1. Introduction
The metaverse is an emerging technology that represents the future iteration of the Internet, where the boundary between the virtual and real worlds becomes increasingly indistinct. It allows users to carry out real-world tasks virtually. With its foundation in the field of human-computer interaction, it has extended into a complex network of virtual environments, with a focus on business, education, and healthcare. In the context of education, the metaverse provides a virtual learning environment where students may engage in innovative educational scenarios and cooperative learning. Additionally, it benefits businesses by opening new channels for interaction, communication, and trade. This innovative concept introduces unique features like avatars, persistence, and continuous connectivity within virtual spaces without the need for physical, real-world movement. With applications spanning a wide range of fields, including social interactions and education, the metaverse has the potential to transform digital interactions completely. It is made possible by 3D virtual worlds and augmented reality. The metaverse is generating excitement despite being in its early phases of development because of its vast potential. It promises to completely transform the way we connect with technology and with one another, whether it is for social interactions, work, education, or gaming. Its uses will probably grow more varied and complex as it develops, and the metaverse will play a significant role in our digital future.
As with any new technology, there are also unknown risks and challenges. In the metaverse, numerous cybercrimes pose significant concerns, including virtual property theft, where cybercriminals steal virtual assets acquired through gaming or purchases, often through hacking, phishing, or deceptive apps. Identity theft is another widespread issue, with cybercriminals using stolen login credentials or personal data to impersonate users or create fraudulent accounts [
1]. Furthermore, the virtual world presents an ideal environment for cybercrime perpetuation. For example, phishing, cyberbullying, and online harassment have been reported in the literature [
1,
2]. These crime types necessitate the need for security capacity such as event blocking and reporting, as well as user education. Other common forms of crime within the metaverse include financial fraud, cyberextortion, and impersonation. Financial fraud encompasses a range of fraudulent online activities, such as phishing scams and credit card fraud, to obtain money or sensitive financial information. Cyberextortion crimes, which frequently employ strategies like ransomware assaults or distributed denial-of-service (DDoS) attacks, entail utilizing digital methods to extort money or assets from people or organizations. These cybercrimes highlight the need for robust cybersecurity measures in the metaverse [
2].
Individuals and organizations must work together to reduce the danger of cybercrime in the metaverse. To begin, users must be educated about cybercrime threats, emphasizing the significance of strong passwords, multi-factor authentication, and caution while downloading virtual products and services. To protect users and their data, organizations must establish robust security measures such as strong authentication systems, data encryption, and thorough surveillance for suspicious activity. Furthermore, combating metaverse cybercrime requires a collective strategy. To combat this growing threat, law enforcement experts and business stakeholders should work together. Sharing intelligence, creating new investigation tools and procedures adapted to the metaverse, and prosecuting cybercriminals are all critical steps in establishing a secure virtual environment.
Different data sources and formats present unique obstacles for digital forensics in the metaverse when compared to traditional digital forensics (as summarized in
Table 1). The decentralized nature of metaverse data, which are spread over a network of servers and devices, makes it more difficult to gather and preserve evidence than in traditional systems. Furthermore, the metaverse produces new kinds of data, such as chat logs, motion capture data, and 3D models, which calls for the creation of specific analytic tools and methods. Another significant difference is jurisdictional concerns. Crimes that happen in the metaverse could cross geographical boundaries, creating difficult moral and legal dilemmas over which jurisdiction has the right to conduct investigations. Furthermore, privacy considerations are paramount in the metaverse, where users may disclose sensitive personal information. Balancing the need for digital forensics investigations with user privacy protection is a crucial aspect that investigators must navigate. Forensic investigators face significant obstacles due to the volatility of data within the metaverse. The data constantly change as users interact with the virtual world, making the collection and preservation of evidence a dynamic process. Furthermore, the continuous evolution of the metaverse adds complexity by evolving data formats and protocols, creating difficulties in establishing dependable tools and techniques for analysis. As the metaverse expands, it is more important than ever to develop new innovative techniques for digital forensics. By tackling the difficulties brought on by decentralized data, changing formats, complex jurisdictional, and the constantly changing nature of user interactions in this new digital environment, these strategies seek to maintain the safety and security of the virtual world.
The current approaches to forensic investigation in the metaverse involve a comprehensive framework consisting of distinct phases. Data collection is a common phase. It involves the identification of possible sources of evidence and the gathering of information from users, services, and metaverse platform domains. Case-specific forensic data are extracted during the subsequent inspection and retrieval phase, overcoming any challenges posed by encryption, encoding, or compression. The analysis phase is similar to traditional forensic procedures in that it involves examining artifacts to make case-specific judgments that may be adjusted according to the specifics of the meta-crime. Further information is obtained through correlation studies, and conclusions are provided in the reporting phase, considering the difficulty of transforming 3D data into a 2D format that is acceptable to courts [
3]. As shown in
Table 1, the metaverse offers complexity in jurisdictional claims, as well as high volatility of digital instances. These inherent characteristics present a rather complicated investigation process that the traditional forensic framework cannot address.
A novel forensic framework is, therefore, needed to guide investigators in investigating cybercrime in the metaverse. This framework should provide investigators with a structured and systematic approach for collecting and analyzing evidence in the metaverse. The framework should also be flexible enough to adapt to the evolving nature of cybercrime in the metaverse. A forensic framework for investigating cybercrime in the metaverse will help to improve the ability of law enforcement to investigate and prosecute cybercrime in the metaverse. It will also help to protect victims of cybercrime and deter cybercrime in the metaverse. There are currently not many forensic frameworks available to investigate cybercrimes in the metaverse. This is a problem because it can make it difficult for law enforcement and investigators to gather evidence and track down attackers. This paper proposes a new forensic framework for investigating cybercrime in the metaverse. The forensic framework is designed to be flexible and adaptable to different scenarios of attacks on a variety of metaverse platforms and devices.
1.1. Problem Background
The fast rise and adoption of metaverse platforms has created a new digital ecosystem with its own set of problems and risks. As this virtual world grows more interconnected in our daily lives and business activities, the requirement for an efficient structure for managing and responding to metaverse incidents becomes crucial. Incidents in the metaverse cover a wide range of concerns, including digital crimes, data breaches, virtual asset theft, and security breaches. These crimes might have profound effects, impacting not just individual users but also businesses and organizations working in the metaverse.
Creating a complete framework for metaverse incidents is critical and offers various advantages. These benefits include more effective incident response, more clarity in dealing with legal and compliance aspects, enhanced user protection, more remarkable economic growth, and the formation of best practices within the metaverse community. To summarize, developing such a framework is critical for addressing growing difficulties and ensuring the metaverse’s secure and sustainable development. This paper aims to develop a comprehensive forensic framework for investigating cybercrime in the metaverse, addressing the unique challenges presented by virtual reality environments, and enhancing digital forensic investigators’ capabilities as well as assisting them in effectively combating cybercrime within virtual reality environments. This study, therefore, contributes to the literature in the following ways:
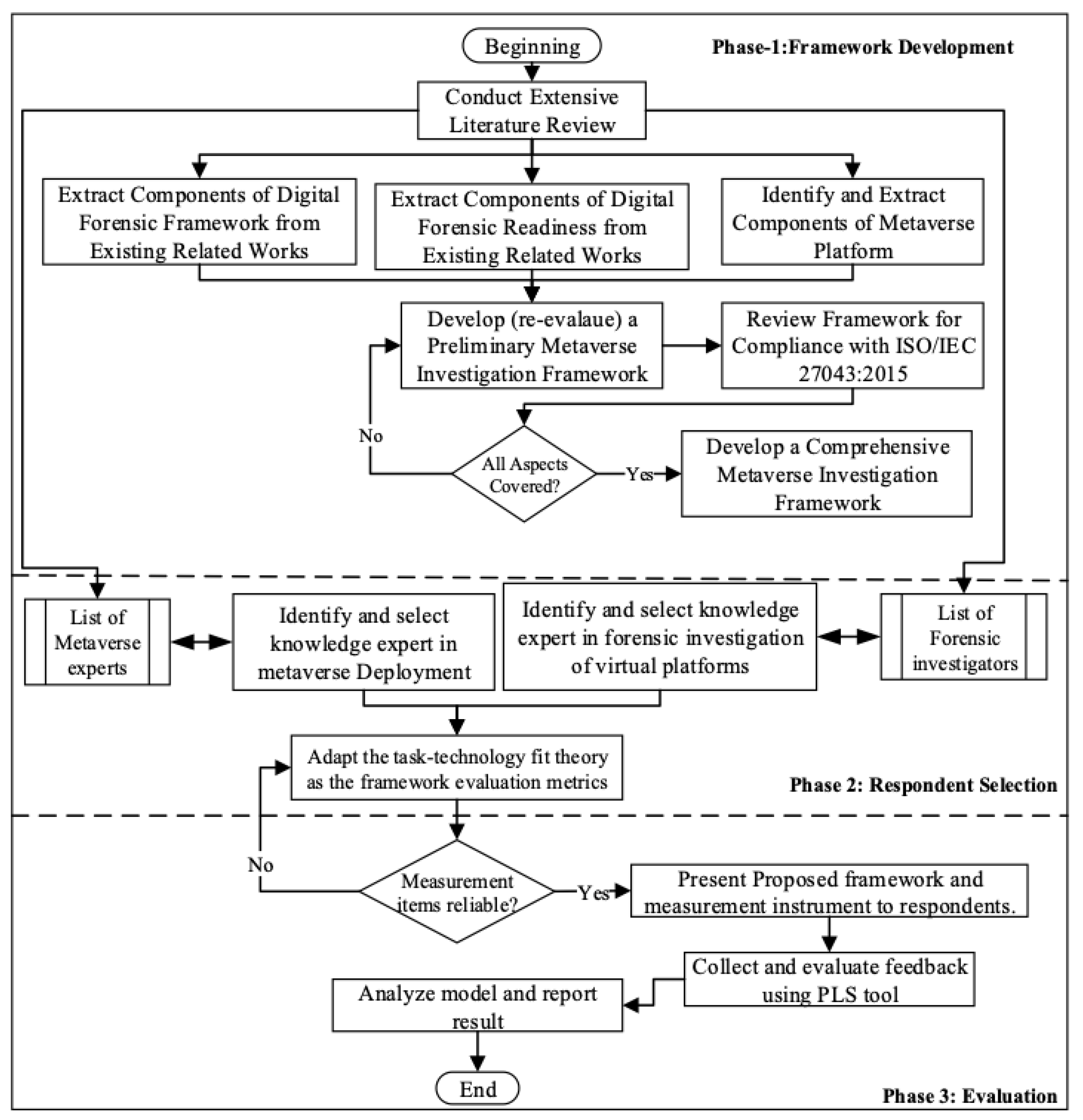
Framework Development: Creation of an organized forensic framework customized to the metaverse, including criteria for digital evidence identification, preservation, and analysis;
Survey Design and Distribution: Design and distribution of a survey to digital forensic investigators to gather their expert insight, opinion, and recommendations on the built metaverse forensic framework;
Data Collection: Gathering of data, opinions, and expertise from digital forensic investigators on the proposed framework’s practicability, relevance, and potential improvements;
Analysis of Survey Results: Analysis of the survey results to gain an understanding of the challenges and requirements in metaverse cybercrime investigations.
Framework Refinement: Refinement of the forensic framework based on the survey findings and analysis, ensuring that the metaverse forensic framework matches the requirements and expectations of digital forensic specialists.
1.2. Related Works and Theoretical Underpinning
This section provides insight into some related works and the theoretical justification for this study, which is further structured as follows:
In
Section 1.2.1, headed ’Cybercrime in Virtual world,’ this study looks at cybercrime in virtual environments. This section provides information about the nature of these digital crimes, how they work, the vulnerabilities they exploit, and the research-based solutions developed to address them;
Section 1.2.2, titled ’Network Forensic Investigation Techniques,’ looks into several approaches used for researching network-based occurrences, emphasizing their importance in dealing with cyber threats;
Section 1.2.3 of this manuscript concentrates on the ’Role of ISO Standards in Network Investigation,’ with a detailed comparison of ISO 27037 [
4] and ISO 27043 [
5]. This section emphasizes the unique properties of these standards as well as their importance in network investigations and forensic readiness;
Section 1.2.4, ’Metaverse Framework Development,’ details the early efforts to create a framework for metaverse digital forensic investigations. It emphasizes the issues of this virtual world, highlighting the necessity for specific frameworks and approaches;
Section 1.2.5, ’Comparison Between Framework Evaluation Approaches’, investigates the existing approaches for assessing forensic investigative frameworks. This research investigates the advantages and disadvantages of several assessment methods, providing valuable insights for improving the effectiveness and efficiency of forensic investigations.
1.2.1. Cybercrime in the Virtual World
Unauthorized acquisition or theft of an individual’s or organization’s informational assets is referred to as virtual property theft. This includes illegally purchasing products from social media applications, online accounts, bitcoin, digital real estate, and intellectual property from people or businesses in the virtual world. This may happen in several ways. Still, those that are most common include using vulnerabilities in online applications, gaining access to user accounts without authorization, and tampering with in-app features to obtain unfair advantages. This crime takes advantage of vulnerabilities in the virtual platforms’ security infrastructure, as well as users’ trust in the safety of these settings. To address this risk, researchers have explored many mechanisms, such as blockchain technology. They are using multiple solutions to minimize it, such as hardening apps, using strong usernames/passwords and multifactor authentication (MFA), and providing transparent and secure ownership records for virtual assets [
1].
In the metaverse, cyberbullying refers to the intentional and persistent use of online gaming consoles, social media, and virtual environments to harass, threaten, or harm others. This type of bullying takes advantage of people’s vulnerability in online environments where an in-person connection is absent, allowing offenders to engage in harmful behavior and remain anonymous. Cyberbullying is a broad term that includes a variety of behaviors [
6], many of which take place online and involve hate speech, exclusion, impersonation, spreading false information, and direct harassment. It makes use of the long-lasting effects of digital information and the possibility of a large audience causing emotional distress and harm to victims. Various tactics, such as education and awareness campaigns, social media campaigns, in-game events, policies and procedures, parental participation, and digital health interventions, can be used to reduce cyberbullying [
7].
Phishing is a prevalent cybercrime that entails the use of deceptive techniques to trick individuals into revealing critical information, such as login credentials. It can occur through various means, including email, instant messaging, and social media. Cybercriminals may disguise phishing attacks as messages from reliable sources, including administrators of virtual worlds or other users so that cybercriminals can obtain a user’s virtual assets or even their actual financial information. There are several ways to carry out phishing attacks in the metaverse [
8,
9]. Cybercriminals may pose as genuine sources in emails or messages they send, requesting people to provide personal information or their login credentials. They could even make fake applications or web pages that seem like reliable platforms in an attempt to deceive users into giving vital data. Cybercriminals may also employ social engineering techniques to win over a user’s trust before tricking them into disclosing their login passwords or other private information. Researchers and cybersecurity specialists advise using two-factor authentication, practicing safe surfing techniques when in virtual environments, and educating users to spot phishing efforts as ways to combat this [
2].
Money laundering develops as a significant threat in the metaverse, adopting approaches such as the use of virtual currencies and anonymous payment channels for increased anonymity and lower detection rates. Criminals use these tactics to create many accounts and conduct financial transactions using stolen credit card information or prepaid gift cards, complicating the monitoring of fund origins. Virtual banks or in-world investment funds provide another avenue for criminals to deposit large sums and transfer funds to real-world banks; however, evolving terms of service in certain virtual worlds now require proof of government registration or financial institution charter, adding to the challenges of illicit banking services. Despite the anonymity provided by metaverse money laundering, there are drawbacks, such as possible financial constraints and the complexity of setting up accounts and transactions. Without proper protections, detection risks loom, emphasizing the need for regulatory measures that reflect reality. Collaboration between law enforcement and service providers is essential for the adoption of systems that detect suspicious activities suggestive of money laundering or terrorism funding. This issue is prevalent in massively online games (MOGs), which are online video games that accommodate many people and frequently feature persistent areas where interactions take place. Examples include Second Life, World of Warcraft, and Entropia Universe. Online financial service providers (OFSPs) within MOGs facilitate financial services, enabling players to trade virtual currencies or credits and offering functions like fund transfers and currency conversion [
10]. A summary of these crimes, highlighting the weakness often exploited and potential research direction, is provided in
Table 2. These crimes in the metaverse bother around the networks, the Internet, and physical devices. One area often associated with investigating such categories of crimes is network forensics. This is further presented in the next section.
1.2.2. Network Forensic Investigation Techniques
To investigate and evaluate network incidents and security breaches, network forensic techniques are employed [
11,
12]. These methods concentrate on detecting, collecting, and analyzing network data to recreate the sequence of security events. By detecting network weaknesses and communication channels, they aid in the tracking of internal and external network assaults. One strategy in network forensics is to record every packet and event that travels across the network. This enables the reconstruction of the recorded data to identify the source of the attack [
1]. Other methods include packet sniffing: Packet sniffers, such as Ethereal, may collect and analyze data sent between computers on a network. These tools enable forensic investigators to gain insight into the hidden information in the various headers of the TCP/IP protocol stack, assisting them in gathering important information from packets. Furthermore, IP traceback techniques help forensic investigators determine the natural origins of attacking IP packets. These approaches enable victims to discover the network pathways taken by attack traffic without the need for assistance from Internet service providers (ISPs). Techniques such as packet marking can be used to reliably establish the origin of an Internet packet [
2].
1.2.3. The Role of ISO Standards in Network Investigation
Network incidents, ranging from data breaches to cyber attacks, pose a significant threat to organizations and individuals. To effectively respond to these threats, the research systematically highlights the essential role of investigative techniques [
13]. Such practices can detect malicious activity, attribute attacks, and close security vulnerabilities. However, these investigations are not without difficulties. One of the main problems is the lack of standardization and consistency [
14]. Each analysis is unique, making it difficult to establish consistent procedures and protocols. This variability can complicate the reliability of forensic findings and the admissibility of evidence in court proceedings. Moreover, the authors in [
15] strongly emphasize the importance of creating standards for the metaverse to make its technology better. Led by the Khronos Group, the Metaverse Standards Forum, which includes big companies like Google and Meta, is working on making rules for important technical things like 3D objects, how users interact, and the standards for augmented and virtual reality. Because metaverse technology is quite complex, it is important to coordinate and work together, and having standards is key to making sure everything works well and smoothly for users on different platforms. Prioritizing open standards is crucial to preventing fragmentation. Furthermore, to meet these challenges, international standards have been developed to guide investigators. The International Organization for Standardization (ISO) has introduced ISO/IEC 27037, a standard specifically designed to facilitate the collection and preservation of digital evidence [
16] ISO standards provide a structured framework that increases the credibility of forensic findings [
17]. They help ensure that investigations comply with established best practices and methods.
The ISO standards in the area of network investigations serve as a model for consistency and reliability. In particular, ISO/IEC 27037 [
4] provides investigators with a roadmap for the standardized conduct of forensic investigations. By adhering to these standards, investigators can ensure the credibility of their findings and the admissibility of evidence in court proceedings. These standards define best practices for collecting, protecting, and analyzing evidence. They highlight the importance of maintaining the integrity and authenticity of digital evidence, an essential aspect of any forensic investigation. ISO standards help bridge the gap between the ever-changing cyber threat landscape and the need for consistent investigative procedures. However, the adoption of ISO standards in network forensic investigations is not without complexities and challenges [
18] Although these standards offer many benefits, researchers must overcome potential obstacles, including resource limitations and the need for specialized training. In [
19,
20,
21], the authors suggested an IoT framework based on ISO/IEC 27043 [
5], emphasizing the significance of the ISO/IEC 27043 standard for the readiness framework since it offers a standardized approach to digital forensic readiness (DFR) procedures. It provides rules and best practices for digital investigation planning, implementation, assessment, and concurrent operations. The ISO/IEC 27043 standard guarantees that relevant and meaningful forensic data are collected and maintained in a manner that can be used throughout an investigation. It also eliminates business interruptions, lowers investigative costs, and saves time by pre-defining, executing, and improving processes before an incident happens. The standard highlights the need to conduct readiness processes using standardized methods, which is a critical component for effective DFR. A comparative analysis of the contextual application of both standards is further presented in
Table 3.
1.2.4. Metaverse Framework
The fast-developing metaverse, which is gaining popularity among consumers and companies, also raises the possibility of criminal activity. In response, researchers developed a customized digital forensic investigation framework with four primary phases based on the National Institute of Standards and Technology (NIST) standard [
22], which provides a widely used digital forensics framework. This framework is divided into four phases: data collection, evidence assessment and retrieval, analysis, and reporting. It is intended to be used as a guide for performing digital forensic investigations [
3]. The framework is relevant to a variety of domains, including the metaverse, and assists investigators in successfully planning and executing their investigations. The data collection phase begins with the systematic gathering of relevant data from the metaverse and the actual world, which are carefully organized into the user domain, service domain, and metaverse platform domain. Following that is the examination and retrieval of evidence phase, in which investigators thoroughly examine and retrieve evidence, ensuring its proper preservation across all relevant domains. Following that, in the analysis phase, investigators look extensively into the gathered information, seeking insights and patterns to better understand the nature of the problem and identify the responsible parties. Finally, the reporting phase concludes with the production of a thorough investigation report, which combines data and evidence, facilitates contact with stakeholders, and lays out the basis for any legal proceedings.
These four phases are supplemented by three essential domains: the user domain, which focuses on user actions and interactions with technologies such as XR and sensors; the service domain, which includes various metaverse services such as e-commerce and cryptocurrency; and the metaverse platform domain, which is in charge of metaverse operation and management using technologies such as blockchain and AI [
3]. This comprehensive approach solves the particular issues of digital forensic investigations in the complex metaverse environment, guaranteeing effective evidence collection and analysis while protecting data integrity and security. This rigorous investigational division across stages and domains solves the particular obstacles of digital forensic investigations inside the metaverse, enabling compelling evidence collecting and processing. However, the lack of forensic readiness and the inability to ensure the forensic soundness of the investigator’s process presents a major limitation of the study.
Another framework was proposed by [
23] to retrieve forensically significant data from IoT systems based on service interconnectivity. It proposes a service-interconnectivity-based forensic framework, identifies relevant forensic evidence, and introduces a proof-of-concept application for visualizing interconnectivity. The goal of the document is to improve knowledge and examination of linked IoT ecosystems through a thorough forensic approach. It also covers IoT services and talks about research on intelligent gadgets. The creation of a proof-of-concept tool for interconnection visualization, the suggestion of a phased IoT forensic framework, and a comparison with current frameworks are important aspects. To expand the scope of the investigation, find hidden evidence, establish a chain of events, find relevant information sources, enable thorough analysis, and enable a comprehensive response to cybercrimes, it is important to identify interconnectivity in IoT systems for forensic investigations.
Other studies, like [
24], proposed creating a digital forensic investigation tool that is specific to the metaverse environment. A unique tool is required since the open-source and commercial digital forensic tools now in use do not include metaverse-analysis-specific capabilities or plugins. The goal of the suggested tool is to follow user activity while collecting and analyzing artifacts from many regions of the metaverse, such as client devices, platforms, clouds, and integrated analysis. Extensibility is given top priority in design so that new artifacts may be added for a variety of metaverse environments. The tool consists of a layer that processes standard file formats, an engine for parsing and analyzing data, and plugins that handle specific data for each artifact. The tool, which was developed using Python 3 and Flask, is verified on experimental datasets and displays the findings in a web page format that includes hash values for source artifact files, an integrated timeline, and basic metadata. The work’s importance stems from its ability to meet the unique digital forensic requirements of the developing metaverse environment. With the growing popularity of the metaverse, the article helps lay the groundwork for metaverse digital forensics by providing investigators with useful tools and insights. Through scenario-based research, this study confirms the suggested procedure and illustrates how it may improve digital forensic investigations in the metaverse. To close the gap in the current tools’ support for metaverse investigations and to increase the effectiveness and precision of digital forensic analysis in this new sector, the creation of this specific tool is very important.
1.2.5. Framework Evaluation Models
Framework evaluation models are used to analyze framework quality, effectiveness, and usefulness. There are various types available, each with their own set of benefits and drawbacks. When choosing a model, it is essential to consider both the specific purpose of the evaluation and the elements of the framework under discussion. Taken together, these points represent the internal and external validity of a measured instrument. This section examines the differences between selected evaluation models for theoretical frameworks depending on the purpose and context. While there are several such models, the technology adoption/acceptance model (TAM), theory of planned behavior (TPB), task–technology fit (TTF), end-user computing satisfaction (EUCS), and unified theory of acceptance and use of technology (UTAUT) are commonly used in information systems literature [
25,
26,
27,
28].
The technology acceptance model (TAM) describes how users interact with technology and institutional institutions. It is based on two significant factors: perceived ease of use and perceived usefulness. Perceived usefulness measures how much an individual believes that adopting a given system will improve their work performance, whereas perceived ease of use measures how easy it is to use the system. These characteristics have a significant impact on an individual’s attitude toward system usage, which influences their intentions and actual adoption. It proposes a direct relationship between perceived usefulness and behavioral intention, emphasizing the importance of an individual’s attitude in shaping their decision to accept and use a system. In addition, it has been integrated with other models, including the task–technology Fit (TTF) model, to provide a more comprehensive explanation of variations in IT utilization [
29].
End-user computing happiness (EUCS) is a model for measuring user happiness with technology, with a particular emphasis on the computing and usage aspects that make up an information system. EUCS includes an overall effective evaluation of the system by end users and employs a 12-item assessment to evaluate criteria such as content, correctness, format, simplicity of use, and timeliness [
29]. It is a reliable predictor of user happiness, especially in integrated systems, and provides valuable insights into the identification of problematic issues in system implementation. It is crucial to highlight that EUCS may involve longitudinal studies to capture developing attitudes over time, and there may be issues with the precision and comparability of overall user satisfaction scores. According to the model, five aspects influence user satisfaction: perceived usefulness, perceived ease of use, information quality, system quality, and service quality. EUCS, as an adaptable tool, significantly contributes to understanding and improving user satisfaction across multiple technical contexts and may be used to evaluate many sorts of technology [
29].
The unified theory of acceptance and use of technology (UTAUT) is a comprehensive model that combines and extends various technology acceptance theories, aiming to understand and predict technology adoption and usage. To gain insight into users’ intentions and activities, it looks into variables such as performance expectations, convenience of use, social impact, and enabling conditions. UTAUT has several applications in information systems and technology, providing insights into the factors that influence technology adoption. Despite its widespread acceptance and use, several experts have raised concerns about its practicality and theoretical assumptions [
30].
The theory of planned behavior (TPB) is a psychological theory designed to elucidate and foresee human conduct. It states that people’s intentions—which are further influenced by their attitudes, subjective standards, and sense of behavioral control—determine their behaviors. Subjective norms are the perceived societal pressure to engage in a behavior; attitudes are an individual’s positive or negative evaluation of an activity; and perceived behavioral control is an individual’s belief in their ability to carry out the behavior. According to the theory of planned conduct (TPB), intentions are the primary factor that determines behavior; people are more likely to act when they have strong intentions to act [
31].
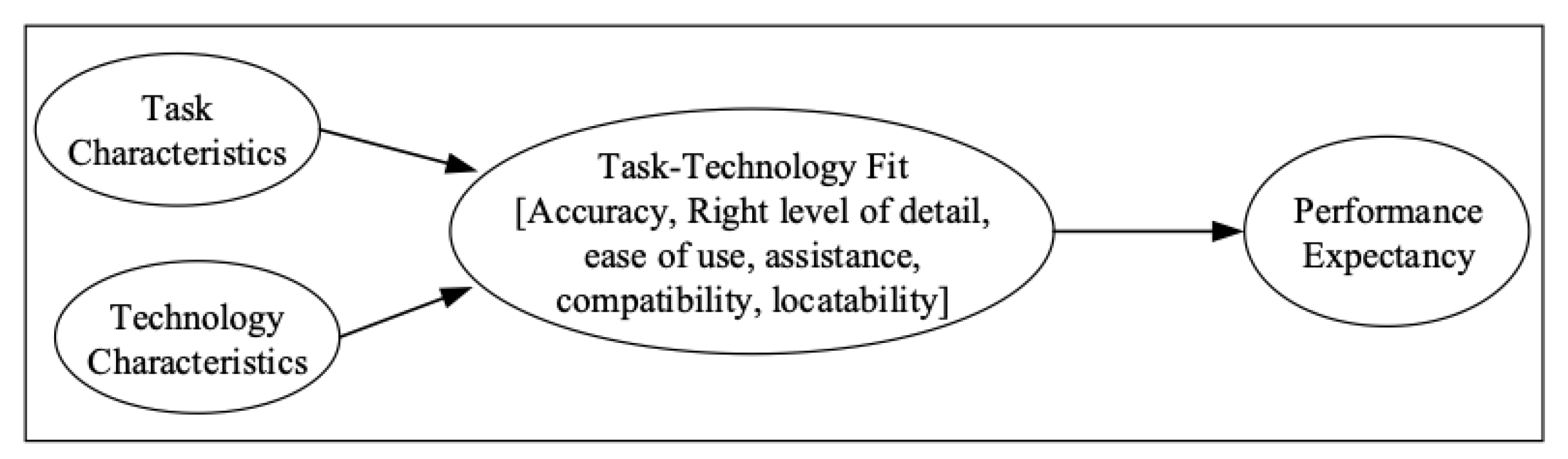
TTF is a model that focuses on the compatibility of technology with the tasks of the user [
29]. The model is based on the idea that individuals are more likely to accept and use technology if it is well-suited to the tasks at hand. When evaluating the fit between a technology and the user’s tasks, TTF assesses three factors: task characteristics (complexity, frequency, importance), system characteristics (features, capabilities), and individual characteristics (user skills, experience, preferences). According to TTF, a good fit between the technology and the user’s tasks will result in higher levels of user acceptability and utilization [
29]. A concise summary of these common models showing their potential suitability for known context is further highlighted in
Table 4.
1.3. Proposed Work
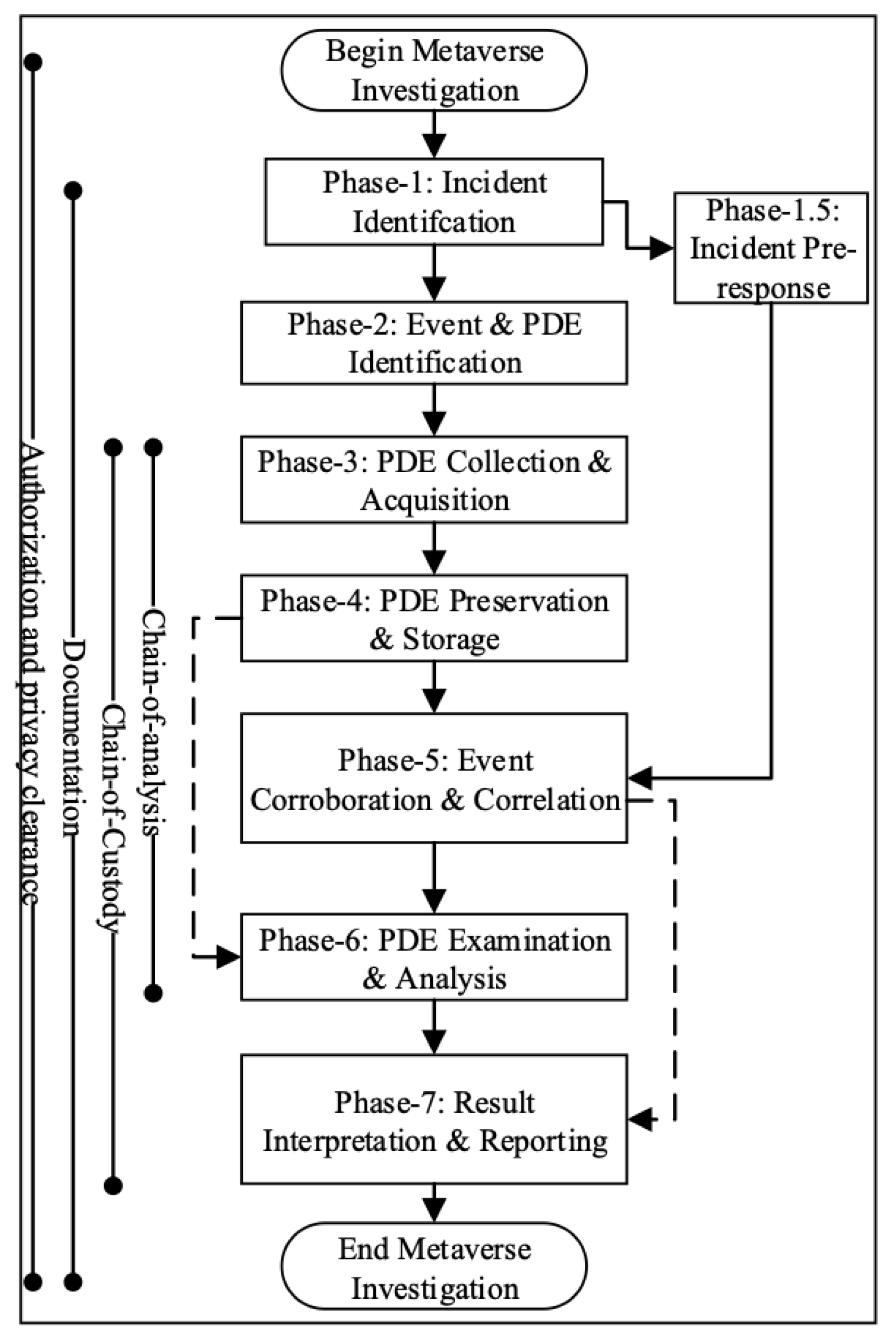
A high-level abstraction of the suggested framework, which is divided into seven related phases, is shown in
Figure 1. The phases described in ISO/IEC 27043:2015 and the metaverse forensic framework, as explained by Seo et al. [
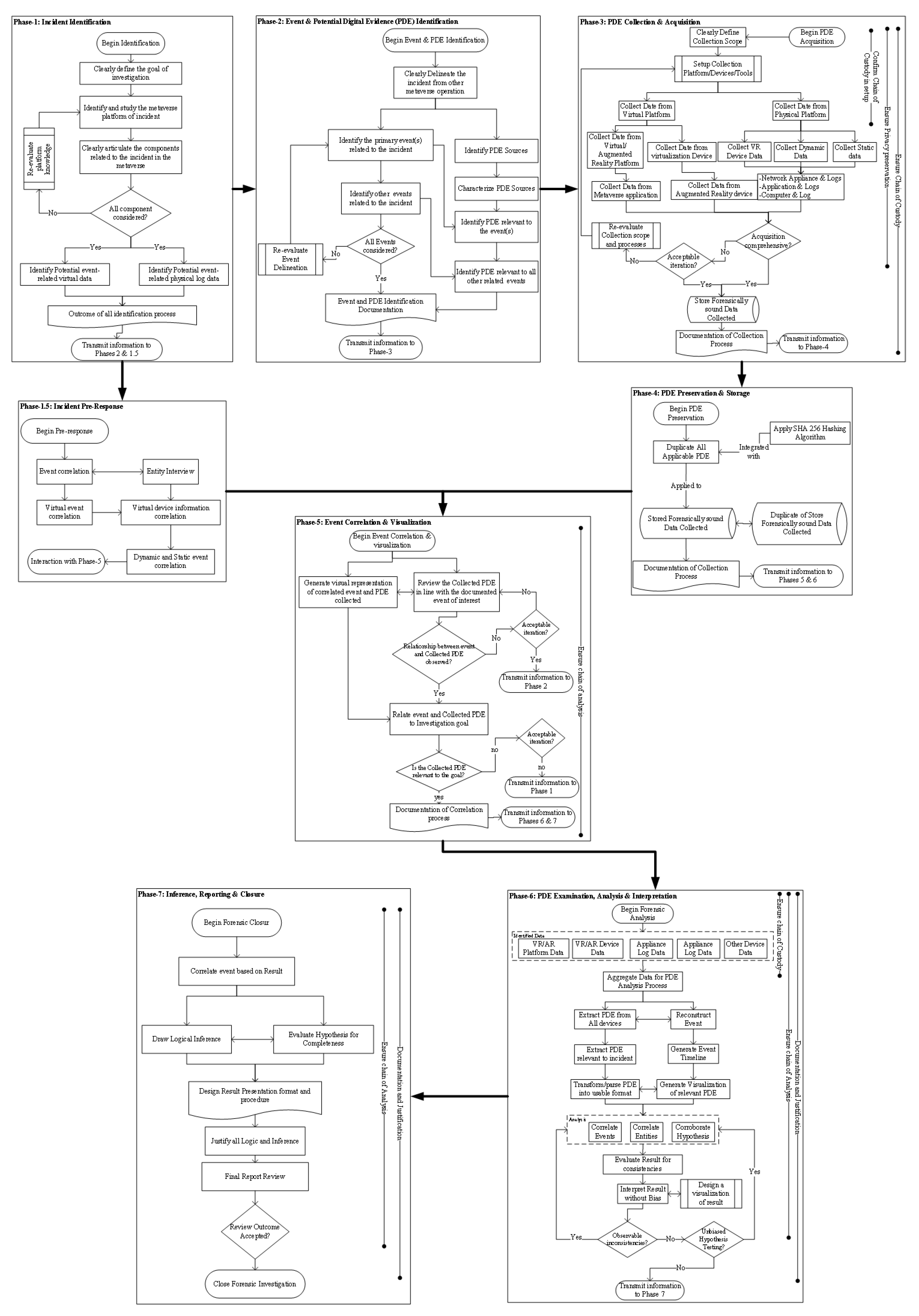
3], have been strategically matched with these proposed phases. However, a detailed breakdown of the complete proposed framework is provided in
Figure 2. While our suggested framework has some similarities to existing frameworks, each step provides a more in-depth method designed especially for digital investigations connected to incidents in the metaverse.The alignment to current standards guarantees a strong and uniform approach, while the distinct characteristics of every phase respond to the variety and complexity present in the metaverse environment.
The first developed framework in [
3] is meant to serve as a guide for digital forensic investigations in the metaverse. It is based on the NIST standard and has four phases: data collection, evidence assessment, analysis, and reporting. By combining three crucial domains—user, service, and metaverse platform—it methodically collects, investigates, and evaluates data to address issues in the metaverse environment. This all-inclusive strategy protects data security and integrity while guaranteeing efficient evidence gathering and analysis.
On the other hand, the proposed framework comprises seven phases and attempts to give a more comprehensive and in-depth procedure for digital investigations in the metaverse. It aligns with ISO/IEC 27043:2015 and the metaverse forensic framework mentioned in [
3]. The readiness component is particularly covered by ISO/IEC 27043:2015 (as asserted in
Table 3), whereas prior frameworks have placed less focus on this area. The proposed framework addresses the various and complicated characteristics of the metaverse environment while ensuring a strong and uniform approach by intentionally matching phases with defined criteria. This sophisticated approach is designed for events in the ever-changing metaverse and considers important factors like readiness that might improve the efficiency of digital investigations. The proposed framework, as detailed in
Figure 2, comprises seven related main phases and a pre-response phase. An incident pre-response phase provides a mechanism for handling incidents in such a way that related events and information are documented before the main investigation. Information such as interviewing entities associated with the incident, identifying and documenting events associated with the incidents (both physical and virtual), and an initial correlation of events to ascertain the extent of the metaverse investigation are documented. The main phases of the proposed framework include:
Incident identification: This phase addresses the respective processes to follow when a security and or privacy violation is identified/reported within the metaverse for which investigation is requested.
Event and potential digital evidence identification: While the first phase addresses the process to follow to prepare for an investigation, this phase provides a guide on defining and identifying what constitutes potential digital artifacts (PDEs) within the metaverse. Within the metaverse platform, PDE preservation of volatile artifacts and non-volatile artifacts is a major focus of this phase. For example, artifacts related to users can be located in wearables (including head-mounted display units) and mobile devices. However, this would differ from common services associated with the platform. These would include the platform’s logging system, the associated data center for the platform, and servers (database and logs).
Collection and acquisition: Upon identification of PDEs, this phase specifies how an investigator should acquire all identified PDEs in a forensically sound manner.
Potential digital evidence preservation and storage: This phase provides a forensically sound procedure for the preservation of all acquired and collected PDEs. This process also specifies the use of SHA-256 as the hashing algorithm, as opposed to the use of deprecated algorithms. The degree of volatility of PDE is given consideration in this phase.
Event correlation and visualization: Input to this phase includes both the incident pre-response phase and the PDE preservation phase. In this phase, an investigator is introduced to the procedure for aligning observed PDEs with the pre-response data collected (often by first responders or incident handlers).
Potential digital evidence examination, analysis, and interpretation: This phase provides a guided sequence on how an investigator can analyze PDEs extracted from a metaverse platform.
Inference, reporting, and closure: here, details on processes to make inferences and provide a forensic report on the conducted investigation are explained. An investigator would be required to ensure forensic soundness throughout this investigation process. Each phase in this proposed framework ensures documentation and verification of procedures.
This largely contrasts the benchmark framework presented in Seo et al. [
3], which comprises only four phases:
data collection, examination and evidence extraction, analysis, and reporting. A framework should provide a procedural guide for ease of use, comparability, and repeatability. These characteristics are missing in the existing framework. Building on this baseline framework, the proposed framework provides an integral sequence and process for metaverse forensics.
4. Discussion
The rise of the metaverse signifies a fundamental change in how we communicate, work, and live digitally. There is much potential for creativity, cooperation, and business in this vast virtual world. However, these advantages also bring with them new, challenging problems, especially in the field of cybersecurity. Addressing the possible rise in cybercrimes in this digital ecosystem is essential as assets and activities progressively move to the metaverse. The complex structures of the metaverse may be beyond the capabilities of traditional forensic techniques, which were designed to examine events in the real world. Thus, the creation of specific frameworks that can guide forensic specialists in carrying out comprehensive and effective investigations in this virtual setting is crucial.
The four phases of the benchmarked framework [
3]—data collection, evidence evaluation, analysis, and reporting—are based on the NIST standard. It focuses on three key domains: user, service, and metaverse platform. Thoroughly obtaining, examining, and assessing data ensure data security and integrity and make evidence collection and analysis more effective. Although this framework offers a strong basis for digital investigations in the metaverse, it might not be broad enough or deep enough to fully handle the complexity of this dynamic environment.
In response to this limitation, a new seven-phase framework that complies with ISO/IEC 27043:2015 and the metaverse forensic framework referenced in [
3] has been offered as a solution to this issue. The goal of this new framework is to offer a more comprehensive process for digital investigations in the metaverse. Unlike the original framework, which might have placed less focus on readiness, the suggested structure takes readiness into account, making sure that investigators have the necessary resources to deal with the metaverse’s constantly evolving features. The proposed framework provides a comprehensive method that is suited to the complexities of the metaverse environment by purposefully matching phases with specified criteria, hence improving the accuracy and efficiency of digital investigations.
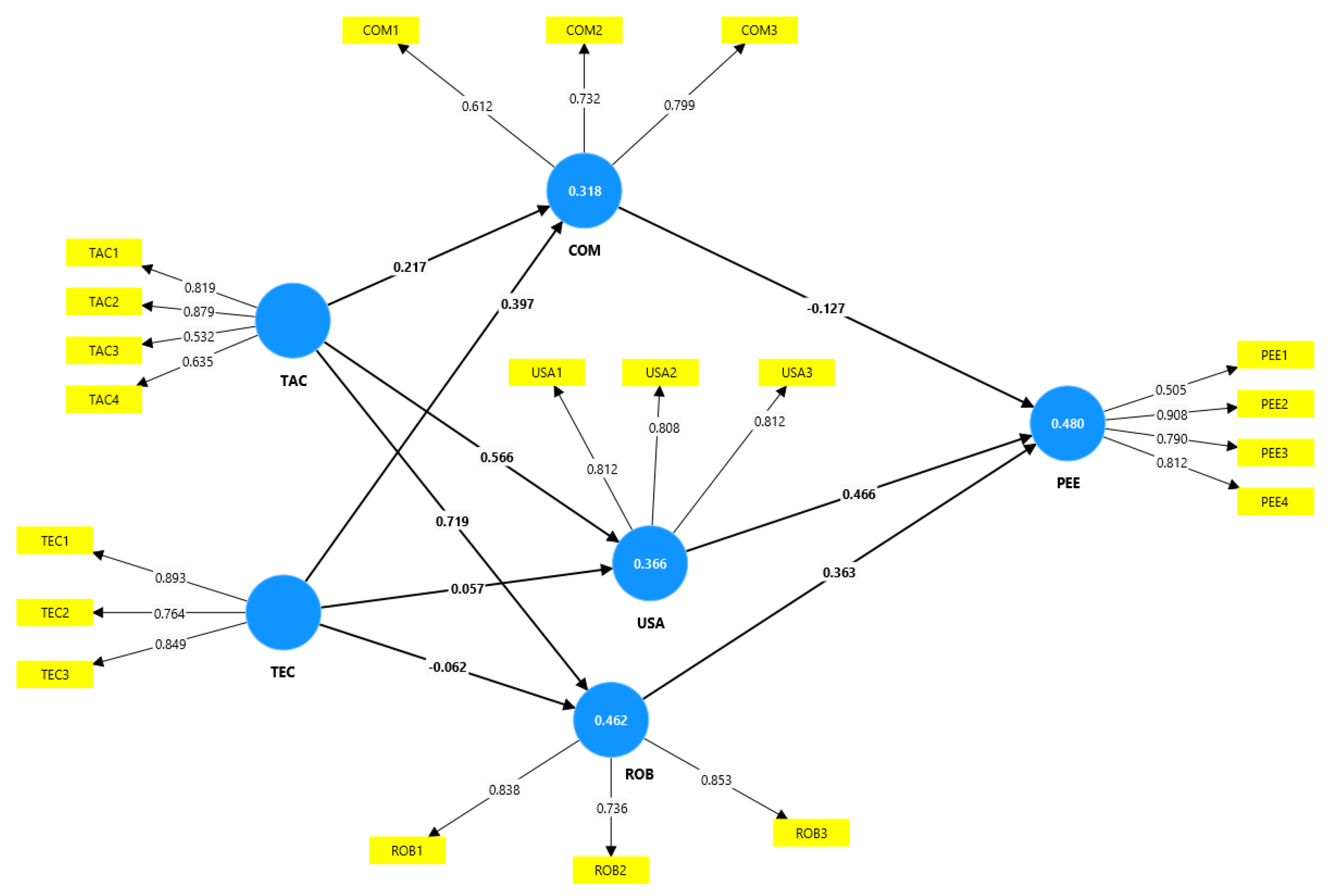
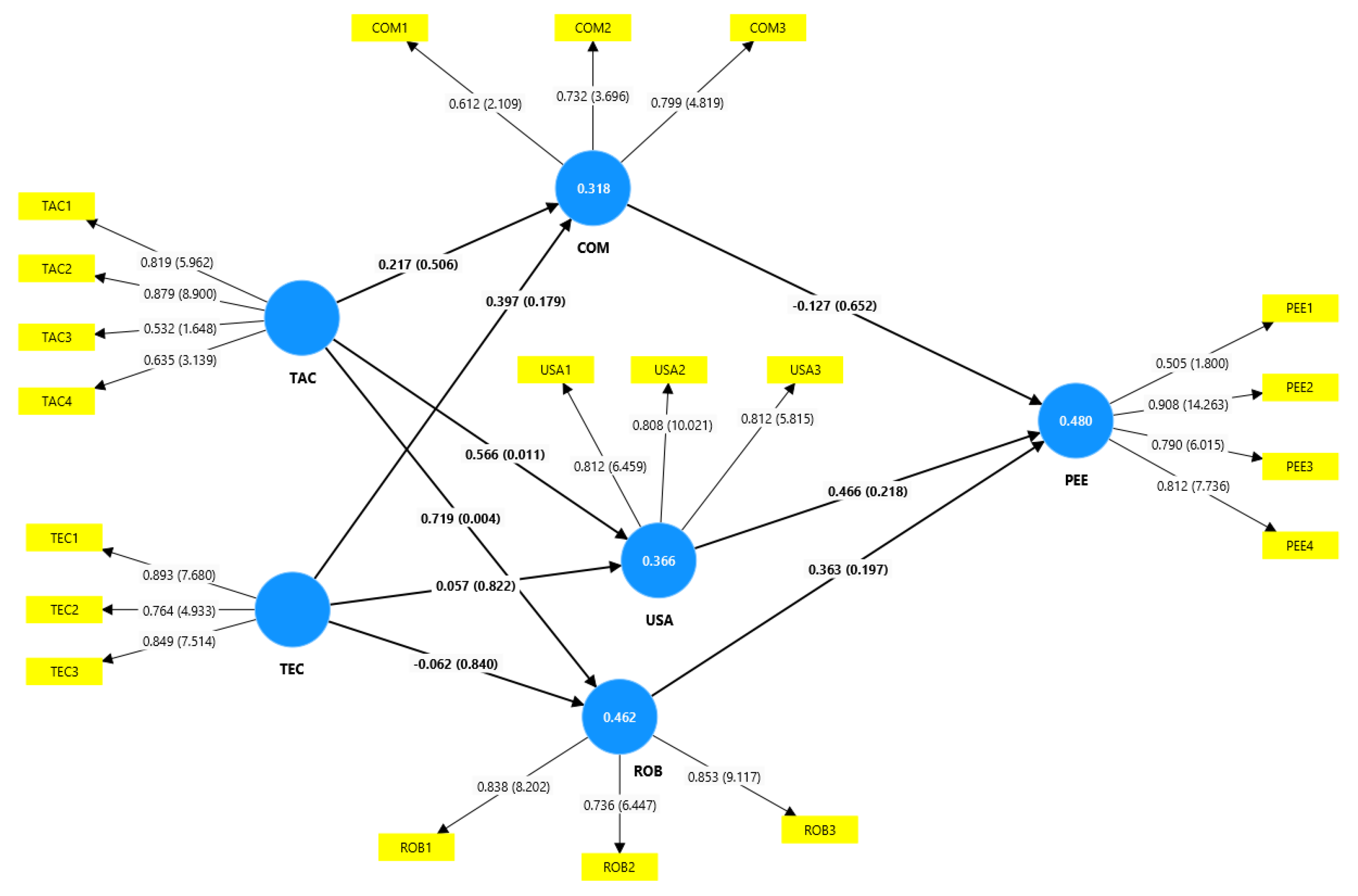
The significance of the proposed framework is in its ability to provide a robust and consistent approach to digital investigations while addressing the diverse and complex nature of the metaverse environment. The proposed framework gives forensic investigators a useful tool to fight cybercrimes in this developing digital environment by complying with recognized standards like ISO/IEC 27043:2015 and the metaverse forensic framework mentioned in the previous research. The responses to the survey given by forensic professionals offer insightful information about how well the suggested framework works. The framework has the potential to greatly enhance the forensic investigation process in the metaverse, as seen by the overwhelmingly positive replies, with the majority of respondents indicating agreement or strong agreement with its accuracy, usability, and application. The significance and applicability of the proposed framework in tackling the particular difficulties faced by cyber investigators in the metaverse are highlighted by this solid support, highlighting its worth as a vital resource for forensic investigators working in this digital environment. The efficiency of the proposed framework is further supported by the analysis of the survey replies. The results of the investigation indicated a considerable indirect association between task characteristics and performance expectancy. This indicates that individuals who handle incidents involving the metaverse think this approach will aid, enhance, simplify, and quicken their investigation. On the other hand, performance expectancy is negatively and negligibly indirectly affected by technical characteristics. This shows that although people view the suggested framework favorably for helping with investigative activities, there can be concerns about the technology itself and how it would affect their expectations for performance. Despite this, the proposed framework provides a thorough and uniform approach that can improve digital investigations’ effectiveness and efficacy while maintaining the environment’s security and integrity. Although there are obstacles to its execution, proactive measures can be taken to maximize the framework’s efficiency and guarantee its applicability in the metaverse’s dynamic environment.
5. Conclusions
In conclusion, this study presents a new “Forensic Framework for Investigating Cybercrime in the Metaverse”, expanding upon an earlier framework with more thorough phases and methodologies for investigation. This framework adds to the changing field of digital forensics by improving the current approach, especially regarding cybercrimes using the metaverse. The comparison with the earlier framework shows the improvements, highlighting the enhanced effectiveness and range of the suggested model.
Furthermore, by actively involving forensic professionals in the United Arab Emirates, the article expands its investigation beyond theoretical improvements. Their insightful opinions and valuable insights into the framework give the study a useful edge. A review of the responses indicates that these specialists are in complete agreement that the framework that was developed is highly beneficial and would help investigators of crimes connected to the metaverse tremendously. This real-world validation strengthens the suggested model’s validity and suitability for use in actual forensic situations.
Even while the results are encouraging, there are several essential limits to be aware of. Further validation through extensive testing on real cases may be necessary to ensure the framework’s effectiveness and flexibility in a variety of metaverse criminal scenarios. This can also include leveraging this proposed framework as a methodology for conducting a forensic investigation in the metaverse. Furthermore, to guarantee that the framework stays applicable and efficient, constant updates and modifications are required due to the dynamic nature of virtual environments and technology.
To verify the robustness and generalizability of the framework, the future research should concentrate on conducting experiments on a range of metaverse-related cases. The suggested framework will be improved and refined even more by ongoing cooperation with forensic specialists, incorporation of cutting-edge technology, and investigation of potential difficulties in various metaverse platforms. This research lays a strong foundation for future developments in the field of digital forensics and represents a significant step forward in tackling the difficulties presented by metaverse cybercrimes.