Ransomware-Resilient Self-Healing XML Documents
Abstract
1. Introduction
- A self-healing version-aware ransomware recovery framework for XML-based documents is identified.
- The proposed framework is evaluated according to different performance metrics, including storage overhead, CPU utilization, and memory requirements for about 500 XML-based documents of various sizes, ranging from a few kilobytes to 30 Megabytes.
2. Background
2.1. Ransomware
2.1.1. Ransomware Lifecycle
- Ransomware distribution: Like other malicious software programs, Ransomware uses social-engineering strategies to seduce victims to click links that lead to ridiculous content or download a malicious dropper or payload that causes infection.
- Infection: The malicious code is downloaded at this stage, and the execution of the code begins. At this stage, a victim’s machine will have been compromised by Ransomware, with the underlying files still not yet encrypted. Encryption is a reversible process, involving highly intensive CPU calculations operations. Encryption does not readily happen in a typical ransomware attack as it requires time for data evaluation by the malware and the scope for data encryption. Once this stage becomes active, all the automatic detection systems will have stopped. The firewall, proxy, antivirus, and intrusion detection programs will have been compromised to allow all malicious communications to take place, ultimately putting the ransomware in total control.
- C2 Communications: The malicious code continues to maintain access to its command-and-control server (C2) at this stage. Here, an attacker manages a C2 server and begins to send commands to the compromised system. The primary C2 communications objective with Ransomware entails the acquisition of an encryption key. Once that is complete, different systems are changed, and persistence is determined.
- File search-scanning: This is when things start to slow down a bit. The malware searches the computer to find files to encrypt first. It also scans for cloud data that are synced through folders and shown as local data. Then it starts searching for file shares. This may take time, depending on how much activity there is across the network. The goal is to examine the available information and determine the victim’s level of permissions (e.g., list, published, delete).
- Encryption: The encryption starts once all data have been inventoried. Local file encryption may take minutes, but it may take several hours to encrypt a network file; this is because data on network file shares are locally copied and encrypted in most ransomware attacks. Then this is followed by uploading the encrypted files and removing the original ones. This phase takes a bit of extra time.
- Ransom demand: At this stage, a victim will receive a ransom message instructing them to render ransom; the Ransomware message is issued immediately once encryption has taken place. The Ransomware shows a screen that instructs its victim to pay before criminals delete the key to decrypt the files. The last function usually performed by Ransomware is to end and uninstall itself from a victim’s machine. At this point, the hackers are ready to receive the ransom to their Bitcoin wallet.
2.1.2. Ransomware Categories
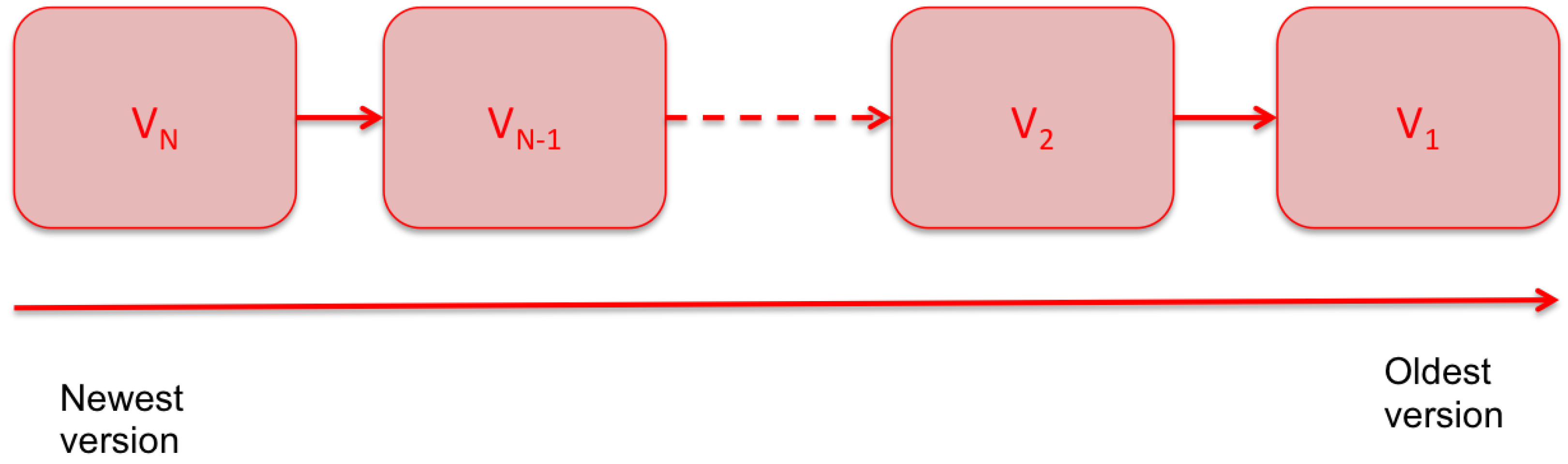
2.2. Version-Control System (VCS)
3. Related Work
3.1. Ransomware Analysis
3.2. Ransomware Detection
3.3. Recovery from Ransomware
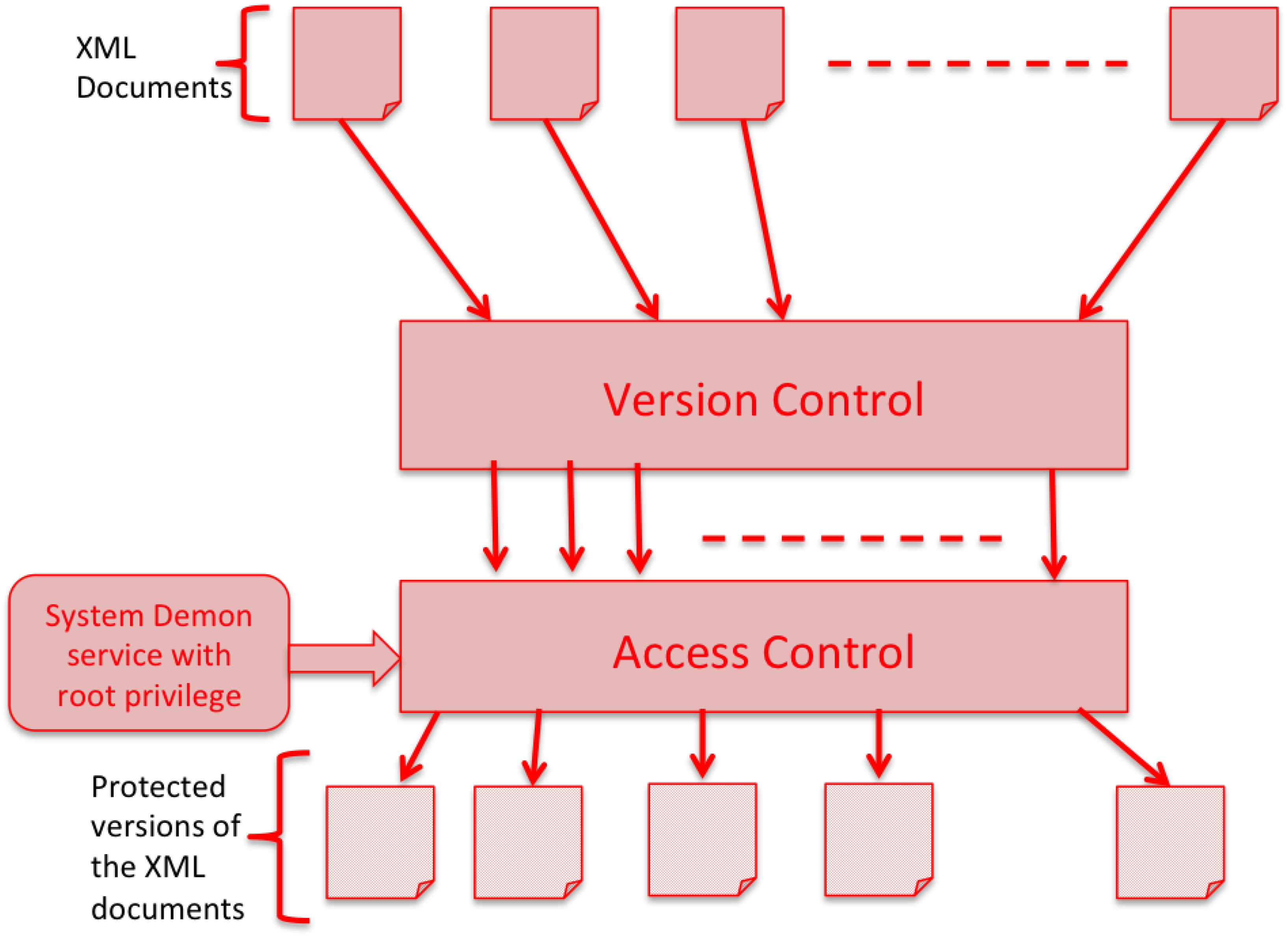
4. Proposed Version-Aware Ransomware Recovery Framework
4.1. Details of the Proposed SH-VARR Framework
4.1.1. Version-Control Module
- Step 1: Changing the .odt/.docx extension of the file to .zip.
- Step 2: Extracting the document archive. By unzipping the resulting .zip file, we obtain the document structure containing XML-based files and directories generated originally by Microsoft Word or LibreOffice. This includes configurations, meta information, content, settings, etc.
- Step 3: Adding a new XML file (link.XML) to the file archive that contains an absolute URL (i.e., a link) of the file version to be created in step 5.
- Step 4: Compressing the resulting ZIP archive, including the link.XML file.
- Step 5: Copying the resulting .zip file to a predefined directory that stores the protected versions. Access control permissions are added by the access control module as discussed in Section 4.1.2.
- Step 6: Changing the .zip extension of the file to .odt.
4.1.2. Access-Control Module
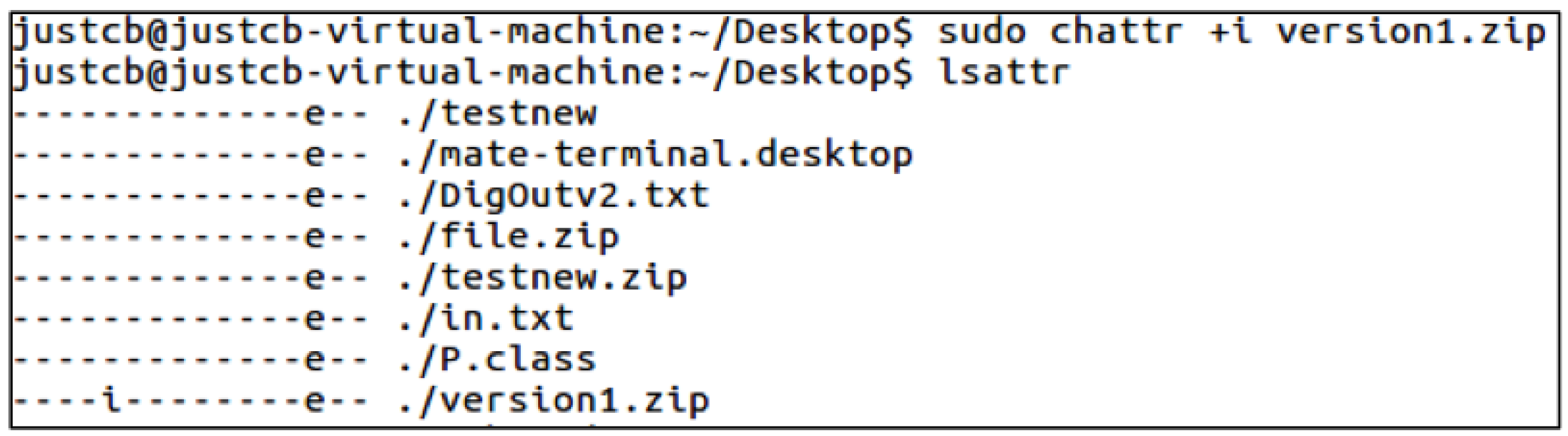
4.2. Recovery from Ransomware Attack
- Removing the immutable flag (i) attribute. This is achieved by performing the command with root privileges only:$chattr -i file.dot.
- Changing the file name extension from .zip to .odt for Linux or .docx for a Windows environment.
4.3. Implementation Challenges and Limitations
- The proposed approach assumes a daemon is running with root privileges to keep versions protected.
- Under the Windows environment, and to ensure that our framework was well in place, we implemented a Microsoft office plugin working as a version-control system by keeping a complete snapshot of the active Word document inside the document itself upon document closure. A background process goes through iterations to span all files inside a directory or folder by calling this function. The main challenge here deals primarily with applying the permissions to the created version of each file; this is so because, under a Windows operating system, the read–write operation does not fall under permissions, but file attributes, which will be readily lost after compressing the file archive.
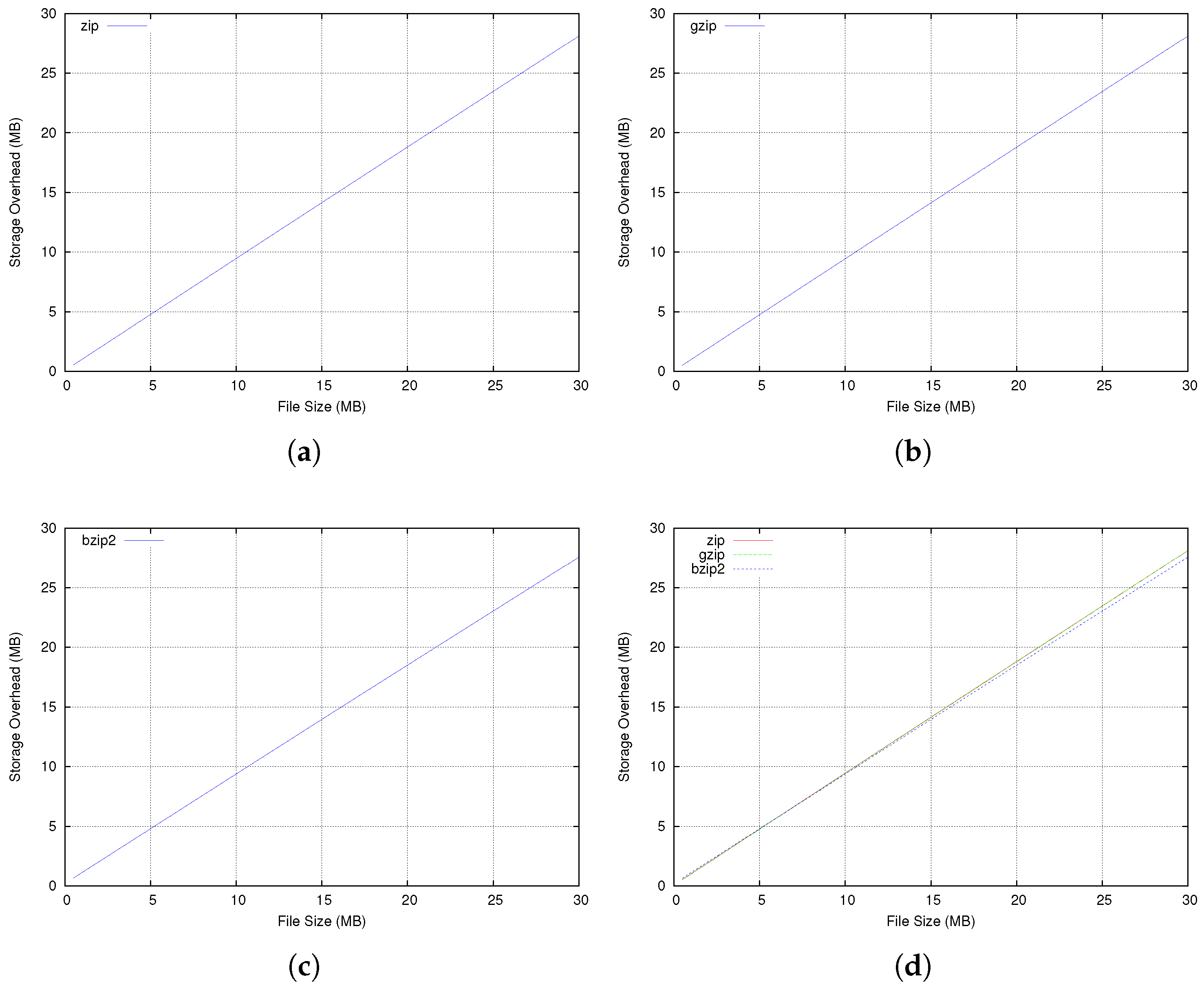
5. Performance Evaluation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mashtalyar, N.; Ntaganzwa, U.N.; Santos, T.; Hakak, S.; Ray, S. Social Engineering Attacks: Recent Advances and Challenges, HCI for Cybersecurity, Privacy and Trust; Springer: New York, NY, USA, 2021; pp. 417–431. [Google Scholar]
- Mukhopadhyay, I. Cyber Threats Landscape Overview Under the New Normal. In ICT Analysis and Applications; Fong, S., Dey, N., Joshi, A., Eds.; Lecture Notes in Networks and Systems; Springer: Singapore, 2022; Volume 314. [Google Scholar] [CrossRef]
- Djenna, A.; Harous, S.; Saidouni, D.E. Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure. Appl. Sci. 2021, 11, 4580. [Google Scholar] [CrossRef]
- Jang-Jaccard, J.; Nepal, S. A survey of emerging threats in cybersecurity. J. Comput. Syst. Sci. 2014, 80, 973–993. [Google Scholar] [CrossRef]
- Zong, S.; Ritter, A.; Mueller, G.; Wright, E. Analyzing the Perceived Severity of Cybersecurity Threats Reported on Social Media. arXiv 2019, arXiv:1902.10680. [Google Scholar]
- Rudd, E.; Rozsa, A.; Günther, M.; Boult, T. A Survey of Stealth Malware Attacks, Mitigation Measures, and Steps Toward Autonomous Open World Solutions. IEEE Commun. Surv. Tutor. 2017, 19, 1145–1172. [Google Scholar] [CrossRef]
- Nakashima, E.U.S. Aims to Thwart Ransomware Attacks by Cracking Down on Crypto Payments. The Washington Post. 2021. Available online: https://www.washingtonpost.com/business/2021/09/17/biden-sanctions-ransomware-crypto (accessed on 19 October 2021).
- Kumar, M.; Ben-Othman, J.; Srinivasagan, K. An Investigation on Wannacry Ransomware and its Detection. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 1–6. [Google Scholar]
- Stallings, W. Network Security Essentials: Applications and Standards; Pearson: London, UK, 2016. [Google Scholar]
- Peter, A.; Peter, S.; Van Ekert, L. An ontology for network security attacks. In Proceedings of the 2nd Asian Applied Computing Conference (AACC’04), LNCS 3285; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Richardson, R.; North, M. Ransomware: Evolution, mitigation and prevention. Int. Manag. Rev. 2017, 13, 10. [Google Scholar]
- Everett, C. Ransomware: To pay or not to pay? Comput. Fraud Secur. 2016, 2016, 8–12. [Google Scholar] [CrossRef]
- Yaqoob, I.; Ahmed, E.; Rehman, M.; Ahmed, A.; Al-garadi, M.; Imran, M.; Guizani, M. The rise of ransomware and emerging security challenges in the Internet of Things. Comput. Netw. 2017, 129, 444–458. [Google Scholar] [CrossRef]
- Shashank, M.; Agrawal, A.K. Multi Pronged Approach for Ransomware Analysis. Available online: https://deliverypdf.ssrn.com/delivery.php?ID=529106093087077008125066087007008126061069029053059024023024048119007044109100058011016111014009004006028061086001098107006013106127099006095000116044119113035023073115003083030043113078009059098044124031019004068007115065011000084085080125073117006075066113004076094086068087090001095082&EXT=pdf&INDEX=TRUE (accessed on 10 March 2022).
- What You Need to Know about the WannaCry Ransomware. Available online: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/wannacry-ransomware-attack (accessed on 10 March 2022).
- Leong, R.; Beek, C.; Cochin, C.; Cowie, N.; Schmugar, C. Understanding Ransomware and Strategies to Defeat It. 2016. Available online: https://www.mcafee.com/enterprise/en-us/assets/white-papers/wp-understanding-ransomware-strategies-defeat.pdf (accessed on 10 March 2022).
- Al-rimy, B.; Maarof, M.; Shaid, S. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Young, A.; Yung, M. Cryptovirology: The birth, neglect, and explosion of ransomware. Commun. ACM 2017, 60, 24–26. [Google Scholar] [CrossRef]
- Young, A.; Yung, M. Cryptovirology: Extortion-based security threats and countermeasures. In Proceedings of the 1996 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 6–8 May 1996; pp. 129–140. [Google Scholar]
- Luo, X.; Liao, Q. Awareness education as the key to ransomware prevention. Inf. Syst. Secur. 2007, 16, 195–202. [Google Scholar] [CrossRef]
- Gostev, A.; Unuchek, R.; Garnaeva, M.; Makrushin, D.; Ivanov, A. IT Threat Evolution in Q1 2016. Kapersky 2015 Report, Kapersky L. 2016. Available online: https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/07192617/Q1_2016_MW_report_FINAL_eng.pdf (accessed on 10 March 2022).
- Thao, C.; Munson, E. Version-aware XML documents. In Proceedings of the 11th ACM Symposium on Document Engineering, Mountain View, CA, USA, 19–22 September 2011; pp. 97–100. [Google Scholar]
- Coakley, S.; Mischka, J.; Thao, C. Version-Aware Word Documents. In Proceedings of the 2nd International Workshop on (Document) Changes: Modeling, Detection, Storage and Visualization, Fort Collins, CO, USA, 16 September 2014; p. 2. [Google Scholar]
- Shatnawi, A.; Ethan, V.M.; Cheng, T. Maintaining integrity and non-repudiation in secure offline documents. In Proceedings of the 2017 ACM Symposium on Document Engineering, Valletta, Malta, 4–7 September 2017; pp. 59–62. [Google Scholar]
- Shatnawi, A.S.; Ethan, V.M. Enhanced Automated Policy Enforcement eXchange framework (eAPEX). In Proceedings of the ACM Symposium on Document Engineering 2019, Berlin, Germany, 23–26 September 2019; pp. 1–4. [Google Scholar]
- Gazet, A. Comparative analysis of various ransomware virii. J. Comput. Virol. 2010, 6, 77–90. [Google Scholar] [CrossRef]
- Kharraz, A.; Kirda, E. Redemption: Real-time protection against ransomware at end-hosts. In International Symposium on Research in Attacks, Intrusions, and Defenses; Springer: Cham, Switzerland, 2017; pp. 98–119. [Google Scholar]
- Bayer, U.; Kruegel, C.; Kirda, E. TTAnalyze: A Tool for Analyzing Malware. 2006. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.60.7584&rep=rep1&type=pdf (accessed on 10 March 2022).
- Cabaj, K.; Mazurczyk, W. Using software-defined networking for ransomware mitigation: The case of cryptowall. IEEE Netw. 2016, 30, 14–20. [Google Scholar] [CrossRef]
- Yen, T.; Heorhiadi, V.; Oprea, A.; Reiter, M.; Juels, A. An epidemiological study of malware encounters in a large enterprise. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 1117–1130. [Google Scholar]
- Zhang, T.; Antunes, H.; Aggarwal, S. Defending connected vehicles against malware: Challenges and a solution framework. IEEE Internet Things J. 2014, 1, 10–21. [Google Scholar] [CrossRef]
- Hampton, N.; Baig, Z.; Zeadally, S. Ransomware behavioural analysis on windows platforms. J. Inf. Secur. Appl. 2018, 40, 44–51. [Google Scholar] [CrossRef]
- Subedi, K.; Budhathoki, D.; Dasgupta, D. Forensic analysis of ransomware families using static and dynamic analysis. In Proceedings of the 2018 IEEE Security And Privacy Workshops (SPW), San Francisco, CA, USA, 24 May 2018; pp. 180–185. [Google Scholar]
- Mansfield-Devine, S. Leaks and ransoms–the key threats to healthcare organisations. Netw. Secur. 2017, 2017, 14–19. [Google Scholar] [CrossRef]
- Kolodenker, E.; Koch, W.; Stringhini, G.; Egele, M. PayBreak: Defense against cryptographic ransomware. In Proceedings of the 2017 ACM on Asia Conference on Computer And Communications Security, Abu Dhabi, United Arab Emirates, 2–6 April 2017; pp. 599–611. [Google Scholar]
- Continella, A.; Guagnelli, A.; Zingaro, G.; De Pasquale, G.; Barenghi, A.; Zanero, S.; Maggi, F. ShieldFS: A self-healing, ransomware-aware filesystem. In Proceedings of the 32nd Annual Conference on Computer Security Applications, Los Angeles, CA, USA, 5–8 December 2016; pp. 336–347. [Google Scholar]
- Gomez-Hernandez, J.; Gonzalez, L.; Garcia-Teodoro, P. R-Locker: Thwarting ransomware action through a honeyfile-based approach. Comput. Secur. 2018, 73, 389–398. [Google Scholar] [CrossRef]
- Sathyanarayan, V.; Kohli, P.; Bruhadeshwar, B. Signature generation and detection of malware families. In Australasian Conference on Information Security And Privacy; Springer: Berlin/Heidelberg, Germany, 2008; pp. 336–349. [Google Scholar]
- Scaife, N.; Carter, H.; Traynor, P.; Butler, K. Cryptolock (and drop it): Stopping ransomware attacks on user data. In Proceedings of the 2016 IEEE 36th International Conference On Distributed Computing Systems (ICDCS), Nara, Japan, 27–30 June 2016; pp. 303–312. [Google Scholar]
- Shafiq, M.; Khayam, S.; Farooq, M. Improving accuracy of immune-inspired malware detectors by using intelligent features. In Proceedings of the 10th Annual Conference On Genetic And Evolutionary Computation, Atlanta, GA, USA, 12–16 July 2008; pp. 119–126. [Google Scholar]
- Yüksel, Ö.; Hartog, J.; Etalle, S. Towards useful anomaly detection for back office networks. In International Conference on Information Systems Security; Springer: Cham, Switzerland, 2016; pp. 509–520. [Google Scholar]
- Hurtuk, J.; Chovanec, M.; Kičina, M.; Billik, R. Case Study of Ransomware Malware Hiding Using Obfuscation Methods. In Proceedings of the 2018 16th International Conference on Emerging ELearning Technologies and Applications (ICETA), Stary Smokovec, Slovakia, 15–16 November 2018; pp. 215–220. [Google Scholar]
- Lim, C.; Ramli, K. Mal-ONE: A unified framework for fast and efficient malware detection. In Proceedings of the 2014 2nd International Conference on Technology, Informatics, Management, Engineering & Environment, Bandung, Indonesia, 19–21 August 2014; pp. 1–6. [Google Scholar]
- Poudyal, S.; Subedi, K.; Dasgupta, D. A Framework for Analyzing Ransomware using Machine Learning. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; pp. 1692–1699. [Google Scholar]
- Cusack, G.; Michel, O.; Keller, E. Machine learning-based detection of ransomware using sdn. In Proceedings of the 2018 ACM International Workshop on Security In Software Defined Networks & Network Function Virtualization, Tempe, AZ, USA, 21 March 2018; pp. 1–6. [Google Scholar]
- Andronio, N.; Zanero, S.; Maggi, F. Heldroid: Dissecting and detecting mobile ransomware. In International Symposium On Recent Advances in Intrusion Detection; Springer: Cham, Switzerland, 2015; pp. 382–404. [Google Scholar]
- Stokkel, M. Ransomware Detection with bro. Talk at BroCon ‘16. Available online: https://old.zeek.org/brocon2016/brocon2016_abstracts.html#toc-top (accessed on 20 January 2020).
- Cuzzocrea, A.; Martinelli, F.; Mercaldo, F. A Novel Structural-Entropy-based Classification Technique for Supporting Android Ransomware Detection and Analysis. In Proceedings of the 2018 IEEE International Conference On Fuzzy Systems (FUZZ-IEEE), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–7. [Google Scholar]
- Takeuchi, Y.; Sakai, K.; Fukumoto, S. Detecting ransomware using support vector machines. In Proceedings of the 47th International Conference on Parallel Processing Companion, Eugene, OR, USA, 13–16 August 2018; p. 1. [Google Scholar]
- Urooj, U.; Al-rimy, B.A.S.; Zainal, A.; Ghaleb, F.A.; Rassam, M.A. Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Appl. Sci. 2022, 12, 172. [Google Scholar] [CrossRef]
- Zimba, A.; Wang, Z.; Simukonda, L. Towards data resilience: The analytical case of crypto ransomware data recovery techniques. Int. J. Inf. Technol. Comput. Sci. 2018, 10, 40–51. [Google Scholar] [CrossRef][Green Version]
- Berrueta Irigoyen, E.; Morató Osés, D.; Magaña Lizarrondo, E.; Izal Azcárate, M. Ransomware encrypted your files but you restored them from network traffic. In Proceedings of the 2018 2nd Cyber Security in Networking Conference, CSnet 2018, Paris, France, 24–26 October 2018. [Google Scholar]
- Thomas, J.; Galligher, G. Improving backup system evaluations in information security risk assessments to combat ransomware. Comput. Inf. Sci. 2018, 11. [Google Scholar] [CrossRef]
- Subedi, K.P.; Budhathoki, D.R.; Chen, B.; Dasgupta, D. RDS3: Ransomware defense strategy by using stealthily spare space. In Proceedings of the 2017 IEEE Symposium Series on Computational Intelligence (SSCI), Honolulu, HI, USA, 27 November–1 December 2017; pp. 1–8. [Google Scholar]
- Martínez-García, H.A. Facing ransomware: An approach with private cloud and sentinel software. Comput. Fraud. Secur. 2020, 2020, 16–19. [Google Scholar] [CrossRef]
- Kim, G.; Kim, S.; Kang, S.; Kim, J. A Method for Decrypting Data Infected with Hive Ransomware. arXiv 2022, arXiv:2202.08477. [Google Scholar]
- Ye, H.; Dai, W.; Huang, X. File Backup to Combat Ransomware. U.S. Patent 9,317,686, 19 April 2016. [Google Scholar]
- 90 Percent of Ransomware Can Execute without Administrator Rights-Business Reporter. Available online: https://engageemployee.com/90-per-cent-ransomware-can-execute-without-administrator-rights/ (accessed on 30 December 2019).





| Category | Symptoms | Example |
|---|---|---|
| Locker | prevents users from accessing their files and data | W32. Rasith Data |
| Crypto | Encrypts victims’ files, file contents, and file names without notification by utilizing different cryptographic methods and notifies victims that their data have been encrypted, forcing them to pay a ransom to decrypt files. | WannaCry |
| Double extortion | Encrypts files and asks victims to pay a ransom. Attackers threaten to publicize stolen data if their demands are not met. | Maze |
| RaaS | Involves perpetrators leasing access to ransomware from the ransomware author, who delivers it as a paid service. | Locky |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Dwairi, M.; Shatnawi, A.S.; Al-Khaleel, O.; Al-Duwairi, B. Ransomware-Resilient Self-Healing XML Documents. Future Internet 2022, 14, 115. https://doi.org/10.3390/fi14040115
Al-Dwairi M, Shatnawi AS, Al-Khaleel O, Al-Duwairi B. Ransomware-Resilient Self-Healing XML Documents. Future Internet. 2022; 14(4):115. https://doi.org/10.3390/fi14040115
Chicago/Turabian StyleAl-Dwairi, Mahmoud, Ahmed S. Shatnawi, Osama Al-Khaleel, and Basheer Al-Duwairi. 2022. "Ransomware-Resilient Self-Healing XML Documents" Future Internet 14, no. 4: 115. https://doi.org/10.3390/fi14040115
APA StyleAl-Dwairi, M., Shatnawi, A. S., Al-Khaleel, O., & Al-Duwairi, B. (2022). Ransomware-Resilient Self-Healing XML Documents. Future Internet, 14(4), 115. https://doi.org/10.3390/fi14040115






