A Secure Scheme for Distributed Consensus Estimation against Data Falsification in Heterogeneous Wireless Sensor Networks
Abstract
:1. Introduction
2. System Model
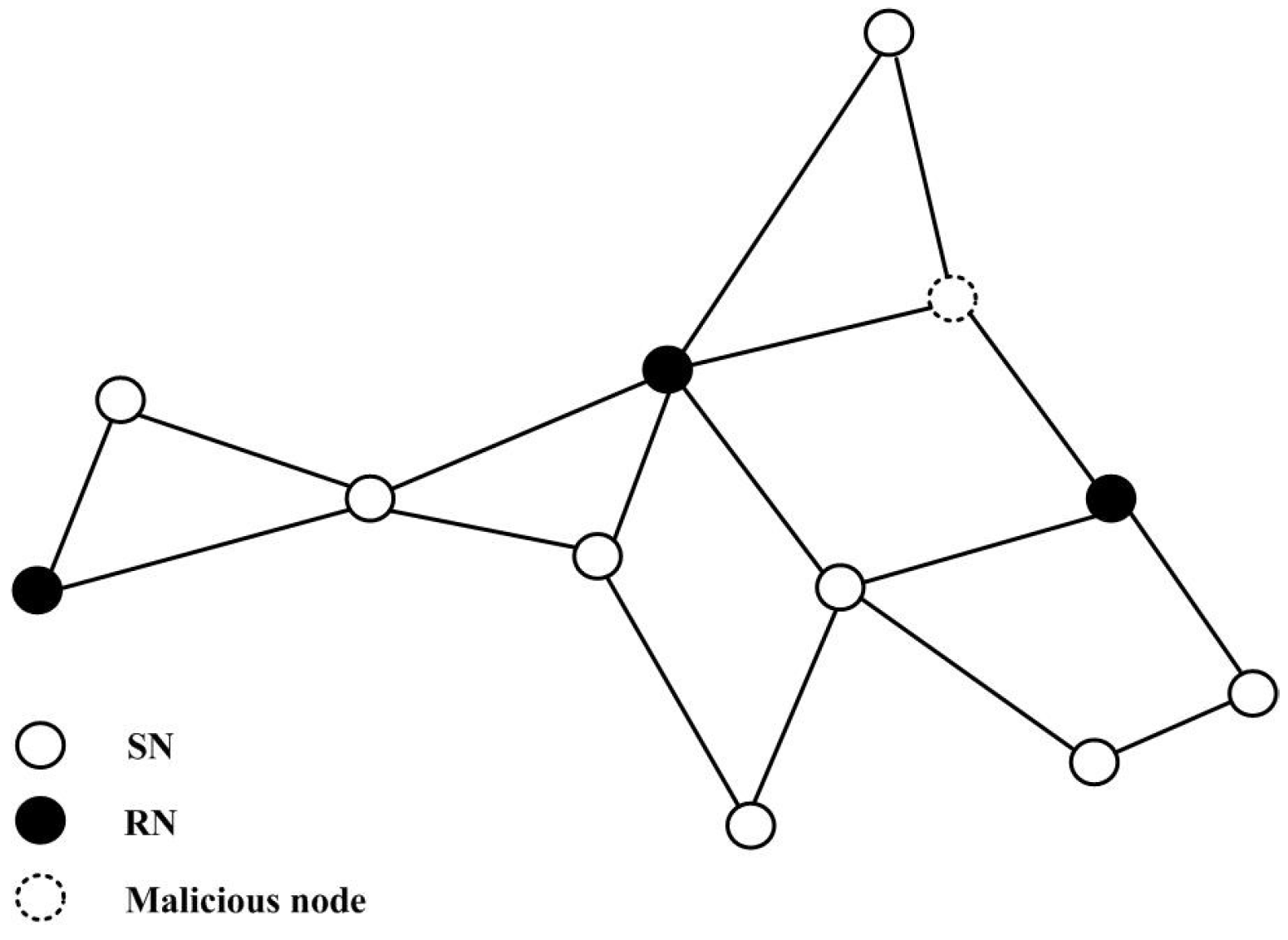
2.1. Network Model
2.2. Attack Model
3. Secure Scheme
3.1. Parameter Adjusted-Based Consensus Scheme
| Algorithm 1: Parameter Adjusted-Based Consensus Scheme (PACS). | ||
| Require: Graph , M SNs, RNs | ||
| Ensure: | ||
| 1: | set | |
| 2: | for do | |
| 3: | set , , and | |
| 4: | i makes the measurement and gets the initial , then transmits to its neighbors. | |
| 5: | end for | |
| 6: | for the consensus is not reached do | |
| 7: | for do | |
| 8: | ||
| 9: | for do | |
| 10: | if then | |
| 11: | ||
| 12: | if then | |
| 13: | ||
| 14: | else | |
| 15: | ||
| 16: | end if | |
| 17: | else | |
| 18: | ||
| 19: | if then | |
| 20: | ||
| 21: | else | |
| 22: | ||
| 23: | end if | |
| 24: | end if | |
| 25: | end for | |
| 26: | if then | |
| 27: | updates its state according to Equation (6) and transmits the state estimation to its neighbors. | |
| 28: | Update and ensure the sum of i-th row sum is 1. | |
| 29: | end if | |
| 30: | end for | |
| 31: | set | |
| 32: | end for | |
3.2. Performance Analysis
4. Evaluation
4.1. Experiments Setup
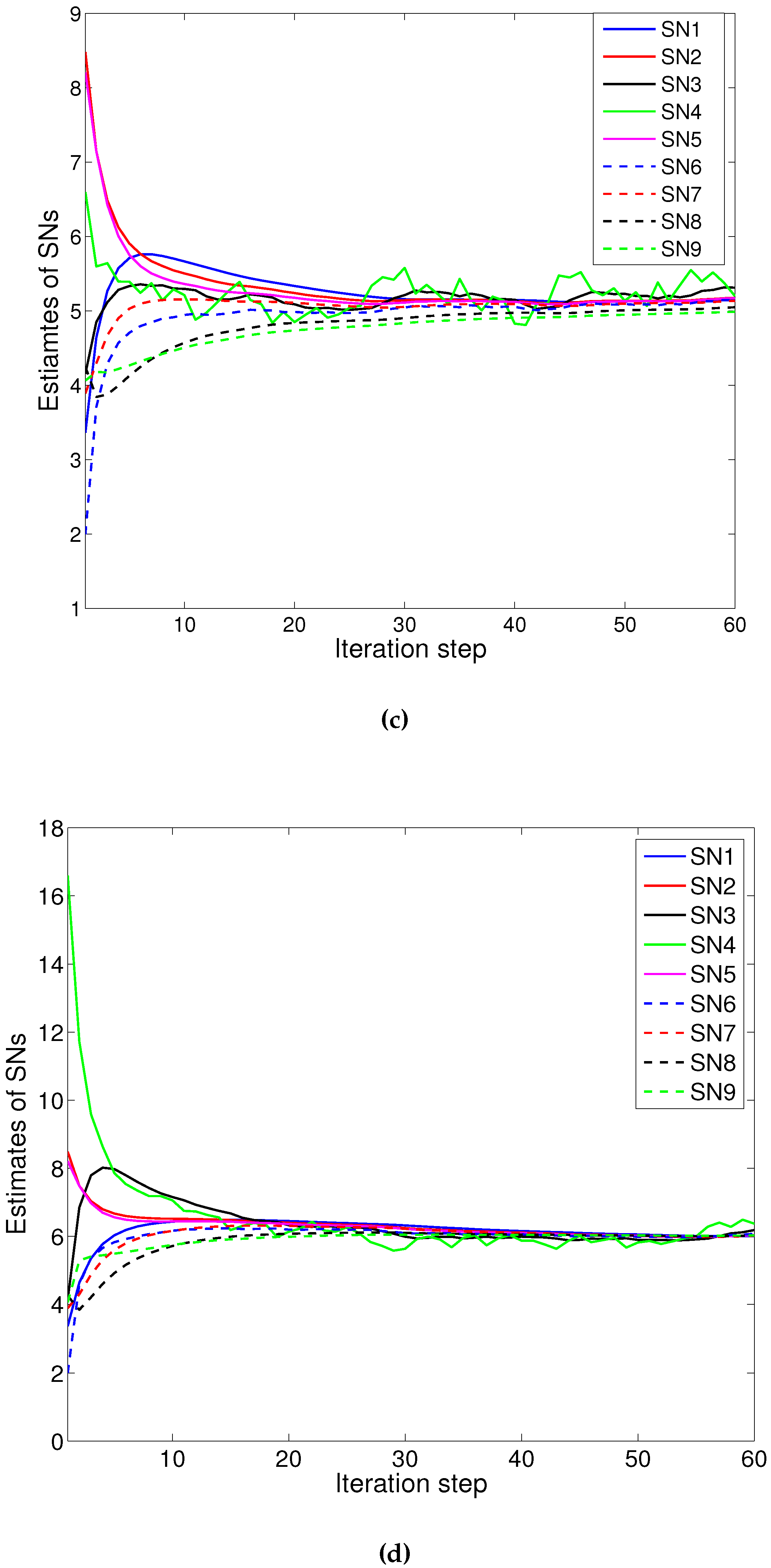
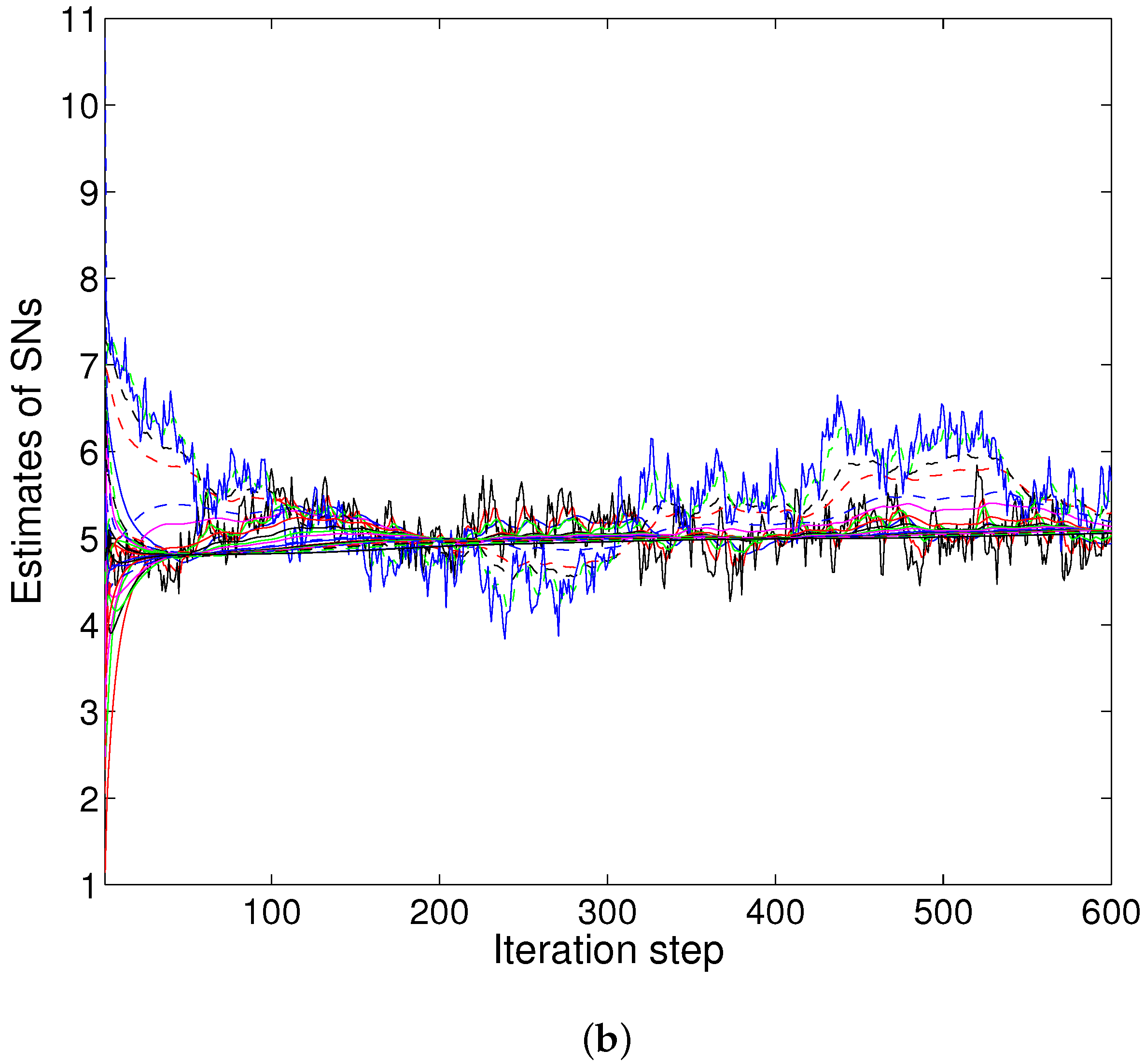
4.2. Numerical Example 1
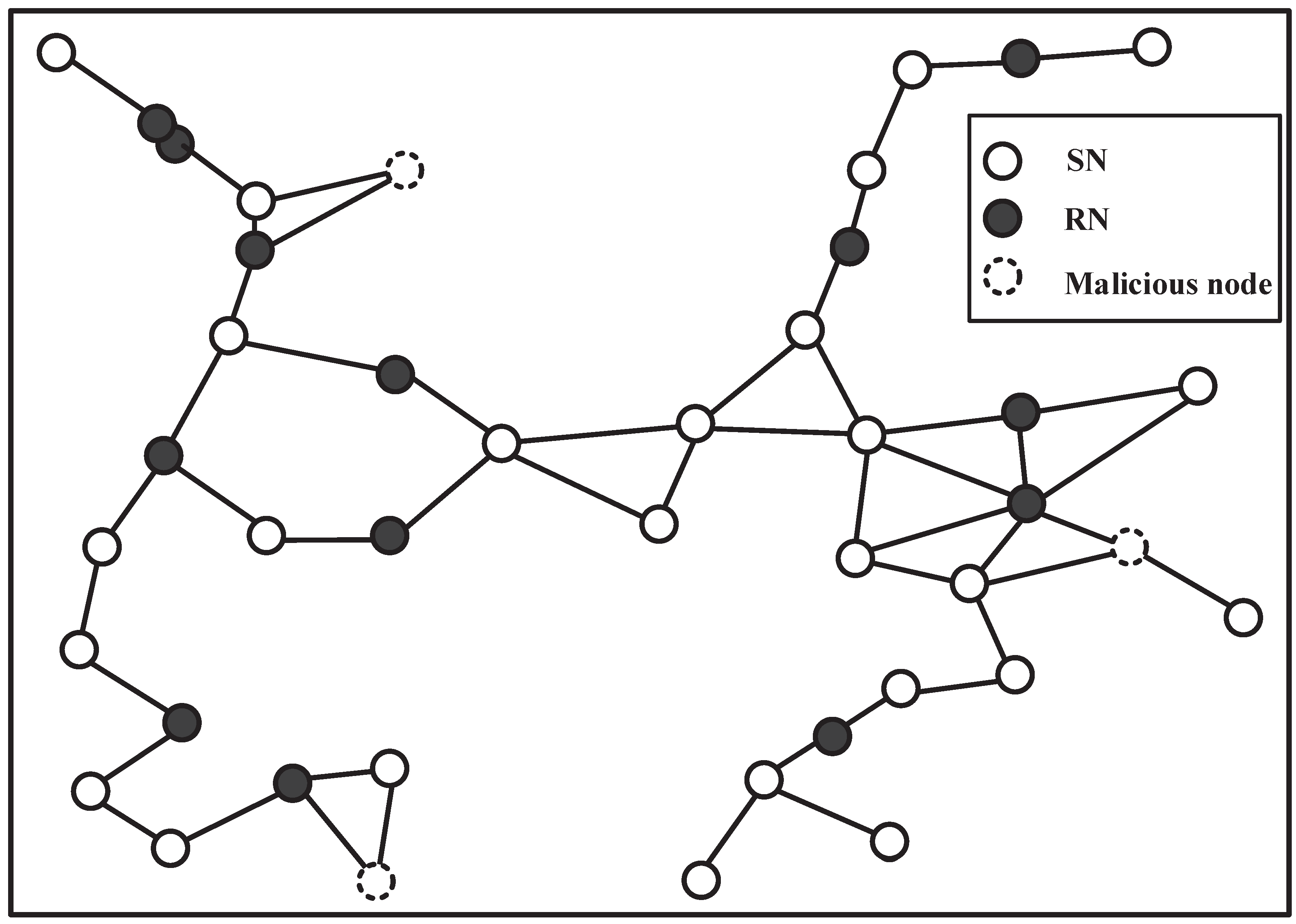
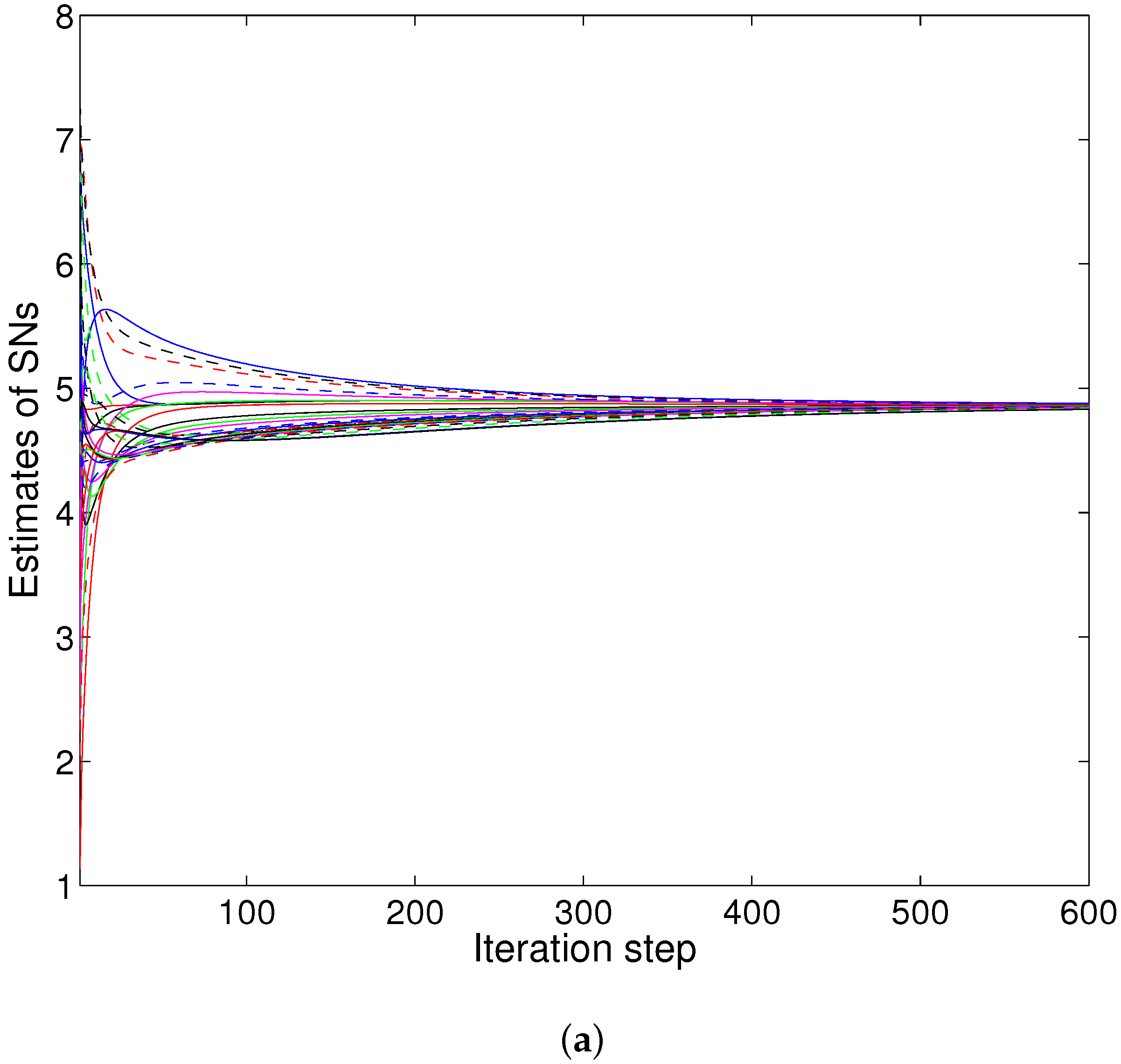
4.3. Numerical Example 2
5. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Gao, T.; Massey, T.; Selavo, L.; Chen, B.; Lorincz, K.; Shnayder, V.; Hauenstein, L.; Dabiri, F.; Jeng, J.; Chanmugam, A.; et al. The advanced health and disaster aid network: A light-weight wireless medical system for triage. IEEE Trans. Biomed. Circuits Syst. 2007, 1, 203–216. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Yu, F.R.; Huang, M. A distributed consensus-based cooperative spectrum-sensing scheme in cognitive radios. IEEE Trans. Veh. Technol. 2010, 59, 383–393. [Google Scholar]
- Buratti, C.; Conti, A.; Dardari, D.; Verdone, R. An overview on wireless sensor networks technology and evolution. Sensors 2009, 9, 6869–6896. [Google Scholar] [CrossRef] [PubMed]
- Xu, K.; Hassanein, H.; Takahara, G.; Wang, Q. Relay Node Deployment Strategies in Heterogeneous Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2009, 9, 145–159. [Google Scholar]
- Cheng, X.; Du, D.; Wang, L.; Xu, B. Relay sensor placement in wireless sensor networks. Wirel. Netw. 2008, 14, 347–355. [Google Scholar] [CrossRef]
- Zhu, S.; Chen, C.; Guan, X. Consensus protocol for heterogeneous multi-agent systems: A Markov chain approach. Chin. Phys. B 2013, 22, 018901:1–018901:5. [Google Scholar] [CrossRef]
- Zhu, S.; Chen, C.; Guan, X. Distributed optimal consensus filter for target tracking in heterogeneous sensor networks. IEEE Trans. Cybern. 2013, 42, 1963–1976. [Google Scholar] [CrossRef] [PubMed]
- Khan, U.A.; Kar, S.; Moura, J.M.F. Distributed sensor localization in random environments using minimal number of anchor nodes. IEEE Trans. Signal Process. 2009, 57, 2000–2016. [Google Scholar] [CrossRef]
- Wei, X.; Li, C.; Zhou, L.; Zhao, L. Distributed Density Estimation Based on a Mixture of Factor Analyzers in a Sensor Network. Sensors 2015, 15, 19047–19068. [Google Scholar] [CrossRef] [PubMed]
- Barbarossa, S.; Scutari, G. Decentralized maximum-likelihood estimation for sensor networks composed of nonlinearly coupled dynamical systems. IEEE Trans. Signal Process. 2007, 55, 3456–3470. [Google Scholar] [CrossRef]
- Olfati-Saber, R.; Fax, J.A.; Murray, R.M. Consensus and cooperation in networked multi-agent systems. IEEE Proc. 2007, 95, 215–233. [Google Scholar] [CrossRef]
- Olfati-Saber, R. Flocking for multi-agent dynamic system: Algorithms and theory. IEEE Trans. Autom. Control 2006, 51, 401–420. [Google Scholar] [CrossRef]
- Mi, S.; Zhu, S.; Chen, C.; Guan, X. TWGS: A Tree Decomposition Based Indoor Pursuit-Evasion Game for Robotic Networks. In Proceedings of the 13th IFAC Symposium on Large Scale Complex Systems: Theory and Applications, Shanghai, China, 7–10 July 2013; pp. 135–140.
- Chen, C.; Zhu, S.; Guan, X.; Shen, X. Wireless Sensor Networks: Distributed Consensus Estimation; Springer: Berlin, Germany, 2014. [Google Scholar]
- Wang, Y.; Attebury, G.; Ramamurthy, B. A Survey of Security Issues In Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2006, 8, 1–23. [Google Scholar] [CrossRef]
- Pathan, A.K.; Lee, H.; Hong, C.S. Security in wireless sensor networks: Issues and challenges. In Proceedings of the 8th International Conference Advanced Communication Technology (ICACT’06), Phoenix Park, UK, 20–22 February 2006; pp. 1043–1048.
- Liu, Y.; Ning, P.; Reiter, M. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 21–32. [Google Scholar] [CrossRef]
- Yan, Q.; Li, M.; Jiang, T.; Lou, W.; Thomas Hou, Y. Vulnerability and protection for distributed consensus-based spectrum sensing in cognitive radio networks. In Proceedings of the International Conference on Computer Communications(INFOCOM’12), Orlando, FL, USA, 25–30 March 2012; pp. 900–908.
- Mo, Y.; Kim, T.H.-J.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyberphysical security of a smart grid infrastructure. IEEE Proc. 2012, 100, 195–209. [Google Scholar]
- Pasqualetti, F.; Bicchi, A.; Bullo, F. Consensus computation in unreliable networks: A system theoretic approach. IEEE Trans. Autom. Control 2012, 57, 90–104. [Google Scholar] [CrossRef]
- LeBlanc, H.J.; Zhang, H.; Koutsoukos, X.; Sundaram, S. Resilient asymptotic consensus in robust networks. IEEE J. Sel. Areas Commun. 2013, 31, 766–781. [Google Scholar] [CrossRef]
- Lu, K.; Qian, Y.; Guizani, M.; Chen, H.H. A framework for a distributed key management scheme in heterogeneous wireless sensor networks. IEEE Trans. Wirel. Commun. 2008, 7, 639–647. [Google Scholar]
- Du, X.; Xiao, Y.; Mohsen, G.; Chen, H. An effective key management scheme for heterogeneous sensor networks. Ad Hoc Netw. 2007, 5, 24–34. [Google Scholar] [CrossRef]
- Kumar, P.; Mika, Y.; Gurtoy, A.; Lee, S.-G.; Lee, H.-J. An Efficient and Adaptive Mutual Authentication Framework for Heterogeneous Wireless Sensor Network-Based Applications. Sensors 2014, 14, 2723–2755. [Google Scholar] [CrossRef] [PubMed]
- Mi, S.; Han, H.; Zhu, S.; Chen, C.; Yang, B.; Guan, X. A Secure Distributed Consensus Scheme for Wireless Sensor Networks Against Data Falsification. In Proceedings of the 11th World Congress on Intelligent Controland Automation (WCICA), Shenyang, China, 29 June–4 July 2014; pp. 3025–3030.
- Liu, S.; Zhu, H.; Li, S.; Li, X.; Chen, C.; Guan, X. An adaptive deviation-tolerant secure scheme for distributed cooperative spectrum Sensing. In Proceedings of the Global Communications Conference (GLOBECOM’12), Anaheim, CA, USA, 3–7 December 2012; pp. 603–608.
- Horn, R.A.; Johnson, C.R. Matrix Analysis; Cambridge Univercity Press: Cambridge, UK, 1985. [Google Scholar]





| Region | 662–670 MHZ | 750–758 MHZ | 798–806 MHZ |
|---|---|---|---|
| 5 | 3.3626 | 8.4791 | 4.1553 |
| 6 | 6.5966 | 1.9973 | 8.2043 |
| 8 | 3.8923 | 4.2489 | 5.0492 |
| 9 | 2.8713 | 8.7158 | 3.9781 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mi, S.; Han, H.; Chen, C.; Yan, J.; Guan, X. A Secure Scheme for Distributed Consensus Estimation against Data Falsification in Heterogeneous Wireless Sensor Networks. Sensors 2016, 16, 252. https://doi.org/10.3390/s16020252
Mi S, Han H, Chen C, Yan J, Guan X. A Secure Scheme for Distributed Consensus Estimation against Data Falsification in Heterogeneous Wireless Sensor Networks. Sensors. 2016; 16(2):252. https://doi.org/10.3390/s16020252
Chicago/Turabian StyleMi, Shichao, Hui Han, Cailian Chen, Jian Yan, and Xinping Guan. 2016. "A Secure Scheme for Distributed Consensus Estimation against Data Falsification in Heterogeneous Wireless Sensor Networks" Sensors 16, no. 2: 252. https://doi.org/10.3390/s16020252
APA StyleMi, S., Han, H., Chen, C., Yan, J., & Guan, X. (2016). A Secure Scheme for Distributed Consensus Estimation against Data Falsification in Heterogeneous Wireless Sensor Networks. Sensors, 16(2), 252. https://doi.org/10.3390/s16020252






