Quantum Key Distribution in Kubernetes Clusters
Abstract
:1. Introduction
2. Background
2.1. Quantum Key Distribution
2.2. Kubernetes and Operators
- Pod: is the smallest deployable object in Kubernetes, and it could be seen as a set of containers that share the same IP address. In order to run those containers, a Container Runtime is available on the node (e.g., Docker, containerd, cri-o);
- Service: is an abstract resource that represents a way to expose an application that could be composed of one or more pods, i.e., replicas of the same applications;
- Deployment: is an object that provides declarative updates for Pods. In practice, it allows managing changes to their status through the Deployment controller. It is possible to describe the desired number of replicas of a specific pod and the policies for the rollout or rollback of the application to previous versions;
- Secret: is an object that contains sensitive data such as passwords, tokens, or keys. Generally is used to avoid including sensitive information in an application or code;
- Custom Resource (CR): this is a way to extend the Kubernetes API by creating a new resource that allows storing objects of a certain type;
- Custom Controller: combined with the CR, it continuously monitors the cluster and based on the state of a CR, it applies changes to the cluster. In this sense, Kubernetes implements a declarative approach.
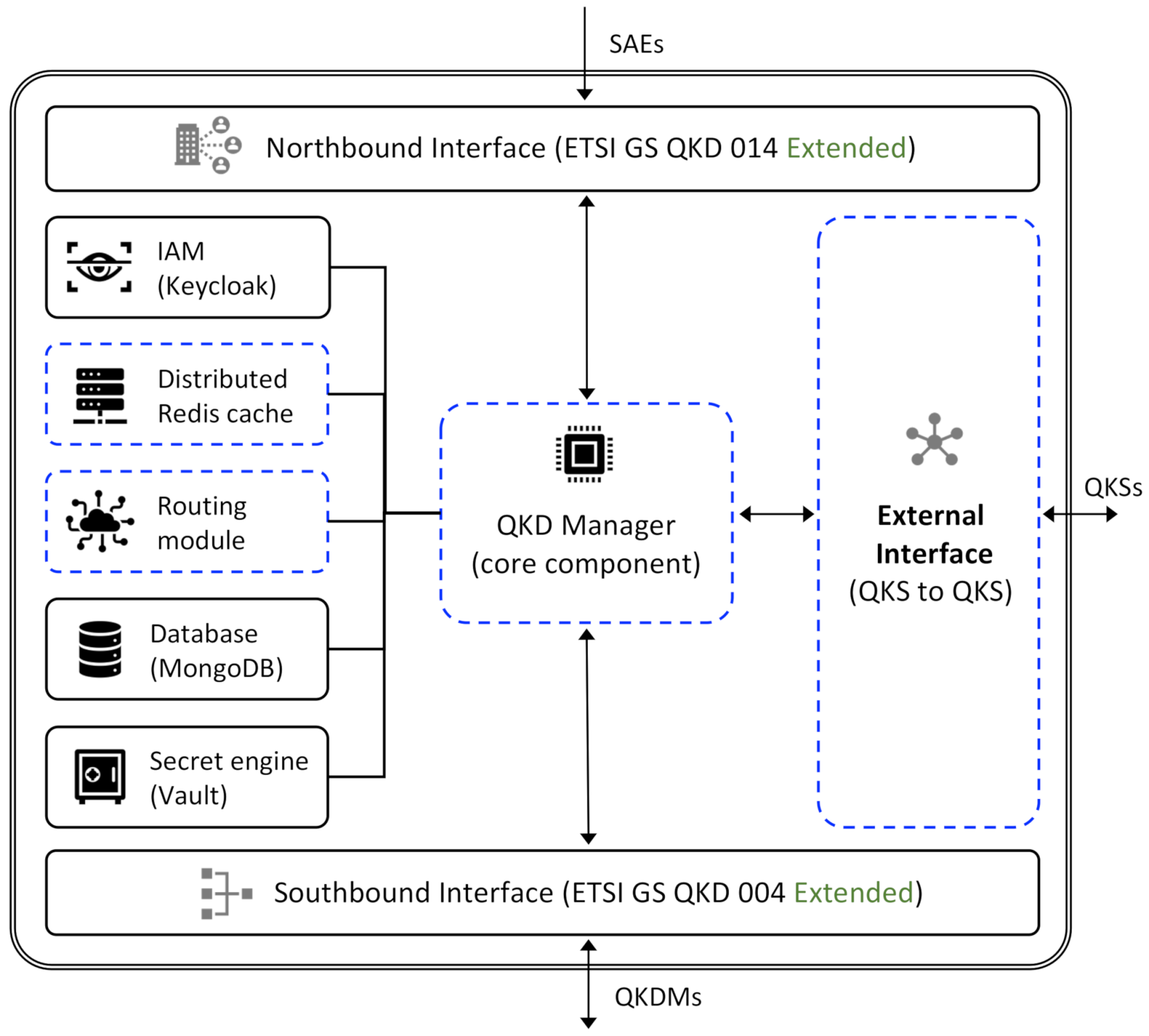
2.3. Quantum Software Stack and the ETSI Standards
- ETSI GS QKD 004 V2.1.1 [15]: the specification “QKD; Application Interfaces” describes the interface to the physical device; in our case, it could be associated with the Southbound Interface;
- ETSI GS QKD 014 V1.1.1 [16]: the specification “QKD; Protocol and data format of REST-based key delivery API” describes a high-level interface from the high-level application to a key manager. In our case, this corresponds to the Northbound Interface;
- ETSI GS QKD 015 V1.1.1 [17]: the specification “QKD; Control Interface for Software-Defined Networks” is recent, and it is a first attempt to standardize a relatively recent trend in QKD device management, namely Software-Defined Quantum Key Distribution (SD-QKD). The concept is to leverage an SDN controller who knows all the topology of the QKD network and manages all the QKD nodes accordingly in a centralized way. This approach could be beneficial in scenarios where the QKD network is switch-based, meaning the quantum channels could be adjusted using optical switches, which the SDN controller itself would control.
3. Quantum Software Stack 2.0
3.1. Asynchronous Approach
3.2. Trusted Repeaters
3.3. Routing
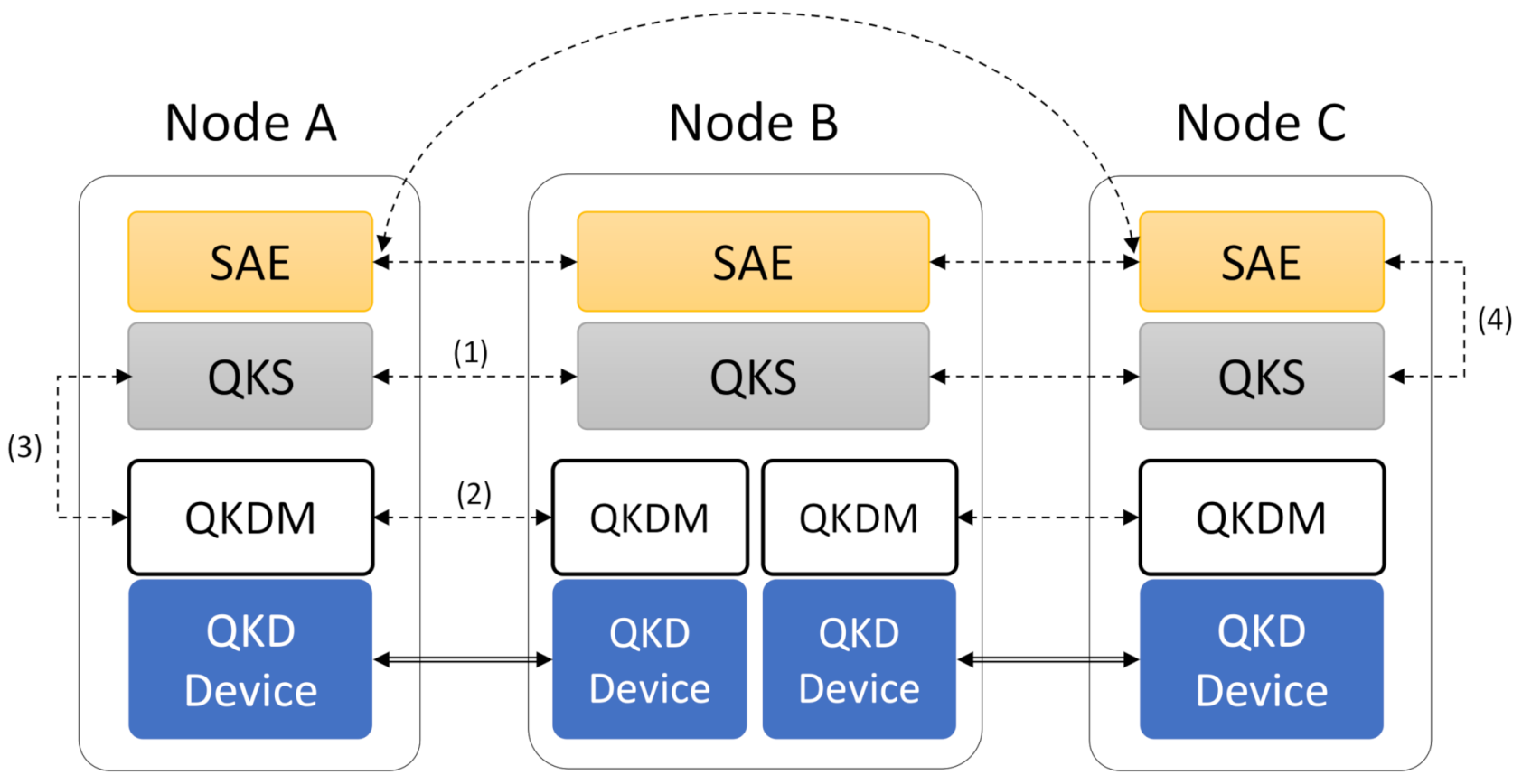
4. Integration in a Kubernetes Cluster
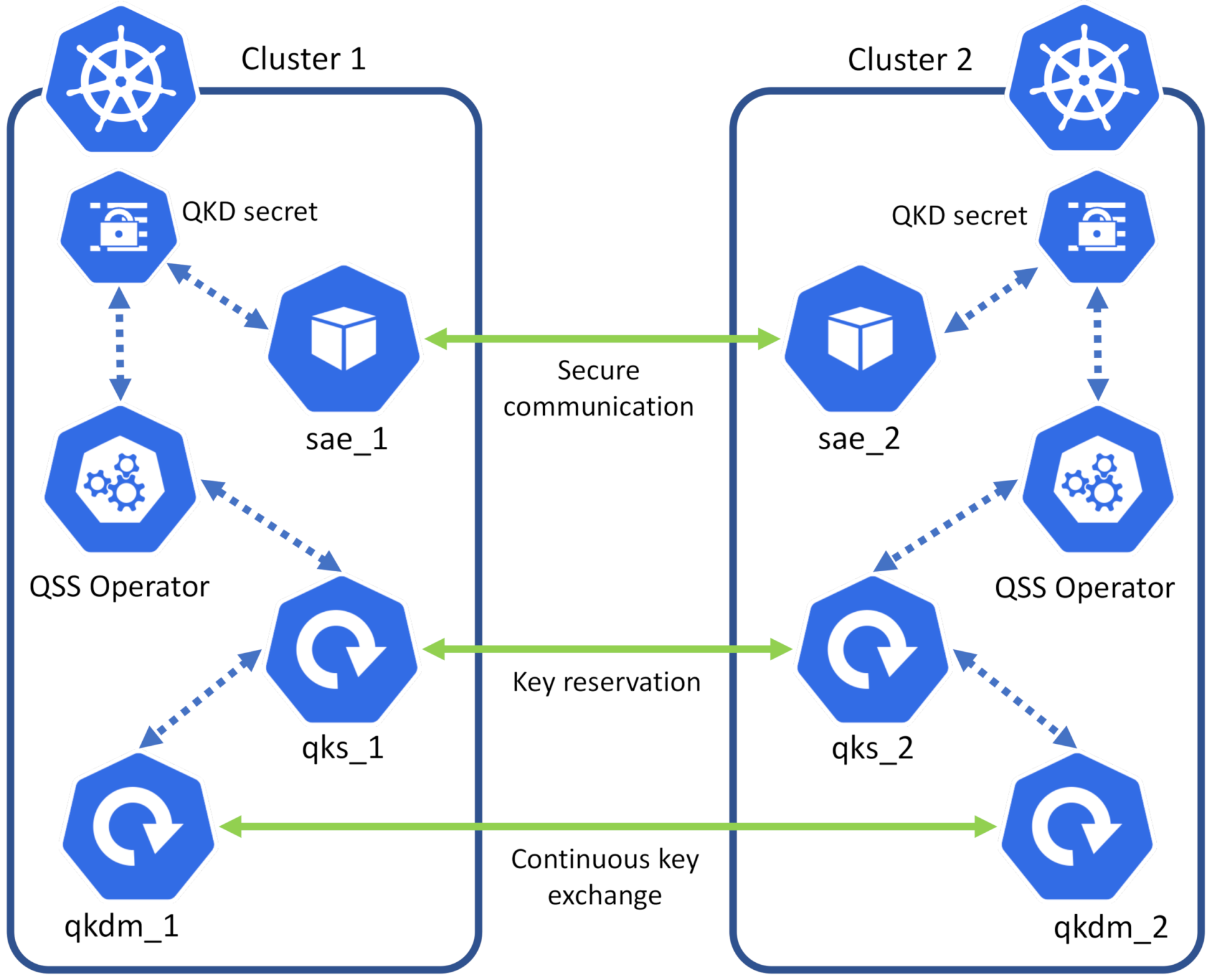
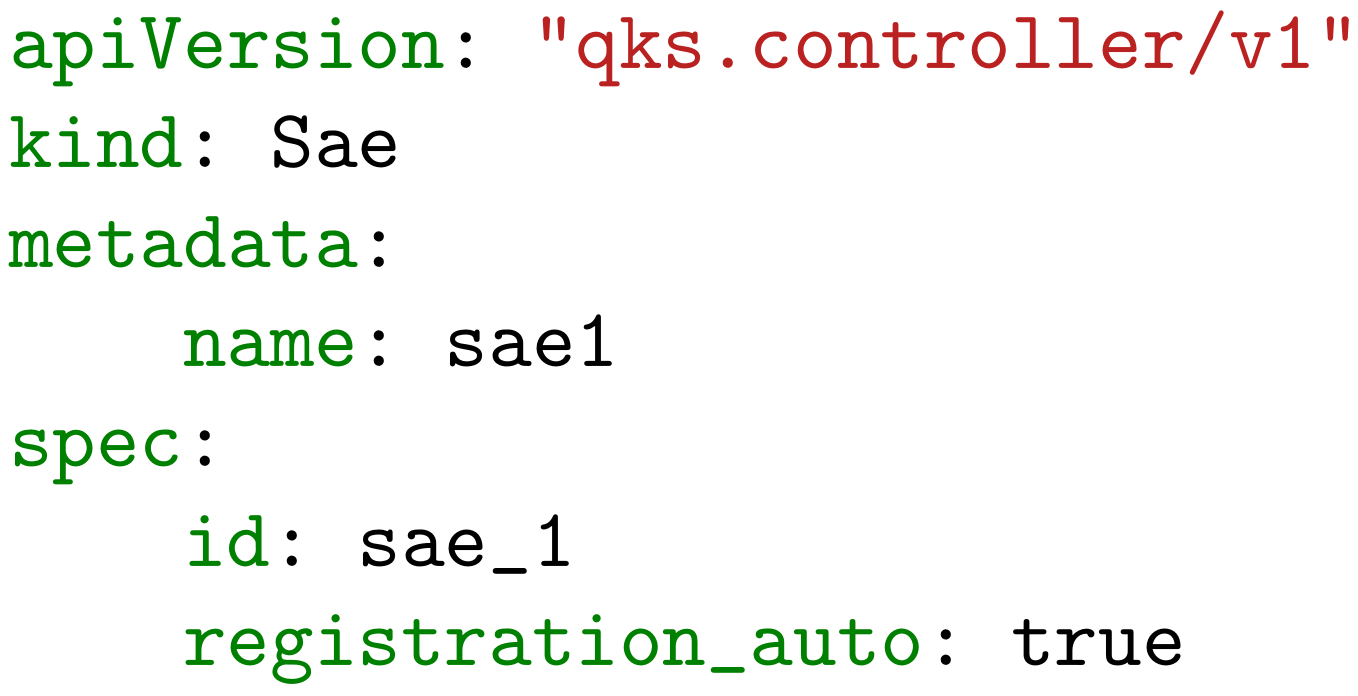
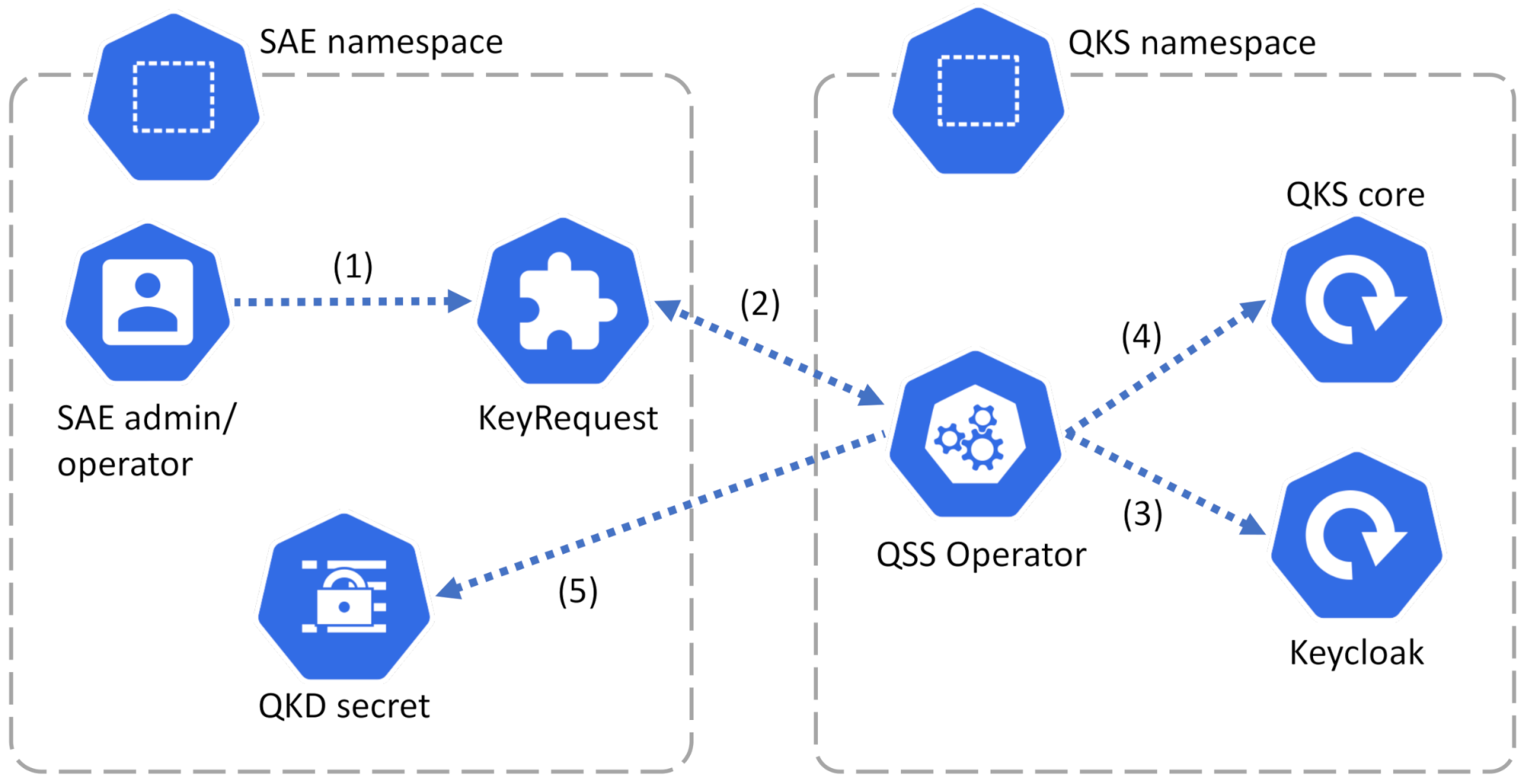
4.1. Quantum Software Stack Operator
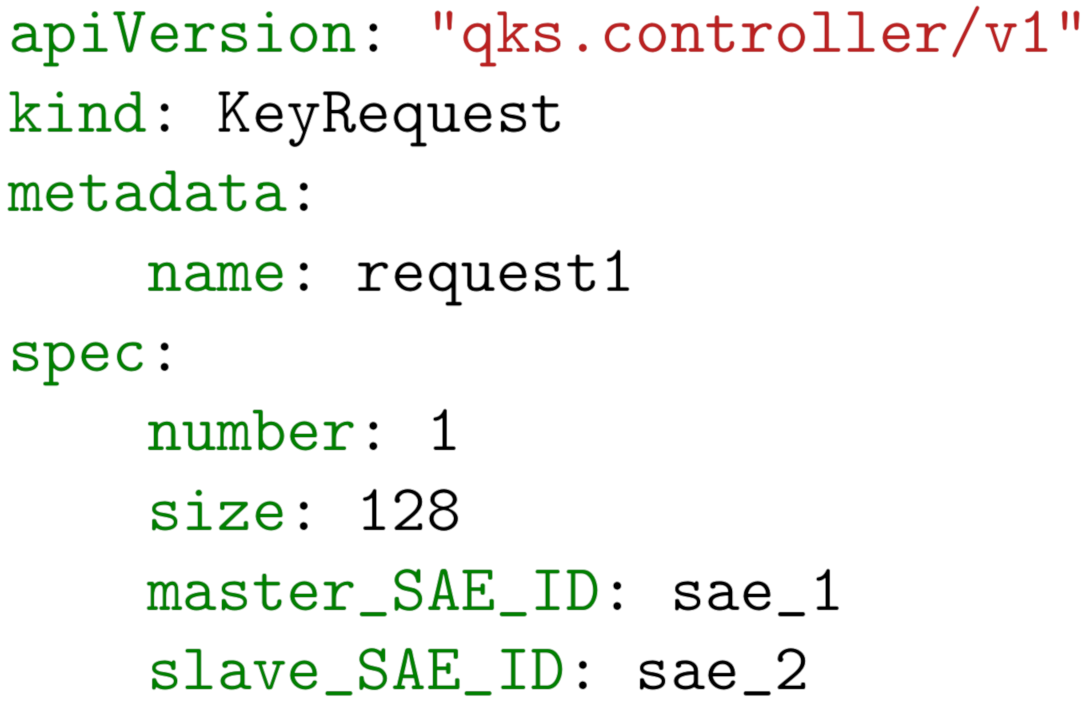
4.2. Resource Creation and Key Exchange
4.3. Applications to Suitable Use Cases
5. Related Work
6. Test and Validation
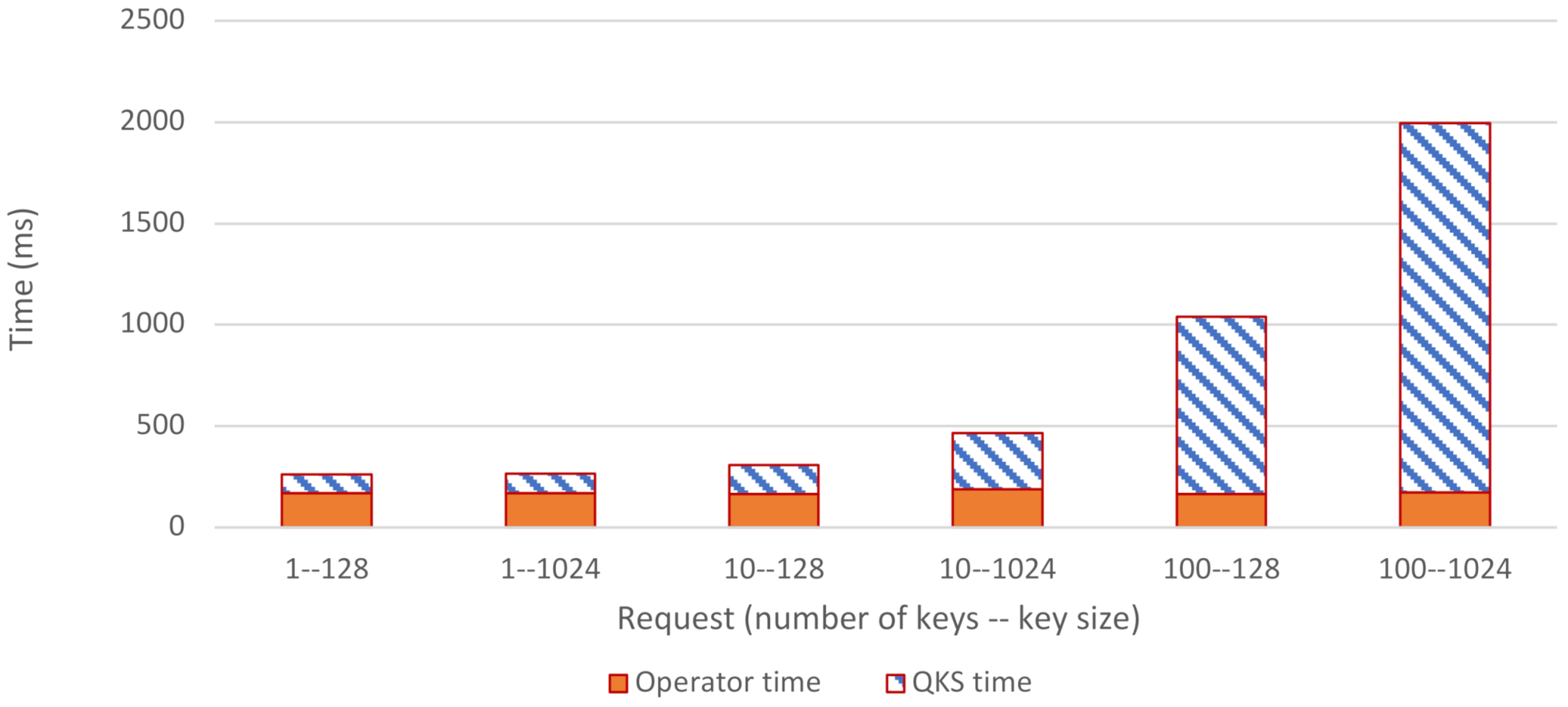
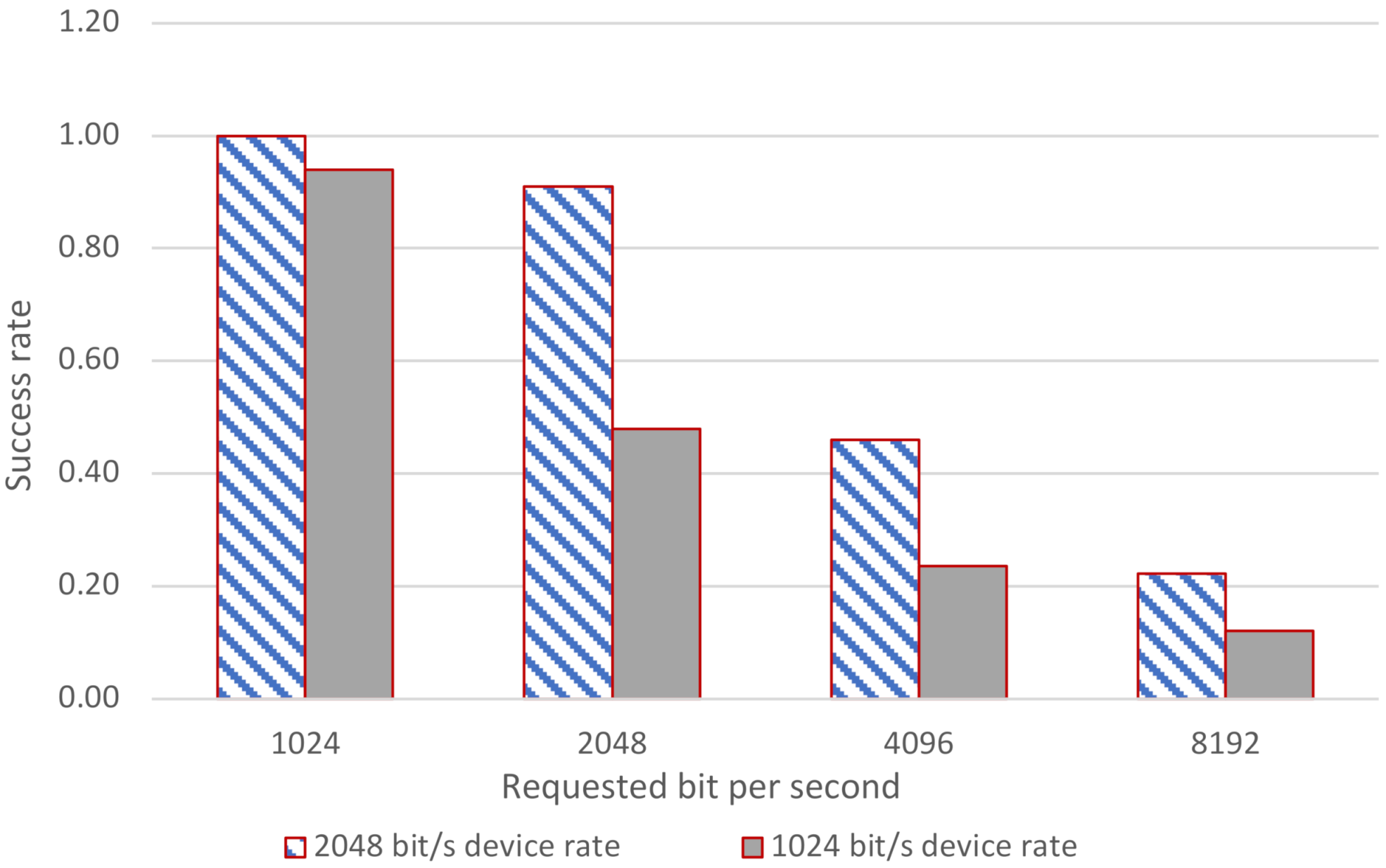
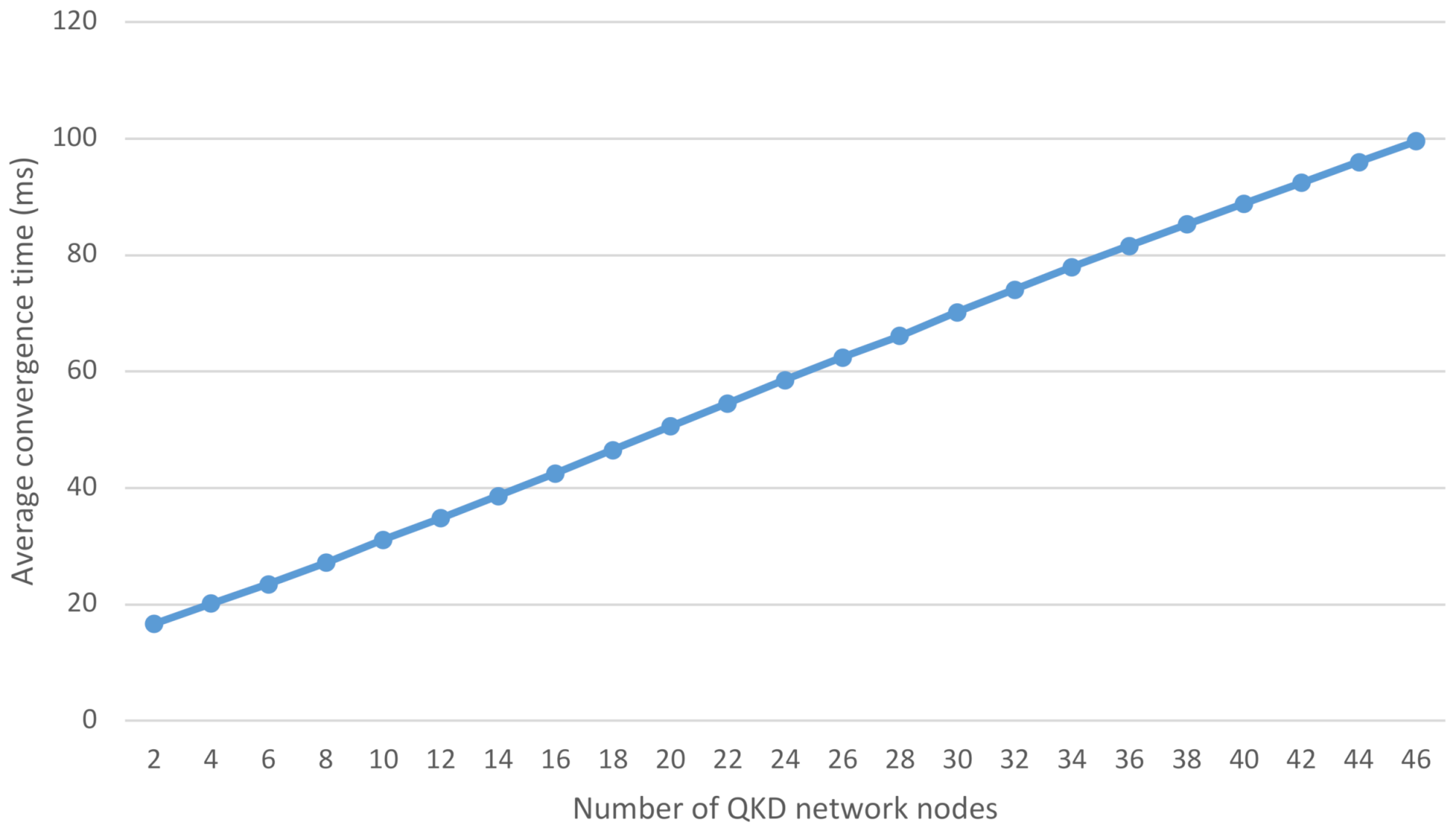
6.1. Key Exchange Time and Throughput
6.2. Routing
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| API | Application Programming Interface |
| CR | Custom Resource |
| CV-QKD | Continuous-Variable QKD |
| DV-QKD | Discrete-Variable QKD |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| ETSI | European Telecommunications Standards Institute |
| ETSI ISG | ETSI Industry Specification Group |
| KRP | Key Reservation Process |
| KS | Key Stream |
| GIL | Global Interpreter Lock |
| IoT | Internet of Things |
| IPsec | Internet Protocol Security |
| MDI-QKD | measurement-device-independent QKD |
| MH | Multi-Hop |
| mSAE | master SAE |
| LSA | Link State Advertisement |
| NFV | Network Functions Virtualisation |
| NIST | National Institute of Standards and Technology |
| OSPF | Open Shortest Path First |
| PQC | Post-Quantum Cryptography |
| PTP | Point-to-Point |
| QKD | Quantum Key Distribution |
| QKDM | QKD Module |
| QKRA | Quantum Key Reservation Approach |
| QKS | Quantum Key Server |
| QoS | Quality of Service |
| QRP | QKDM Registration Process |
| QSS | Quantum Software Stack |
| RM | Routing Module |
| RSA | Rivest Shamir Adleman |
| SAE | Secure Application Entity |
| SD-QKD | Software-Defined QKD |
| SDN | Software-Defined Networking |
| SIP | Session Intiation Protocol |
| sSAE | slave SAE |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| TLS-PSK | TLS pre-shared key ciphersuites |
| TF-QKD | twin-field QKD |
| VPN | Virtual Private Network |
| YAML | YAML Ain’t a Markup Language |
References
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Chen, L.; Chen, L.; Jordan, S.; Liu, Y.K.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. Report on Post-Quantum Cryptography; US Department of Commerce, National Institute of Standards and Technology: Washington, DC, USA, 2016; Volume 12. [CrossRef]
- Pedone, I.; Atzeni, A.; Canavese, D.; Lioy, A. Toward a Complete Software Stack to Integrate Quantum Key Distribution in a Cloud Environment. IEEE Access 2021, 9, 115270–115291. [Google Scholar] [CrossRef]
- Kubernetes Project. Available online: https://kubernetes.io (accessed on 7 April 2022).
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef] [Green Version]
- Lucamarini, M.; Patel, K.; Dynes, J.; Fröhlich, B.; Sharpe, A.; Dixon, A.; Yuan, Z.; Penty, R.; Shields, A. Efficient decoy-state quantum key distribution with quantified security. Opt. Express 2013, 21, 24550–24565. [Google Scholar] [CrossRef] [PubMed]
- ID Quantique Manufacturer. Available online: https://www.idquantique.com (accessed on 7 April 2022).
- Cerberis XG QKD System. Available online: https://www.idquantique.com/quantum-safe-security/products/cerberis-xg-qkd-system/ (accessed on 7 April 2022).
- Toshiba QKD systems. Available online: https://www.toshiba.co.jp/qkd/en/products.htm (accessed on 7 April 2022).
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y.; Chen, T.Y.; Wang, L.J.; Liang, H.; Shentu, G.L.; Wang, J.; Cui, K.; Yin, H.L.; Liu, N.L.; Li, L.; et al. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2013, 111, 130502. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- ETSI QKD Standards. Available online: https://www.etsi.org/committee/qkd (accessed on 7 April 2022).
- Keycloak Solution. Available online: https://www.keycloak.org (accessed on 7 April 2022).
- Quantum Key Distribution (QKD): Application Interface; Technical Report; European Telecommunications Standards Institute (ETSI): Nice, France, 2020.
- Quantum Key Distribution (QKD): Protocol and Data Format of REST-Based Key Delivery API; Technical Report; European Telecommunications Standards Institute (ETSI): Nice, France, 2019.
- Quantum Key Distribution (QKD): Control Interface for Software Defined Networks; Technical Report; European Telecommunications Standards Institute (ETSI): Nice, France, 2021.
- Global Interpreter Lock Documentation. Available online: https://wiki.python.org/moin/GlobalInterpreterLock (accessed on 7 April 2022).
- Quart Project. Available online: https://gitlab.com/pgjones/quart (accessed on 7 April 2022).
- Hypercorn Project. Available online: https://gitlab.com/pgjones/hypercorn (accessed on 7 April 2022).
- Mehic, M.; Niemiec, M.; Rass, S.; Ma, J.; Peev, M.; Aguado, A.; Martin, V.; Schauer, S.; Poppe, A.; Pacher, C.; et al. Quantum key distribution: A networking perspective. ACM Comput. Surv. 2020, 53, 1–41. [Google Scholar] [CrossRef]
- Peev, M.; Pacher, C.; Alléaume, R.; Barreiro, C.; Bouda, J.; Boxleitner, W.; Debuisschert, T.; Diamanti, E.; Dianati, M.; Dynes, J.; et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 2009, 11, 075001. [Google Scholar] [CrossRef] [Green Version]
- Moy, J. OSPF Version 2; RFC 2328, IETF; Ascend Communications, Inc.: Alameda, CA, USA, 1998. [Google Scholar] [CrossRef]
- Elliott, C.; Colvin, A.; Pearson, D.; Pikalo, O.; Schlafer, J.; Yeh, H. Current status of the DARPA quantum network. In Proceedings of the Quantum Information and computation III. International Society for Optics and Photonics, Orlando, FL, USA, 25 May 2005; Volume 5815, pp. 138–149. [Google Scholar] [CrossRef]
- Maurhart, O. QKD networks based on Q3P. In Applied Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2010; pp. 151–171. [Google Scholar] [CrossRef]
- Etcd Project. Available online: https://etcd.io (accessed on 7 April 2022).
- Sasaki, M. Quantum Key Distribution and Its Applications. IEEE Secur. Priv. 2018, 16, 42–48. [Google Scholar] [CrossRef]
- Conrad, A.; Isaac, S.; Cochran, R.; Sanchez-Rosales, D.; Wilens, B.; Gutha, A.; Rezaei, T.; Gauthier, D.J.; Kwiat, P. Drone-based quantum key distribution: QKD. In Proceedings of the Free-Space Laser Communications XXXIII; International Society for Optics and Photonics: Bellingham, WA, USA, 2021; Volume 11678, p. 116780. [Google Scholar] [CrossRef]
- Istio Project. Available online: https://istio.io (accessed on 7 April 2022).
- Zhang, P.; Wang, L.; Wang, W.; Fu, K.; Wang, J. A blockchain system based on quantum-resistant digital signature. Secur. Commun. Netw. 2021, 2021. [Google Scholar] [CrossRef]
- Ikeda, K. qBitcoin: A peer-to-peer quantum cash system. In Proceedings of the Science and Information Conference; Springer: Berlin/Heidelberg, Germany, 2018; pp. 763–771. [Google Scholar] [CrossRef] [Green Version]
- Allende, M.; León, D.L.; Cerón, S.; Leal, A.; Pareja, A.; Da Silva, M.; Pardo, A.; Jones, D.; Worrall, D.; Merriman, B.; et al. Quantum-resistance in blockchain networks. arXiv 2021, arXiv:2106.06640. [Google Scholar] [CrossRef]
- Hyperledger Project. Available online: https://www.hyperledger.org (accessed on 7 April 2022).
- K3s Project. Available online: https://k3s.io (accessed on 7 April 2022).
- Cheng, X.; Sun, Y.; Ji, Y. A QoS-supported scheme for quantum key distribution. In Proceedings of the 2011 International Conference on Advanced Intelligence and Awareness Internet (AIAI 2011), Shenzhen, China, 28–30 October 2011; pp. 220–224. [Google Scholar] [CrossRef]
- Apostolopoulos, G.; Guerin, R.; Kamat, S. Implementation and performance measurements of QoS routing extensions to OSPF. In Proceedings of the IEEE INFOCOM ’99. Conference on Computer Communications. Proceedings. Eighteenth Annual Joint Conference of the IEEE Computer and Communications Societies. The Future is Now (Cat. No.99CH36320), New York, NY, USA, 21–25 March 1999; Volume 2, pp. 680–688. [Google Scholar] [CrossRef]
- Mehic, M.; Maurhart, O.; Rass, S.; Komosny, D.; Rezac, F.; Voznak, M. Analysis of the public channel of quantum key distribution link. IEEE J. Quantum Electron. 2017, 53, 17140300. [Google Scholar] [CrossRef]
- Aguado, A.; Lopez, V.; Lopez, D.; Peev, M.; Poppe, A.; Pastor, A.; Folgueira, J.; Martin, V. The engineering of software-defined quantum key distribution networks. IEEE Commun. Mag. 2019, 57, 20–26. [Google Scholar] [CrossRef] [Green Version]
- Aguado, A.; Hugues-Salas, E.; Haigh, P.A.; Marhuenda, J.; Price, A.B.; Sibson, P.; Kennard, J.E.; Erven, C.; Rarity, J.G.; Thompson, M.G.; et al. Secure NFV orchestration over an SDN-controlled optical network with time-shared quantum key distribution resources. J. Light. Technol. 2017, 35, 1357–1362. [Google Scholar] [CrossRef] [Green Version]
- QSS Source Code. Available online: https://github.com/ignaziopedone/qkd-keyserver (accessed on 7 April 2022).
- QKDM Source Code. Available online: https://github.com/ignaziopedone/qkd-module (accessed on 7 April 2022).


| Name | Type | Description |
|---|---|---|
| SAE_ID | String | name used to identify the destination SAE |
| next_hop | String | ID of the next QKS in the path to the destination SAE |
| dest | String | ID of the QKS of the destination SAE |
| cost | Integer | the cost associated to the path from the current SAE to the destination |
| length | Integer | number of nodes in the path to reach the destination |
| Field Name | Description |
|---|---|
| version | protocol version |
| type | type of information carried, S for SAEs and K for QKDM links |
| source | QKS source ID, address and port |
| routing | source routing module address and port |
| forwarder | ID of the last QKS which forwarded the packet |
| neighbors | list of connected SAEs or active QKDM links, based on the type field |
| timestamp | packet creation time |
| authentication | data for authentication and integrity checks |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pedone, I.; Lioy, A. Quantum Key Distribution in Kubernetes Clusters. Future Internet 2022, 14, 160. https://doi.org/10.3390/fi14060160
Pedone I, Lioy A. Quantum Key Distribution in Kubernetes Clusters. Future Internet. 2022; 14(6):160. https://doi.org/10.3390/fi14060160
Chicago/Turabian StylePedone, Ignazio, and Antonio Lioy. 2022. "Quantum Key Distribution in Kubernetes Clusters" Future Internet 14, no. 6: 160. https://doi.org/10.3390/fi14060160
APA StylePedone, I., & Lioy, A. (2022). Quantum Key Distribution in Kubernetes Clusters. Future Internet, 14(6), 160. https://doi.org/10.3390/fi14060160






