RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks
Abstract
1. Introduction
2. Relevant Work
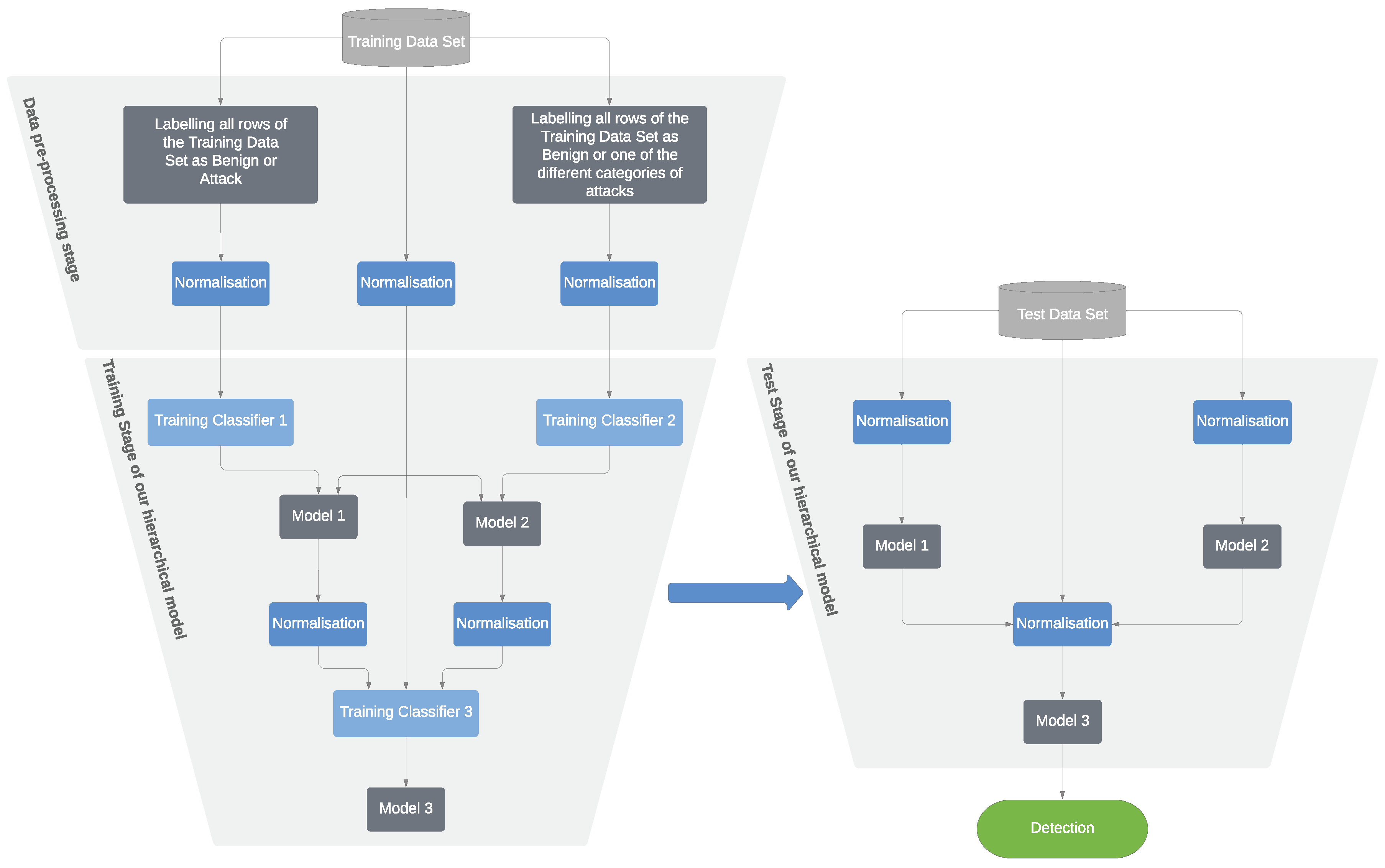
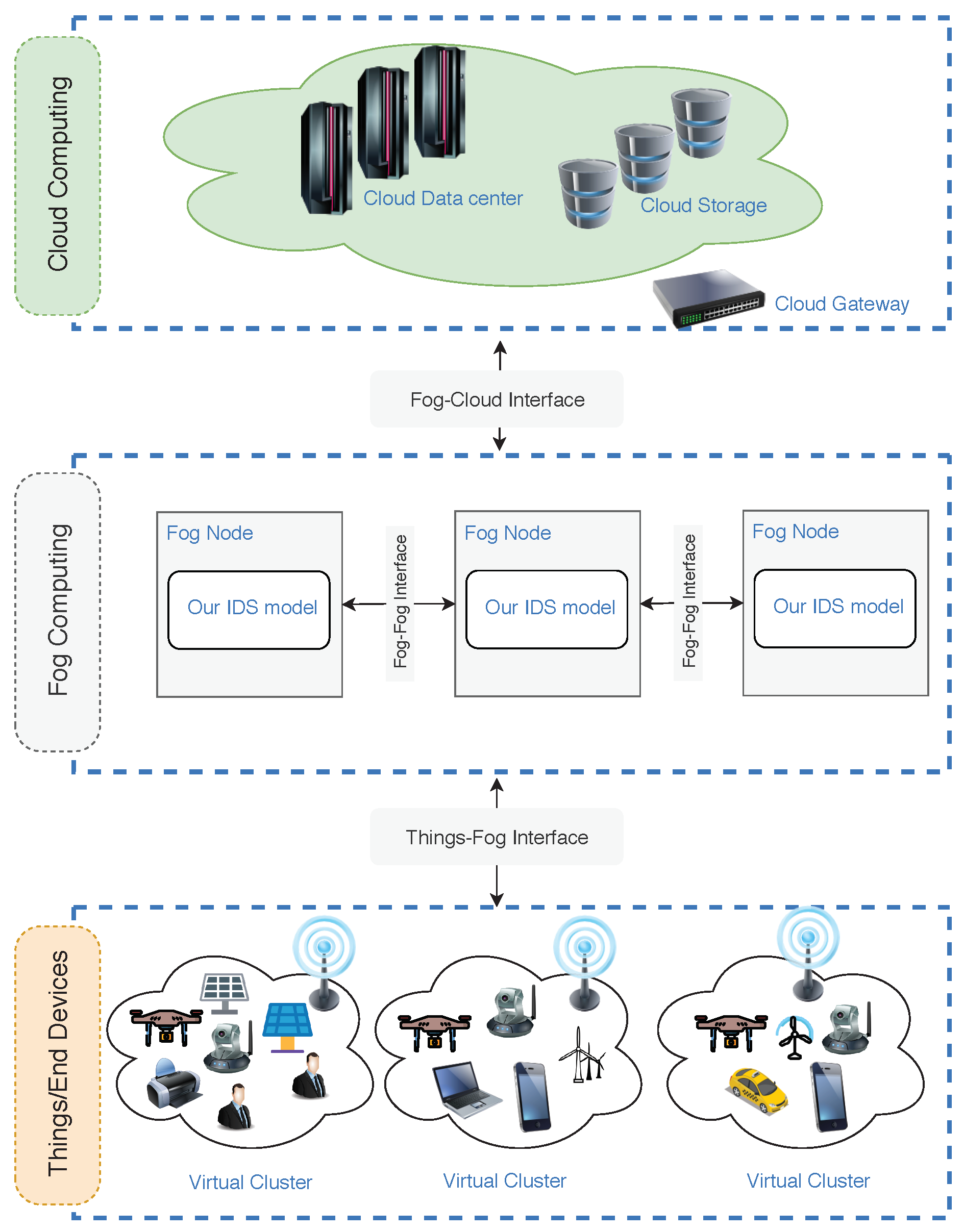
3. The Proposed Model
Operation Mode
4. Experimentation
4.1. Data Set and Data Pre-Processing
4.2. Performance Metrics
4.3. Practical Structure of RDTIDS System
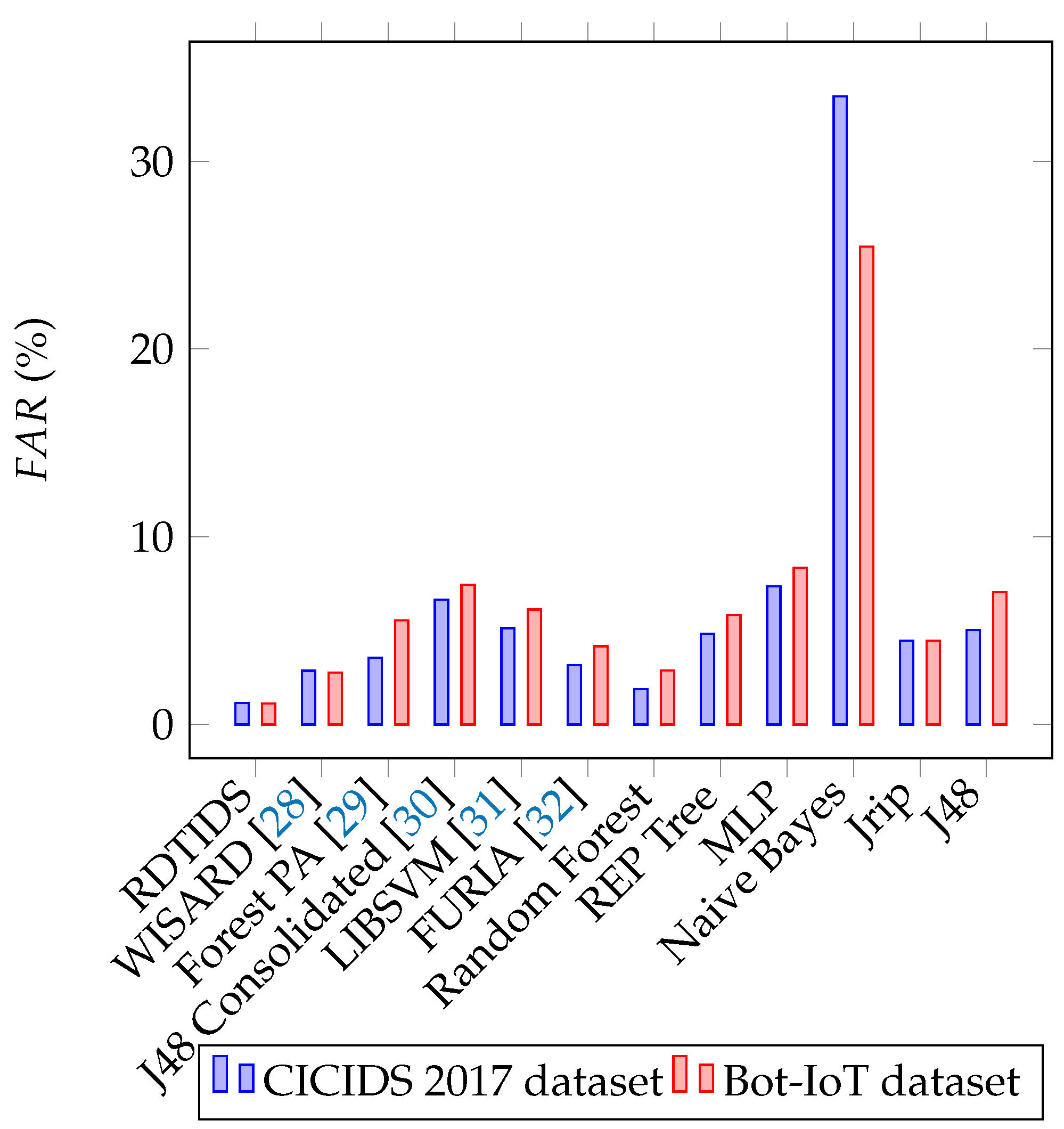
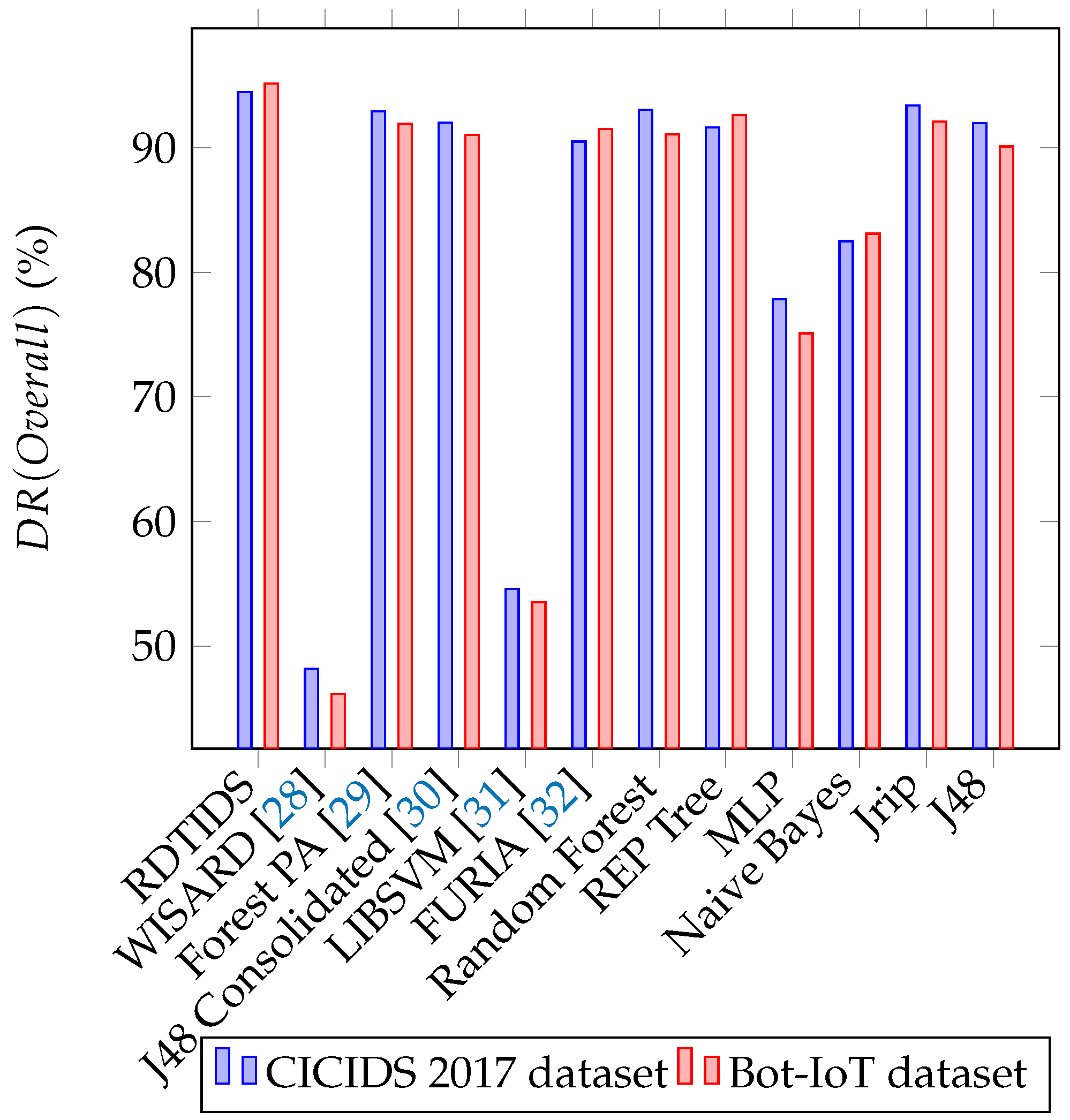
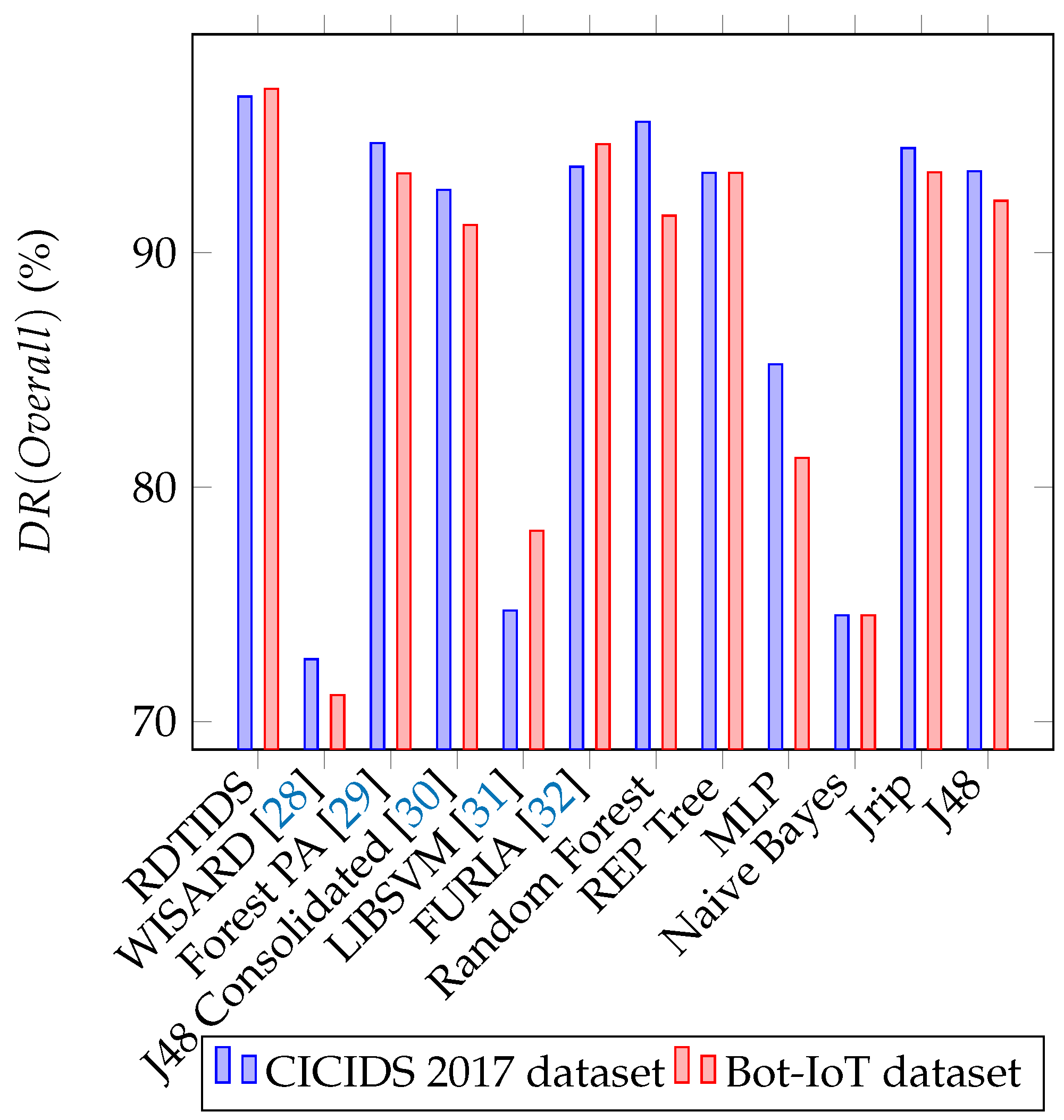
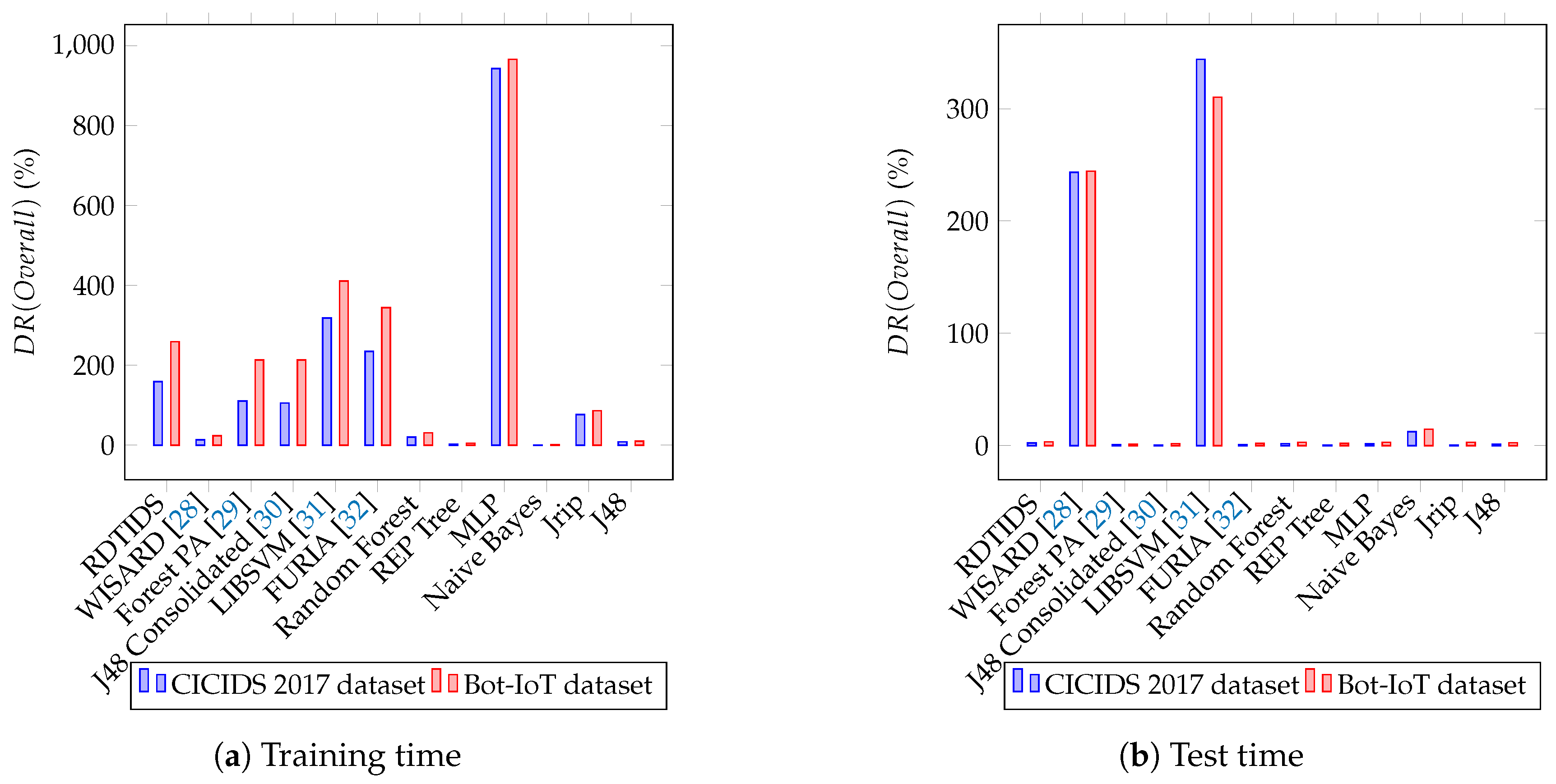
4.4. Comparative Study
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Maglaras, L.A.; Kim, K.H.; Janicke, H.; Ferrag, M.A.; Rallis, S.; Fragkou, P.; Maglaras, A.; Cruz, T.J. Cyber security of critical infrastructures. ICT Express 2018, 4, 42–45. [Google Scholar] [CrossRef]
- Ferrag, M.A. EPEC: An efficient privacy-preserving energy consumption scheme for smart grid communications. Telecommun. Syst. 2017, 66, 671–688. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Nafa, M.; Ghanemi, S. EPSA: An efficient and privacy-preserving scheme against wormhole attack on reactive routing for mobile ad hoc social networks. Int. J. Secur. Netw. 2016, 11, 107–125. [Google Scholar] [CrossRef]
- Alcaraz, C.; Zeadally, S. Critical infrastructure protection: Requirements and challenges for the 21st century. Int. J. Crit. Infrastruct. Prot. 2015, 8, 53–66. [Google Scholar] [CrossRef]
- Maglaras, L.; Cruz, T.; Ferrag, M.A.; Janicke, H. Teaching the process of building an Intrusion Detection System using data from a small-scale SCADA testbed. Internet Technol. Lett. 2020, 3, e132. [Google Scholar] [CrossRef]
- Hu, Y.; Yang, A.; Li, H.; Sun, Y.; Sun, L. A survey of intrusion detection on industrial control systems. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718794615. [Google Scholar] [CrossRef]
- Cruz, T.; Rosa, L.; Proença, J.; Maglaras, L.; Aubigny, M.; Lev, L.; Jiang, J.; Simoes, P. A cybersecurity detection framework for supervisory control and data acquisition systems. IEEE Trans. Ind. Inf. 2016, 12, 2236–2246. [Google Scholar] [CrossRef]
- Ahmim, A.; Maglaras, L.; Ferrag, M.A.; Derdour, M.; Janicke, H. A novel hierarchical intrusion detection system based on decision tree and rules-based models. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 228–233. [Google Scholar]
- Aydın, M.A.; Zaim, A.H.; Ceylan, K.G. A hybrid intrusion detection system design for computer network security. Comput. Electr. Eng. 2009, 35, 517–526. [Google Scholar] [CrossRef]
- Wang, G.; Hao, J.; Ma, J.; Huang, L. A new approach to intrusion detection using Artificial Neural Networks and fuzzy clustering. Expert Syst. Appl. 2010, 37, 6225–6232. [Google Scholar] [CrossRef]
- Govindarajan, M.; Chandrasekaran, R. Intrusion detection using neural based hybrid classification methods. Comput. Netw. 2011, 55, 1662–1671. [Google Scholar] [CrossRef]
- Chung, Y.Y.; Wahid, N. A hybrid network intrusion detection system using simplified swarm optimization (SSO). Appl. Soft Comput. 2012, 12, 3014–3022. [Google Scholar] [CrossRef]
- Elbasiony, R.M.; Sallam, E.A.; Eltobely, T.E.; Fahmy, M.M. A hybrid network intrusion detection framework based on random forests and weighted k-means. Ain Shams Eng. J. 2013, 4, 753–762. [Google Scholar] [CrossRef]
- Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. [Google Scholar] [CrossRef]
- Lin, W.C.; Ke, S.W.; Tsai, C.F. CANN: An intrusion detection system based on combining cluster centers and nearest neighbors. Knowl. Syst. 2015, 78, 13–21. [Google Scholar] [CrossRef]
- Aslahi-Shahri, B.; Rahmani, R.; Chizari, M.; Maralani, A.; Eslami, M.; Golkar, M.; Ebrahimi, A. A hybrid method consisting of GA and SVM for intrusion detection system. Neural Comput. Appl. 2016, 27, 1669–1676. [Google Scholar] [CrossRef]
- Kevric, J.; Jukic, S.; Subasi, A. An effective combining classifier approach using tree algorithms for network intrusion detection. Neural Comput. Appl. 2017, 28, 1051–1058. [Google Scholar] [CrossRef]
- Al-Yaseen, W.L.; Othman, Z.A.; Nazri, M.Z.A. Multi-level hybrid support vector machine and extreme learning machine based on modified K-means for intrusion detection system. Expert Syst. Appl. 2017, 67, 296–303. [Google Scholar] [CrossRef]
- Ahmim, A.; Derdour, M.; Ferrag, M.A. An intrusion detection system based on combining probability predictions of a tree of classifiers. Int. J. Commun. Syst. 2018, 31, e3547. [Google Scholar] [CrossRef]
- Aljawarneh, S.; Aldwairi, M.; Yassein, M.B. Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J. Comput. Sci. 2018, 25, 152–160. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L. DeepCoin: A novel deep learning and blockchain-based energy exchange framework for smart grids. IEEE Trans. Eng. Manag. 2019, 1–13. [Google Scholar] [CrossRef]
- Derhab, A.; Guerroumi, M.; Gumaei, A.; Maglaras, L.; Ferrag, M.A.; Mukherjee, M.; Khan, F.A. Blockchain and random subspace learning-based IDS for SDN-enabled industrial IoT security. Sensors 2019, 19, 3119. [Google Scholar] [CrossRef] [PubMed]
- Ferrag, M.A.; Maglaras, L. DeliveryCoin: An IDS and Blockchain-Based Delivery Framework for Drone-Delivered Services. Computers 2019, 8, 58. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the ICISSP, Funchal, Portugal, 22–24 January 2018; pp. 108–116. [Google Scholar]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Janicke, H.; Smith, R. Deep Learning Techniques for Cyber Security Intrusion Detection: A Detailed Analysis. In Proceedings of the 6th International Symposium for ICS & SCADA Cyber Security Research 2019, Athens, Greece, 10–12 September 2019; pp. 126–136. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. [Google Scholar] [CrossRef]
- De Gregorio, M.; Giordano, M. An experimental evaluation of weightless neural networks for multi-class classification. Appl. Soft Comput. 2018, 72, 338–354. [Google Scholar] [CrossRef]
- Adnan, M.N.; Islam, M.Z. Forest PA: Constructing a decision forest by penalizing attributes used in previous trees. Expert Syst. Appl. 2017, 89, 389–403. [Google Scholar] [CrossRef]
- Ibarguren, I.; Pérez, J.M.; Muguerza, J.; Gurrutxaga, I.; Arbelaitz, O. Coverage-based resampling: Building robust consolidated decision trees. Knowl. Syst. 2015, 79, 51–67. [Google Scholar] [CrossRef]
- Chang, C.C.; Lin, C.J. LIBSVM: A library for support vector machines. ACM Trans. Intell. Syst. Technol. 2011, 2, 27. [Google Scholar] [CrossRef]
- Huehn, J.C.; Huellermeier, E. FURIA: An Algorithm for Unordered Fuzzy Rule Induction. Data Min. Knowl. Discov. 2009, 19, 293–319. [Google Scholar] [CrossRef]
- Kang, P.; Cho, S. EUS SVMs: Ensemble of under-sampled SVMs for data imbalance problems. In Proceedings of the International Conference on Neural Information Processing, Hong Kong, China, 3–6 October 2006; pp. 837–846. [Google Scholar]
- Tsoumakas, G.; Katakis, I.; Vlahavas, I. Effective voting of heterogeneous classifiers. In Proceedings of the European Conference on Machine Learning, Pisa, Italy, 20–24 September 2004; pp. 465–476. [Google Scholar]
- Folino, G.; Pisani, F.S. Evolving meta-ensemble of classifiers for handling incomplete and unbalanced datasets in the cyber security domain. Appl. Soft Comput. 2016, 47, 179–190. [Google Scholar] [CrossRef]
- Frank, E.; Witten, I.H. Reduced-Error Pruning with Significance Tests. Available online: https://researchcommons.waikato.ac.nz/bitstream/handle/10289/1039/uow-cs-wp-1999-10.pdf?sequence=1&isAllowed=y (accessed on 29 February 2020).
- Cohen, W.W. Fast Effective Rule Induction. In Proceedings of the Twelfth International Conference on Machine Learning, Tahoe City, CA, USA, 9–12 July 1995; pp. 115–123. [Google Scholar]
- Bot-IoT Dataset. Available online: https://www.unsw.adfa.edu.au/unsw-canberra-cyber/cybersecurity/ADFA-NB15-Datasets/bot_iot.php (accessed on 30 May 2019).
- Gharib, A.; Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. An evaluation framework for intrusion detection dataset. In Proceedings of the 2016 International Conference on Information Science and Security (ICISS), Pattaya, Thailand, 19–22 December 2016; pp. 1–6. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-iot dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
| Year | Paper | Machine Learning and Data Mining Methods | Cyber Approach | Data Used |
|---|---|---|---|---|
| 2009 | Aydin et al. [9] | - Packet header anomaly detection - Network traffic anomaly detection | Hybrid IDS, which combing anomaly-based IDSs | IDEVAL |
| 2010 | Wang et al. [10] | - Artificial neural networks Fuzzy clustering | Hybrid IDS, which the fuzzy aggregation module is employed to aggregate the results | KDD CUP 1999 |
| 2011 | Govindarajan and Chandrasekaran [11] | - Multilayer perceptron neural network - Radial basis function neural network | Neural based hybrid IDS | UNM Send-Mail Data |
| 2012 | Chung and Wahid [12] | - Intelligent dynamic swarm - Simplified swarm optimization | Hybrid IDS | KDD CUP 1999 |
| 2013 | Elbasiony et al. [13] | - Random forests algorithm - K-means clustering algorithm | Combining misuse and anomaly detection into a hybrid framework | KDD CUP 1999 |
| 2014 | Kim et al. [14] | - C4.5 decision tree algorithm - Support vector machine model | Combining misuse and anomaly detection into a hybrid framework | NSL-KDD |
| 2015 | Lin et al. [15] | - k-Nearest Neighbor (k-NN) classifier | Combining cluster centers and nearest neighbors | KDD CUP 1999 |
| 2016 | Aslahi-Shahri et al. [16] | - Support vector machine - Genetic algorithm | Hybrid IDS | KDD CUP 1999 |
| 2017 | Kevric et al. [17] | - Random tree - C4.5 decision tree algorithm - NBTree | Combining classifier model based on tree-based algorithms | NSL-KDD |
| 2017 | Al-Yaseen et al. [18] | - Support vector machine - Extreme learning machine - K-means clustering algorithm | Hybrid IDS | KDD CUP 1999 |
| 2018 | Ahmim et al. [19] | - Repeated Incremental Pruning to Produce Error, Reduction (RIPPER), RBF Network (RBFN), Ripple-down rule learner (Ridor), and Random Forests - Naive Bayes (NB) | Combining probability predictions of a tree of classifiers | KDD CUP 1999 + NSL-KDD |
| 2018 | Aljawarneh et al. [20] | J48, Meta Pagging, RandomTree, REPTree, AdaBoostM1, DecisionStump, and NaiveBayes | Hybrid IDS, which combing anomaly-based IDSs | NSL-KDD |
| 2019 | Ferrag et al. [21] | Recurrent neural networks | Hybrid IDS, which combing recurrent neural networks with blockchain | CICIDS2017, Power System dataset, and Bot-IoT |
| 2019 | Derhab et al. [22] | Random subspace learning | Hybrid IDS, which combing random subspace learning with blockchain | Power System dataset |
| 2019 | Ferrag et al. [23] | Deep learning techniques | Hybrid IDS, which combing deep learning techniques with blockchain | CSE-CIC-IDS2018 dataset |
| RDTIDS | - REP Tree - JRip algorithm - Random Forest | Hybrid IDS, which combining classifier model based on tree-based algorithms | CICIDS2017 |
| Category | Total | Total (-Rows with Lack Info) | Training | Test | |
|---|---|---|---|---|---|
| BENIGN | BENIGN | 2,273,097 | 2,271,320 | 20,000 | 20,000 |
| DOS | DDoS | 128,027 | 128,025 | 2700 | 3300 |
| DoS slowloris | 5796 | 5796 | 1350 | 1650 | |
| DoS Slowhttptest | 5499 | 5499 | 2171 | 1169 | |
| DoS Hulk | 231,073 | 230,124 | 4500 | 5500 | |
| DoS GoldenEye | 10,293 | 10,293 | 1300 | 700 | |
| Heartbleed | 11 | 11 | 5 | 5 | |
| PortScan | PortScan | 158,930 | 158,804 | 3808 | 4192 |
| Bot | Bot | 1966 | 1956 | 936 | 624 |
| Brute-Force | FTP-Patator | 7938 | 7935 | 900 | 1100 |
| SSH-Patator | 5897 | 5897 | 900 | 1100 | |
| Web Attack | Web Attack-Brute Force | 1507 | 1507 | 910 | 490 |
| Web Attack-XSS | 652 | 652 | 480 | 160 | |
| Web Attack-SQL Injection | 21 | 21 | 16 | 4 | |
| Infiltration | Infiltration | 36 | 36 | 24 | 6 |
| Total Attack | 471,454 | 470,365 | 20,000 | 20,000 | |
| Total | 2,830,743 | 2,827,876 | 40,000 | 40,000 | |
| Category | Attack Type | Flow Count | Training | Test |
|---|---|---|---|---|
| BENIGN | BENIGN | 9543 | 7634 | 1909 |
| Information gathering | Service scanning | 1,463,364 | 117,069 | 29,267 |
| OS Fingerprinting | 358,275 | 28,662 | 7166 | |
| DDoS attack | DDoS TCP | 19,547,603 | 1,563,808 | 390,952 |
| DDoS UDP | 18,965,106 | 1,517,208 | 379,302 | |
| DDoS HTTP | 19,771 | 1582 | 395 | |
| DoS attack | DoS TCP | 12,315,997 | 985,280 | 246,320 |
| DoS UDP | 20,659,491 | 1,652,759 | 413,190 | |
| DoS HTTP | 29,706 | 2376 | 594 | |
| Information | Keylogging | 1469 | 1175 | 294 |
| theft | Data theft | 118 | 94 | 24 |
| Total | / | 73,370,443 | 5,877,647 | 1,469,413 |
| Predicted Class | |||
|---|---|---|---|
| Negative Class | Positive | ||
| Actual class | Negative Class | True negative (TN) | False positive (FP) |
| Positive Class | False negative (FN) | True positive (TP) | |
| RDTIDS | [28] | [29] | [30] | [31] | Random Forest | REP Tree | MLP | Naive Bayes | Jrip | J48 | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TNR (BENIGN) | 98.855% | 97.135% | 96.450% | 93.355% | 94.870% | 96.835% | 98.120% | 95.165% | 92.650% | 66.545% | 95.530% | 94.960% |
| DR DDoS | 99.879% | 54.697% | 99.818% | 93.212% | 55.970% | 99.758% | 99.818% | 99.788% | 91.212% | 93.879% | 99.667% | 99.788% |
| DR DoS slowloris | 97.758% | 78.909% | 92.848% | 95.030% | 78.182% | 93.758% | 93.758% | 92.727% | 78.485% | 82.667% | 93.333% | 93.879% |
| DR DoS Slowhttptest | 93.841% | 23.353% | 86.826% | 83.832% | 76.561% | 78.358% | 81.352% | 75.364% | 88.537% | 70.060% | 85.543% | 80.325% |
| DR DoS Hulk | 96.782% | 67.600% | 93.945% | 95.891% | 73.709% | 98.655% | 95.164% | 92.218% | 86.891% | 73.782% | 97.364% | 93.600% |
| DR DoS GoldenEye | 67.571% | 48.714% | 67.571% | 67.143% | 57.571% | 65.143% | 67.571% | 66.429% | 65.429% | 62.143% | 63.857% | 67.286% |
| DR Heartbleed | 100% | 80.000% | 100% | 80.000% | 0.000% | 40.000% | 100% | 100% | 0.000% | 80.000% | 80.000% | 100% |
| DR PortScan | 99.881% | 51.407% | 99.594% | 99.046% | 48.521% | 87.118% | 99.881% | 99.881% | 48.521% | 99.499% | 99.881% | 98.569% |
| DR Bot | 46.474% | 1.442% | 48.718% | 52.083% | 0.000% | 48.077% | 49.679% | 47.756% | 51.282% | 29.968% | 46.474% | 47.756% |
| DR FTP-Patator | 99.636% | 0.000% | 99.727% | 100% | 0.000% | 99.636% | 99.727% | 99.182% | 99.000% | 99.455% | 99.545% | 99.545% |
| DR SSH-Patator | 99.909% | 0.000% | 100% | 99.727% | 0.000% | 100% | 99.818% | 100% | 99.727% | 99.182% | 100% | 100% |
| DR Web Attack—Brute Force | 73.265% | 4.694% | 73.469% | 55.102% | 80.816% | 49.796% | 70.408% | 70.816% | 90.408% | 5.102% | 61.837% | 60.408% |
| DR Web Attack—XSS | 30.625% | 1.250% | 34.375% | 48.750% | 0.000% | 38.750% | 37.500% | 32.500% | 1.875% | 91.875% | 38.125% | 41.250% |
| DR Web Attack—SQL Injection | 50.000% | 0.000% | 50.000% | 100% | 0.000% | 50.000% | 100% | 50.000% | 50.000% | 100% | 75.000% | 50.000% |
| DR Infiltration | 100% | 50.000% | 83.333% | 100% | 0.000% | 83.333% | 83.333% | 83.333% | 16.667% | 83.333% | 100% | 66.667% |
| DR Service scanning | 99.472% | 54.697% | 99.111% | 92.211% | 53.170% | 99.158% | 99.118% | 99.188% | 91.212% | 93.172% | 99.267% | 94.718% |
| DR OS Fingerprinting | 98.158% | 79.109% | 93.141% | 94.111% | 77.182% | 94.7581% | 94.751% | 93.100% | 79.185% | 83.967% | 94.381% | 94.129% |
| DR DDoS TCP | 95.841% | 22.322% | 87.727% | 84.532% | 77.869% | 79.559% | 82.454% | 76.666% | 89.937% | 71.223% | 86.599% | 80.325% |
| DR DDoS UDP | 98.655% | 67.600% | 93.945% | 95.891% | 73.709% | 96.782% | 96.466% | 91.318% | 84.441% | 72.811% | 95.119% | 93.600% |
| DR DDoS HTTP | 93.171% | 47.914% | 68.888% | 68.242% | 59.971% | 65.143% | 67.222% | 67.666% | 66.489% | 63.243% | 62.111% | 61.236% |
| DR DoS TCP | 100% | 82.111% | 100% | 82.123% | 2.000% | 40.234% | 92.123% | 100% | 3.000% | 80.000% | 82.123% | 100% |
| DR DoS UDP | 100% | 55.007% | 100% | 100% | 41.198% | 86.119% | 100% | 99.991% | 49.521% | 98.422% | 99.181% | 98.111% |
| DR DoS HTTP | 77.474% | 1.442% | 48.718% | 49.083% | 0.000% | 49.012% | 49.373% | 47.756% | 51.282% | 29.968% | 47.174% | 46.156% |
| DR Keylogging | 100% | 0.000% | 99.727% | 100% | 0.000% | 99.145% | 99.727% | 98.182% | 100% | 99.855% | 98.545% | 98.145% |
| DR Data theft | 100% | 0.000% | 100% | 99.222% | 0.000% | 100% | 99.718% | 100% | 99.927% | 99.982% | 99.187% | 99.276% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ferrag, M.A.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks. Future Internet 2020, 12, 44. https://doi.org/10.3390/fi12030044
Ferrag MA, Maglaras L, Ahmim A, Derdour M, Janicke H. RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks. Future Internet. 2020; 12(3):44. https://doi.org/10.3390/fi12030044
Chicago/Turabian StyleFerrag, Mohamed Amine, Leandros Maglaras, Ahmed Ahmim, Makhlouf Derdour, and Helge Janicke. 2020. "RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks" Future Internet 12, no. 3: 44. https://doi.org/10.3390/fi12030044
APA StyleFerrag, M. A., Maglaras, L., Ahmim, A., Derdour, M., & Janicke, H. (2020). RDTIDS: Rules and Decision Tree-Based Intrusion Detection System for Internet-of-Things Networks. Future Internet, 12(3), 44. https://doi.org/10.3390/fi12030044








