In this section, we review existing MAC protocols for CRBANs and highlight them with regard to their key characteristics and features.
3.1. CR-Based MAC Protocol for Cognitive Wireless Sensor Body Area Networking
In the CR-based MAC (CR-MAC) protocol for wireless sensor body area networks [
15], a separate type of sensor node is used for critical health information and non-critical health information. In this protocol, the network nodes are assumed to have the capability to dynamically adjust their transmission power according to the level of urgency of the traffic. The CR-MAC protocol regulates access by critical and non-critical packets to the transmission medium by transmitting packets with higher and lower transmission powers, respectively. The receiver circuit at the PAN coordination node enables the successful reception of critical packets with higher power, even though other, lower priority packets with a lower power are simultaneously received.
In CR-MAC, three transmission power levels of P1, P2 and P3 are assigned to non-critical traffic, moderately urgent traffic and critical traffic, respectively, where P1 < P2 < P3. Critical traffic has the highest priority, and moderately urgent traffic has the second-highest. The successful transmission of a moderately urgent packet using power level P2 occurs as long as there are no transmitted packets of higher priority in the traffic. Non-critical traffic is subsequently transmitted using power level P1, and the successful transmission of packets requires only a single packet in a time slot.
The CR-MAC protocol was analyzed mathematically for two transmission power levels in [
15]. In the analysis, a star topology composed of a number of different sensor nodes and a single network coordinator was used. The different sensor nodes are composed of reduced function devices (RFDs), and the coordinator is a full function device (FFD). The RFD nodes are classified into critical and non-critical sensor nodes according to their assigned physiological variable of measurement, such as EEG, ECG, heartbeat, blood pressure, temperature,
etc. The RFD nodes periodically report the measured physiological values to the FFD coordinator node, which transfers the data to the server through other networks, such as cellular systems or wireless local area networks (WLANs), where the data are monitored and analyzed.
Critical traffic throughput is first analyzed because critical traffic transmission is independent of non-critical traffic transmission. The output is then applied to the analysis of non-critical traffic throughput, which depends on the transmission of critical traffic. As an essential parameter, the traffic rejection rate for critical and non-critical packets was also analyzed in [
15]. The probability of critical traffic rejection depends on the number of allowed critical packet retransmissions. For the transmission of the first packet, the probability of packet transmission failure is
, where
is the probability of a successful critical packet transmission in a particular time slot. The probability of critical packet transmission failure is
, where
is the number of allowed packet retransmissions for critical nodes.
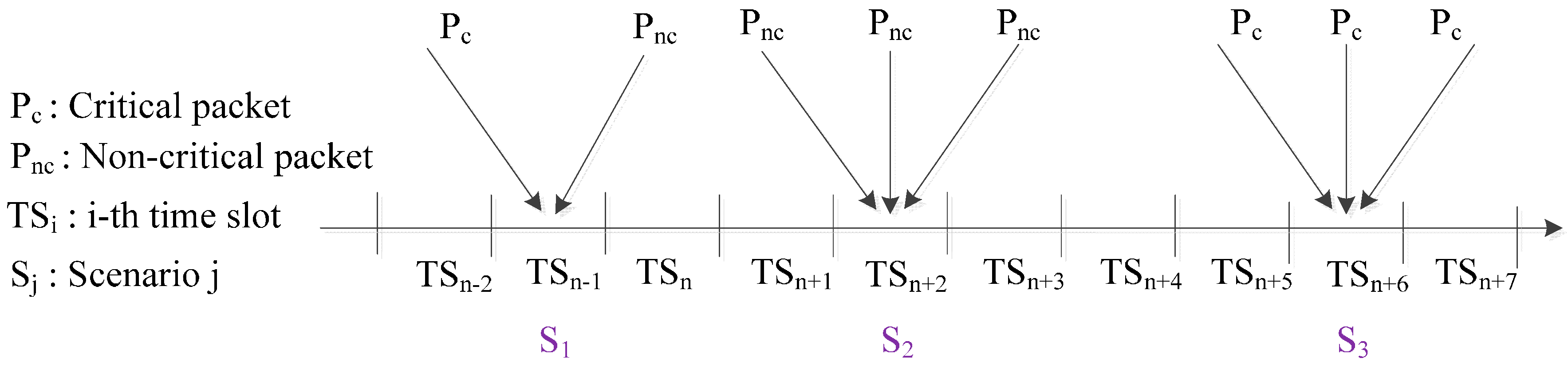
In the CR-MAC protocol, packet collision scenarios are defined in three states, as shown in
Figure 1:
S1: One critical packet arrival of transmission power level P2 and one or more non-critical packet arrivals of P1;
S2: More than one non-critical packet arrival;
S3: More than one critical packet arrival.
In S1, the collision is partial due to the critical packet transmission being considered successful because of the cognitive radio transmission feature of CR-MAC. However, collisions occur between non-critical packets, as well. The states S2 and S3 involve the simultaneous arrival of more than one non-critical packet and more than one critical packet, respectively.
In the CR-MAC protocol, there are three successful packet transmission scenarios, as shown in
Figure 2:
Single critical packet arrival and the arrival of one or more non-critical packets in the scenario represented by state S1
Single non-critical packet arrival, in the scenario represented by state S2
Single critical packet arrival, represented by state S3
Figure 1.
Collided packet transmission in cognitive radio (CR)-MAC.
Figure 1.
Collided packet transmission in cognitive radio (CR)-MAC.
Figure 2.
Successful packet transmission in CR-MAC.
Figure 2.
Successful packet transmission in CR-MAC.
CR-MAC achieves not only relatively high throughput, but also QoS promising for traffic of different priority classes. In CR-MAC, the traffic of sensor nodes is classified into critical traffic and non-critical traffic. After critical traffic throughput is first analyzed, the output is then applied to the analysis of non-critical traffic throughput, which depends on the transmission of critical traffic. Critical and non-critical traffic are prioritized according to transmission power. The analytical and simulation-based results disclosed different practical design approaches as follows: In critical nodes, when the number of packet retransmissions increases, the throughput increases and the number of packet rejections decreases. In non-critical nodes, the throughput decreases and the packet rejection rate increases. When the number of packet retransmissions in critical nodes reaches a certain value, the throughput of critical and non-critical nodes reaches a saturation point.
3.2. Dynamic Channel Adjustable Asynchronous Cognitive Radio MAC Protocol
Because of the fast channel switching capability of asynchronous MAC, the dynamic channel adjustable asynchronous cognitive radio MAC (DCAA-MAC) protocol [
16] provides low latency, energy efficiency, configurability and no need for synchronization in wireless medical body area networks.
At initialization, each node scans and selects a channel with the best conditions (e.g., low signal-to-noise ratio (SNR), least frequently used, etc.). Each node in the network goes to sleep and wakes up periodically and independently. A node first sends a preamble; then, after receiving the acknowledgment (ACK) message from the destination node, it sends the data packets. On the receiver side, the receiver detects the preamble and remains woken up in order to receive the data. Once transmission is complete, both the sender and receiver nodes go to sleep mode. If the node detects interference (appearance of noise or PUs) on its channel, it switches to another available channel for effective communication.
Multiple channels allow the maintenance of effective communication even upon the appearance of PUs. Nodes detect signals with greater frequency than the threshold during clear channel assessment (CCA) with a fast sensing period on the current channel and listen to signals to find the address of the destination periodically. If the address of the destination matches its own address, the node sends the ACK message; otherwise, it goes to sleep mode. If the address of the destination is not decoded, it determines that there is interference or that PUs have appeared and switches to another channel for PU protection and QoS provision. The node switches to a control channel and listens to find another node that is broadcasting a channel switching preamble (CSPreamble). After receiving the preamble, the node transmits the channel switching ACK (CSACK) message to the source node and switches to the channel.
Spectrum sensing is one of the major requirements of cognitive radio. Energy detection and feature detection are the most commonly used techniques for spectrum sensing in the CR environment. In feature detection, the presence of primary users is determined by extracting specific features. The feature detection technique is most effective for CR networks, but requires significantly long sensing times and is computationally complex. Energy detection is the optimal solution to sense the presence/absence of PUs. In DCAA-MAC, channel switching is performed on the basis of energy detection. The fast channel switching mechanism provides QoS for medical body area sensor networks.
In DCAA-MAC, PU protection and QoS provision are considered, that is, a node switches to another channel if the address of the destination is not decoded, by assuming that PUs have appeared. Channel switching is performed based on energy detection to provide QoS. Each node goes to sleep mode and wakes up periodically and independently of others. DCAA-MAC has low energy consumption and low latency and allows coexistence with simultaneously operating and independent networks.
3.3. Asynchronous MAC Protocol for Spectrum Agility
Energy consumption plays a major role in the design of wireless body area sensor networks (WBASNs). The wireless spectrum in ISM bands becomes crowded and causes coexisting interference. High coexisting interference in networks causes high energy consumption, increased packet delay and low network throughput. An energy-efficient MAC protocol, the cognitive-receiver initiated cycled receiver (C-RICER), was designed for WBASNs in high interference environments [
17]. C-RICER adjusts both channel frequency and transmission power to reduce interference and energy consumption. The main purpose of applying CR is to maintain the SNR for data exchange and to overcome the disadvantages of high coexisting interference in WBANs. By dynamically scanning and switching channels, WBANs can avoid coexisting interference, save energy and reduce packet drops and packet delays.
The energy required for the cognitive task of C-RICER is mainly consumed at the coordinator. The spectrum agility function of C-RICER is considered to be a very important characteristic of WBANs. The use of a transceiver-per-sensor node with energy constraints renders the design of C-RICER more challenging and different from traditional cognitive MAC protocols. Traditional MAC protocols are divided into two families depending on how a node gains medium access: contention-based and reservation-based protocols.
The contention-based MAC is more suitable for WSNs, because of limits on traffic and energy [
18]. Receiver-initiated protocols in the contention-based family seem more suited to the context of WBANs. A well-known protocol in this family is the RICER protocol; RICER3b and RICER5b are variants of RICER according to the number of required handshakes. In the RICER3b protocol, the destination node with no data packet to transmit wakes up periodically and transmits a short wakeup beacon to indicate that it is awake. Having transmitted the beacon, it monitors the channel for a response; if there is no response, the node goes back to sleep mode. A source node with data to transmit stays awake, monitors the channel and awaits a wakeup beacon from the destination nodes.
The use of beacons in RICER3b is different than that in ZigBee [
19]. In ZigBee, the beacons are used to synchronize the superframes of nodes. The data are transmitted using the carrier sense multiple access with collision avoidance (CSMA-CA) algorithm based on an appropriate back-off timer. However, in the case of RICER3b, having received a wakeup beacon, the source node instantly sends back a buzz signal and starts transmitting data. Having received the buzz signal, the destination stays awake and waits for data from the source node.
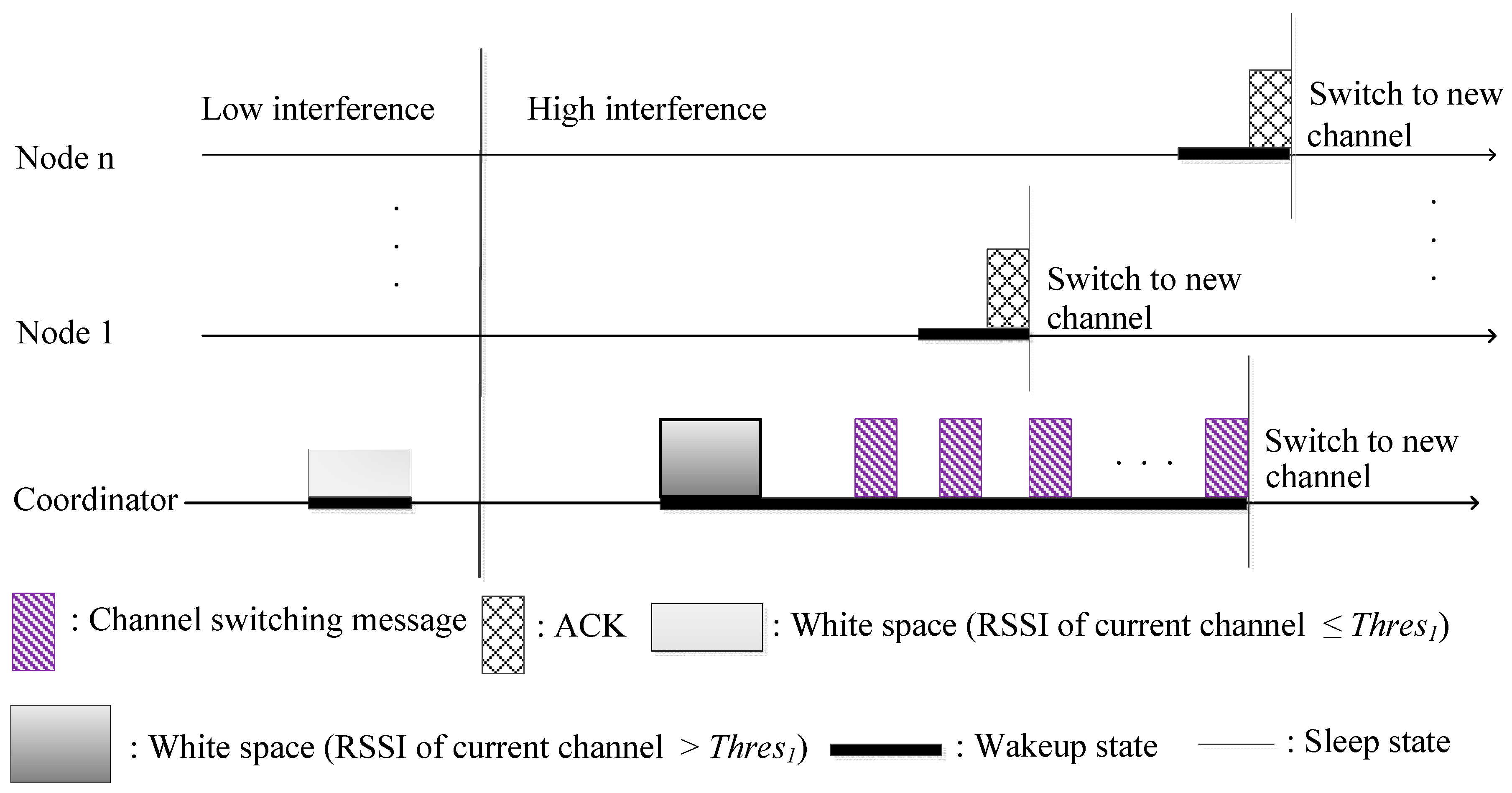
The main objective of C-RICER is early detection of interference in its working channel. Channel sensing is periodically performed at the coordinator. According to the detected level of interference, the WBASN can adaptively switch to the channel with the lowest interference to prevent coexisting interference. The conceptual operation in C-RICER is shown in
Figure 3. In C-RICER, sensing and switching is continuously performed during the operation. Channel inferences can be unpredictable, which prompts frequent channel switching and costs a considerable amount of energy. To address this, C-RICER uses power adaption methods prior to considering channel adaption. The working mechanism of C-RICER involves two tasks: a data exchange task and a cognitive task. The data exchange task is used for data collection, and the cognitive task is used to dynamically adapt both the transmission power and the channel according to the interference levels in question.
Data communication in C-RICER is based on RICER3b, with the destination node as the coordinator and the source as the sensor node. The coordinator wakes up and sends a wakeup beacon. The sensor node receives the beacon and transmits a buzz signal to caution the coordinator to wait for data. Having received the buzz signal, the coordinator waits for data. The sensor node sends the data and waits for the ACK signal. The coordinator receives the data and sends the ACK to the sensor node. The cognitive task of C-RICER has three main features: channel sensing, power adaption and channel adaption.
Figure 3.
Conceptual operation in cognitive-receiver initiated cycled receiver (C-RICER).
Figure 3.
Conceptual operation in cognitive-receiver initiated cycled receiver (C-RICER).
Channel sensing is the initial step in detecting interference. The received signal strength indicator (RSSI) is used to measure the interference level in different channels. In WBASNs, the coordinator is the node in the network most suited to channel sensing. It is the only node that has less energy constraints than sensor nodes in the network; thus, exploiting the energy at the coordinator instead of sensor nodes can prolong the network’s lifetime. Communication is only established after a transmitter has successfully received a wakeup beacon from a receiver. The coordinator of C-RICER periodically senses the interference level only at its current channel instead of in the entire frequency band in order to reduce the required sensing energy. The coordinator scans for the interference level of the remaining channels only when the interference level of its current channel is greater than a threshold value.
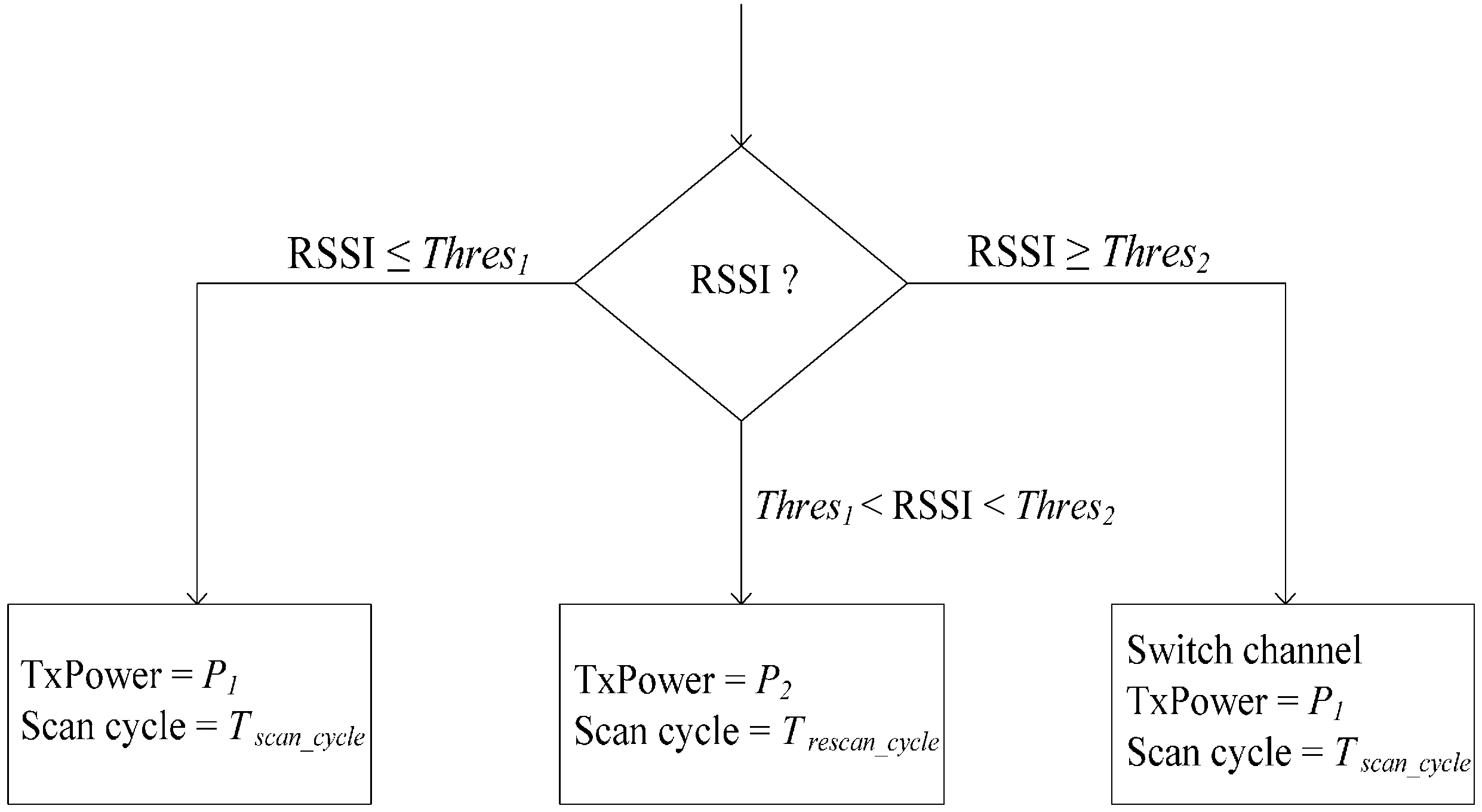
Not only can increasing the transmission power enhance SNR, it can also reduce retransmissions. As shown in
Figure 4, transmission powers (TxPowers)
P1 and
P2 (
P1 <
P2) and interference threshold values
Thres1 and
Thres2 are specified in the transceiver at each node. The transceiver of each sensor node will work at its default transmission power
P1 if the RSSI of the current working channel is less than
Thres1. When the RSSI of the current channel is greater than
Thres1, but less than
Thres2, TxPower increases to
P2. Once
P2 is used, the coordinator will adaptively change its scanning cycle by
Trescan_cycle seconds to rescan the channel.
If the RSSI of the current channel is less than Thres1, the network will return to using P1. The coordinator scans the remaining channels to build the interference map when the RSSI is higher than Thres1. If the RSSI of the current working channel is greater than Thres2, the coordinator also scans the remaining channels to build the interference map. The WBASN will switch to the channel with the lowest interference level without changing transmission power. The coordinator utilizes the wakeup beacon message to broadcast TxPower information. The sensor nodes extract the bit from the beacon message. If the bit is zero, P1 is used; otherwise, P2 is used.
Figure 4.
Power adaption strategy in C-RICER. RSSI, received signal strength indicator; TxPower, transmission power.
Figure 4.
Power adaption strategy in C-RICER. RSSI, received signal strength indicator; TxPower, transmission power.
When the interference level of the current working channel is greater than
Thres2, the WBASN decides to switch to a new channel. The C-RICER coordinator sends the channel switching information to the sensor nodes. Two transceivers are used at each node: one for data transfer and the other for channel information [
18]. The wakeup function of the sensor nodes depends on the demand to send data. Sensor nodes with different sensing functions will wake up randomly and will not receive the switching information simultaneously from a coordinator. A checklist table is used by the coordinator to gather information regarding sensor nodes that successfully received the switching information.
Figure 5 shows the channel switching algorithm. Once a channel switching decision is made, the index of the channel with the lowest RSSI is attached to the channel switching message. The coordinator periodically broadcasts the channel switching message and waits for the ACK message from the sensor nodes. The channel switching checklist table of the coordinator is filled with successfully received ACK messages from a sensor node. If there is a data packet to transmit, the sensor nodes will wake up and wait for the wakeup beacon form the coordinator.
Figure 5.
Channel switching in C-RICER.
Figure 5.
Channel switching in C-RICER.
In C-RICER, power adaption methods are used prior to consider channel adaption because channel inferences can be unpredictable and frequent channel switching costs a considerable amount of energy. Furthermore, sensing energy is additionally reduced by sensing the interference level only at the current channel instead of in the entire frequency band. In addition, the C-RICER protocol with cognitive functions eludes interference and enhances network performance. C-RICER adjusts both channel frequency and transmission power to reduce interference and energy consumption. By dynamically scanning and switching channels, the WBANs can avoid coexisting interference, save energy and reduce packet drop and packet delay. In a high-interference environment involving high energy consumption, the C-RICER protocol can outperform RICER3b.
3.4. Cognitive Radio for Medical Body Area Networks Using Ultra-Wideband
Medical body area networks (MBANs) have been introduced to unlicensed frequency bands, where mutual interference between electronic devices is high. CR technology can potentially alleviate such problems in MBANs and increase the efficiency of spectrum management. In [
20], CR features based on ultra-wideband (UWB) technology for MBANs were proposed by considering both the PHY and MAC layers. A WBAN comprises multiple sensor nodes capable of sampling, processing and communicating biomedical information [
21]. Cognitive capabilities are implemented in the body network controller (BNC) using impulse radio (IR) and multiband orthogonal frequency-division multiplexing (MB-OFDM). Impulse radio ultra-wideband (IR-UWB) technology was introduced as a solution in IEEE 802.15.6 and is currently being developed by the IEEE 802.15.6 Task Group 6 [
22].
The advantages of IR-UWB technologies are their low power, low complexity and low cost with highly reliable wireless communication. The main objective of the standard is to specify a MAC sublayer that can support several PHY layers, including UWB. IR-UWB provides high QoS, and frequency modulation UWB (FM-UWB) is optimized for low power consumption and reliable communication.
The European Computer Manufacturers Association’s ECMA-368 specification is a high-rate UWB PHY and MAC wireless standard, uses MB-OFDM and divides the spectrum into 14 bands of 528 MHz each [
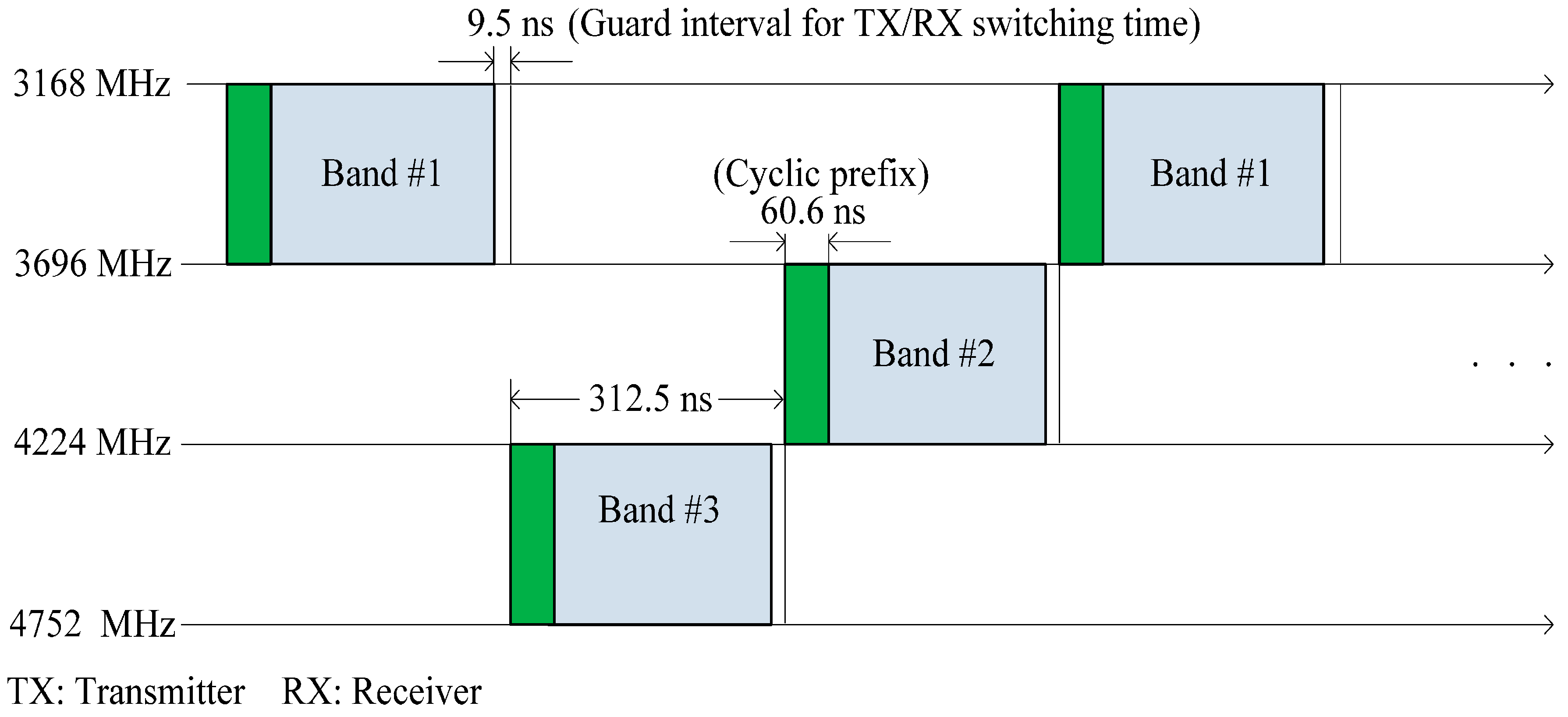
23]. OFDM is based on a frequency diversity transmission scheme that distributes modulated data across closely and mutually overlapping space. An OFDM signal is generated in the frequency domain by using inverse fast Fourier transform (IFFT) to create a time domain multiplexed signal. UWB signals have an inherent noise-like behavior that makes UWB difficult to detect and requires a complex encryption algorithm. In MB-OFDM, symbols are interleaved over multiple sub-bands across time and frequency, as shown in
Figure 6. By interleaving the OFDM symbols across sub-bands, multiband UWB can maintain the power level associated with a single-band OFDM. The characteristics of UWB technology can be exploited to turn a BNC into a cognitive radio controller (CRC) that controls the transmission parameter of CR clients. The communication links between the sensors and the BNC should be implemented using IR-UWB, which is specified by IEEE 802.15.6.
The architecture for CRC consists of two transceivers: an IR-UWB transceiver with on-off keying (OOK) and an MB-OFDM UWB transceiver. The division of the 3.1–10.6 GHz UWB spectrum into 14 sub-bands of 528 MHz each is adopted. The lower UWB frequency band (3.1–4.8 GHz) is enclosed with three sub-band frequencies at 3232, 3960 and 4488 MHz. The three sub-band frequencies are preferred for first-tier communication, because of their better propagation characteristics. The MB-OFDM transceiver also protects medical devices and sensors from UWB interference by using frequency domain spectrum shaping.
Figure 6.
Multiband orthogonal frequency-division multiplexing (MB-OFDM).
Figure 6.
Multiband orthogonal frequency-division multiplexing (MB-OFDM).
UWB facilitates a high processing gain and allows coexistence with a narrow wide-band system through spectrum shaping. Spectrum shaping can be achieved by adopting time hopping codes using a pulse-position modulation scheme or the pulse shape at a transmitter. The MB-OFDM UWB system provides clear advantages over IR-UWB in terms of sensing using power spectral density (PSD). A sub-band or channel ranking scheme can be implemented using a combination of two methods: using the sub-band’s PSD information to identify available channels and using bit error rate (BER) information obtained from active channels to yield channel quality [
24].
To avoid interferences and collisions between signals, wireless devices need to coordinate access time periods with their neighbors. This type of coordination is governed by the MAC sublayer. The IEEE 802.15.6 standard is used for the intra-WBAN tier, whereas inter-tier access is provided by ECMA-368 [
23]. IEEE 802.15.6 supports the beacon and non-beacon modes of operations. It is similar to MAC defined for IEEE 802.15.4, except for the definition of multiple phases in the time division multiple access (TDMA) frame. Here, the standard defines exclusive access phases (EAPs) for high-priority devices, such as emergency signals related to a patient’s vital signs, random access phases (RAPs) based on slotted Aloha, contention access phases (CAPs) and Type I/II phases based on polling. The ECMA-368 MAC provides a distributed reservation-based channel access mechanism, as well as a prioritized contention-based channel access mechanism. The architecture of the ECMA-368 MAC is fully distributed.
All devices provide all required MAC functions and optional functions as determined by the application. No device acts as a central coordinator. Channel time is divided into superframes, with each superframe composed of two major parts: the beacon period (BP) and the data period. The BP is organized into slots and is used to achieve network synchronization, exchange reservation and scheduling information for medium access purposes. During the data period, devices send and receive data using prioritized contention access (PCA) or in reservations established using the distributed reservation protocol (DRP).
Although beacons make network operations significantly simpler, it should be noted that beacon-less operation is possible, as well, by relying on header extensions within the physical layer service data unit used for piggybacking control information. The CRC sends the following information to the IR-UWB devices: schedule of sensing and data reporting and input of selected pulse shapes according to the results of sensing. The 802.15.6 MAC operates using TDMA and supports beacon mode, where the BNC sends broadcast information towards the WBAN devices followed by a TDMA frame. The beacon can be modified to include shaping information (e.g., pulse shape, code parameter, etc.) for IR-UWB devices.
This protocol functionally adopts IEEE 802.15.6 for communication in intra-WBAN tiers and ECMA-368 in inter-WBAN tiers. The distributed reservation-based channel access mechanism is also supported in addition to the prioritized contention-based channel access mechanism. Of course, the design of the MAC protocol for a CR network is among the challenging tasks if the network needs to operate in a distributed fashion [
25]. Further research is needed to manage the multiple radio access technologies (RATs) available in CRC.
3.5. HCVP: Hybrid Cognitive Validation Platform for WBANs
Because of their complexity and energy inefficiency, field-programmable gate arrays (FPGAs) are not reliable for wireless networks, like WBANs. Instead, a hybrid cognitive validation platform (HCVP) [
26] was proposed by integrating software and hardware devices. An adaptive CR-MAC algorithm was implemented to minimize the impact of interference. HCVP is based on programmable system-on-chip (SoC) processors and provides a simulation environment close to the practical scenario.
Network simulation tools, such as network simulator version 2 (NS-2), optimized network engineering tool (OPNET),
etc., are widely used and are convenient to develop, deploy, debug and modify different algorithms and parameters. However, the simulation software faces several challenges, such as modifying the PHY layer, which is very difficult to accurately implement. The HCVP is composed of two parts, the lower part and the upper part. The lower part consists of the PHY and MAC layers, and the upper part comprises the CR algorithm and the network layer.
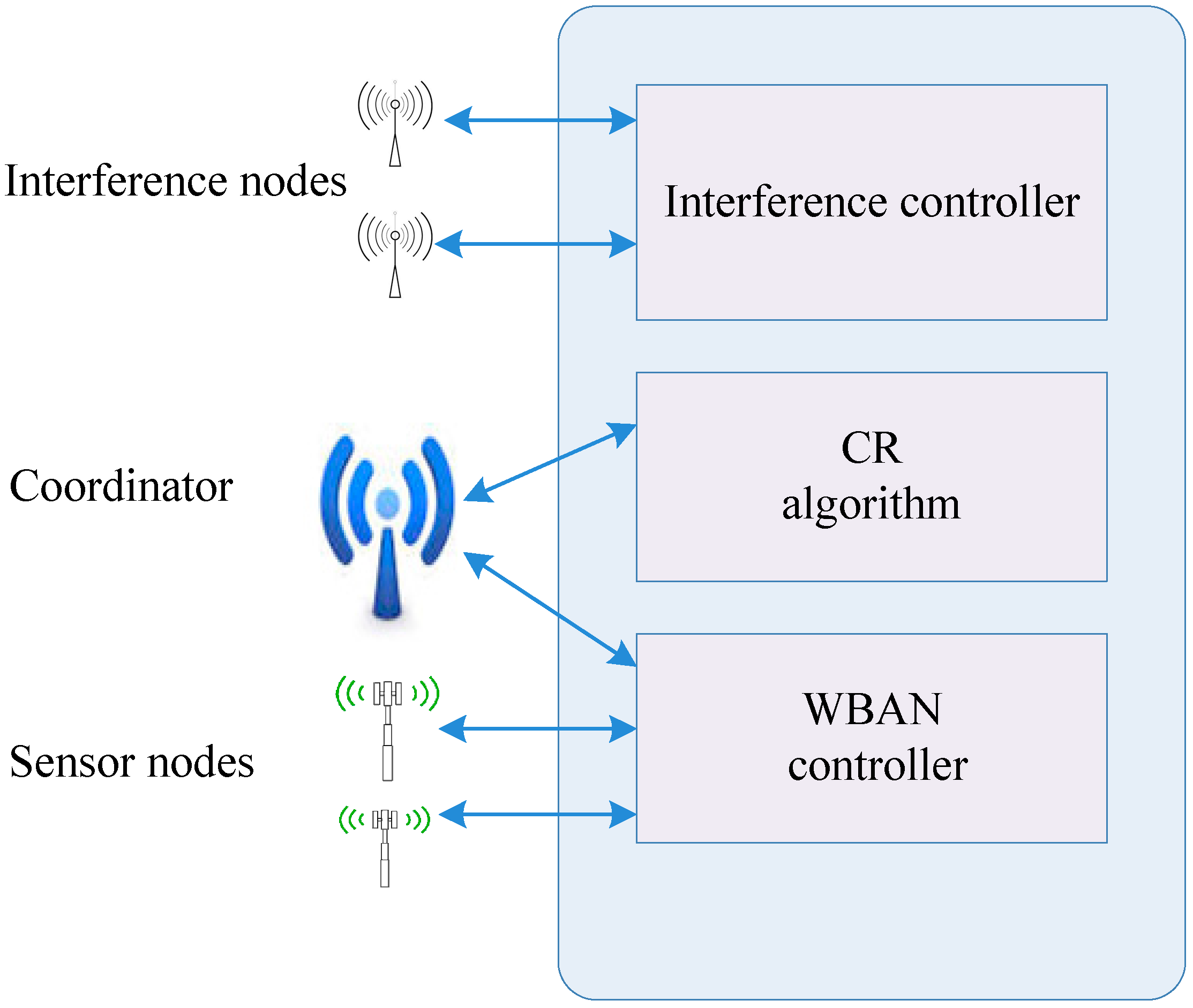
Figure 7 shows the system architecture of HCVP. The interference controller generates traffic distribution for the evaluation. In HCVP, the workflow of a CRBAN includes the WBAN control process and the CR process.
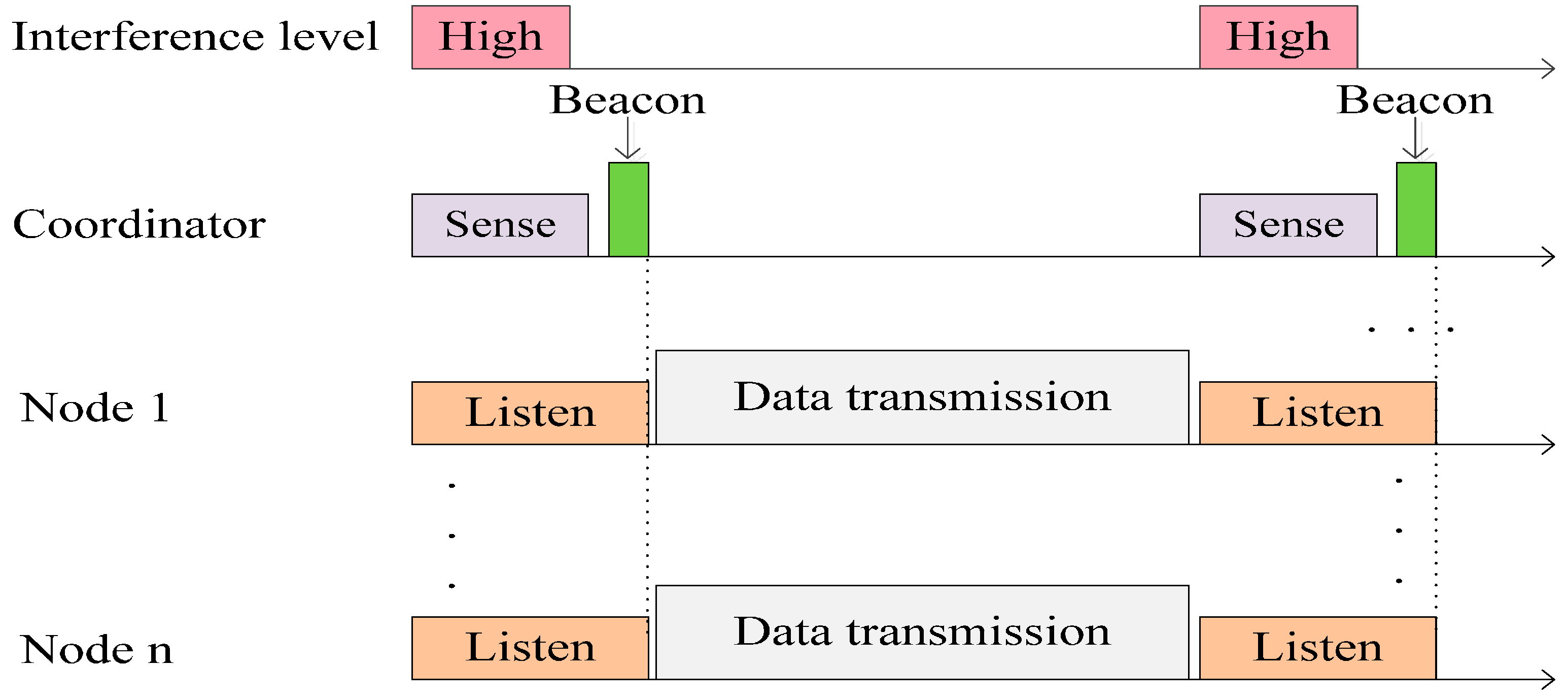
To mitigate coexisting interference, an adaptive CR MAC is implemented, as shown in
Figure 8. The coordinator node is equipped with a high-capacity battery. The nodes in a CRBAN form a star topology with the central coordinator node. The coordinator node assumes the responsibility of managing the entire CRBAN, as well as CR functions. The CR algorithm analyzes the channel parameters according to sensing results, estimates the idle time and passes the result on to the network controller. The network coordinator broadcasts a beacon with the information regarding each superframe. Having received a beacon, member nodes attempt to access the channel during a superframe.
For the implementation of HCVP, a programmable wireless SoC CC2510 was used. CC2510 is a high-performance, low-cost, low power consumption 2.4-GHz system SoC designed for power-critical wireless systems. This chip is integrated with a microcontroller, memory, RF transceiver and other common interferences, such as the universal synchronous/asynchronous receiver/transmitter (USART). In this system, the MAC layer is bound to the firmware of SoC, whereas the PHY layer corresponds to the RF module. To evaluate the performance of the adaptive MAC algorithm, two different traffic models are used. The exponential distribution model is applied to generate same-frequency interference. Four categorized priority levels of the traffic model are established based on real applications, such as mobile healthcare. Without CR functions, the collision rate increases linearly according to the increase in interference traffic.
Figure 7.
System architecture of hybrid cognitive validation platform (HCVP).
Figure 7.
System architecture of hybrid cognitive validation platform (HCVP).
Figure 8.
Adaptive CR-MAC diagram.
Figure 8.
Adaptive CR-MAC diagram.
The HCVP platform effectively integrates the hardware and software with the PHY and MAC layers working on practical hardware devices and the CR algorithm. That is, HCVP is based on programmable SoC processors, in which a simulation environment close to the practical scenario is provided, as well. The network throughput is greatly improved by implementing the CR algorithm, because the collision rate gradually decreases when the CR algorithm is introduced. The channel estimation is effectively carried out on the basis of the RSSI measured during the sensing period and the packet collision rate during the WBAN accessing period. HCVP achieves excellent performance on energy efficiency and is suitable for the validation of power-critical applications.