Super-Activation as a Unique Feature of Secure Communication in Malicious Environments
Abstract
:1. Introduction
Notation
2. Arbitrarily Varying Wiretap Channels
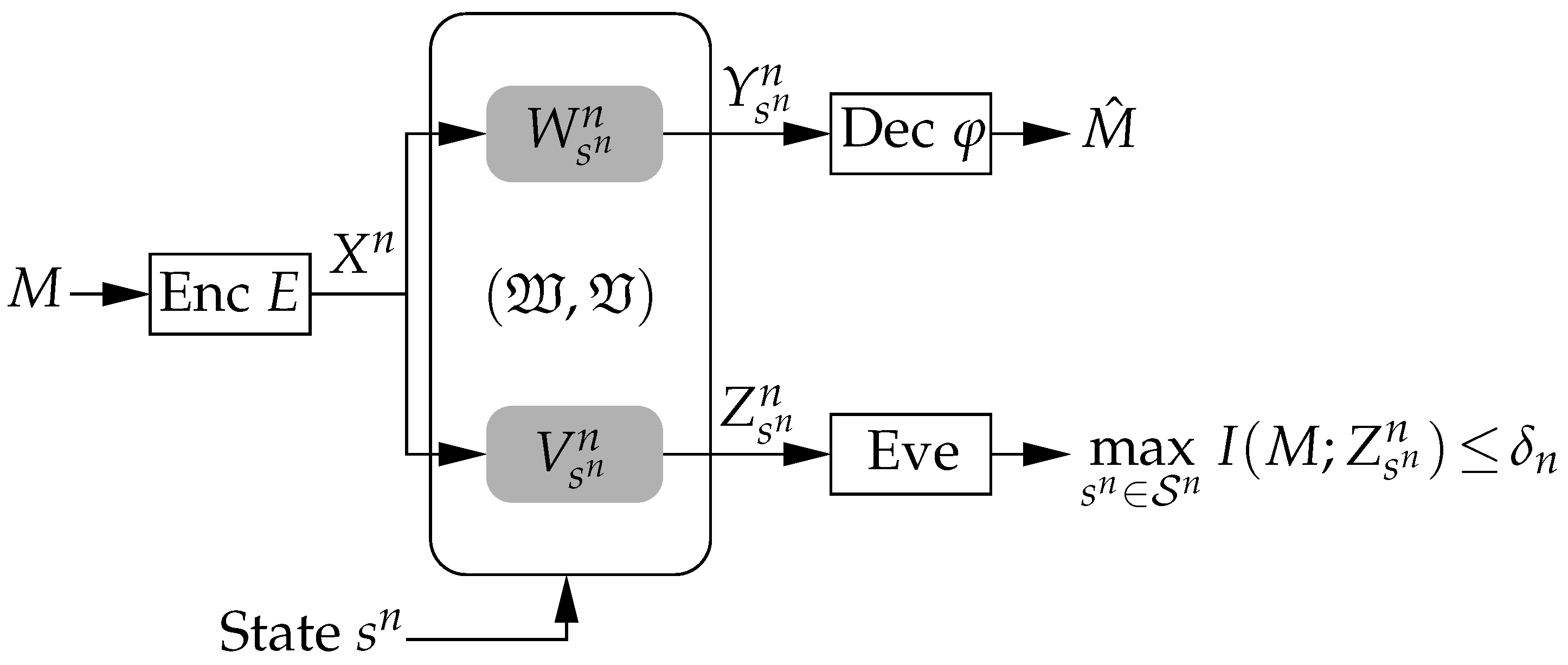
2.1. System Model
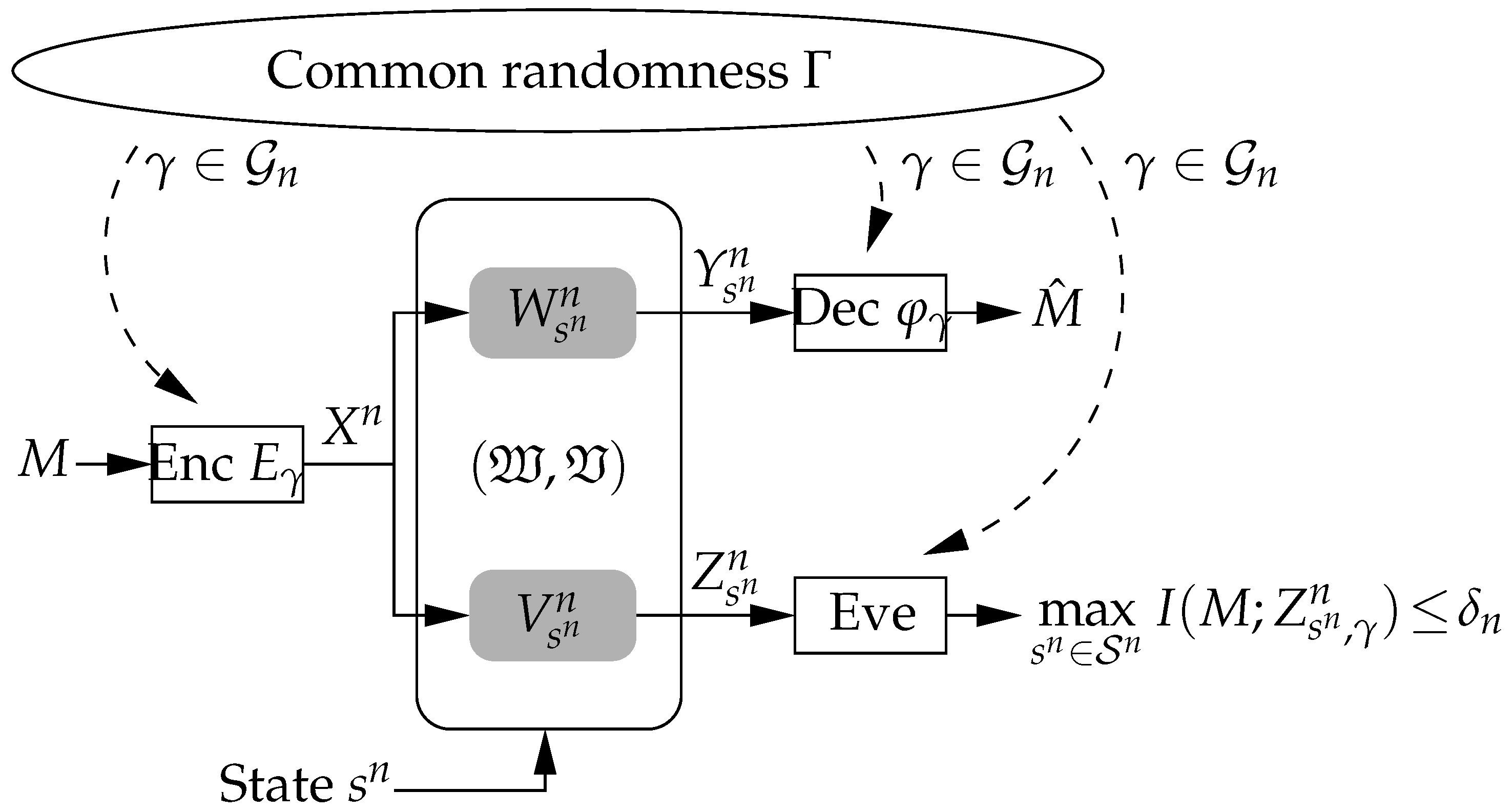
2.2. Code Concepts
2.2.1. Unassisted Codes
2.2.2. CR-Assisted Codes
2.3. Capacity Results
- The AVWC is a discontinuity point of if and only if the following holds: First, , and second, but for every there is a finite with and .
- If is discontinuous in the point then it is discontinuous for all for which .
3. Super-Activation and Robustness
3.1. Secure Communication over Orthogonal AVWCs
3.2. Super-Activation of Orthogonal AVWCs
- If , thenif and only if is non-symmetrizable and . If and can be super-activated it holds that
- If shows no super-activation for and , then super-activation of can only happen if is non-symmetrizable and is symmetrizable and and . The statement is independent of the specific labeling.
- There exist AVWCs that exhibit the behavior described by the second property.
4. Communication over Orthogonal AVCs
4.1. Capacity Results
4.2. Additivity of CR-Assisted Capacity
4.3. Super-Additivity of Unassisted Capacity
5. Discussion
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Liang, Y.; Poor, H.V.; Shamai, S. Information theoretic security. Found. Trends Commun. Inf. Theory 2009, 5, 355–580. [Google Scholar] [CrossRef]
- Liu, R.; Trappe, W. (Eds.) Securing Wireless Communications at the Physical Layer; Springer: New York, NY, USA, 2010.
- Jorswieck, E.A.; Wolf, A.; Gerbracht, S. Secrecy on the physical layer in wireless networks. In Trends in Telecommunications Technologies; Intech: Rijeka, Croatia, 2010; pp. 413–435. [Google Scholar]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Zhou, X.; Song, L.; Zhang, Y. (Eds.) Physical Layer Security in Wireless Communications; CRC Press: Boca Raton, FL, USA, 2013.
- Schaefer, R.F.; Boche, H. Physical layer service integration in wireless networks—Signal processing challenges. IEEE Signal Process. Mag. 2014, 31, 147–156. [Google Scholar] [CrossRef]
- Deutsche Telekom AG Laboratories. Next generation mobile networks: (R)evolution in mobile communications. Technology Radar Edition III/2010, Feature Paper. 2010. Available online: http://www.lti.ei.tum.de/fileadmin/w00bgd/www/pdf/2010-III_Feature_Paper_Next-Generation-Mobile-Networks_final.pdf (accessed on 28 April 2016).
- Helmbrecht, U.; Plaga, R. New challenges for IT-security research in ICT. In World Federation of Scientists International Seminars on Planetary Emergencies; World Scientific: Singapore, 2008; pp. 1–6. [Google Scholar]
- Fettweis, G.; Boche, H.; Wiegand, T.; Zielinksi, E.; Schotten, H.; Merz, P.; Hirche, S.; Festag, A.; Häffner, W.; Meyer, M.; et al. The Tactile Internet; Technology Watch Report of ITU (International Telecommunication Union): Geneva, Switzerland, 2014. [Google Scholar]
- Schaefer, R.F.; Boche, H.; Poor, H.V. Secure communication under channel uncertainty and adversarial attacks. Proc. IEEE 2015, 102, 1796–1813. [Google Scholar] [CrossRef]
- Blackwell, D.; Breiman, L.; Thomasian, A.J. The capacities of certain channel classes under random coding. Ann. Math. Stat. 1960, 31, 558–567. [Google Scholar] [CrossRef]
- Ahlswede, R. Elimination of correlation in random codes for arbitrarily varying channels. Z. Wahrscheinlichkeitstheorie Verw. Gebiete 1978, 44, 159–175. [Google Scholar] [CrossRef]
- Csiszár, I.; Narayan, P. The capacity of the arbitrarily varying channel revisited: Positivity, constraints. IEEE Trans. Inf. Theory 1988, 34, 181–193. [Google Scholar] [CrossRef]
- MolavianJazi, E.; Bloch, M.; Laneman, J.N. Arbitrary jamming can preclude secure communication. In Proceedings of the 47th Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, 30 September–2 October 2009; pp. 1069–1075.
- Bjelaković, I.; Boche, H.; Sommerfeld, J. Capacity results for arbitrarily varying wiretap channels. In Information Theory, Combinatorics, and Search Theory; Springer: Berlin/Heidelberg, Germany, 2013; pp. 123–144. [Google Scholar]
- Boche, H.; Schaefer, R.F. Capacity results and super-activation for wiretap channels with active wiretappers. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1482–1496. [Google Scholar] [CrossRef]
- Boche, H.; Schaefer, R.F.; Poor, H.V. On arbitrarily varying wiretap channels for different classes of secrecy measures. In Proceedings of the IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 2376–2380.
- Janda, C.R.; Scheunert, C.; Jorswieck, E.A. Wiretap-channels with constrained active attacks. In Proceedings of the Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 2–5 November 2014; pp. 1984–1988.
- Wiese, M.; Nötzel, J.; Boche, H. A channel under simultaneous jamming and eavesdropping attack—Correlated random coding capacities under strong secrecy criteria. 2015. [Google Scholar]
- Nötzel, J.; Wiese, M.; Boche, H. The arbitrarily varying wiretap channel—Secret randomness, stability and super-activation. In Proceedings of 2015 IEEE International Symposium on Information Theory, Hong Kong, China, 14–19 June 2015; pp. 2151–2155.
- Boche, H.; Schaefer, R.F.; Poor, H.V. On the continuity of the secrecy capacity of compound and arbitrarily varying wiretap channels. IEEE Trans. Inf. Forensics Secur. 2015, 12, 2531–2546. [Google Scholar] [CrossRef]
- Shannon, C.E. The zero error capacity of a noisy channel. IRE Trans. Inf. Theory 1956, 2, 8–19. [Google Scholar] [CrossRef]
- Lovász, L. On the Shannon capacity of a graph. IEEE Trans. Inf. Theory 1979, 25, 1–7. [Google Scholar] [CrossRef]
- Ahlswede, A.; Althöfer, I.; Deppe, C.; Tamm, U. (Eds.) Rudolf Ahlswede’s Lectures on Information Theory 3—Hiding Data: Selected Topics; Springer: Cham, Switzerland, 2016.
- Haemers, W. On some problems of Lovász concerning the Shannon capacity of a graph. IEEE Trans. Inf. Theory 1979, 25, 231–232. [Google Scholar] [CrossRef]
- Alon, N. The Shannon capacity of a union. Combinatorica 1998, 18, 301–310. [Google Scholar] [CrossRef]
- Ahlswede, R. A note on the existence of the weak capacity for channels with arbitrarily varying channel probability functions and its relation to Shannon’s zero error capacity. Ann. Math. Stat. 1970, 41, 1027–1033. [Google Scholar] [CrossRef]
- Aigner, M.; Ziegler, G.M. Proofs from THE BOOK, 5th ed.; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Smith, G.; Smolin, J.A.; Yard, J. Quantum communication with Gaussian channels of zero quantum capacity. Nat. Photonics 2011, 5, 624–627. [Google Scholar] [CrossRef]
- Giedke, G.; Wolf, M.M. Quantum communication: Super-activated channels. Nat. Photonics 2011, 5, 578–580. [Google Scholar] [CrossRef]
- Csiszár, I. Almost independence and secrecy capacity. Probl. Pered. Inform. 1996, 32, 48–57. [Google Scholar]
- Maurer, U.M.; Wolf, S. Information-theoretic key agreement: From weak to strong secrecy for free. In Advances in Cryptology — EUROCRYPT 2000; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1807, pp. 351–368. [Google Scholar]
- Liang, Y.; Kramer, G.; Poor, H.V.; Shamai, S. Compound wiretap channels. EURASIP J. Wirel. Commun. Netw. 2009. [Google Scholar] [CrossRef]
- Bjelaković, I.; Boche, H.; Sommerfeld, J. Secrecy results for compound wiretap channels. Probl. Inf. Transm. 2013, 49, 73–98. [Google Scholar] [CrossRef]
- Schaefer, R.F.; Loyka, S. The secrecy capacity of compound MIMO Gaussian channels. IEEE Trans. Inf. Theory 2015, 61, 5535–5552. [Google Scholar] [CrossRef]
- Milnor, J. Games against Nature; RAND Corporation: Santa Monica, CA, USA, 1951; pp. 49–59. [Google Scholar]
- Aumann, R.J.; Hart, S. Handbook of Game Theory with Economic Applications; Elsevier: Oxford, UK, 1994; Volume 2. [Google Scholar]
- Basar, T.; Olsder, G.J. Dynamic Noncooperative Game Theory, 2nd ed.; SIAM: New York, NY, USA, 1999. [Google Scholar]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Schaefer, R.F.; Boche, H.; Poor, H.V. Super-Activation as a Unique Feature of Secure Communication in Malicious Environments. Information 2016, 7, 24. https://doi.org/10.3390/info7020024
Schaefer RF, Boche H, Poor HV. Super-Activation as a Unique Feature of Secure Communication in Malicious Environments. Information. 2016; 7(2):24. https://doi.org/10.3390/info7020024
Chicago/Turabian StyleSchaefer, Rafael F., Holger Boche, and H. Vincent Poor. 2016. "Super-Activation as a Unique Feature of Secure Communication in Malicious Environments" Information 7, no. 2: 24. https://doi.org/10.3390/info7020024
APA StyleSchaefer, R. F., Boche, H., & Poor, H. V. (2016). Super-Activation as a Unique Feature of Secure Communication in Malicious Environments. Information, 7(2), 24. https://doi.org/10.3390/info7020024






