Abstract
Idle bandwidth resources are inefficiently distributed among different users. Currently, the utilization of user bandwidth resources mostly relies on traditional IP networks, implementing relevant techniques at the application layer, which creates scalability issues and brings additional system overheads. Information-Centric Networking (ICN), based on the idea of separating identifiers and locators, offers the potential to aggregate idle bandwidth resources from a network layer perspective. This paper proposes a method for utilizing user bandwidth resources in ICN; specifically, we treat the use of user bandwidth resources as a service and assign service IDs (identifiers), and when network congestion (the network nodes are overloaded) occurs, the traffic can be routed to the user side for forwarding through the ID/NA (Network Address) cooperative routing mechanism of ICN, thereby improving the scalability of ICN transmission and the utilization of underlying network resources. To enhance the willingness of users to contribute idle bandwidth resources, we establish a secure and trustworthy bandwidth trading market using blockchain technology. We also design an incentive mechanism based on the Proof-of-Network-Contribution (PoNC) consensus algorithm; users can “mine” by forwarding packets. The experimental results show that utilizing idle bandwidth can significantly improve the scalability of ICN transmission under experimental conditions, bringing a maximum throughput improvement of 19.4% and reducing the packet loss rate. Compared with existing methods, using ICN technology to aggregate idle bandwidth for network transmission will have a more stable and lower latency, and it brings a maximum utilization improvement of 13.7%.
1. Introduction
According to a survey report by Cisco, internet users and traffic have grown rapidly in the past five years. It is projected that by 2023, 66% of the world’s population will be using internet services, and the global average fixed broadband speed will reach 110 Mbps [1]. Bandwidth-intensive applications such as video conferencing, virtual reality, ultra-high-definition video, and online gaming have emerged in large numbers. This has prompted users to purchase more expensive network bandwidth services. However, according to the survey, the average weekly internet usage time for internet users is less than 30 h [2], which means that for most of the time, users’ network bandwidth resources remain idle and not in use. This leads to the waste of network bandwidth resources and inadequate bandwidth utilization efficiency. In general, idle bandwidth can be quantified as the peak data transmission rate minus the actual data transmission rate.
In this context, researchers have proposed methods for utilizing idle bandwidth resources at the user end in different scenarios [3,4] to optimize network resource utilization and help third-party service providers reduce operating costs and improve service quality. These methods are based on Transmission Control Protocol and Internet Protocol (TCP/IP). However, the original design of the TCP/IP network protocol was to ensure reliable end-to-end transmission, and it lacks native support for addressing and routing in the process of resource sharing. Therefore, these methods usually implement relevant techniques and mechanisms at the application layer. This can affect system scalability, and the complex application layer methods can also incur high computational and network resource overhead. Unlike the traditional TCP/IP protocol stack, ICN [5,6] decouples identifier and locator, replacing the IP-based network architecture of traditional networks with a new network architecture that uses the ID as the thin waist. This avoids the problems caused by IP semantic overload. ICN uses globally unique IDs to name entities or resources within the network, providing a foundation for utilizing idle bandwidth resources at the user end from a network layer technology perspective.
The development of ICN has given rise to many related projects. Based on different routing and forwarding methods, existing ICN paradigms can be mainly divided into two types: the name-based routing ICN paradigm and the independent name resolution ICN paradigm. The former mainly uses hierarchical naming, combining name resolution with message routing. Typical examples of this paradigm include Content-Centric Networking (CCN) [7], Named Data Networking (NDN) [8], and Content Network (CONET) [9]. These ICN architectures are incompatible with existing IP networks and require comprehensive upgrades to the underlying network infrastructure, resulting in high deployment costs. The latter type uses flat naming, decoupling name resolution from the message routing process. Examples include MobilityFirst [10], Network of Information (NetInf) [11], and SEANET [12]. In this ICN architecture, a Name Mapping Resolution System (NMRS) is responsible for maintaining the relationship between network addresses and identifiers. Resource or service publishers can register their NA and corresponding ID with the NMRS. The network can then obtain the publisher’s NA from the NMRS using the resource identifier ID and perform routing and forwarding based on the NA. IP can be used as the NA to ensure compatibility with existing network infrastructure, enabling a smooth evolution of the network architecture. Our proposed solution is based on the latter ICN paradigm.
To encourage users to actively contribute their idle bandwidth resources, this paper proposes the use of blockchain technology to build a bandwidth resource sharing marketplace. Blockchain is a distributed ledger technology that can transparently and securely record transactions in a tamper-poof manner. It is possible to securely account for the network contribution of users, and blockchain naturally carries payment and transaction characteristics, which can distribute token rewards to users. By designing blockchain incentive mechanisms, user behavior can be effectively changed. In different scenarios, there have been many works on incentive mechanisms based on blockchain [13,14,15]. This paper mainly presents a fusion architecture of the blockchain and ICN network and designs corresponding incentive mechanisms to encourage users to contribute their idle bandwidth to the ICN network. Since monetary mechanisms are the most direct and widely adopted way to incentivize users, this paper proposes an incentive model based on the PoNC blockchain consensus algorithm. Users can “mine” by forwarding messages and receive token rewards.
In this paper, we propose the utilization of users’ idle bandwidth resources in ICN through a blockchain-based incentive mechanism. Our goal is to leverage the characteristics of ICN to utilize user bandwidth resources and enhance network transmission scalability. To our best of knowledge, we are the first to propose an idle bandwidth aggregation and utilization method in an IP-compatible ICN architecture. Compared to existing solutions in the same scenario, it has more advantages, and further introduces blockchain technology to address incentive and trust issues. The main contributions of this paper are as follows:
- We introduce the background knowledge of ICN and propose a fusion architecture of ICN and blockchain. Within this architecture, we present a scheme to utilize user bandwidth resources. We use User Bandwidth Sharing Service ID (UBSID) to identify a group of user nodes. These user nodes serve as backup nodes for transmission in ICN. They can replace ICN routing nodes or alleviate their load in specific situations.
- To fully utilize user bandwidth resources, we propose a node selection strategy that takes into account different network states. This strategy aims to select the user nodes with the optimal network resource to assist in ICN packet forwarding. In order to incentivize user nodes to actively contribute their network bandwidth resources and prolong their online time, we design a consensus algorithm based on network contribution proof to incentivize user behavior.
- We conducted a series of simulation experiments to validate the feasibility of our proposed scheme. The experimental results demonstrate significant improvements in ICN average network throughput and packet loss rate. Additionally, we compared our scheme with an application layer solution for network transmission. The experimental results indicate that our proposed scheme exhibits significant advantages in terms of end-to-end latency and bandwidth utilization.
The remaining parts of this paper are organized as follows: In Section 2, we review relevant research on utilizing user bandwidth resources through solutions at the application layer and network layer. In Section 3, we introduce the background knowledge of ICN and propose a fusion architecture of ICN and blockchain. Within this architecture, we present a scheme to utilize user bandwidth resources. we further provide a detailed explanation of the node selection strategy based on NMRS and the incentive mechanism based on PoNC. Next, we conduct simulation experiments to evaluate the overall scheme and discuss the experimental results in Section 4. Finally, in Section 5, we summarize our research and provide an outlook on future work.
2. Related Work and Background
Utilizing idle user resources is beneficial for creating a win-win situation. Consequently, it has gained widespread attention and research in both the industrial and academic sectors. Currently, the utilization of idle bandwidth resources of users is mostly achieved at the application layer. Therefore, we will separately introduce the research status of application layer technology solutions and network layer technology solutions.
2.1. Application Layer
Based on different scenarios, the existing application layer solutions for utilizing user bandwidth resources can be categorized into content delivery, network transmission, and file sharing scenarios.
In the content delivery scenario, idle user bandwidth and storage resources are utilized to assist in content distribution in CDN. The hybrid content delivery network (HCDN) [16] deploys CDN-level distribution systems in the backbone network and delivers content to the edge of the network. During edge replica transmission, P2P technology is employed to leverage user-side bandwidth resources for content distribution, thereby reducing the number of edge servers and saving deployment costs. However, HCDN requires the introduction of additional entities to establish resource indexes and adopts centralized management and scheduling methods, which undoubtedly increases the implementation cost of the solution and poses scalability issues. Building upon HCDN, the literature [17] proposes a mechanism based on oligopoly to balance the load on edge servers and utilizes a profit-maximizing auction to maximize user contributions in P2P content delivery. Although this method increases the net profit of HCDN providers and reduces content distribution costs, the algorithmic modeling is overly complex and difficult to apply in practical scenarios. In [18], the authors introduced the adaptive bit rate (ABR) algorithm to HCDN to enhance video transmission quality of experience (QoE) and proposed an efficiency improvement method based on delay response to merge ABR and P2P.
In the network transmission scenario, user bandwidth resources are utilized to forward data packets. One of the most typical examples is the New Kind of Network (NKN) [19]. NKN adds a blockchain layer on top of the existing TCP/IP and uses chord DHT to maintain the network topology and routing. Users can “mine” NKN packets by forwarding them and receive token rewards. However, the addressing and routing based on DHT often do not match the underlying network routing paths, and updating and maintaining the DHT routing table requires a significant amount of computational and network bandwidth resources. RightMesh [20] uses Wi-Fi and Bluetooth signals on mobile devices to build a mesh network, solving the problem of limited access to the internet in remote areas with no cellular network coverage. It also introduces blockchain technology to create a secure and efficient environment for sharing network bandwidth. However, this technology is only applicable to wireless access scenarios. In the file sharing domain, users’ idle bandwidth and storage resources are utilized for peer-to-peer file transfers. Examples include Bittorrent [21] and IPFS [22]. However, these technologies have a narrow scope of application. Overall, while there are various solutions for utilizing user bandwidth resources in different scenarios, most of them have limitations and are not widely applicable in the broader network infrastructure.
2.2. Network Layer
Due to the limitations of IP networks, most existing solutions for utilizing user bandwidth resources through network layer technologies rely on ICN.
In one study [23], the authors combined the concept of crowdsourcing with ICN and proposed Crowdsourced CCN Mobile Networks (CCCMNs). CCCMN considers a group of mobile users, where all mobile devices are equipped with name-based routing and content caching (CCN services). Nearby users can form a collaboration group through Wi-Fi, crowdsourcing their wireless bandwidth and caching resources for collaborative content distribution. Contribution-aware ICN [24] utilizes user-side resources to assist in content delivery. CA-ICN extends the ICN architecture by introducing a content distribution manager to manage and generate user contribution levels (CLs). It also proposes contribution-aware name routing to incentivize users to contribute in ICN. In [25], the authors proposed a method to construct a Named Data Networking (NDN) resource leasing market using blockchain technology. The market is designed as a reverse auction operated by content providers, and incentive mechanisms for user access points are studied. All of these methods are based on name-based routing in the ICN paradigm and are mainly applicable for innovative ICN architecture research. They are difficult to integrate with existing network infrastructure.
Table 1 compares and summarizes the above methods for aggregating and utilizing idle bandwidth. Although there are differences in the hierarchy and application scenarios of these methods, they all indicate that using idle bandwidth can bring improvements and benefits to the corresponding systems, and these methods can be further divided into centralized and distributed methods. The centralized method uses a central index server to establish resource indexes and be responsible for task scheduling, while the distributed method adopts the DHT approach. Although it avoids the drawbacks of centralized architecture, it will affect the efficiency of routing.

Table 1.
Comparison of methods for utilizing idle bandwidth in different scenarios.
3. System Design
In this section, we first provide an introduction to the background knowledge of ICN. We then analyze the technical advantages of ICN to elucidate our research motivation. Finally, we provide a detailed description of the overall architecture and mechanisms of the system.
3.1. Background and Motivation
One of the methods for achieving smooth evolution of future network architectures is to incrementally deploy ICN routers on top of existing network infrastructure [26]. In the context of IP-compatible ICN protocol stack design, one approach is to incrementally deploy an identifier protocol (IDP) on top of the IP layer [27], thereby empowering the implementation of network functions. The identifier protocol defines a set of rules that govern how packets should act on addresses based on ID, including actions such as addition, deletion, and modification. Figure 1 provides a design diagram of IP compatible ICN packets from the perspective of Ethernet frame structure. The IDP protocol is located at the network layer and can be implemented based on the extension header of IPv6.
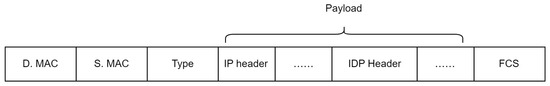
Figure 1.
Structure of ICN packet.
At the same time, a hierarchical resolution system called NMRS is utilized in our ICN to maintain the mapping relationship between ID and addresses [12]. Specifically, it is divided into Global Name Mapping and Resolution System (GNMRS) and Local Name Mapping and Resolution System (LNMRS). GNMRS maintains global identity address mapping and provides services to all users to ensure the accessibility of name resolution services. LNMRS maintains local identity address mapping and provides on-site services to users, with global and on-site resolution complementing each other. NMRS is a distributed autonomous system and can divide the entire network into hierarchical administrative domains (AD) based on constraints such as delay [28] and deploy a name mapping and resolution node in each administrative domain to accelerate name resolution services. Figure 2 illustrates the structure of NMRS. The figure shows a three-level administrative domain structure, with each administrative domain providing different levels of name resolution service latency protection. The number of administrative domain levels can be changed according to actual needs. Software-Defined Networking (SDN) [29] technology separates the control logic and forwarding plane of network devices, providing convenience for validating new network protocols and architectures. Currently, many SDN-based ICN architectures [30,31] have been proposed. In our ICN architecture [12], we also use an SDN controller to manage the ICN routers. The SDN controller is responsible for collecting network topology and status information, and after route calculation, it pushes the forwarding information base to the data plane through a southbound interface. The data plane then performs ICN packet routing and forwarding based on the forwarding table.
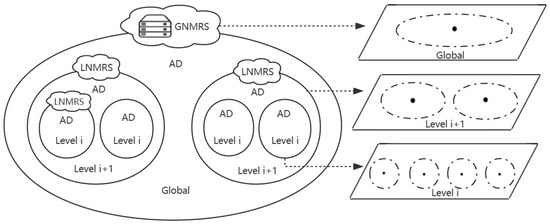
Figure 2.
The structure diagram of the name mapping resolution system in ICN.
Drawing on the deployment scheme of ICN in [32], we consider using the overlay approach to deploy the ICN. IP routers form a underlay network, while ICN routers form an overlay network. ICN routers have computing and storage resources, can forward ICN packets and provide corresponding packet forwarding strategies, and are interconnected through IP logical links. The NA of data packets can be modified based on the local computation module’s policy when passing through ICN routers. The following are examples of the extended functionalities of ICN on top of the IP network infrastructure: In a multipath transmission scenario [33], some ICN routers register their NA and Multipath Transmission Service ID (MPSID) mapping with the NMRS. These ICN routers are considered as relay nodes for end-to-end transmission. The data source can select multiple suitable relay ICN routers to construct multiple parallel single-hop relay paths between the data source and the receiver. In terms of mobility support [34], when a terminal device changes its network address due to a cellular change, it can register its device ID and new network address on the resolution system. The router or sending source can query the resolution system to obtain its network address, ensuring that there is no interruption during transmission. Due to the aforementioned advantages of ICN technology, incrementally deploying ICN networks on top of the existing network infrastructure can greatly empower the implementation of network functions, thus possessing potential application value. This proposed approach aims to reduce the deployment verification cost for ICN service providers and improve the utilization of underlying network resources. In the ICN overlay network, different ICN routers are interconnected through IP logical links. The underlying network resources possessed by ICN routers are limited, while regular internet users have a large amount of idle bandwidth resources. Therefore, deploying ICN routers at the internet user side can expand the underlying network resources of the ICN overlay network.
3.2. Architecture
In ICN, all elements in the network are considered entities, including devices, services, and content. Network services are assigned identifiers, such as in-network caching service [27] and multicast service [35]. Drawing on the experience of this, we consider using user bandwidth for ICN transmission as a service and allocate corresponding UBSID. When a user installs a complete ICN protocol stack locally, they are considered capable of providing ICN packet forwarding functionality. In addition to this, the ICN routers provided by the users also function as blockchain nodes participating in blockchain consensus. Some of these ordinary ICN routers are selected as blockchain consensus nodes to supervise the stability and security of the blockchain system. Figure 3 depicts the architecture of the proposed system. The system consists of two types of nodes. The first is ordinary ICN routers, which are owned by network service providers and have complete ICN network functionality. They are incrementally deployed on top of the existing IP network infrastructure using a hybrid networking approach. The other type of nodes is ICN routers contributed by internet users. These nodes have basic ICN packet processing capabilities and participate in consensus as blockchain nodes. Smart contracts bound to blockchain can securely and automatically measure the contribution of user nodes. For user nodes within the same location resolution domain, we use LNMRS to manage the mapping between the user nodes’ NA and UBSID. The LNMRS ensures timely access to user-side resources and reduces the impact of variable paths on network transmission delay [28]. Considering the high dynamism of user nodes, in this architecture, user bandwidth resources are used by treating user nodes as backup nodes for ordinary ICN routing nodes. In general, packet forwarding is based on the shortest path using ordinary ICN nodes. However, in cases of high network load or node failure with ordinary ICN nodes, the ID/NA cooperative routing mechanism is used to forward packets through ICN routers contributed by internet users.
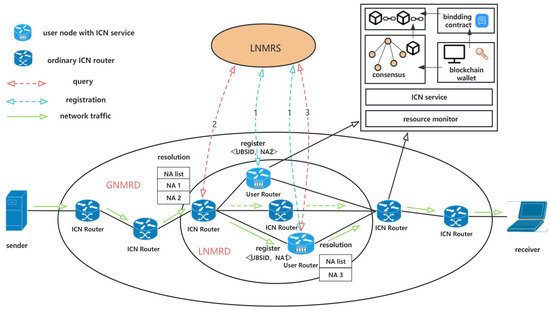
Figure 3.
Logical topology diagram of the integration of ICN and blockchain in an overlay network.
The overall process of the system is as follows:
Step 1: User nodes locally install applications such as blockchain, ICN protocol stack, and resource monitoring module and select some ICN ordinary nodes as blockchain nodes. Within a local resolution domain, the controller designates multiple user nodes as backup nodes for a specific ordinary node in the domain, for example, nodes that frequently operate under high load. Then, the controller distributes configuration information, such as ICN overlay routing tables, to the user nodes.
Step 2: The user nodes, which serve as backup nodes within the same group, are assigned a UBSID. When a user node comes online, it registers the mapping between UBSID and its own NA with the local resolution system. When the user node goes offline, it deregisters the mapping relationship. Within a local resolution domain, there can be one or multiple UBSIDs present.
Step 3: The sender sends the data packet to the ICN edge router. The data is encapsulated with an ICN header to form an ICN data packet. The ICN data packet is then forwarded to the next ICN router based on the Network-Address-based routing. When the ICN packet passes through underlying IP routers, they do not process the ICN packet but only forward it.
Step 4: When the network load of an ICN ordinary node becomes too high, it proactively sends notification messages to the upstream ICN ordinary nodes. The upstream ICN ordinary nodes query the local resolution system based on the UBSID. Then, based on node selection policies, they choose a specific user node as the next hop for ICN network transmission. The NA of the data packet is modified to the NA of the selected user node.
Step 5: The user node receives the packet and queries the destination NA based on the destination ID. It also consults the local routing table to select the next hop ICN routing node. The user node modifies the address of the data packet to the address of the next hop and forwards it to the underlying IP network. The local resource monitoring module measures the forwarding workload.
Step 6: The data packet returns to the ICN ordinary node for routing and forwarding. During the data transmission process, it may pass through different local resolution domains. In each of these domains, user bandwidth resources can be utilized to assist in ICN network transmission.
Step 7: At regular intervals, the blockchain application selects the accounting nodes based on the network contribution of the user nodes. Block rewards are distributed proportionally to the contribution level, with accounting nodes that exceed a certain threshold receiving additional economic incentives.
The workflow can be summarized as shown in Figure 4. Compared to some application-layer overlay network methods, our approach fully utilizes the characteristics of ICN’s locator–identifier separation. We implement relevant mechanisms at the network layer based on ID/NA cooperative routing, whitch refers to the ability to query new network addresses from NMRS based on specific IDs during packet routing and modify the destination address of the packets as needed. In our ICN architecture, the ID design is inspired by the flat ID design method in MobilityFirst [10], using 20 bytes to name various entities in the network. Additionally, the NMRS plays a crucial role as both the receiver device ID and UBSID query NA operations require the involvement of NMRS. Finally, we employ blockchain technology to provide a secure and transparent network resource sharing environment, encouraging users to contribute bandwidth resources and extend online time. Existing methods for utilizing user bandwidth resources are mostly implemented at the application layer, either a centralized management server needs to be introduced for node management and task scheduling, which will have scalability issues, or a decentralized approach is adopted, but the routing efficiency is low and node selection cannot be based on network status. Some network layer implementation methods are limited in application scenarios and belong to innovative network architectures, and the cost of device updates is too expensive, which does not meet the needs of future network smooth evolution. This paper proposes a method of using users’ idle bandwidth under an IP-compatible ICN architecture and further proposes the introduction of blockchain technology to solve the incentive problem on the user side.
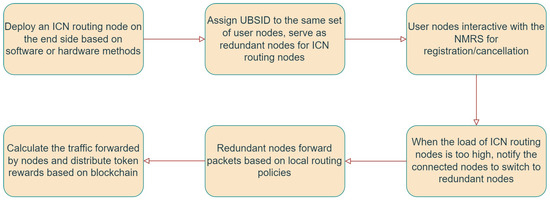
Figure 4.
System workflow diagram.
3.3. Algorithm
In our proposed solution, the user-side ICN routers bound with UBSID function as backup nodes for ICN network transmission, thereby enhancing the scalability of ICN transmission. To fully utilize the idle bandwidth resources on the user side, it is crucial to select the user-side ICN routers with optimal states to assist in packet forwarding. To address this, we introduce a node selection strategy based on the resources and network status at the user side. Considering the dynamic nature of user-side nodes, we have integrated a blockchain consensus algorithm into our design to incentivize users and extend their online time by encouraging them to contribute network resources. This incentive mechanism operates similarly to Filecoin’s storage “mining” mechanism, allowing users to “mine” by forwarding data packets.
3.3.1. Relay Node Selection
Node selection plays a critical role in determining the reliability and efficiency of a system. In HCDN [16], a resource-to-node index is established through edge servers, and the selection of transmission nodes takes into account factors such as node bandwidth and stability. However, the index server in HCDN has single-point performance bottlenecks and scalability issues. In NKN [19], the next hop node is selected based on the logical distance between nodes in the Chord ring. This node selection method lacks the ability to perceive network status, which can impact end-to-end transmission efficiency and scalability. In our system, we manage user nodes based on NMRS. The NMRS divides the entire network into hierarchical management domains based on constraints such as latency, which accelerates resource resolution services. Additionally, we introduce link status to characterize the availability of user nodes, and task scheduling is performed by distributed network nodes. This approach allows for more efficient utilization of network resources compared to the method used in NKN.
Node selection for ordinary ICN routers, based on the UBSID query to the NMRS for a list of candidate relay node addresses, involves choosing the user node with the optimal network state as the next hop node for transmission. In [36], the authors point out that relay node selection is an NP-hard problem. To mitigate the complexity of node selection, we utilize the LNMRS to manage user nodes and subsequently greedily select relay nodes based on computed link states. The calculation of link states directly affects the efficiency of node selection, as shown in Formula (1):
We consider various factors such as bandwidth, latency, and packet loss rate in our node selection process. The bandwidth can be the difference between the peak bandwidth of the nodes and the actual bandwidth used. These parameters can be obtained by sending probe messages to user nodes. In Formula (1), represents the weight of bandwidth on the path state, and represents the weight of round-trip latency on the path state. In practical systems, the values of and need to be adjusted based on specific requirements. represents the packet loss rate to node i and reflects the congestion level of the link. Since the recovery time for packet loss is relatively long, we can use the function to characterize its impact on the link state. The function is defined in Formula (2); represents the average packet loss rate, which is typically set to 0.03 based on empirical values. The factor in the function can be adjusted to control the degree of impact that has on the link state. If a certain factor’s impact on the link state is not considered, the corresponding weight value can be set to 0. By adjusting the weights and factors in the node selection process, we can prioritize and consider the influence of different factors on the link state.
Assuming K is the set of candidate nodes obtained from the LNRS, our objective is to select the node with the optimal link state as the next hop relay node from the set of candidate nodes. The measurement of the link state is determined by the calculation formula mentioned earlier, where a higher value indicates a better link state to the corresponding user node. The link state can be periodically probed, calculated, and cached locally, or it can be computed again during node selection to provide a more accurate reflection of the link state. The detailed node selection algorithm is presented below as Algorithm 1, where represents the optimal link state:
| Algorithm 1: Node Selection |
| Input: UBSID, K |
| Output: |
| 1: Initialize: , , , , , , |
| 2: |
| 3: for each i in K do: |
| 4: send Link Detection Message to k and get , , |
| 5: |
| 6: if then |
| 7: |
| 8: |
| 9: end if |
| 10: end for |
| 11: Return |
3.3.2. Incentive Mechanism
The incentive mechanism is a rationalized system that reflects the interaction between incentive agents and incentive objects. It belongs to a branch of game theory. Common incentive mechanisms can be categorized into three types: reputation-based mechanisms [15], tit-for-tat mechanisms [21], and monetary mechanisms [13]. Reputation-based mechanisms aim to identify selfish nodes and impose penalties on them. Tit-for-tat mechanisms use service as an incentive measure to prevent free-riding behavior. Monetary mechanisms, on the other hand, employ a more flexible payment structure to regulate participants’ behavior. Due to its characteristics, the monetary mechanism is widely adopted in resource leasing, such as computing, bandwidth, storage, and other resources.
Blockchain, with its inherent payment and transaction features, can be used to record ledgers in a trustful, transparent, and tamper-resistant manner. This makes it advantageous for building a secure and trustworthy bandwidth sharing market. In blockchain, incentive mechanisms are often designed in conjunction with consensus algorithms. For example, Bitcoin uses proof of work for mining computational power, while Filecoin uses proof of storage for mining storage capacity. Different blockchain consensus algorithms need to be designed based on the characteristics of the specific blockchain system and cannot be simply applied from other consensus algorithms. Our goal is to allow users to mine by forwarding messages, so we propose an incentive mechanism based on the PoNC consensus algorithm. In this mechanism, network contribution is defined as the number of packets forwarded by users, which can be calculated using local or distributed measurement methods [4]. The PoNC consensus algorithm is specifically designed to align with the objective of our blockchain system, where users can mine by participating in packet forwarding activities.
The selection of consensus nodes in the PoNC algorithm is shown in Figure 5. All user nodes are considered as regular nodes participating in the selection of consensus nodes. Additionally, a subset of ICN regular nodes is selected as regulatory nodes to maintain the security and stability of the entire system. The first round of election considers whether the storage and computing resources of the nodes meet the requirements and whether the nodes are online to do a round of pre-screening; when the first round of pre-screening is over, the network contribution of all the user-side nodes is regularly calculated and the elected nodes are sorted according to the network contribution. Then, based on a threshold set by the system, nodes with network contributions greater than the threshold are selected as consensus nodes, while nodes with contributions below the threshold are selected as backup consensus nodes. If a consensus node goes offline, a node can be selected from the backup consensus nodes to replace it. The right to record transactions in the blockchain belongs only to the consensus nodes, while other nodes are responsible for collectively maintaining the distributed ledger.
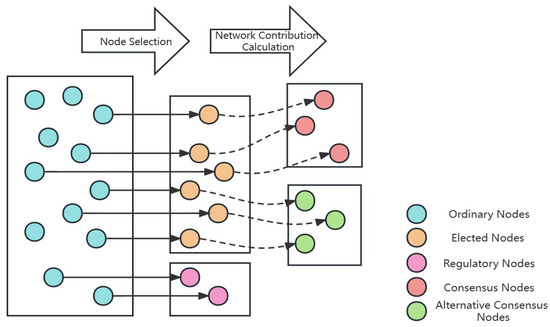
Figure 5.
PoNC consensus node selection process.
After a round of consensus node selection, the consensus nodes will validate the generated block data through digital signatures and broadcast the data to the entire system. The sequence diagram for achieving consensus on block data is shown in Figure 6. The node with the highest network contribution (let us assume it is Consensus Node 1) is responsible for recording transactions and packaging blocks. The block includes business data, timestamps, and the hash value of the previous block. Once the complete block is packaged, Consensus Node 1 broadcasts it to the other consensus nodes. The other consensus nodes validate the transactions in the received block, confirm and sign them, and return the information to Consensus Node 1. Then, Consensus Node 1 broadcasts the block and signature information to the regular nodes. The regular nodes verify the signature information of the block. The regulatory nodes can perform supervision and management tasks to ensure the legality and validity of the transactions. Afterwards, the system adds the new block to the end of the chain structure in chronological order, thus updating the entire blockchain system.
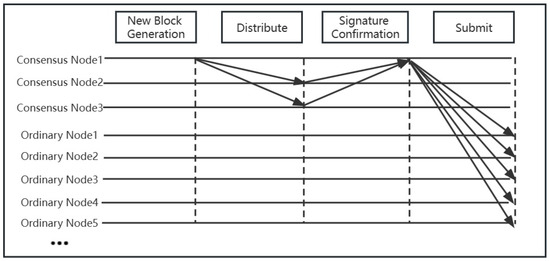
Figure 6.
Sequence diagram for consensus on transactions.
Our goal is to design an incentive mechanism based on Network Contribution Proof in PoNC. In PoNC, the election of consensus nodes relies on the network contribution of the nodes. The calculation of network contribution is not the focus of this article. The incentive mechanism based on network contribution is beneficial to encourage active participation of user nodes in the consensus process and prolong their online time. The following is a detailed description of the token incentive process: Firstly, the ICN network service provider, as the proactive party for incentives, determines the total amount of token rewards for each round. A portion of these rewards is allocated based on the actual workload of the nodes. Specifically, the rewards are distributed proportionally according to the actual forwarding workload of each user node relative to the total workload. Another portion of the rewards is allocated as additional incentives for nodes with network contributions exceeding a certain threshold. These token incentives are distributed to the consensus nodes. The tokens can be exchanged for real-world currency on exchanges. Below is the mathematical description of the token incentive mechanism:
where and represent the total number of tokens and bonuses at time t, represents the conversion coefficient between real-world currency and tokens. and represent the fixed number of tokens and additional incentive tokens to be distributed at time t, respectively. Formulas (3) and (4) are different expressions of total token rewards. Formula (3) converts real-world currencies into tokens, while Formula (4) reflects the different components of token rewards, namely fixed income and additional rewards. and represent the amount of token rewards received by non-consensus node i and consensus node i at time t, respectively. represents the network contribution of node i at time t, and n represents the number of consensus nodes.
4. Simulation
In this section, we simulated and implemented the system and analyzed the experimental results. Firstly, we introduced the experimental environment and settings. Then, we demonstrated the advantages of the proposed solution at different levels of experimental indicators. Finally, we analyzed and discussed the experimental results.
4.1. Experiment Setup
Our experiments are based on the well-known discrete-event network simulator NS3 [37], which is used to meet the needs of academic research and teaching. In order to verify the scalability of the proposed scheme under different network topologies, as shown in Figure 7, we use a real-world topology from The Internet Topology Zoo [38] dataset, specifically the INTEGRA and AGIS topologies, as the underlying physical topologies for our simulation experiments. The default bandwidth between backbone nodes in the topology is set to 55 Mbps and 155 Mbps, with a delay of 4 ms. ICN routers are incrementally deployed on top of the underlying physical network. The entire network is composed of a mix of traditional network devices and SDN network devices. We added two data source points (S1, S2) and two data receiver points (C1, C2) at the network edge, distinguished by different colors. The access nodes for the data source (receiver) points are ICN edge routers, with an access bandwidth of 300 Mbps and a delay of 1 ms. The maximum queue length for each router is set to 100 packets, and each packet has a payload size of 1000 bytes.
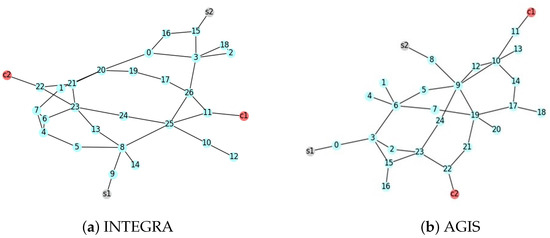
Figure 7.
Simulated physical topologies.
To validate the scalability of our solution for ICN transmission, we continuously increase the sending rate of the data source and compare the performance between using default ICN transmission and using users’ idle bandwidth-assisted ICN transmission. Our scalability metrics are average throughput and average packet loss rate. The main objective is to verify the support of the proposed solution for high bandwidth demand scenarios. In addition, we also compared the impact of the incentive mechanism on system performance. The introduction of the incentive mechanism is beneficial for aggregating more underlying physical link resources.
4.2. Throughout
Throughoutput is one of the most important metrics for measuring data transmission performance. In this section, we use throughput as a scalability metric to evaluate the performance improvement brought by utilizing users’ idle bandwidth and the incentive mechanism.
We first incrementally deploy an ICN overlay network on the INTEGRA and AGIS topologies, with user-side ICN router nodes serving as backup nodes for ICN network transmission. We conducted ten rounds of simulations, where data source nodes (S1, S2) send data to data receiver nodes (C1, C2) and measured the stable throughput of the network at different sending rates. As shown in Figure 8, in both network topologies, when the sending rate is low, the advantage of the proposed solution is not evident as the ICN network transmission does not utilize the users’ idle bandwidth. However, as the sending rate increases, using the users’ idle bandwidth effectively improves network throughput compared to native ICN network transmission, resulting in a maximum throughput improvement of 19.4%. This enhancement further improves the scalability of the solution in high bandwidth demand scenarios. Furthermore, we compared the impact of using a blockchain incentive mechanism on system performance. The use of the incentive mechanism extends the online time of user nodes and increases the bandwidth resources contributed by user nodes and the number of user nodes, which is beneficial for aggregating more underlying physical link resources. In this experiment, we used the same settings as the previous one and introduced the blockchain incentive mechanism. We compared the network throughput before and after the introduction of the incentive mechanism, as shown in Figure 8. It can be observed that at lower sending rates, the incentive mechanism does not bring significant advantages and even slightly decreases the throughput compared to before the incentive mechanism was introduced, which is due to the increased overhead of node selection with too many user nodes. However, as the sending rate increases, the end-to-end throughput of the system improves more with the effect of the incentive mechanism, as ICN regular nodes can choose the user node with the best state for ICN packet forwarding.
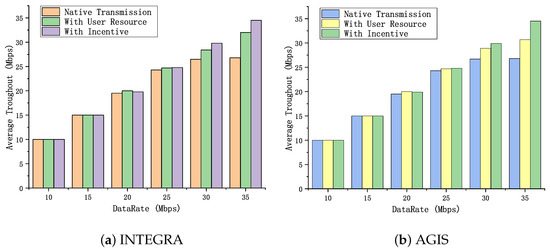
Figure 8.
Comparison of average throughput testing.
4.3. Packet Loss Rate
Packet loss rate refers to the proportion of data packets that fail to reach their destination due to network congestion, network device failures, or poor transmission link quality. The packet loss rate is typically expressed as a percentage and is an important indicator of network quality.
In this section, we use the packet loss rate as a scalability metric to evaluate system performance improvements. We conducted ten rounds of experimental simulations, where data source nodes (S1, S2) sent data to receiver nodes (C1, C2). Packet captures were used to measure the end-to-end packet loss rate. As shown in Figure 9, in both network topologies, compared to native ICN network transmission, utilizing users’ idle bandwidth resources effectively reduces packet loss rate in high bandwidth transmission scenarios. This is because when ICN regular routing nodes experience high network load, they can switch to user nodes for ICN packet forwarding, thereby reducing packet loss rate.
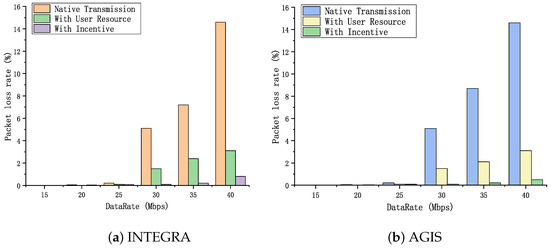
Figure 9.
Comparison of average packet loss rate testing.
Similar to the throughput testing experiments, we also compared the further improvement of system performance with the introduction of an incentive mechanism. The incentive mechanism provides a wider range of node selection, thereby aggregating more underlying link resources. As shown in the figure, compared to the solution without the incentive mechanism, this solution can further reduce the end-to-end packet loss rate, especially at high sending rates. The introduction of the incentive mechanism allows ICN regular nodes to select the best performing user nodes for ICN packet forwarding, thus improving packet loss rate performance. Based on the experimental results, we can conclude that utilizing users’ idle bandwidth resources and implementing an incentive mechanism can effectively improve system scalability, reduce packet loss rate, and enhance transmission quality.
4.4. Delay and Bandwidth Utilization
We leverage ICN technology to aggregate users’ idle bandwidth, while some application-layer methods, such as NKN overlay network, utilize DHT algorithms to maintain the global network topology and message routing. However, as the network scales, updating and maintaining the DHT routing table consumes significant computational and network resources. This undoubtedly increases the workload on user nodes. Moreover, DHT-based routing cannot consider the underlying physical network topology and network load between nodes, which may result in longer routing paths or increased end-to-end latency; bandwidth resource utilization is also low. In this experiment, we compare the performance of solutions that aggregate idle bandwidth using ICN network technology and application-layer methods. The primary evaluation metric is end-to-end latency and the bandwidth resource utilization, and delay comparison experiments are conducted under different backbone link transmission delays. Bandwidth resource utilization is measured under different time sequences, where resource utilization is defined as the proportion of available bandwidth of the selected relay node to the available bandwidth of all nodes. The results, in both network topologies, as shown in Figure 10, indicate that the end-to-end latency based on NKN is unstable, which is determined by the characteristics of the DHT routing algorithm. In contrast, ICN is a network technology that uses ICN to aggregate idle bandwidth for network transmission provides more stable end-to-end latency and has a competitive advantage in terms of latency compared to the NKN solution.
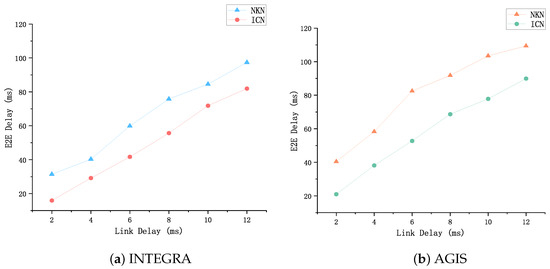
Figure 10.
Comparison of average delay testing.
We also compared the resource utilization efficiency of two technical solutions, and the experimental results are shown in Figure 11. From Figure 11, it can be seen that compared with NKN, the method proposed in this paper has higher idle bandwidth utilization on both network topologies. This is because the selection of nodes in NKN is based on chord distance and does not perceive the network state information of nodes. This article combines different network parameters to select the optimal relay node, which can more effectively utilize idle bandwidth resources.
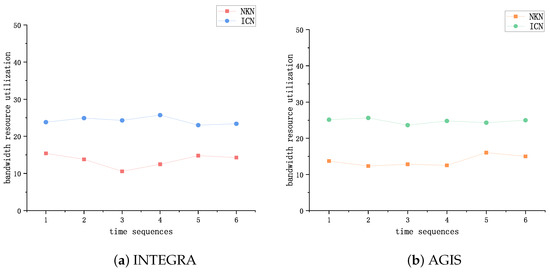
Figure 11.
Comparison of average bandwidth utilization testing.
5. Conclusions
In this paper, we propose a method to leverage users’ idle bandwidth in an IP compatible ICN architecture, combined with blockchain technology to design an incentive mechanism that encourages users to contribute bandwidth. Firstly, we introduce the architecture of ICN as described in this paper and provide a detailed description of how to utilize users’ idle bandwidth based on the inherent advantages of ICN technology. Then, we focus on discussing the optimization method for utilizing idle bandwidth, which involves introducing link state to represent the availability of user nodes and greedily selecting the user node with the optimal network state as the next hop for transmission. Additionally, we design a consensus algorithm based on network contribution proof to select blockchain ledger nodes based on the number of forwarded messages by nodes, and we further design an incentive model based on this consensus algorithm. Finally, we conducted simulation experiments to evaluate the effectiveness of the proposed method. The experimental results showed that by utilizing idle bandwidth on the end side, the maximum throughput of ICN network transmission was improved by 19.4%, and the packet loss rate under high transmission data rates was significantly reduced. At the same time, using ICN technology to aggregate idle bandwidth has more advantages in end-to-end latency compared to existing methods, and also brings a maximum utilization improvement of 13.7%. In our approach, node selection and traffic scheduling are based on distributed ICN network nodes, while NMRS is also a distributed autonomous system. Blockchain is a typical decentralized distributed ledger technology, so our solution is entirely based on a distributed architecture when working.
In future research, we will focus on the study of network contribution measurement methods. We define the number of forwarded messages by users as network contribution and need to consider measurement security. Adopting a single-point measurement may lead to cheating possibilities and an inability to generate forwarding proof, while existing distributed measurement methods such as proof of relay rely on building a chain of signatures, which incurs significant computational overhead. We consider leveraging the inherent advantages of ICN to design a more efficient proof algorithm.
Author Contributions
Conceptualization, Q.L., R.H. and Y.L.; methodology, Q.L., R.H. and Y.L.; software, Q.L.; writing—original draft preparation, Q.L.; writing—review and editing, R.H. and Y.L.; supervision, R.H.; project administration, Y.L.; funding acquisition, R.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was funded by Goal-Oriented Project Independently Deployed by Institute of Acoustics, Chinese Academy of Sciences: Distributed Supercomputing Based on SEANET Network (project no. MBDX202114).
Data Availability Statement
Data are contained within the article.
Acknowledgments
We would like to express our gratitude to Jinlin Wang, Rui Han, and Jiali You for their meaningful support of this work.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
| ICN | Information-Centric Networking |
| PoNC | Proof-of-Network-Contribution |
| ID | Identifier |
| IDP | Identifier Protocol |
| CCN | Content-Centric Networking |
| NDN | Named Data Networking |
| DHT | Distributed Hash Table |
| NetInf | Network of Information |
| NMRS | Name Mapping Resolution System |
| NA | Network Addresses |
| UBSID | User Bandwidth Sharing Service ID |
| HCDN | Hybrid Content Delivery Network |
| ABR | Adaptive Bit Rate |
| QoE | Quality of Experience |
| NKN | New Kind of Network |
| CCCMN | Crowdsourced CCN Mobile Networks |
| CL | Contribution Levels |
| GNMRS | Global Name Mapping and Resolution System |
| LNMRS | Local Name Mapping and Resolution System |
| AD | Administrative Domains |
| SDN | Software-Defined Networking |
| MPSID | Multipath Transmission Service ID |
References
- Cisco. Cisco Annual Internet Report (2018–2023) White Paper; Cisco: San Jose, CA, USA, 2020; Volume 10, pp. 1–35. [Google Scholar]
- CNNIC. The 51st Statistical Report on Internet Development in China; CNNIC: Beijing, China, 2023. [Google Scholar]
- Yin, H.; Liu, X.; Zhan, T.; Sekar, V.; Qiu, F.; Lin, C.; Zhang, H.; Li, B. Design and deployment of a hybrid CDN-P2P system for live video streaming: Experiences with LiveSky. In Proceedings of the 17th ACM international conference on Multimedia, Beijing, China, 19–24 October 2009; pp. 25–34. [Google Scholar]
- Jung, E.; Wang, Y.; Prilepov, I.; Maker, F.; Liu, X.; Akella, V. User-profile-driven collaborative bandwidth sharing on mobile phones. In Proceedings of the 1st ACM Workshop on Mobile Cloud Computing & Services: Social Networks and Beyond, San Francisco, CA, USA, 15 June 2010; pp. 1–9. [Google Scholar]
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A survey of information-centric networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Jiang, X.; Bi, J.; Nan, G.; Li, Z. A survey on information-centric networking: Rationales, designs and debates. China Commun. 2015, 12, 1–12. [Google Scholar] [CrossRef]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Detti, A.; Blefari Melazzi, N.; Salsano, S.; Pomposini, M. CONET: A content centric inter-networking architecture. In Proceedings of the ACM SIGCOMM Workshop on Information-Centric Networking, Toronto, ON, Canada, 19 August 2011; pp. 50–55. [Google Scholar]
- Raychaudhuri, D.; Nagaraja, K.; Venkataramani, A. Mobilityfirst: A robust and trustworthy mobility-centric architecture for the future internet. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2012, 16, 2–13. [Google Scholar] [CrossRef]
- Dannewitz, C.; Kutscher, D.; Ohlman, B.; Farrell, S.; Ahlgren, B.; Karl, H. Network of information (netinf)–an information-centric networking architecture. Comput. Commun. 2013, 36, 721–735. [Google Scholar] [CrossRef]
- Wang, J.; Chen, G.; You, J.; Sun, P. Seanet: Architecture and technologies of an on-site, elastic, autonomous network. J. Netw. New Media 2020, 6, 1–8. [Google Scholar]
- Vakilinia, I.; Wang, W.; Xin, J. An incentive-compatible mechanism for decentralized storage network. IEEE Trans. Netw. Sci. Eng. 2023, 10, 2294–2306. [Google Scholar] [CrossRef]
- Wang, J.; Li, M.; He, Y.; Li, H.; Xiao, K.; Wang, C. A blockchain based privacy-preserving incentive mechanism in crowdsensing applications. IEEE Access 2018, 6, 17545–17556. [Google Scholar] [CrossRef]
- Liu, W.; Song, X.; Kong, L.; Li, Q. PBIM: A Participant Based Incentive Mechanism for Consortium Chain. In Proceedings of the 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hangzhou, China, 4–6 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 263–268. [Google Scholar]
- Lu, Z.; Wang, Y.; Yang, Y.R. An Analysis and Comparison of CDN-P2P-hybrid Content Delivery System and Model. J. Commun. 2012, 7, 232–245. [Google Scholar] [CrossRef][Green Version]
- Garmehi, M.; Analoui, M.; Pathan, M.; Buyya, R. An economic mechanism for request routing and resource allocation in hybrid CDN–P2P networks. Int. J. Netw. Manag. 2015, 25, 375–393. [Google Scholar] [CrossRef]
- Yousef, H.; Le Feuvre, J.; Ageneau, P.L.; Storelli, A. Enabling adaptive bitrate algorithms in hybrid CDN/P2P networks. In Proceedings of the 11th ACM Multimedia Systems Conference, Istanbul, Turkey, 8–11 June 2020; pp. 54–65. [Google Scholar]
- NKN. NKN: A Scalable Self-Evolving and Self-Incentivized Decentralized Network; 2018. Available online: https://nkn.org/wp-content/uploads/2020/10/NKN_Whitepaper.pdf (accessed on 26 December 2023).
- RightMesh. RightMesh White Paper: A Decentralized Mobile Mesh Networking Platform Powered by Blockchain Technology and Tokenization; RightMesh AG: Zug, Switzerland, 2019. [Google Scholar]
- Bharambe, A.R.; Herley, C.; Padmanabhan, V.N. Analyzing and improving a bittorrent networks performance mechanisms. In Proceedings of the Proceedings IEEE INFOCOM 2006. 25TH IEEE International Conference on Computer Communications, Barcelona, Spain, 23–29 April 2006; IEEE: Piscataway, NJ, USA, 2006; pp. 1–12. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Li, C.; Wang, X.; Gong, S.; Wang, Z.H.; Jiang, Q. Performance analysis for content distribution in crowdsourced content-centric mobile networking. In Proceedings of the Quality, Reliability, Security and Robustness in Heterogeneous Systems: 13th International Conference, QShine 2017, Dalian, China, 16–17 December 2017; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2018; pp. 131–141. [Google Scholar]
- Lee, H.; Nakao, A. Incentivizing user-assisted content distribution in information-centric network. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 5839–5843. [Google Scholar]
- Wei, X.; Yu, Z.; Guo, S.; Shen, J.; Qi, F.; Qiu, X. A hybrid chain based incentive mechanism for resource leasing in NDN. In Proceedings of the Cognitive Radio-Oriented Wireless Networks: 14th EAI International Conference, CrownCom 2019, Poznan, Poland, 11–12 June 2019; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2019; pp. 247–261. [Google Scholar]
- Conti, M.; Gangwal, A.; Hassan, M.; Lal, C.; Losiouk, E. The road ahead for networking: A survey on icn-ip coexistence solutions. IEEE Commun. Surv. Tutor. 2020, 22, 2104–2129. [Google Scholar] [CrossRef]
- Dang, S.; Han, R. An In-Network Cooperative Storage Schema Based on Neighbor Offloading in a Programmable Data Plane. Future Internet 2021, 14, 18. [Google Scholar] [CrossRef]
- Li, J.; Sheng, Y.; Deng, H. Two optimization algorithms for name-resolution server placement in information-centric networking. Appl. Sci. 2020, 10, 3588. [Google Scholar] [CrossRef]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A survey on software-defined networking. IEEE Commun. Surv. Tutor. 2014, 17, 27–51. [Google Scholar] [CrossRef]
- Vahlenkamp, M.; Schneider, F.; Kutscher, D.; Seedorf, J. Enabling ICN in IP networks using SDN. In Proceedings of the 2013 21st IEEE International Conference on Network Protocols (ICNP), Göttingen, Germany, 7–10 October 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–2. [Google Scholar]
- Li, J.; Xue, K.; Liu, J.; Zhang, Y.; Fang, Y. An ICN/SDN-based network architecture and efficient content retrieval for future satellite-terrestrial integrated networks. IEEE Netw. 2019, 34, 188–195. [Google Scholar] [CrossRef]
- Shailendra, S.; Panigrahi, B.; Rath, H.K.; Simha, A. A novel overlay architecture for information centric networking. In Proceedings of the 2015 Twenty First National Conference on Communications (NCC), Mumbai, India, 27 February–1 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–6. [Google Scholar]
- Xu, Y.; Ni, H.; Zhu, X. A Novel Multipath Transmission Scheme for Information-Centric Networking. Future Internet 2023, 15, 80. [Google Scholar] [CrossRef]
- Zhou, T.; Sun, P.; Han, R. An active path-associated cache scheme for mobile scenes. Future Internet 2022, 14, 33. [Google Scholar] [CrossRef]
- Li, B.; Wang, J. An identifier and locator decoupled multicast approach (ILDM) based on ICN. Appl. Sci. 2021, 11, 578. [Google Scholar] [CrossRef]
- Ekici, F.; Gözüpek, D. Joint overlay routing and relay assignment for green networks. Comput. Netw. 2015, 79, 323–344. [Google Scholar] [CrossRef]
- Riley, G.F.; Henderson, T.R. The ns-3 network simulator. In Modeling and Tools for Network Simulation; Springer: Berlin/Heidelberg, Germany, 2010; pp. 15–34. [Google Scholar]
- Knight, S.; Nguyen, H.X.; Falkner, N.; Bowden, R.; Roughan, M. The internet topology zoo. IEEE J. Sel. Areas Commun. 2011, 29, 1765–1775. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).