An Agent-Based Model of Task-Allocation and Resource-Sharing for Social Internet of Things
Abstract
1. Introduction
- should be decentralized in nature.
- should be capable of taking autonomous decisions.
- should be interacting with other objects within their zones of influence, described by network configurations.
- could optionally be mobile, which result-in ad-hoc connectivity and, thus, the interaction among objects.
2. Background and Motivation
2.1. Internet of Things
2.2. Social Capabilities of Things in SIoT
2.3. From Centralized to Distributed Communication
2.4. SIoT Applications
2.5. Related Work in Modeling SIoT
2.6. Outline of the Proposed Model
3. Model
3.1. Overview
3.2. Design Concepts
- Service units denied: represents the total number of service units in terms of iterations (time) that are denied (peer requested with no response) by the system at a given time.
- Service units completed: maintains the total number of service units in terms of iterations (time) that are completed by the system at a given time.
3.3. Details
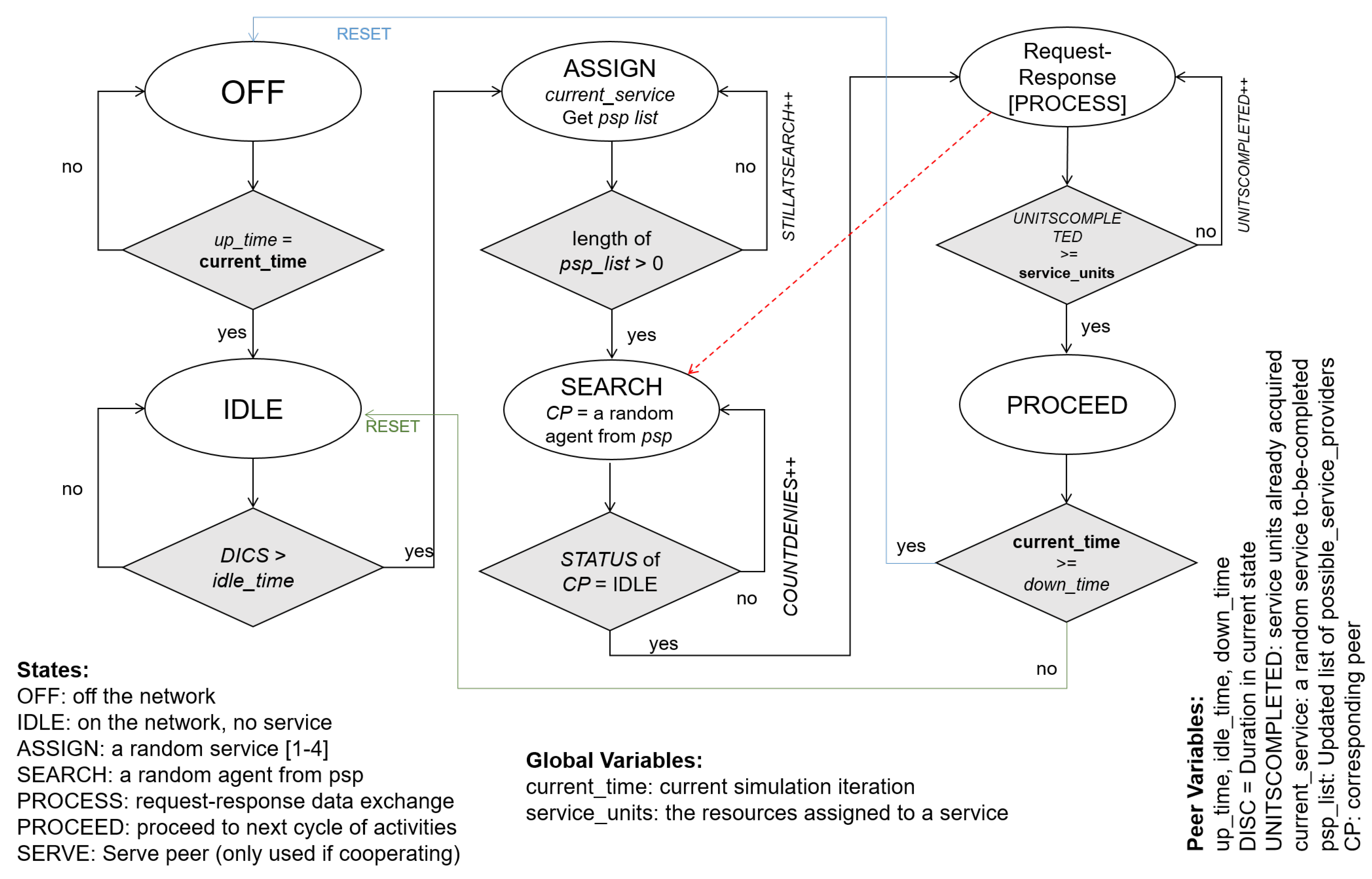
3.3.1. Model of Resource Sharing in Competitive Mode
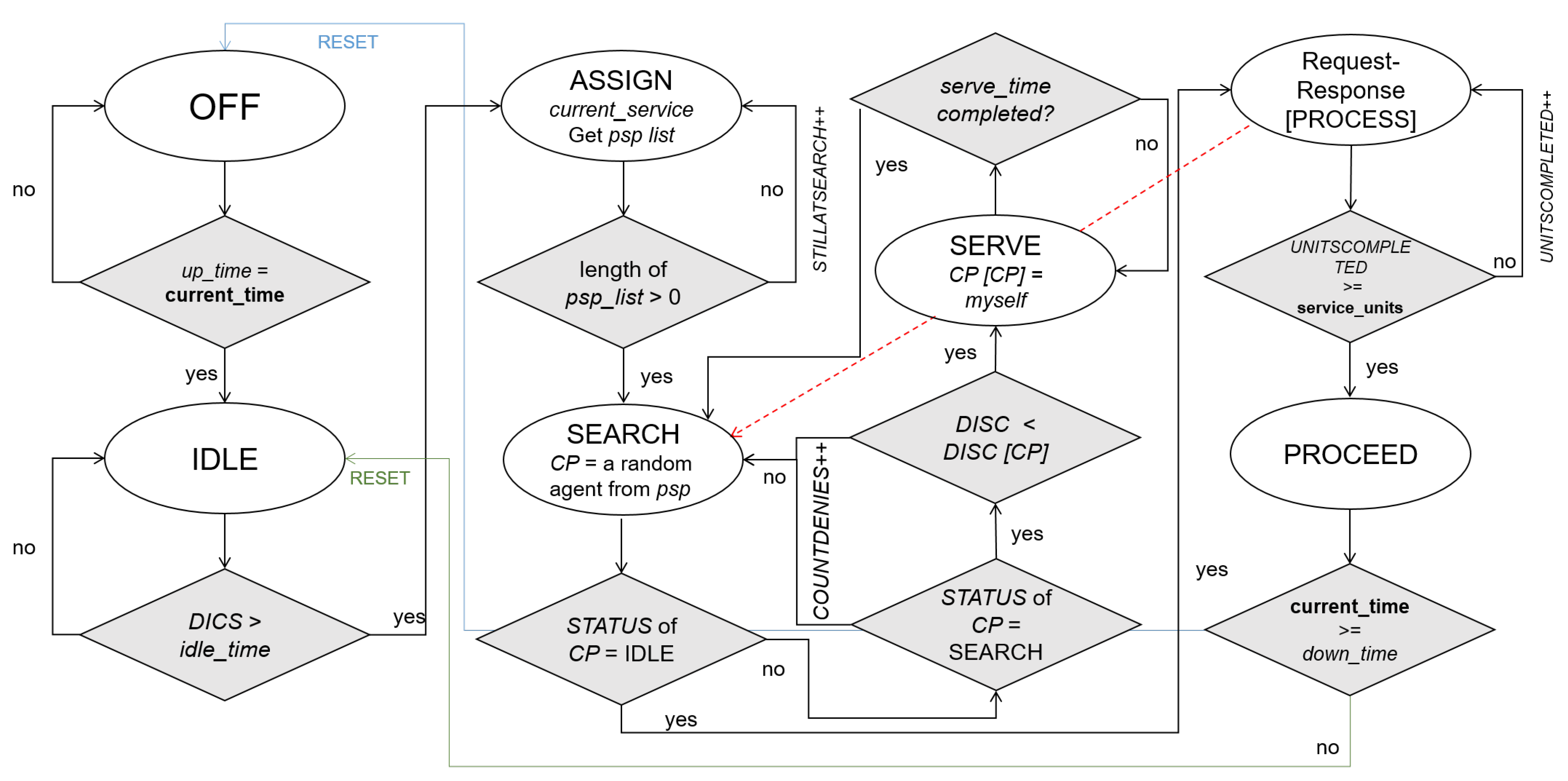
3.3.2. Model of Resource Sharing in Cooperative Mode
3.3.3. Model of Friendship (Restricted Cooperation)
3.3.4. Mobility Modes
- Mobility 1: No mobility, in which all agents are stationary.
- Mobility 2: Random walk, in which the agents choose a direction to move randomly at each iteration.
- Mobility 3: Profile-based walk, in which the agents select some random locations to move to, and they move from one location to another.
3.3.5. Networking
4. Simulation and Results
4.1. Simulation Setup
- resource sharing when all agents are in competitive mode (see Section 3.3.1).
- resource sharing when all agents are in cooperative mode (see Section 3.3.2).
- resource sharing when all agents are in restricted cooperative mode (see Section 3.3.3).
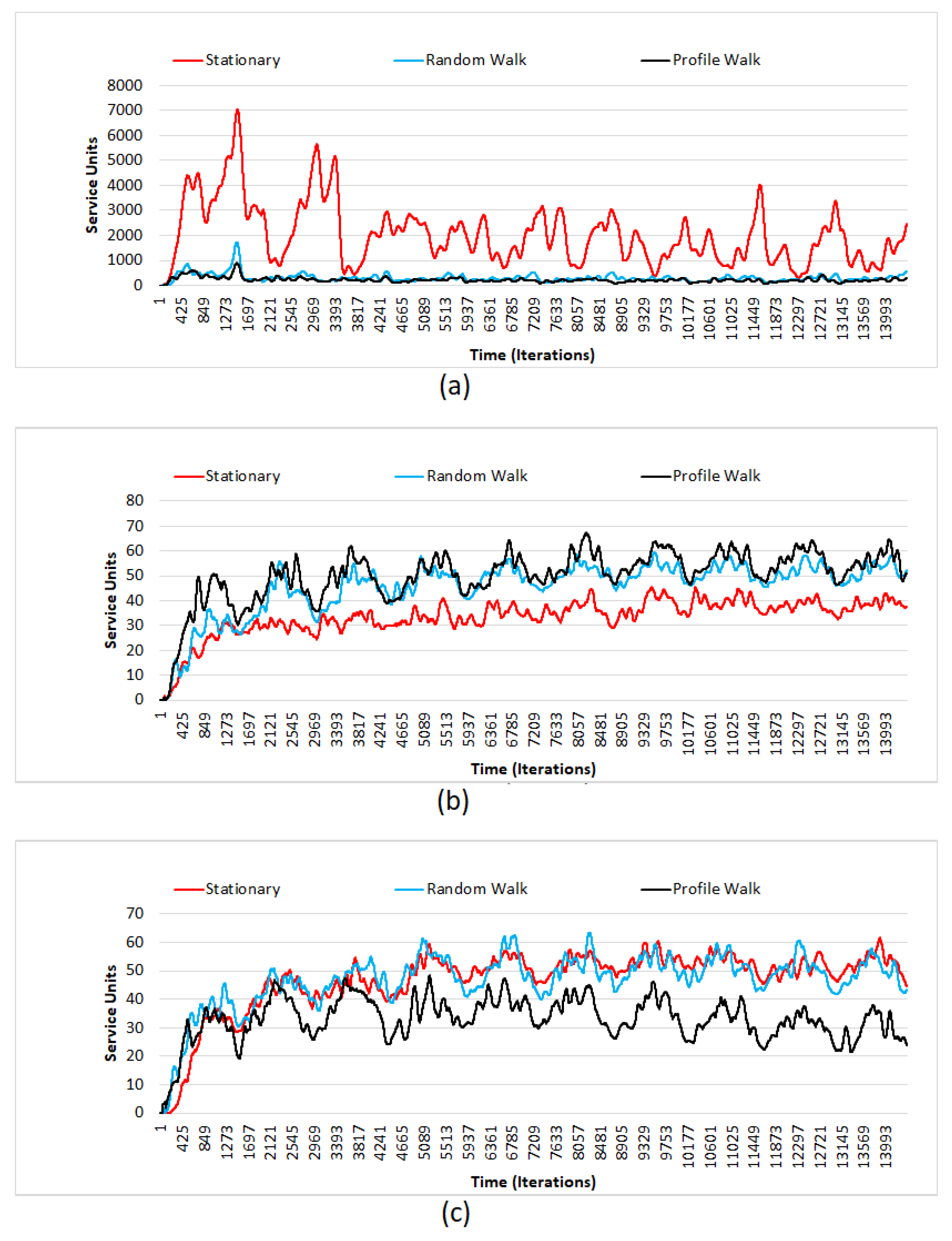
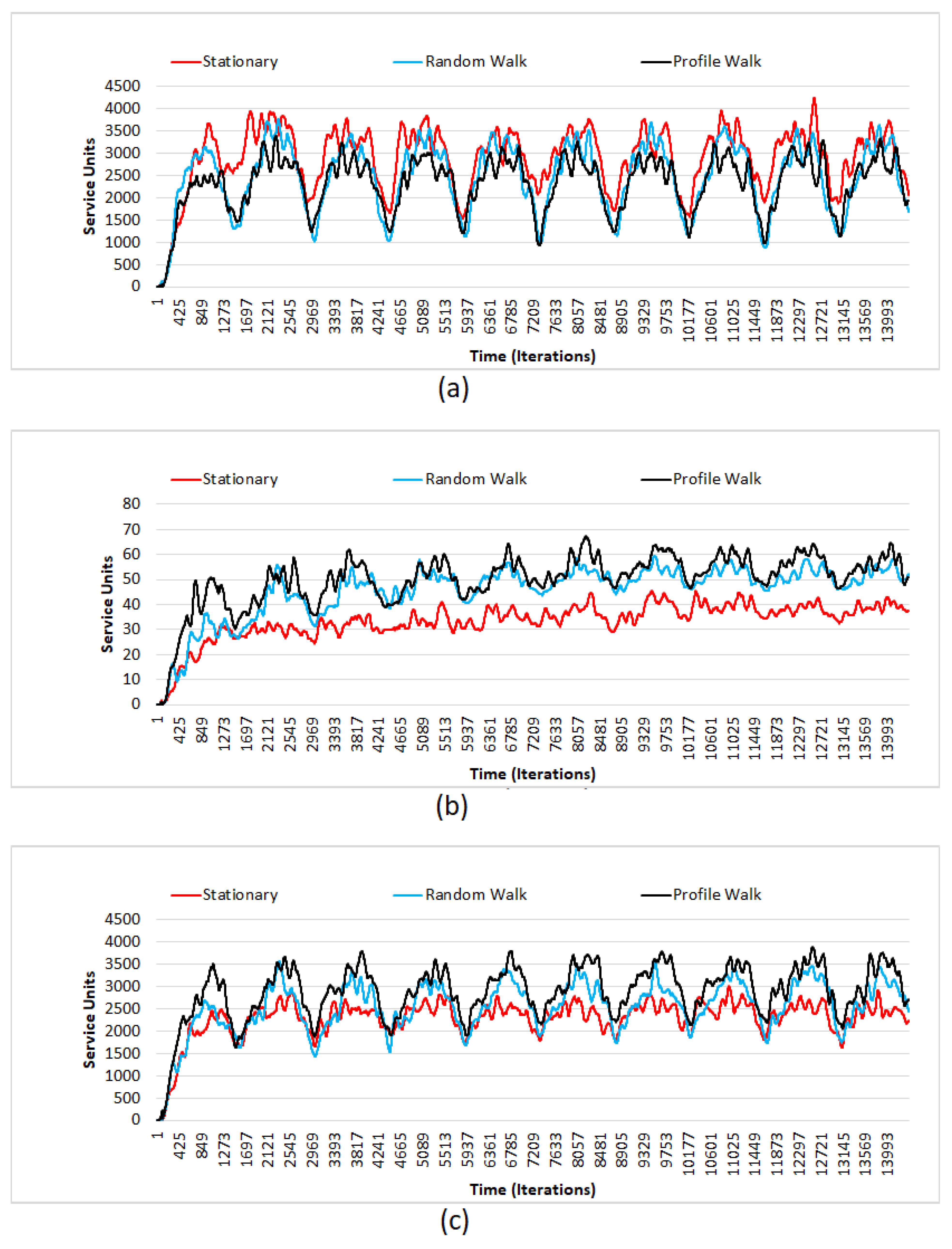
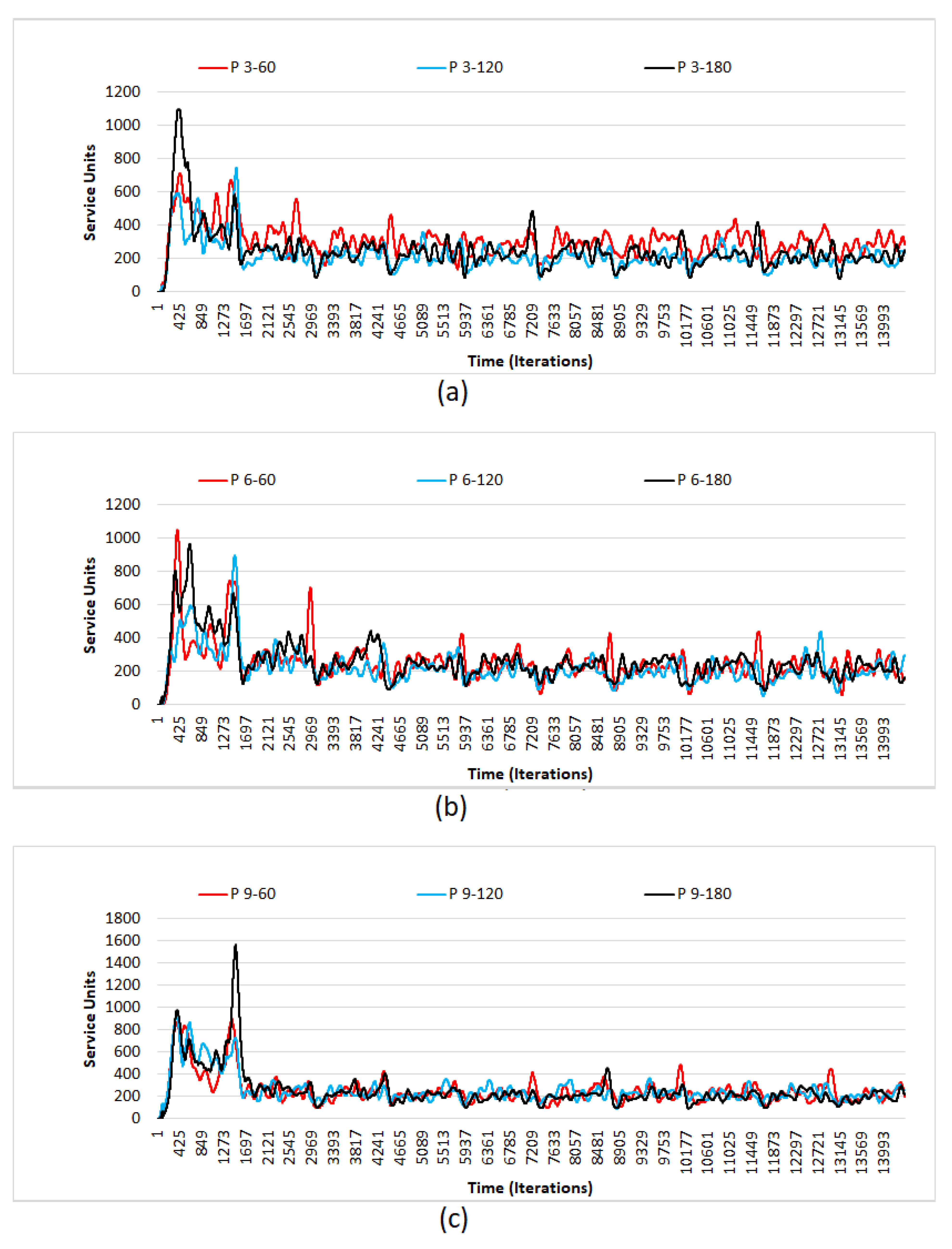
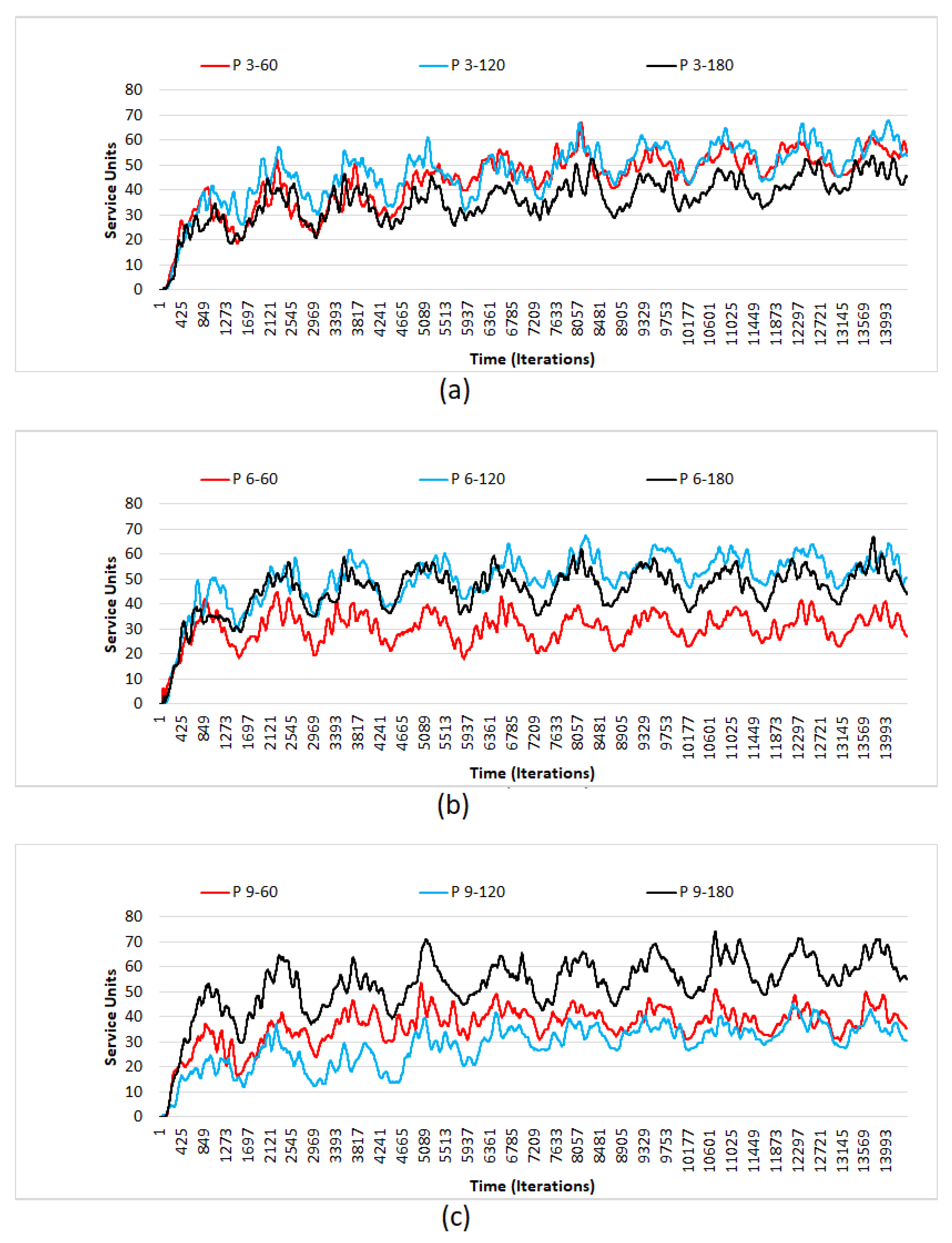
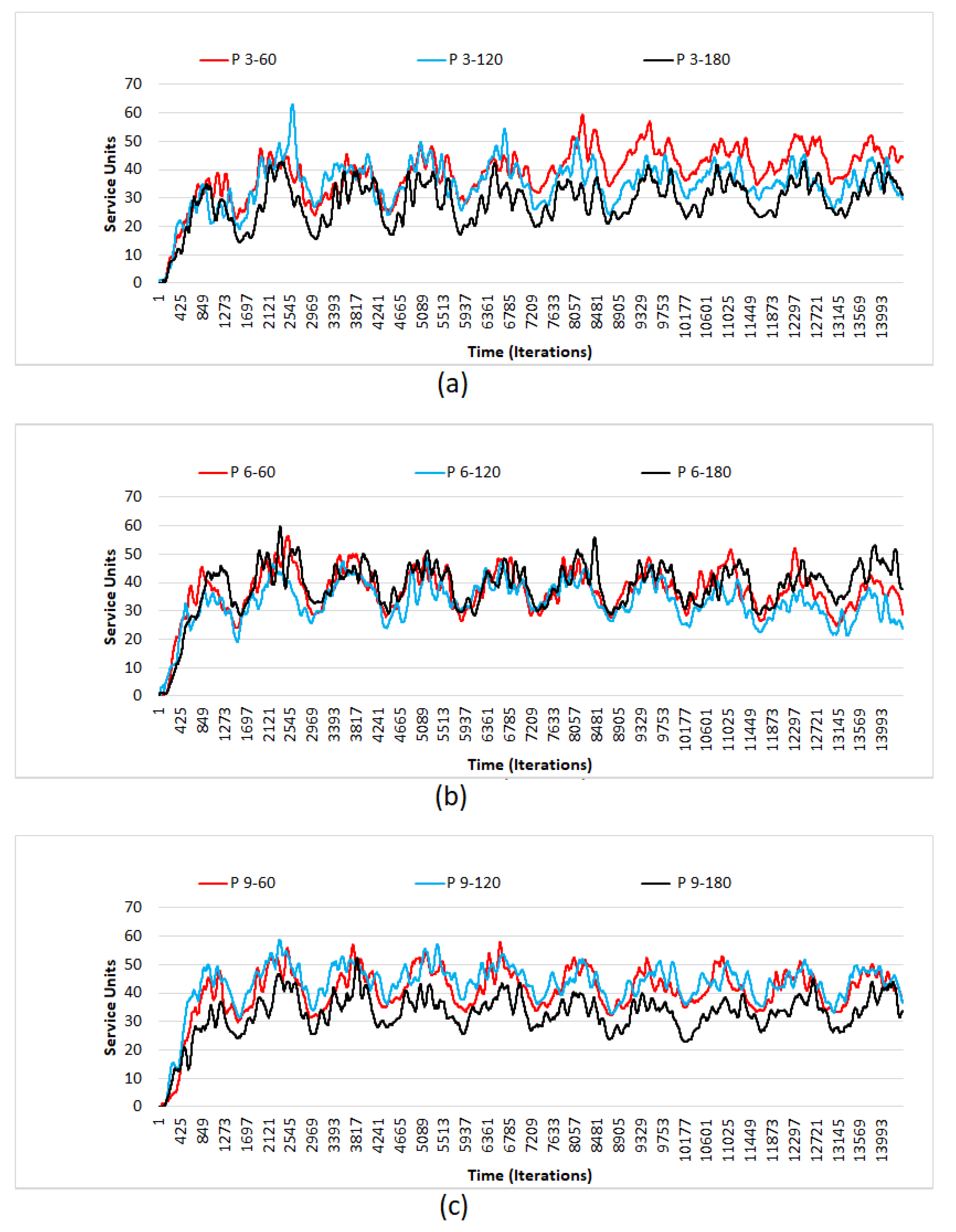
4.2. Simulation Results
- In [55], it is reported that “cooperative strategy is comparable with competitive strategy, particularly, when the population is large. It is expected that cooperation would always outperform competition above a density threshold”.
- In [56], we learnt that “the nature of the underlying structure of network connectivity has a profound impact. In general, peers communicating in a mesh network achieve the best results. However, in some settings, a small-world network competes with a mesh network. Further, with an increase in the density of objects, the beta value of small-world may be reduced without degrading the standard of service provisioning.”
- The results in [8] suggested that “As a whole, cooperation between peers improves the system. In particular, cooperation in a restricted network is never counterproductive; in-fact, it is evident to be marginally better than open-ended cooperation.”
- There is a definite difference, in terms of units denied, between different combinations of values for extent and scale.
- It is also observed that the units denied has a gradual increase, as the time, in terms of days, pass by.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Park, H.; Kim, H.; Joo, H.; Song, J. Recent advancements in the Internet-of-Things related standards: A oneM2M perspective. ICT Express 2016, 2, 126–129. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The social internet of things (siot)–when social networks meet the internet of things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. Social Internet of Things: Turning Smart Objects into Social Objects to Boost the IoT. Available online: https://iot.ieee.org/newsletter/november-2014/social-internet-of-things-turning-smart-objects-into-social-objects-to-boost-the-iot.html?__hstc=77947915.ab7bf88e972fdd7a7debc8575bac5a80.1457222400146.1457222400147.1457222400148.1&__hssc=77947915.1.1457222400149&__hsfp=3972014050 (accessed on 22 March 2021).
- Atzori, L.; Iera, A.; Morabito, G. From “smart objects” to “social objects”: The next evolutionary step of the internet of things. IEEE Commun. Mag. 2014, 52, 97–105. [Google Scholar] [CrossRef]
- Zia, K.; Muhammad, A.; Saini, D.K. Modeling and Assessment of Resource-sharing Efficiency in Social Internet of Things. In Dependable IoT for Human and Industry: Modeling, Architecting, Implementation; River Publishers: Alsbjergvej, Denmark, 2018; p. 83. [Google Scholar]
- Valenzuela, S.; Park, N.; Kee, K.F. Is there social capital in a social network site?: Facebook use and college students’ life satisfaction, trust, and participation1. J. Comput. Mediat. Commun. 2009, 14, 875–901. [Google Scholar] [CrossRef]
- Zia, K.; Al Maskari, S.; Saini, D.K.; Muhammad, A.; Farooq, U. A Simulation Model Demonstrating the Impact of Social Aspects on Social Internet of Things. In Proceedings of the 21st International Conference on Information Integration and Web-Based Applications & Services; Association for Computing Machinery: New York, NY, USA, 2019; pp. 202–211. [Google Scholar] [CrossRef]
- Helbing, D. Agent-based modeling. In Social Self-Organization; Springer: Berlin/Heidelberg, Germany, 2012; pp. 25–70. [Google Scholar]
- Caram, L.F.; Caiafa, C.F.; Ausloos, M.; Proto, A.N. Cooperative peer-to-peer multiagent-based systems. Phys. Rev. E 2015, 92, 022805. [Google Scholar] [CrossRef] [PubMed]
- Loo, A.W.S. Peer-To-Peer Computing; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cognit. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Naha, R.K.; Garg, S.; Georgakopoulos, D.; Jayaraman, P.P.; Gao, L.; Xiang, Y.; Ranjan, R. Fog computing: Survey of trends, architectures, requirements, and research directions. IEEE Access 2018, 6, 47980–48009. [Google Scholar] [CrossRef]
- Cisco Annual Internet Report (2018–2023) White Paper. 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 25 June 2020).
- IoT Platforms: Enabling the Internet of Things. 2016. Available online: https://cdn.ihs.com/www/pdf/enabling-IOT.pdf (accessed on 27 July 2020).
- White Paper for Opening up Huawei IoT Capabilitles. 2017. Available online: http://developer.huawei.com/ict/en/marketing?menuID=50 (accessed on 4 January 2017).
- Khelloufi, A.; Ning, H.; Dhelim, S.; Qiu, T.; Ma, J.; Huang, R.; Atzori, L. A Social Relationships Based Service Recommendation System For SIoT Devices. IEEE Internet Things J. 2020, 8, 1859–1870. [Google Scholar] [CrossRef]
- Gupta, B.B.; Perez, G.M.; Agrawal, D.P.; Gupta, D. Handbook of Computer Networks and Cyber Security; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Popovskyy, V.; Popovska, K. Analysis of content replication mechanism in random search in peer-to-peer networks. Inf. Telecommun. Sci. 2017, 23–26. [Google Scholar] [CrossRef]
- Tetarave, S.K.; Tripathy, S. PJ-Sec: Secure node joining in mobile P2P networks. CCF Trans. Pervasive Comput. Interact. 2020, 3, 13–24. [Google Scholar] [CrossRef]
- Navimipour, N.J.; Milani, F.S. A comprehensive study of the resource discovery techniques in Peer-to-Peer networks. Peer Peer Netw. Appl. 2015, 8, 474–492. [Google Scholar] [CrossRef]
- Pticek, M.; Podobnik, V.; Jezic, G. Beyond the Internet of Things: The Social Networking of Machines. Int. J. Distrib. Sens. Netw. 2016, 12, 8178417. [Google Scholar] [CrossRef]
- Bartodziej, C.J. The Concept Industry 4.0. In The Concept Industry 4.0; Springer: Berlin/Heidelberg, Germany, 2017; pp. 27–50. [Google Scholar]
- Oztemel, E.; Gursev, S. Literature review of Industry 4.0 and related technologies. J. Intell. Manuf. 2020, 31, 127–182. [Google Scholar] [CrossRef]
- Camarinha-Matos, L.M.; Fornasiero, R.; Afsarmanesh, H. Collaborative networks as a core enabler of industry 4.0. In Working Conference on Virtual Enterprises; Springer: Berlin/Heidelberg, Germany, 2017; pp. 3–17. [Google Scholar]
- Kehal, M. Business Analytics: Through SIoT and SIoV. In Data Analytics in Marketing, Entrepreneurship, and Innovation; Auerbach Publications: Boca Raton, FL, USA, 2021; pp. 1–14. [Google Scholar]
- Zia, K.; Shafi, M.; Farooq, U. Improving recommendation accuracy using social network of owners in social internet of vehicles. Future Internet 2020, 12, 69. [Google Scholar] [CrossRef]
- Rehman, A.U.; Naqvi, R.A.; Rehman, A.; Paul, A.; Sadiq, M.T.; Hussain, D. A trustworthy siot aware mechanism as an enabler for citizen services in smart cities. Electronics 2020, 9, 918. [Google Scholar] [CrossRef]
- Cervantes, M.; Ramani, R.; Worthy, P.; Weigel, J.; Viller, S.; Matthews, B. Could the Inherent Nature of the Internet of Things Inhibit Person-to-Person Connection? In Proceedings of the 2016 ACM Conference Companion Publication on Designing Interactive Systems; ACM: New York, NY, USA, 2016; pp. 177–180. [Google Scholar]
- Worthy, P.; Matthews, B.; Viller, S. Trust me: Doubts and concerns living with the Internet of Things. In Proceedings of the 2016 ACM Conference on Designing Interactive Systems; ACM: New York, NY, USA, 2016; pp. 427–434. [Google Scholar]
- Jayasinghe, U.; Lee, H.W.; Lee, G.M. A computational model to evaluate honesty in social internet of things. In Proceedings of the Symposium on Applied Computing; ACM: New York, NY, USA, 2017; pp. 1830–1835. [Google Scholar]
- Anjomshoa, F.; Aloqaily, M.; Kantarci, B.; Erol-Kantarci, M.; Schuckers, S. Social behaviometrics for personalized devices in the internet of things era. IEEE Access 2017, 5, 12199–12213. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. Siot: Giving a social structure to the internet of things. IEEE Commun. Lett. 2011, 15, 1193–1195. [Google Scholar] [CrossRef]
- Savaglio, C.; Ganzha, M.; Paprzycki, M.; Bădică, C.; Ivanović, M.; Fortino, G. Agent-based Internet of Things: State-of-the-art and research challenges. Future Gener. Comput. Syst. 2020, 102, 1038–1053. [Google Scholar] [CrossRef]
- Cicirelli, F.; Guerrieri, A.; Spezzano, G.; Vinci, A. An edge-based platform for dynamic smart city applications. Future Gener. Comput. Syst. 2017, 76, 106–118. [Google Scholar] [CrossRef]
- Nguyen, H.L.; Jung, J.E. SocioScope: A framework for understanding Internet of Social Knowledge. Future Gener. Comput. Syst. 2018, 83, 358–365. [Google Scholar] [CrossRef]
- Romero, D.; Wuest, T.; Stahre, J.; Gorecky, D. Social factory architecture: Social networking services and production scenarios through the social internet of things, services and people for the social operator 4.0. In IFIP International Conference on Advances in Production Management Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 265–273. [Google Scholar]
- Lippi, M.; Mamei, M.; Mariani, S.; Zambonelli, F. An argumentation-based perspective over the social IoT. IEEE Internet Things J. 2017, 5, 2537–2547. [Google Scholar] [CrossRef]
- Fortino, G.; Russo, W.; Savaglio, C.; Viroli, M.; Zhou, M. Opportunistic cyberphysical services: A novel paradigm for the future Internet of Things. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 488–492. [Google Scholar]
- Casadei, R.; Fortino, G.; Pianini, D.; Russo, W.; Savaglio, C.; Viroli, M. A development approach for collective opportunistic Edge-of-Things services. Inf. Sci. 2019, 498, 154–169. [Google Scholar] [CrossRef]
- Casadei, R.; Fortino, G.; Pianini, D.; Russo, W.; Savaglio, C.; Viroli, M. Modelling and simulation of opportunistic IoT services with aggregate computing. Future Gener. Comput. Syst. 2019, 91, 252–262. [Google Scholar] [CrossRef]
- Hauert, C. Cooperation, collectives formation and specialization. Adv. Complex Syst. 2006, 9, 315–335. [Google Scholar] [CrossRef]
- Dorigo, M.; Birattari, M.; Stutzle, T. Ant colony optimization. IEEE Comput. Intell. Mag. 2006, 1, 28–39. [Google Scholar] [CrossRef]
- Fehr, E.; Schmidt, K.M. A theory of fairness, competition, and cooperation. Q. J. Econ. 1999, 114, 817–868. [Google Scholar] [CrossRef]
- Barreira da Silva Rocha, A.; Laruelle, A. Evolution of cooperation in the snowdrift game with heterogeneous population. Adv. Complex Syst. 2013, 16, 1350036. [Google Scholar] [CrossRef]
- Schweitzer, F.; Behera, L. Optimal migration promotes the outbreak of cooperation in heterogeneous populations. Adv. Complex Syst. 2012, 15, 1250059. [Google Scholar] [CrossRef]
- Koponen, I.T.; Nousiainen, M. Formation of reciprocal appreciation patterns in small groups: An agent-based model. Complex Adapt. Syst. Model. 2016, 4, 24. [Google Scholar] [CrossRef]
- Dhelim, S.; Ning, H.; Zhu, T. STLF: Spatial-temporal-logical knowledge representation and object mapping framework. In Proceedings of the 2016 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Budapest, Hungary, 9–12 October 2016; pp. 001550–001554. [Google Scholar]
- Gilbert, N. Agent-Based Models; Sage Publications, Incorporated: Thousand Oaks, CA, USA, 2019; Volume 153. [Google Scholar]
- Grimm, V.; Polhill, G.; Touza, J. Documenting social simulation models: The ODD protocol as a standard. In Simulating Social Complexity; Springer: Berlin/Heidelberg, Germany, 2017; pp. 349–365. [Google Scholar]
- Wilensky, U. NetLogo (and NetLogo User Manual). Available online: http://ccl.northwestern.edu/netlogo/ (accessed on 22 March 2021).
- Centola, D.; Macy, M. Complex contagions and the weakness of long ties. Am. J. Sociol. 2007, 113, 702–734. [Google Scholar] [CrossRef]
- Watts, D.J.; Strogatz, S.H. Collective dynamics of’small-world’networks. Nature 1998, 393, 440. [Google Scholar] [CrossRef] [PubMed]
- Wilensky, U.; Rand, W. An Introduction to Agent-Based Modeling: Modeling Natural, Social, and Engineered Complex Systems with NetLogo; MIT Press: Cambridge, MA, USA, 2015. [Google Scholar]
- Zia, K.; Muhammad, A.; Saini, D.K. Socially aware peers for futuristic web of things. In Proceedings of the 2017 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017; Volume 2, pp. 579–583. [Google Scholar]
- Zia, K.; Saini, D.K.; Farooq, U.; Ferscha, A. Web of social things: Socially-influenced interaction modeling. In Proceedings of the 15th International Conference on Advances in Mobile Computing & Multimedia, Salzburg, Austria, 4–6 December 2017; pp. 123–130. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zia, K.; Farooq, U.; Shafi, M.; Arshad, M. An Agent-Based Model of Task-Allocation and Resource-Sharing for Social Internet of Things. IoT 2021, 2, 187-204. https://doi.org/10.3390/iot2010010
Zia K, Farooq U, Shafi M, Arshad M. An Agent-Based Model of Task-Allocation and Resource-Sharing for Social Internet of Things. IoT. 2021; 2(1):187-204. https://doi.org/10.3390/iot2010010
Chicago/Turabian StyleZia, Kashif, Umar Farooq, Muhammad Shafi, and Muhammad Arshad. 2021. "An Agent-Based Model of Task-Allocation and Resource-Sharing for Social Internet of Things" IoT 2, no. 1: 187-204. https://doi.org/10.3390/iot2010010
APA StyleZia, K., Farooq, U., Shafi, M., & Arshad, M. (2021). An Agent-Based Model of Task-Allocation and Resource-Sharing for Social Internet of Things. IoT, 2(1), 187-204. https://doi.org/10.3390/iot2010010






