A Secure-Enhanced Data Aggregation Based on ECC in Wireless Sensor Networks
Abstract
: Data aggregation is an important technique for reducing the energy consumption of sensor nodes in wireless sensor networks (WSNs). However, compromised aggregators may forge false values as the aggregated results of their child nodes in order to conduct stealthy attacks or steal other nodes' privacy. This paper proposes a Secure-Enhanced Data Aggregation based on Elliptic Curve Cryptography (SEDA-ECC). The design of SEDA-ECC is based on the principles of privacy homomorphic encryption (PH) and divide-and-conquer. An aggregation tree disjoint method is first adopted to divide the tree into three subtrees of similar sizes, and a PH-based aggregation is performed in each subtree to generate an aggregated subtree result. Then the forged result can be identified by the base station (BS) by comparing the aggregated count value. Finally, the aggregated result can be calculated by the BS according to the remaining results that have not been forged. Extensive analysis and simulations show that SEDA-ECC can achieve the highest security level on the aggregated result with appropriate energy consumption compared with other asymmetric schemes.1. Introduction
Wireless sensor networks (WSNs) consist of thousands of sensors that collect data from a certain deployed range. Currently, WSNs have plenty of applications, such as military investigation, environment monitoring and accident reporting, etc. Typically, sensors have strictly limited computation and communication abilities and power resources; therefore, reducing the power consumption is a critical concern for WSNs. For better energy utilization, data aggregation [1,2] has been proposed recently. The original concept is to aggregate multiple sensing messages by performing statistical or algebraic operations, such as addition, minimum, maximum, median, etc. Since only the aggregated results need to reach the base station (BS) instead of sensing data, communication costs can be significantly reduced. Unfortunately, data aggregation is vulnerable to some attacks. For example, an adversary could compromise cluster heads (aggregators) similar to compromising all its cluster members. To solve this problem, several schemes, such as SDAP [3], PEPDA [4], Jung et al.'s scheme [5] have been proposed. However, these schemes can only guarantee the data privacy during the process of data aggregation and have a long aggregation delay.
An alternative method for secure data aggregation is to use privacy homomorphic encryption (PH), which can aggregate encrypted messages directly from sensors without decrypting so that it has a short aggregation delay. An adversary knows nothing from forging aggregated results even if the aggregators are compromised, because aggregators are unable to encrypt messages. PH is allowed to carry out specific types of computations on ciphertext, and the decrypted aggregation result matches the result of operations performed on the plaintext. PH has been used for data aggregation in WSNs, such as in Wang et al.'s scheme [6], CDAMA [7], Tiny PEDS [8], etc. However, the existing PH schemes suffer from the data integrity issue.
In this paper, we focus on bridging the gap between data privacy and integrity in WSNs. Some symmetric secure aggregation schemes [9,10] have been proposed to achieve both data privacy and integrity, but they cannot defend against node compromise attacks due to its inherent drawback that the encryption key is same as the decryption key. In general, symmetric schemes are less secure than asymmetric ones, although they are more efficient in terms of computational cost. Therefore, we originally propose a secure-enhanced data aggregation scheme based on Elliptic Curve Cryptography (ECC), called SEDA-ECC, which is an improved version of Boneh et al.'s asymmetric scheme [11]. To the best of our knowledge, SEDA-ECC can defend against the most attacks with appropriate energy consumption compared with other asymmetric schemes.
The rest of the paper is organized as follows: in Section 2, the existing secure data aggregation schemes in WSNs are presented. The system model and preliminaries are discussed in Section 3. In Section 4, a secure-enhanced data aggregation scheme based on ECC is proposed. Section 5 describes the security analysis of SEDA-ECC, and Section 6 presents performance evaluation and comparison to prove the effectiveness and efficiency of our scheme. Finally, we conclude SEDA-ECC in Section 7.
2. Related Works
Currently, many secure data aggregation schemes have been proposed. For symmetric schemes, Ozdemir et al. [9] integrated false data detection with data aggregation and confidentiality, and proposed an authentication protocol. In the scheme, every aggregator has some monitoring nodes which also perform data aggregation for data verification, and the integrity of the encrypted data is verified by the sensors between two consecutive aggregators. Its limitation is the rigorous topological constraints. Papadopoulos et al. [10] presented an exact aggregation scheme with integrity and confidentiality, named SIES. SIES combines the symmetric homomorphic encryption with secret sharing. A wide range of aggregates can be covered, and a small amount of bandwidth consumption is introduced in SIES. However, the data transmission efficiency is low due to the oversize space of secret keys. Based on Aggregation-Commit-Verify approach, Chan et al. [12] first proposed a provably secure hierarchical data aggregation scheme, where the adversary is forced to commit to its choice of aggregation results, then the sensors are allowed to verify whether their aggregation contributions are correct or not. The scheme can be used for multiple malicious nodes and arbitrary topologies, but it inherits the weakness of large amount of communication and computation overheads. To address this issue, Frikken et al. [13] improve Chan's scheme by reducing the maximum communication per node from O(Δlog2n) to O(Δlogn), where n is the number of nodes in WSNs, and Δ is the maximum degree of the aggregation tree.
For asymmetric schemes, Zhu et al. [14] focused on preserving data integrity and proposed an efficient integrity-preserving data aggregation protocol named EIPDAP. The scheme is based on the modulo addition operation using ECC, and has the most optimal upper bound on solving the integrity-preserving problem for data aggregation. Niu et al. [15] proposed a secure identity-based lossy data aggregation scheme using homomorphic hashing and identity-based aggregate signature. In the scheme, the authenticity of aggregated data can be verified by both aggregators and BS. The computation and communication overheads could be significantly reduced because the BS can perform batch verification. However, the above two schemes may lead to the leakage of data privacy due to decryption at the aggregator. Based on PH, Westhoff et al. [16] and Girao et al. [17] proposed CDA methods to facilitate aggregation in encrypted data, where richer algebraic operations can be directly executed on encrypted data by aggregators. Mykletun et al. [18] adopted several public-key-based PH encryptions to achieve data concealment in WSNs. Furthermore, Girao et al. [8] proposed a novel scheme by extending the ELGamal PH encryption. However, the above schemes cannot resist node compromise attacks. Specific security analysis is presented in Section 5.
3. System Model and Preliminaries
In this section, we describe the aggregation model and the attack model. The aggregation model defines how aggregation works, and the attack model defines what kinds of attacks our secure data aggregation scheme should protect against.
3.1. Aggregation Model
We consider large scale WSNs with densely deployed sensors. In WSNs, there are three types of nodes: base station (BS), aggregator, and leaf node. In this paper, we consider the aggregation tree roots at the BS like general data aggregation protocol [1,3]. Sensor nodes have overlapping sensing regions due to the dense deployment, and the same event is often detected by multiple sensors. Hence, data aggregation is proposed to reduce data transmission. The non-leaf nodes, except the BS, may also serve as aggregators. They are responsible for combining answers from their child nodes and forwarding intermediate aggregation results to their parents. Without loss of generality, we focus on additive aggregation, which can serve as the base of other statistical operations (e.g., count, mean, or variance).
3.2. Attack Model
First, we categorize the abilities of the adversary as follows:
- (1)
An adversary can eavesdrop on transmission data in a WSN.
- (2)
An adversary can send the forged data to leaf nodes, aggregators, or BS.
- (3)
An adversary can compromise secrets in sensors or aggregators.
Then, we define five attacks to qualify the security strength of the secure data aggregation schemes, based on adversary's abilities and purposes.
- (1)
Ciphertext analysis
Ciphertext analysis is a very common and basic attack. In such an attack, an adversary wants to deduce the secret key or obtain information only by interpreting ciphertext. A secure scheme must ensure that it is not possible to gain any information or key, and an adversary cannot decide whether an encrypted ciphertext corresponds to a specific plaintext or not.
- (2)
Chosen plaintext attacks
Given some chosen samples of plaintexts and corresponding ciphertexts, the adversary can determine secret information or deduce the key. A secure scheme must ensure that an adversary cannot deduce secret keys or additional information out of the known set, even with a large set of plaintexts and their ciphertexts.
- (3)
Malleability
The aim of the adversary is to alter the valid ciphertexts without leaving marks. In this kind of attack, an attack can randomly generate meaningless ciphertexts that are syntactically correct to harm the system. For many PH schemes, it is possible to alter the ciphertexts without knowing the concrete content. Hence, a secure scheme should not let the adversary be able to successfully change the contents of encrypted packet.
- (4)
Unauthorized aggregation
In this kind of attack, an adversary is to aggregate two or more ciphertexts into forged but format-valid ciphertexts, then to inject them into the network for vandalizing the system.
- (5)
Node compromise attacks
An adversary can compromise sensors or aggregators. When an adversary compromises an aggregator and gets its secret, it can easily launch unauthorized aggregation and malleability attacks. When an adversary compromises a sensor and gets its secret, it can decrypt the ciphertexts of all sensors in the symmetric schemes; besides, it also can impersonate the sensor or the other sensors to generate legal ciphertexts in both symmetric and asymmetric schemes.
3.3. Privacy Homomorphism
A privacy homomorphism is an encryption transformation which allows direct computation on the encrypted data. Let m1 and m2 be two plaintexts, and ⊗, × be the homomorphic operations on the ciphertexts and plaintexts respectively, we have Enc(m1) ⊗ Enc(m2) = Enc(m1 × m2), where Enc(m) represents the ciphertext of m. Component-wise multiplications and additions of ciphertexts result in the corresponding multiplications and additions of plaintexts. If E(p,q)(m1) = (x1,y1) and E(p,q)(m2) = (x2,y2), then:
However, symmetric cryptography-based privacy homomorphism has been proved to be insecure in chosen plaintext attacks for some specific parameters [19]. Therefore, privacy homomorphism based on asymmetric cryptography should be used instead of privacy homomorphism based on symmetric cryptography for some mission critical networks.
3.4. BGN Scheme
Boneh et al. [11] propose a PH scheme (abbreviated as BGN) based on the encryption schemes proposed by Paillier [20] and Okamoto-Uchiyama [21]. Both additive and multiplicative homomorphisms are provided in BGN, however, multiplicative homomorphism is inefficient and very expensive for WSNs because it is based on the bilinear pairing. Hence, we only adapt additive homomorphism of BGN to our scheme. The additive homomorphic encryption of BGN can be applied to private data aggregation, which is described in Algorithm 1.
Due to large computational overhead of the asymmetric cryptography, Boneh et al. construct BGN on a cyclic group of elliptic curve point. In phase 1 of BGN scheme, supposing E is the set of elliptic curve points that form a cyclic group, ord(E) denotes the number of points in E. Supposing













| Algorithm 1. BGN scheme. | |
| Phase 1. Key-Gen(λ): generate a public-private key pair. | |
| 01: | Compute (q1, q2, E) using security parameter λ, where E is the set of elliptic curve points that form a cyclic group. ord(E)= n= q1q2, where q1, q2 are large primes, and the bit lengths of them are the same, i.e., |q1| = |q2|. |
| 02: | Randomly select two generators,
 and and
 such that ord( such that ord(
 ) = ord( ) = ord(
 ) = n. ) = n. |
| 03: | Compute point
 = q2* = q2*
 such that ord( such that ord(
 ) = q1. ) = q1. |
| 04: | Select parameter T < q1 as the maximum plaintext boundary. |
| 05: | Generate Public key PK = (n, E,
 , ,
 , T) and Private key SK = q1. , T) and Private key SK = q1. |
| Phase 2. Enc(PK, M): message encryption on M by public key PK. | |
| 01: | Check if the message space of a sensor node M ∈ {0, 1, …, T}. |
| 02: | Random pick up R ∈ {0, 1, …, n−1}. |
| 03: | Generate the ciphertext C =M*
 + R* + R*
 . . |
| 04: | Return C. |
Phase 3. Agg(C1, C2): message aggregation on two ciphertexts C1 and C2, where Ci = Mi*
 + Ri* + Ri*
 , i = 1,2. , i = 1,2. | |
| 01: | Randomly select R'∈{0, 1, …, n − 1}. |
| 02: | Compute the aggregated ciphertext C′ = C1 + C2 + R′*
 = (M1 + M2)* = (M1 + M2)*
 + (R1 + R2 + R′)* + (R1 + R2 + R′)*
 |
| 03: | Return C′. |
| Phase 4. Dec(SK, C): message decryption on C using private key SK. | |
| 01: | Compute M = log  (q1 * C) log (q1 * C) log  (q1 * (M * (q1 * (M *
 + R * + R *
 ); = log ); = log  (q1 * M * (q1 * M *
 ), where ), where
 = q1* = q1*
 . . |
| 02: | Return M. |
4. SEDA-ECC: A Secure-Enhanced Data Aggregation Based on ECC
In this section, we modify BGN to fit the SEDA-ECC scheme, so the security of BGN and SEDA-ECC are all based on the hardness assumption of subgroup decision problem. If we only provide the privacy protection of data aggregation, BGN can be used in SEDA-ECC directly, however, we also aim to ensure the data integrity, hence, different public-private key pairs and disjoint aggregation tree will be adopted. We first describe the details of SEDA-ECC scheme, which consists of six phases listed in Algorithm 2, then we present a case study of SEDA-ECC.
4.1. Key Generation Phase
Given a security parameter λ∈ℤ, the tuple (q1, q2, q3, E) is generated. E is the set of elliptic curve points that form a cyclic group, and ord(E) = n = q1q2q3, where q1, q2, q3 are large primes, and the bit lengths of them are the same. Then, randomly select three points (













| Algorithm 2. SEDA-ECC scheme. | |
| Input: | An aggregated WSN and SQL type SUM aggregation query |
| Output: | SUM aggregation result after integrity checked. |
| Phase 1. Key-Gen(λ): generate public-private key pairs for tree Ti, where i = r, g and b. | |
| 01: | Compute (qi1, qi2, qi3, E) based on security parameter λ, where E is the set of elliptic curve points that form a cyclic group. ord(E) = n = qi1qi2qi3, where qi1, qi2, qi3 are large primes, and the bit lengths of them are the same, i.e., |qi1| = |qi2| = |qi3|. |
| 02: | Randomly select generators,
 i1, i1,
 i2 and i2 and
 i3 such that ord( i3 such that ord(
 i1) = ord( i1) = ord(
 i2) = ord( i2) = ord(
 i3) = n. i3) = n. |
| 03: | Compute point
 i = qi1qi2* i = qi1qi2*
 i3 such that ord( i3 such that ord(
 i) = qi3, i) = qi3,
 i = qi2qi3* i = qi2qi3*
 i1 such that ord( i1 such that ord(
 i) = qi1, and i) = qi1, and
 i = qi1qi3* i = qi1qi3*
 i2 such that ord( i2 such that ord(
 i) = qi2. Then output Public key PK = (n, E, i) = qi2. Then output Public key PK = (n, E,
 i, i,
 i, i,
 i) and Private key SK = {(qi1qi3), (qi2qi3)}. i) and Private key SK = {(qi1qi3), (qi2qi3)}. |
| Phase 2. Dis-Tree(pr, pg, pb): disjoint aggregation tree construction with probability pr, pg and pb. | |
| 01: | BS triggers the aggregation by a HELLO message, when receiving such a message, nodes select their roles: red aggregator, green aggregator and blue aggregator. Aggregators then also forward the HELLO messages. |
| 02: | If a node receives HELLO messages from red, green and blue aggregators, it randomly selects its role according to pi; otherwise it waits until the HELLO messages from all kinds of aggregators are received. |
| 03: | Three disjoint aggregation trees rooted at the BS can be formed as the disjoint tree construction procedure continues. Red aggregators, green aggregators and blue aggregators interleave with each other. |
| Phase 3. Enc(PK, Mi): message encryption in three trees respectively, where i = r, g and b. | |
| 01: | Set TM < qi1. Check if the message space of a sensor node Mi ∈ {0, 1, …, TM}. |
| 02: | Randomly pick up Ri∈{0, 1, …, n − 1}. |
| 03: | Generate the ciphertext Ci = Mi*
 i + i +
 i + Ri* i + Ri*
 i. i. |
| 04: | Return Ci. |
| Phase 4. Agg(Ci1, Ci2): message aggregation on two ciphertexts Ci1 and Ci2, where i = r, g and b. | |
| 01: | Compute the aggregated ciphertext Cia = Ci1 + Ci2 = (ΣMij)*
 i + ζi* i + ζi*
 i + (ΣRij)* i + (ΣRij)*
 i, where ΣMij represents the aggregated result of tree Ti, ζi represents the number of aggregated ciphertexts in tree Ti, and ΣRij represents the aggregated randomness in tree Ti. i, where ΣMij represents the aggregated result of tree Ti, ζi represents the number of aggregated ciphertexts in tree Ti, and ΣRij represents the aggregated randomness in tree Ti. |
| 02: | Return Cia. |
| Phase 5. Dec(SK, Cia): message decryption on Cia in tree Ti. | |
| 01: | Compute Mi = ΣMij = log  l (qi2qi3), where l (qi2qi3), where
 = qi2qi3* = qi2qi3*
 i. i. |
| 02: | Compute ζi = log  l(qi1qi3 * Ci), where l(qi1qi3 * Ci), where
 = qi1qi3* = qi1qi3*
 i. i. |
| 03: | Return Mi, ζi. |
| Phase 6. Chec(Mi): check message Mi integrity at the BS, where i = r, g and b. | |
| 01: | Set i, j,k ∈ {r, g, b}, and i ≠ j ≠ k. |
| If |ζi − ζj| ≤ Th, and |ζj − ζk| ≤ Th, | |
| BS accepts the three aggregated results and computes the final result M = Mi + Mj + Mk; | |
| else if |ζi − ζj| ≤ Th, and |ζj − ζk| > Th, | |
| BS rejects Mk, and computes the final aggregated result M = 3/2(Mi + Mj); | |
| else if |ζi − ζj| > Th, and |ζj − ζk| > Th, | |
| BS either decides which aggregated result is real through gathering topology information, or rejects all the aggregated result Mi, Mj and Mk, and return NULL. | |
The scalar of






4.2. Aggregation Tree Disjoint Phase
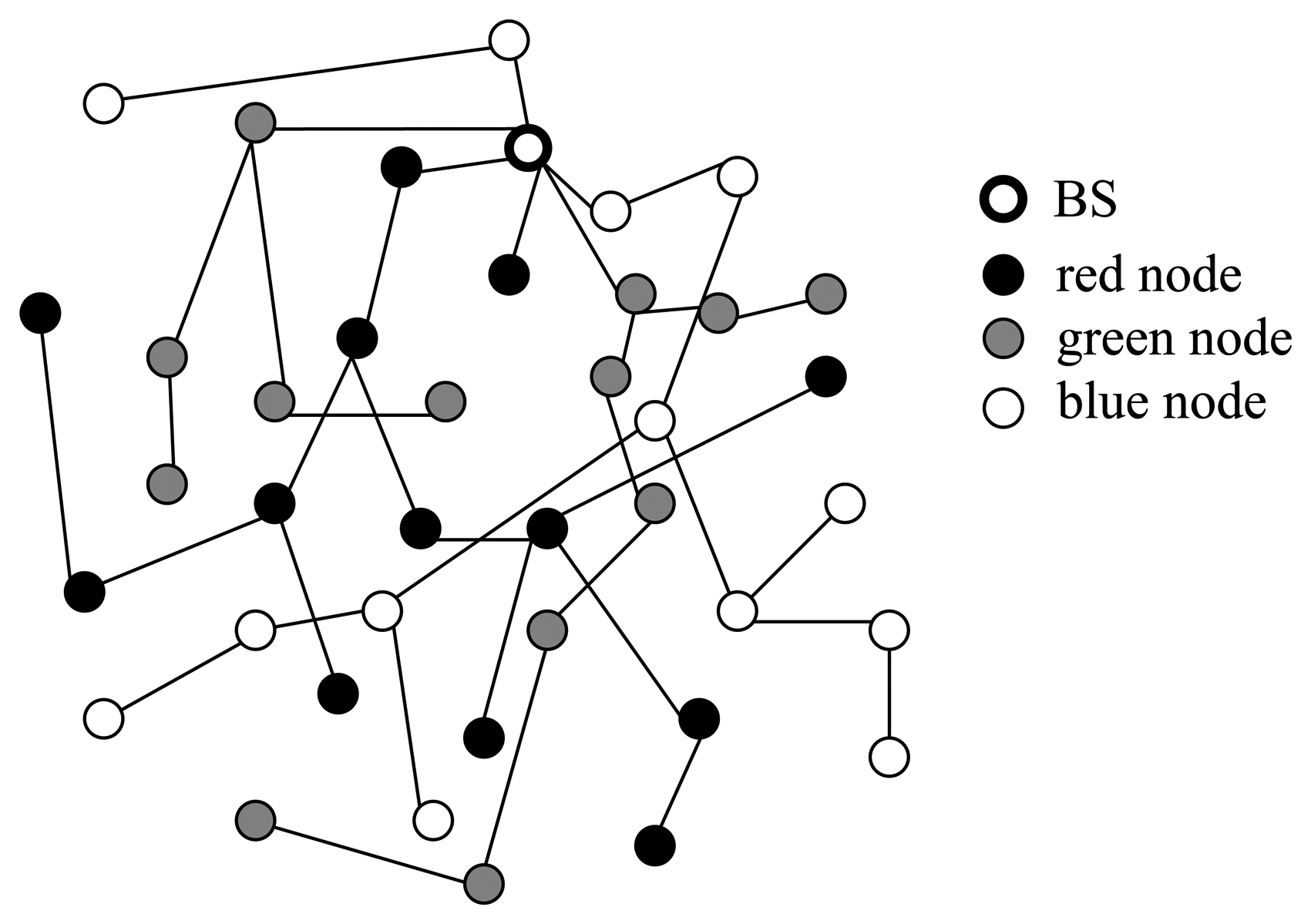
Three subtrees are built in this scheme, which are called red aggregation tree, green aggregation tree, and blue aggregation tree, respectively, and the BS is the root of the above three subtrees. Assuming the network is dense enough, each node, except the BS, takes one of the four roles: red aggregator, green aggregator, blue aggregator, or leaf node. We partition the tree into three subtrees, the disjoint tree is as shown in Figure 1, where the black colored nodes represent red aggregators, grey colored nodes represent green aggregators, and white colored nodes represent blue aggregators.
Step 1
BS is appointed to be the root of the above three subtrees, which initiates a HELLO message requesting sensors to organize into one of the three aggregation trees. In that message, it contains its own ID and its level information Lr = Lg = Lb = 0.
Step 2
Each sensor receiving the message should make the decision on its role, assign its own level to be Li + 1(i = r, g, b), and select the sender node as its parent. A node becomes a red aggregator with probability pr, a green aggregator with probability pg, and a blue aggregator with probability pb, respectively. The probability will be subject to the conditions: 0 < pr = pg = pb < 1, and pr + pg + pb = 1.
Step 3
Each node in one aggregation tree rebroadcasts the colored message corresponding tree, which contains its own ID and level. If any node has already been in the tree when receives the message, it will reject the message; otherwise, the node also assigns its level Li to be Li + 1. Three aggregation trees are constructed till all nodes have a level and a parent. To balance the red, green and blue aggregators in a given neighborhood, a node should wait enough time to receive HELLO messages from red, green and blue aggregators as much as possible before the decision on its color is made. Then, pr, pg and pb can be computed by each node as follows:
Step 4
During the process of aggregation, red aggregators are not allowed to forward the data for green and blue aggregators, and vice versa. Then, the separation of data aggregation can be achieved along the disjoint trees. Finally, the BS will receive three aggregated results Mr, Mg and Mb respectively.
Note that an adversary may compromise the data integrity during this phase by sending two HELLO messages with different colors. This can be prevented by guaranteeing that a node in one tree cannot be in another two trees. However, such attack can be detected easily by its neighbors because of the shared-medium nature of wireless links. Therefore, the adversary can be excluded from the three aggregation trees.
4.3. Encryption Phase
We set TM < q1. The message space of a sensor node M should subject to Mi ∈ {0, 1, …, TM}, where i = r, g and b. Each sensor picks a random Ri ∈ {0, 1, …, n − 1}, and encrypt the message Mi using public key PK, then it generates the ciphertext Ci = Mi*



4.4. Aggregation Phase
Let ΣMij denote the aggregated message of tree Ti, ζi denote the number of aggregated ciphertexts of tree Ti, and ΣRij denote the aggregated randomness in tree Ti, consequently, k ciphertexts for j = 1 to k are aggregated into a ciphertext of Cia as follows:
4.5. Decryption Phase
During the decryption phase, the BS can separately decrypt the aggregated result Mi and its count ζi from the aggregated ciphertext in tree Ti respectively as follows:
4.6. Data Integrity Check Phase
When the BS receives the three aggregated results from the red, green and blue subtrees, it should decrypt them and extract the count ζi, respectively. If a compromised aggregator tampers with the aggregated result Mi, the count value ζi must be changed simultaneously because the aggregators do not know the base point


If |ζi − ζj| ≤ Th, and |ζj − ζk| ≤ Th, it shows each result has not been tampered, then the BS accepts the three aggregated results and computes the final result M = Mi +Mj + Mk; if |ζi − ζj| ≤ Th, and |ζj − ζk| > Th, it shows Mk has been tampered, then the BS rejects Mk, and computes the approximate aggregated result = 3/2(Mi + Mj); if |ζi − ζj| > Th, and |ζj − ζk| > Th, it shows the three aggregated results maybe have been tampered totally, then the BS either rejects all the aggregated results Mi, Mj and Mk, or decides which aggregated result is real by gathering topology information.
4.7. A Case Study
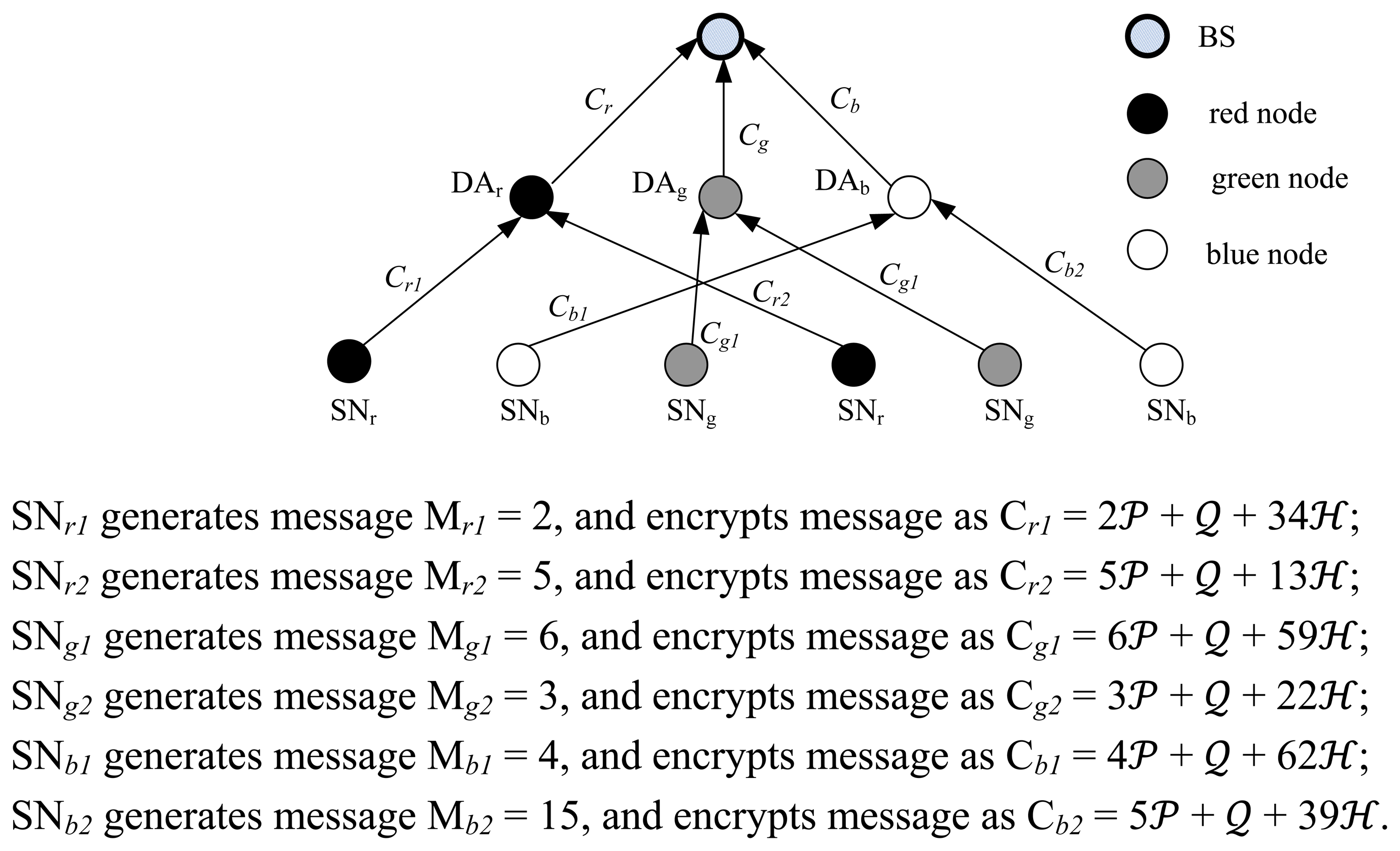
We present a case study to show how SEDA-ECC works. For simplicity, we assume that the network only consists of six leaf nodes and three aggregators besides BS, and the three subtrees have the same public key PK = (n, E,










The encrypted messages are sent to data aggregators. Data aggregator DAr aggregates Cr1 and Cr2 as Cr = 7




















The aggregated result of red subtree Mr = Mr1 + Mr2 = 7 can be obtained by decrypting Cr as follows:
- (1)
Compute q2q3* Cr = 323* (7
+ 2
+9
) = 2,261
= 12
, where 13
= 17
= 19
= ∞.
- (2)
Mr = log
(q2q3 * Cr)= log
12
, where
= q2q3*
= 323
= 11
. Then Mr *
= Mr*11
= 12
can be obtained because Mr = log
12
.
- (3)
Finally, the aggregated result of red subtree Mr = 7 can be obtained by the BS according to Pollard's λ method.
Similarly, the BS can also extract the aggregated count result ζ by computing the discrete logarithm of q1q3*Cr to the base point


5. Theoretical Analysis
In this section, we analyze the coverage of aggregation trees first because it has great effect on our scheme's availability, then analyze the security of SEDA-ECC and compare it with five well-known secure data aggregation schemes: CDA [16,17], Castelluccia et al.'s scheme [22], BGN scheme [11], EC-OU scheme [18], and TinyPEDS scheme [8].
5.1. Coverage of Aggregation Trees
In SEDA-ECC scheme, a sensor reports its data to BS by aggregation only when it can reach red, green and blue aggregation trees within one hop. If a node cannot reach the three aggregation trees, it is disconnected from the BS for aggregation. We define Φ(G) as the probability that all the sensors are covered by all the three aggregation trees. It means that many sensors cannot contribute their data to the aggregation result if Φ(G) is small. Therefore, the coverage of aggregation trees impacts the accuracy of aggregation results. The aggregation accuracy is one of the most important performance metrics, because it can affect the decision of BS, so we should first analyze the coverage of aggregation trees to verify our scheme's availability.
Consider a random network G (n, l), where n is the number of sensors, and l is the transmission range of a sensor. We randomly assign red, green or blue to sensors in the networks, and let S denote the number of sensors which are isolated from red, green or blue sensors, then:
We define Si as the variable of whether sensor i has red, green and blue neighbors within one hop distance, then
{Si} can be approximated as identical independent distributions for a random network whose size is large enough, therefore, can be denoted as the total number of sensors which are isolated by red, green or blue aggregation tree. Let di denote the number of neighbors of sensor i, then the probability that i is isolated by the red aggregation tree is labeled as . Similarly, i is isolated by the green (blue) aggregation tree with the probability . Let pi be the probability that note i is isolated by red sensors, green sensors or blue sensors, then:
Since , we can get a lower bound of Φ(G) by applying Markov Inequality . That is:
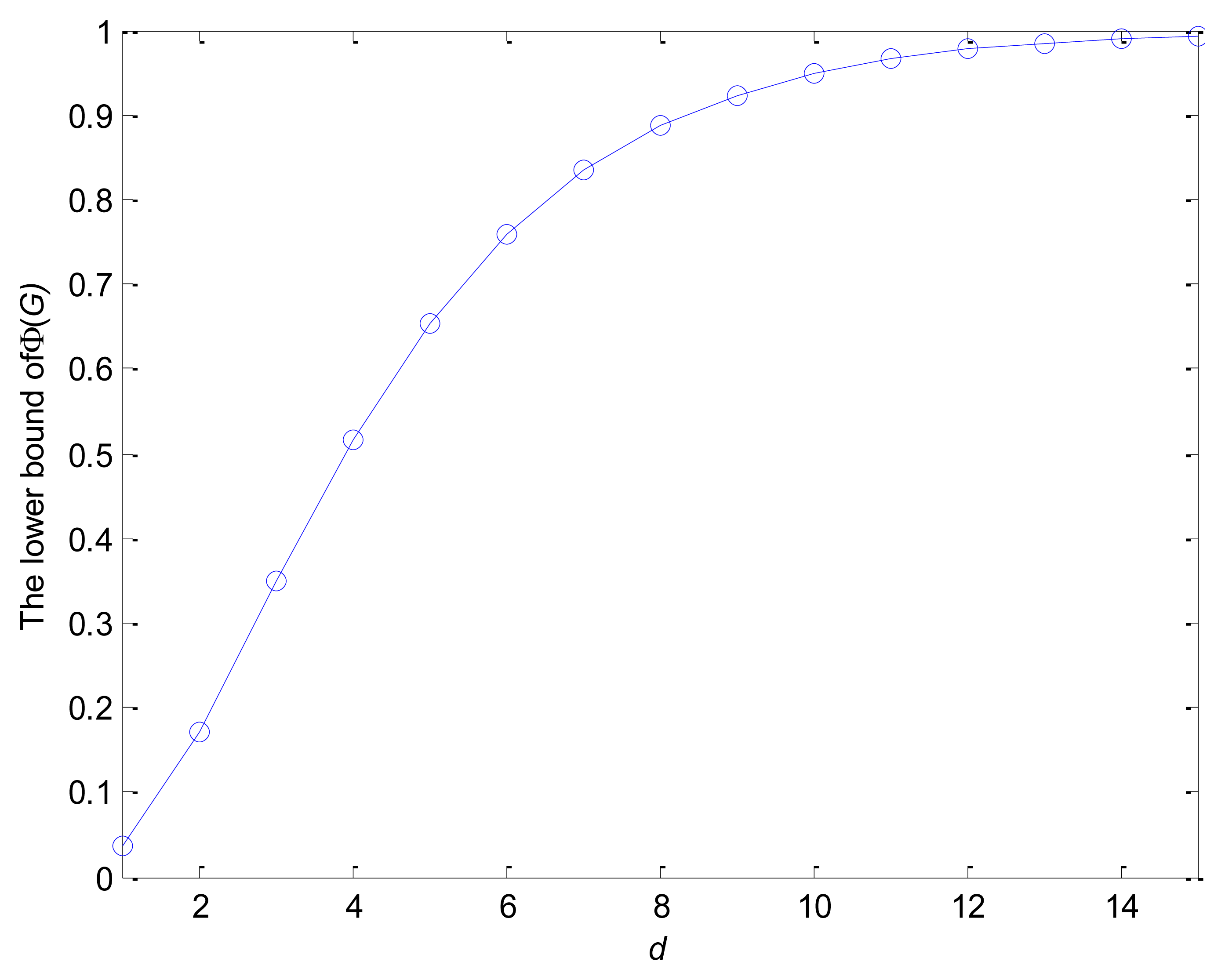
When the network is dense enough, i.e., di is large, a small pi can be obtained. For example, assuming pr = pg = pb = 1/3, we can obtain the lower bound of Φ(G) which varies with the variation of d under the condition of the d-regular network according to Equation (9). It can be observed from Figure 3 that Φ(G) ≥ 0.95 for d = 10, therefore, the coverage of aggregation trees is perfect for dense networks from Equation (10).
5.2. Ciphertext Analysis
This is the most basic attack in WSNs. SEDA-ECC is robust to ciphertext analysis attack, because the elliptic curve cryptography-based encryption depends on the factorization of large integers. Other schemes are also robust to ciphertext analysis attacks.
5.3. Chosen Plaintext Attacks
SEDA-ECC is robust to chosen plaintext attacks, because its encryption relies on random numbers, and the ciphertext is probabilistic. Other schemes based on ECC can defend against this attack too. Wagner's cryptanalysis [23] has indicated that CDA might suffer from chosen plaintext attacks because of improper security parameters. However, the cost of proper parameter would render CDA infeasible to WSNs. Castelluccia et al.'s scheme is also robust to this attack, because its security is based on the indistinguishability property of a pseudorandom function, and the previous encryption keys cannot be used to deduce the present or subsequent encryption key.
5.4. Malleability
In the analysis of this attack, we give the example that the adversary wants to increase the measured data by 50. Since Castelluccia et al.'s scheme is based on modular addition, adversaries can add the value of plaintext trivially through adding a certain value to the corresponding ciphertext directly, so it suffers from this attack. For example, a ciphertext (m + Kn) mod M can be easily altered by ((m + 50) + Kn) mod M = (m + Kn) + 50 mod M. Other schemes can defend against this attack because they are based on either modular multiplication or ECC.
5.6. Node Compromise Attacks
For asymmetric schemes, SEDA-ECC, BGN, EC-OU and TinyPEDS do not suffer from unauthorized decryption under compromised sensor node conditions, because an adversary cannot obtain the private key through a compromised sensor. However, except for SEDA-ECC, they cannot defend against unauthorized aggregation in a compromised aggregator situation. The compromised aggregator might arbitrarily increase the aggregated result by aggregating the same ciphertext repeatedly or decrease it by selective aggregation. After the aggregation process, the forged value is difficult to detect or remove by the BS. SEDA-ECC can prevent this attack targeting data integrity by constructing disjoint aggregation subtrees. It is impossible for attackers to alter the aggregated result M without changing the count value ζ because the aggregators do not know the base points


We use the case study of SEDA-ECC in Section 4.7 to validate its ability of defending against this attack. Supposing the aggregation ciphertexts excluding Cr, Cg, and Cb are C'r = M'r 





















For symmetric schemes, the inherent drawback of CDA and Castelluccia et al.'s schemes is that the encryption key is identical with the decryption key. Therefore, an adversary can decrypt the ciphertext once the sensor is compromised. In addition, because the CDA's key is shared by all sensors and BS, if any sensor is compromised, the whole system security is broken. Castelluccia et al.'s scheme suffers from a minor impact due to the fact its distinct key is shared by BS.
Table 1 shows the security analysis comparisons for all schemes. It clearly shows that symmetric schemes are less secure than asymmetric ones, although they are more efficient in terms of communication and computation costs. Compared with other asymmetric schemes, SEDA-ECC is superior in defending against compromised node attacks because it can protect data integrity by constructing disjoint aggregation trees when the aggregators are compromised.
6. Performance Evaluation and Comparison
Generally, symmetric key-based homomorphic schemes are more efficient than asymmetric ones, however, the security of symmetric schemes is weaker than that of asymmetric ones. For the sake of fairness, the performance of SEDA-ECC is only compared with other three asymmetric key-based homomorphic encryption schemes. In this section, we first discuss the threshold value Th, then evaluate the computation overhead, communication cost, and the accuracy of SEDA-ECC, BGN, EC-OU and TinyPEDS. We conduct simulations using TinyOS 2.0 simulator (TOSSIM). The parameters are shown in Table 2, and the topology of nodes is depicted in Figure 4, where the transmission range of a sensor is 50 m, and the BS coordinate is (200,200).
6.1. Th Parameter Setting
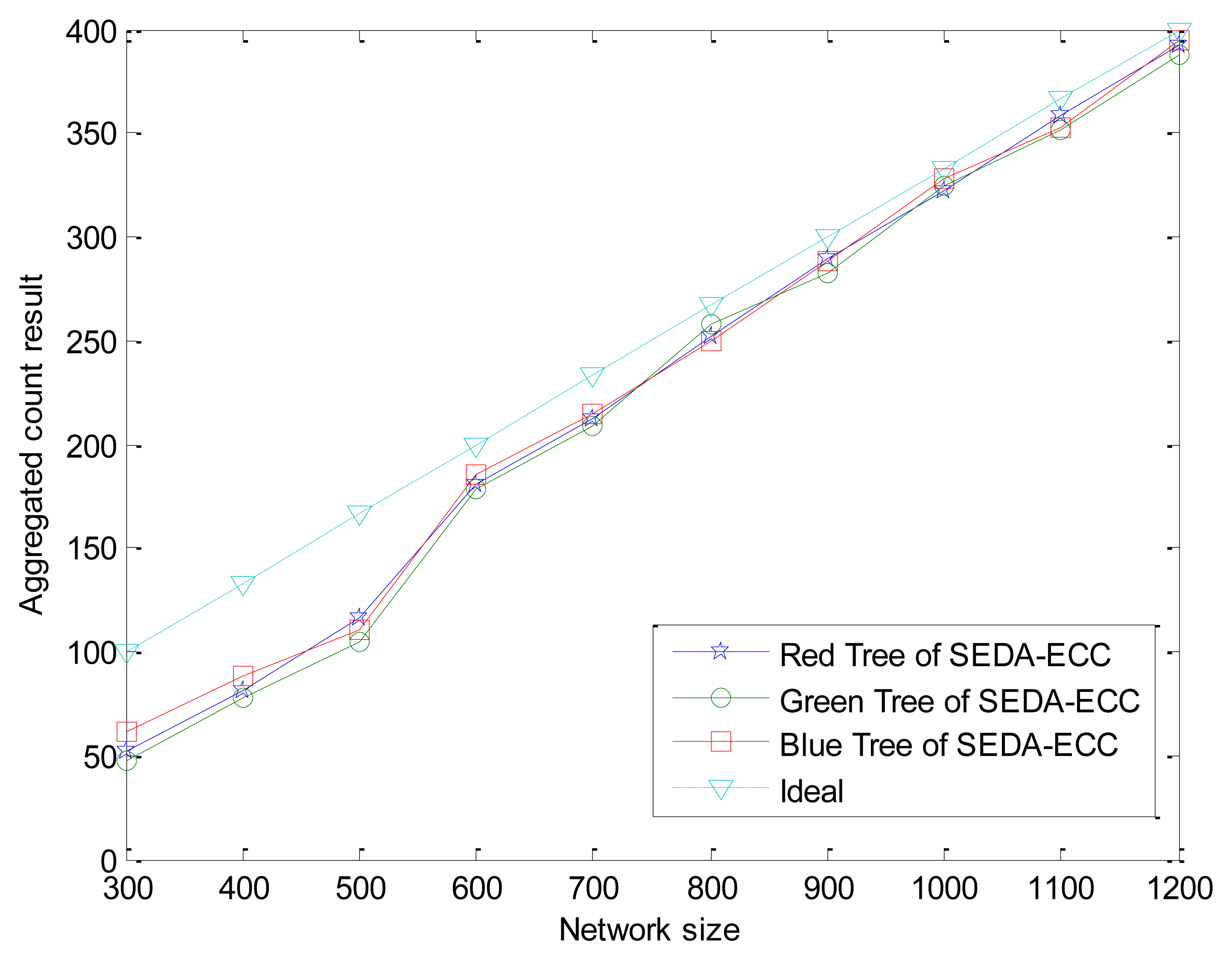
In general, the more sensors that participate in the data aggregation, the larger the probability of constructing disjoint aggregation trees which have the same number of sensors. In addition, the aggregated count results ζ from three aggregation trees may not agree with each other exactly due to collisions and congestions in wireless channels. Therefore, an adjustable threshold value Th and the lowest bound of network size are introduced to accomodate these factors. Since whether the BS accepts the result depends on the threshold value Th, hence Th is an important parameter. In order to get Th, we did extensive simulations, where the number of nodes (network size) was varied from 300 to 1,200 in a 400 m × 400 m area.
The difference value among aggregated count results from three aggregation subtrees is simulated 40 times, and the average value is depicted in Figure 5, where the “ideal” curve shows the aggregated result in an ideal situation. According to the simulation result, we notice that the differences, which are between 2 and 9, are very small. Hence, the threshold can be set as a small value, e.g., Th = 10. We can adjust Th if the network conditions are changed. Note that the average count result is only half of the ideal number and the difference extends to 9 when the network size is nearly 300. In addition, the smaller network size is, the larger differences became. As we analyzed in Section 5.1, it is because the coverage is bad enough in a sparse network to deteriorate the aggregation accuracy. Therefore, we set the lowest bound of network size as 300 in a 400 m × 400 m area to make our scheme available.
6.2. Communication Overhead
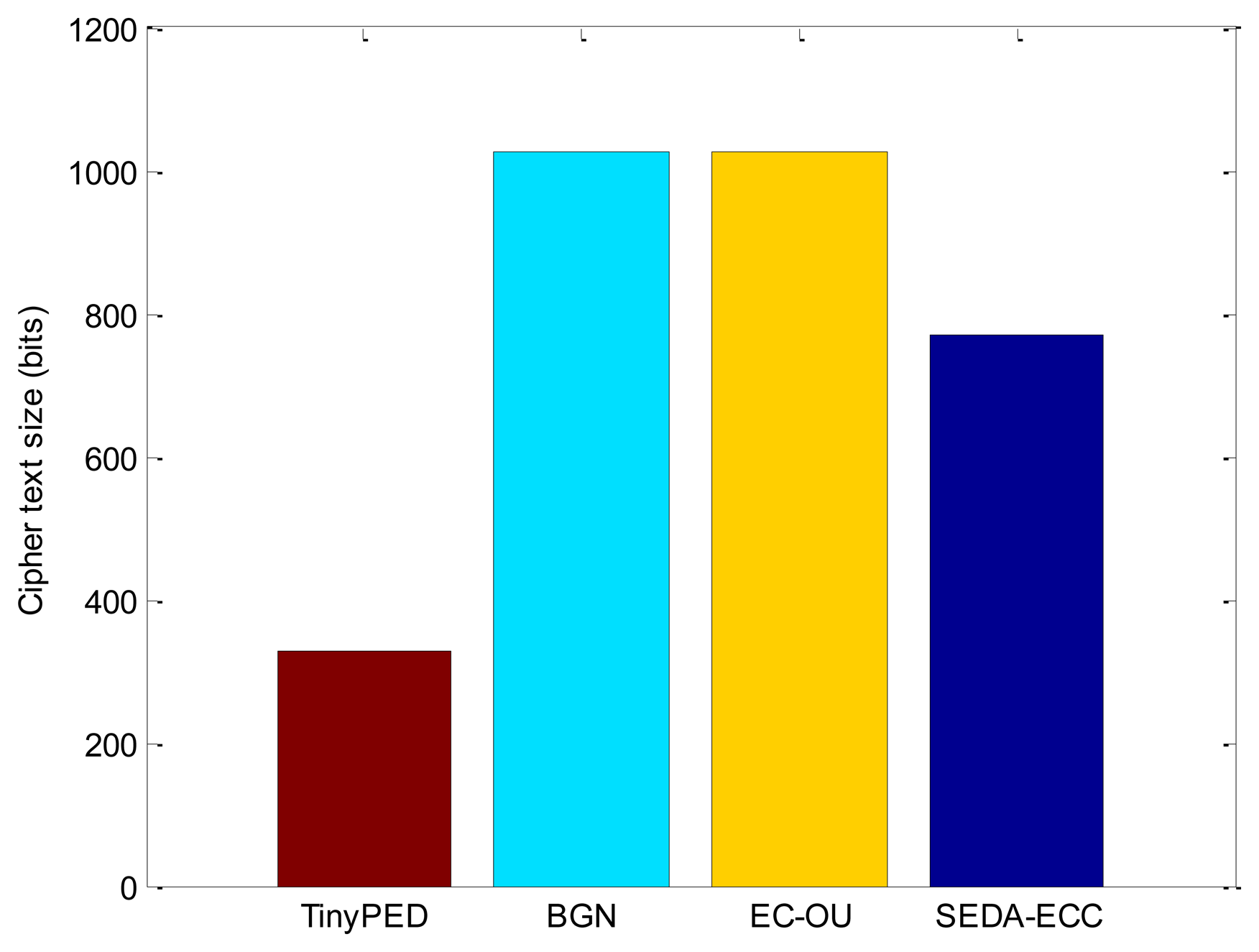
The number of exchanged messages in each scheme is the same. Though there are three subtrees need to be built in SEDA-ECC, similar to the other schemes, each node needs to send two messages for data aggregation: one HELLO message to form the aggregation tree, and the other message for data aggregation. Therefore, the communication overhead mainly depends on the ciphertext size of each scheme on the condition that the number of message sending to the BS is the same. Supposing the order of elliptic curve is N, SEDA-ECC's security relies on the hardness of factoring the order N. N is a product of several different large prime numbers, e.g., N = q1q2⋯qk, where k is the number of prime numbers. If the length of prime number is 256-bit, there is no efficient approach to factor the product N [7]. Therefore, in SEDA-ECC, we generate N = q1q2q3, where the prime numbers qi are all 256-bit. Since the size of the ciphertext is almost the same as |N| + 1, the SEDA-ECC's ciphertext size is 3 × |q| + 1(|q| = 256-bit). EC-OU's ciphertext size is 3 × |q| + 2(|q| = 341-bit) according to [24]. BGN's ciphertext size is 1,025-bit, and TinyPEDS's ciphertext size is 328-bit according to [7]. Figure 6 shows the comparison of ciphertext sizes.
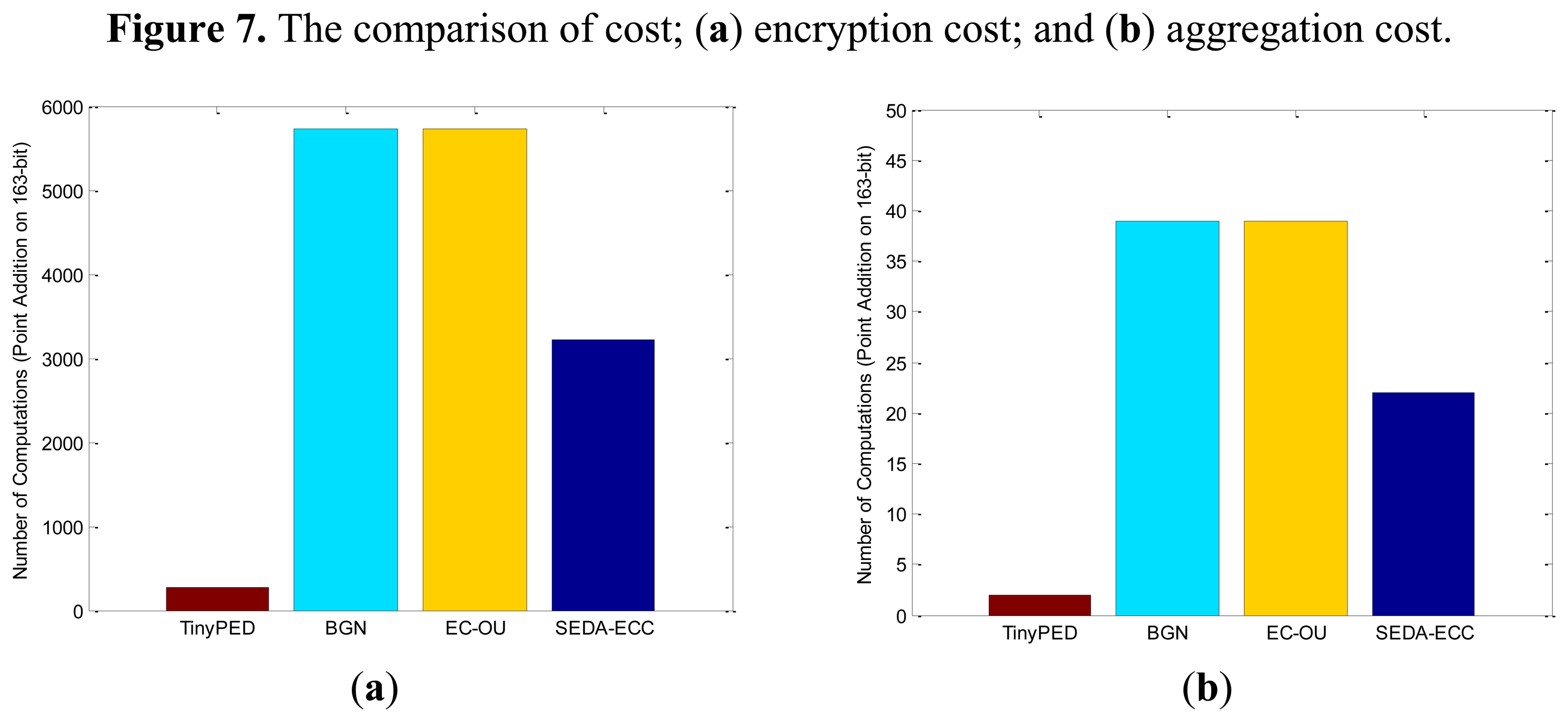
6.3. Computation Overhead
Since SEDA-ECC, BGN, EC-OU and TinyPEDS schemes are all built on elliptic curves, encryption and aggregation operation are based on point addition and point scalar multiplication. In elliptic curve arithmetic, point doubling and adding are two basic operations. Scalar multiplication can be accomplished by the half-and-add algorithm based on point doubling and adding [25]. It requires about |r| doubling and |r|/2 additions for computing r*

It should be noted that SEDA-ECC, BGN, EC-OU and TinyPEDS schemes are built on different mathematical foundations. We assume the finite field of elliptic curve is





In summary, TinyPED is the most efficient one for both communication overhead and computation cost, because its curves are chosen from the smaller field

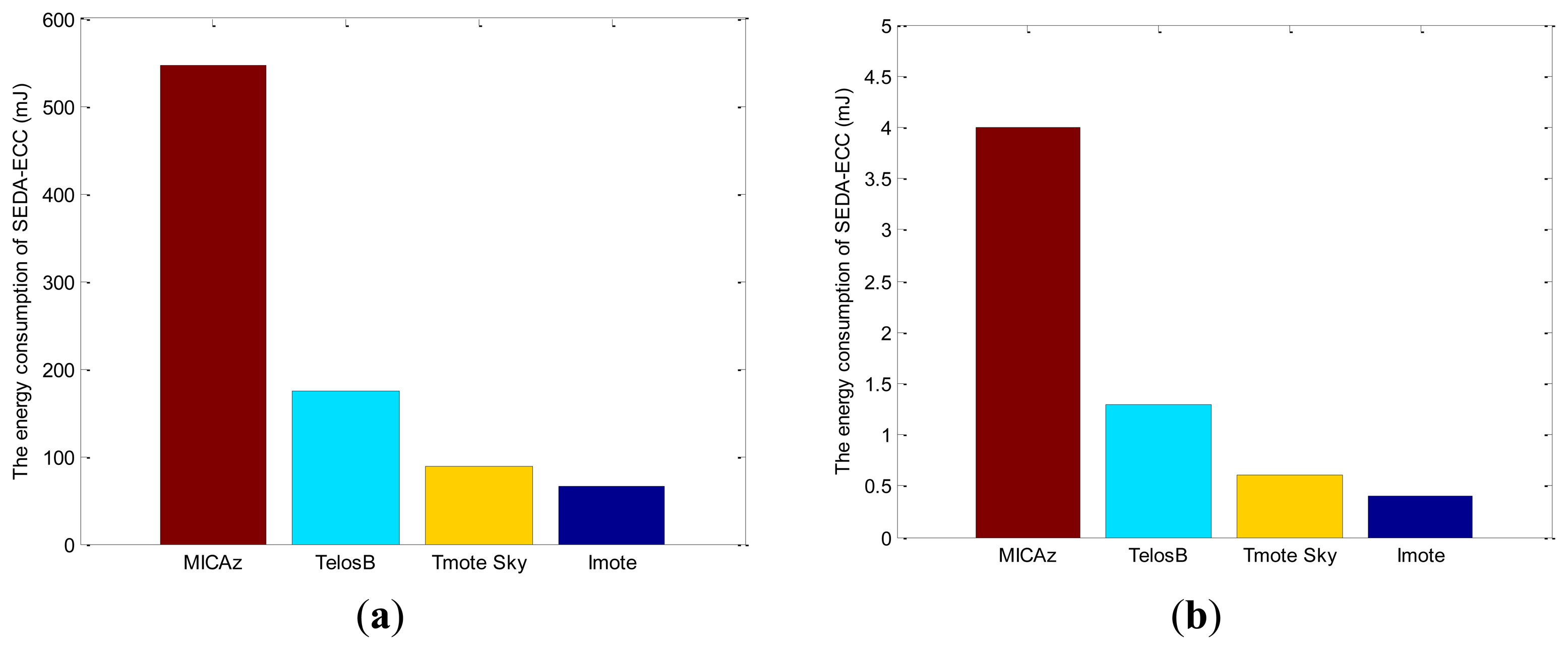
Furthermore, the energy consumption of SEDA-ECC is evaluated in different sensor devices according to TinyECC [26], which is one well-known implementation of ECC for WSNs, as shown in Figure 8. The energy consumption can be significantly reduced with more advanced devices. Therefore, the secure data aggregation schemes based on asymmetric encryption, e.g., ECC, have extensive applications with the development of the advanced sensors.
6.4. Accuracy
We define the accuracy as the ratio between the aggregated sum result by the data aggregation scheme in use and the real sum of all sensors participating in the data aggregation. It is an important issue because it could affect the decision of the BS. All the schemes should achieve 100% accurate aggregated results in an ideal situation. However, data packets may be lost or delayed due to data collisions, processing delays and noisy wireless channels. We evaluate the data accuracy of SEDA-ECC, BGN, EC-OU, and TinyPED with respect to different time intervals, as shown in Figure 9.
It shows that all these schemes almost perform equally in term of accuracy. We can observe that the accuracy increases as the time interval increases, because the data collisions and congestions between data aggregators are reduced, and the data packets should have enough time to be delivered.
7. Conclusions
Providing hierarchical data aggregation without losing data privacy and integrity guarantee is a challenging problem in WSNs. In this article, we propose a novel Secure-Enhanced Data Aggregation based on Elliptic Curve Cryptography (SEDA-ECC) for WSNs. SEDA-ECC divides the aggregation tree into three subtrees to reduce the importance of the high-level sensor nodes. It also generates three aggregated results by performing PH-based aggregations in the three subtrees, respectively, so that the BS could verify the subtree aggregated results by comparing the aggregated count value. Extensive analytical and simulation results indicate that SEDA-ECC can achieve the highest security level on the aggregated result comparing with other asymmetric schemes, and SEDA-ECC is efficient with respect to a reasonable energy cost.
Acknowledgments
This work is supported by the National Basic Research Program (973 Program) of China under Grant No. 2011CB302903, the National Natural Science Foundation of China under Grant Nos. 61272084 and 61300240, the National Research Project of China under Grant No. 2012A138, the Key Project of the Natural Science Research of Jiangsu University under Grant No. 11KJA520002, the Research Innovation Program for College Graduates of Jiangsu Province under Grant No. CXZZ12_0477, the Key Foundation for Outstanding Young Talent of Chuzhou University under Grant No. 2013RC002, and the Natural Science Foundation of Chuzhou University under Grant Nos. 2012kj003Z and 2011kj014B.
Author Contributions
All authors have contributed to the presented work in various degrees. Qiang Zhou and Geng Yang proposed the network model and scheme. Qiang Zhou performed theoretical analysis and wrote the manuscript. Qiang Zhou and Liwen He conducted the experimental simulations, and revised the manuscript. All authors have read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Madden, S.; Franklin, M.J.; Hellerstein, J.; Hong, W. TAG: A tiny aggregation service for ad-hoc sensor networks. Proceedings of the 5th Operating Systems Design and Implementation Symposium (ACM OSDI '02), Boston, MA, USA,, 9–11 December 2002; pp. 131–146.
- Fasolo, E.; Rossi, M.; Widmer, J.; Zorzi, M. In-network aggregation techniques for wireless sensor networks: A survey. IEEE Wirel. Commun. 2007, 14, 70–87. [Google Scholar]
- Yang, Y.; Wang, X.; Zhu, S.; Cao, G. SDAP: A secure hop-by-hop data aggregation protocol for sensor networks. ACM Trans. Inf. Syst. Secur. TISSEC 2008, 11, 1–43. [Google Scholar]
- Yang, G.; Li, S.; Xu, X.; Dai, H.; Yang, Z. Precision-enhanced and encryption-mixed privacy-preserving data aggregation in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2013, 2013, 427275. [Google Scholar]
- Jung, T.; Mao, X.F.; Li, X.Y.; Tang, S.J.; Gong, W.; Zhang, L. Privacy-preserving data aggregation without secure channel: Multivariate polynomial evaluation. Proceedings of the 32th Conference on Computer Communications (IEEE INFOCOM '13), Turin, Italy, 14–19 April 2013; pp. 2734–2742.
- Wang, L.; Wang, L.; Pan, Y.; Zhang, Z.; Yang, Y. Discrete logarithm based additively homomorphic encryption and secure data aggregation. Inf. Sci. 2011, 181, 3308–3322. [Google Scholar]
- Lin, Y.; Chang, S.; Sun, H. CDAMA: Concealed data aggregation scheme for multiple applications in wireless sensor networks. IEEE Trans. Knowl. Data Eng. 2012, 25, 1471–1483. [Google Scholar]
- Girao, J.; Westhoff, D.; Mykletun, E.; Araki, T. TinyPEDS: Tiny persistent encrypted data storage in asynchronous wireless sensor networks. Ad Hoc Netw. 2007, 5, 1073–1089. [Google Scholar]
- Ozdemir, S.; Cam, H. Integration of false data detection with data aggregation and confidential transmission in wireless sensor networks. IEEE CM Trans. Netw. TON 2010, 18, 736–749. [Google Scholar]
- Papadopoulos, S.; Kiayias, A.; Papadias, D. Exact In-network aggregation with integrity and confidentiality. IEEE Trans. Knowl. Data Eng. 2012, 24, 1760–1773. [Google Scholar]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF formulas on ciphertexts. Proceedings of the 2nd International Conference on Theory of Cryptography (TCC '05), Cambridge, MA, USA, 10–12 February 2005; pp. 325–341.
- Chan, H.; Perrig, A.; Song, D. Secure hierarchical in-network aggregation in sensor networks. Proceedings of the 13th ACM Conference on Computer and Communications Security (ACM CCS '06), Alexandria, VA, USA, 30 October–3 November 2006; pp. 278–287.
- Frikken, K.B.; Dougherty, J.A., IV. An efficient integrity-preserving scheme for hierarchical sensor aggregation. Proceedings of the first ACM Conference on Wireless Network Security (ACM WISEC '08), Alexandria, VA, USA, 31 March–2 April 2008; pp. 68–76.
- Zhu, L.; Yang, Z.; Li, M.; Liu, D. An Efficient data aggregation protocol concentrated on data integrity in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2013, 2013, 256852. [Google Scholar]
- Niu, S.; Wang, C.; Yu, Z.; Cao, S. Lossy data aggregation integrity scheme in wireless sensor networks. Comput. Electr. Eng. 2013, 39, 1726–1735. [Google Scholar]
- Westhoff, D.; Girao, J.; Acharya, M. Concealed data aggregation for reverse multicast traffic in sensor networks: Encryption, key distribution, and routing adaptation. IEEE Trans. Mob. Comput. 2006, 5, 1417–1431. [Google Scholar]
- Girao, J.; Westhoff, D.; Schneider, M. CDA: Concealed data aggregation for reverse multicast traffic in wireless sensor networks. Proceedings of the IEEE International Conference on Communications (IEEE ICC '05), Seoul, Korea, 16–20 May 2005; pp. 3044–3049.
- Mykletun, E.; Girao, J.; Westhoff, D. Public key based cryptoschemes for data concealment in wireless sensor networks. Proceedings of the IEEE International Conference on Communications (IEEE ICC '06), Istanbul, Turkey, 11–15 June 2006; pp. 2288–2295.
- Cheon, J.H.; Kim, W.H.; Nam, H.S. Known-plaintext cryptanalysis of the Domingo-Ferrer algebraic privacy homomorphism scheme. Inf. Process. Lett. 2006, 97, 118–123. [Google Scholar]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques (EUROCRYPT '99), Prague, Czech Republic, 2–6 May 1999; pp. 223–238.
- Okamoto, T.; Uchiyama, S. A new public-key cryptosystem as secure as factoring. Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques (EUROCRYPT '98), Helsinki, Finland, 31 May–4 June 1998; pp. 308–318.
- Castelluccia, C.; Chan, A.; Mykletun, E.; Tsudik, G. Efficient and provably secure aggregation of encrypted data in wireless sensor networks. ACM Trans. Sens. Netw. TOSN 2009, 5, 1–20. [Google Scholar]
- Wagner, D. Cryptanalysis of an algebraic privacy homomorphism. Proceedings of the 6th International Conference on Information Security, Bristol, UK, 1–3 October 2003; pp. 234–239.
- Peter, S.; Westhoff, D.; Castelluccia, C. A survey on the encryption of convergecast traffic with in-network processing. IEEE Trans. Dependable Secur. Comput. 2010, 7, 20–34. [Google Scholar]
- Cohen, H.; Frey, G.; Avanzi, R. Handbook of Elliptic and Hyperelliptic Curve Cryptography; CRC Press: Boca Raton, FL, USA, 2010; pp. 157–215. [Google Scholar]
- Liu, A.; Ning, P. TinyECC: A configurable library for elliptic curve cryptography in wireless sensor networks. Proceedings of the International Conference on Information Processing in Sensor Networks (IPSN'08), Missouri, USA, 22–24 April 2008; pp. 245–256.


| Requirement | Ciphertext Analysis | Chosen Plaintext Attacks | Malleability | Unauthorized Aggregation | Node Compromise Attacks |
|---|---|---|---|---|---|
| CDA | √ | × | √ | × | × |
| Castelluccia et al.'s scheme | √ | √ | × | × | × |
| SEDA-ECC | √ | √ | √ | √ | √ |
| BGN | √ | √ | √ | √ | × |
| EC-OU | √ | √ | √ | √ | × |
| TinyPEDS | √ | √ | √ | √ | × |
| Radio Parameters | Topology Parameters | ||
|---|---|---|---|
| Noise Floor | White Gaussian Noise | Terrain Dimensions | Number of Nodes |
| −105 dB | 4 dB | 400 m × 400 m | 600 |
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Zhou, Q.; Yang, G.; He, L. A Secure-Enhanced Data Aggregation Based on ECC in Wireless Sensor Networks. Sensors 2014, 14, 6701-6721. https://doi.org/10.3390/s140406701
Zhou Q, Yang G, He L. A Secure-Enhanced Data Aggregation Based on ECC in Wireless Sensor Networks. Sensors. 2014; 14(4):6701-6721. https://doi.org/10.3390/s140406701
Chicago/Turabian StyleZhou, Qiang, Geng Yang, and Liwen He. 2014. "A Secure-Enhanced Data Aggregation Based on ECC in Wireless Sensor Networks" Sensors 14, no. 4: 6701-6721. https://doi.org/10.3390/s140406701
APA StyleZhou, Q., Yang, G., & He, L. (2014). A Secure-Enhanced Data Aggregation Based on ECC in Wireless Sensor Networks. Sensors, 14(4), 6701-6721. https://doi.org/10.3390/s140406701





