The Mine Locomotive Wireless Network Strategy Based on Successive Interference Cancellation
Abstract
:1. Introduction
2. The Problem Model
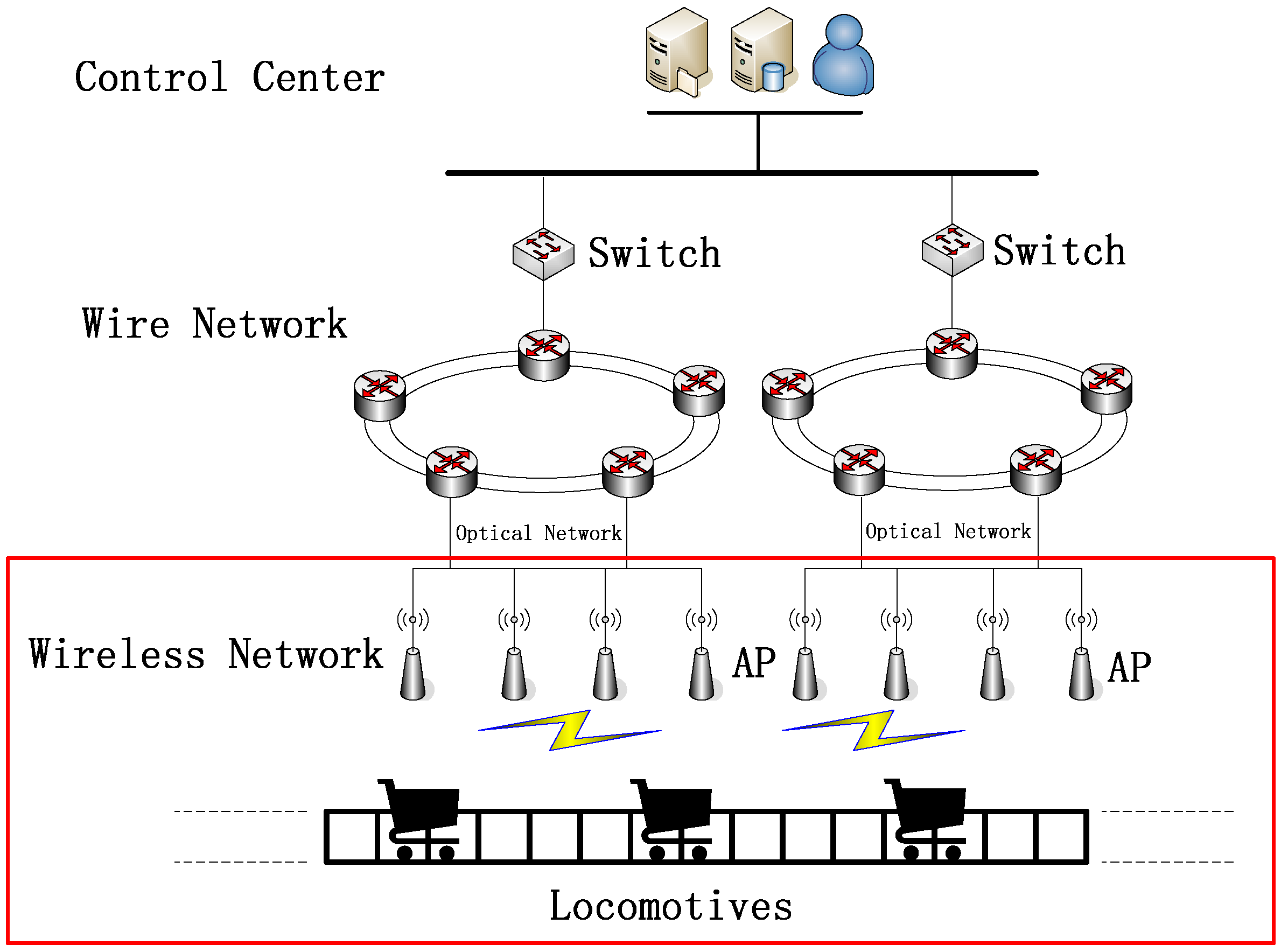

3. The Optimal Locomotive Communication Strategy Based on SIC
3.1. Some Theorems

3.2. New Model and the Algorithm
- Divide the whole scheduling time into several segments.
- Divide each segment into several time slots, arrange these time slots for locomotives. If a locomotive is in a time slot, it means the locomotive can transmit in this time slot. Otherwise, it means the locomotive can not transmit.
- To each locomotive, give the transmitting power scheme when it transmits.

4. Simulation Results
4.1. Results for a Wireless Network with 20 Locomotives
| n | Start Time (s) | n | Start Time (s) | n | Start Time (s) | n | Start Time (s) |
|---|---|---|---|---|---|---|---|
| 1 | 0 | 6 | 56 | 11 | 102 | 16 | 146 |
| 2 | 13 | 7 | 67 | 12 | 108 | 17 | 155 |
| 3 | 23 | 8 | 76 | 13 | 119 | 18 | 168 |
| 4 | 37 | 9 | 88 | 14 | 127 | 19 | 181 |
| 5 | 50 | 10 | 96 | 15 | 138 | 20 | 193 |
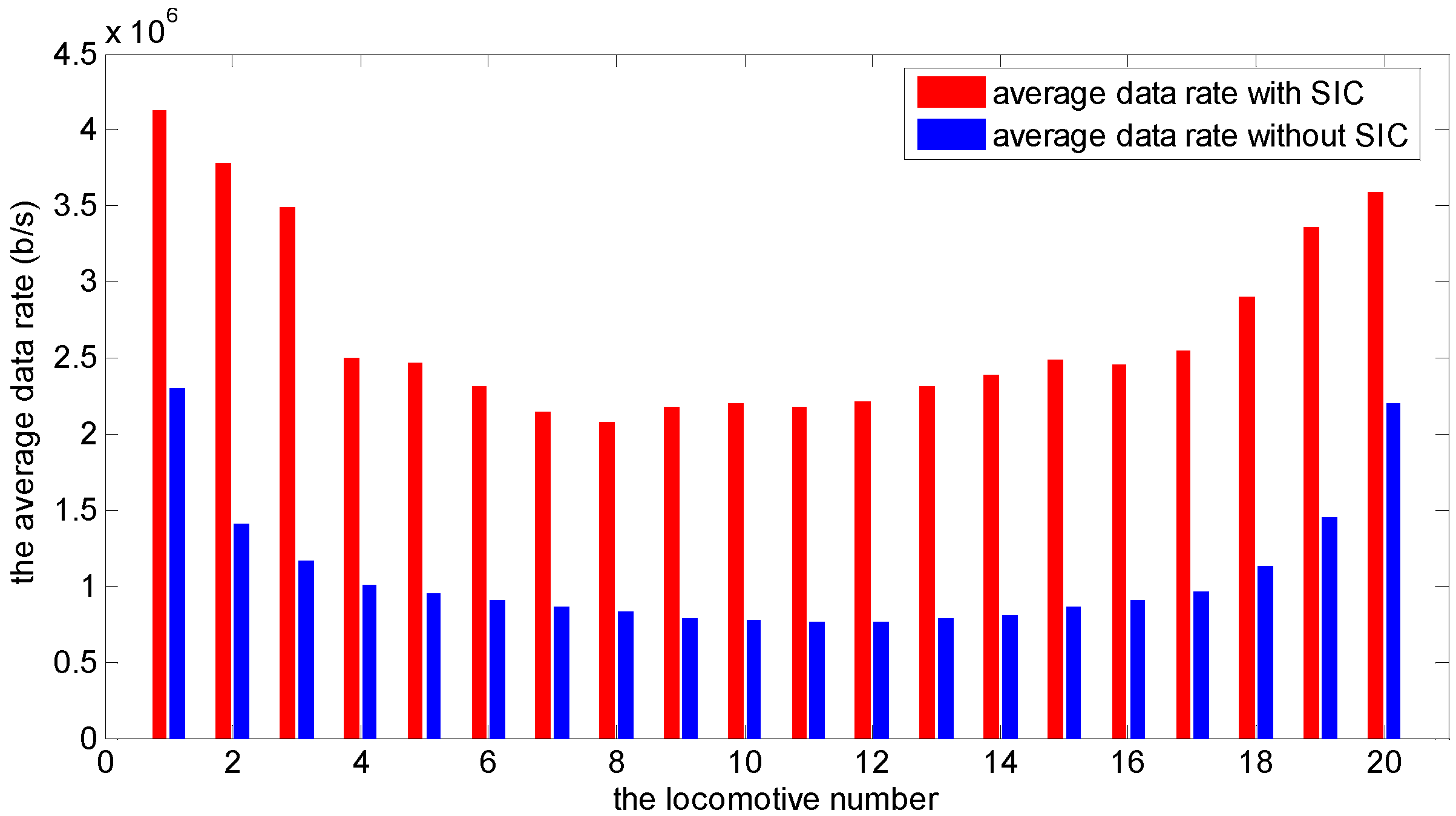
| n | Average Data Rate | Scaling Factor | Average Data Rate | Scaling Factor |
|---|---|---|---|---|
| with SIC (Mbps) | with SIC | without SIC (Mbps) | without SIC | |
| 1 | 4.13 | 8.26 | 2.30 | 4.60 |
| 2 | 3.78 | 7.56 | 1.40 | 2.80 |
| 3 | 3.49 | 6.98 | 1.16 | 2.32 |
| 4 | 2.50 | 5.00 | 1.01 | 2.02 |
| 5 | 2.46 | 4.92 | 0.95 | 1.90 |
| 6 | 2.31 | 4.62 | 0.91 | 1.82 |
| 7 | 2.15 | 4.30 | 0.87 | 1.74 |
| 8 | 2.07 | 4.14 | 0.83 | 1.66 |
| 9 | 2.17 | 4.34 | 0.79 | 1.58 |
| 10 | 2.20 | 4.40 | 0.77 | 1.54 |
| 11 | 2.18 | 4.36 | 0.76 | 1.52 |
| 12 | 2.21 | 4.42 | 0.77 | 1.54 |
| 13 | 2.32 | 4.64 | 0.79 | 1.58 |
| 14 | 2.39 | 4.78 | 0.81 | 1.62 |
| 15 | 2.49 | 4.98 | 0.81 | 1.62 |
| 16 | 2.46 | 4.92 | 0.91 | 1.82 |
| 17 | 2.55 | 5.10 | 0.96 | 1.92 |
| 18 | 2.90 | 5.80 | 1.13 | 2.26 |
| 19 | 3.36 | 6.72 | 1.45 | 2.90 |
| 20 | 3.60 | 7.20 | 2.20 | 4.40 |
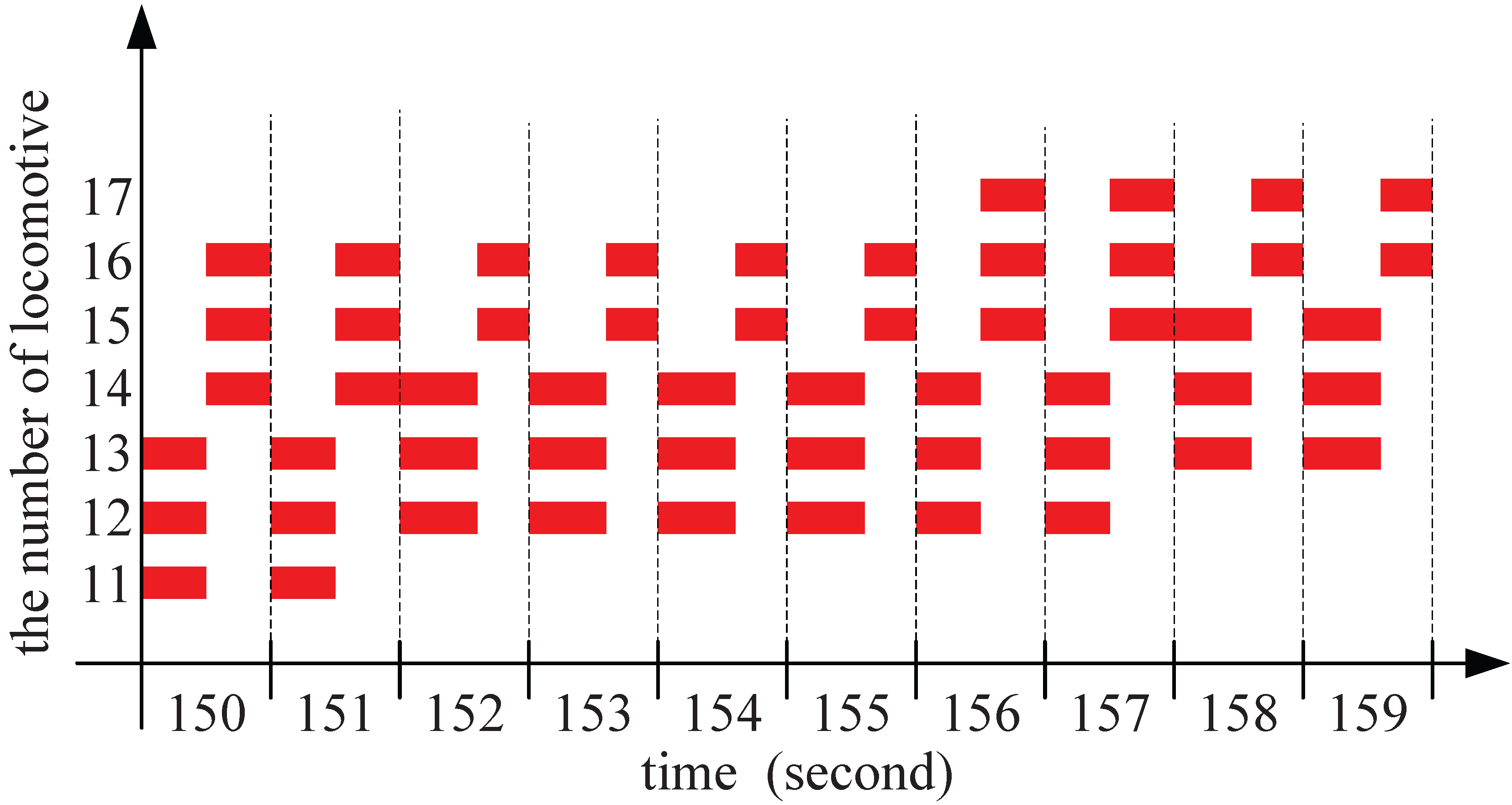
4.2. Results for All Network Instances

5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Chen, Z.; Lv, M.; Xu, X.; Yu, F.; Jin, H. Design of distributed monitoring and diagnosis system for locomotive diesel based on GPRS-Internet. In Proceedings of the ICECE, Wuhan, China, 25–27 June 2010; pp. 2737–2740.
- Berglund, T.; Brodnik, A.; Jonsson, H.; Staffanson, M.; Croucamp, P.L.; Rimer, S.; Kruger, C. Planning smooth and obstacle-avoiding B-spline paths for Autonomous Mining Vehicles. IEEE Trans. Autom. Sci. Eng. 2010, 7, 167–172. [Google Scholar] [CrossRef]
- Yu, G.; Kou, L.; Zhang, Y. Research on real-time location-tracking of underground mine locomotive based on wireless mobile video. In Proceedings of the MEC, Changchun, China, 19–22 August 2011; pp. 625–627.
- Yao, Y.; Rao, L.; Liu, X. Performance and reliability analysis of IEEE 802.11p safety communication in a highway environment. IEEE Trans. Vehicul. Technol. 2013, 62, 4198–4262. [Google Scholar] [CrossRef]
- Standard Specification for Telecommunications and Information Exchange Roadside and Vehicle Systems-5 GHz Band Dedicated Short Range Communications (DSRC) Medium Access Control (MAC) and Physical Layer (PHY) Specifications; ASTM International: West Conshohocken, PA, USA, 2009.
- Kopetz, H.; Bauer, G. The time-triggered architecture. IEEE Proc. 2003, 91, 112–126. [Google Scholar] [CrossRef]
- Sahoo, J.; Wu, E.H.K.; Sahu, P.K.; Gerla, M. Congestion-controlled-coordinator-based MAC for safety-critical message transmission in VANETs. IEEE Trans. Intell. Transp. Syst. 2013, 14, 1423–1437. [Google Scholar] [CrossRef]
- Yu, F.; Biswas, S. Self-configuring TDMA protocols for enhancing vehicle safety with DSRC based vehicle-to-vehicle communications. IEEE Trans. Sel. Areas Commun. 2007, 25, 1526–1537. [Google Scholar] [CrossRef]
- Kaiser, S. OFDM code-division multiplexing in fading channels. IEEE Trans. Commun. 2002, 50, 1266–1273. [Google Scholar] [CrossRef]
- Linnartz, J.P.M.G. Performance analysis of synchronous MC-CDMA in mobile Rayleigh channel with both delay and Doppler spreads. IEEE Trans. Vehicul. Technol. 2001, 6, 1375–1387. [Google Scholar] [CrossRef]
- Yee, N.; Linnartz, J.P. BER of multicarrier CDMA in an indoor Rician fading channel. In Proceedings of the Twenty-Seventh Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 1–3 November 1993.
- Slimane, S. Partial equalization of multicarrier CDMA in frequency-selective fading channels. In Proceedings of the IEEE ICC, New Orleans, LA, USA, 18–22 June 2000.
- Yang, L.; Hanzo, L. Performance of fractionally spread multicarrier CDMA in AWGN as well as slow and fast Nakagami-m fading channels. IEEE Trans. Vehicul. Technol. 2005, 54, 1817–1827. [Google Scholar] [CrossRef]
- Conti, A.; Masini, B.; Zabini, F.; Andrisano, O. On the downlink performance of multicarrier CDMA systems with partial equalization. IEEE Trans. Wirel. Commun. 2007, 6, 230–239. [Google Scholar] [CrossRef]
- Zabini, F.; Masini, B.M.; Conti, A.; Hanzo, L. Partial equalization for MC-CDMA systems in non-ideally estimated correlated fading. IEEE Trans. Vehicul. Technol. 2010, 59, 3818–3830. [Google Scholar] [CrossRef]
- Miridakis, N.I.; Vergados, D.D. A survey on the successive interference cancellation performance for single-antenna and multiple-antenna OFDM systems. IEEE Commun. Surveys Tutor. 2013, 15, 312–335. [Google Scholar] [CrossRef]
- Zhang, X.; Haenggi, M. The performance of successive interference cancellation in random wireless networks. IEEE Trans. Inf. Theory 2014, 60, 6368–6388. [Google Scholar] [CrossRef]
- Jiang, C.; Shi, Y.; Hou, Y.T.; Lou, W.; Kompella, S.; Midkiff, S.F. Squeezing the most out of interference: An optimization framework for joint interference exploitation and avoidance. In Proceedings of the INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2951–2955.
- Shi, L.; Zhang, J.; Shi, Y.; Ding, X.; Wei, Z. Optimal base station placement for wireless sensor networks with successive interference cancellation. Sensors 2015, 15, 1676–1690. [Google Scholar] [CrossRef] [PubMed]
- Shi, L.; Shi, Y.; Ye, Y.X.; Wei, Z.C.; Han, J.H. An efficient interference management framework for multi-hop wireless networks. In Proceedings of the WCNC, Shanghai, China, 7–10 April 2013; pp. 1129–1134.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, L.; Han, J.; Wei, X.; Shi, L.; Ding, X. The Mine Locomotive Wireless Network Strategy Based on Successive Interference Cancellation. Sensors 2015, 15, 28257-28270. https://doi.org/10.3390/s151128257
Wu L, Han J, Wei X, Shi L, Ding X. The Mine Locomotive Wireless Network Strategy Based on Successive Interference Cancellation. Sensors. 2015; 15(11):28257-28270. https://doi.org/10.3390/s151128257
Chicago/Turabian StyleWu, Liaoyuan, Jianghong Han, Xing Wei, Lei Shi, and Xu Ding. 2015. "The Mine Locomotive Wireless Network Strategy Based on Successive Interference Cancellation" Sensors 15, no. 11: 28257-28270. https://doi.org/10.3390/s151128257





