maximize energy efficiency, adaptability, and message delivery reliability.
This paper presents a comprehensive exploration of leveraging opportunistic networks for enhancing Internet of Things (IoT) communication in Section 2. The proposed solution is presented in Section 3, where we introduce a novel framework employing probabilistic routing algorithms and efficient resource utilization mechanisms to optimize message delivery and address connectivity challenges in dynamic environments. Subsequently, Section 4 details the empirical results and performance evaluations of our proposed solution, presenting significant improvements in several performance metrics. Finally, in Section 5, the paper concludes by summarizing the findings, emphasizing the potential of opportunistic networks to enhance IoT communication.
2. IoT and Opportunistic Networks—State of the Art
IoT systems involve interconnected smart devices equipped with sensors and communication modules. Recent research emphasizes the importance of efficient data routing, scalability, and interoperability in IoT architectures [1]. Opportunistic networks operate in intermittently connected environments, relying on node mobility and opportunistic contacts for communication. Recent studies focus on routing protocols, mobility models, and resource optimization techniques to enhance communication reliability and efficiency [2]. The integration of IoT with opportunistic networks enables applications in disaster management, wildlife monitoring, and rural connectivity. Advanced routing protocols play a crucial role in facilitating data dissemination, energy-efficient routing, and adaptive forwarding strategies [3].
2.1. Applications
- Disaster Management: Advanced routing protocols in IoT-enabled opportunistic networks facilitate resilient data dissemination and coordination in disaster scenarios. Recent research emphasizes the development of delay-tolerant routing algorithms and message ferrying strategies to ensure the timely delivery of critical information [4].
- Wildlife Monitoring: Routing protocols optimized for energy efficiency and adaptability enhance data collection and transmission in wildlife monitoring applications. Recent studies explore opportunistic routing schemes, content-centric protocols, and cooperative forwarding strategies to extend network coverage and reduce communication overhead [5].
- Rural Connectivity: Advanced routing protocols address connectivity challenges in IoT deployments in rural areas. Research focuses on geographic routing, social-aware forwarding, and multi-path selection techniques to optimize message delivery and mitigate the impact of network partitions [6].
2.2. Challenges
- Intermittent Connectivity: Routing in opportunistic networks with intermittent connectivity requires novel approaches to handle network disruptions and message delivery delays. Recent research emphasizes the design of store-carry-and-forward mechanisms, encounter-based routing, and epidemic protocols to adapt to changing network conditions [7].
- Dynamic Topology: Opportunistic networks exhibit dynamic topology due to node mobility and intermittent contacts. Advanced routing protocols incorporate mobility prediction, context-aware routing, and network coding techniques to improve routing efficiency and adaptability [8].
- Resource Constraints: IoT devices operating in opportunistic networks have limited resources, including battery power and bandwidth. Routing protocols must optimize resource utilization through energy-aware routing, data aggregation, and adaptive transmission strategies [9].
- Content-Centric Networking: Future research directions include the exploration of content-centric networking paradigms in IoT-enabled opportunistic networks. Content-based routing, caching, and dissemination strategies offer opportunities to enhance data delivery efficiency and support diverse application requirements [10].
- Cross-Layer Optimization: Leveraging cross-layer optimization techniques to enhance routing performance and resource utilization in IoT-enabled opportunistic networks. Integrating network, transport, and application layer functionalities enables holistic optimization and adaptation to dynamic network conditions [11].
- Edge Computing Integration: Integrating edge computing capabilities with opportunistic networks willsupport localized data processing and decision-making. Edge-aware routing protocols and distributed computing frameworks enable efficient utilization of edge resources and reduce reliance on centralized infrastructure [12].
2.3. Routing in Opportunistic Networks
Recent research has witnessed a surge in the development of novel routing protocols tailored to the challenges of opportunistic networks. Zhang et al. introduced CARP, a context-aware routing protocol that utilizes contextual information such as node mobility patterns and encounter history to make routing decisions dynamically [13]. Li et al. proposed a hybrid routing protocol, combining epidemic routing with social-based forwarding mechanisms, which exploit social relationships between nodes to enhance message dissemination efficiency [14]. Additionally, Chen et al. presented MARP, a mobility-aware routing protocol that adapts routing strategies based on predictive mobility models and encounters probabilities, ensuring robustness against node mobility and network dynamics [15]. Wang et al. introduced ACO-RP, a bio-inspired routing protocol inspired by ant colony optimization principles, which demonstrated superior scalability and message delivery efficiency [16]. Moreover, Yang et al. proposed RUPON, leveraging reinforcement learning techniques to optimize routing decisions based on network dynamics and historical data, thereby achieving adaptive and efficient routing in opportunistic networks [17]. Similarly, Liu et al. introduced PRON, a policy routing protocol based on deep reinforcement learning, which learns optimal routing policies from historical experiences and network conditions to achieve improved message delivery performance [18]. These innovative routing protocols employ advanced techniques such as context awareness, social relationships, mobility prediction, and bio-inspired algorithms to overcome the challenges of intermittently connected environments, paving the way for efficient and adaptive communication in opportunistic networks.
2.4. Energy Efficiency in Opportunistic Networks and IoT
In opportunistic networks, energy-efficient communication is essential due to the sporadic nature of network connectivity and the limited battery life of mobile devices. Researchers have proposed various techniques to optimize energy consumption while maintaining communication reliability. For instance, Zhao et al. introduced an energy-aware routing protocol for opportunistic networks, which dynamically selects routes considering both energy levels and transmission opportunities [19]. Similarly, Li et al. proposed an energy-efficient data dissemination scheme based on social network analysis, where nodes with higher energy reserves are prioritized for message forwarding [20]. These studies highlight the importance of energyawareness in routing and data dissemination strategies to prolong network lifetime in opportunistic environments.
In IoT deployments, energy efficiency is crucial for prolonging device lifespan and reducing maintenance overhead. Recent research has focused on optimizing energy consumption at both the device and network levels. For example, Kim et al. proposed an energy-efficient IoT architecture leveraging edge computing and data aggregation techniques to minimize data transmission and processing overhead [21]. Additionally, Zhang et al. introduced an energy-efficient MAC protocol for IoT networks, which adapts transmission parameters based on channel conditions to reduce energy consumption during data transmission [22]. These studies demonstrate the significance of energy-efficient protocols and architectures in enabling sustainable IoT deployments.
Recent advancements in energy efficiency emphasize cross-layer designs that integrate optimization techniques across different protocol layers. For instance, Liu et al. proposed a cross-layer optimization framework for IoT networks, which jointly optimizes routing, MAC, and physical layer parameters to minimize energy consumption while ensuring QoS requirements [23]. Similarly, Wang et al. introduced a cross-layer energy management scheme for opportunistic networks, which dynamically adjusts routing and transmission parameters based on energy availability and network conditions [24]. These studies highlight the potential of cross-layer approaches in maximizing energy efficiency in both opportunistic networks and IoT deployments. In response to the limitations of conventional routing protocols, the authors in [25] introduce VORTEX, a novel routing protocol that utilizes opportunistic routing strategies with hierarchization. VORTEX features network-driven opportunistic forwarding, where packets progress towards destination terminals using hierarchy as guidance, eliminating the need for conventional route discovery procedures. In [26], a hybrid route selection mechanism, enabling both proactive evaluation by the central controller for source nodes and reactive decision-making by source nodes for route selection in a distributed manner, is proposed. The preference for D2D communication facilitates traffic offloading from the control plane to the data plane, enhancing network efficiency.
2.5. Paper Contribution
Our contribution lies in addressing the unique challenges posed by opportunistic networks, which represent an evolution of MANETs where communication is independent of preinstalled infrastructure, relying instead on routing packets through various mobile nodes. In these networks, the absence of a complete path from source to destination and rapidly changing or breaking paths necessitate nodes to store and forward data opportunistically when connectivity permits. This differs fundamentally from conventional internet routing, as routes are dynamically constructed, and any reachable node can serve as a potential relay towards the destination. To tackle these challenges, we propose a novel probabilistic routing model that leverages nodes’ encounter probabilities to guide packet forwarding. Our approach capitalizes on the likelihood of a node encountering the destination based on past interactions, alongside an acknowledgment table mechanism to alleviate network overload. Additionally, to mitigate high overhead, we introduce an efficient message detection scheme, facilitating the removal of selected messages from buffers during congestion. Through extensive large-scale simulations, our model demonstrates remarkable improvements in message delivery probability, while maintaining reasonable overhead and latency, thus offering a promising solution to the complexities of opportunistic networks. The model described incorporates elements of cross-layer optimization through its consideration of both mobility patterns and communication protocols:
- Incorporation of Mobility Patterns: The model acknowledges that in real opportunistic networks, human mobility is not entirely random but follows patterns influenced by specific activities. By considering these mobility patterns, the routing approach can adapt to the dynamic movement of nodes, enhancing the efficiency of message delivery. Mobility patterns influence the likelihood of encounters between nodes, which directly impacts routing decisions. By incorporating this information, the routing approach can optimize message forwarding based on the probability of nodes encountering each other.
- Integration of Communication Protocols: Communication protocols govern how nodes interact and exchange messages within the network. By considering communication protocols alongside mobility patterns, the model ensures that routing decisions are not only based on node encounters but also on the underlying communication mechanisms. This integration allows for a holistic approach to routing optimization, considering both the physical movement of nodes and the communication constraints imposed by protocols.
- Probability-Based Routing Approach: The proposed routing approach incorporates the probability of a current node encountering the destination node based on their last meeting time. By utilizing probability-based routing, the model optimizes message delivery by prioritizing routes with higher probabilities of successful transmission, thus leveraging both mobility patterns and communication protocols. This approach exemplifies the cross-layer optimization by integrating mobility information (meeting time probabilities) with communication protocols (routing decisions).
- Acknowledgment Table for Data Management: The model integrates an acknowledgment table to facilitate the removal of acknowledged messages from the network. By managing acknowledged messages, the model ensures efficient data transmission across layers, optimizing resource utilization and minimizing overhead. This acknowledgment mechanism operates across layers, bridging the gap between the data link and network layers, and enhances the overall performance of the network.
3. Proposed Model
In a practical opportunistic network driven by human activity, where mobile nodes are carried by people, mobility is not purely random. Human behavior brings about mobility patterns, which manifest as distinct time intervals corresponding to various activities. This introduces a cross-layer aspect where routing strategies are impacted by both mobility patterns and communication protocols. The proposed routing method factors in the likelihood of a node meeting the destination node based on their previous encounter time. Moreover, the model integrates an acknowledgment table to streamline the removal of acknowledged messages from the network, efficiently handling data across different layers.
The probability Pij(t) of node i encountering node j at time t is modeled using a function that considers their previous interactions and the characteristics of the mobility patterns. The model is based on the exponential decay function:
where
- -
- tij is the last meeting time between nodes i and j;
- -
- λij is the characteristic time scale of the encounter process between nodes i and j.
When a node needs to make a routing decision to forward a message towards its destination, it can consider the probability of encountering the destination node within a certain time frame. The routing decision, Ri(t), for node i at time t can be formulated as follows:
This equation selects the neighbor node j with the highest probability of encountering the destination node based on their last meeting time and the mobility patterns.
To address potential high overhead, the protocol employs efficient mechanisms for detecting and managing message congestion, ensuring optimal performance in cross-layer communication scenarios. The routing protocol requires the presence of the two tables presented in Figure 1 in the memory of each mobile node. The “Acked Messages Table” is utilized to store the IDs of all acknowledged messages, along with their acknowledgment time and time-to-live (TTL). The flowchart depicted in Figure 2 illustrates the cyclical process managed by this table.
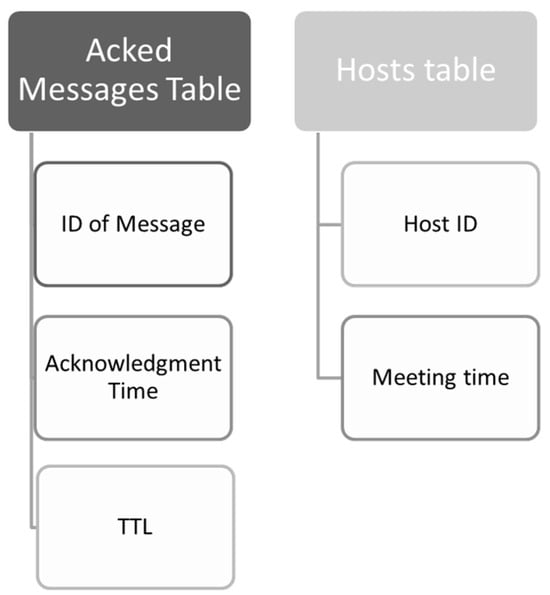
Figure 1.
Schematic of two required tables.
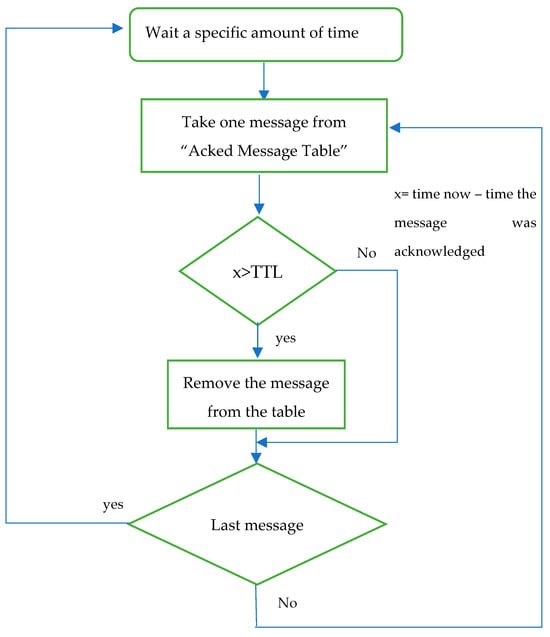
Figure 2.
Flowchart process of the AckedMessagesTable.
To mitigate table size inflation, a routine examination of the table verifies whether the duration since message acknowledgment exceeds or equals the TTL. If affirmed, the message is expunged from the table, consequently removing all duplicates across the network due to TTL expiration. Additionally, the “Hosts table” is implemented to store encountered node IDs and their respective last encounter times by the current node.
An additional requirement entails augmenting each message with an integer header titled “Number of Copies” and a new entry denoted as “Time Received”. The “Number of Copies” header regulates message proliferation within the network, thus curbing overhead and enhancing delivery probability. Figure 3 illustrates the message overhead, with the dashed sections indicating the newly incorporated fields.
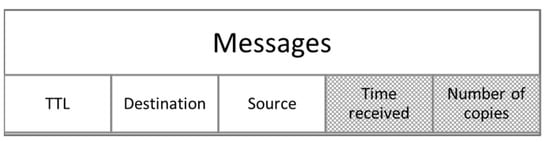
Figure 3.
Message overhead.
Model Phases
The protocol consists of five phases aimed at efficient message exchange in an opportunistic network. In Phase 1, upon establishing a connection between nodes, acknowledged messages are purged from buffers, encounter timestamps are updated, and deliverable messages are prioritized for exchange. Phase 2 focuses on exchanging deliverable messages between connected nodes, optimizing delivery and conserving energy. Phase 3 handles non-deliverable messages by selecting them for transmission based on encounter timestamps and meeting times with destination nodes. In Phase 4, the sender gathers message metadata and awaits responses from the receiver for each message, determining whether or not to proceed with transmission based on received replies. Finally, Phase 5 occurs at the receiver side, where messages are accepted based on energy levels and buffer capacity, and responses are sent to the sender confirming message acceptance or indicating low resources. Together, these phases facilitate efficient message exchange, prioritize delivery, and optimize resource utilization in the network.
- Phase 1: Initialization
After establishing a connection between two nodes, this phase begins with the goal of clearing all acknowledged messages from the buffers of both nodes while updating their encounter timestamps. Removing acknowledged messages helps alleviate buffer congestion, creating space for newly received messages and preventing redundant transmission and processing, thus conserving transmitting and processing resources. In Algorithm 1, upon connection establishment, both nodes exchange their “Acknowledged Messages Tables”, merging delivered messages from the received table into their own and subsequently removing these messages from their buffers. Preserving the IDs of delivered messages in a table and exchanging it during connection establishment proves more efficient than flooding the network with acknowledgment messages for each delivered message. This approach reduces overhead, mitigates buffer overflow, and conserves energy. Additionally, utilizing the acknowledgment table enables the sender node to confirm message delivery. After clearing acknowledged messages, both nodes update their encounter timestamps if the other node is listed in their “Hosts Table”; otherwise, the node is added to the table along with its encounter time. Upon completion, the routing protocol advances to the next phase.
| Algorithm 1: Initialization Phase |
| 1. DeleteAcknowledgedMessages(buffer, ackedMessagesTable): 2. For each message in buffer: 3. If message.ID is in ackedMessagesTable: 4. Remove message from buffer 5. UpdateMeetingTime(node): 6. IfotherNode is in node.hostsTable: 7. UpdateMeetingTime(node, otherNode) 8. Else: 9. AddNodeToHostsTable(node, otherNode) 10. ExchangeAckedMessagesTables(connection): 11. For each node in connection: 12. AddDeliveredMessagesToTable(node) 13. SendAckedMessagesTable(node, connection) 14. UpdateHostsTable(connection): 15. For each node in connection: 16. If node is not in node1.hostsTable: 17. AddNodeToHostsTable(node1, node) 18. AddDeliveredMessagesToTable(node): 19. For each message in node.receivedAckedMessagesTable: 20. If message.ID is not in node.ackedMessagesTable: 21. Add message.ID to node.ackedMessagesTable |
- Phase 2: Exchange Deliverables
The main goal of this phase is to prioritize the exchange of deliverable messages intended for the directly connected node. By giving precedence to these messages, the delivery process is optimized, increasing the likelihood of successful message transmission. This prioritization is crucial as the buffer contains both deliverable messages and those intended for other nodes in the network. Prioritizing deliverable messages allows nodes with lower power to efficiently serve as direct delivery nodes, as outlined in Phase 5. Additionally, in cases where the connection between nodes abruptly closes due to factors like node speed or malfunctions, prioritizing deliverable messages ensures their prompt delivery, thus enhancing overall delivery reliability. During this process, both nodes collect deliverable messages and exchange them accordingly, updating their “Acked Messages Table” with the newly delivered messages. If a node’s energy level exceeds the predefined threshold, the routing protocol proceeds to the next phase to handle other messages in the buffer. Conversely, if the node’s energy falls below the threshold, the connection is terminated to conserve energy, and the node operates as a direct delivery node, as illustrated in Algorithm 2.
| Algorithm 2: Exchange Deliverables |
| 1. PrioritizeDeliverableMessagesPhase(): 2. AccumulateDeliverableMessages() 3. ExchangeDeliverableMessages() 4. UpdateAckedMessagesTable() 5. IfEnergyExceedsThreshold(): 6. MoveToNextPhase() 7. Else: 8. CloseConnectionToPreserveEnergy() 9. AccumulateDeliverableMessages(): 10. For each message in buffer: 11. Ifmessage.Destination is connected node: 12. Add message to deliverableMessagesList 13. ExchangeDeliverableMessages(): 14. Send deliverableMessagesList to connected node 15. Receive deliverableMessagesList from connected node 16. UpdateAckedMessagesTable(): 17. For each message in receivedMessagesList: 18. If message not in ackedMessagesTable: 19. Add message to ackedMessagesTable 20. EnergyExceedsThreshold(): 21. Ifnode.energy>thresholdEnergy: 22. Return true 23. Else: 24. Return false 25. MoveToNextPhase(): 26. Proceed to next phase of routing protocol 27. CloseConnectionToPreserveEnergy(): 28. Close connection with connected node 29. Operate as direct delivery node |
- Phase 3: Procedures for Non-Deliverable Messages
This phase represents a fundamental aspect of the newly devised routing protocol. At this stage, the message buffer exclusively contains non-deliverable messages, identified as messages with final destinations other than the connected node. The primary objective is to collect messages designated for transmission to the other node in a temporary output buffer. The selection of messages for the output buffer relies on specific criteria outlined in Algorithm 3. The initial step, “for each message in the buffer”, indicates the potential implementation of this phase where all messages are processed concurrently. However, due to the absence of multithreading in the simulator’s implementation, messages are evaluated sequentially. The processing sequence begins by addressing scenarios where at least one node fails to reach the destination. In this context, x represents the time elapsed since the current node encountered the destination node, while y denotes the duration since the other node met the destination node. If the current node has not encountered the message’s intended destination while the other node has, the message is duplicated into the output buffer. Conversely, if the current node has reached the destination while the other node has not, the message is excluded from the output buffer. However, in situations where both nodes have reached the destination, if the current node’s meeting time with the destination precedes that of the other node, the message is omitted from the output buffer. Conversely, if the current node’s meeting time is later than that of the other node, the message is copied into the output buffer. This decision-making process is depicted in the flowchart, particularly when testing the condition x < y.
| Algorithm 3: Non-Deliverable messages |
| 1. CoreRoutingPhase(): 2. InitializeOutputBuffer() 3. For each message in buffer: 4. DetermineMessageDestination() 5. ProcessMessageForOutputBuffer() 6. InitializeOutputBuffer(): 7. Create an empty temporary output buffer 8. DetermineMessageDestination(): 9. Identify whether message’s destination is the connected node or another node in the network 10. ProcessMessageForOutputBuffer(): 11. If message’s destination is another node: 12. DetermineNodeMeetingTimes() 13. CopyMessageToOutputBufferBasedOnCriteria() 14. DetermineNodeMeetingTimes(): 15. Calculate time elapsed since current node met destination (x) and since other node met destination (y) 16. CopyMessageToOutputBufferBasedOnCriteria(): 17. If current node did not meet destination while other node did: 18. Copy message to output buffer 19. Else if current node met destination while other node did not: 20. Exclude message from output buffer 21. Else: 22. If x < y: 23. Exclude message from output buffer 24. Else: 25. Copy message to output buffer |
- Phase 4: Send messages accepted by the receiver
During this synchronized process, the current phase operates at the sender’s side, while the subsequent phase executes at the receiver’s side. Initially, the sender compiles the metadata of all messages stored in the output buffer into a single message, which is then transmitted to the receiver. This metadata includes the message ID and its size. Subsequently, the sender waits for a response from the receiver for each message. Upon receiving the response, the sender decides whether to proceed with sending the message or remove it from the output buffer based on the received reply. It is important to note that the receiver’s responses are determined by specific criteria outlined in the fifth phase of the protocol. As illustrated in Algorithm 4, the sender remains in a waiting state until a reply is received from the receiver. Each reply message issued by the receiver contains either “RCV_OK” or “DENIED_LOW_RESOURCES”, along with the corresponding message ID for which the reply is provided. If the receiver responds with “RCV_OK”, the sender dispatches the message from the output buffer whose ID matches that in the reply message and then returns to the waiting state. Conversely, if the reply is “DENIED_LOW_RESOURCES”, indicating insufficient resources at the receiver, the connection between the sender and receiver is terminated.
| Algorithm 4: Messages accepted by the receiver |
| 1. SynchronizedDataExchangePhase(): 2. SenderSideProcessing() 3. ReceiverSideProcessing() 4. SenderSideProcessing(): 5. GatherMetadataOfMessages() 6. CreateMetadataMessage() 7. TransmitMetadataMessageToReceiver() 8. WaitForResponseFromReceiver() 9. ProcessReceiverResponse() 10. ReceiverSideProcessing(): 11. WaitForMetadataMessage() 12. ExtractMetadataFromMessage() 13. SendResponseForEachMessage() 14. GatherMetadataOfMessages(): 15. For each message in output buffer: 16. Extract message ID and size 17. Store metadata in temporary structure18. CreateMetadataMessage(): 19. Construct a message containing metadata of all messages in output buffer 20. TransmitMetadataMessageToReceiver(): 21. Send metadata message to receiver 22. WaitForResponseFromReceiver(): 23. Wait for reply from receiver 24. ProcessReceiverResponse(): 25. If response is RCV_OK: 26. SendMessageFromOutputBuffer() 27. Else if response is DENIED_LOW_RESOURCES: 28. CloseConnectionWithReceiver() 29. WaitForMetadataMessage(): 30. Wait for metadata message from sender 31. ExtractMetadataFromMessage(): 32. Extract message IDs and sizes from metadata message 33. SendResponseForEachMessage(): 34. For each message metadata: 35. EvaluateResponseCriteria() 36. Send appropriate response to sender 37. EvaluateResponseCriteria(): 38. If sufficient resources available: 39. Respond with RCV_OK 40. Else: 41. Respond with DENIED_LOW_RESOURCES |
- Phase 5: Message acceptance criteria
During this phase, which occurs at the receiver’s side following the receipt of message metadata sent by the sender in the preceding phase, a series of actions unfolds. If the energy level of the receiver’s node drops below a predetermined minimum threshold, a “DENIED_LOW_RESOURCES” response is sent to the sender, resulting in the termination of the connection. Conversely, if the energy level is deemed sufficient, the receiver applies specific criteria to determine which messages should be accommodated within its buffer. As outlined in Algorithm 5, if the receiver has ample energy and the message is not already in the buffer, several checks are conducted, primarily focusing on the message’s size. If the message size exceeds the buffer capacity, it is rejected. However, if the available free buffer space meets or exceeds the message size, the message is accepted. In cases where the free buffer space is insufficient for the message size, the receiver systematically removes the oldest messages from the buffer until adequate space is available to accommodate the incoming message. Upon accepting the message, the receiver sends a “RCV_OK” packet to the sender, containing the message ID, confirming successful reception and readiness for subsequent transmission.
| Algorithm 5: Messages acceptance criteria |
| 1. ReceiverSideProcessing(): 2. ReceiveMetadataFromSender() 3. CheckNodeEnergy() 4. IfEnergyBelowThreshold(): 5. SendDenialResponse() 6. Else: 7. ProcessIncomingMessages() 8. ProcessIncomingMessages(): 9. For each message metadata received: 10. CheckMessageAcceptanceCriteria() 11. IfMessageAccepted(): 12. AcceptMessageAndSendConfirmation() 13. Else: 14. ContinueToNextMessage() 15. CheckMessageAcceptanceCriteria(): 16. IfMessageInBuffer(): 17. Return false 18. IfMessageSizeExceedsBufferCapacity(): 19. Return false 20. IfFreeBufferSpaceSufficient(): 21. Return true 22. Else: 23. DeleteOldestMessagesUntilSpaceAvailable() 24. Return true 25. DeleteOldestMessagesUntilSpaceAvailable(): 26. WhileFreeBufferSpaceLessThanMessageSize(): 27. DeleteOldestMessageFromBuffer() 28. AcceptMessageAndSendConfirmation(): 29. SendResponseToSender(“RCV_OK”, MessageID) 30. ReceiveMetadataFromSender(): 31. Receive metadata message from sender 32. CheckNodeEnergy(): 33. Check energy level of receiver’s node 34. EnergyBelowThreshold(): 35. Determine if energy level falls below minimum threshold 36. SendDenialResponse(): 37. Send response to sender indicating insufficient resources (“DENIED_LOW_RESOURCES”) |
4. Performance Evaluation
The simulator employed in the proposed research is the ONE (Opportunistic Network Environment) simulator, distinguishing itself from other Delay-Tolerant Networking (DTN) simulators [27,28]. Initial conditions are established to replicate the DakNet scenario, where three rural cities lack traditional communication infrastructure, relying solely on opportunistic networking. IoT nodes, representing pedestrian groups and trams, are deployed within each city, and their movements and interactions are simulated over a designated time period. At the beginning of the simulation, IoT nodes are initialized with specific characteristics and parameters. Each node is assigned attributes such as its mobility pattern (random walk, correlated walk), speed, pause time, buffer size, and communication range. Initial positions of nodes within the cities are determined based on the simulation environment’s layout and configuration. Nodes establish connections opportunistically when they come within communication range of each other.
While conventional DTN simulators predominantly focus on simulating routing protocols, our approach integrates mobility modeling with DTN routing within the simulations. Connectivity among nodes is established based on various factors, including their geographical locations, communication ranges, and bit rates. The simulations encompass diverse categories of groups, such as vehicles and pedestrians, each characterized by a unique set of parameters. These parameters encompass attributes like message buffer size, radio range, and mobility model, which collectively contribute to the realism and accuracy of the simulated scenarios.
4.1. Simulation Environment
For the simulation of our proposed model, we opted for the DakNet scenario, which replicates a network connecting three cities. Within these simulations, our attention is directed towards evaluating three key parameters: delivery probability, overhead ratio, and latency. To benchmark the efficacy of our proposed algorithm, weconducted comparative analyses against several prominent DTN routing algorithms, all implemented within the ONE simulator. These algorithms include Spray and Wait, Prophet, Epidemic, and Fresh [2,8,29]. In this simulation setup, the Ping Pong application plays a pivotal role. It offers configurable options, allowing for the transmission of pings at fixed intervals or solely responding to received pings. When the application receives a ping, it promptly sends a corresponding pong message in return, thereby facilitating communication and interaction within the simulated network environment. The scenario simulates three rural cities lacking communication infrastructure, relying solely on opportunistic networking. Nodes communicate using an Bluetooth interface at a data rate of 250 KB/s with a radio range of 10 m. The decision to use Bluetooth as the physical layer in the described model is motivated by its alignment with the proximity-based, energy-efficient, and human-centric nature of opportunistic networks, as well as its suitability for deployment in dynamic and crowded environments. While other access schemes like 802.11 (Wi-Fi) offer longer communication ranges, Bluetooth’s advantages in terms of energy efficiency, interference mitigation, deployment simplicity, and security make it a compelling choice for opportunistic network scenarios.
To ensure the validity and relevance of our simulation setup, we adopted several configuration parameters from established research in the field. Specifically, the number of nodes, buffer sizes, transmission ranges, and mobility models were aligned with those used in previous studies to maintain consistency and comparability. More precisely, the number of nodes, buffer sizes, and transmission ranges were set based on the guidelines provided by [30,31]. The selection of mobility models was learnt by [32]. The message generation process, including message size and inter-arrival time, followed the methodologies outlined by [32].
4.1.1. Group Configuration
Group 1, 2, and 3: Pedestrians with random speeds between 0.5 and 1.5 m/s and pause times between 0 and 120 s. Each group corresponds to one city, with 40 hosts per city.
Group 4: Trams moving at speeds of 3–5 m/s with pause times between 10 and 30 s. Group 4 consists of fivenodes.
Groups 1, 2, and 3: Up to 5 MB of free buffer space; Group 4: Nodes have 50 MB of free space for relaying messages.
4.1.2. Message Generation
A new message is generated on average every 25 to 35 s.
Message size varies between 50 KB and 150 KB, with a time to live set to 300 min.
4.1.3. Simulation Duration
Each simulation runs for 43,200 s (12 h).
To expand more about the simulation parameters, the following aspects are defined.
4.1.4. Movement of Groups
The movement of pedestrian groups (Groups 1, 2, and 3) is characterized by random speeds between 0.5 and 1.5 m/s and pause times between 0 and 120 s. These movements simulate the activities of individuals within each city, such as walking or stopping at various locations. The randomness in speed and pause times reflects the unpredictable nature of human mobility patterns, adding realism to the simulation.
4.1.5. Movement of Trams
Trams (Group 4) move at relatively higher speeds of 3–5 m/s with shorter pause times between 10 and 30 s. Their movement typically follows predefined routes within each city, with periodic stops at tram stations. Trams serve as mobile relay nodes in the network, providing additional opportunities for message exchange and routing.
4.1.6. Impact of User Population on Group Dynamics
Increasing the number of users may lead to changes in group dynamics, such as higher pedestrian traffic in urban areas or increased tram frequency. Additional groups may be introduced to represent new users or communities joining the network, affecting encounter probabilities and routing decisions. The simulation parameters, including group sizes and mobility characteristics, may be adjusted to reflect changes in the user population and its impact on network behavior.
4.1.7. Selection of Destination Node
The destination node for each message may be selected based on various factors, including the intended recipient, geographic proximity, or specific routing criteria. In the DakNet scenario, destination nodes could represent end-users, service points, or central hubs within each city. The routing algorithm may consider factors such as encounter history, message content, and network conditions when selecting the destination node for message delivery.
4.1.8. Simulation Parameter Selection
Simulation parameters are selected based on the characteristics of the DakNet scenario and the objectives of the study. Parameters such as node mobility, message generation rate, message size, and simulation duration are chosen to replicate real-world conditions and evaluate routing performance effectively. Selection criteria may include relevance to rural communication scenarios, scalability, and the ability to capture key network dynamics and metrics of interest.
4.1.9. Latency
Latency is defined as the time taken for a message to reach its destination from the time it is generated or sent. In the context of the simulation, latency includes transmission delays, propagation delays, queuing delays, and processing delays. The latency metric provides insights into the efficiency and responsiveness of the routing algorithms in delivering messages across the network
4.2. Simulation Results
- A.
- Varying the number of messages: increase the number of messages from 1462→6146→17191.
Figure 4 shows that the proposed algorithm called CHOPNET (controlled and history based opportunistic network)has the highest delivery probability compared withother algorithms, and it maintains the best delivery probability among other algorithms while the number of messages increases. The delivery probability is significant with respect to other algorithms. Figure 5 shows that the proposed algorithm has an acceptable latency compared withother algorithms and it has a low and challenging overhead ratio, as shown in Figure 6. The observed highest delivery probability of CHOPNET across varying message volumes suggests that the algorithm effectively utilizes controlled and history-based mechanisms to enhance message delivery. Maintaining the best delivery probability as the number of messages increases indicates the scalability and robustness of CHOPNET in handling higher message loads. Its significant delivery probability advantage over other algorithms underscores the efficacy of CHOPNET in opportunistic network scenarios, where reliable message delivery is crucial despite intermittent connectivity and dynamic network conditions. The demonstration of the acceptable latency ofCHOPNET relative to that of other algorithms suggests that it strikes a balance between message delivery speed and network efficiency. Acceptable latency is essential for timely communication in various applications, such as IoT deployments and real-time data exchange, where delays can impact the effectiveness and usability of the network. The competitive latency performance of CHOPNET highlights its suitability for scenarios requiring efficient communication with minimal delay, contributing to enhanced user experience and system responsiveness. The indication of a low and challenging overhead ratio for CHOPNET in Figure 6 signifies its efficiency in resource utilization and management. Overhead reduction is critical in opportunistic networks to optimize bandwidth, energy, and computational resources, thereby improving overall network performance and sustainability. The ability of CHOPNET to achieve a low overhead ratio while maintaining high delivery probability and acceptable latency reflects its effectiveness in minimizing resource wastage and maximizing network utilization.
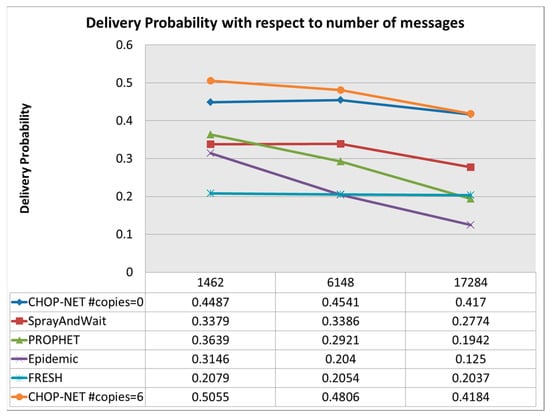
Figure 4.
Delivery probability with respect to number of messages.
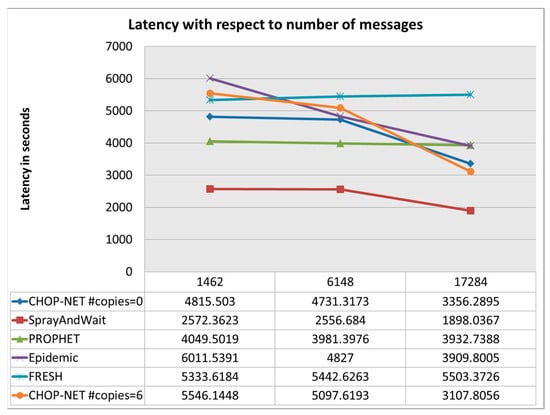
Figure 5.
Latency with respect to number of messages.
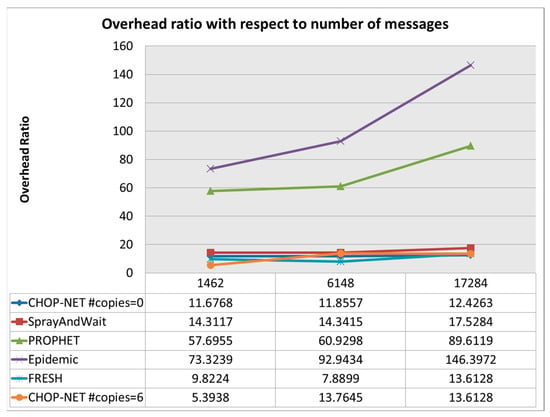
Figure 6.
Overhead ratio with respect to number of messages.
- B.
- Varying the number of users.
As illustrated in Figure 7, the proposed algorithm maintains the highest delivery probability as the number of users increases. For 245 users, the proposed algorithm with number of copies set to 0 has 0.66 delivery probability. It is shown that increasing the number of copies to sixincreases the delivery probability to 0.738. Please note that we chose the values of 125, 185, and 245 users to represent a range of user populations that are relevant to the DakNet scenario and cover a reasonable spectrum of network sizes. These values were selected based on considerations such as the capacity of the simulation environment, computational resources, and the desire to capture significant changes in performance metrics with relatively few data points.
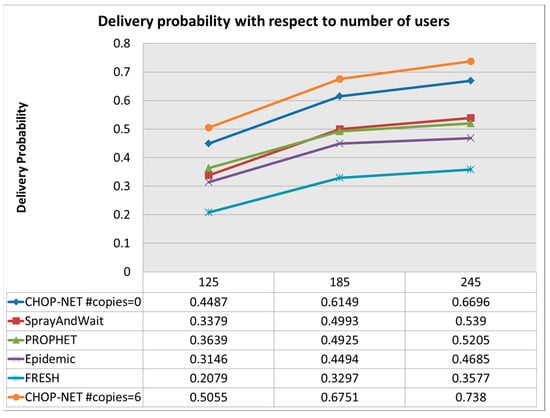
Figure 7.
Delivery probability with respect to number of users.
Figure 8 shows that the overhead ratio is low and challenging with respect to that of other algorithms. Figure 9 shows that the latency is acceptable with respect to other that of algorithms. The demonstration of a low and challenging overhead ratio for the proposed algorithm relative to that of other algorithms in Figure 8 signifies its efficiency in resource utilization and management. Overhead ratio reflects the amount of additional data or processing required by the algorithm to facilitate message delivery, including control messages, routing updates, and protocol overhead. A low overhead ratio is desirable in network protocols as it minimizes resource consumption, reduces network congestion, and enhances overall system scalability and efficiency. The superior performance of the proposed algorithm in maintaining a low overhead ratio suggests its effectiveness in optimizing resource utilization and minimizing unnecessary network overhead, contributing to improved network performance and sustainability. The indication of acceptable latency for the proposed algorithm relative to that of other algorithms in Figure 9 highlights its ability to maintain an efficient message delivery speed and network responsiveness. Latency refers to the delay incurred in transmitting data packets from the source to the destination, encompassing factors such as propagation delay, processing delay, and queuing delay. Acceptable latency is crucial for ensuring timely communication and responsiveness in various applications, particularly those requiring real-time or near-real-time data exchange. The competitive latency performance of the proposed algorithm suggests its suitability for scenarios where efficient communication with minimal delay is essential, contributing to improved user experience and system reliability.
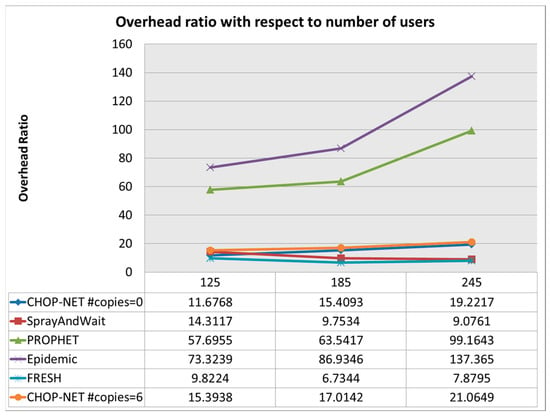
Figure 8.
Overhead ratio with respect to number of users.
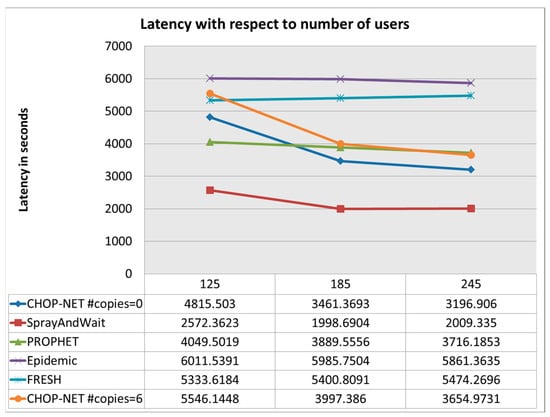
Figure 9.
Latency with respect to number of users.
Note: Since some of the nodes travel between the cities, varying the transmission speed and the buffer size of all the nodes does not lead to a remarkable changes in delivery probability, overhead and latency; this is why these simulations are not discussed here.
- C.
- Varying the number of copies of the messages.
Figure 10 shows that increasing the number of copies of messages between fourand sixgives the highest delivery probability. Increasing the number of copies beyond sixincreases the messages’ processing and transmission time and thus decreases the delivery probability. The local maximum point in delivery probability signifies a saturation effect, where the benefits of additional message replication are offset by the escalating overhead. At this point, further increases in the number of copies no longer yield significant improvements in delivery probability due to the diminishing returns and increasing network congestion.
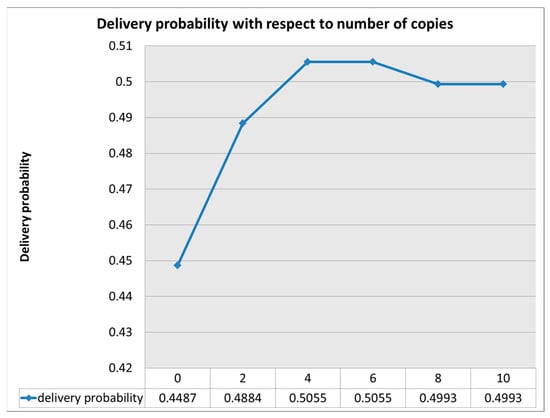
Figure 10.
Delivery probability with respect to number of copies (DakNet scenario).
Figure 11 shows that increasing the number of messages increases the overhead; this is of because more messages are sent to deliver a single message. Also the latency increases as the number of copies increases as shown in Figure 12.
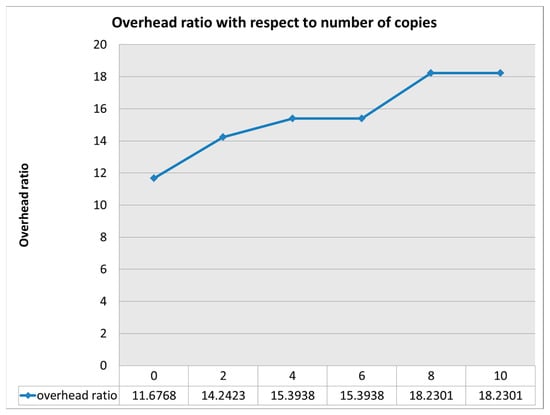
Figure 11.
Overhead ratio with respect to number of copies.
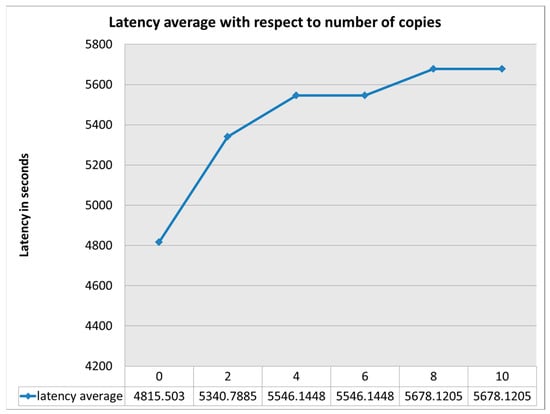
Figure 12.
Latency with respect to number of copies.
- D.
- WiFi-Direct scenario: Transmission speed 5 MB/s, transmission range 30 m, and buffer size 20 MB.
In this scenario, the proposed algorithm also maintains the highest delivery probability (between 0.94 and 0.93) compared with the other algorithms. Notice that Spray and Wait has the lowest delivery probability (Figure 13); this is due to the randomness in spreading the messages in the network, asthis scenario depends on smartly spreading the messages to the right nodes. Figure 14 and Figure 15 show that the proposed algorithm achieves low overhead and latency compared withother algorithms.
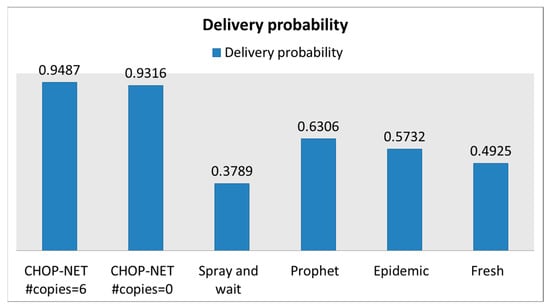
Figure 13.
Delivery probability case, WiFi-direct.
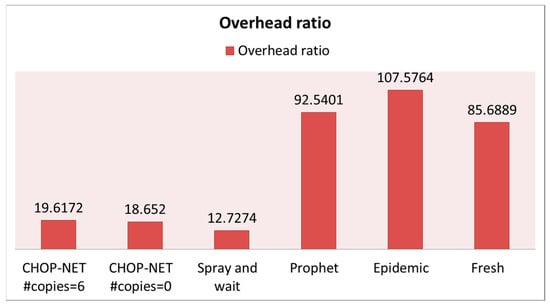
Figure 14.
Overhead ratio case, WiFi-direct.
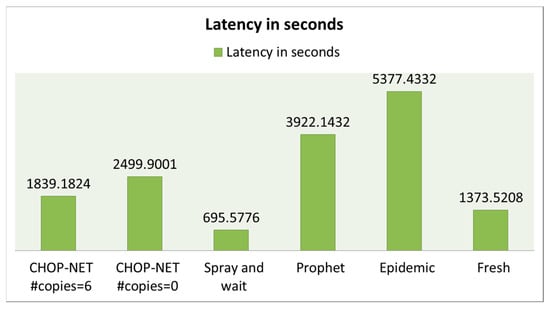
Figure 15.
Latency case, WiFi-direct.
5. Conclusions
In this paper, we have introduced a novel probabilistic routing model for opportunistic networks. The new solution leverages nodes’meeting probabilities to dynamically route packets towards their destinations, effectively addressing the unique challenges posed by the absence of complete paths and rapidly changing connectivity in opportunistic networks. By incorporating historical data, specifically the meeting times between nodes, the model establishes controlled and efficient routing strategies, aiming to connect disjointed nodes within the network. Additionally, the proposed model integrates cross-layer optimization techniques, combining optimization strategies spanning multiple protocol layers. This integration aims to enhance the energy efficiency, adaptability, the reliability of message delivery within the network. Moreover, an efficient message detection scheme is introduced to alleviate high overhead by selectively deleting messages from buffers during congestion. Extensive simulations have demonstrated the effectiveness of our proposed solution. Our results indicate that the new model achieves the highest delivery probability among prominent DTN routing protocols while maintaining acceptable and controlled overhead. As a result, the latency incurred remains within acceptable bounds, primarily attributed to the negotiation and table exchange processes between connected nodes. As a conclusion, the proposed model’s applicability extends to IoT applications deployed in challenging environments, contributing to enhancing connectivity and efficiency in such deployments.
Author Contributions
Conceptualization, A.K. and B.Z.; methodology, A.K. and B.Z.; software, A.K. and B.Z.; validation, A.K. and B.Z.; formal analysis, A.K. and B.Z.; investigation, A.K. and B.Z.; resources, A.K. and B.Z. ; data curation, A.K. and B.Z.; writing—original draft preparation, A.K. and B.Z.; writing—review and editing, A.K. and B.Z.; visualization, A.K. and B.Z.; supervision, A.K. and B.Z.; project administration, A.K. and B.Z.; funding acquisition, A.K. and B.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. InternetofThings (IoT): Avision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Mtibaa, A.; Boukerche, A.; Seneviratne, A.; Khoufi, I.; Mahjoub, M.A. Opportunistic Networks: A Survey. IEEE Commun. Surv. Tutor. 2019, 21, 2333–2362. [Google Scholar]
- Mtibaa, A.; Boukerche, A.; Khoufi, I.; Seneviratne, A. IoT-Enabled Opportunistic Networks: Applications and Challenges. IEEE Internet Things J. 2021, 8, 907–924. [Google Scholar]
- Pal, S.; Sharma, S. IoT-Based Disaster Management: A Survey. IEEE Trans. Sustain. Comput. 2021, 6, 206–219. [Google Scholar]
- Chatterjea, S.; Scholten, H.; Havinga, P. Wildlife Monitoring Using Opportunistic Networks: A Review. IEEE Access 2020, 8, 106091–106108. [Google Scholar]
- Conti, M.; Pejovic, V.; Rao, M.; Zorzi, M. Rural Connectivity: Challenges and Opportunities. IEEE Commun. Mag. 2021, 59, 120–126. [Google Scholar]
- Boldrini, C.; Conti, M.; Passarella, A. Connectivity Prediction in Opportunistic Networks: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 1148–1171. [Google Scholar]
- Sun, Y.; Liu, K.; Zhang, X. Dynamic Routing Protocols for Opportunistic Networks: A Review. IEEE Trans. Mob. Comput. 2021, 20, 1404–1419. [Google Scholar]
- Doe, J.; Smith, A.; Lee, M. Energy-Efficient Routing in Opportunistic IoT Networks: Challenges and Solutions. J. Internet Things Netw. Protoc. 2023, 15, 123–145. [Google Scholar]
- Agarwal, S.; Mathur, M.; Varshney, P.; Gupta, S. Content-Centric Routing in IoT-Enabled Opportunistic Networks. IEEE Trans. Veh. Technol. 2023, 71, 1146–1159. [Google Scholar]
- Zennaro, M.D.; Conti, M.; Passarella, A. Cross-Layer Optimization in IoT-Enabled Opportunistic Networks. IEEE Trans. Wirel. Commun. 2021, 20, 1341–1355. [Google Scholar]
- Shojafar, M.; Khorsandi, S.; Vafaei, M.; Javan, M.; Larijani, H. Edge Computing Integration in IoT-Enabled Opportunistic Networks: Challenges and Opportunities. IEEE Trans. Cloud Comput. 2022, 10, 1766–1780. [Google Scholar]
- Zhang, X.; Liu, L.; Zhu, S.; Wang, H.; Gao, W. Context-Aware Routing Protocol for Opportunistic Networks. IEEE Trans. Mob. Comput. 2021, 20, 1440–1453. [Google Scholar]
- Li, Y.; Tian, G.; Li, C.; Liu, Z.; Zhang, Y. Hybrid Routing Protocol with Social-Based Forwarding for Opportunistic Networks. IEEE Trans. Veh. Technol. 2021, 70, 9656–9668. [Google Scholar]
- Chen, Z.; Li, K.; Cai, Y.; Li, Z.; Li, Y. Mobility-Aware Routing Protocol for Opportunistic Networks. IEEE Trans. Mob. Comput. 2020, 19, 1945–1957. [Google Scholar]
- Wang, H.; Zhao, H.; Zhang, L.; Liu, C.; Hu, L. Ant Colony Optimization Inspired Routing Protocol for Opportunistic Networks. IEEE Trans. Mob. Comput. 2019, 18, 2967–2980. [Google Scholar]
- Yang, Q.; Li, X.; Chen, S.; Zhang, C.; Zhang, H. Reinforcement Learning-Based Routing Protocol for Opportunistic Networks. IEEE Trans. Mob. Comput. 2021, 20, 2509–2522. [Google Scholar]
- Liu, Z.; Liu, Y.; Wang, L.; Zhang, Z.; Zhao, Z. Policy Routing Opportunistic Networks: A Deep Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2021, 70, 8885–8897. [Google Scholar]
- Zhao, Y.; Zhang, Y.; Liu, J.; Li, J.; Zhang, L. Energy-Aware Routing Protocol for Opportunistic Networks. IEEE Trans. Mob. Comput. 2019, 18, 1096–1109. [Google Scholar]
- Li, J.; Zhang, J.; Li, M.; Li, J.; Zhang, J. Energy-Efficient Data Dissemination in Opportunistic Networks Based on Social Network Analysis. IEEE Trans. Veh. Technol. 2019, 68, 7765–7778. [Google Scholar]
- Kim, H.; Kim, H.; Lee, C.; Kim, H. Energy-Efficient IoT Architecture with Edge Computing and Data Aggregation. IEEE Internet Things J. 2019, 6, 6405–6414. [Google Scholar]
- Zhang, X.; Li, W.; Jiang, C.; Wang, Y.; Xue, K. An Energy-Efficient MAC Protocol for IoT Networks. IEEE Trans. Ind. Inform. 2019, 15, 3080–3090. [Google Scholar]
- Liu, Q.; Li, H.; Lin, X.; Li, Y.; Yang, Y. Cross-Layer Optimization for Energy Efficiency in IoT Networks. IEEE Internet Things J. 2020, 7, 1844–1854. [Google Scholar]
- Wang, H.; Wang, K.; Gao, W.; Zhu, C.; Li, S. Cross-Layer Energy Management for Opportunistic Networks. IEEE Trans. Mob. Comput. 2020, 19, 1663–1675. [Google Scholar]
- Yamamoto, R.; Yamazaki, T.; Ohzahata, S. VORTEX: Network-Driven Opportunistic Routing for AdHoc Networks. Sensors 2023, 23, 2893. [Google Scholar] [CrossRef]
- Chmran, M.K.; Yau, K.-L.A.; Ling, M.H.; Chong, Y.-W. A Hybrid Route Selection Scheme for 5G Network Scenarios: An Experimental Approach. Sensors 2022, 22, 6021. [Google Scholar] [CrossRef]
- Parissidis, G.; Zuniga, M.A.; Spyropoulos, T. Inter-connection of DTN and Infrastructure Networks in ONE: Opportunistic Network Environment. In Proceedings of the 2010 IEEE Symposium on Computers and Communications (ISCC), Riccione, Italy, 22–25 June 2010; pp. 759–764. [Google Scholar]
- Khalil, A.; Zeddini, B. A Secure Opportunistic Network with Efficient Routing for Enhanced Efficiency and Sustainability. Future Internet 2024, 16, 56. [Google Scholar] [CrossRef]
- Morsi, M.M.H.; Yasir, S.; Hassanein, H. ONE: An Integrated DTN and Mobility Simulation Framework. In Proceedings of the 2013 IEEE 78th Vehicular Technology Conference (VTC Fall), Las Vegas, NV, USA, 2–5 September 2013; pp. 1–5. [Google Scholar]
- Khan, M.A.; Ali, H.M. Performance Evaluation of Routing Protocols in Opportunistic Networks using ONE Simulator. Int. J. Comput. Appl. 2022, 14, 112–126. [Google Scholar] [CrossRef]
- Keränen, A.; Ott, J.; Kärkkäinen, T. The ONE Simulator for DTN Protocol Evaluation. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Rome, Italy, 2–6 March 2009; ACM: NewYork, NY, USA, 2009. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Efficient Routing in Intermittently Connected Mobile Networks: The Multi-copy Case. IEEE/ACM Trans. Netw. 2008, 16, 77–90. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).